MT 311 Oct 2004 Java Application Development Tutorial












































- Slides: 58

MT 311 (Oct 2004) Java Application Development Tutorial 4 Java Security, Cryptography, Authentication, PKI, Digital Signature & SSL

Tutor Information l l Edmund Chiu (Group 4) Email: gianted@netvigator. com OR t 439934@ouhk. edu. hk Please begin your email subject with [MT 311] Webpage: http: //learn. ouhk. edu. hk/~t 439934

Security Issues in Java l When a computer is connected to a network, it is not enough to have physical security alone. – l Communication security is a concern when computers communicate across a network In Java applications, there are two main areas of security issues: – – System security – safety and stability of the computing environment against malicious applications (e. g. virus) Information security – the secrecy and integrity of data

Sandbox Model l In early days, Java use a basic security model called the sandbox model – – l Local applications are considered as trustable and are granted full access to the system Download applets are not trusted and could not use any local resources It is a quick solution related to downloaded applications at that time, but – – – has lots of shortcomings because you can either trust or not trust the entire application/applet Cannot prevent a local application downloaded from the Internet from accessing a sensitive file Even printing from an applet is impossible

Security Policy Model l In a security policy model, resource can be granted or denied different access independently – – For example, if the resource is a file, you can grant a “read”, “write”, “execute” and “delete” permission We can grant different types of permission to the following different resources also l l l Audio, AWT, Network, Property, Runtime and etc Details are given in the Java Documentation on Security To provide an even more flexible implementation, Java allows different policies to apply to different application, or even to different invocations of the same application.

Applet Security l Consider an Applet writing a file to your PC – l Click Here to view the Applet source code (Applet. Security. Test. java on course homepage) By default, Sandbox Model is used – Access denied. A security exception is shown in the applet

Applying Security Policy in Applet l You local PC needs to release the restriction by specifying a different policy grant { permission java. io. File. Permission "Applet. Security. Test. txt", "write"; }; – – Save the above text as a policy file named “policy. Allow. Write” in you current directory View your applet using applet viewer applying the policy appletviewer -J-Djava. security. policy=policy. Allow. Write Applet. Security. html

Security Policy l As in the previous example, you can see a policy is identified in the following format: permission <permission> <target> <action>; – – – l Permission type (java. io. File. Permission) The target source (Applet. Security. Test. java) The action (write) You can also specifying the permission for applets loaded from a URL specified by the code base grant code. Base http: //java. sun. com/- { permission java. io. File. Permission “<<ALL FILES>>”, “write”; }; grant code. Base http: //www. microsoft. com/- { permission java. io. File. Permission “<<ALL FILES>>”, “read”; };

Using the Policy Tool l To save the time and avoid from making mistakes that will lead to security vulnerabilities, Java provides a GUI tool policytool to manage the policies

Code Signing l We can grant a permission to applets from a particular URL to access our computer – l l URL can be hijacked or forged, how can we really know the applet file is from the exact party Java provides another layer of security called code signing To apply code signing, you need: – – Create a JAR file (Java Archive, which is Java’s mechanism for bundling multiple files) using jar tool (Details) Sign it using a Java tool jarsigner. You need a key pair generated by Java keytool to sign the JAR file (Details) jarsigner <jar_file> <key_file>

Code Signing II l The HTML code to read a jarred applet <applet code = Applet. Class. Name. class archive=“Jar. File. Naem. jar” width=XXX height=YYY> l When the runtime loads a JAR file, it verifies if the JAR file has been signed and determine if it can be trusted – – A signed JAR file authenticates the file owner and integrity of the signed files in the JAR archive Web browser can apply a standard policy to trust an applet if the applet is signed by a trusted authority

Java Archive (JAR) l What is in a JAR file? – – – Create by: jar cf <jar_file> <all_files> Execute by: java –jar my. JAR. jar Can also be viewed, extracted or even executed (Main-Class header is required in the Manifest file) After code signing, the JAR files includes the class files, a fingerprint of the jarred files, code signer’s credentials, expiry date, the manifest and other related information Fingerprint is an unique authentication token generated using a one-way hash algorithm – any alteration in code will generate a totally different fingerprint Manifest is the directory of the archive – listing the files, the signatures, and other information (like Main-Class)

Cryptography l The main objectives of cryptography are: – – Confidentiality – the information cannot be understood by others whom were not intended Integrity – the information cannot be altered in the transition between sender and intended receiver without being detected Non-repudiation – sender cannot deny his/her intention of sending/creating a message Authentication – the sender and receiver can confirm other’s identity and the origin/destination of the information

Secure Communication l The simplest form of secure communication – – – Sender and recipient agree on a shared key Communication is encrypted using the shared key Only the objective of confidentiality is achieved

Sending a Message Securely l Steps of sending messages achieving all four cryptography objectives – Encrypt the original message with sender’s secret key l – Create a message digest of the message l – Integrity – digest is unique to the message Encrypt the encrypted message and the message digest using the sender’s secret key l – Confidentiality and authentication – encryption done using sender’s secret key Non-repudiation – digest and message were encrypted together Encrypt the encrypted message, message digest and the sender’s signature with the recipient's secret key l Authentication and confidentiality – only recipient can decrypt the message

Receiving a Message Securely l Steps of receiving messages in a secured way – – Decrypt the package with the recipient’s key Decrypt the pieces with the sender’s key Compute the message digest to verify the integrity of the message Decrypt the encrypted message using the sender’s key

Problem in a Secret-Key Algorithm l l l We require a number of secret keys, one for each step The sender and recipient need to agree on the secret keys used in steps 1 and 2. The sender and recipient need to give their secret keys to each other – – – If sender uses the same key for all recipients, the key in not secret then. If sender uses different keys for each recipient, key management is complex Key distribution is difficult, especially when the two parties are previously unknown

Public-Key Algorithm l Each party has a pair of keys – – – l public key – made public to all parties you want to communicate with private key – kept confidential The key pair is generated using mathematical properties of prime number. Each key pair is unique It is difficult to compute the private key from the public key The key pair has an interesting property – – Decrypt (Encrypt(message, private. Key), public. Key) = message Decrypt (Encrypt(message, public. Key), private. Key) = message

Public-Key Algorithm (cont’d) l How public-key algorithm achieve the objectives – – – l Messages in public-key algorithm – – l Confidentiality and integrity can be achieved when used with signatures Non-refutable – the private key is secret and there is only one right combination of public/private keys Authentication – a message that A can read will be encrypted using A’s public key, only A, who have the respective private key can read the message Sender: Encrypt(msg, Send. Priv. Key), Rec. Pub. Key) Recipient: Decrypt(msg, Rec. Pri. Key), Send. Pub. Key) Key distribution problem is solved because public key can be made available publicly.

Symmetric Algorithm (Shared Key) l Public key algorithm uses two different keys for encryption and decryption – we call it an asymmetric algorithm – – l Public key algorithm requires a lot of computations In practical, public key algorithm is used to establish the identities of the two parties and exchange a session key Symmetric algorithm (shared key algorithm) use the same key for encryption and decryption – – Decrypt (Encrypt (message, key) = message The session key agreed in the above step is used to encrypt and decrypt the communication after the initial handshake

Java Cryptography Extension (JCE) l JCE provides cryptographic functions, include – – l Key generation Encryption/decryption Message digest Certificates and more… The standard APIs are defined, but the implementation can be substituted – – – JDK 1. 4. 2 includes some service implementation provided by Suns You can still easily install other cryptography providers implementation (like IBM’s) to the Java Security API and the implementation should still work Advantages: Different algorithm can be used – some may only trust certain cryptographic implementation

Some commonly used Cryptographic Services l l l l l Secure. Random – SHA 1 PRNG Key. Generator – DES, Triple. DES, Blowfish Key. Pair. Generator – DSA, RSA, DH Message. Digest – SHA 1, MD 5 MAC – Hmac. MD 5, Hmac. SHA 1 Signature – SHA 1 with. DSA, SHA 1 With. RSA Certificate. Factory – X 509 Cipher – DES, Triple. DES, Blowfish Key. Agreement – DH List can be retrieved through Provider class in java. security package (see List. CSPs. java for details)

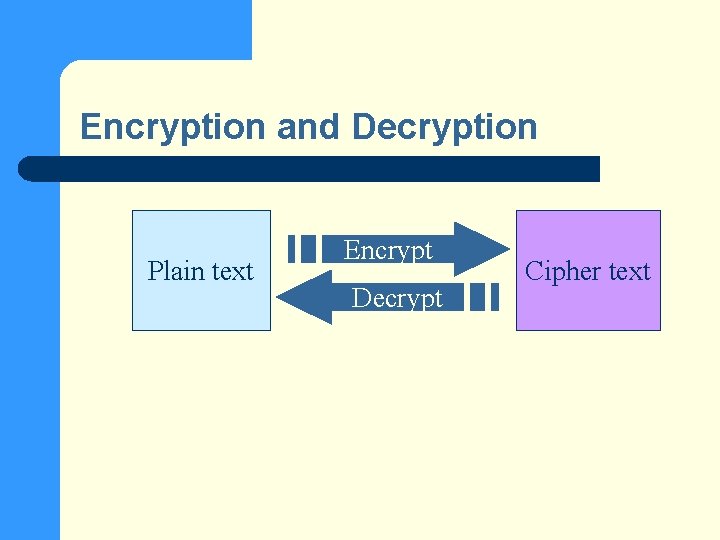
Encryption and Decryption Plain text Encrypt Decrypt Cipher text

Encryption Strength l Encryption algorithms are measured by their strength – – Example: 64 -bit SSL and 128 bit-SSL Key lengths provide a basic measure of strength when the same protocol is used l l – 128 -bit SSL is 264 stronger than 64 -bit SSL Actually, the strength also depends on other factor, e. g. , randomness of keys Key lengths are not comparable when different algorithm is used l In RSA, when not all possible keys are valid, typical RSA keys are 1024 -bit or even 2048 -bit.

Secret-Key Encryption and Decryption l l Most encryption and encryption are based on secret key algorithm DES (Data Encryption Standard) was the de facto standard until recently – – – l 56 -bit key length Possible to break a DES encryption by searching all possible keys – in less than 23 hours using 100, 000 computers in 1999 Now, Triple-DES is used by running DES three times using three different key Newer standard used in US government is AES (Advanced Encryption Standard) – More extensible algorithm whose strength can be extended by using different key lengths

Using JCE to Encrypt/Decrypt a Message l l Java cryptographic APIs are defined in java. security and javax. crypto pacakges For a basic encryption, we need a secret key and a cryptographic algorithm – – l javax. crypto. Secret. Key javax. crypto. Cipher To create a Secret. Key, – – we first need a Key. Spec (e. g, javax. crypto. spec. DESKey. Spec), which defines the attributes of the cryptographic key Key. Spec is then passed to a Secret. Key. Factory in which the actual Secret. Key object is created

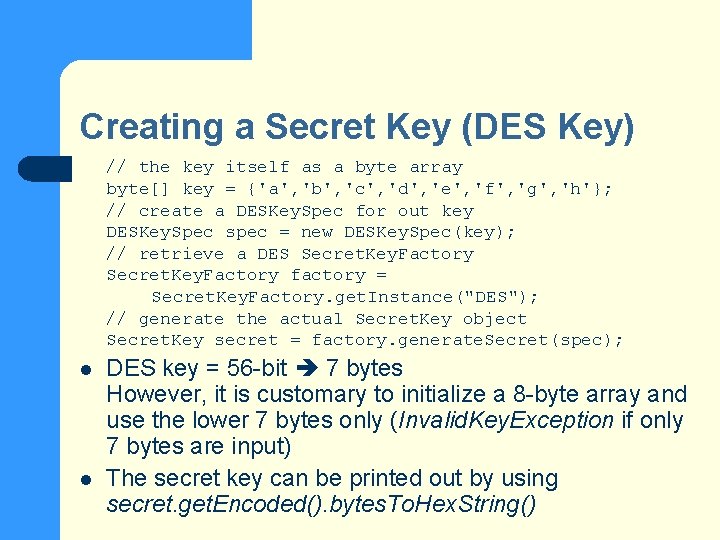
Creating a Secret Key (DES Key) // the key itself as a byte array byte[] key = {'a', 'b', 'c', 'd', 'e', 'f', 'g', 'h'}; // create a DESKey. Spec for out key DESKey. Spec spec = new DESKey. Spec(key); // retrieve a DES Secret. Key. Factory factory = Secret. Key. Factory. get. Instance("DES"); // generate the actual Secret. Key object Secret. Key secret = factory. generate. Secret(spec); l l DES key = 56 -bit 7 bytes However, it is customary to initialize a 8 -byte array and use the lower 7 bytes only (Invalid. Key. Exception if only 7 bytes are input) The secret key can be printed out by using secret. get. Encoded(). bytes. To. Hex. String()

Creating a Cipher l To create a cipher, you need to specify a right provider and call the get. Instance static method from the Cipher class – l Then, you can initialize the Cipher object to either encrypt or decrypt a message (reinitialize will clear all previous data) – – l c. update(buffer); // buffer is a byte array To retrieve the encrypted/decrypted result, you invoke the do. Final method – l c. init(Cipher. ENCRYPT_MODE, secret); secret refers to the key you obtained in the secret key factory Now, you can call the update method to encrypt/decrypt the message (repeatedly call to process multi-parts) – l Cipher c = Cipher. get. Instance("DES"); Byte[] is. Encrypted = c. do. Final(); Please refer to API specification for other forms of update/do. Final

Encryption and Decryption Example DESEncrypt. java l Main method – l encrypt method – – l Open a file, encrypt the contents and write the encrypted data in another file Create a cipher and initialize it using the secret key in the input parameter Encrypt the input byte array and return the encrypted result make. DESKey method – Create and return a DES cryptographic key according to the given byte array DESDecrypt. java l Exactly the same as DESEncrypt. java except the Cipher is initialized to decrypt instead of encrypt

Encrypted Echo Server/Client l The Echo server/client can have a more secured communication by adding DES encryption/decryption – l Messages cannot be processed if the key was wrongly typed See: – – DESEcho. Server. java DESEcho. Client. java

AES Encryption and Decryption l In AES, apart from creating the Key. Spec, we need to also create a Iv. Parameter. Spec for the initialization vector – l Example: Iv. Parameter. Spec params = new Iv. Parameter. Spec(i. VBytes); We call Cipher's init method with the mode (encrypt/decrypt), key. Spec and the parameter. Spec: – Example: cipher. init(Cipher. ENCRYPT_MODE, key, params);

Message Digest l l Message digests is used to guarantee the integrity of a message, is also known as a fingerprint or a hash. A message digest is generated using a mathematical transformation called a hash function – l The hash function used to produce message digest should have the following properties: – – l The resultant message digest is typically fixed length Extremely difficult to produce a same message digest from two different messages – the hash must be one-to-one Extremely difficult to produce the original message from a given message digest – the hash must be irreversible The most popular algorithms are SHA 1 and MD 5.

MD 5 Algorithm l l l MD 5 algorithm takes in a message of arbitrary length and produces a 128 -bit or 16 -byte message digest MD 5 is popular because it is one of the faster message digest algorithm MD 5 ensure a download file has not tampered by providing a MD 5 checksum – l After the file is downloaded, MD 5 checksum is generated and checked against the original one In this way, two parties can know the secret without transferring the secret itself – Example: a password's hash is transferred to a homepage and the hash is checked with the hash stored in the web server

Message Digest in Java l l Message digests are encapsulated in the class java. security. Message. Digest Like Cipher, we create a Message. Digest using get. Instance method Message. Digest md = Message. Digest. get. Instance("MD 5"); l Data can then feed in to the Message. Digest object using the update method md. update(buffer); // buffer is a byte array l The hash is retrieved using the digest method md. digest(); l See the sample code in MD 5. java

SHA 1 and Keyed MD 5 l l SHA 1 is similar to MD 5 but it produces a 160 -bit message digest. Going back to the previous password handling technique – l Man-in-the-middle can still impersonate the user without knowing the actual password To prevent the man-in-the-middle attack, we modify the protocol to a challenge-and-response authentication – – – Server sends the client a random string The client computes the MD 5 hash of the random string using the password as a secret key Previously computed hash cannot be reused because the string is randomly generated each time

Message Authentication Code (MAC) l MAC (message authentication code) is similar to a message digest, but with the addition of a secret key. – – l In addition to integrity, MAC also ensures the authenticity of the message digest MAC still has the same key distribution problem To generate a MD 5 MAC, we first create the necessary key from javax. crypto. Key. Generator kg = Key. Generator. get. Instance("Hmac. MD 5"); Secret. Key sk = kg. generate. Key(); l MAC object is then created and initialized using the key Mac mac = Mac. get. Instance("Hmac. MD 5"); mac. init(sk); l Data is then feed into the MAC object and the resultant code can be retrieved using do. Final mac. update(buffer); // buffer is a byte array byte[] result = mac. do. Final();

Public-Key Infrastructure (PKI) l Public-key algorithm solve the key distribution issue – – l Public key is distributed widely Anyone can send you a message that only you can read If message was also encrypted with the sender's private key, you can also verify the identity of the sender But, how do we know a particular public key really belongs to a particular person? Instead of distributing the public keys in PKI, the public keys are distributed as certificates – – Certificates should contain enough info to authenticate the owner and associate the owner of a particular public key Most popular standards for certificates include X. 509 and PGP

Certificate Authorities l How do you know the certificate is authentic – – It needs to be signed by a trusted party called the Certificate Authority (CA) using CA's private key – it validate the integrity and authenticity of the cert. To verify a certificate, we check the signature using CA's public key, obtainable from CA's root certificate (self-signed) l l CA must guarantee its own private key has not been compromised All certificate related classes in Java are in java. security. cert package – – java. security. cert. Certificate java. security. cert. X 509 Certificate

Keys Management l l Keys and certificates can be stored in binary or text files, and in Java, a special format called key store. To create a key store and generate a certificate, you can invoke keytool as: – – keytool –keystore my. Key. Store –gen. Key –alias my. Key Password is required for the key store You will also be prompted for the information necessary for the X. 509 certificate

Certificates Management l The certificate created by the recent step can be exported by calling: – – l For binary file export: keytool -keystore my. Key. Store -storepass <passwd> -alias <my. Key> -export –file <file> For text format export: keytool -keystore my. Key. Store -storepass <passwd> -alias <my. Key> -export –rfc –file <file> The certificates generated by keytool are selfsigned

Using Certificate in Java l Import a certificate from a file File. Input. Stream is = new File. Input. Stream(file); Certificate. Factory cf = Certificate. Factory. get. Instance("X. 509"); Certificate cert = cf. generate. Certificate(is);

Information within the Certificate l Information within a cert is abstracted as Principle – – l Subject is retrieved by: Principal p = cert. get. Subject. DN(); // p. get. Name() will return the subject Issuer is retrieved by: Principal p = cert. get. Issuer. DN(); // p. get. Name() will return the issuer name See View. Cert. java

Verifying the Certificate l To verify the certificate – – l Possible exceptions in a certificate – – – l Get the public key from the cert. (normally from CA's cert): Public. Key key = cert. get. Public. Key(); Verify the certificate using the public key cert. verify(key); // give out exceptions if verification fails No. Such. Algorithm. Exception Invalid. Key. Exception No. Such. Provider. Exception Signature. Exception Certificate. Exception See View. Cert 2. java

Other Certificate Issues l Trust is transitive in most PKI – – l Certificate can be chained Once you validate a certificate, you need to validate all intermediate certificates Revocation – Certificates that are no longer valid is to be put in the certificate revocation lists

Comparing Secret-Key and Public-Key Algorithm l l l Secret-key are much faster than public-key Public key requires certificate authorities as a trusted third party Secret-key requires pre-agreement on keys and key distribution using public key is easier (using certificates)

Digital Signature l Secret-key MAC key distribution problem revisit – – – Can be solved by using private key to generate MAC and use public key to verify it – too slow Hash the message and sign using our private key, the process is called digital signing Digital signature verifies the identity and integrity of the message

Digital Signature in Java l In Java, java. security. Signature contains the function used in digital signing – l Key pair is first generated – l Key. Pair. Generator kpg = new Key. Pair. Generator. get. Instance("DSA"); Then, initialize the key generator with the desired length – l The most popular algorithm used is Digital Signature Algorithm (DSA) kpg. intialize(1024, new Secure. Random()); The key pair can be generated according to followings – – – Key. Pair keypair = kpg. generate. Key. Pair(); DSAPublic. Key public = (DSAPublic. Key) keypair. get. Public()); DSAPrivate. Key private = (DSAPrivate. Key) keypair. get. Private());

Digital Signature in Java (cont'd) l The signing process Signature sign = Signature. get. Instance("DSA"); sign. init. Sign(private. Key); sign. update(buffer); return sign(); // signature is created l The verifying process Signature sign = Signature. get. Instance("DSA"); sign. init. Verify(private. Key); sign. update(buffer); return sign. verify();

Other Issues on Digital Signature l l l A DSA algorithm requires a key of at least 1024 bits and the resultant signature is 46 -bytes long Though we can create a DSA for the entire message, it works very slowly. Thus, it is typical we create a hash for the message first, and use DSA to sign the hash only

Before Starting SSL l Special Notes: Please ignore the Installation Notes in your Course Materials if you use JDK 1. 4. x. It is for previous versions only.

Secure Socket Layer (SSL) l l SSL is the de facto standard for securing communication on the Internet SSL uses a combination of public key algorithm and symmetric key algorithms to authenticate the parties and secure the communication – – – Public key is nice but slow and symmetric key is fast but key distribution is a headache When SSL session is started, the tow parties use a public key mechanism to authenticate each other Then, they exchange a session key and is used in a symmetric algorithm to encrypt and decrypt the communication

HTTPS Connection to a Website l You can connect a URL with https (in fact invoking SSL communication) – l URLConnection url. Conn = url. open. Connection(); You can test if you can make a HTTPS connection using the given example (SSLTest. java): – – java SSLTest <host> Java –Djavax. net. debug=ssl SSLTest <host>

SSL in Socket Programming l SSL can write socket programs similar to normal socket programs – – Instead of Socket and Server. Socket, SSL uses SSLSocket and SSLServer. Socket However, SSL Sockets are constructed using the get. Default method in SSLSocket. Factory (unless you have other SSL provider) After obtaining a SSLSocket. Factory (casting the Socket. Factory obtained above), you can use the create. Socket method to create an SSLSocket You need to cast the obtained Socket back to SSLSocket. Factory ssl. Socket. Factory = (SSLSocket. Factory) SSLSocket. Factory. get. Default(); SSLSocket ssl. Socket = (SSLSocket) ssl. Socket. Factory. create. Socket(server, port);

SSL in Socket Programming (cont'd) l SSLServer. Socket can be created in a similar method as in SSLSocket First, we retrieve a SSLServer. Socket. Factory using get. Default method in the class – Casting back the obtained Server. Socket. Factory to SSLServer. Socket. Factory, we create an SSLServer. Socket using the create. Server. Socket method SSLServer. Socket. Factory ssl. SSFactory = (SSLServer. Socket. Factory) SSLServer. Socket. Factory. get. Factory(); SSLServer. Socket ssl. SSocket = (SSLServer. Socket) ssl. SSFactory. create. Server. Socket(port); SSLSocket ssl. Socket = (SSLSocket) ssl. SSocket. accept(); –

SSL Implementation l SSL protocol only defines the basic mechanisms for handshaking and data exchange – l The public-key and/or secret-key algorithms are not defined The secret keys, key length and the encryption algorithm are collectively called cipher suites – You can retrieve the default and supported cipher suites from SSLSocket. Factory and SSLServer. Socket. Factory using the following methods: String[] get. Default. Cipher. Suites(); String[] get. Supported. Cipher. Suites();

SSL Communication l Step 1 is to authenticate the two parties – – l Then, the two parties agree on the cipher to use – l Involves certificate checking However, SSLSocket and SSLServer. Socket has done all checking for you Cipher suites can be retrieved using methods in SSLSocket and SSLServer. Socket Other than the above, SSLSocket and SSLServer. Socket are the same as Socket and Server. Socket

SSL Echo Server/Client l l In order to run the given SSL echo server and client, we need to provide the necessary certificates In this example, we create a keystore using keytool – l keytool –keystore <file> -genkey –alias <key. Name> In a production environment, CA will issue the server certificate and the client will have the lists of root certs and other certs it trusts.

SSL Echo Server/Client l In the server side, we specify the server certificate to use by – l java –Djavax. net. ssl. key. Store=<cert file> -Djavax. net. ssl. key. Store. Password=<passwd> SSLEcho. Server In the client side, we specify a key store for certificates that the clients trust – java –Djavax. net. ssl. trust. Store=<trusted cert> -Djavax. net. ssl. trust. Store. Password=<passwd> SSLEcho. Client