Forti Mail Overview Dedicated email security solution Last

















- Slides: 85

Forti. Mail Overview Dedicated email security solution Last Update: March 2008 Nathalie Rivat

Agenda • • • Introducing Forti. Mail deployment scenarios Forti. Mail product line Differentiated services: policies and profiles Antispam techniques Virus detection Forti. Mail HA Email archiving Reporting

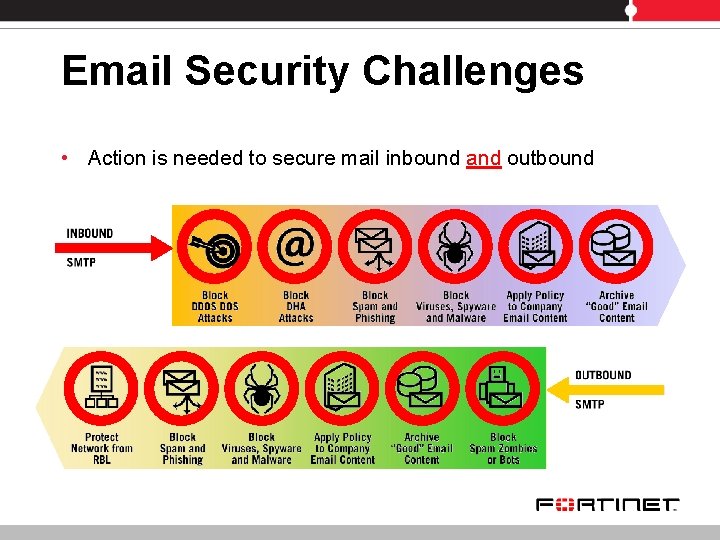
Email Security Challenges • Action is needed to secure mail inbound and outbound

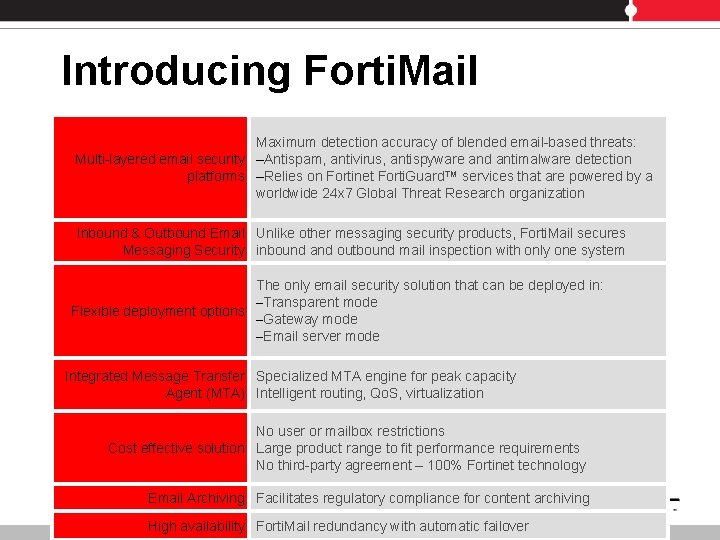
Introducing Forti. Mail Maximum detection accuracy of blended email-based threats: Multi-layered email security –Antispam, antivirus, antispyware and antimalware detection platforms –Relies on Fortinet Forti. Guard™ services that are powered by a worldwide 24 x 7 Global Threat Research organization Inbound & Outbound Email Unlike other messaging security products, Forti. Mail secures Messaging Security inbound and outbound mail inspection with only one system The only email security solution that can be deployed in: –Transparent mode Flexible deployment options –Gateway mode –Email server mode Integrated Message Transfer Specialized MTA engine for peak capacity Agent (MTA) Intelligent routing, Qo. S, virtualization No user or mailbox restrictions Cost effective solution Large product range to fit performance requirements No third-party agreement – 100% Fortinet technology Email Archiving Facilitates regulatory compliance for content archiving High availability Forti. Mail redundancy with automatic failover

Agenda • • • Introducing Forti. Mail deployment scenarios Forti. Mail product line Differentiated services: policies and profiles Antispam techniques Virus detection Forti. Mail HA Email archiving Reporting

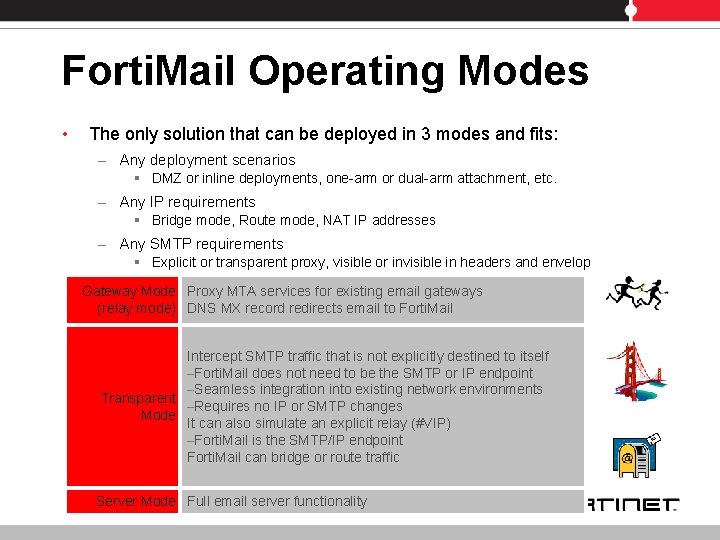
Forti. Mail Operating Modes • The only solution that can be deployed in 3 modes and fits: – Any deployment scenarios § DMZ or inline deployments, one-arm or dual-arm attachment, etc. – Any IP requirements § Bridge mode, Route mode, NAT IP addresses – Any SMTP requirements § Explicit or transparent proxy, visible or invisible in headers and envelop Gateway Mode Proxy MTA services for existing email gateways (relay mode) DNS MX record redirects email to Forti. Mail Intercept SMTP traffic that is not explicitly destined to itself –Forti. Mail does not need to be the SMTP or IP endpoint –Seamless integration into existing network environments Transparent –Requires no IP or SMTP changes Mode It can also simulate an explicit relay (#VIP) –Forti. Mail is the SMTP/IP endpoint Forti. Mail can bridge or route traffic Server Mode Full email server functionality

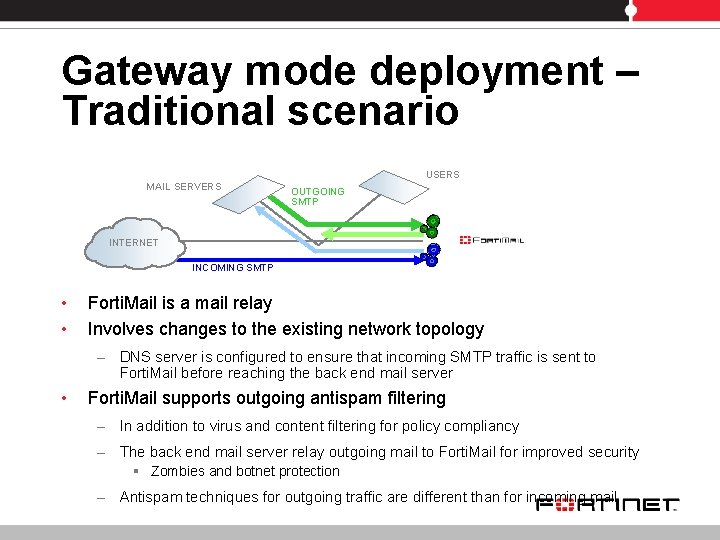
Gateway mode deployment – Traditional scenario USERS MAIL SERVERS OUTGOING SMTP INTERNET INCOMING SMTP • • Forti. Mail is a mail relay Involves changes to the existing network topology – DNS server is configured to ensure that incoming SMTP traffic is sent to Forti. Mail before reaching the back end mail server • Forti. Mail supports outgoing antispam filtering – In addition to virus and content filtering for policy compliancy – The back end mail server relay outgoing mail to Forti. Mail for improved security § Zombies and botnet protection – Antispam techniques for outgoing traffic are different than for incoming mail

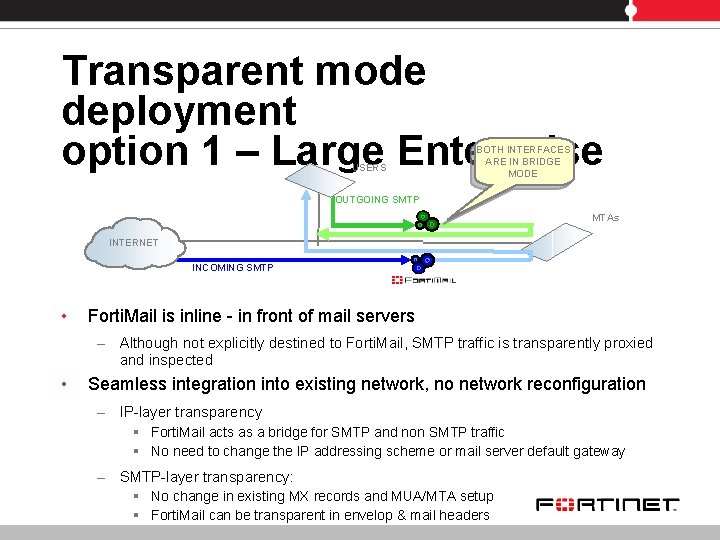
Transparent mode deployment option 1 – Large Enterprise USERS BOTH INTERFACES ARE IN BRIDGE MODE OUTGOING SMTP MTAs INTERNET INCOMING SMTP • Forti. Mail is inline - in front of mail servers – Although not explicitly destined to Forti. Mail, SMTP traffic is transparently proxied and inspected • Seamless integration into existing network, no network reconfiguration – IP-layer transparency § Forti. Mail acts as a bridge for SMTP and non SMTP traffic § No need to change the IP addressing scheme or mail server default gateway – SMTP-layer transparency: § No change in existing MX records and MUA/MTA setup § Forti. Mail can be transparent in envelop & mail headers

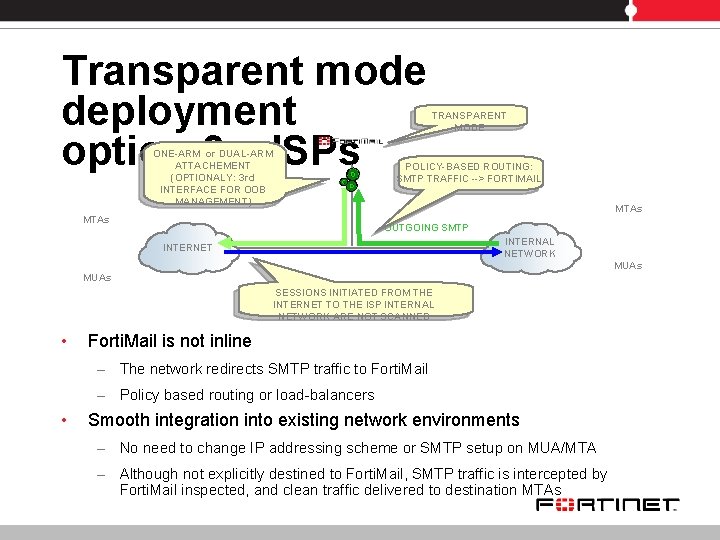
Transparent mode deployment option 2 – ISPs ONE-ARM or DUAL-ARM ATTACHEMENT (OPTIONALY: 3 rd INTERFACE FOR OOB MANAGEMENT) TRANSPARENT MODE POLICY-BASED ROUTING: SMTP TRAFFIC --> FORTIMAIL MTAs OUTGOING SMTP INTERNAL NETWORK INTERNET MUAs SESSIONS INITIATED FROM THE INTERNET TO THE ISP INTERNAL NETWORK ARE NOT SCANNED • Forti. Mail is not inline – The network redirects SMTP traffic to Forti. Mail – Policy based routing or load-balancers • Smooth integration into existing network environments – No need to change IP addressing scheme or SMTP setup on MUA/MTA – Although not explicitly destined to Forti. Mail, SMTP traffic is intercepted by Forti. Mail inspected, and clean traffic delivered to destination MTAs

ISP scenario • ISP and Mobile Operators are concerned about filtering outgoing spam to protect their IP addresses from blacklisting – Spammers cause ISP addresses to be black-listed by DNSBL servers – Outgoing SMTP connections = any SMTP session initiated from the internal network and destined to MTAs on the Internet – Outgoing mail flow are NATed behind the Service Provider public IP addresses

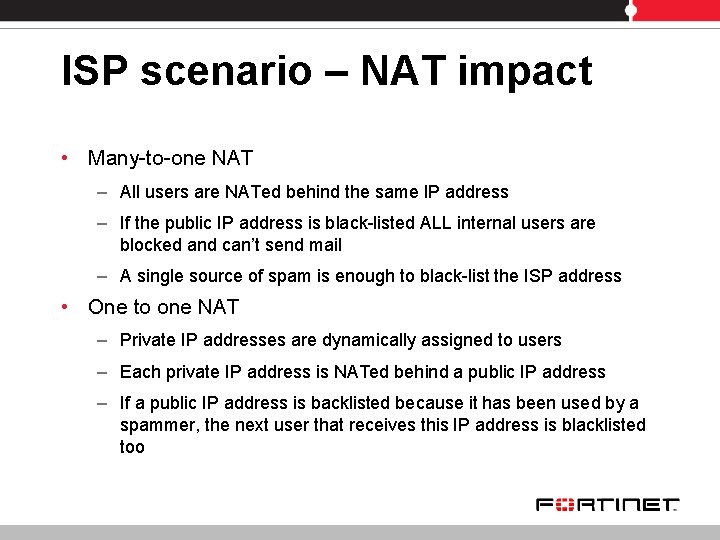
ISP scenario – NAT impact • Many-to-one NAT – All users are NATed behind the same IP address – If the public IP address is black-listed ALL internal users are blocked and can’t send mail – A single source of spam is enough to black-list the ISP address • One to one NAT – Private IP addresses are dynamically assigned to users – Each private IP address is NATed behind a public IP address – If a public IP address is backlisted because it has been used by a spammer, the next user that receives this IP address is blacklisted too

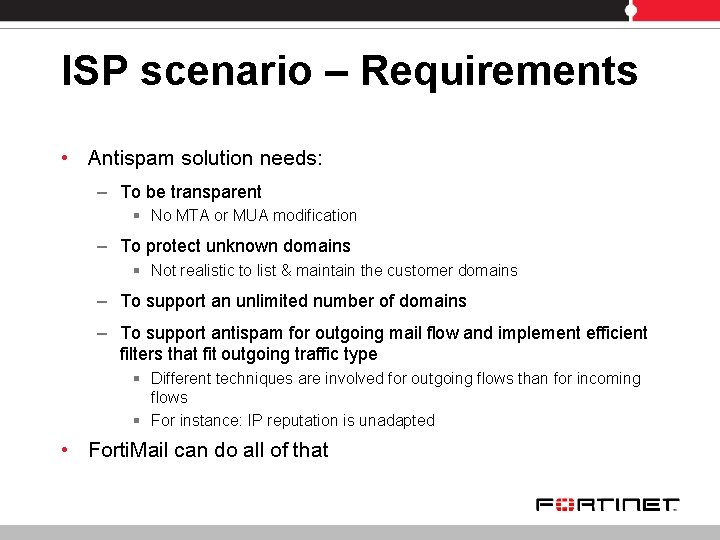
ISP scenario – Requirements • Antispam solution needs: – To be transparent § No MTA or MUA modification – To protect unknown domains § Not realistic to list & maintain the customer domains – To support an unlimited number of domains – To support antispam for outgoing mail flow and implement efficient filters that fit outgoing traffic type § Different techniques are involved for outgoing flows than for incoming flows § For instance: IP reputation is unadapted • Forti. Mail can do all of that

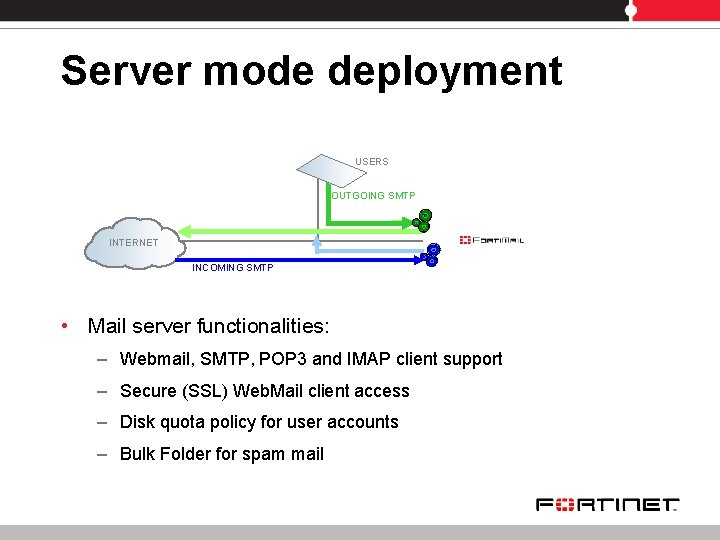
Server mode deployment USERS OUTGOING SMTP INTERNET INCOMING SMTP • Mail server functionalities: – Webmail, SMTP, POP 3 and IMAP client support – Secure (SSL) Web. Mail client access – Disk quota policy for user accounts – Bulk Folder for spam mail

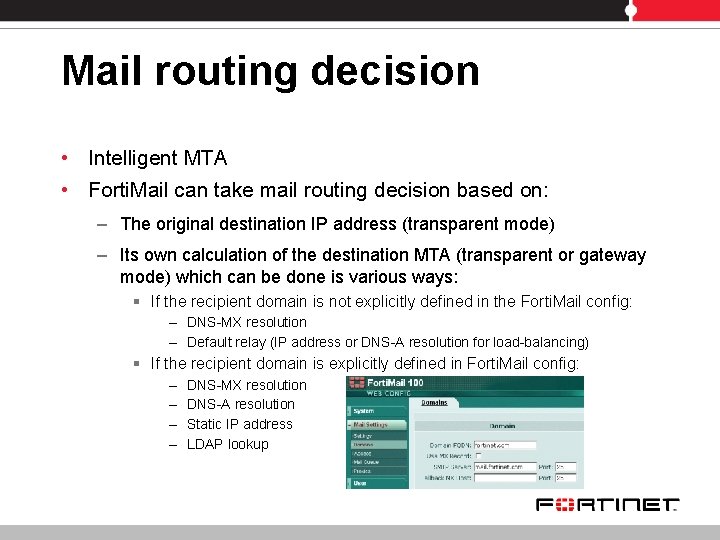
Mail routing decision • Intelligent MTA • Forti. Mail can take mail routing decision based on: – The original destination IP address (transparent mode) – Its own calculation of the destination MTA (transparent or gateway mode) which can be done is various ways: § If the recipient domain is not explicitly defined in the Forti. Mail config: – DNS-MX resolution – Default relay (IP address or DNS-A resolution for load-balancing) § If the recipient domain is explicitly defined in Forti. Mail config: – – DNS-MX resolution DNS-A resolution Static IP address LDAP lookup

Agenda • • • Introducing Forti. Mail deployment scenarios Forti. Mail product line Differentiated services: policies and profiles Antispam techniques Virus detection Forti. Mail HA Email archiving Reporting

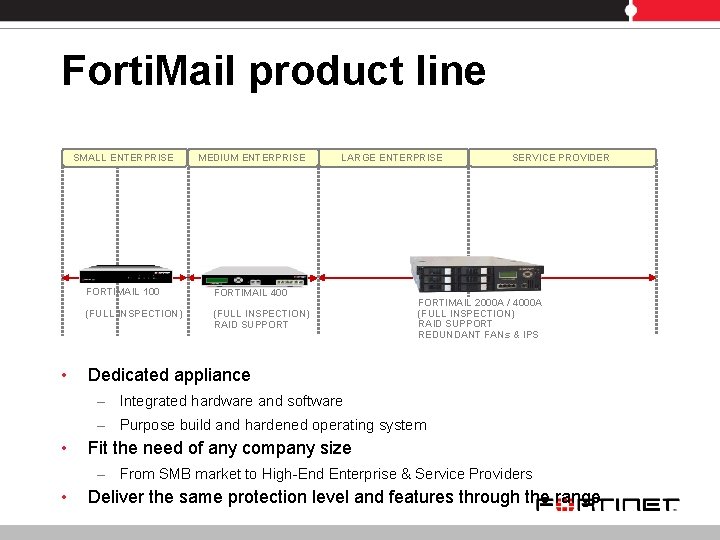
Forti. Mail product line • SMALL ENTERPRISE MEDIUM ENTERPRISE FORTIMAIL 100 FORTIMAIL 400 (FULL INSPECTION) RAID SUPPORT LARGE ENTERPRISE SERVICE PROVIDER FORTIMAIL 2000 A / 4000 A (FULL INSPECTION) RAID SUPPORT REDUNDANT FANs & IPS Dedicated appliance – Integrated hardware and software – Purpose build and hardened operating system • Fit the need of any company size – From SMB market to High-End Enterprise & Service Providers • Deliver the same protection level and features through the range

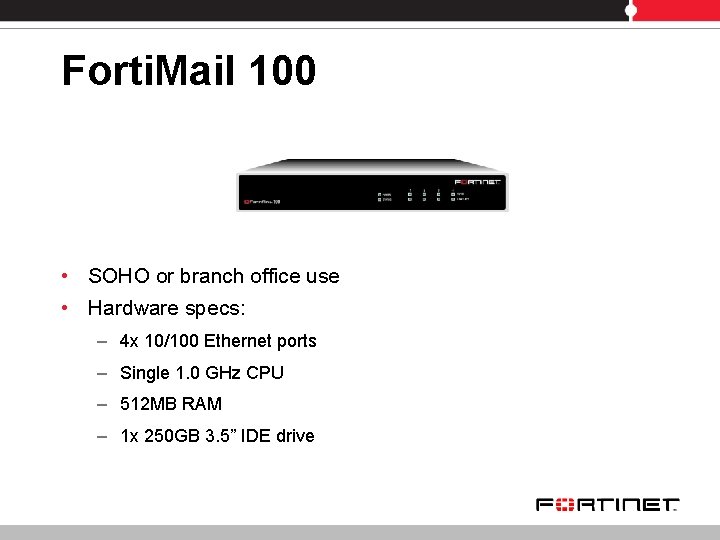
Forti. Mail 100 • SOHO or branch office use • Hardware specs: – 4 x 10/100 Ethernet ports – Single 1. 0 GHz CPU – 512 MB RAM – 1 x 250 GB 3. 5” IDE drive

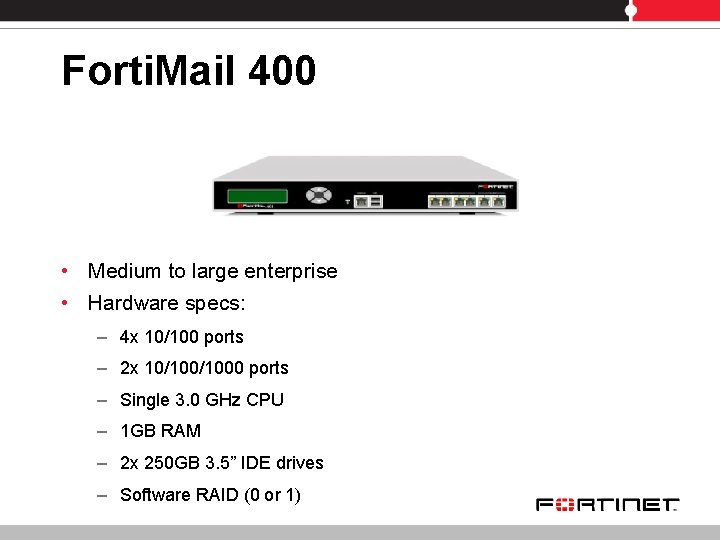
Forti. Mail 400 • Medium to large enterprise • Hardware specs: – 4 x 10/100 ports – 2 x 10/1000 ports – Single 3. 0 GHz CPU – 1 GB RAM – 2 x 250 GB 3. 5” IDE drives – Software RAID (0 or 1)

Forti. Mail 2000 A / 4000 A • • Large enterprise and Service Providers Hardware specs: – 4 x 10/1000 Ethernet ports – Single / Dual Xeon 3. 0 GHz CPUs – 2 GB of RAM – 6 x / 12 x 250 GB 3. 5” SATA drives – Hardware RAID (0, 1, 5, 10 or 50) – Redundant power supplies – Hot-swappable fans

Agenda • • • Introducing Forti. Mail deployment scenarios Forti. Mail product line Differentiated services: policies and profiles Antispam techniques Virus detection Forti. Mail HA Email archiving Reporting

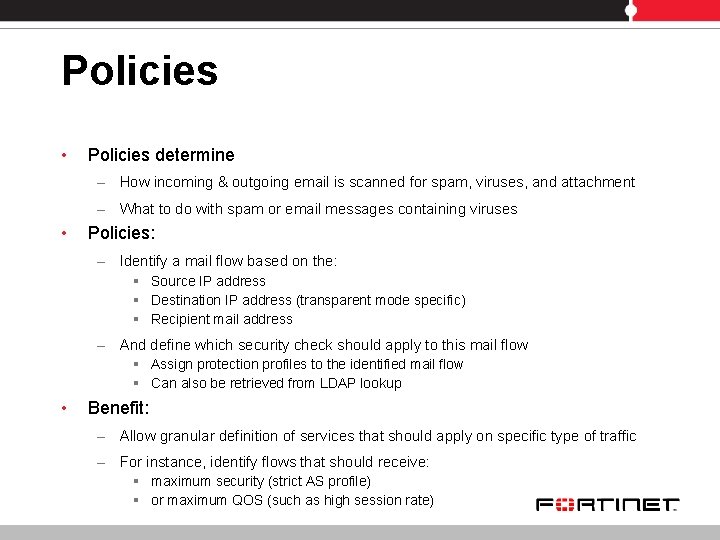
Policies • Policies determine – How incoming & outgoing email is scanned for spam, viruses, and attachment – What to do with spam or email messages containing viruses • Policies: – Identify a mail flow based on the: § Source IP address § Destination IP address (transparent mode specific) § Recipient mail address – And define which security check should apply to this mail flow § Assign protection profiles to the identified mail flow § Can also be retrieved from LDAP lookup • Benefit: – Allow granular definition of services that should apply on specific type of traffic – For instance, identify flows that should receive: § maximum security (strict AS profile) § or maximum QOS (such as high session rate)

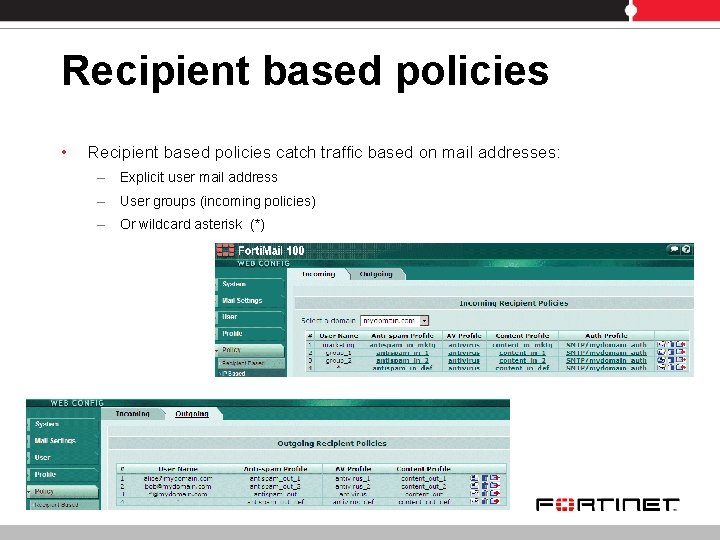
Recipient based policies • Recipient based policies catch traffic based on mail addresses: – Explicit user mail address – User groups (incoming policies) – Or wildcard asterisk (*)

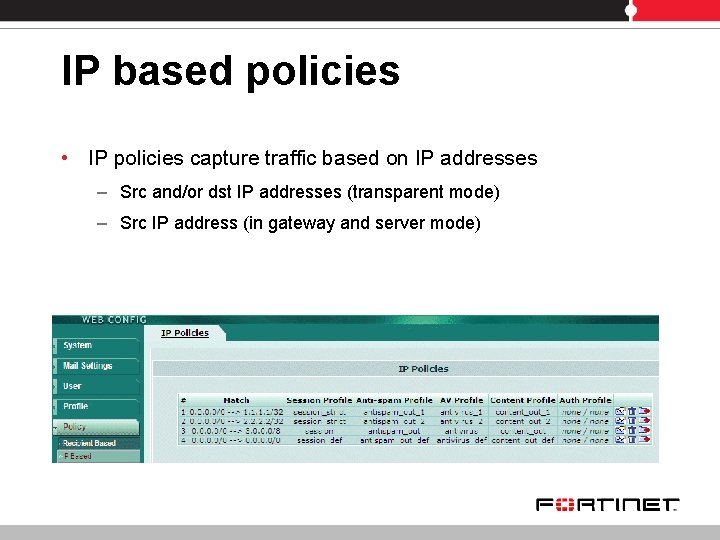
IP based policies • IP policies capture traffic based on IP addresses – Src and/or dst IP addresses (transparent mode) – Src IP address (in gateway and server mode)

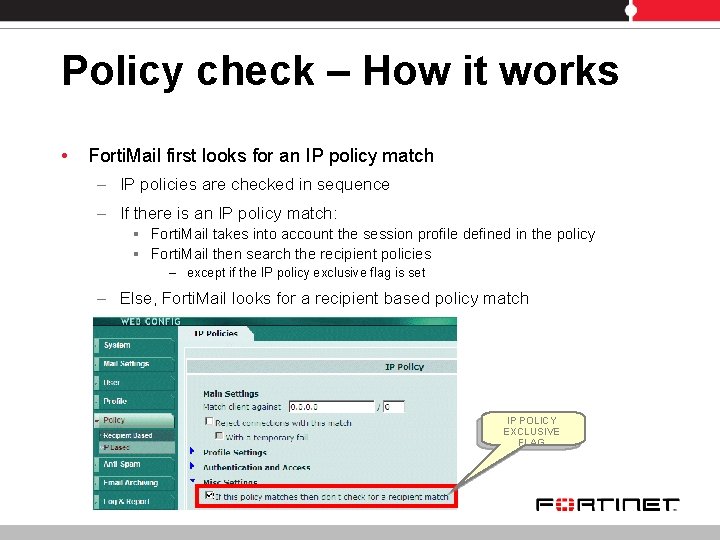
Policy check – How it works • Forti. Mail first looks for an IP policy match – IP policies are checked in sequence – If there is an IP policy match: § Forti. Mail takes into account the session profile defined in the policy § Forti. Mail then search the recipient policies – except if the IP policy exclusive flag is set – Else, Forti. Mail looks for a recipient based policy match IP POLICY EXCLUSIVE FLAG

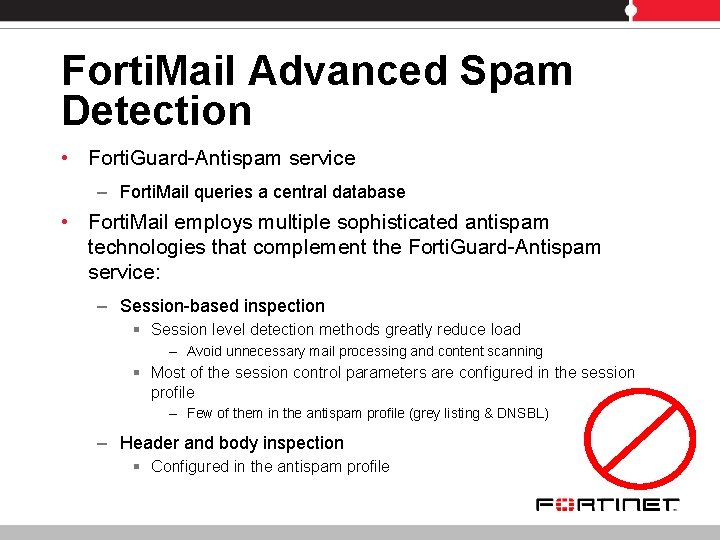
Protection profiles • • • Profile = a collection of Forti. Mail settings that control the email flow Profiles are selected in policies and run on any traffic the policy controls Several types of profile: – Session profile § Set session rate § Restrict the number of mail per session, of recipients per mail, of simultaneous session for the same client § Prevent session encryption, § Perform SMTP strict syntax check, domain check, etc. – Antispam profile – Antivirus profile – Content profile § Filter file type, file extensions, banned content § Defer large message – Authentication profile § Authenticate sessions using SMTP, POP 3, IMAP, or RADIUS servers

Comments • You do not have to define the protected domains – Mail Service Provider and Internet Service Provider environment – Differentiated services can still apply based on IP addresses or recipient mail addresses • Wildcard policies – IP=0. 0/0 – or recipient address=* • Antispam, antivirus, content and session profiles are available for incoming or outgoing mail flow

Agenda • • • Introducing Forti. Mail deployment scenarios Forti. Mail product line Differentiated services: policies and profiles Antispam techniques Virus detection Forti. Mail HA Email archiving Reporting

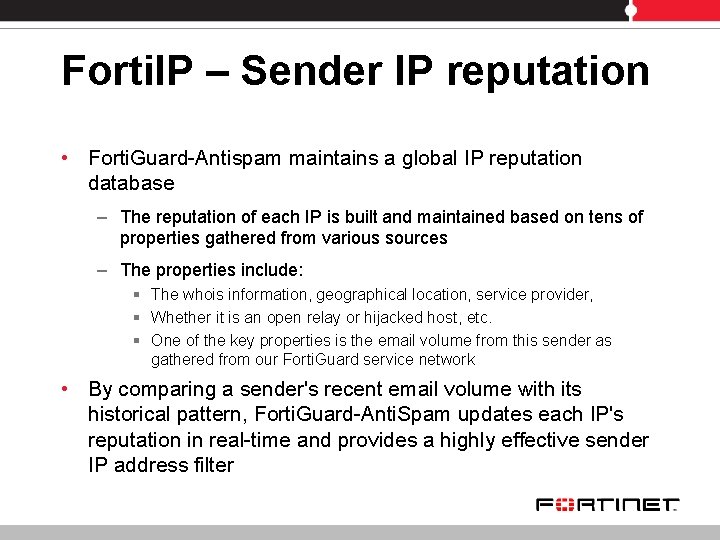
Forti. Mail Advanced Spam Detection • Forti. Guard-Antispam service – Forti. Mail queries a central database • Forti. Mail employs multiple sophisticated antispam technologies that complement the Forti. Guard-Antispam service: – Session-based inspection § Session level detection methods greatly reduce load – Avoid unnecessary mail processing and content scanning § Most of the session control parameters are configured in the session profile – Few of them in the antispam profile (grey listing & DNSBL) – Header and body inspection § Configured in the antispam profile

Forti. Guard-Antispam • Forti. Guard-Antispam uses a number of filtering techniques to detect and filter spam: – Forti. IP = Sender IP reputation database § IP address scoring – Forti. Sig 1 = Spamvertised URLs § Block messages that have spam hosts mentioned in message bodies § Detect spam based on the URIs (usually web sites) contained in the message body as opposed to the spam origin (used by RBL) – Forti. Sig 2 = Spamvertised email addresses § Lots of spam have an email address in the message body that prompts one to contact the spammers. Those email addresses are added to Forti. Sig – Forti. Sig 3 = Spam object checksums § Objects in spam are identified and a fuzzy checksum is calculated from each object which it then added top the Forti. Sig database – Objects can be part of the message body or an attachment • Forti. Rule – Forti. Guard also updates Forti. Mail local set of heuristics rules

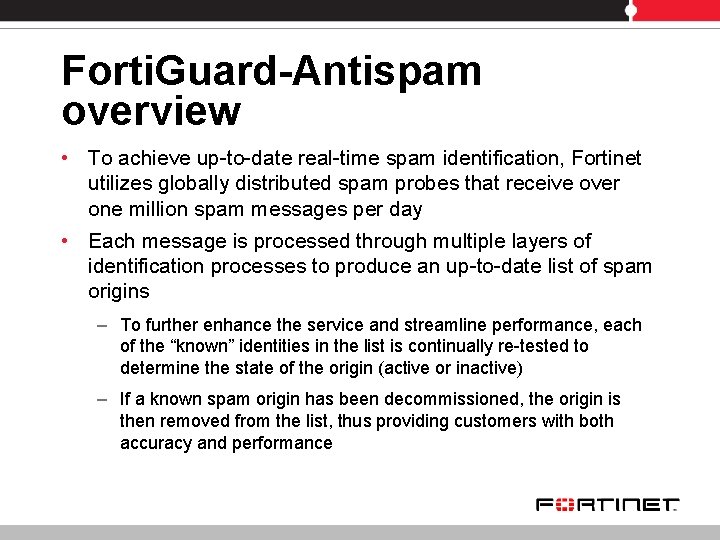
Forti. IP – Sender IP reputation • Forti. Guard-Antispam maintains a global IP reputation database – The reputation of each IP is built and maintained based on tens of properties gathered from various sources – The properties include: § The whois information, geographical location, service provider, § Whether it is an open relay or hijacked host, etc. § One of the key properties is the email volume from this sender as gathered from our Forti. Guard service network • By comparing a sender's recent email volume with its historical pattern, Forti. Guard-Anti. Spam updates each IP's reputation in real-time and provides a highly effective sender IP address filter

Forti. Guard-Antispam overview • To achieve up-to-date real-time spam identification, Fortinet utilizes globally distributed spam probes that receive over one million spam messages per day • Each message is processed through multiple layers of identification processes to produce an up-to-date list of spam origins – To further enhance the service and streamline performance, each of the “known” identities in the list is continually re-tested to determine the state of the origin (active or inactive) – If a known spam origin has been decommissioned, the origin is then removed from the list, thus providing customers with both accuracy and performance

Forti. Mail Advanced Spam Detection • Session based inspection – SMTP syntax verification and RFC compliancy – SMTP checks (sender/recipient domain check, prevent open relay, etc. ) – SMTP rate limiting (simultaneous sessions, new sessions / period of time, etc. ) – SMTP error control – Recipient address check (valid mail address) – Greylist Filtering – Local Reputation Filtering – Etc.

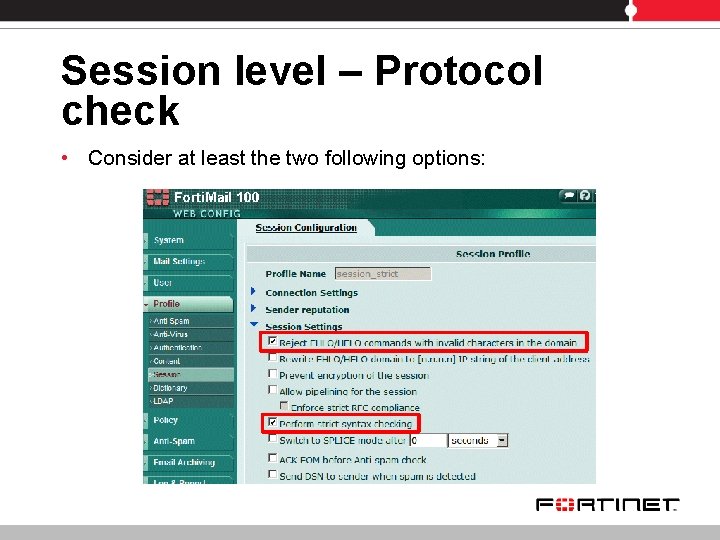
Session level – Protocol check • Consider at least the two following options:

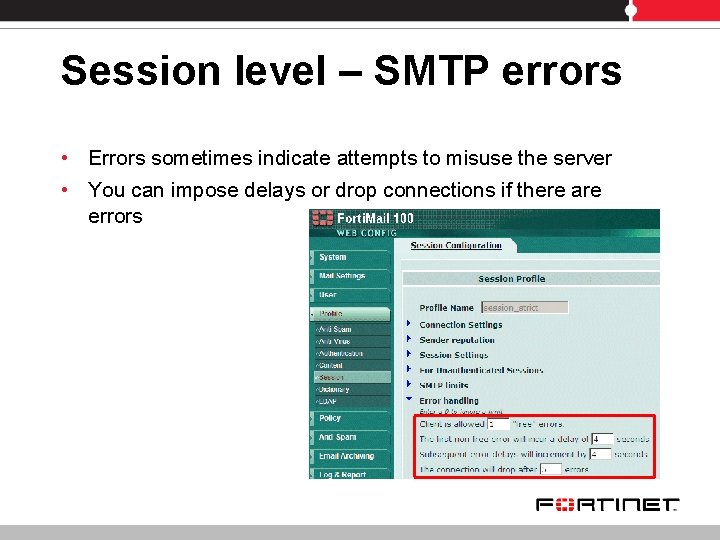
Session level – SMTP errors • Errors sometimes indicate attempts to misuse the server • You can impose delays or drop connections if there are errors

Session level – Unauth sessions • Check sender domain – Checks the existence of the sender domain by looking up both the MX record and A record – One successful query would pass the check – Enable it depending on deployment scenario § Useful for ISP outgoing antispam and MSP/Enterprise incoming mail • Check recipient domain – Checks the existence of the sender domain by looking up both the MX record and A record – One successful query would pass the check – Enable this depending on your deployment scenario § Useful for ISP/MSP/Enterprise outgoing antispam

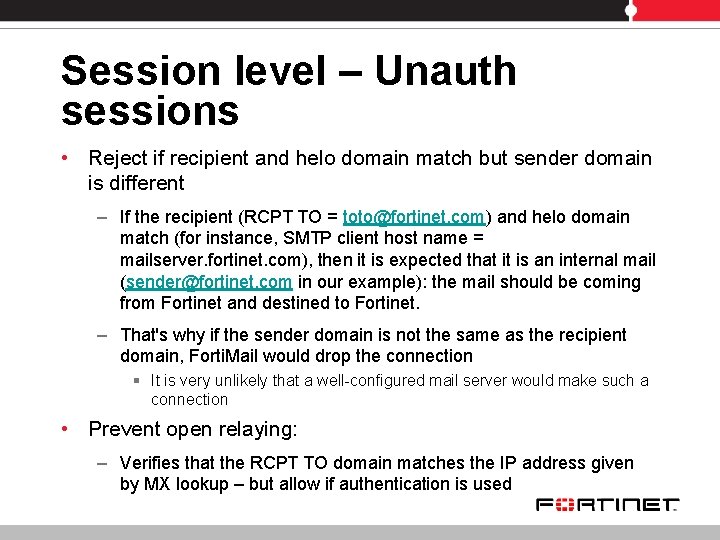
Session level – Unauth sessions • Reject if recipient and helo domain match but sender domain is different – If the recipient (RCPT TO = toto@fortinet. com) and helo domain match (for instance, SMTP client host name = mailserver. fortinet. com), then it is expected that it is an internal mail (sender@fortinet. com in our example): the mail should be coming from Fortinet and destined to Fortinet. – That's why if the sender domain is not the same as the recipient domain, Forti. Mail would drop the connection § It is very unlikely that a well-configured mail server would make such a connection • Prevent open relaying: – Verifies that the RCPT TO domain matches the IP address given by MX lookup – but allow if authentication is used

Session level – Settings for unauth sessions

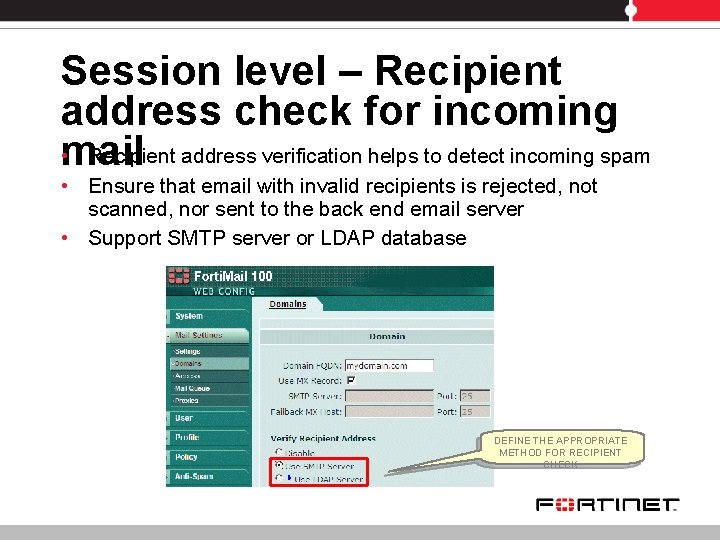
Session level – Recipient address check for incoming • mail Recipient address verification helps to detect incoming spam • Ensure that email with invalid recipients is rejected, not scanned, nor sent to the back end email server • Support SMTP server or LDAP database DEFINE THE APPROPRIATE METHOD FOR RECIPIENT CHECK

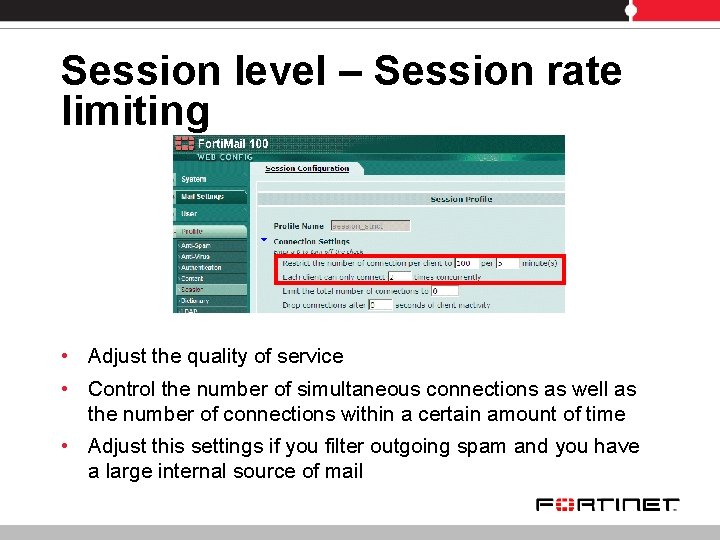
Session level – Session rate limiting • Adjust the quality of service • Control the number of simultaneous connections as well as the number of connections within a certain amount of time • Adjust this settings if you filter outgoing spam and you have a large internal source of mail

Session level – Sender Reputation • An anti-spam measure managed by Forti. Mail and requiring no maintenance or attention • Forti. Mail keeps track of SMTP client behavior – If a sender delivers mail including spam and/or viruses, or a large number of invalid users, the sender reputation feature will take measures against them • Those sending excessive spam messages, infected mail, or messages to invalid recipients will have their deliveries limited • Should clients continue delivering these types of messages, their connection attempts will be rejected entirely • To make it working efficiently, network must not hide the client IP addresses to Forti. Mail – Forti. Mail is not connected behind a NAT device – Forti. Mail is not receiving connections from a relay

Sender Reputation – Specifics • Forti. Mail records for each SMTP client (IP address): – Total number of messages delivered – Number of messages detected as spam – Number of messages infected with viruses or worms – Total number of recipients – Number of invalid recipients • Forti. Mail determines a sender’s reputation score using 2 ratios: – The amount of good email compared to the bad mail – The total number of recipients as compared to the number of bad recipients • Forti. Mail uses email information up to twelve hours old, and recent mail influences the score calculation more than older mail – Score from 0 to 100, (0= a very well behaved sender, 100 = the type of sender you’d rather avoid) – After 12 hours without a mail delivery from a client, client records are deleted • The sender reputation score is compared to 3 thresholds (customizable): – Above the 1 st value, Forti. Mail limits the number of messages accepted per hour – Above the 2 nd value, Forti. Mail rejects the connection returning a temporary fail error – Above third value, Forti. Mail refuses the connection returning a reject message

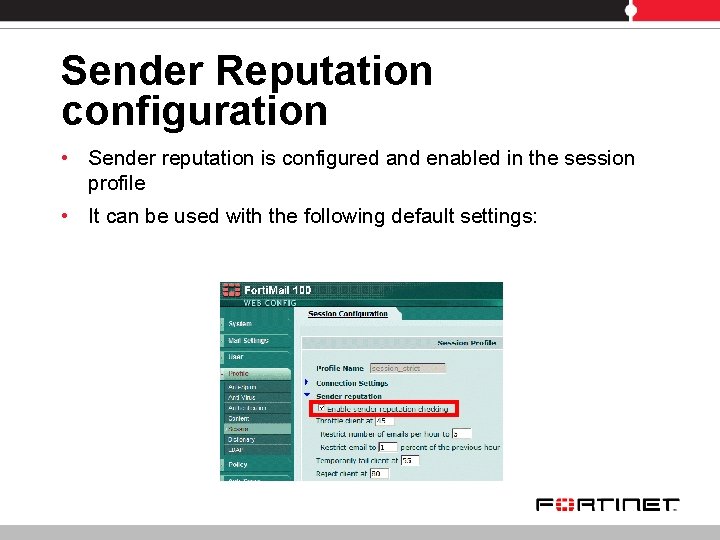
Sender Reputation configuration • Sender reputation is configured and enabled in the session profile • It can be used with the following default settings:

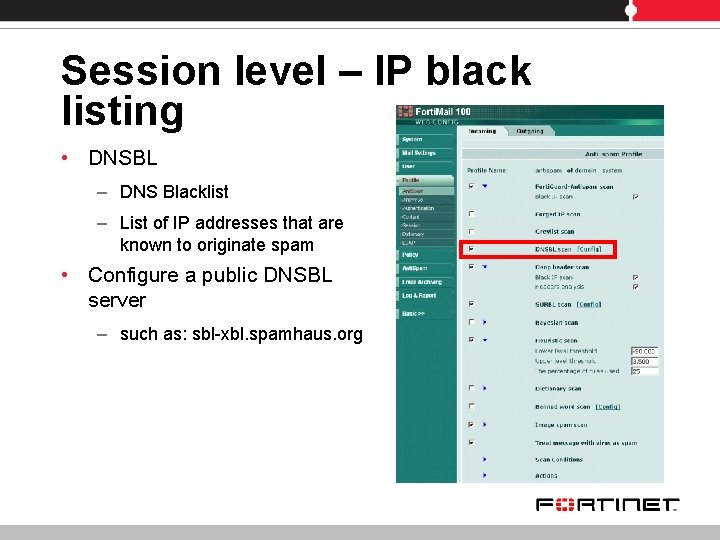
Session level – IP black listing • DNSBL – DNS Blacklist – List of IP addresses that are known to originate spam • Configure a public DNSBL server – such as: sbl-xbl. spamhaus. org

Session level – Greylisting • A mean of reducing spam in a relatively low maintenance manner – No IP address lists, email lists, or word lists to keep up to date – The only required list is automatically maintained by the Forti. Mail unit • Block spam based on the behavior of the sending server, rather than the content of the messages – When receiving an email from an unknown server, the Forti. Mail temporarily rejects the email – If the mail is legitimate, the originating server will try again later, at which time the Forti. Mail unit will accept it – Spam servers will very unlikely attempt a retry • Grey listing is enabled in the antispam incoming/outgoing profiles

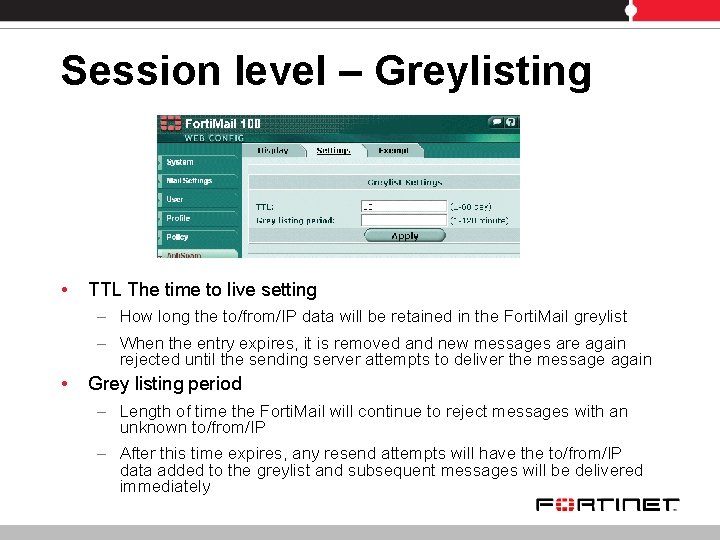
Session level – Greylisting • TTL The time to live setting – How long the to/from/IP data will be retained in the Forti. Mail greylist – When the entry expires, it is removed and new messages are again rejected until the sending server attempts to deliver the message again • Grey listing period – Length of time the Forti. Mail will continue to reject messages with an unknown to/from/IP – After this time expires, any resend attempts will have the to/from/IP data added to the greylist and subsequent messages will be delivered immediately

Greylisting – Specifics • Greylist routine looks at the envelop and extract 3 values: – Sender address (Mail From: ) – Recipient address (Rctp to: ) – IP address of the mail server delivering the message • If the greylist routine doesn’t have a record of a message with these three values: – Message is refused – Temporary error is reported to the server attempting delivery • The delivering server should later attempt to send the mail again – Mail servers following specifications (RFC 821) will attempt to retry deliveries that fail with expected error codes § Most spam mail is not delivered by standard mail servers, but rather by applications designed specifically for spam distribution – If another delivery is attempted, the message is accepted § Forti. Mail has stored the 3 attributes so any subsequent messages with these same three values is immediately accepted

Grey listing – Comments • Grey listing is a very efficient method that is destined to MTA sessions • Grey listing should not apply to MUA sessions – If it is not possible for Forti. Mail to distinguish MUA sessions from MTA sessions, do not enable grey listing – Example: ISP deployment for outgoing antispam • Forti. Mail automatically bypass grey listing for SMTP sessions it authenticates

Header and body inspection • Header and body inspection – Deep header scanning – Image Analysis Filtering – Heuristics Rules (several thousands) – dynamic update § Maintained by Fortinet’s antispam research team § Automatic upload through Forti. Guard services – Public SURBL – Attachment filtering (PDF scan) – Per User / Domain Bayesian Filtering – Locally administered black/white list of domains and users – Banned words / dictionnary scanning

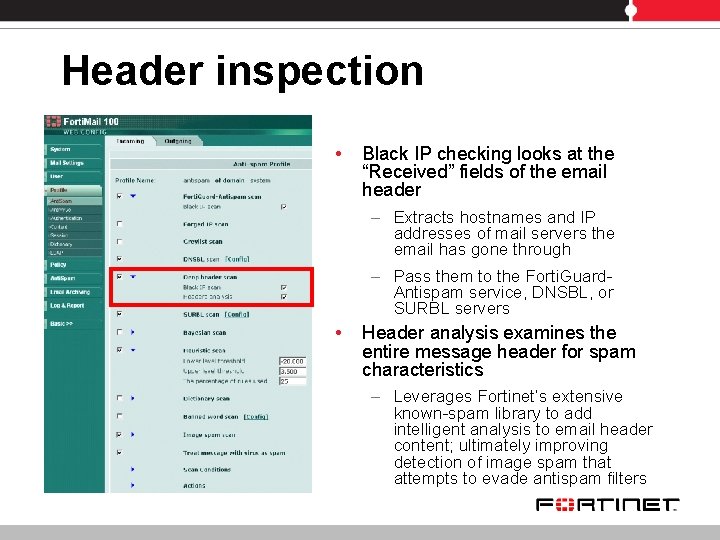
Header inspection • Black IP checking looks at the “Received” fields of the email header – Extracts hostnames and IP addresses of mail servers the email has gone through – Pass them to the Forti. Guard. Antispam service, DNSBL, or SURBL servers • Header analysis examines the entire message header for spam characteristics – Leverages Fortinet’s extensive known-spam library to add intelligent analysis to email header content; ultimately improving detection of image spam that attempts to evade antispam filters

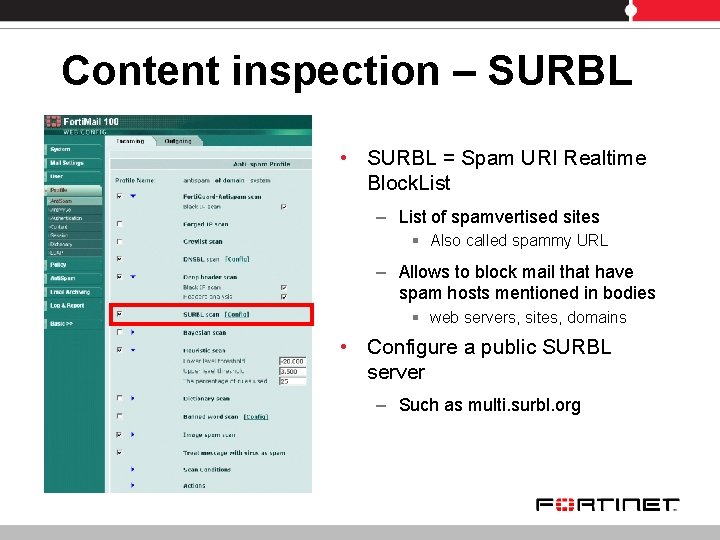
Content inspection – SURBL • SURBL = Spam URI Realtime Block. List – List of spamvertised sites § Also called spammy URL – Allows to block mail that have spam hosts mentioned in bodies § web servers, sites, domains • Configure a public SURBL server – Such as multi. surbl. org

Content inspection – Image scanning • An increasingly common tactic used by spammers is to replace the message body with an image file – This image file displays a graphic of the desired text • Image spam are difficult to detect since spammers slightly change the image – To avoid signature based detection methods (such as Forti. Sig 3 = Spam object checksums) • Forti. Mail’s image scan detects spam where the message body includes an image – Examines and identifies GIF, JPEG, and PNG graphics – Detects spam based on email header and body analysis, and image processing • Process is locally achieved by Forti. Mail and does not use OCR (optical character recognition) – Our testing has shown this method is not effective enough

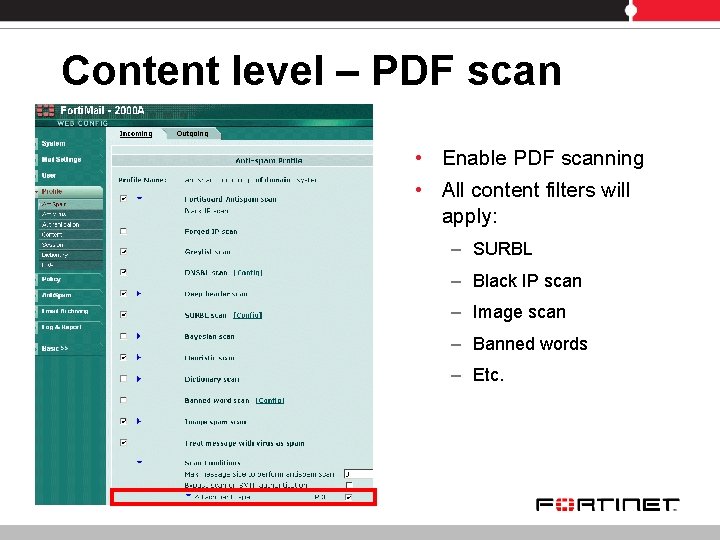
Content level – PDF scan • Enable PDF scanning • All content filters will apply: – SURBL – Black IP scan – Image scan – Banned words – Etc.

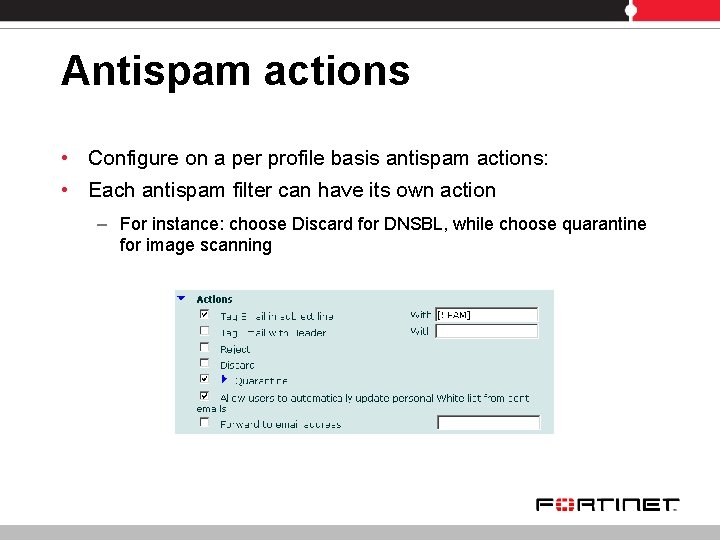
Antispam actions • Configure on a per profile basis antispam actions: • Each antispam filter can have its own action – For instance: choose Discard for DNSBL, while choose quarantine for image scanning

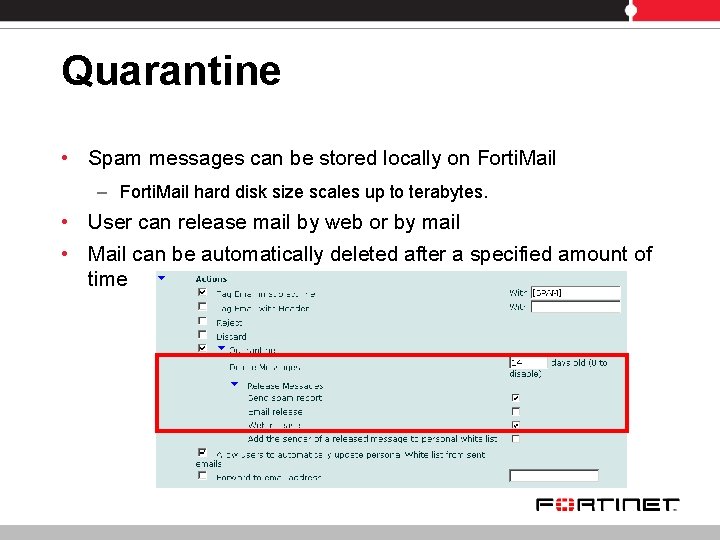
Quarantine • Spam messages can be stored locally on Forti. Mail – Forti. Mail hard disk size scales up to terabytes. • User can release mail by web or by mail • Mail can be automatically deleted after a specified amount of time

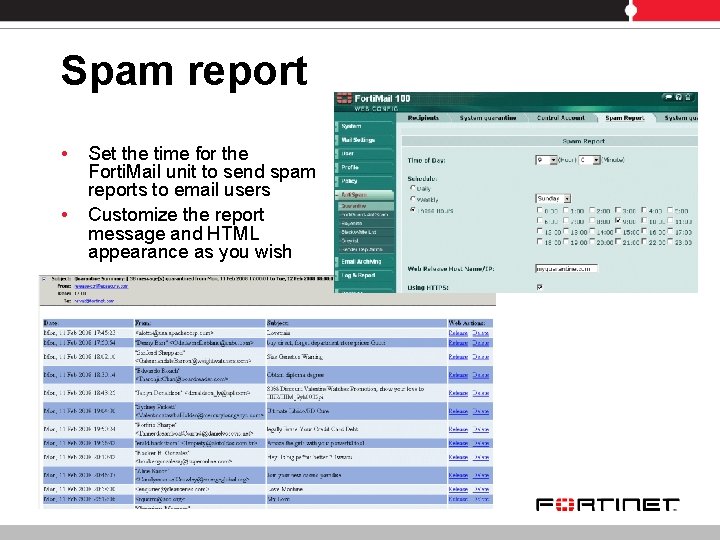
Spam report • • Set the time for the Forti. Mail unit to send spam reports to email users Customize the report message and HTML appearance as you wish

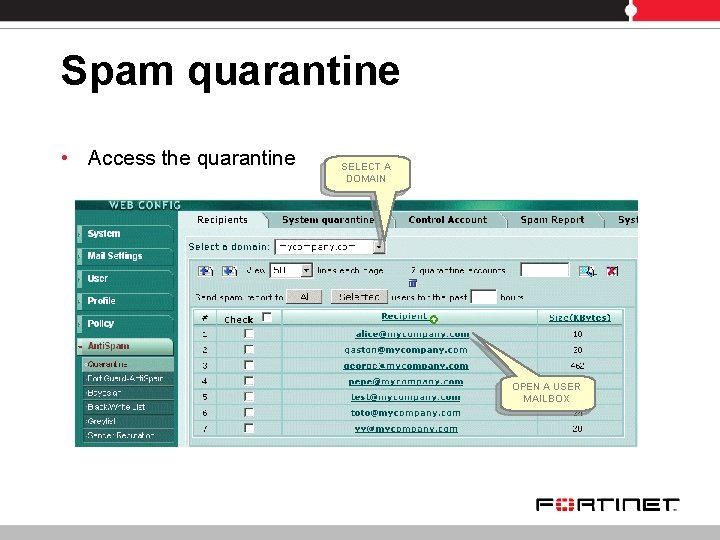
Spam quarantine • Access the quarantine SELECT A DOMAIN OPEN A USER MAILBOX

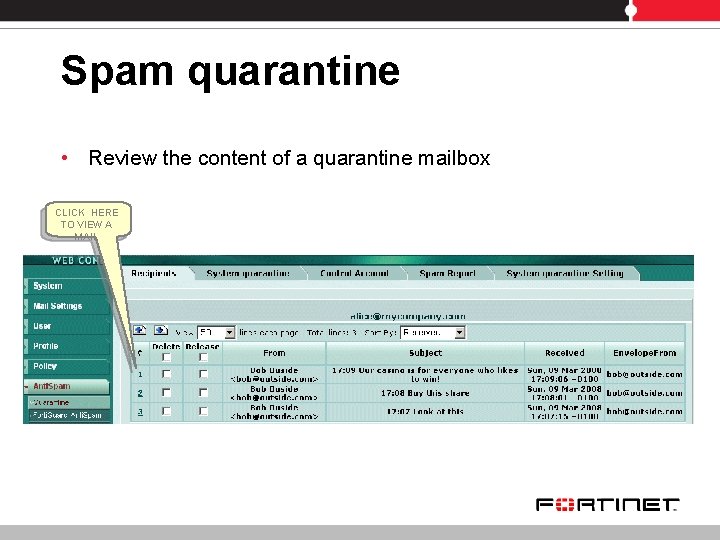
Spam quarantine • Review the content of a quarantine mailbox CLICK HERE TO VIEW A MAIL

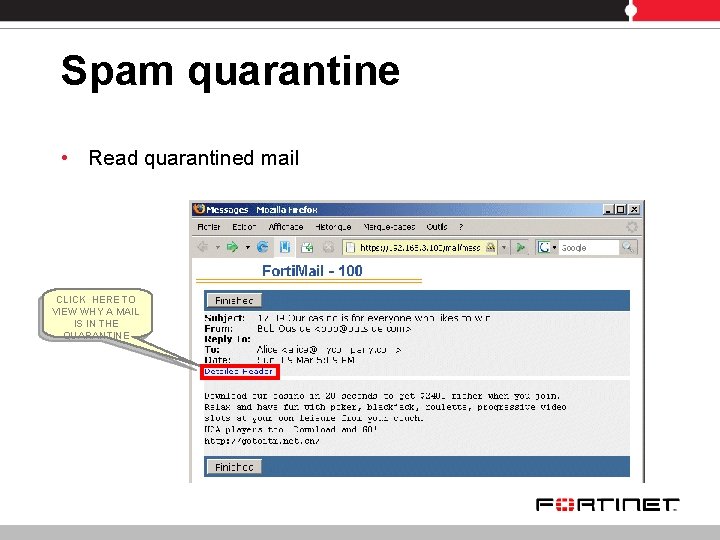
Spam quarantine • Read quarantined mail CLICK HERE TO VIEW WHY A MAIL IS IN THE QUARANTINE

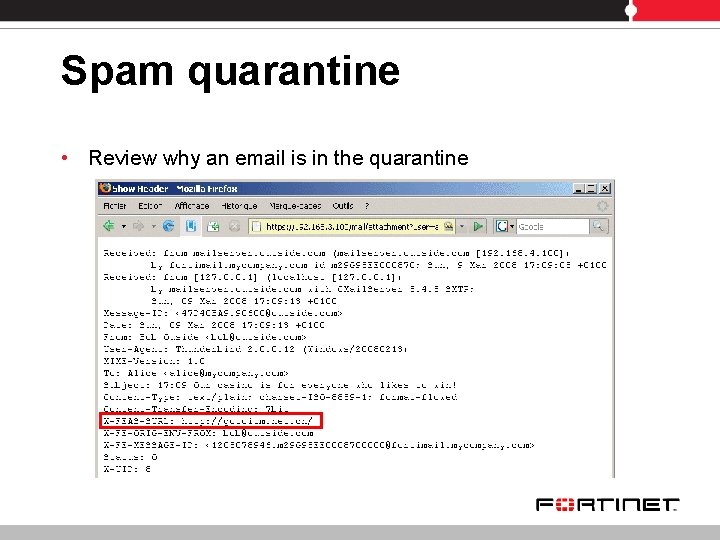
Spam quarantine • Review why an email is in the quarantine

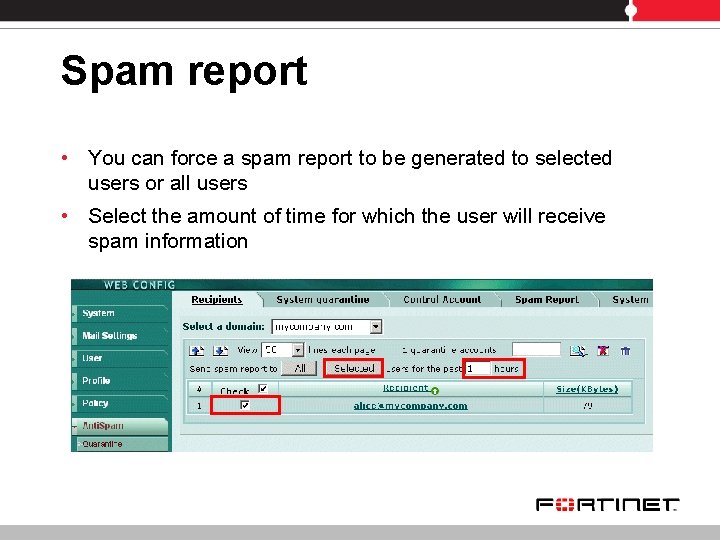
Spam report • You can force a spam report to be generated to selected users or all users • Select the amount of time for which the user will receive spam information

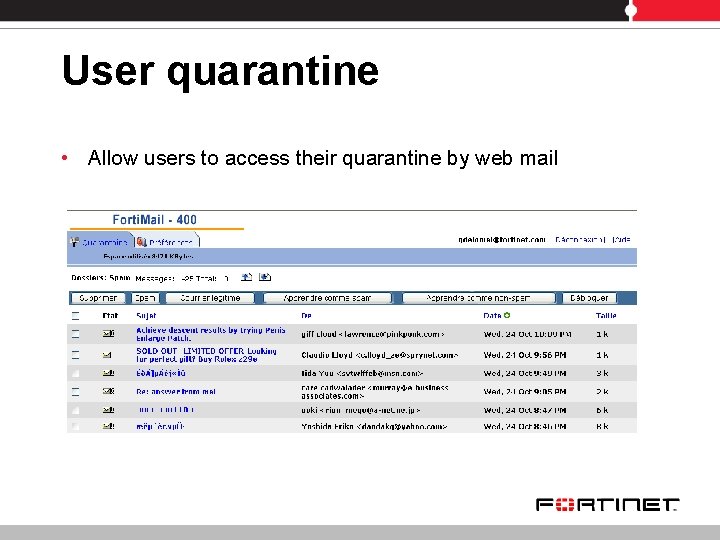
User quarantine • Allow users to access their quarantine by web mail

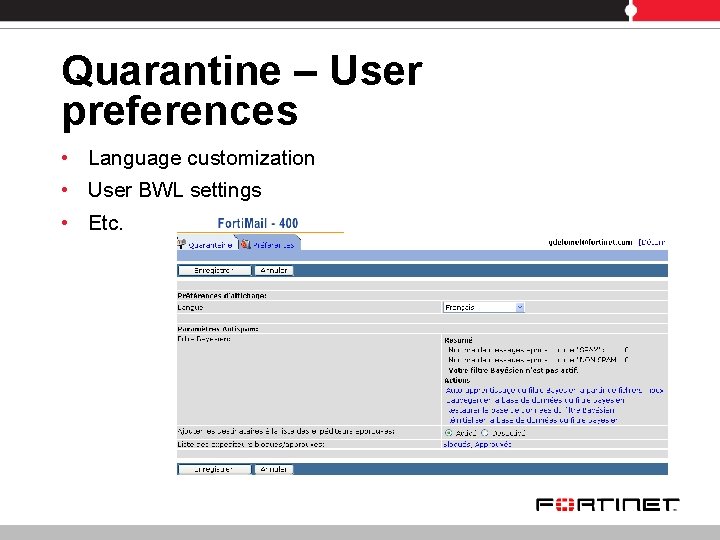
Quarantine – User preferences • Language customization • User BWL settings • Etc.

Agenda • • • Introducing Forti. Mail deployment scenarios Forti. Mail product line Differentiated services: policies and profiles Antispam techniques Virus detection Forti. Mail HA Email archiving Reporting

Antivirus check • Forti. Mail detects viruses and spyware embedded in SMTP email messages and removes them – Provides both Wildlist and Zoolist/legacy virus protection against more than 300, 000 viruses and variants – Leverage the award winning Fortinet Antivirus engine § ICSA certified • Forti. Mail inserts replacement messages to notify the recipient, or silently block infected email or warn sender of failed delivery • Automatic antivirus engine and signature files update • Do NOT charge per user mailbox

Agenda • • • Introducing Forti. Mail deployment scenarios Forti. Mail product line Differentiated services: policies and profiles Antispam techniques Virus detection Forti. Mail HA Email archiving Reporting

Forti. Mail clustering • Supported in transparent/gateway/server mode • Supports 2 HA modes • Config-only HA mode: – Up to 25 Forti. Mail units share a common configuration, but operate as separate Forti. Mail units – Usually implemented with external load sharing: § load-balancers, DNS round robin, etc.

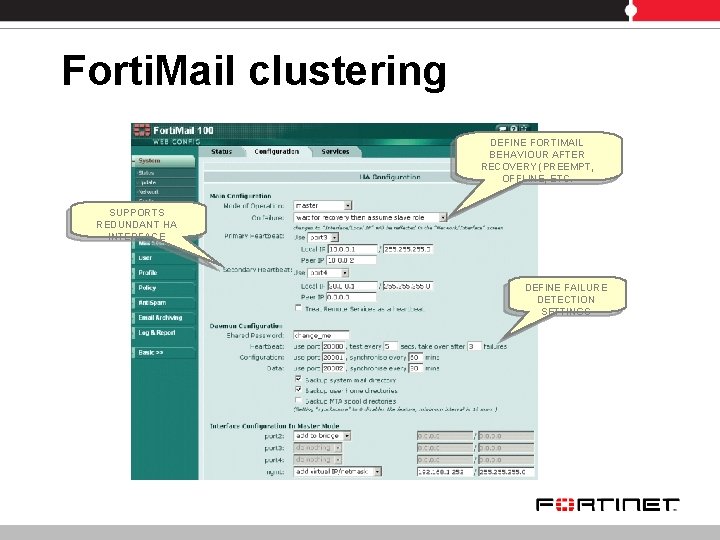
Forti. Mail clustering • HA Active-passive mode – Two Forti. Mail units provide failover protection – HA synchronization § Configuration synchronization – Except few parameters that should not be synchronized: Forti. Mail hostname, SNMP information, some HA settings § Mail data synchronization – Include and selectively synchronize: System mail directory, user home directories, and MTA spool directories – HA health check § Interface monitoring § Service monitoring (SMTP, POP 3, etc. ) – Supports redundant HA interfaces – Choose behaviour after recovery: preemption ON/OFF, offline state, etc.

Forti. Mail clustering DEFINE FORTIMAIL BEHAVIOUR AFTER RECOVERY (PREEMPT, OFFLINE, ETC. SUPPORTS REDUNDANT HA INTERFACE DEFINE FAILURE DETECTION SETTINGS

Agenda • • • Introducing Forti. Mail deployment scenarios Forti. Mail product line Differentiated services: policies and profiles Antispam techniques Virus detection Forti. Mail HA Email archiving Reporting

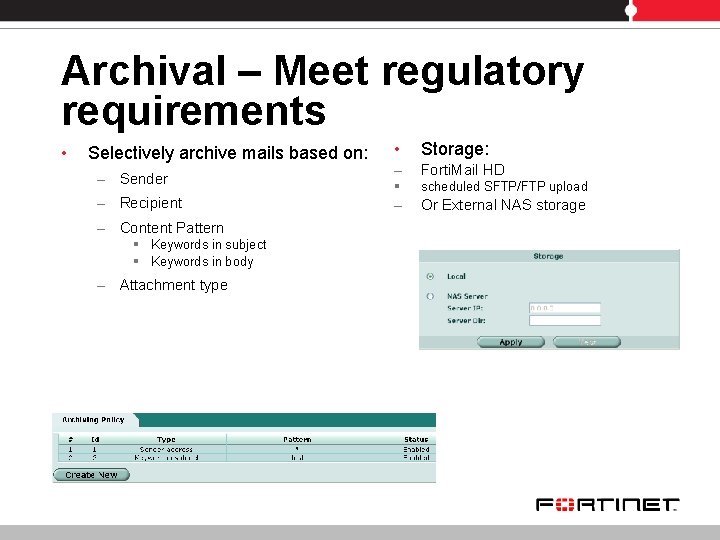
Archival – Meet regulatory requirements • Selectively archive mails based on: – Sender – Recipient – Content Pattern § Keywords in subject § Keywords in body – Attachment type • Storage: – Forti. Mail HD § scheduled SFTP/FTP upload – Or External NAS storage

Agenda • • • Introducing Forti. Mail deployment scenarios Forti. Mail product line Differentiated services: policies and profiles Antispam techniques Virus detection Forti. Mail HA Email archiving Management / Logging / Reporting

Logging • Logs – On device local logging – Syslog/Forti. Analyzer output • Alerts and resources usage – SNMP traps and MIB polling – CPU Usage, Memory Usage, Log Disk Usage, Mailbox Disk Usage, Deferred queue, Detected virus, Detected spam, etc.

Logs CHOOSE WHERE TO LOG

Logs SPECIFY THE EVENTS YOU WANT TO LOG • Antispam logs – sample:

Management • Easy management that answers SMB and High End need – Wizard option for fast and easy deployment • Configuration tasks – Through Intuitive GUI (basic and advanced modes) – Though CLI mode

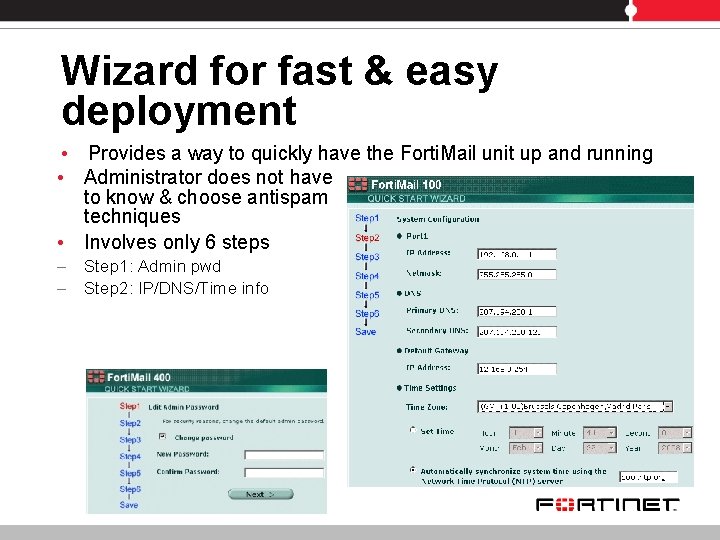
Wizard for fast & easy deployment • Provides a way to quickly have the Forti. Mail unit up and running • Administrator does not have to know & choose antispam techniques • Involves only 6 steps – Step 1: Admin pwd – Step 2: IP/DNS/Time info

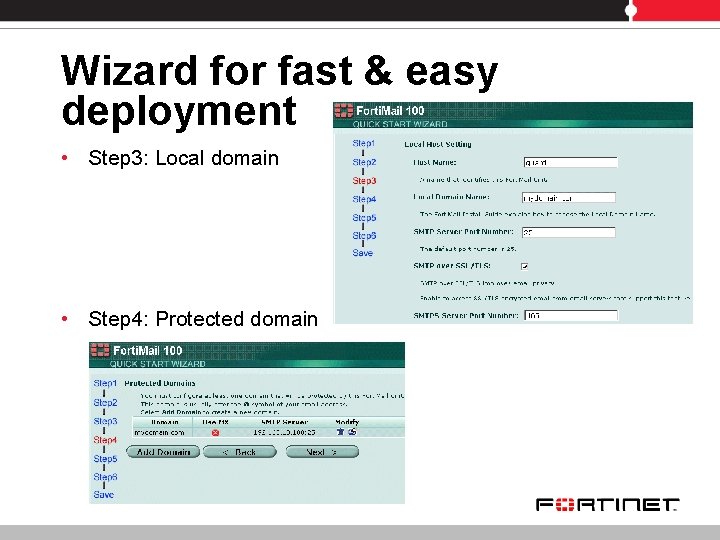
Wizard for fast & easy deployment • Step 3: Local domain • Step 4: Protected domain

Wizard for fast & easy deployment • Step 5: Incoming protection – Antispam level (high/medium/low) – Antivirus service ON/OFF • Step 6: Outgoing protection – Antispam level (high/medium/low) – Antivirus service ON/OFF – Access control for relay permission

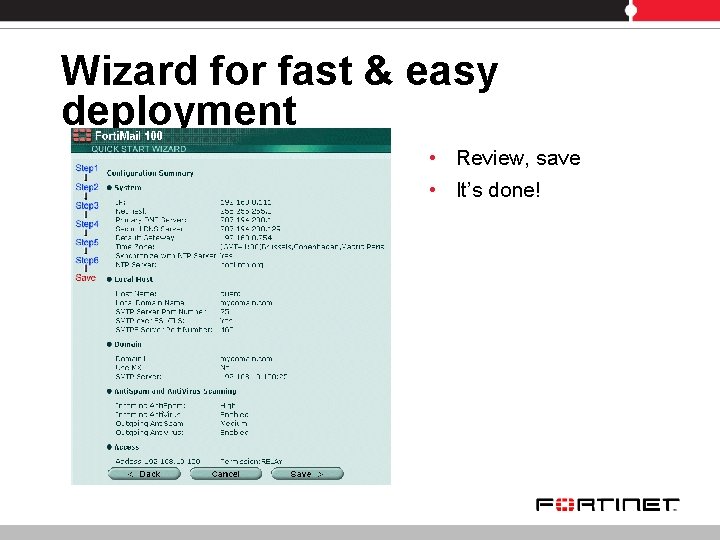
Wizard for fast & easy deployment • Review, save • It’s done!

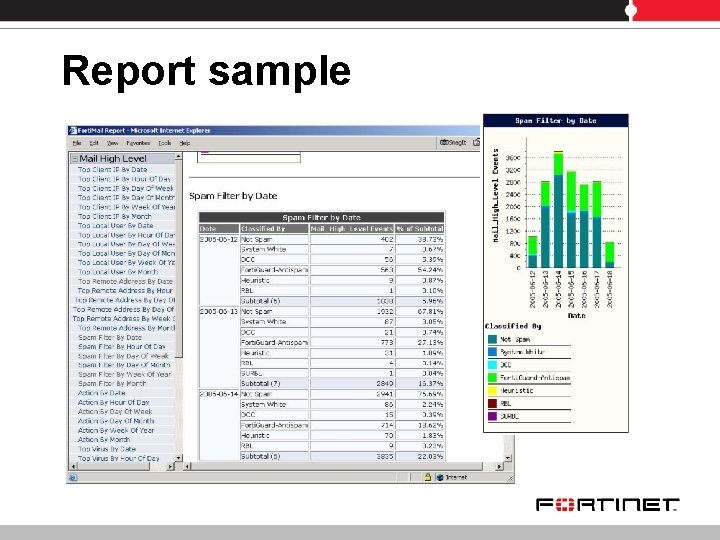
Reporting • Provide full visibility about the mail usage – Over 240 embedded HTML or PDF reports – Mail stats, virus stats, spam stats, etc. • The Forti. Mail unit comprehensive reporting with over 240 reports in nine categories. • Reports can be run : – on demand or scheduled – on a specific period of time – for all domains or a specific set of domains – for incoming or outgoing mail

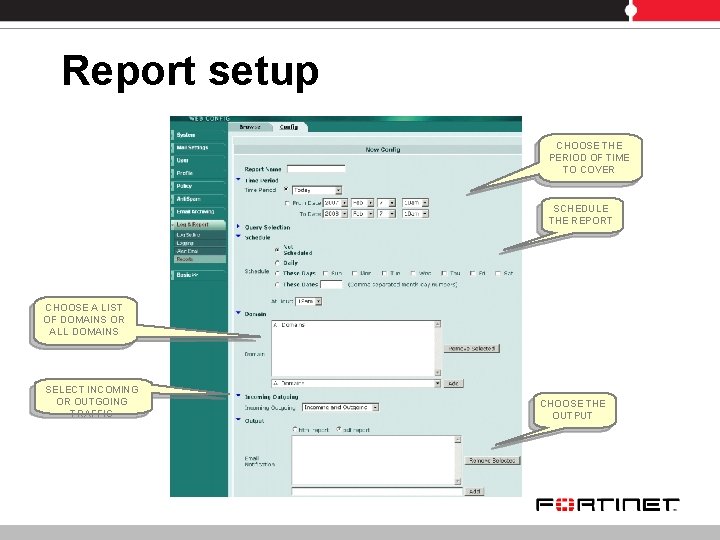
Report setup CHOOSE THE PERIOD OF TIME TO COVER SCHEDULE THE REPORT CHOOSE A LIST OF DOMAINS OR ALL DOMAINS SELECT INCOMING OR OUTGOING TRAFFIC CHOOSE THE OUTPUT

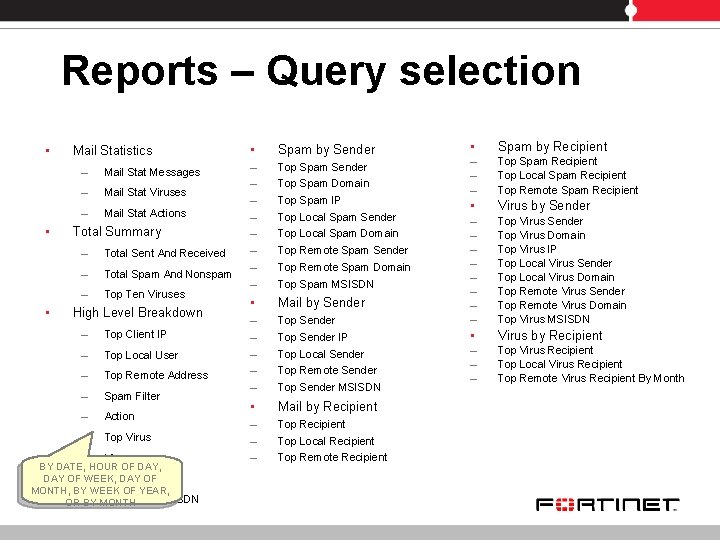
Reports – Query selection • • • Mail Statistics – Mail Stat Messages – Mail Stat Viruses – Mail Stat Actions Total Summary – Total Sent And Received – Total Spam And Nonspam – Top Ten Viruses High Level Breakdown – Top Client IP – Top Local User – Top Remote Address – Spam Filter – Action – Top Virus – Virus BY DATE, HOUR OF DAY, System User DAY OF –WEEK, DAY OF MONTH, BY WEEK OF YEAR, Top Client MSISDN OR – BY MONTH • Spam by Recipient – – – Top Spam Recipient Top Local Spam Recipient Top Remote Spam Recipient • Virus by Sender Top Sender – – – – Top Virus Sender Top Virus Domain Top Virus IP Top Local Virus Sender Top Local Virus Domain Top Remote Virus Sender Top Remote Virus Domain Top Virus MSISDN Top Sender IP • Virus by Recipient Top Local Sender – – – Top Virus Recipient Top Local Virus Recipient Top Remote Virus Recipient By Month • Spam by Sender – – – – Top Spam Sender • Mail by Sender – – – • Mail by Recipient – – – Top Recipient Top Spam Domain Top Spam IP Top Local Spam Sender Top Local Spam Domain Top Remote Spam Sender Top Remote Spam Domain Top Spam MSISDN Top Remote Sender Top Sender MSISDN Top Local Recipient Top Remote Recipient

Report sample

Forti. Mail key points Fit any deployment scenario and network requirement (explicit or transparent proxy, route or bridge packets, visible or unvisible in the headers, etc). No OEM agreement, 100% Fortinet technology, no user licences Support advanced HA with network and service check, mail data synchronization, etc. Supports outgoing spam filtering Includes extended reports and large quarantine server Administration that fits SMB, Enterprises and Service Providers

Thank you ! Questions ?