Identity Relationship Management The Next Evolution of Identity




























- Slides: 38

Identity Relationship Management The Next Evolution of Identity and Access Management for the Internet of Everything

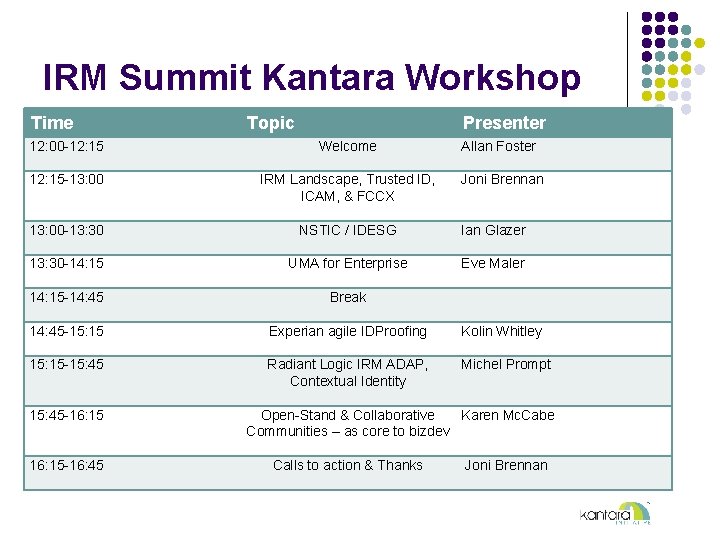
IRM Summit Kantara Workshop Time Topic Presenter 12: 00 -12: 15 Welcome Allan Foster 12: 15 -13: 00 IRM Landscape, Trusted ID, ICAM, & FCCX Joni Brennan 13: 00 -13: 30 NSTIC / IDESG Ian Glazer 13: 30 -14: 15 UMA for Enterprise Eve Maler 14: 15 -14: 45 Break 14: 45 -15: 15 Experian agile IDProofing Kolin Whitley 15: 15 -15: 45 Radiant Logic IRM ADAP, Contextual Identity Michel Prompt 15: 45 -16: 15 -16: 45 Open-Stand & Collaborative Karen Mc. Cabe Communities – as core to bizdev Calls to action & Thanks Joni Brennan

IRM Summit l l IRM Landscape Kantara Initiative Overview Trusted ID FICAM & FCCX

IRM Summit IRM Landscape

The IRM Story

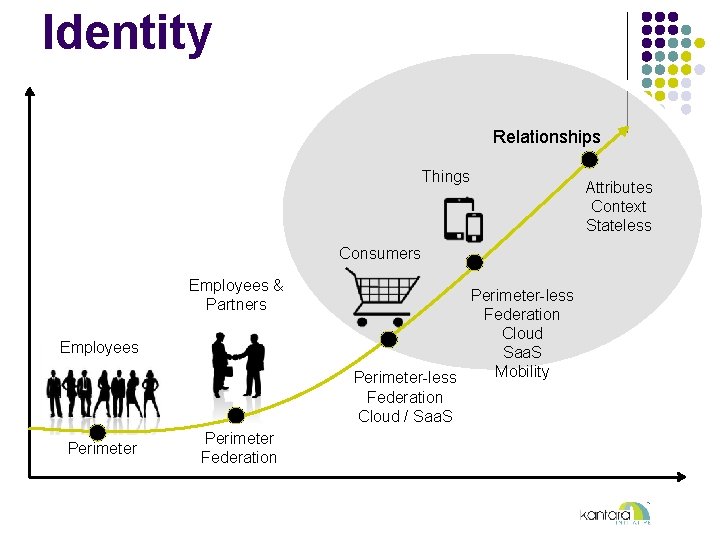
Identity Relationships Things Consumers Employees & Partners Employees Perimeter Federation Perimeter-less Federation Cloud Saa. S Mobility Perimeter-less Federation Cloud / Saa. S Attributes Context Stateless

Identity Relationship Management l l Model for managing a company’s interactions with current and future customers and “things” using Identity and Access Management (IAM). IRM rapidly and cost effectively unleashes new business opportunities that drive next generation consumer-facing services and top line revenue.

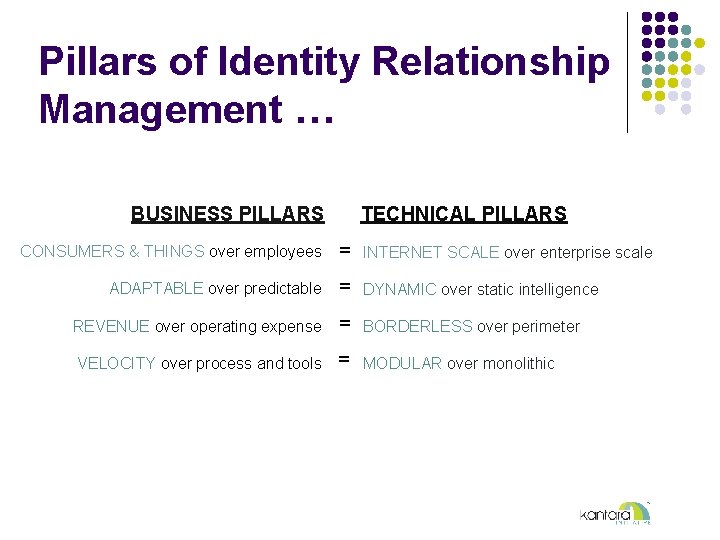
Pillars of Identity Relationship Management … BUSINESS PILLARS TECHNICAL PILLARS CONSUMERS & THINGS over employees = INTERNET SCALE over enterprise scale ADAPTABLE over predictable = DYNAMIC over static intelligence REVENUE over operating expense = BORDERLESS over perimeter VELOCITY over process and tools = MODULAR over monolithic

CONSUMERS & THINGS over employees only

INTERNET SCALE over enterprise scale

ADAPTABLE over predictable

DYNAMIC INTELLIGENCE over static intelligence

TOP LINE REVENUE over operating expense

BORDERLESS over perimeter

VELOCITY over process and tools

MODULAR over monolithic

The Next Generation of Identity & Access Management

What’s Next?

Tell us how you ‘do’ IRM! Join the community @

IRM Summit Kantara Initiative Overview

Who is Kantara 60+ Leading Organizations, 100’s of Participants, Industry and Governments: l Trust l Privacy l Security l Community Trustees At-Large: • Government of Canada • Trans-European Research Education Networking Association

What We Do The building blocks of Trusted Identity…

So that you can • • • INFLUENCE CONNECT LEARN PARTNER SHARE GROW

What we provide • • • RULES TOOLS EXPERTS

IRM Summit Trusted Identity

Trusted Identity l l l NSTIC – National Strategy for Trusted Identities in Cyberspace Trust is not the goal Identity is not the goal Trust and Identity are tools to enable business and public services growth Trustworthy Identities enable Trusted platforms where businesses connect and services grow.

Trusted Identity l Kantara Programs verify l Id. Ps and Assessors l l Reusable program applicable to l l l Policy, Technology, Privacy FICAM, FCCX, NSTIC, EU e. IDAS, IDAP, + Id. Ps, RPs, FOs Our part in the trust chain

IRM Summit For FICAM and FCCX

FICAM & FCCX l FICAM – Federal Identity Credential and Access Management (Policy) l l l Connects citizens to public services leveraging private sector Credential Service Providers Kantara Operates Certification Program – Trust Framework Provider FCCX – Federal Cloud Credential e. Xchange (Implementation) l l The technical identity hub that operates FICAM Kantara Operates Certification Program – Trust Framework Provider

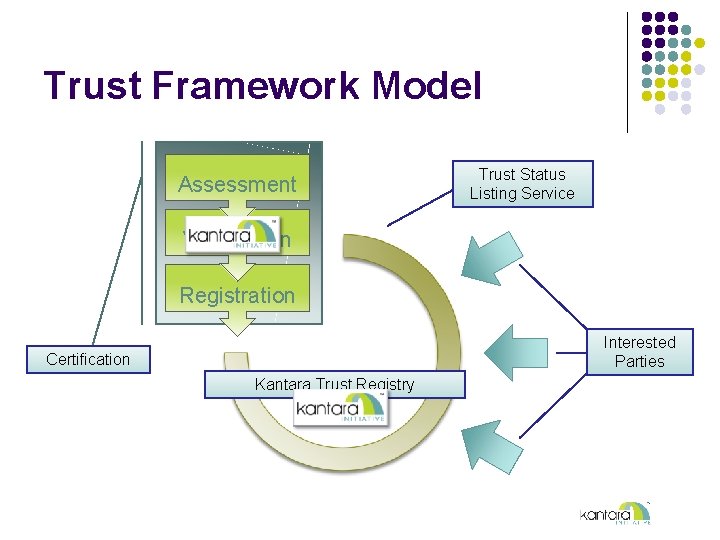
Trust Framework Model Assessment Trust Status Listing Service Verification Registration Interested Parties Certification Kantara Trust Registry

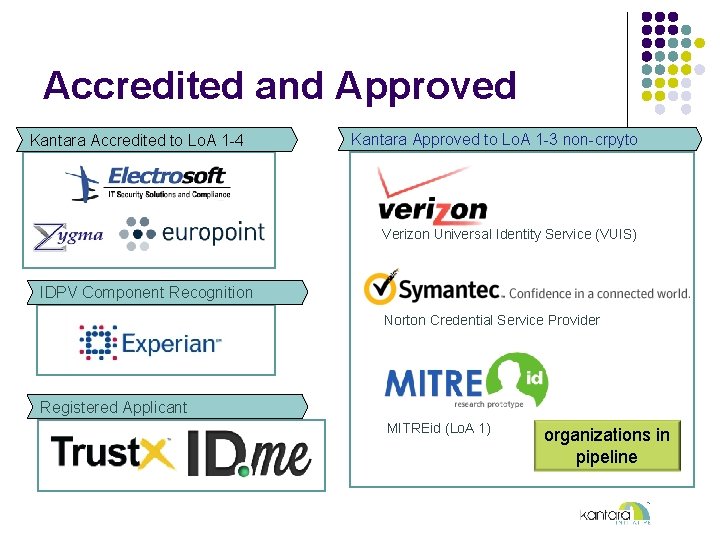
Accredited and Approved Kantara Accredited to Lo. A 1 -4 Kantara Approved to Lo. A 1 -3 non-crpyto Verizon Universal Identity Service (VUIS) IDPV Component Recognition Norton Credential Service Provider Registered Applicant MITREid (Lo. A 1) organizations in pipeline

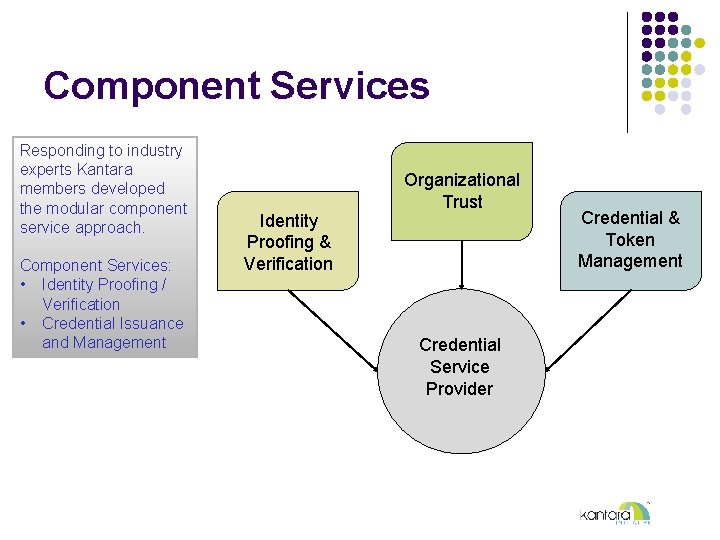
Component Services Responding to industry experts Kantara members developed the modular component service approach. Component Services: • Identity Proofing / Verification • Credential Issuance and Management Identity Proofing & Verification Organizational Trust Credential Service Provider Credential & Token Management

MODULAR Assurance

CONTEXTUAL Assurance

ADAPTABLE Assurance

BORDERLESS Assurance

Thanks! JOIN INNOVATE TRUST Questions? • Kantara Executive Director: Joni Brennan joni@kantarainitiative. org • General Inquiries: support@kantarainitiative. org

Shaping the Future of Digital Identity l l l @kantaranews kantarainitiative. org/listinfo/community bit. ly/Kantara_Assurance kantarainitiative. org/membership/
 X.next = x.next.next
X.next = x.next.next Relationship management vs relationship marketing
Relationship management vs relationship marketing Identity relationship management
Identity relationship management Functional components of e-crm
Functional components of e-crm Personal identity identity map
Personal identity identity map Hình ảnh bộ gõ cơ thể búng tay
Hình ảnh bộ gõ cơ thể búng tay Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Chó sói
Chó sói Glasgow thang điểm
Glasgow thang điểm Hát lên người ơi
Hát lên người ơi Môn thể thao bắt đầu bằng từ đua
Môn thể thao bắt đầu bằng từ đua Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Công thức tính độ biến thiên đông lượng
Công thức tính độ biến thiên đông lượng Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Mật thư anh em như thể tay chân
Mật thư anh em như thể tay chân 101012 bằng
101012 bằng độ dài liên kết
độ dài liên kết Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Thơ thất ngôn tứ tuyệt đường luật
Thơ thất ngôn tứ tuyệt đường luật Quá trình desamine hóa có thể tạo ra
Quá trình desamine hóa có thể tạo ra Một số thể thơ truyền thống
Một số thể thơ truyền thống Cái miệng xinh xinh thế chỉ nói điều hay thôi
Cái miệng xinh xinh thế chỉ nói điều hay thôi Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Thế nào là sự mỏi cơ
Thế nào là sự mỏi cơ đặc điểm cơ thể của người tối cổ
đặc điểm cơ thể của người tối cổ Giọng cùng tên là
Giọng cùng tên là Vẽ hình chiếu đứng bằng cạnh của vật thể
Vẽ hình chiếu đứng bằng cạnh của vật thể Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Thẻ vin
Thẻ vin đại từ thay thế
đại từ thay thế điện thế nghỉ
điện thế nghỉ Tư thế ngồi viết
Tư thế ngồi viết Diễn thế sinh thái là
Diễn thế sinh thái là Dạng đột biến một nhiễm là
Dạng đột biến một nhiễm là Số nguyên tố là số gì
Số nguyên tố là số gì Tư thế ngồi viết
Tư thế ngồi viết