Introduction to Computer Organization and Architecture Lecture 2








![One-Address Instruction Thus, C [A]+[B] can be implemented as (Assembly Language) Move A Add One-Address Instruction Thus, C [A]+[B] can be implemented as (Assembly Language) Move A Add](https://slidetodoc.com/presentation_image/6952d6f672df6fcc070ff0a0c9e6d9fe/image-60.jpg)
![One-Address Instruction In the IBM PC, C [A]+[B] can be implemented as ; Assembly One-Address Instruction In the IBM PC, C [A]+[B] can be implemented as ; Assembly](https://slidetodoc.com/presentation_image/6952d6f672df6fcc070ff0a0c9e6d9fe/image-61.jpg)

![Using Processor Registers for Arithmetic Operations C=A+B that is, C [A]+[B] can be implemented Using Processor Registers for Arithmetic Operations C=A+B that is, C [A]+[B] can be implemented](https://slidetodoc.com/presentation_image/6952d6f672df6fcc070ff0a0c9e6d9fe/image-63.jpg)
![If One of the Arithmetic Operands is in Memory C=A+B that is, C [A]+[B] If One of the Arithmetic Operands is in Memory C=A+B that is, C [A]+[B]](https://slidetodoc.com/presentation_image/6952d6f672df6fcc070ff0a0c9e6d9fe/image-64.jpg)




![Subroutine Calling p p Link register: n Call SUB n Return LR <- [PC] Subroutine Calling p p Link register: n Call SUB n Return LR <- [PC]](https://slidetodoc.com/presentation_image/6952d6f672df6fcc070ff0a0c9e6d9fe/image-80.jpg)

- Slides: 86

Introduction to Computer Organization and Architecture Lecture 2 By Juthawut Chantharamalee http: //dusithost. dusit. ac. th/~juthawut_cha/ home. htm

Outline Information representation p Arithmetic operations (addition and subtraction) p Instruction Formats p Addressing Modes p Assembly Language Programming p Basic input/output operations p Subroutine linkage p Introduction to Computer Organization and Architecture 2

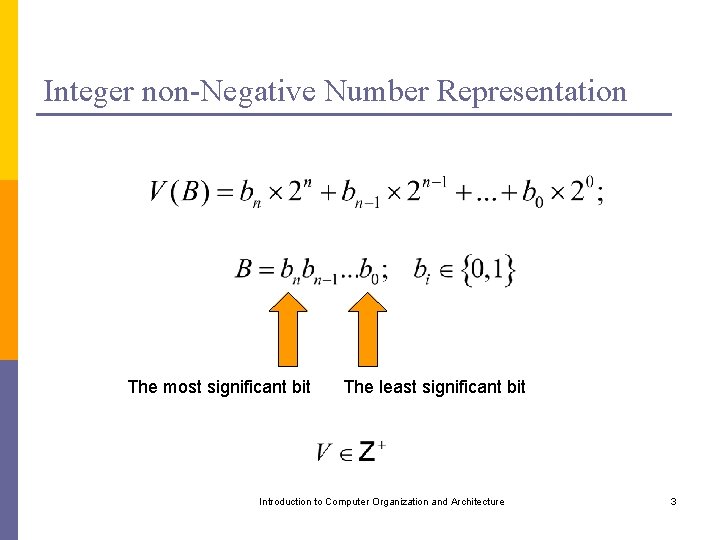
Integer non-Negative Number Representation The most significant bit The least significant bit Introduction to Computer Organization and Architecture 3

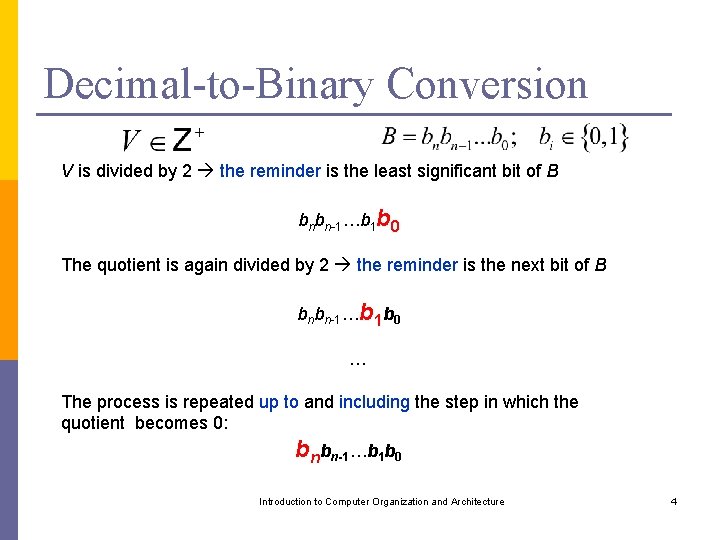
Decimal-to-Binary Conversion V is divided by 2 the reminder is the least significant bit of B bnbn-1…b 1 b 0 The quotient is again divided by 2 the reminder is the next bit of B bnbn-1…b 1 b 0 … The process is repeated up to and including the step in which the quotient becomes 0: bnbn-1…b 1 b 0 Introduction to Computer Organization and Architecture 4

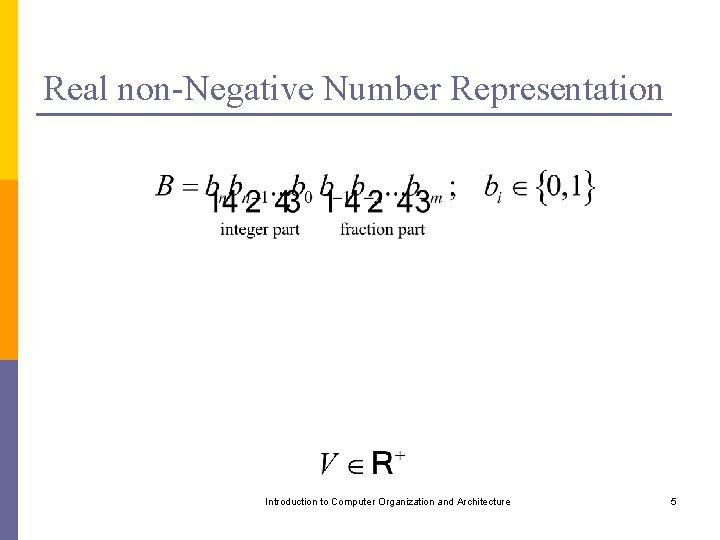
Real non-Negative Number Representation Introduction to Computer Organization and Architecture 5

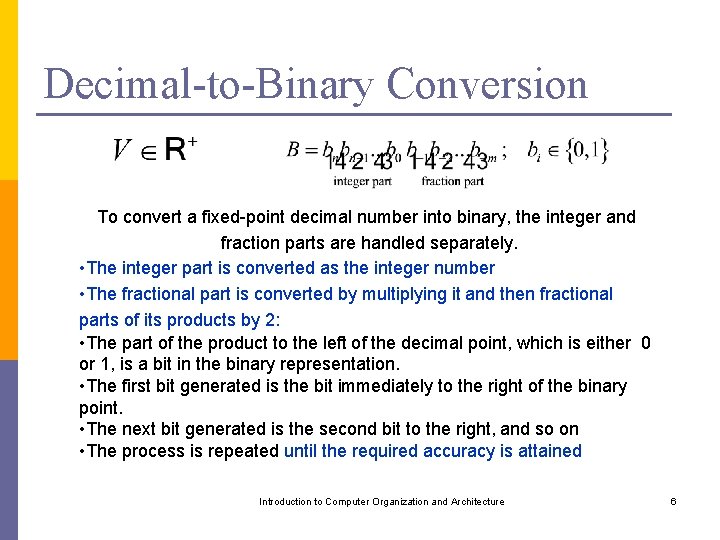
Decimal-to-Binary Conversion To convert a fixed-point decimal number into binary, the integer and fraction parts are handled separately. • The integer part is converted as the integer number • The fractional part is converted by multiplying it and then fractional parts of its products by 2: • The part of the product to the left of the decimal point, which is either 0 or 1, is a bit in the binary representation. • The first bit generated is the bit immediately to the right of the binary point. • The next bit generated is the second bit to the right, and so on • The process is repeated until the required accuracy is attained Introduction to Computer Organization and Architecture 6

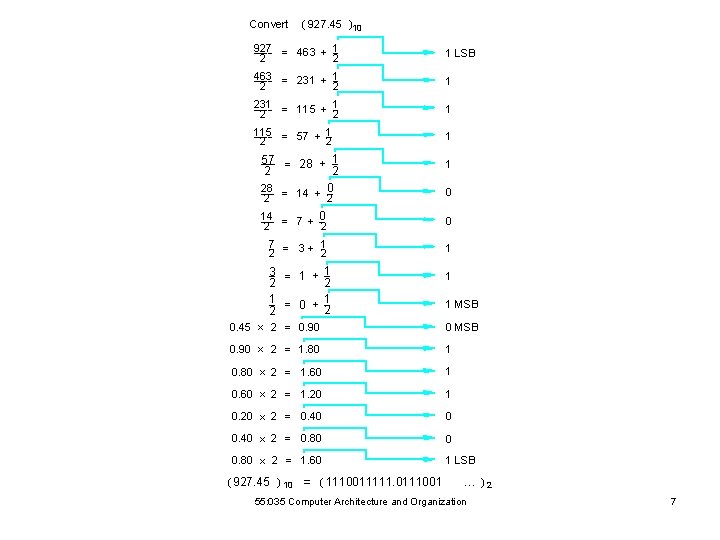
Convert ( 927. 45 ) 10 927 1 -------2 - = 463 + --2 - 1 LSB 463 1 -------2 - = 231 + --2 - 1 231 1 -------2 - = 115 + --2 - 1 115 1 -------2 - = 57 + -2 1 57 ------ = 28 + 1 --2 2 28 ------ = 14 + 0 --2 2 1 0 0 14 ----2 - = 7 + --2 - 0 7 --2 - = 3 + 1 --2 - 1 3 --- = 1 + 1 --2 2 1 --- = 0 + 1 -22 1 1 MSB 0. 45 ´ 2 = 0. 90 0 MSB 0. 90 ´ 2 = 1. 80 1 0. 80 ´ 2 = 1. 60 1 0. 60 ´ 2 = 1. 20 1 0. 20 ´ 2 = 0. 40 0 0. 40 ´ 2 = 0. 80 0 0. 80 ´ 2 = 1. 60 1 LSB ( 927. 45 ) 10 = ( 1110011111. 0111001 ¼ )2 55: 035 Computer Architecture and Organization 7

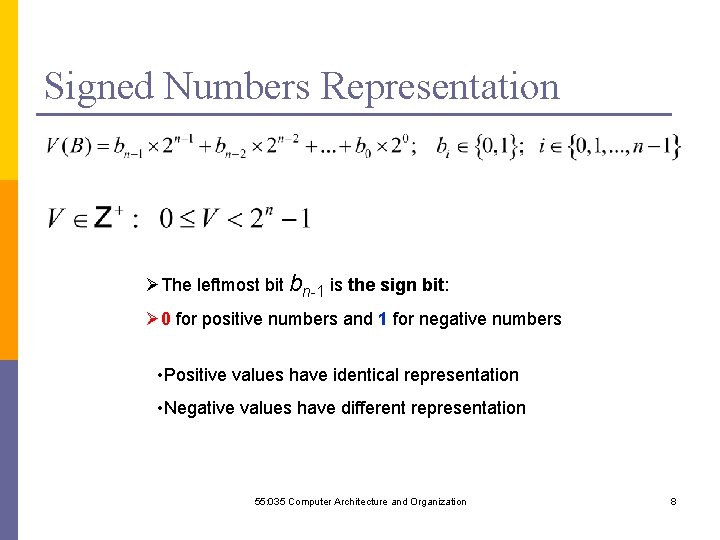
Signed Numbers Representation ØThe leftmost bit bn-1 is the sign bit: Ø 0 for positive numbers and 1 for negative numbers • Positive values have identical representation • Negative values have different representation 55: 035 Computer Architecture and Organization 8

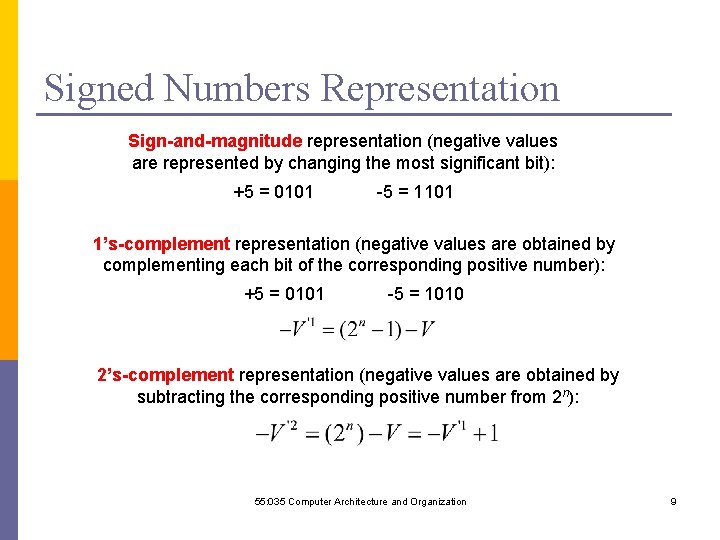
Signed Numbers Representation Sign-and-magnitude representation (negative values are represented by changing the most significant bit): +5 = 0101 -5 = 1101 1’s-complement representation (negative values are obtained by complementing each bit of the corresponding positive number): +5 = 0101 -5 = 1010 2’s-complement representation (negative values are obtained by subtracting the corresponding positive number from 2 n): 55: 035 Computer Architecture and Organization 9

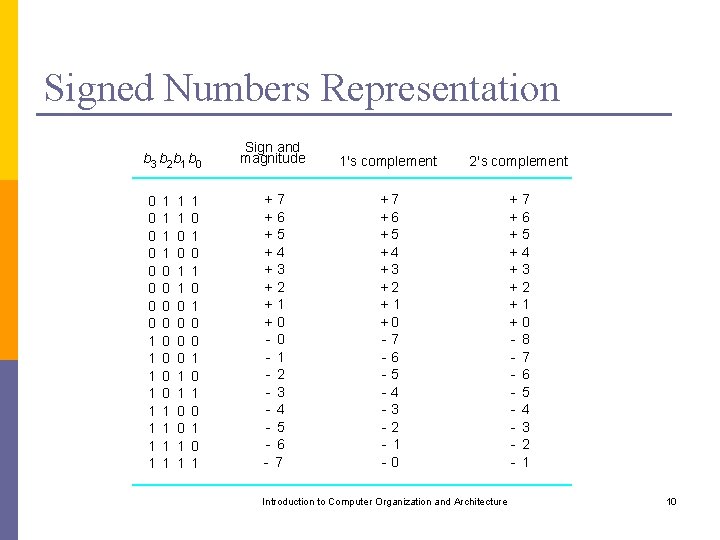
Signed Numbers Representation b 3 b 2 b 1 b 0 0 0 0 0 1 1 1 0 0 0 0 1 1 1 0 0 1 1 1 0 1 0 1 Sign and magnitude 1's complement +7 +6 +5 +4 +3 +2 +1 +0 - 1 - 2 - 3 - 4 - 5 - 6 - 7 +7 +6 +5 +4 +3 +2 +1 +0 -7 -6 -5 -4 -3 -2 - 1 -0 2's complement Introduction to Computer Organization and Architecture + + + + - 7 6 5 4 3 2 1 0 8 7 6 5 4 3 2 1 10

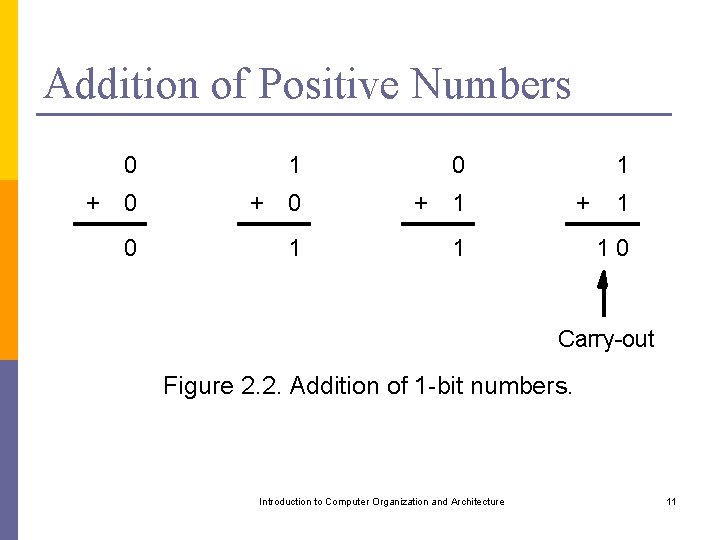
Addition of Positive Numbers 0 + 0 0 1 + 0 1 0 + 1 1 10 Carry-out Figure 2. 2. Addition of 1 -bit numbers. Introduction to Computer Organization and Architecture 11

S/M and 1’s-Complement Representation Since we can’t perform addition and subtraction in the same manner, development of special circuitry for subtraction is needed p 1’s-Complement Representation does not allow a universal representation of 0: there are +0 and -0 that become formally different values p Introduction to Computer Organization and Architecture 12

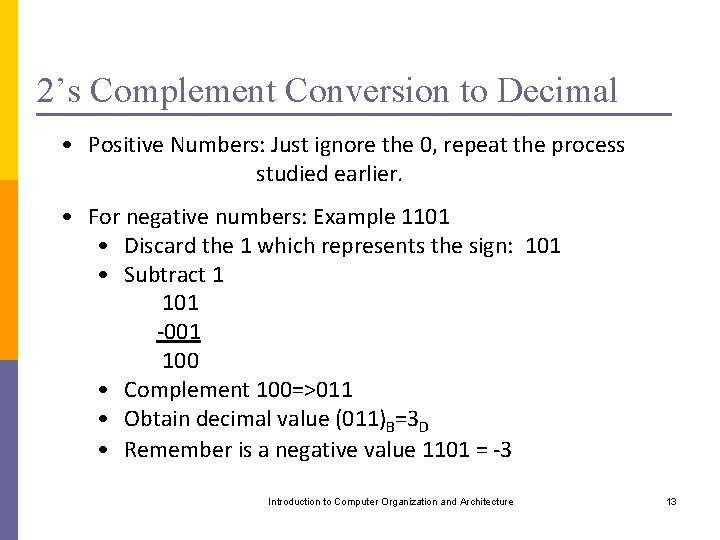
2’s Complement Conversion to Decimal • Positive Numbers: Just ignore the 0, repeat the process studied earlier. • For negative numbers: Example 1101 • Discard the 1 which represents the sign: 101 • Subtract 1 101 -001 100 • Complement 100=>011 • Obtain decimal value (011)B=3 D • Remember is a negative value 1101 = -3 Introduction to Computer Organization and Architecture 13

Decimal Conversion to 2’s Complement Positive Numbers • Find signed representation Negative numbers • Subtract number from 2 n • Find signed representation Introduction to Computer Organization and Architecture 14

Addition of 2’s-Complement Numbers n To add two numbers, add their n-bit representations, ignoring the carry-out signal from the most significant bit (MSB) position. Note: The sum will be correct in the 2’s complement representation as long as the answer is in the range -2 n-1 through 2 n-1 -1 Introduction to Computer Organization and Architecture 15

Subtraction of 2’s-Complement Numbers n To subtract two numbers X and Y, that is, to perform X-Y, form the 2’s-complement of Y and then add it to X according to the addition rule. Note: The result will be correct in the 2’s complement representation as long as the answer is in the range -2 n-1 through 2 n -1 -1 Introduction to Computer Organization and Architecture 16

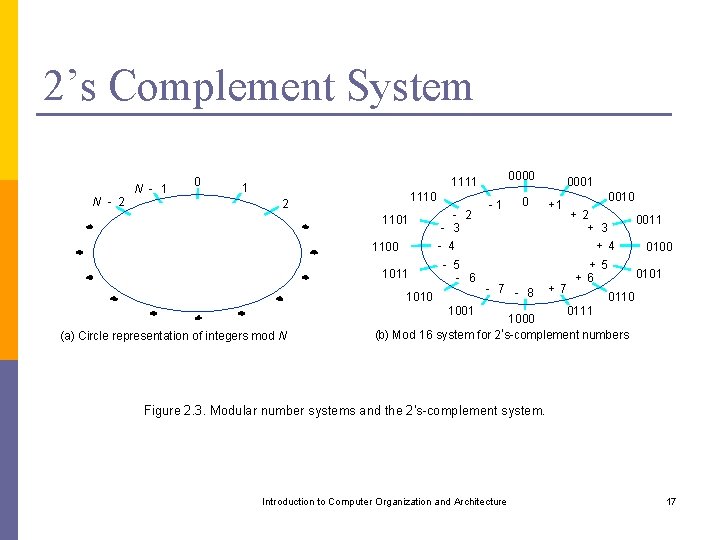
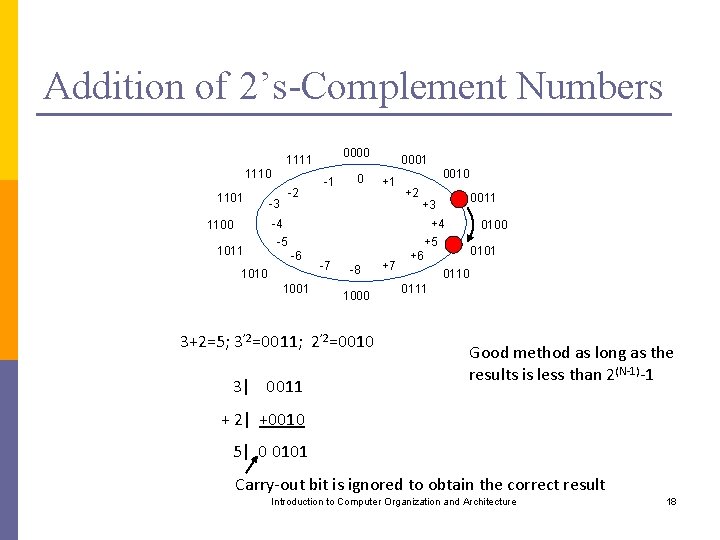
2’s Complement System N - 2 N - 1 0 0000 1111 1 1110 2 1101 - 2 - 3 -1 0 +1 0010 + 2 + 3 - 4 1100 1011 - 5 - 6 1010 0011 + 4 - 7 - 8 1001 (a) Circle representation of integers mod N 0001 + 7 + 5 + 6 0100 0101 0110 0111 1000 (b) Mod 16 system for 2's-complement numbers Figure 2. 3. Modular number systems and the 2's-complement system. Introduction to Computer Organization and Architecture 17

Addition of 2’s-Complement Numbers 0000 1111 1110 1101 -2 -3 -1 0 0001 +1 0010 +2 -4 1100 1011 0011 +3 +4 -5 0100 +5 -6 1010 1001 -7 -8 1000 3+2=5; 3’ 2=0011; 2’ 2=0010 3| 0011 +7 0101 +6 0110 0111 Good method as long as the results is less than 2(N-1)-1 + 2| +0010 5| 0 0101 Carry-out bit is ignored to obtain the correct result Introduction to Computer Organization and Architecture 18

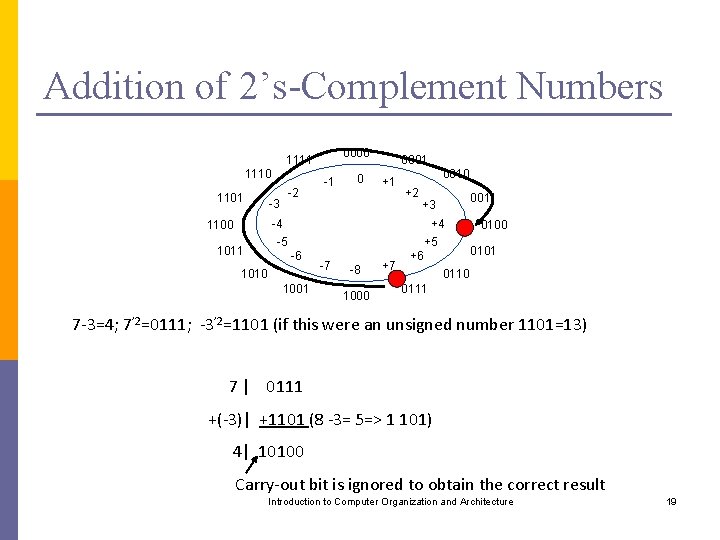
Addition of 2’s-Complement Numbers 0000 1111 1110 1101 -2 -3 -1 0 0001 +1 0010 +2 -4 1100 1011 0011 +3 +4 -5 +5 -6 1010 1001 -7 -8 1000 +7 0100 0101 +6 0110 0111 7 -3=4; 7’ 2=0111; -3’ 2=1101 (if this were an unsigned number 1101=13) 7 | 0111 +(-3)| +1101 (8 -3= 5=> 1 101) 4| 10100 Carry-out bit is ignored to obtain the correct result Introduction to Computer Organization and Architecture 19

2’s-Complement Addition p The 2’s-Complement System is the most efficient for addition and subtraction of signed numbers because both can be performed in the same manner for both positive and negative numbers p Same manner=Same circuitry=Less $$$$ Introduction to Computer Organization and Architecture 20

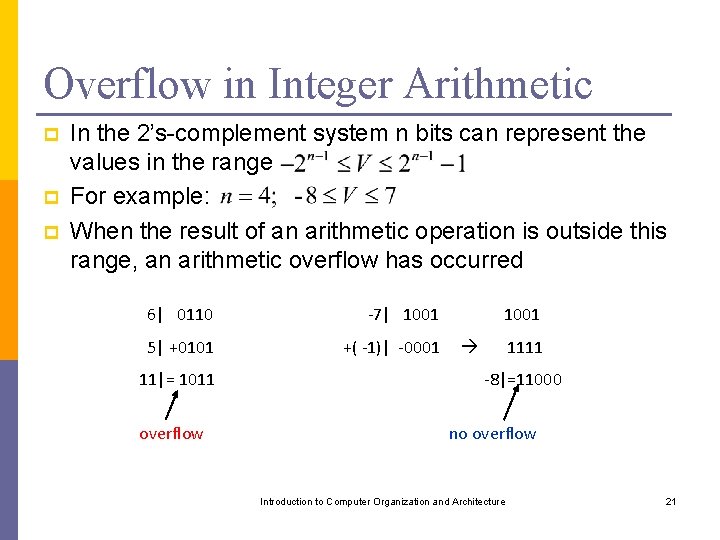
Overflow in Integer Arithmetic p p p In the 2’s-complement system n bits can represent the values in the range For example: When the result of an arithmetic operation is outside this range, an arithmetic overflow has occurred 6| 0110 -7| 1001 5| +0101 +( -1)| -0001 11|= 1011 overflow 1001 1111 -8|=11000 no overflow Introduction to Computer Organization and Architecture 21

Overflow in Integer Arithmetic p Overflow can occur only when adding two numbers that have the same sign p The carry-out signal from the sign-bit position is not a sufficient indicator of overflow when adding signed numbers A simple way to detect overflow is to examine the signs of the two summands (X and Y ) and the sign of the result S (S=X+Y). When both operands X and Y have the same sign, an overflow occurs if the sign of sum S is not the same as the signs of X and Y. p p Introduction to Computer Organization and Architecture 22

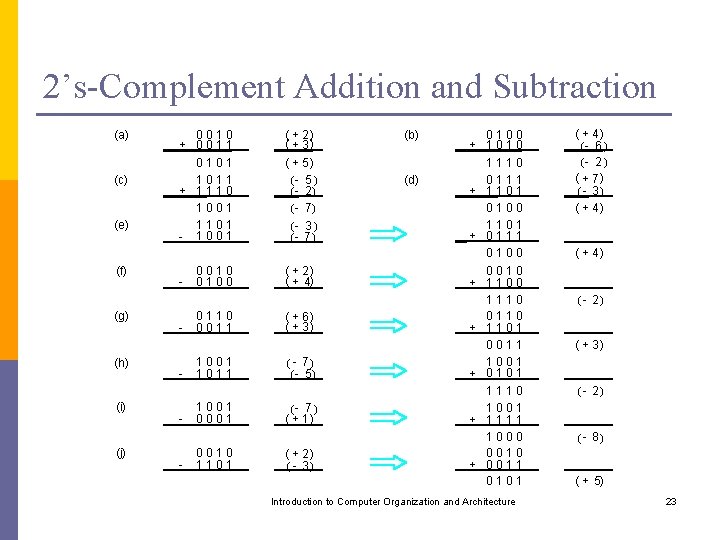
2’s-Complement Addition and Subtraction (a) (c) (e) (f) (g) (h) (i) (j) 0 0 1 0 + 0 0 1 1 + 1 1 1 0 0 1 1 1 0 1 - 1 0 0 1 - - - 0 0 1 0 0 0 1 1 1 0 0 0 1 0 1 ( + 2) ( + 3) ( + 5) (- 5 ) ( - 2) ( - 7) (- 3 ) (- 7 ) ( + 2) ( + 4) ( + 6) ( + 3) ( - 7) ( - 5) (- 7 ) ( + 1) ( + 2) ( - 3) (b) (d) 0 1 0 0 + 1 0 1 1 1 0 0 1 1 1 + 1 1 0 1 0 0 1 1 0 1 + 0 1 1 1 0 0 0 0 1 0 + 1 1 0 0 1 1 1 0 0 1 + 0 1 1 1 1 0 0 1 + 1 1 1 0 0 0 1 0 + 0 0 1 1 0 1 Introduction to Computer Organization and Architecture ( + 4) (- 6 ) (- 2 ) ( + 7) ( - 3) ( + 4) ( - 2) ( + 3) ( - 2) ( - 8) ( + 5) 23

Comparison of Signed Representations Introduction to Computer Organization and Architecture 24

Character Representation Each character is encoded by 8 bits p American Standards Committee on Information Interchange (ASCII) encoding system – 7 bits encoding p The 8 th (most significant) bit is used to encode characters from different alphabets and some extra special symbols p Introduction to Computer Organization and Architecture 25

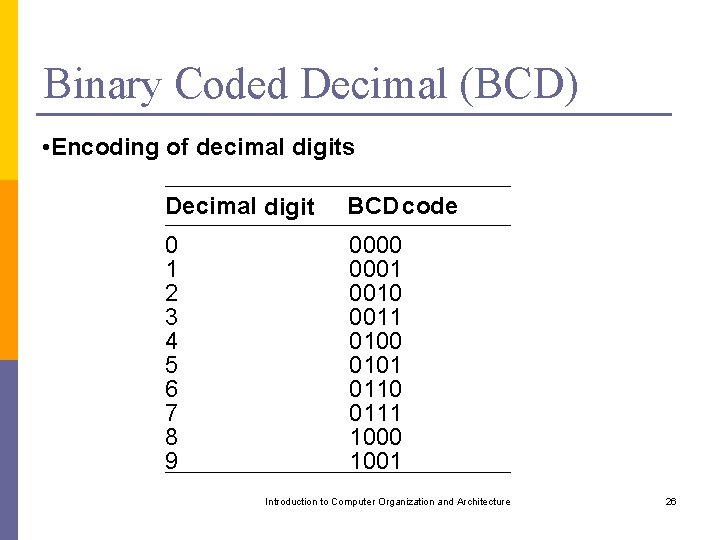
Binary Coded Decimal (BCD) • Encoding of decimal digits Decimal digit BCD code 0 1 2 3 4 5 6 7 8 9 0000 0001 0010 0011 0100 0101 0110 0111 1000 1001 Introduction to Computer Organization and Architecture 26

Hexadecimal Numbers p Base 16 ={0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A, B, C, D, E, F} (Z 3 Z 2 Z 1 Z 0)H= (Z 3 x 163)+(Z 3 x 162)+(Z 3 x 161)+(Z 3 x 160)= (Z 3 x 4096)+(Z 3 x 256)+(Z 3 x 1) p Example: (A 34 E)H= (A x 163)+(3 x 162)+(4 x 161)+(E x 160)= (Ax 4096)+(3 x 256)+(4 x 16)+(E x 1)= (10 x 4096)+(3 x 256)+(4 x 16)+(14 x 1)= 40960+768+64+14=41806. p Introduction to Computer Organization and Architecture 27

Hexadecimal Numbers Advantages Easier to represent large numbers in compact manner p Close relationship to binary numbers Ex. : Find the binary representation of 1101011101 110 1011 0101 1101 p 6 D=6 H 11 D=BH 5 D=5 H 13 D=CH (1101011101)B=(6 B 5 C)H 55: 035 Computer Architecture and Organization 28

Conversion Hexadecimal-Decimal p Hexadecimal to Decimal: As shown on previous slide p Decimal to HEX: Same process as with binary. Example: (1574)D=(? )H 1974 / 16 = 123 rem 6 123 / 16 = 7 rem 11 Hence (1574)D=(7 B 6)H Introduction to Computer Organization and Architecture 29

Table of ASCII Characters Char (nul) (soh) (eot) (enq) (ack) (bel) (bs) (ht) (nl) (vt) (cr) (so) (si) (dle) (dc 1) (dc 2) (dc 3) (dc 4) (nak) (syn) (etb) (can) (em) (sub) (fs) (gs) (rs) (us) Hex 0 x 00 0 x 01 0 x 04 0 x 05 0 x 06 0 x 07 0 x 08 0 x 09 0 x 0 a 0 x 0 b 0 x 0 d 0 x 0 e 0 x 0 f 0 x 10 0 x 11 0 x 12 0 x 13 0 x 14 0 x 15 0 x 16 0 x 17 0 x 18 0 x 19 0 x 1 a 0 x 1 c 0 x 1 d 0 x 1 e 0 x 1 f Char (sp) ! $ % & ' ( ) * +. / 0 1 2 3 4 5 6 7 8 9 : < = > ? Hex 0 x 20 0 x 21 0 x 24 0 x 25 0 x 26 0 x 27 0 x 28 0 x 29 0 x 2 a 0 x 2 b 0 x 2 d 0 x 2 e 0 x 2 f 0 x 30 0 x 31 0 x 32 0 x 33 0 x 34 0 x 35 0 x 36 0 x 37 0 x 38 0 x 39 0 x 3 a 0 x 3 c 0 x 3 d 0 x 3 e 0 x 3 f Char @ A D E F G H I J K M N O P Q R S T U V W X Y Z ] ^ _ Hex 0 x 40 0 x 41 0 x 44 0 x 45 0 x 46 0 x 47 0 x 48 0 x 49 0 x 4 a 0 x 4 b 0 x 4 d 0 x 4 e 0 x 4 f 0 x 50 0 x 51 0 x 52 0 x 53 0 x 54 0 x 55 0 x 56 0 x 57 0 x 58 0 x 59 0 x 5 a 0 x 5 c 0 x 5 d 0 x 5 e 0 x 5 f Char ` a d e f g h i j k m n o p q r s t u v w x y z | } ~ (del) Introduction to Computer Organization and Architecture Hex 0 x 60 0 x 61 0 x 64 0 x 65 0 x 66 0 x 67 0 x 68 0 x 69 0 x 6 a 0 x 6 b 0 x 6 d 0 x 6 e 0 x 6 f 0 x 70 0 x 71 0 x 72 0 x 73 0 x 74 0 x 75 0 x 76 0 x 77 0 x 78 0 x 79 0 x 7 a 0 x 7 c 0 x 7 d 0 x 7 e 0 x 7 f 30

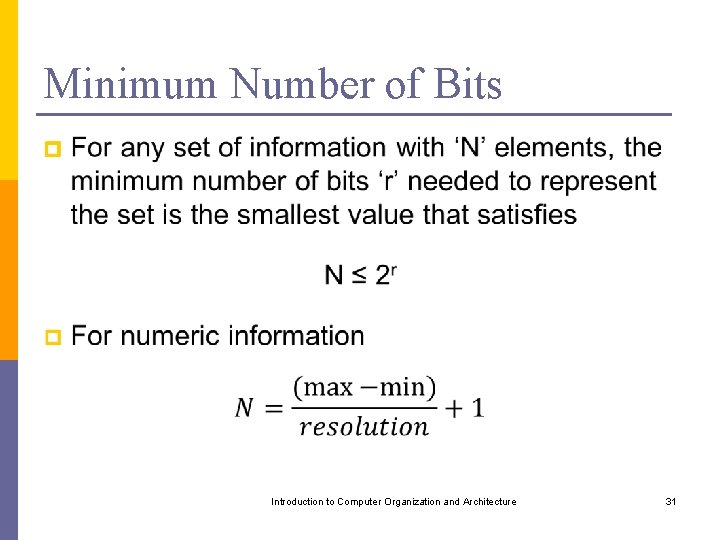
Minimum Number of Bits p Introduction to Computer Organization and Architecture 31

Memory ………………. Cells Each cell can store 1 bit of information having the value 0 or 1 Introduction to Computer Organization and Architecture 32

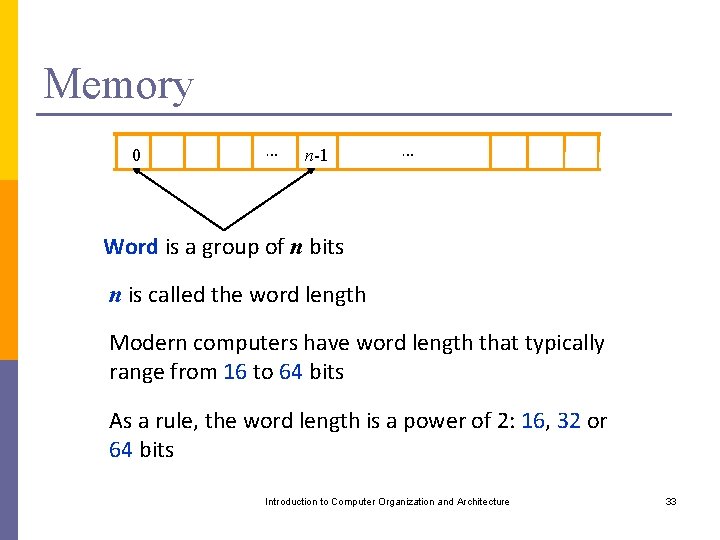
Memory 0 … n-1 … Word is a group of n bits n is called the word length Modern computers have word length that typically range from 16 to 64 bits As a rule, the word length is a power of 2: 16, 32 or 64 bits Introduction to Computer Organization and Architecture 33

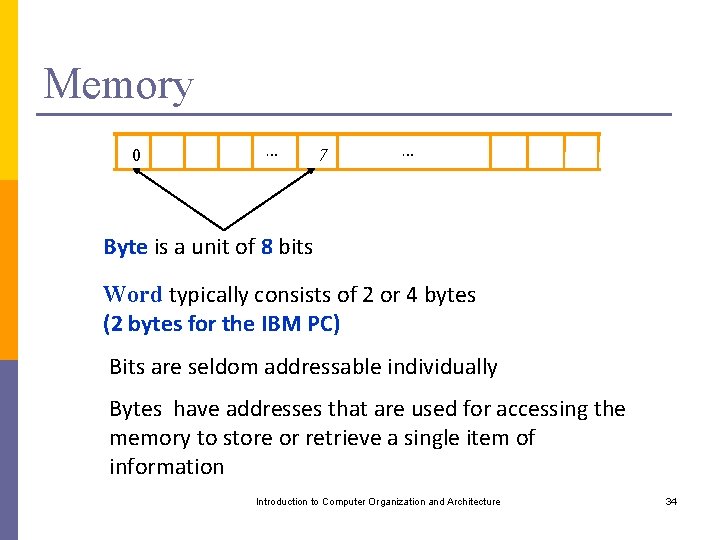
Memory 0 … 7 … Byte is a unit of 8 bits Word typically consists of 2 or 4 bytes (2 bytes for the IBM PC) Bits are seldom addressable individually Bytes have addresses that are used for accessing the memory to store or retrieve a single item of information Introduction to Computer Organization and Architecture 34

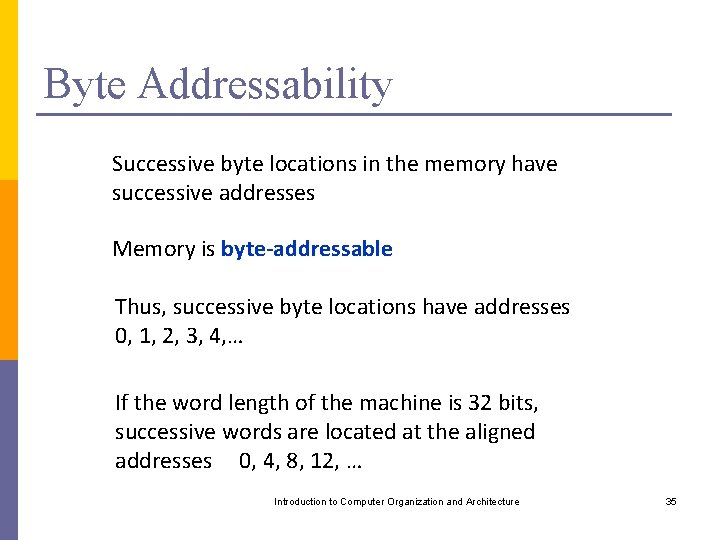
Byte Addressability Successive byte locations in the memory have successive addresses Memory is byte-addressable Thus, successive byte locations have addresses 0, 1, 2, 3, 4, … If the word length of the machine is 32 bits, successive words are located at the aligned addresses 0, 4, 8, 12, … Introduction to Computer Organization and Architecture 35

Memory n bits first word (0) second word (4) • • • i th word • • • last word Introduction to Computer Organization and Architecture 36

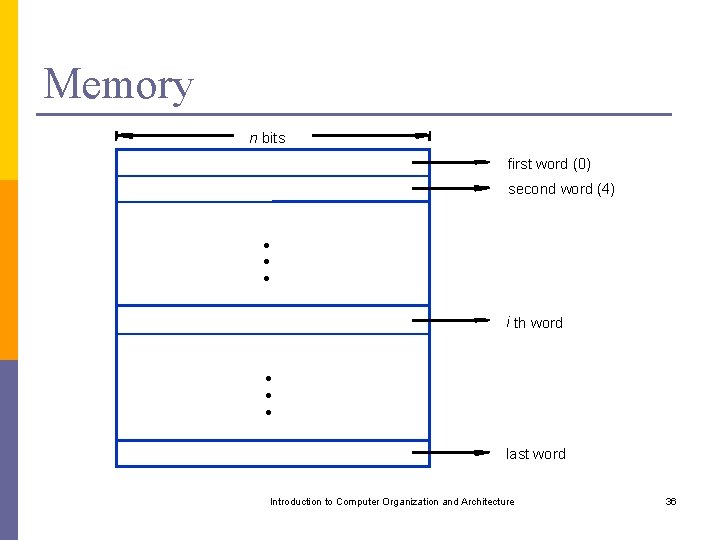
Encoded Information 32 bits b 1 b 0 • • • b 31 b 30 Sign bit: b 31= 0 for positive numbers b 31= 1 for negative numbers (a) A signed integer 8 bits ASCII character 8 bits ASCII character (b) Four characters Introduction to Computer Organization and Architecture 37

Memory Usually numbers from 0 through 2 k-1 for some suitable value of k are used as the addresses of successive locations (bytes) in the memory The 2 k addresses constitutes the address space of the computer, and the memory has up to 2 k addressable locations Introduction to Computer Organization and Architecture 38

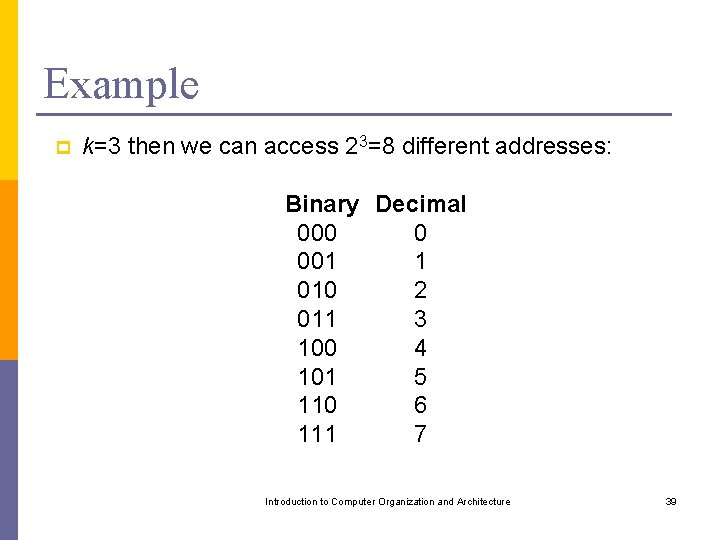
Example p k=3 then we can access 23=8 different addresses: Binary Decimal 000 0 001 1 010 2 011 3 100 4 101 5 110 6 111 7 Introduction to Computer Organization and Architecture 39

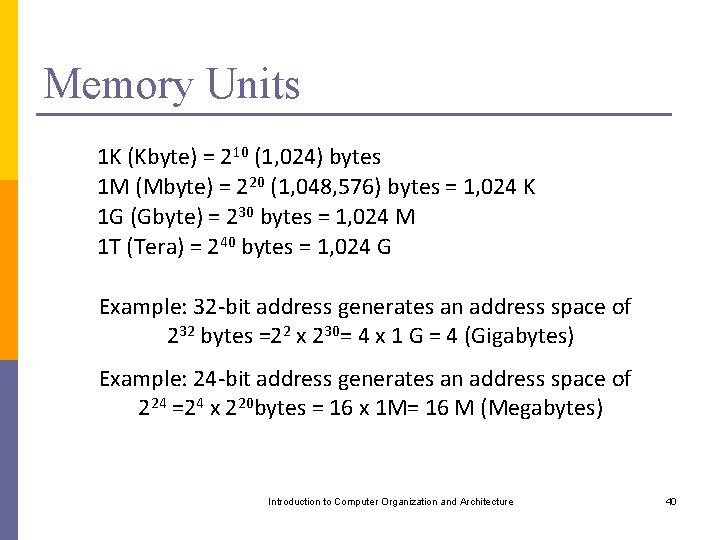
Memory Units 1 K (Kbyte) = 210 (1, 024) bytes 1 M (Mbyte) = 220 (1, 048, 576) bytes = 1, 024 K 1 G (Gbyte) = 230 bytes = 1, 024 M 1 T (Tera) = 240 bytes = 1, 024 G Example: 32 -bit address generates an address space of 232 bytes =22 x 230= 4 x 1 G = 4 (Gigabytes) Example: 24 -bit address generates an address space of 224 =24 x 220 bytes = 16 x 1 M= 16 M (Megabytes) Introduction to Computer Organization and Architecture 40

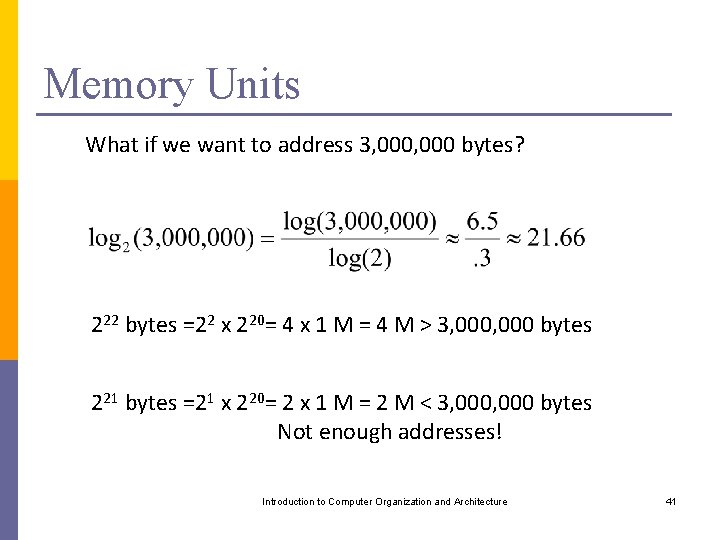
Memory Units What if we want to address 3, 000 bytes? 222 bytes =22 x 220= 4 x 1 M = 4 M > 3, 000 bytes 221 bytes =21 x 220= 2 x 1 M = 2 M < 3, 000 bytes Not enough addresses! Introduction to Computer Organization and Architecture 41

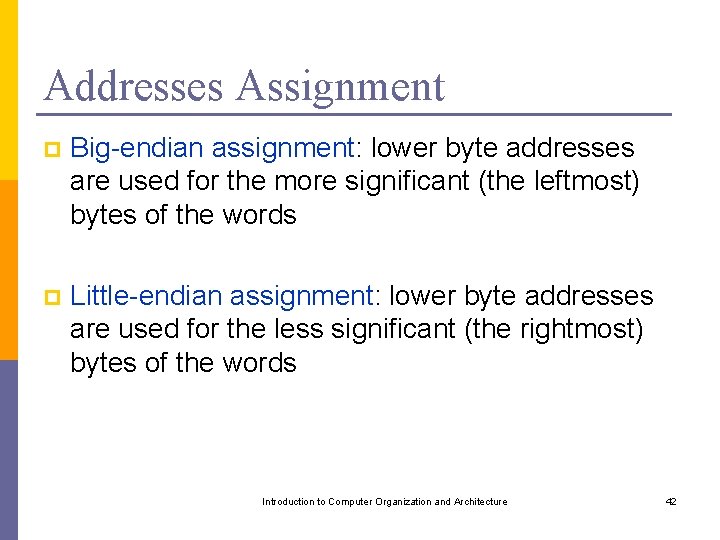
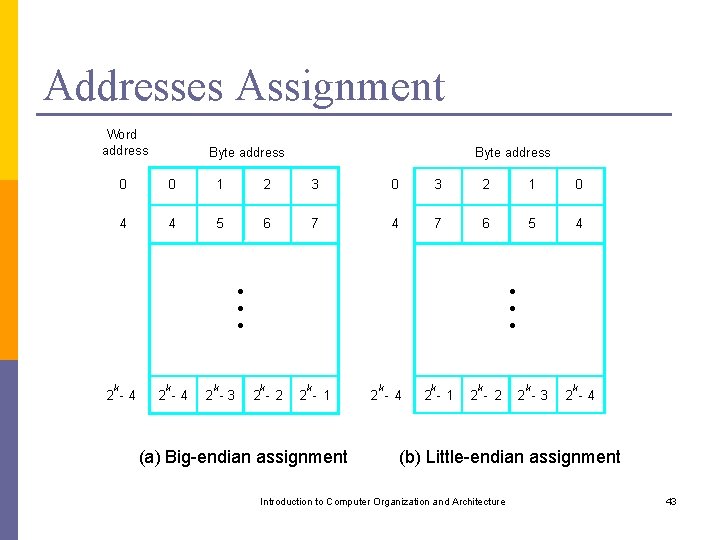
Addresses Assignment p Big-endian assignment: lower byte addresses are used for the more significant (the leftmost) bytes of the words p Little-endian assignment: lower byte addresses are used for the less significant (the rightmost) bytes of the words Introduction to Computer Organization and Architecture 42

Addresses Assignment Word address Byte address 0 0 1 2 3 0 3 2 1 0 4 4 5 6 7 4 7 6 5 4 • • • k 2 -4 k 2 -3 • • • k 2 - 2 k 2 - 1 (a) Big-endian assignment k 2 - 4 k 2 - 1 k 2 - 2 k 2 -3 k 2 -4 (b) Little-endian assignment Introduction to Computer Organization and Architecture 43

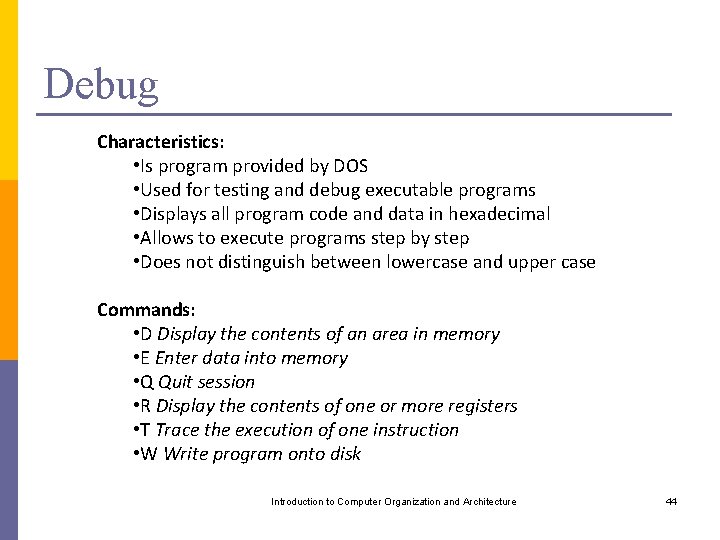
Debug Characteristics: • Is program provided by DOS • Used for testing and debug executable programs • Displays all program code and data in hexadecimal • Allows to execute programs step by step • Does not distinguish between lowercase and upper case Commands: • D Display the contents of an area in memory • E Enter data into memory • Q Quit session • R Display the contents of one or more registers • T Trace the execution of one instruction • W Write program onto disk Introduction to Computer Organization and Architecture 44

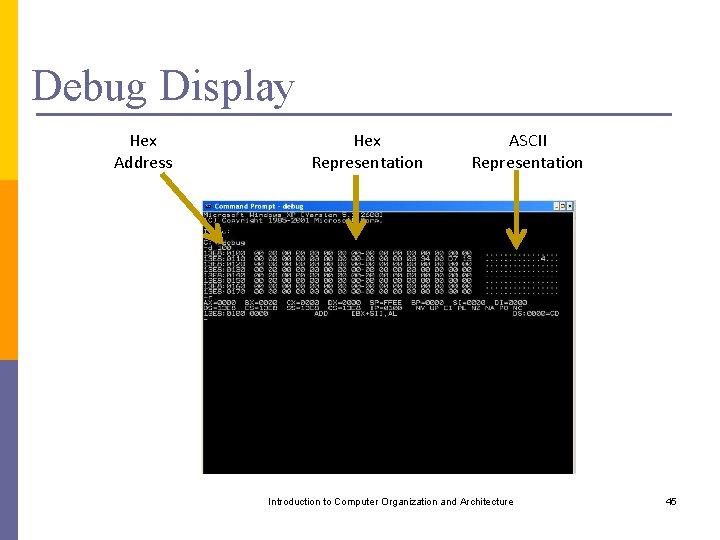
Debug Display Hex Address Hex Representation ASCII Representation Introduction to Computer Organization and Architecture 45

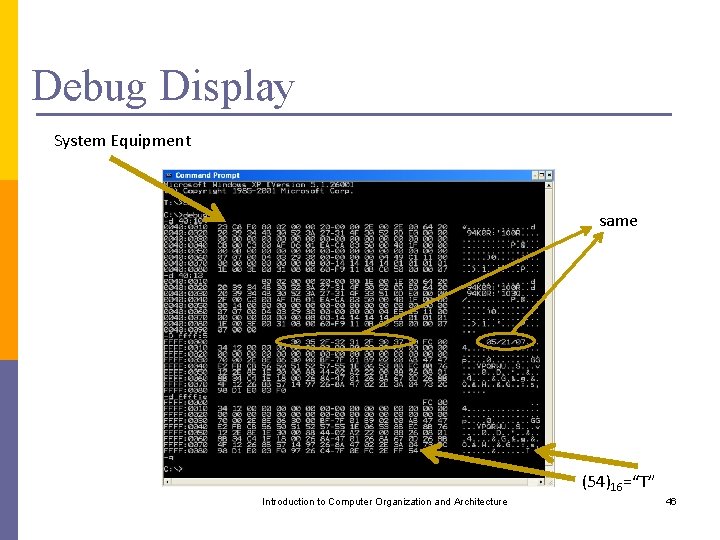
Debug Display System Equipment same (54)16=“T” Introduction to Computer Organization and Architecture 46

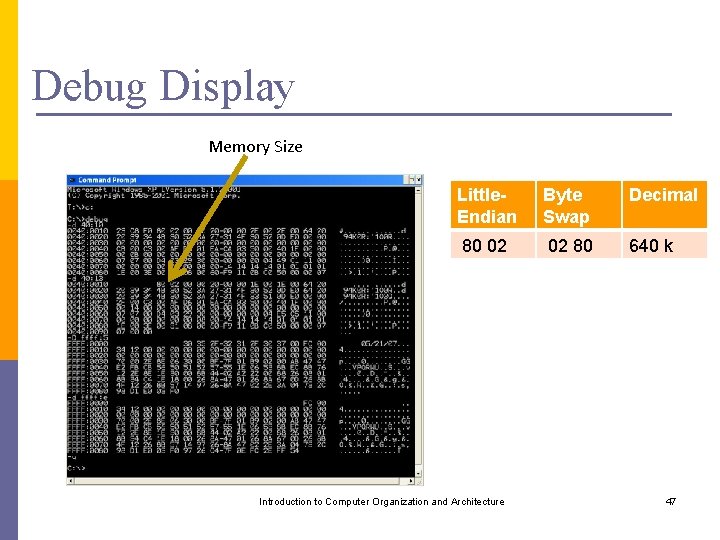
Debug Display Memory Size Little. Endian Byte Swap Decimal 80 02 80 640 k Introduction to Computer Organization and Architecture 47

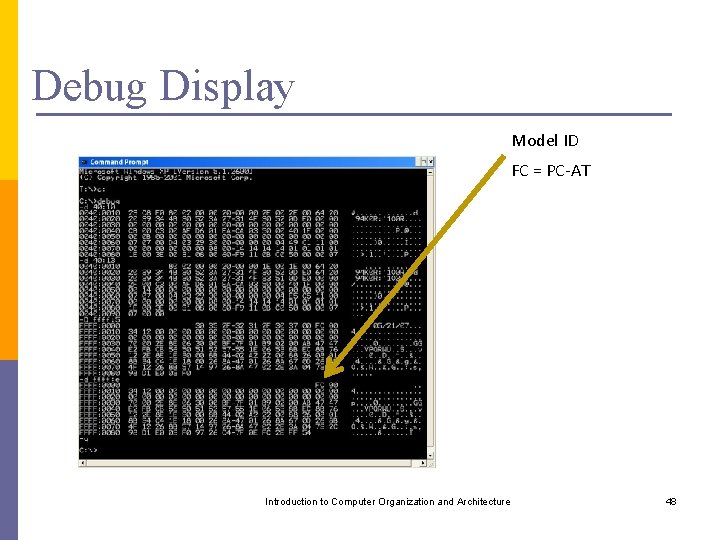
Debug Display Model ID FC = PC-AT Introduction to Computer Organization and Architecture 48

Machine Instructions A computer must have instructions capable of performing four types of operations: p n n Data transfers between the memory and the processor registers Arithmetic and logic operations on data Program sequencing and control Input/Output (I/O) transfers Introduction to Computer Organization and Architecture 49

Data Transfers: Possible Locations Memory locations p Processor registers p Registers in the I/O subsystem p In the instruction itself (immediate data) p Most of the time we identify a location by a symbolic name standing for its hardware binary address: • Memory Locations: LOCA, LOC, PLACE, A, VAR 2, JOHN_SMITH • Processor register names: R 0, R 5, R 10, … • I/O register names: DATAIN, OUTSTATUS Introduction to Computer Organization and Architecture 50

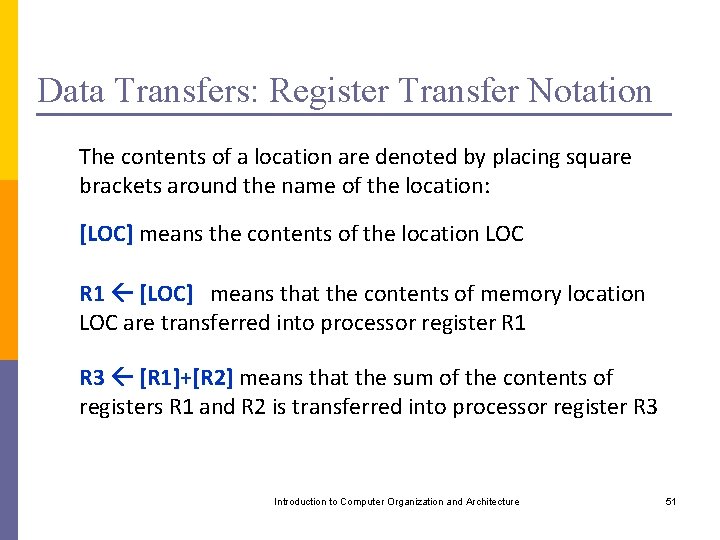
Data Transfers: Register Transfer Notation The contents of a location are denoted by placing square brackets around the name of the location: [LOC] means the contents of the location LOC R 1 [LOC] means that the contents of memory location LOC are transferred into processor register R 1 R 3 [R 1]+[R 2] means that the sum of the contents of registers R 1 and R 2 is transferred into processor register R 3 Introduction to Computer Organization and Architecture 51

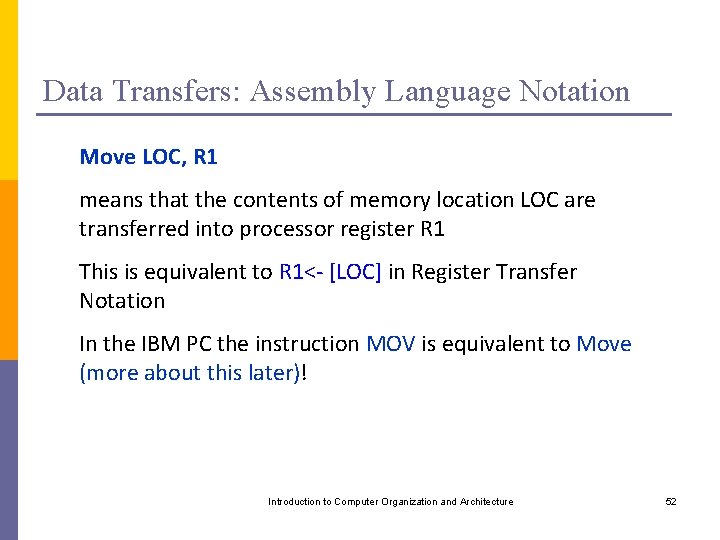
Data Transfers: Assembly Language Notation Move LOC, R 1 means that the contents of memory location LOC are transferred into processor register R 1 This is equivalent to R 1<- [LOC] in Register Transfer Notation In the IBM PC the instruction MOV is equivalent to Move (more about this later)! Introduction to Computer Organization and Architecture 52

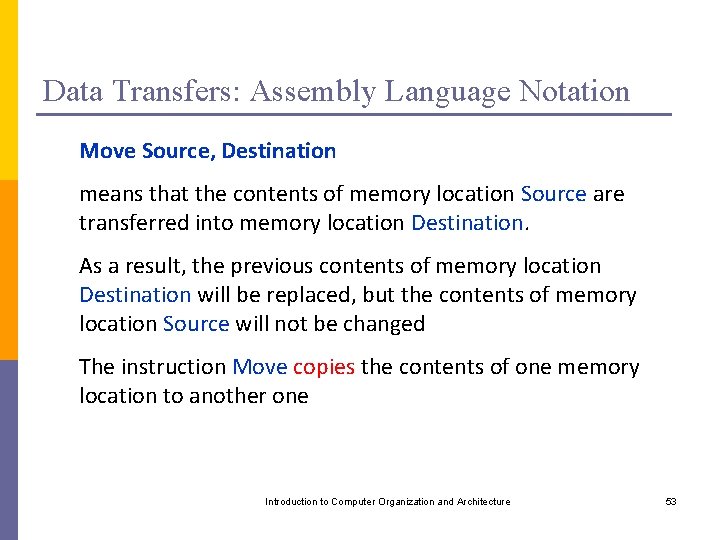
Data Transfers: Assembly Language Notation Move Source, Destination means that the contents of memory location Source are transferred into memory location Destination. As a result, the previous contents of memory location Destination will be replaced, but the contents of memory location Source will not be changed The instruction Move copies the contents of one memory location to another one Introduction to Computer Organization and Architecture 53

What is “Standard” Assembly? Book: IBM PC Assembly • ”Standard” Assembly • Real-life Assembly Language • Format OPcode src, dst Language • Format OPcode dst, src Introduction to Computer Organization and Architecture 54

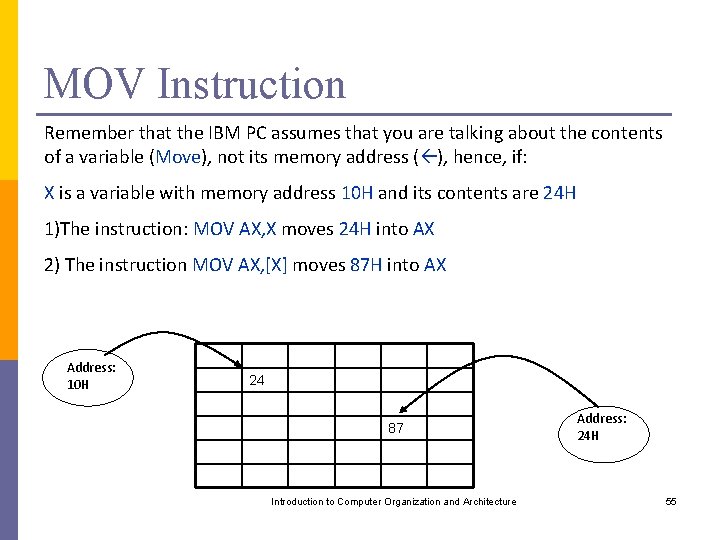
MOV Instruction Remember that the IBM PC assumes that you are talking about the contents of a variable (Move), not its memory address ( ), hence, if: X is a variable with memory address 10 H and its contents are 24 H 1)The instruction: MOV AX, X moves 24 H into AX 2) The instruction MOV AX, [X] moves 87 H into AX Address: 10 H 24 87 Introduction to Computer Organization and Architecture Address: 24 H 55

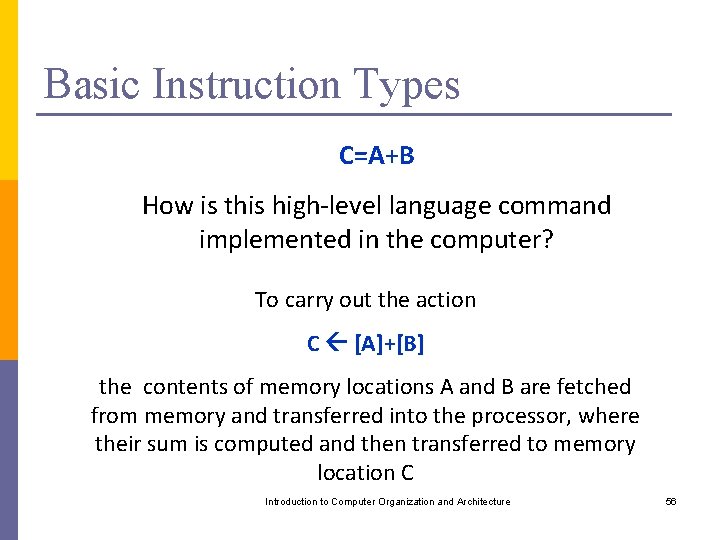
Basic Instruction Types C=A+B How is this high-level language command implemented in the computer? To carry out the action C [A]+[B] the contents of memory locations A and B are fetched from memory and transferred into the processor, where their sum is computed and then transferred to memory location C Introduction to Computer Organization and Architecture 56

Three-Address Instruction General form: Operation Source 1, Source 2, Destination Add A, B, C Disadvantage: This form has 3 operands. If memory addresses were to be used to specify operands, the memory space would be very limited. Example: if k=10 bits (enough for a memory of 1 KB), then 30 bits will be needed for the 3 operands. Introduction to Computer Organization and Architecture 57

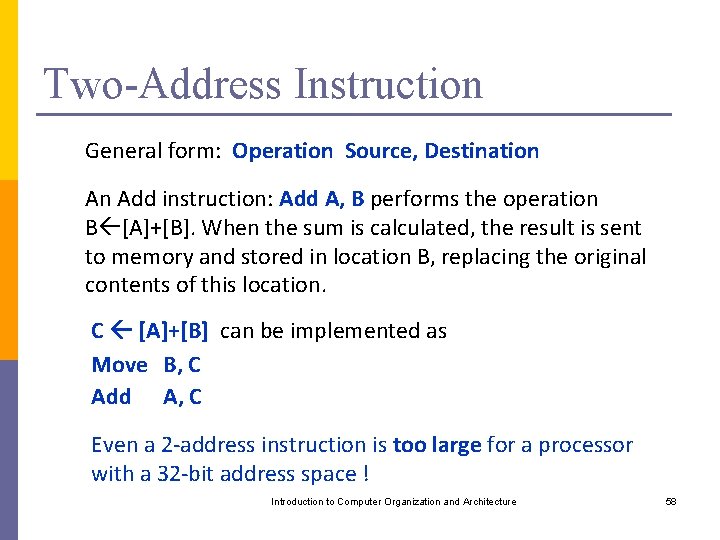
Two-Address Instruction General form: Operation Source, Destination An Add instruction: Add A, B performs the operation B [A]+[B]. When the sum is calculated, the result is sent to memory and stored in location B, replacing the original contents of this location. C [A]+[B] can be implemented as Move B, C Add A, C Even a 2 -address instruction is too large for a processor with a 32 -bit address space ! Introduction to Computer Organization and Architecture 58

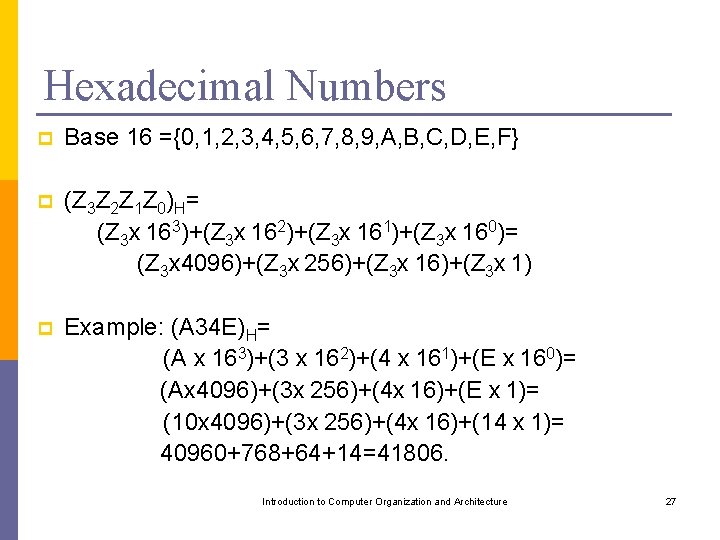
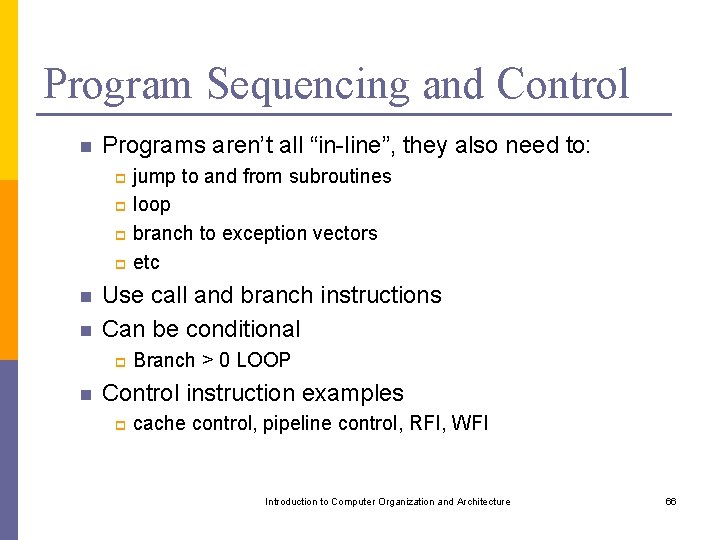
One-Address Instruction General form: Operation Source Examples: Add A means: Add the contents of memory location A to the contents of the accumulator register and place the sum back into the accumulator Move A means: Copy the contents of memory location A to the accumulator register Store A means: Copy the contents of the accumulator register to memory location A Introduction to Computer Organization and Architecture 59
![OneAddress Instruction Thus C AB can be implemented as Assembly Language Move A Add One-Address Instruction Thus, C [A]+[B] can be implemented as (Assembly Language) Move A Add](https://slidetodoc.com/presentation_image/6952d6f672df6fcc070ff0a0c9e6d9fe/image-60.jpg)
One-Address Instruction Thus, C [A]+[B] can be implemented as (Assembly Language) Move A Add B Store C Notice that now the 32 -bits will be use only to access 1 memory location and to denote the operation which means (Register Notation): Accumulator [A] Accumulator [Accumulator] + [B] C [Accumulator] A two-operand instruction, how is it possible? One Register, One memory location Introduction to Computer Organization and Architecture 60
![OneAddress Instruction In the IBM PC C AB can be implemented as Assembly One-Address Instruction In the IBM PC, C [A]+[B] can be implemented as ; Assembly](https://slidetodoc.com/presentation_image/6952d6f672df6fcc070ff0a0c9e6d9fe/image-61.jpg)
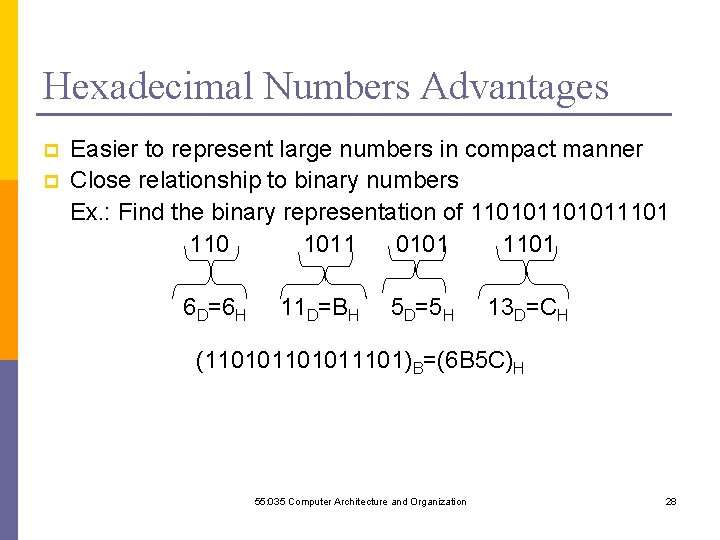
One-Address Instruction In the IBM PC, C [A]+[B] can be implemented as ; Assembly Language Register Notation MOV AX, A ; [AX] [A] ADD AX, B ; [AX] + [B] MOV C, AX ; [C] [ AX] Notice that in the IBM PC Assembly Language the operation “addition” is represented by the instruction “ADD”. The symbol “; ” is used to indicate the start of comments. Comments are useful to remind us what the program is doing, but they do NOT effect the behavior of it Introduction to Computer Organization and Architecture 61

Processor Registers n n n Because the number of registers is relatively small, only a few bits are needed to specify, which register takes part in an operation For example, for 32 registers only 5 bits are needed to address them (while 8 bits are needed to address a single byte in the memory) This makes it possible to use “two”- and “three”- address instructions Introduction to Computer Organization and Architecture 62
![Using Processor Registers for Arithmetic Operations CAB that is C AB can be implemented Using Processor Registers for Arithmetic Operations C=A+B that is, C [A]+[B] can be implemented](https://slidetodoc.com/presentation_image/6952d6f672df6fcc070ff0a0c9e6d9fe/image-63.jpg)
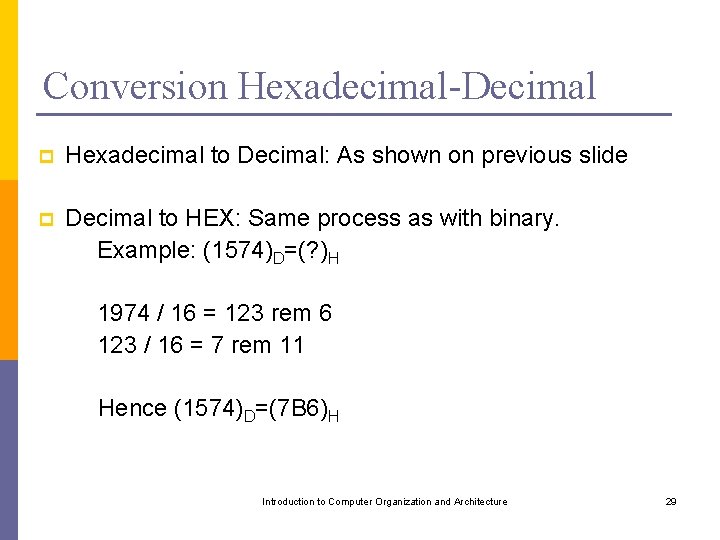
Using Processor Registers for Arithmetic Operations C=A+B that is, C [A]+[B] can be implemented as Move Add Move A, Ri B, Rj Ri, Rj Rj, C 4 instructions If we wanted to do it in this manner, for the IBM PC we would have: MOV ADD MOV DX, A AX, B AX, DX C, AX Introduction to Computer Organization and Architecture 63
![If One of the Arithmetic Operands is in Memory CAB that is C AB If One of the Arithmetic Operands is in Memory C=A+B that is, C [A]+[B]](https://slidetodoc.com/presentation_image/6952d6f672df6fcc070ff0a0c9e6d9fe/image-64.jpg)
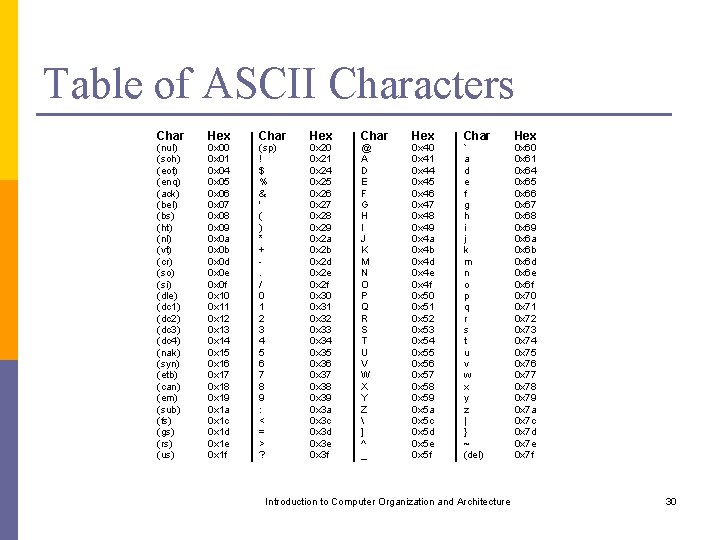
If One of the Arithmetic Operands is in Memory C=A+B that is, C [A]+[B] can be implemented as Move A, Ri Add B, Ri Move Ri, C 3 instructions For the IBM PC we would have: MOV AX, A ADD AX, B MOV C, AX Introduction to Computer Organization and Architecture 64

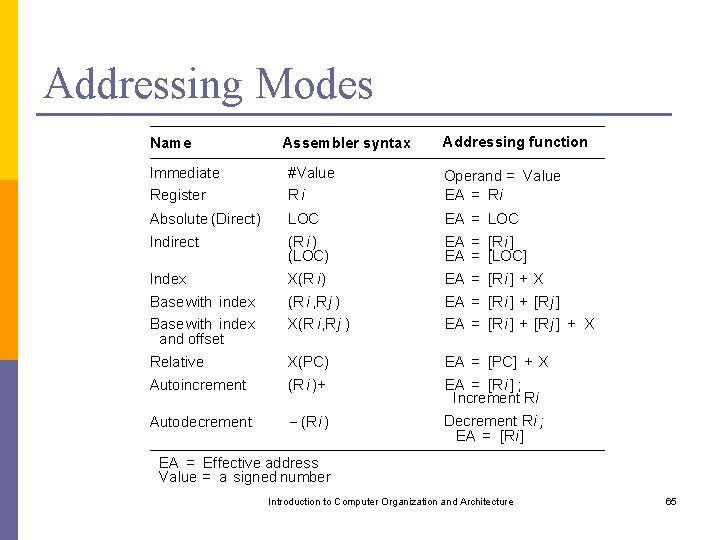
Addressing Modes Name Assembler syntax Addressing function Immediate Register #Value Ri Operand = Value EA = Ri Absolute (Direct) LOC EA = LOC Indirect (Ri ) (LOC) X(R i) EA = [Ri ] EA = [LOC] EA = [Ri ] + X Base with index and offset (Ri , Rj ) X(R i, Rj ) EA = [Ri ] + [Rj ] + X Relative X(PC) EA = [PC] + X Autoincrement (Ri )+ EA = [Ri ] ; Increment Ri Autodecrement (R i ) Decrement Ri ; EA = [Ri] Index EA = Effective address Value = a signed number Introduction to Computer Organization and Architecture 65

Program Sequencing and Control n Programs aren’t all “in-line”, they also need to: jump to and from subroutines p loop p branch to exception vectors p etc p n n Use call and branch instructions Can be conditional p n Branch > 0 LOOP Control instruction examples p cache control, pipeline control, RFI, WFI Introduction to Computer Organization and Architecture 66

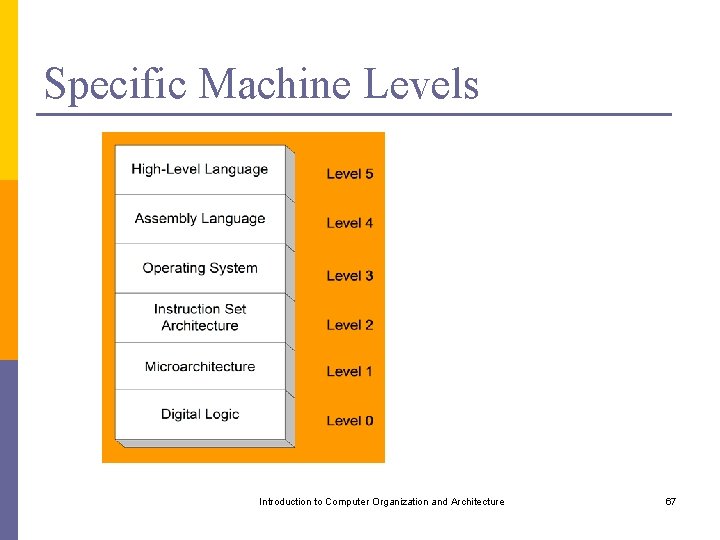
Specific Machine Levels Introduction to Computer Organization and Architecture 67

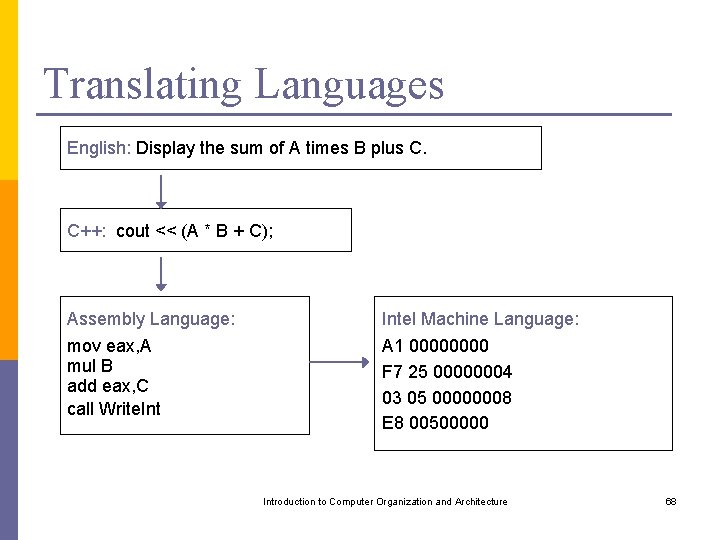
Translating Languages English: Display the sum of A times B plus C. C++: cout << (A * B + C); Assembly Language: Intel Machine Language: mov eax, A mul B add eax, C call Write. Int A 1 0000 F 7 25 00000004 03 05 00000008 E 8 00500000 Introduction to Computer Organization and Architecture 68

Assembly Language Mnemonics, symbolic names, and rules for their use for a specific computer type p For example: p n n n p Operation: MOV, ADD, INC, BR Register or Memory: R 2 or LOC Syntax: ADDI 5, R 3 Viable programming language(s) n n Very good control of the machine Albeit cumbersome! Introduction to Computer Organization and Architecture 69

Assembly Language No standard format p Assembly language is converted into machine instructions (1’s and 0’s) by a program called an Assembler p Assembler Directives provide other information to the assembler p n n n where to place instructions where to put data constant values Introduction to Computer Organization and Architecture 70

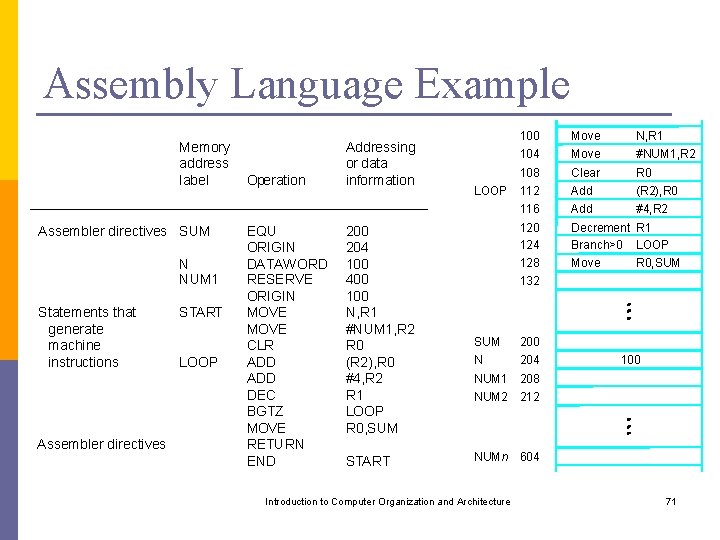
Assembly Language Example Memory address label Assembler directives SUM N NUM 1 Statements that generate machine instructions Assembler directives START LOOP Operation EQU ORIGIN DATAWORD RESERVE ORIGIN MOVE CLR ADD DEC BGTZ MOVE RETURN END Addressing or data information 200 204 100 400 100 N, R 1 #NUM 1, R 2 R 0 (R 2), R 0 #4, R 2 R 1 LOOP R 0, SUM START LOOP SUM N 100 104 Move N, R 1 #NUM 1, R 2 108 112 116 Clear Add R 0 (R 2), R 0 #4, R 2 120 124 128 132 Decrement R 1 Branch>0 LOOP Move R 0, SUM 200 204 100 NUM 1 208 NUM 2 212 NUMn Introduction to Computer Organization and Architecture 604 71

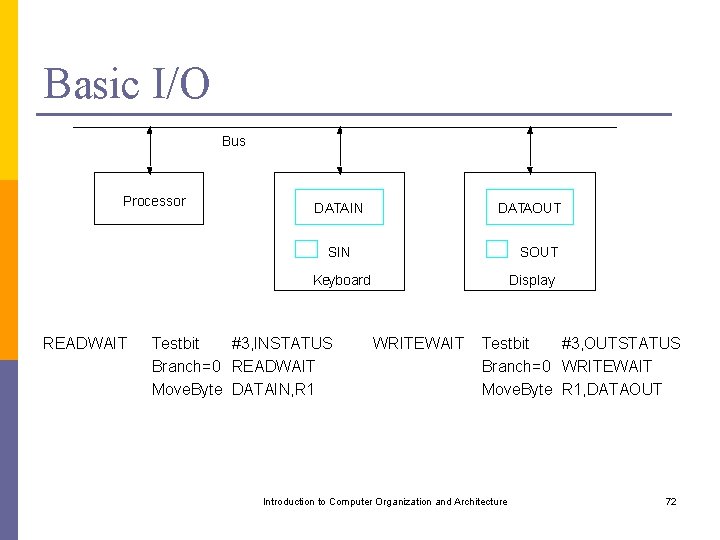
Basic I/O Bus Processor DATAIN DATAOUT SIN SOUT Keyboard READWAIT Testbit #3, INSTATUS Branch=0 READWAIT Move. Byte DATAIN, R 1 Display WRITEWAIT Testbit #3, OUTSTATUS Branch=0 WRITEWAIT Move. Byte R 1, DATAOUT Introduction to Computer Organization and Architecture 72

Queues / FIFOs p First In — First Out n Buffer data between two entities: Keyboard => Processor p Processor => Printer p Processor 1 => Processor 2 p n Scheduling as well: Printer queue p Queue of processes for multi-tasking p Event queue in Verilog. HDL p n Queues may use priority ranking Introduction to Computer Organization and Architecture 73

Queues / FIFOs p First In — First Out n The two basic functions are: APPEND an element on one end p REMOVE an element from the other p n n Frequently, one entity appends items to the queue and another removes it Two moving pointers are needed: IN: location for next APPEND p OUT: location for next REMOVE p n Wrap-around is needed Introduction to Computer Organization and Architecture 74

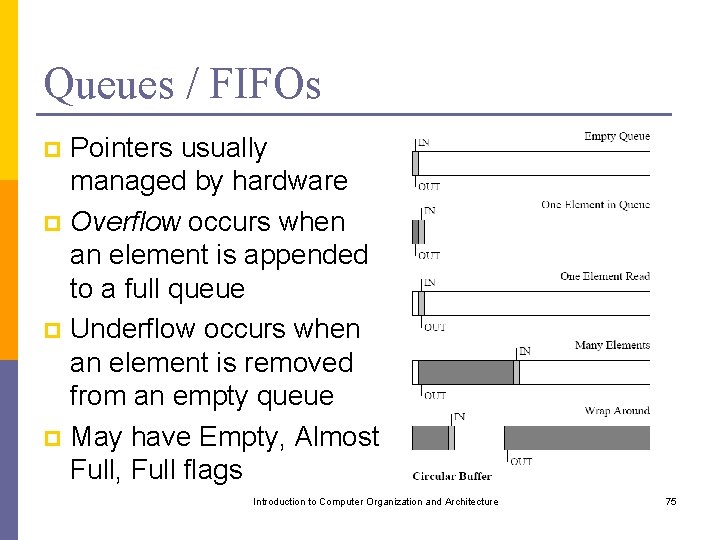
Queues / FIFOs Pointers usually managed by hardware p Overflow occurs when an element is appended to a full queue p Underflow occurs when an element is removed from an empty queue p May have Empty, Almost Full, Full flags p Introduction to Computer Organization and Architecture 75

Stacks/LIFOs p Last In — First Out n n Stacks are used to temporarily store items The two basic functions are: PUSH an element on the top p POP the top element from the stack p n n Frequently, the same entity that pushed the item on stack also pops it In contrast to the queue Only one pointer needed – it points to the top element p PUSH and POP in different directions p Wrap-around is not needed p Introduction to Computer Organization and Architecture 76

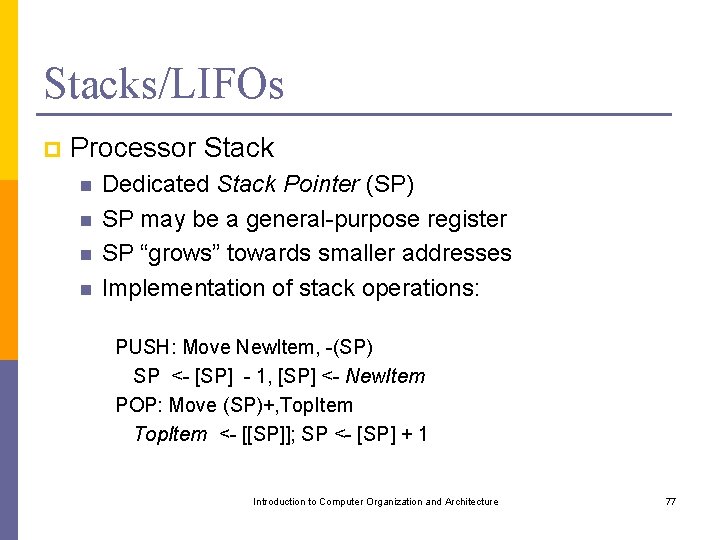
Stacks/LIFOs p Processor Stack n n Dedicated Stack Pointer (SP) SP may be a general-purpose register SP “grows” towards smaller addresses Implementation of stack operations: PUSH: Move New. Item, -(SP) SP <- [SP] - 1, [SP] <- New. Item POP: Move (SP)+, Top. Item <- [[SP]]; SP <- [SP] + 1 Introduction to Computer Organization and Architecture 77

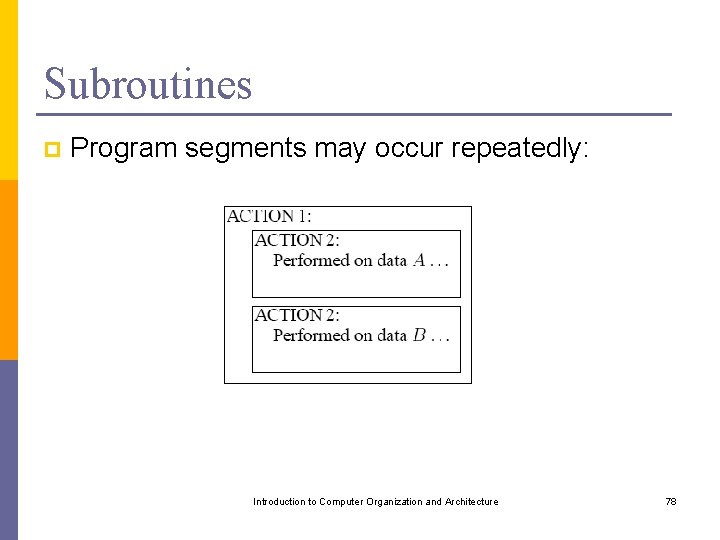
Subroutines p Program segments may occur repeatedly: Introduction to Computer Organization and Architecture 78

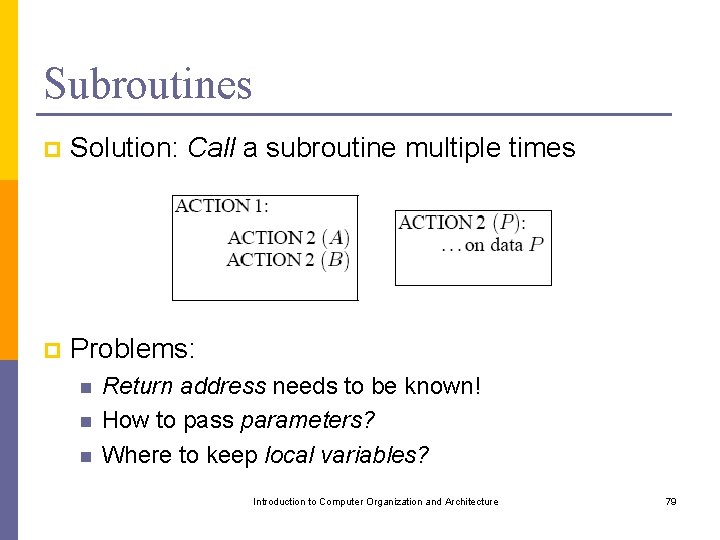
Subroutines p Solution: Call a subroutine multiple times p Problems: n n n Return address needs to be known! How to pass parameters? Where to keep local variables? Introduction to Computer Organization and Architecture 79
![Subroutine Calling p p Link register n Call SUB n Return LR PC Subroutine Calling p p Link register: n Call SUB n Return LR <- [PC]](https://slidetodoc.com/presentation_image/6952d6f672df6fcc070ff0a0c9e6d9fe/image-80.jpg)
Subroutine Calling p p Link register: n Call SUB n Return LR <- [PC] PC <- SUB PC <- [LR] Address on stack: n Call SUB n Return SP <- [SP] – 1 [SP] <- [PC] PC <- SUB PC <- [[SP]] SP <- [SP] + 1 Introduction to Computer Organization and Architecture 80

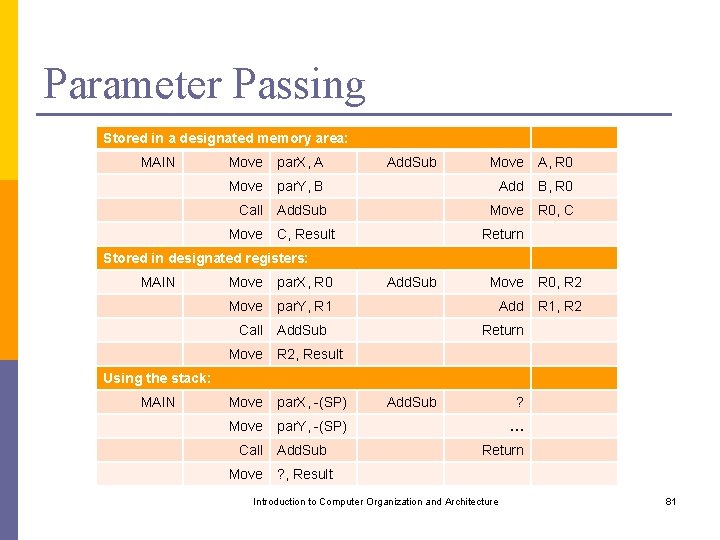
Parameter Passing Stored in a designated memory area: MAIN Move par. X, A Move Call Move Add. Sub Move A, R 0 par. Y, B Add B, R 0 Add. Sub Move R 0, C C, Result Return Stored in designated registers: MAIN Move par. X, R 0 Move par. Y, R 1 Call Add. Sub Move R 2, Result Move par. X, -(SP) Move par. Y, -(SP) Move R 0, R 2 Add R 1, R 2 Return Using the stack: MAIN Call Move Add. Sub ? … Return ? , Result Introduction to Computer Organization and Architecture 81

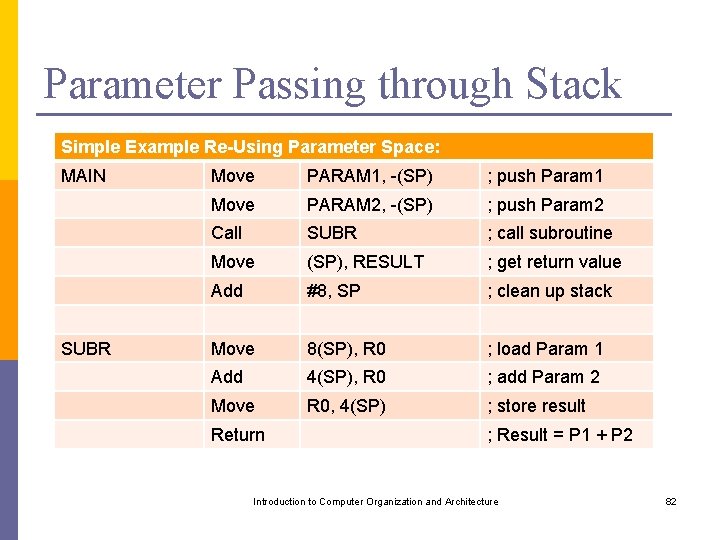
Parameter Passing through Stack Simple Example Re-Using Parameter Space: MAIN SUBR Move PARAM 1, -(SP) ; push Param 1 Move PARAM 2, -(SP) ; push Param 2 Call SUBR ; call subroutine Move (SP), RESULT ; get return value Add #8, SP ; clean up stack Move 8(SP), R 0 ; load Param 1 Add 4(SP), R 0 ; add Param 2 Move R 0, 4(SP) ; store result Return ; Result = P 1 + P 2 Introduction to Computer Organization and Architecture 82

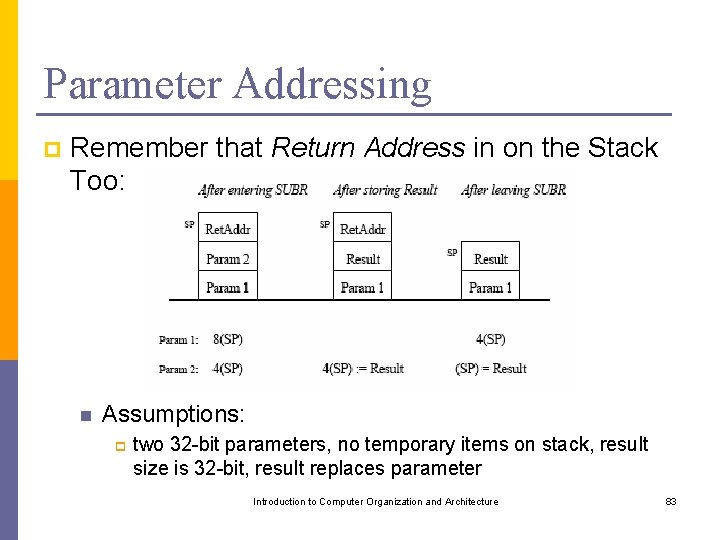
Parameter Addressing p Remember that Return Address in on the Stack Too: n Assumptions: p two 32 -bit parameters, no temporary items on stack, result size is 32 -bit, result replaces parameter Introduction to Computer Organization and Architecture 83

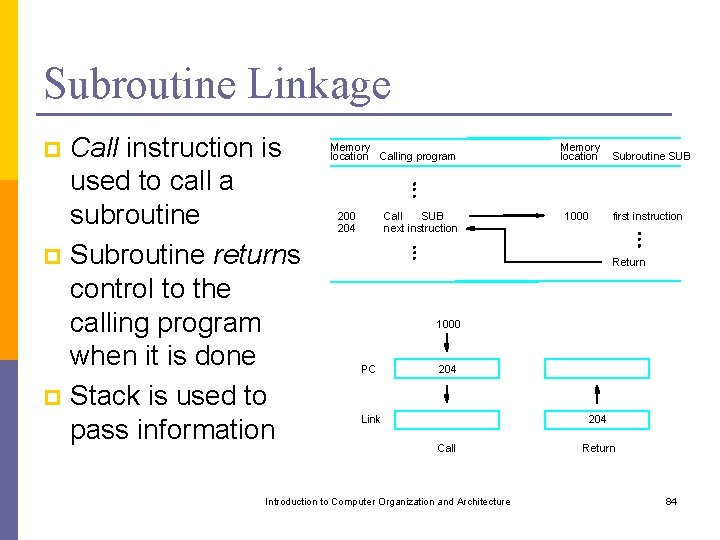
Subroutine Linkage Call instruction is used to call a subroutine p Subroutine returns control to the calling program when it is done p Stack is used to pass information p Memory location Calling program 200 204 Call SUB next instruction Memory location 1000 Subroutine SUB first instruction Return 1000 PC 204 Link 204 Call Introduction to Computer Organization and Architecture Return 84

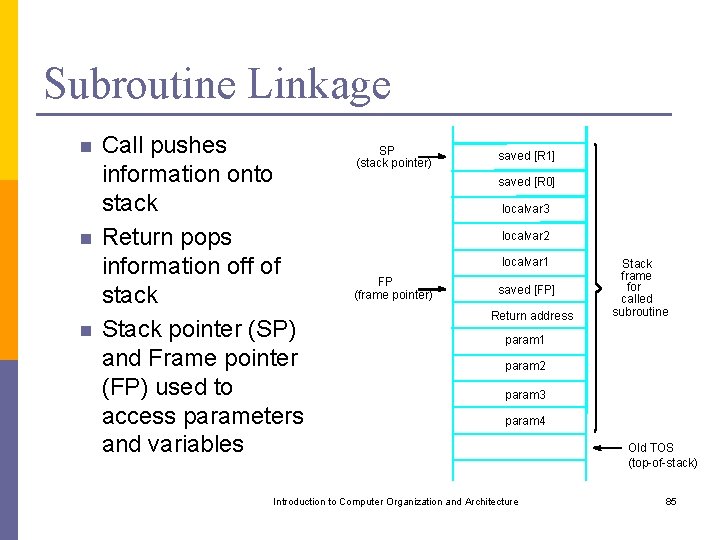
Subroutine Linkage n n n Call pushes information onto stack Return pops information off of stack Stack pointer (SP) and Frame pointer (FP) used to access parameters and variables SP (stack pointer) saved [R 1] saved [R 0] localvar 3 localvar 2 localvar 1 FP (frame pointer) saved [FP] Return address Stack frame for called subroutine param 1 param 2 param 3 param 4 Introduction to Computer Organization and Architecture Old TOS (top-of-stack) 85

The End Lecture 2