GCSE ICT Input and Output Devices Inputs Presented

























































































- Slides: 121

GCSE ICT Input and Output Devices – Inputs Presented By Professor Ken Regis

Input devices • Input devices are used to get data into a system. • They should be able to do this as accurately and quickly as possible, and with the minimum of human intervention.

Input devices • The most common types of input devices are: – Keyboards – Point and Click devices (including mouse, tracker balls, touch sensitive pads, joysticks, light pens, touch screens, and graphic tablets)

Input devices • The most common types of input devices are: – Readers (including magnetic strip readers, barcode readers, optical character readers/recognition, magnetic ink character readers/recognition, and optical mark readers/recognition) – Punched cards and tape (including punched cards and Kimball tags)

Input devices • The most common types of input devices are: – Sound capture devices (including voice recognition and microphones) – Terminals (including EPOS and EFTPOS terminals)

Input devices • The most common types of input devices are: – Digital imaging devices (including video digitisers, scanners, digital cameras, and web cams) – Tonal devices (including touch tone telephones)

Keyboards • The most common type of keyboard is the QWERTY keyboard (so called because the top line of letters are q, w, e, r, t, and y.

Keyboards • Another type of keyboard is the concept keyboard. • The can be specially designed so that people with restricted vision can use them to interface with a computer. • Concept keyboards can also be programmed to perform common functions with one keystroke (e. g. a computerised till in a fast food restaurant).

Keyboard • Common input device • Standardised layout (QWERTY) (although non-alphanumeric keys are placed differently, and there is a difference between key assignments on UK and USA keyboards) QWERTY arrangement not optimal for typing - layout due to typewriters. Other keyboard designs allow faster typing but large social base of QWERTY typists produces reluctance to change. • Keypress closes connection, causing a character code to be sent • Usually connected by an umbilical cord • Allows rapid entry of text by experienced users

Keyboards cont

Other Keyboards Alphabetic Keys arranged in alphabetic order • not faster for trained typists • not faster for beginners either

Dvorak • common letters under dominant fingers • biased towards right hand • common combinations of letters alternate between hands • 10 -15% improvement in speed and reduction in fatigue • But - large social base of QWERTY typists produce market pressures not to change

Chord keyboards • only a few keys - four or 5 • letters typed as combination of key presses • compact size - ideal for portable applications • short learning time – key preses reflect shape of desired letter • fast • But - social resistance, plus fatigue after extended use

Point and Click devices • Point and Click devices include mouse, tracker balls, touch sensitive pads, joysticks, light pens, touch screens, and graphic tablets.

TRACKERBALL • A trackball is a pointing device consisting of a ball held by a socket containing sensors to detect a rotation of the ball about two axes—like an upside-down mouse with an exposed protruding ball. The user rolls the ball with the thumb, fingers, or the palm of the hand to move a cursor. Large tracker balls are common on CAD workstations for easy precision.

Trackball Bit like an upside-down mouse. Ball is rotated inside static housing, relative motion moves cursor. Indirect device, fairly accurate. Requires buttons for picking. Size and “feel” of trackball itself important. Requires little space, becoming popular for portable and notebook computers.

Tracker ball • The tracker ball is essentially an upside down mouse. • Instead of moving the mouse on the table top, the ball is rotated. • This achieves the same result as using a mouse but takes up far less room.

Mouse • The mouse translates movement on the desktop into digital information. • This is information is converted into movement of the cursor on the screen. • A mouse will also have one, two, or three buttons which can be clicked to help the user to select what functions they wish to use.

Mouse cont Mouse located on desktop • requires physical space • no arm fatigue Relative movement only is detectable. Movement of mouse moves screen cursor Screen cursor oriented in (x, y) plane, mouse movement in (x, z) plane: an indirect manipulation device. Device itself doesn’t obscure screen, is accurate and fast. Can lead to hand-eye coordination problems due to indirectness of manipulation.

How does it work? Two methods for detecting motion Mechanical Ball on underside of mouse turns as mouse is moved Rotates orthogonal potentiometers Can be used on almost any flat surface

Optical Mouse light emitting diode on underside of mouse sits on special grid-like pad on desk; less susceptible to dust and dirt detects fluctuating alterations in reflected intensity as mouse is moved over the gridlines, used to calculate relative motion in (x, z) plane Also a device known as the foot mouse - operated with the feet; a rare device, not in common use

Touch sensitive pad • These are most commonly found on laptop computers. • A stylus or the user’s finger is pressed gently onto the pad, and as it is moved the cursor moves on the screen.

Joystick • These are most commonly used to interact with computer games, although they are also used in other circumstances (e. g. on hospital scanners). • Like the tracker ball, the movement of the joystick moves the cursor on the screen,

Joystick Indirect device Takes up very little space Controlled by either • movement (absolute joystick) - position of cursor • pressure (isometric or velocity-controlled stick corresponds to velocity of cursor joystick corresponds to joystick) - pressure on Usually provided with buttons (either on top or on front like a trigger) for selection Does not obscure screen Inexpensive (often used for computer games, also because they are more familiar to users)

Light pen • Light pens are usually used with specialist design software. • The light pen works by being touched against the screen. • As the pen is moved on the screen, the cursor moves.

Light pen Coiled cable connects pen to c. r. t. In operation, pen held to screen and detects burst of light from screen phosphor during display scan. Direct pointing device: accurate (can address individual pixels), so can be used for fine selection and drawing. Problems: pen can obscure display, is fragile, can be lost on a busy desk, tiring on the arm. Both much less popular than the mouse

Touch screen • The touch screen is a special type of screen which is sensitive to touch. • Selections can be made by touching the screen. • These are particularly useful in banks, building societies, and shops, where customers who are not used to using a keyboard can interact with a computer system.

Touch screen

Touch-sensitive screen (touch screens) Detect the presence of finger or stylus on the screen. Work by interrupting matrix of light beams or by capacitance changes or ultrasonic reflections. Direct pointing devices. Advantages: Fast, and require no specialized pointer. Good for menu selection. Suitable for use in hostile environment: clean and safe from damage. Disadvantages: Finger can mark screen. Imprecise (finger is a fairly blunt instrument!) - difficult to select small regions or perform accurate drawing. Lifting arm can be tiring, and can make screen too close for easy viewing.

Graphics tablet • A graphics tablet allows the user to create designs directly onto the screen. • A special stylus is connected to the computer via the graphics tablet, and as the user ‘draws’ on the tablet with the stylus the drawing appears on screen.

Handwriting recognition Handwritten text can be input into the computer, using a pen and a digesting tablet • common form of interaction Problems in • capturing all useful information - stroke path, pressure, etc. in a natural manner • segmenting joined up writing into individual letters • interpreting individual letters • coping with different styles of handwriting Handheld organizers being released now that incorporate handwriting recognition technology and do away with a bulky keyboard

Handwriting recognition

Readers • The most common types of reader used include magnetic strip readers, barcode readers, optical character readers/recognition, magnetic ink character readers/recognition, and optical mark readers/recognition).

Magnetic strip readers • The most common magnetic tape readers are those used at electronic points of sale (EPOS). • These ‘read’ the personal data stored on the magnetic strip of a credit or debit card.

Barcode readers • Barcodes are used in shops, libraries, luggage handling, and stock control. • The lines on a barcode represent numbers, and can be scanned very quickly using a laser scanner.

Optical character readers/recognition • Optical character recognition is a method of inputting text using a scanner. • It requires special software to convert the scanned image of each letter into an ASCII (American Standard Code for Information Interchange) code, and it often confuses similar shaped letters and numbers (e. g. S and 5, B and 8).

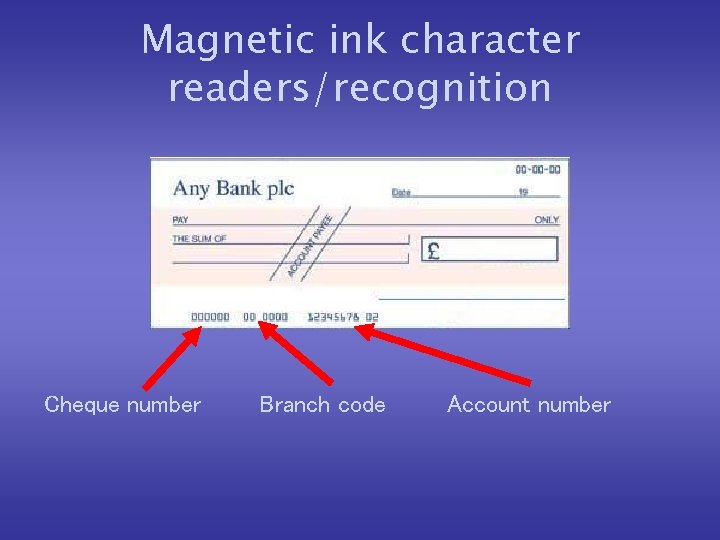
Magnetic ink character readers/recognition • Magnetic ink characters are printed at the bottom of cheques. • They are used by banks to identify the bank a customer banks with, the individual branch where their account is held, and the customer’s bank account number.

Magnetic ink character readers/recognition Cheque number Branch code Account number

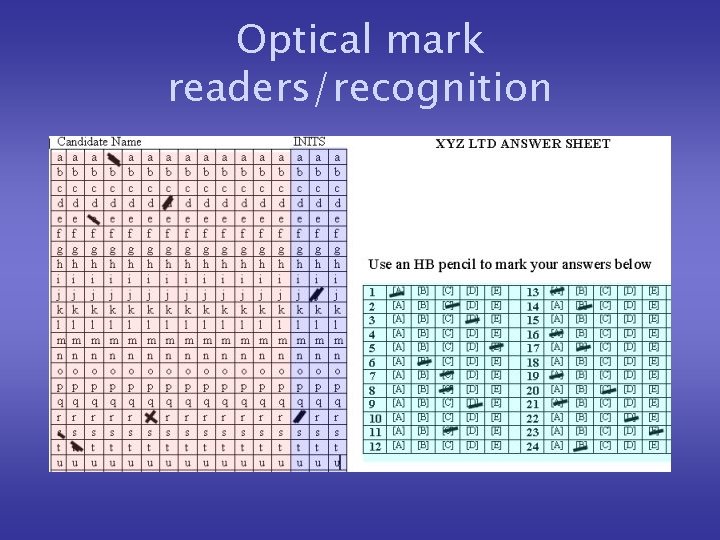
Optical mark readers/recognition • Optical mark recognition sense marks made on specially designed forms (e. g. multiple choice answer sheets, lottery cards). • OMR is a very cheap, easy and quick to handle system of inputting data, but if a user makes a mistake they are difficult to correct.

Optical mark readers/recognition

Punched cards and tape • Punched cards and tape were used by the first computers to store programs and data. • They are seldom used today except for clock cards, which records when a person starts and ends work, and Kimball tags, which are used for stock control.

Sound capture devices • The most common use of sound capture devices involves the use of voice recognition software and microphones.

Sound capture devices • Voice recognition software ‘remembers’ the way a user speaks, and converts their speech into text that appears on screen. • Although voice recognition software has become increasingly sophisticated, many such programs have difficulty converting more than 90% of common words accurately.

Terminals • EPOS (Electronic Point Of Sale) and EFTPOS (Electronic Fund Transfer at Point Of Sale) terminals are connected, via secure Internet connections, to the computers of the main banks and credit card companies.

Terminals • EPOS and EFTPOS allow a retailer to transfer the cost of what they have sold to a customer from the customer’s credit card or bank account to their own bank account. • This is much faster than accepting payment by cheque, and more secure than accepting payment in cash.

Terminals • It also gives the retailer an opportunity to collect information about their customers, and to develop individual customer profiles (i. e. know what an individual customer may want to buy). • This helps to retailer to ‘target’ individual customers with special offers etc.

EPOS & EFTPOS

Digital imaging devices • These include video digitisers, scanners, digital cameras, and web cams.

Video Digitisers • The video digitiser is a combination of hardware and dedicated software that converts an analogue signal into a digital signal. • This is the basis of most set top boxes that give access to digital television on standard television sets. • It can also be used to ‘capture’ still images from video.

Scanners • Scanners are used to scan text or images so that they can be stored on and manipulated by computer. • The scanner converts the text or image into a digital signal which it sends to the computer. • The user can then decide whether they want to store or manipulate what they have scanned.

TYPES OF SCANNERS • • DRUM SCANNER FLATBED SCANNER HANDHELD SCANNER SHEET FED SCANNER PHOTO SCANNER SINGLE SHEET SCANNER SLIDE SCANNER

DRUM SCANNER • A drum scanner provides high-quality scans. They are also very large. They are more on the expensive and most advanced. This scanner works with • a rotating drum that scans the object with an intricate array of sensors.

FLATBED SCANNER • This is smaller scanner that will fit on top of a desk. The document to be scanned is placed on top of a sheet of glass inside the scanner and then the lid is shut. A small scanning sensor, like a digital camera, moves back and forth inside the scanner, taking pictures of the document and compiling them into a large picture of the entire document that appears on the computer screen. Flatbed scanners produce medium quality images.

HANDHELD SCANNER • The Hand Scanner is for manual scanning. Hand Scanners look similar to mice. You must move them back and forth across the document to scan a document that is more then a couple inches in length. Hand Scanners aren’t used much, except for scanning barcodes at stores.

SHEET FED SCANNER • This scanner is designed to scan several documents at once. A stack of papers can be placed in the scanner and the scanner will scan them all one at a time in order. Some sheet-fed scanners can scan both sides of a document at once. Sheet-fed Scanners work the same way Single Sheet Scanners do, but Sheet-fed Scanners usually produce slightly better quality images.

PHOTO SCANNER • Although you can scan photos on other types of scanners, the Photo Scanner is made just for photographs. Most Photo Scanners can scan images up to 4 x 6 inches in size. Photo Scanners are great for converting film photographs into digital pictures. Some Photo Scanners are like small Flatbed Scanners. Others come built into computers like a disk drive. Both types of Photo Scanners work the same way the Flatbed Scanner does, producing medium quality images.

PHOTO SCANNERS

SINGLE SHEET SCANNER • This type of scanner only works for single sheets of paper. This scanner looks just like a printer. Like paper feeding into a printer, the document is fed into the scanner, and a little digital camera inside the scanners moves back and forth, taking pictures of parts of the document, one line at a time, and then compiling them into a large picture of the entire document that appears on the computer screen. Single Sheet Scanners produce low quality images.

SINGLE SHEET SCANNER

SLIDE SCANNER • This scanner is specially designed for scanning slides (those little pieces of film). Flatbed Scanners can slides, but Slide Scanners are better at scanning slides. Some slide scanners can convert negative slides to positive when scanning. The good thing about Slide Scanners is that they produce very high quality images. The bad thing is that they can only scan slides.

SLIDE SCANNER

BAR CODE TECHNOLOGY • It is an automatic identification technology • Bar code is a predefined format of dark bars and white spaces • Structured to contain a specific piece of information • It allows real-time data to be collected accurately and rapidly • Combination of barcode technology with computer and application software improves performance, productivity and profitability

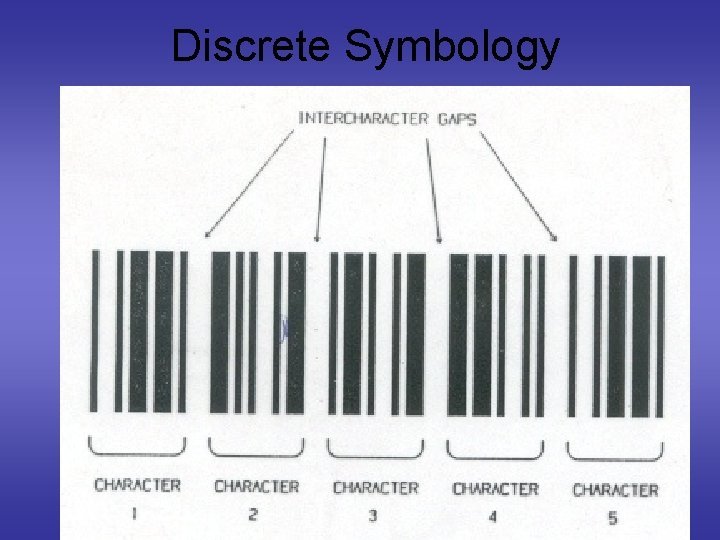
Discrete Symbology

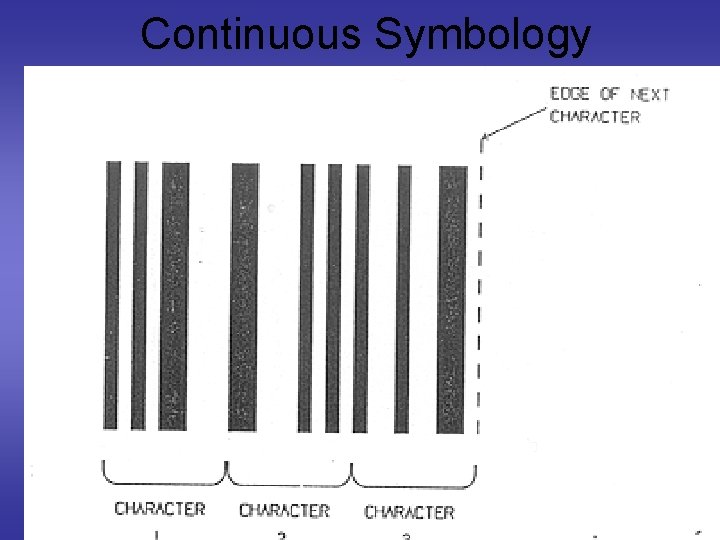
Continuous Symbology

DATA ENTRY TECHNIQUES • MANUAL METHODS – KEYBOARD OPERATION – 1 ERROR/300 CHARACTERS • AUTOMATIC METHODS – OPTICAL CHARACTER RECOGNITION – MAGNETIC INK – MACHINE VISION – RADIO FREQUENCY IDENTIFICATION – SMART CARDS – BAR CODE

BENEFITS OF BAR CODING • REPRESENT UNIQUE IDENTITY OF A PRODUCT • ACCURACY OF DATA INPUT (ERROR FREE) • AID EFFECTIVE MANAGEMENT OF RESOURCES AND INVENTORIES • LABOUR SAVINGS BY AVOIDING MANUAL SYSTEM

BENEFITS … • COST EFFICIENT • REAL TIME DATA COLLECTION • MEASUREMENT OF WORK IN PROGRESS THROUGHOUT THE FACTORY • RAPID ACCESS TO TOTAL PRODUCTION COSTS • MORE ACCURATE DESPATCH

BAR CODE TERMINOLOGY o BAR - The darker, non reflective element of a Bar Code o BI-DIRECTIONAL SYMBOL - A Bar Code symbol format which permits reading in either direction across the bars and spaces o CHECK DIGIT - A calculated character included within the Bar Code for error detection o FIXED BEAM SCANNER - A stationary Bar Code Scanner. The symbol must be moved through the light beam to be read

TERMINOLOGY … • HAND-HELD SCANNER – A scanner held and operated by a human operator • INTER-CHARACTER GAP – The space between the bars or spaces • MOVING BEAM SCANNER – A Bar Code scanner that uses a moving light beam to dynamically scan and decode a Bar

TERMINOLOGY … • SPACE – The lighter, reflective element of a Bar Code • START CHARACTER – A special pattern of bars and spaces used to identify the beginning of a Bar Code symbol • STOP CHARACTER – A special pattern of bars and spaces used to identify the end of a Bar Code symbol

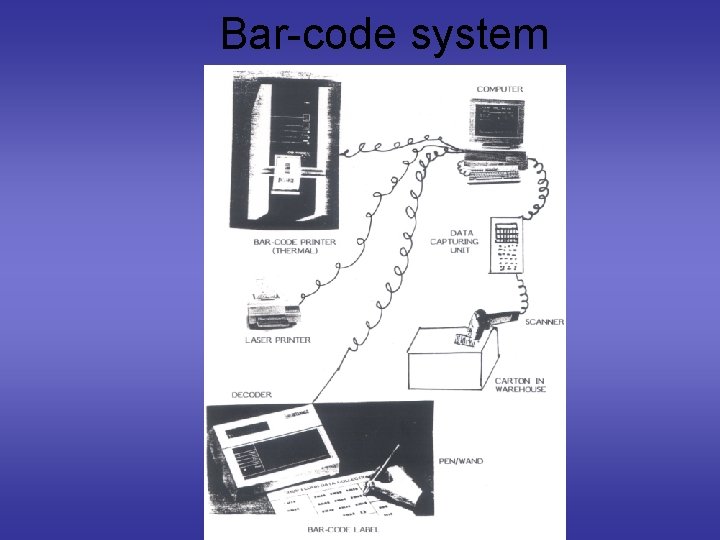
Bar-code system

Thermal Transfer Printer

BAR CODE SCANNERS • A device used to extract information optically from a Bar Code • Bar Code symbol consists of series of vertical dark bars separated by light spaces • When illuminated reflected light is detected by electro optical sensor • The intensity of reflected light from the

SCANNERS … • Reflected light is converted into electrical voltage signals • Analog voltages are digitized into raw data • The decoder converts this data into the character data representation of the

TYPES OF SCANNERS (READERS) • CONTACT READERS – Must touch or come in close proximity of symbol – Good where the label cannot be placed in an easy-to-view position – Normally hand-held/stationary units – Common type is pen/wand reader – A high-density resolution wand used to read a low-density symbol might see an ink spot as bar or an ink void as a space

CONTACT READERS … • A low-resolution wand may not be able to recognise a narrow bar of highdensity symbol • Positioned angle of wand to the surface and movement speed across the symbol are key parameters

Contact Readers

NON-CONTACT READERS • Reader need not come in contact with symbol • Scan distance may be from 6” to several feet depending upon symbol size and scanner design • Hand-held, fixed beam readers

Table mounted fixed beam reader

Table mounted fixed beam reader

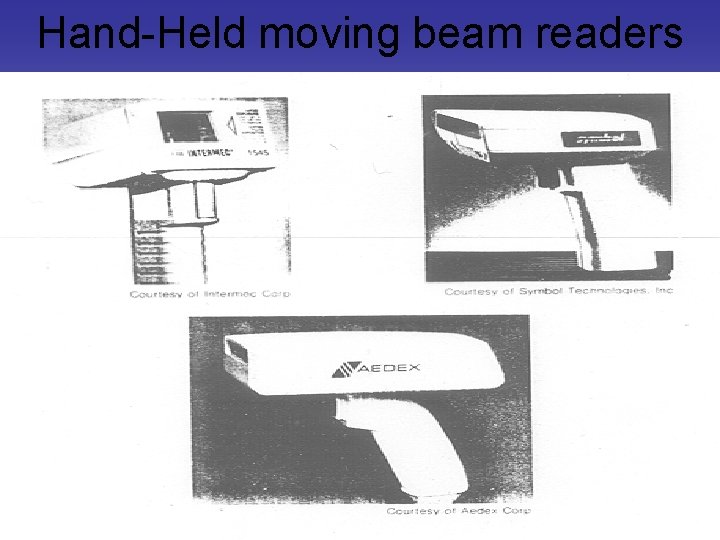
Hand-Held moving beam readers

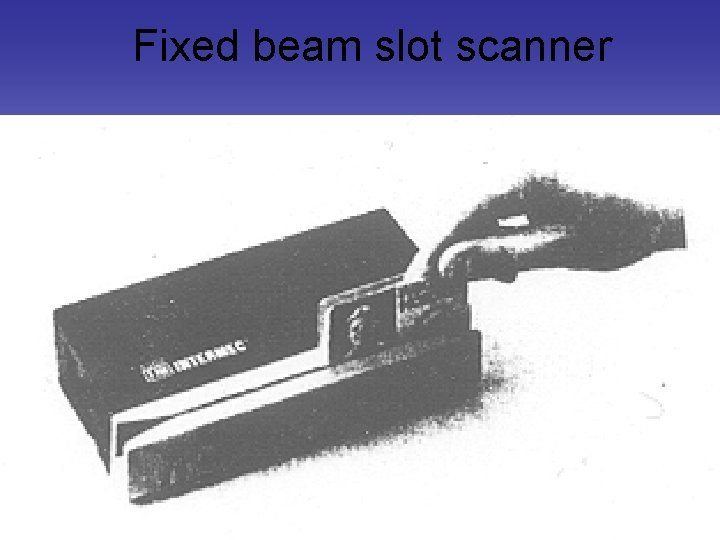
Fixed beam slot scanner

CCD Scanner

Portable Data Collection Equipment

BAR CODE APPLICATIONS • INVENTORY CONTROL – Portable readers • WORK-IN PROCESS TRACKING (WIP) COMPANY INVENTORY – Raw materials – WIP (Components, Assemblies, Semi finished Products) – Finished Products

APPLICATIONS … • SHIPPING • ELECTRONIC DATA INTERCHANGE (EDI) – Direct communication between computers of two companies (Manufacturer & Vendor) – Industry-wide EDI standards – Reduces cost and saves time of business transaction

APPLICATIONS … • RETAIL APPLICATIONS – Super markets – Counter-mounted Bar Code scanners – Universal Product Code (UPC) – Price and description information • WARE HOUSING • HEALTH CARE APPLICATIONS – Drugs, devices, instruments – Identification of expiry date – Blood banking • Blood group • Expiry date • Donor traceability

APPLICATIONS …

BAR CODING IN LIBRARIES • EFFECTIVE LIBRARY NEEDS EACH DOCUMENT BAR CODED • TWO LABELS PREFERABLY • LABEL TO CONTAIN – Accession number equivalent Bar Code – Call number – Institution logo advantageous • ISBN BAR CODE COULD BE USED

BARCODING IN LIBRARIES … • DATABASE PROGRAM LINKS THE BAR CODE TO BIBLIOGRAPHIC DETAILS OF DOCUMENTS • AUTHORISED ID CARD INCLUDES BAR CODE – Card could be used by library – Institutional ID card – Social security number • BAR CODE READER INTERFACED TO COMPUTER • TRACKING OF BOOKS

INCORPORATING BAR CODE IN LIBRARIES • THE TYPICAL SEQUENCE WOULD BE – Database creation (OPAC) – Generate Bar Code for all transact able documents – Bar Code membership cards – Installation of suitable scanning equipment – Set different criteria for transactions

ADVANTAGES OF BAR CODE IN LIBRARIES n. Quick and error free entry of access and membership codes n. Ensures total integrity of collected data n. No queuing up at check out/check in counters n. Avoids piling up of data entry work for counter staff n. Aids generation of suitable reminders to delinquent borrowers n. Stock verification made easy

Digital cameras • Digital cameras convert the analogue image seen through the camera’s lense into a digital signal that can be stored. • Each picture is split up into millions of tiny squares (or pixels), each of which is a different colour. • Each pixel is stored as a ‘bit’ of digital information.

Web cams • Web cameras (web cams for short) are small digital cameras which are attached to computers so that still and motion digital images can be ‘captured’ and used. • They are often used in conjunction with the Internet so that people can videoconference.

Tonal devices • Touch tone telephones are the most common tonal device used to input data. • Customers can use them to interact with computerised telephone systems so that they can respond to choices given to them by recorded messages.

Speech Recognition Promising, but only successful in limited situations - single user, limited vocabulary systems Problems with • external noise interfering • imprecision of pronunciation

Indirect device. Resistive tablet detects point contact between 2 separated sheets: has advantages in that it can be operated without specialized stylus - a pen or the user’s finger is fine. Magnetic tablet detects current pulses in magnetic field using small loop coil housed in special pen. Also capacitive and electrostatic tablets. Sonic tablet similar to above but requires no special surface: ultrasonic pulse emitted by pen detected by two or more microphones which then triangulate the pen position. Can be adapted to provide 3 -d input. High resolution, available in a range of sizes from A 5 to 60 x 60 in. Sampling rate between 50 and 200 Hz. Can be used to detect relative motion or absolute motion. Can also be used for text input (if supported by character recognition software). Require large amount of desk space, and may be awkward to use if displaced by the keyboard.

Data. Glove Lycra glove with optical fibre sensors. Detects joint angles and 3 -d hand position. Solution in search of a problem - the technology to utilize the power of this form of input properly does not exist yet. Advantages: easy to use, potentially powerful and expressive (10 joint angles + 3 -d. spatial information, at 50 Hz. ). Disadvantages: difficult to use with a keyboard, expensive (~£ 10 k/glove). Potential: vast - gesture recognition, sign language interpretation, etc. Eye gaze Headset detects user’s eye movements to control cursor. Very fast and accurate, also expensive.

Data Glove

Plastic Cards • Visual identity application – Plain plastic card is enough • Magnetic strip (e. g. credit cards) – Visual data also available in machine readable form – No security of data • Electronic memory cards – Machine readable data – Some security (vendor specific)

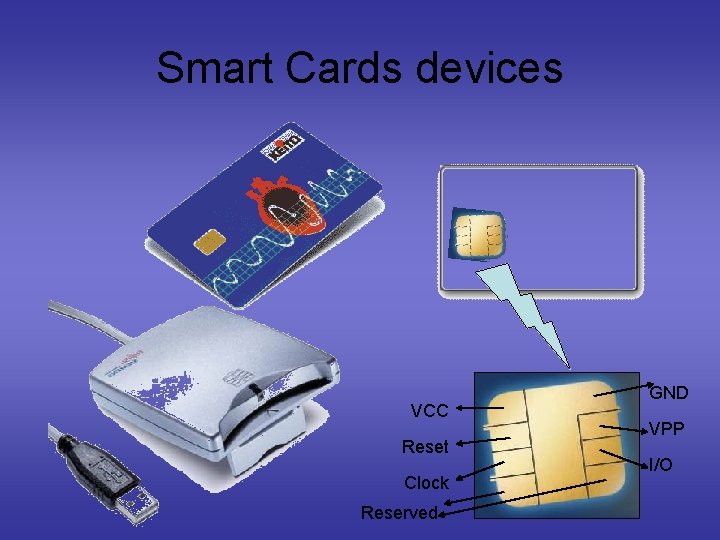
Smart Cards • Processor cards (and therefore memory too) • Credit card size – With or without contacts. • Cards have an operating system too. • The OS provides – A standard way of interchanging information – An interpretation of the commands and data. • Cards must interface to a computer or terminal through a standard card reader.

Smart Cards devices VCC Reset Clock Reserved GND VPP I/O

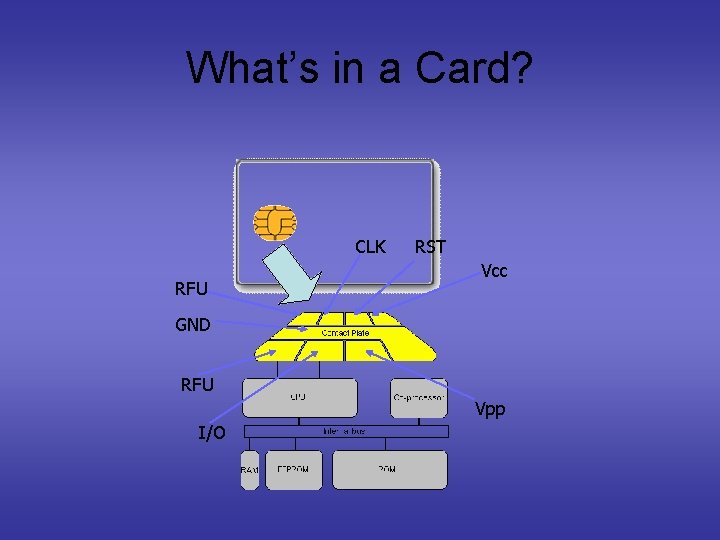
What’s in a Card? CLK RFU RST Vcc GND RFU Vpp I/O

Typical Configurations • • 256 bytes to 4 KB RAM. 8 KB to 32 KB ROM. 1 KB to 32 KB EEPROM. Crypto-coprocessors (implementing 3 DES, RSA etc. , in hardware) are optional. • 8 -bit to 16 -bit CPU. 8051 based designs are common. The price of a mid-level chip when produced in bulk is less than US$1.

Smart Card Readers ¢ • Dedicated terminals Usually with a small screen, keypad, printer, often also have biometric devices such as thumb print scanner. Computer based readers Connect through USB or COM (Serial) ports

Terminal/PC Card Interaction • The terminal/PC sends commands to the card (through the serial line). • The card executes the command sends back the reply. • The terminal/PC cannot directly access memory of the card – data in the card is protected from unauthorized access. This is what makes the card smart.

Communication mechanisms • Communication between smart card and reader is standardized – ISO 7816 standard • Commands are initiated by the terminal – Interpreted by the card OS – Card state is updated – Response is given by the card. • Commands have the following structure CLAfrom. INS P 1 include P 21. . Le. Lc • Response the card bytes 1. . Lc followed. Le by Response Code

Security Mechanisms • Password – Card holder’s protection • Cryptographic challenge Response – Entity authentication • Biometric information – Person’s identification • A combination of one or more

Password Verification • Terminal asks the user to provide a password. • Password is sent to Card for verification. • Scheme can be used to permit user authentication. – Not a person identification scheme

Cryptographic verification • Terminal verify card (INTERNAL AUTH) – Terminal sends a random number to card to be hashed or encrypted using a key. – Card provides the hash or cyphertext. • Terminal can know that the card is authentic. • Card needs to verify (EXTERNAL AUTH) – Terminal asks for a challenge and sends the response to card to verify – Card thus know that terminal is authentic. • Primarily for the “Entity Authentication”

Biometric techniques • Finger print identification. – Features of finger prints can be kept on the card (even verified on the card) • Photograph/IRIS pattern etc. – Such information is to be verified by a person. The information can be stored in the card securely.

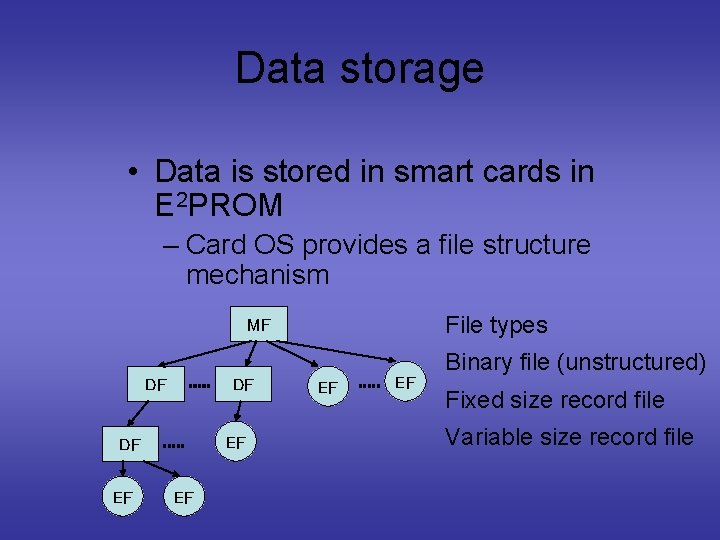
Data storage • Data is stored in smart cards in E 2 PROM – Card OS provides a file structure mechanism File types MF DF DF EF EF Binary file (unstructured) Fixed size record file Variable size record file

File Naming and Selection • Each files has a 2 byte file ID and an optional 5 -bit SFID (both unique within a DF). DFs may optionally have (globally unique) 16 byte name. • OS keeps tack of a current DF and a current EF. • Current DF or EF can be changed using SELECT FILE command. Target file specified as either: – – – DF name File ID SFID Relative or absolute path (sequence of File IDs). Parent DF

Basic File Related Commands • Commands for file creation, deletion etc. , File size and security attributes specified at creation time. • Commands for reading, writing, appending records, updating etc. – Commands work on the current EF. – Execution only if security conditions are met. • Each file has a life cycle status indicator (LCSI), one of: created, initialized, activated, deactivated, terminated.

Access control on the files • Applications may specify the access controls – A password (PIN) on the MF selection • For example SIM password in mobiles – Multiple passwords can be used and levels of security access may be given • Applications may also use cryptographic authentication

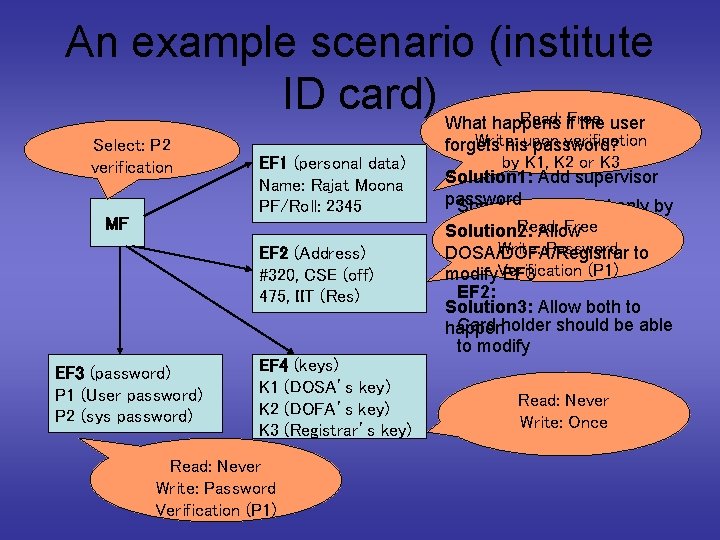
An example scenario (institute ID card) What happens Read: if. Free the user Select: P 2 verification MF EF 1 (personal data) Name: Rajat Moona PF/Roll: 2345 EF 2 (Address) #320, CSE (off) 475, IIT (Res) EF 3 (password) P 1 (User password) P 2 (sys password) EF 4 (keys) K 1 (DOSA’s key) K 2 (DOFA’s key) K 3 (Registrar’s key) Read: Never Write: Password Verification (P 1) Write: verification Security requirements: forgets hisupon password? by K 1, K 2 or K 3 EF 1: Solution 1: Add supervisor password Should be modified only by Read: Free the DOSA/DOFA/Registrar Solution 2: Allow Write: Password to DOSA/DOFA/Registrar Readable to all (P 1) modify. Verification EF 3 EF 2: Solution 3: Allow both to Card holder should be able happen to modify Read: Never Write: Once

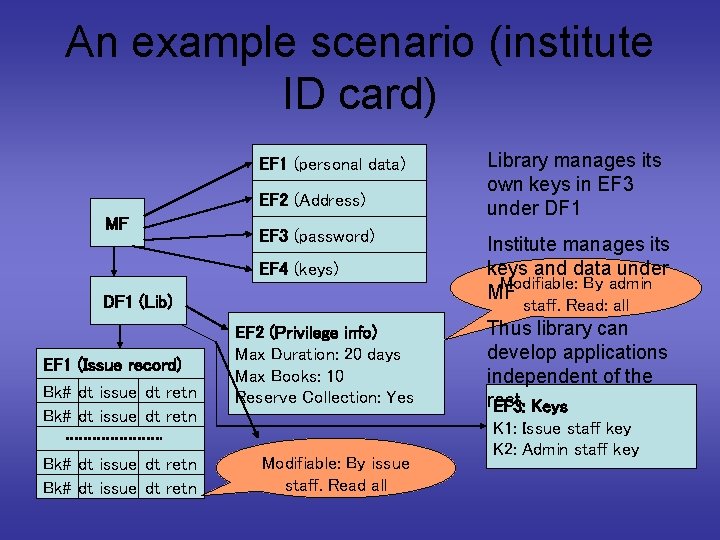
An example scenario (institute ID card) EF 1 (personal data) EF 2 (Address) MF EF 3 (password) EF 4 (keys) DF 1 (Lib) EF 1 (Issue record) Bk# dt issue dt retn Library manages its own keys in EF 3 under DF 1 Institute manages its keys and data under Modifiable: By admin MF staff. Read: all EF 2 (Privilege info) Max Duration: 20 days Max Books: 10 Reserve Collection: Yes Modifiable: By issue staff. Read all Thus library can develop applications independent of the rest. EF 3: Keys K 1: Issue staff key K 2: Admin staff key

How does it all work? Card is inserted in the terminal ATR negotiations take place to set up data transfer speeds, capability negotiations etc. Terminal sends first command to select MF Terminal prompts the user to provide password Terminal sends password for verification Terminal sends command to select MF again Terminal sends command to read EF 1 Card gets power. OS boots up. Sends ATR (Answer to reset) Card responds with an error (because MF selection is only on password presentation) Card verifies P 2. Stores a status “P 2 Verified”. Responds “OK” Card responds “OK” Card supplies personal data and responds “OK”

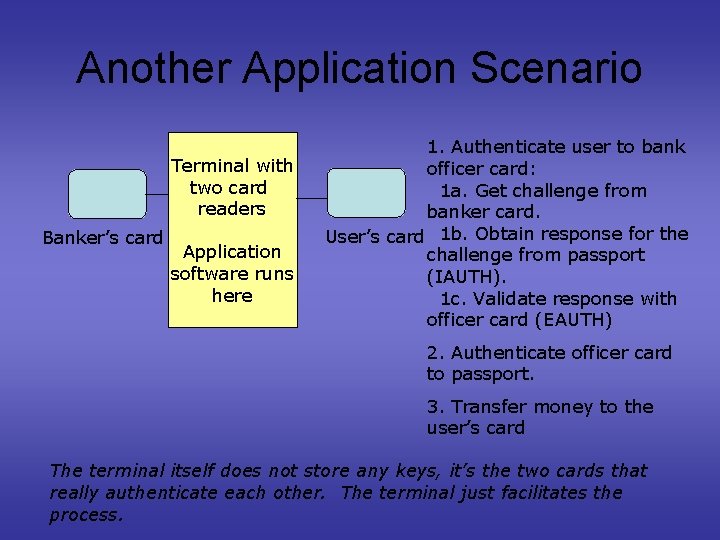
Another Application Scenario Terminal with two card readers Banker’s card Application software runs here 1. Authenticate user to bank officer card: 1 a. Get challenge from banker card. User’s card 1 b. Obtain response for the challenge from passport (IAUTH). 1 c. Validate response with officer card (EAUTH) 2. Authenticate officer card to passport. 3. Transfer money to the user’s card The terminal itself does not store any keys, it’s the two cards that really authenticate each other. The terminal just facilitates the process.

Status of smart card deployments • Famous Gujarat Dairy card – Primarily an ID card • GSM cards (SIM cards for mobiles) – Phone book etc. + authentication. • Cards for “credit card” applications. – By 2007 end all credit cards will be smart. – EMV standard • Card for e-purse applications – Bank cards • Card technology has advanced – Contactless smart cards, – 32 -bit processors and bigger memories – JAVA cards

Thank You