CSC 311 CHAPTER TEN CONNECTING NETWORKS CSC 311

















- Slides: 46

CSC 311 CHAPTER TEN CONNECTING NETWORKS

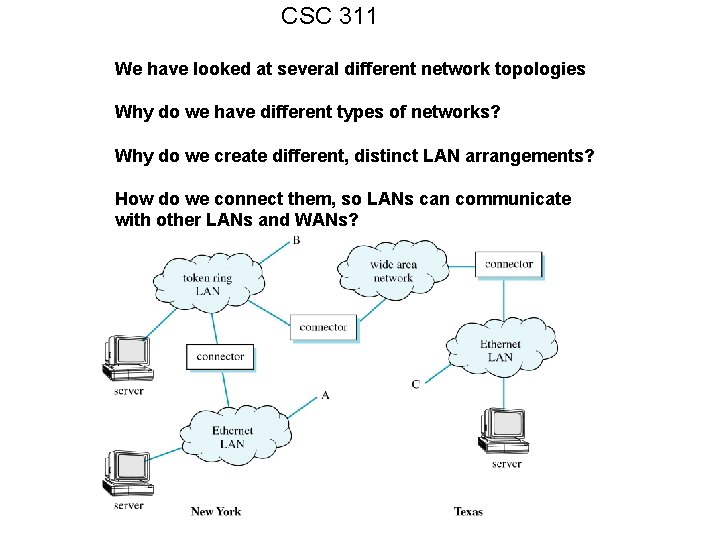
CSC 311 We have looked at several different network topologies Why do we have different types of networks? Why do we create different, distinct LAN arrangements? How do we connect them, so LANs can communicate with other LANs and WANs?

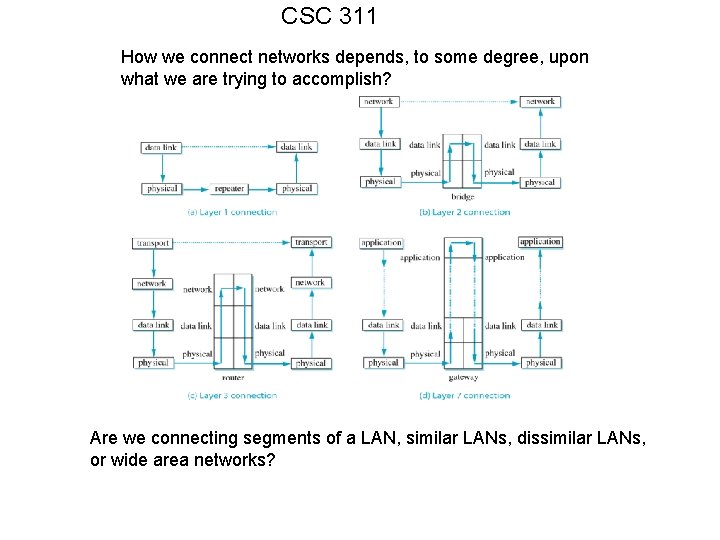
CSC 311 How we connect networks depends, to some degree, upon what we are trying to accomplish? Are we connecting segments of a LAN, similar LANs, dissimilar LANs, or wide area networks?

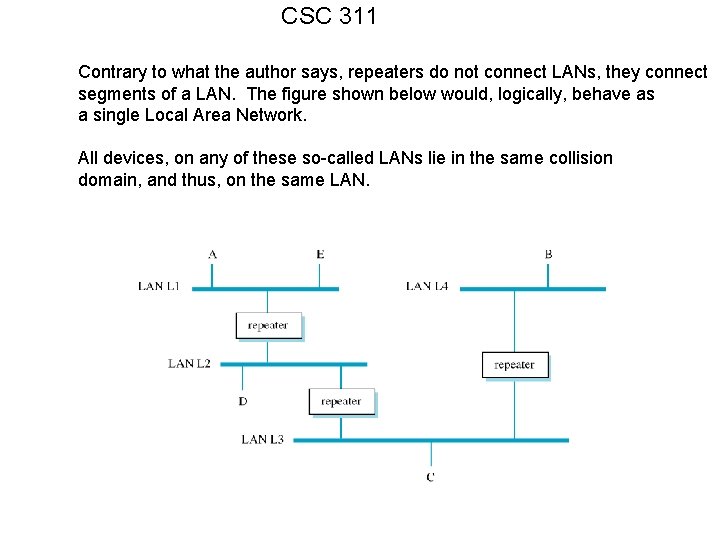
CSC 311 Contrary to what the author says, repeaters do not connect LANs, they connect segments of a LAN. The figure shown below would, logically, behave as a single Local Area Network. All devices, on any of these so-called LANs lie in the same collision domain, and thus, on the same LAN.

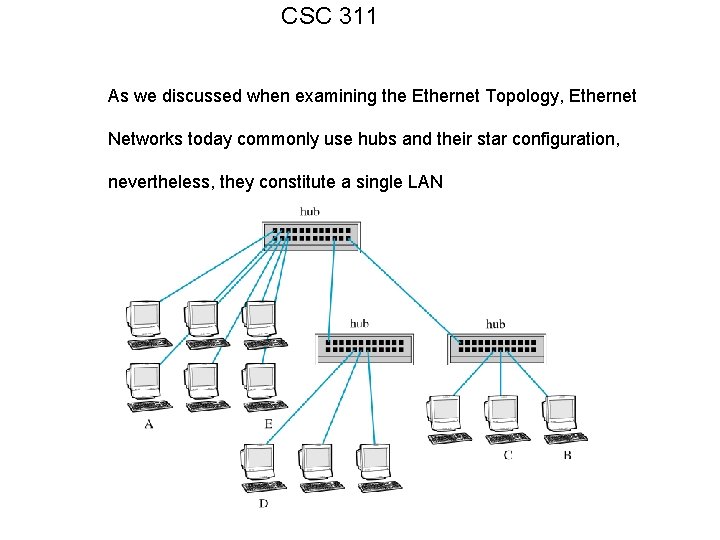
CSC 311 As we discussed when examining the Ethernet Topology, Ethernet Networks today commonly use hubs and their star configuration, nevertheless, they constitute a single LAN

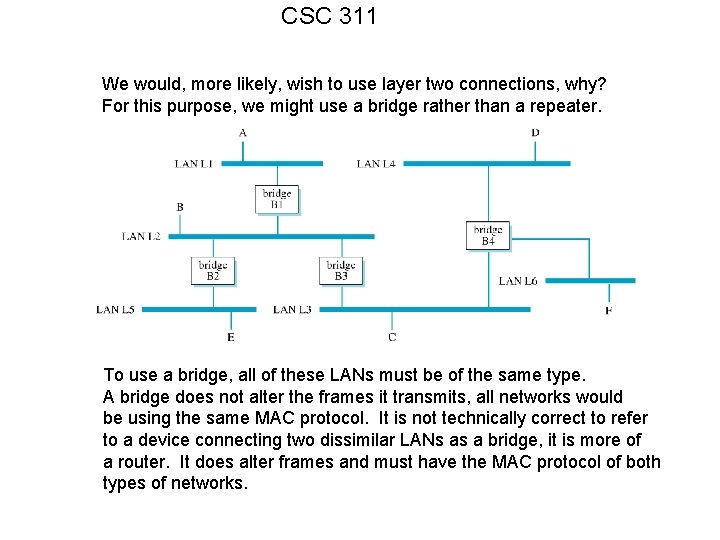
CSC 311 We would, more likely, wish to use layer two connections, why? For this purpose, we might use a bridge rather than a repeater. To use a bridge, all of these LANs must be of the same type. A bridge does not alter the frames it transmits, all networks would be using the same MAC protocol. It is not technically correct to refer to a device connecting two dissimilar LANs as a bridge, it is more of a router. It does alter frames and must have the MAC protocol of both types of networks.

CSC 311 How does a bridge know when, or where, to forward a particular frame, or whether it should be forwarded at all? Next slide…. Bridges use routing tables, these can be installed on the bridge by the systems manager or it can be a transparent bridge that will “learn” its routing table based on the traffic. following slide…

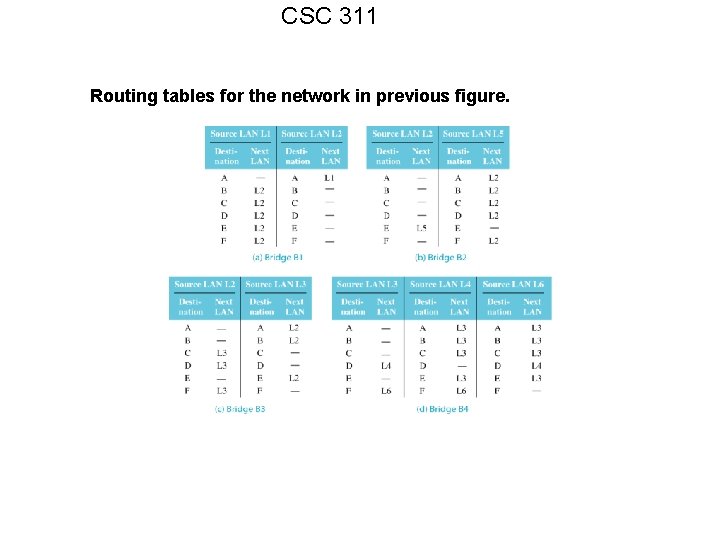
CSC 311 Routing tables for the network in previous figure.

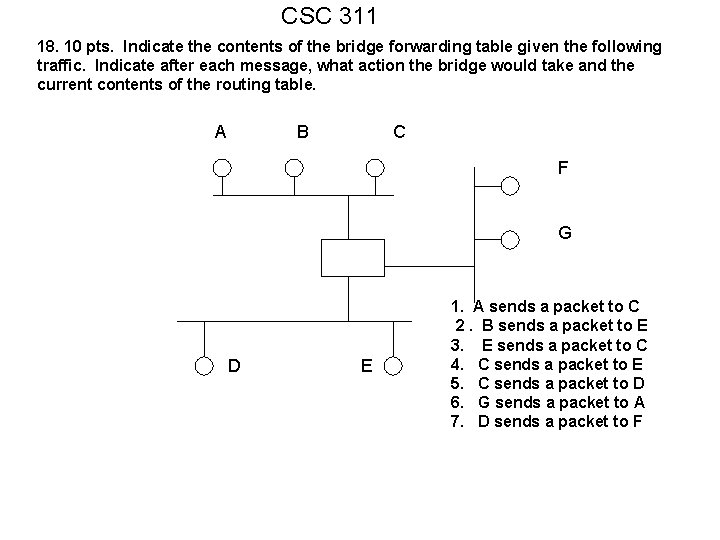
CSC 311 18. 10 pts. Indicate the contents of the bridge forwarding table given the following traffic. Indicate after each message, what action the bridge would take and the current contents of the routing table. A B C F G D E 1. A sends a packet to C 2. B sends a packet to E 3. E sends a packet to C 4. C sends a packet to E 5. C sends a packet to D 6. G sends a packet to A 7. D sends a packet to F

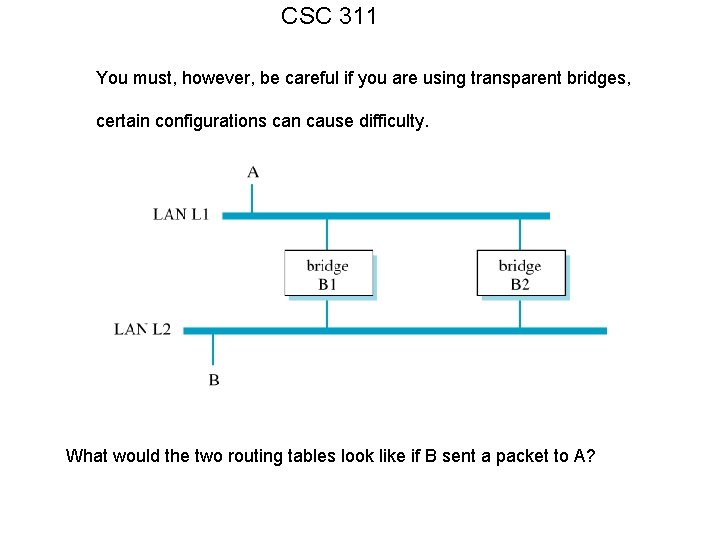
CSC 311 You must, however, be careful if you are using transparent bridges, certain configurations can cause difficulty. What would the two routing tables look like if B sent a packet to A?

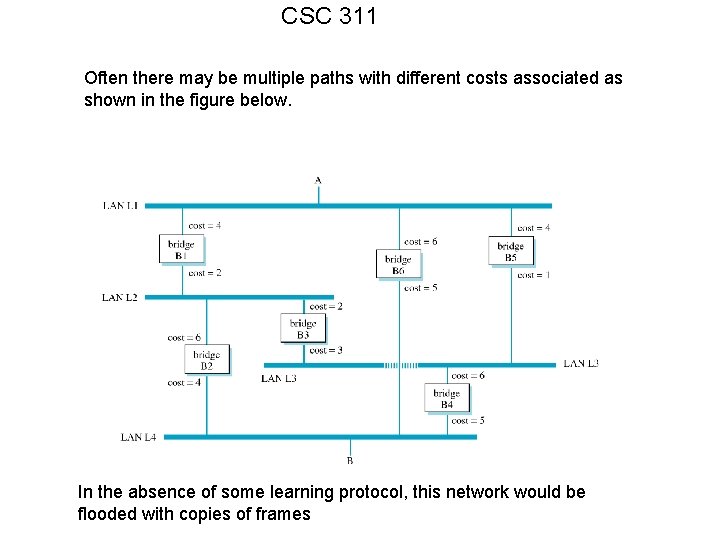
CSC 311 Often there may be multiple paths with different costs associated as shown in the figure below. In the absence of some learning protocol, this network would be flooded with copies of frames

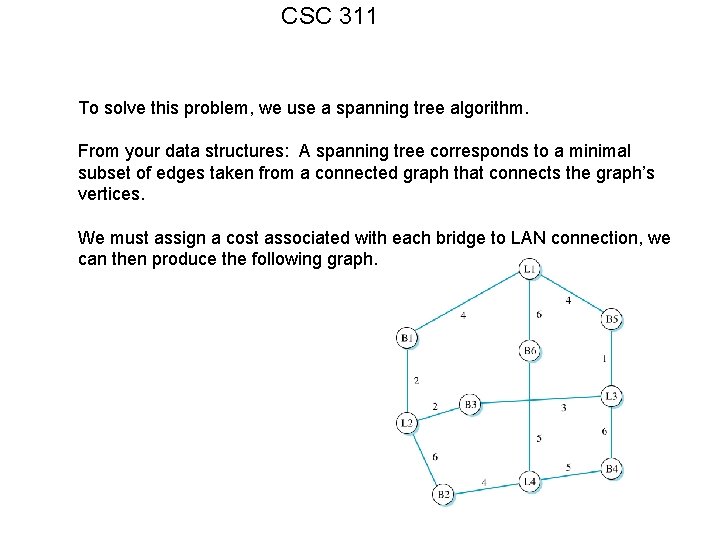
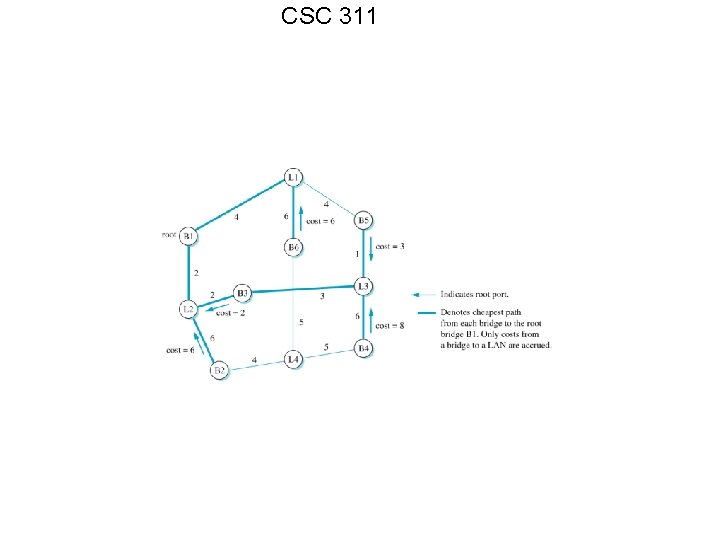
CSC 311 To solve this problem, we use a spanning tree algorithm. From your data structures: A spanning tree corresponds to a minimal subset of edges taken from a connected graph that connects the graph’s vertices. We must assign a cost associated with each bridge to LAN connection, we can then produce the following graph.

CSC 311

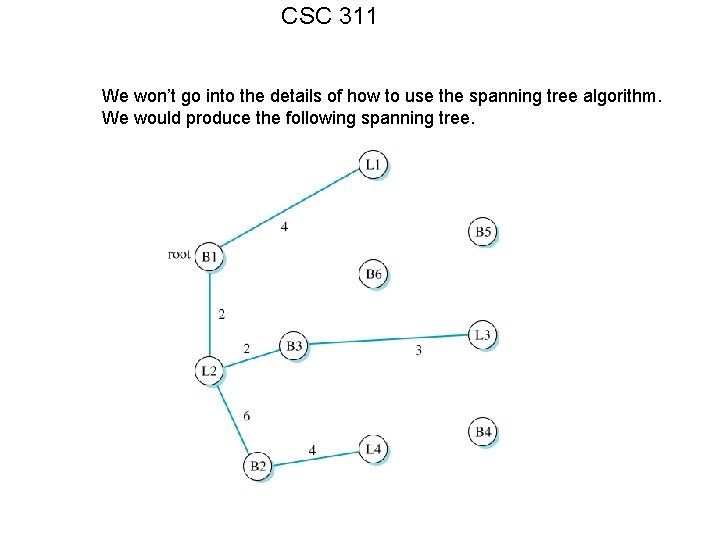
CSC 311 We won’t go into the details of how to use the spanning tree algorithm. We would produce the following spanning tree.

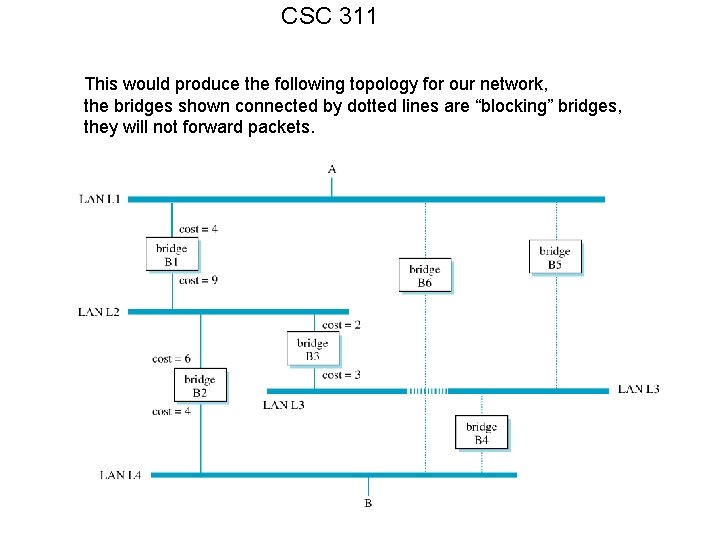
CSC 311 This would produce the following topology for our network, the bridges shown connected by dotted lines are “blocking” bridges, they will not forward packets.

CSC 311 We have discussed two routing strategies for bridges, namely: Routing tables loaded into each bridge by the system administrator FIXED ROUTING Transparent bridges that “learn” the routes ADAPTIVE ROUTING, ROUTE LEARNING, ETC. A third method is SOURCE ROUTING: The source specifies the route to the destination, routing info is included in the packet.

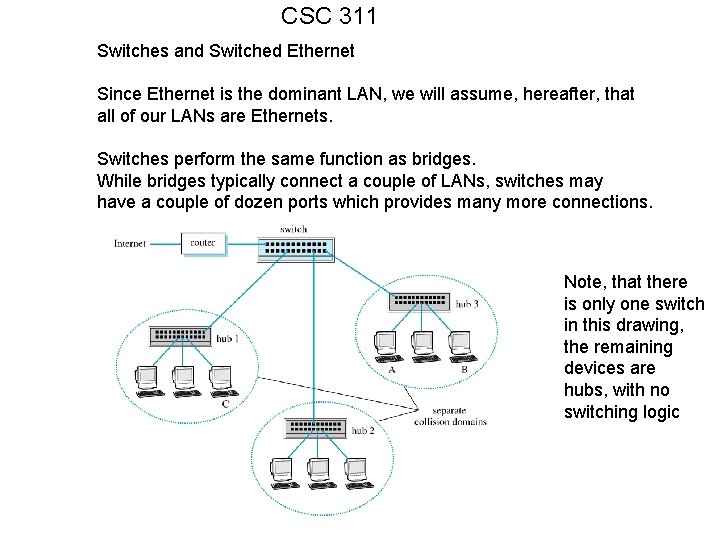
CSC 311 Switches and Switched Ethernet Since Ethernet is the dominant LAN, we will assume, hereafter, that all of our LANs are Ethernets. Switches perform the same function as bridges. While bridges typically connect a couple of LANs, switches may have a couple of dozen ports which provides many more connections. Note, that there is only one switch in this drawing, the remaining devices are hubs, with no switching logic

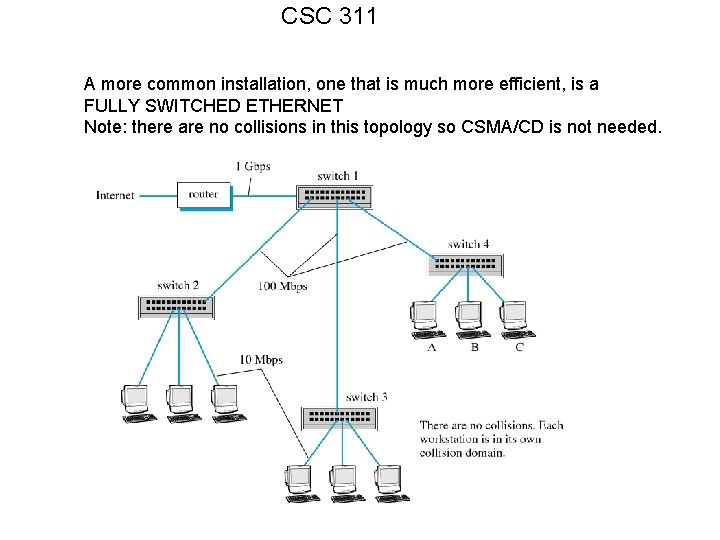
CSC 311 A more common installation, one that is much more efficient, is a FULLY SWITCHED ETHERNET Note: there are no collisions in this topology so CSMA/CD is not needed.

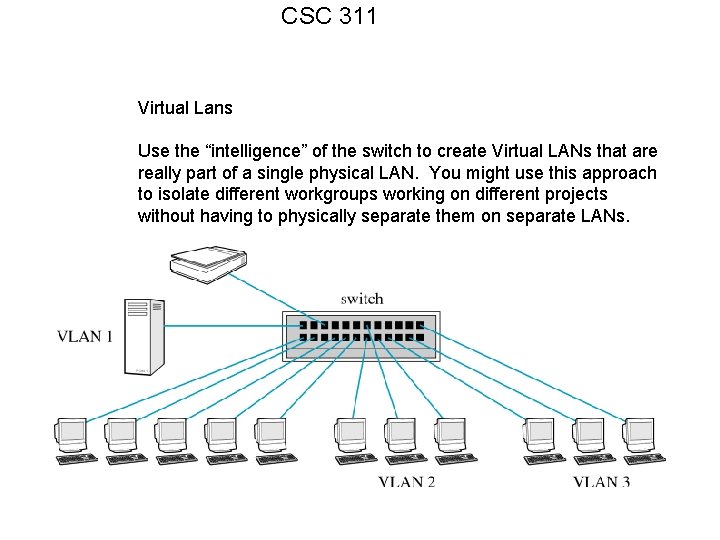
CSC 311 Virtual Lans Use the “intelligence” of the switch to create Virtual LANs that are really part of a single physical LAN. You might use this approach to isolate different workgroups working on different projects without having to physically separate them on separate LANs.

CSC 311 Layer Three Connections LANs and the layer 1 and 2 connections typically cover small geographic areas Wide Area Networks (WAN) span the globe and need more sophisticated techniques Much like the highway system, internets or the Internet provide multiple paths from one point in the Internet to another. We need a technique to select the best among these many possibilities. In the highway example, what do you do if a bridge is out? Find an alternate route. Networks are frequently faced with the same problem when one of the nodes in the network fails or becomes congested.

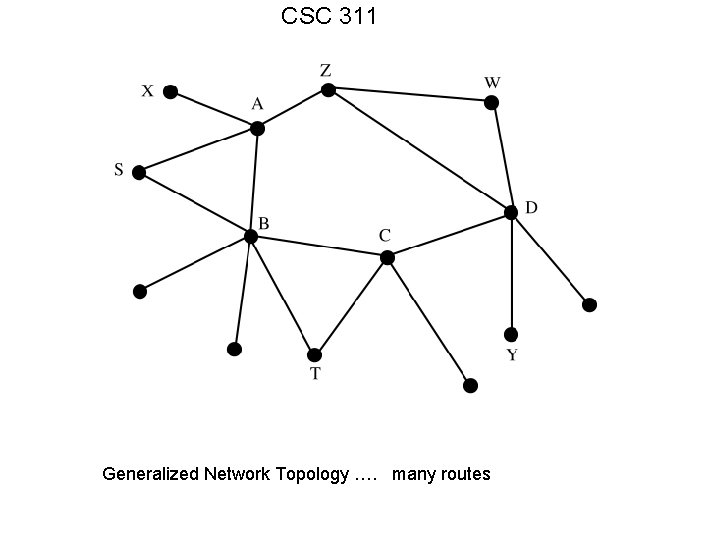
CSC 311 Generalized Network Topology …. many routes

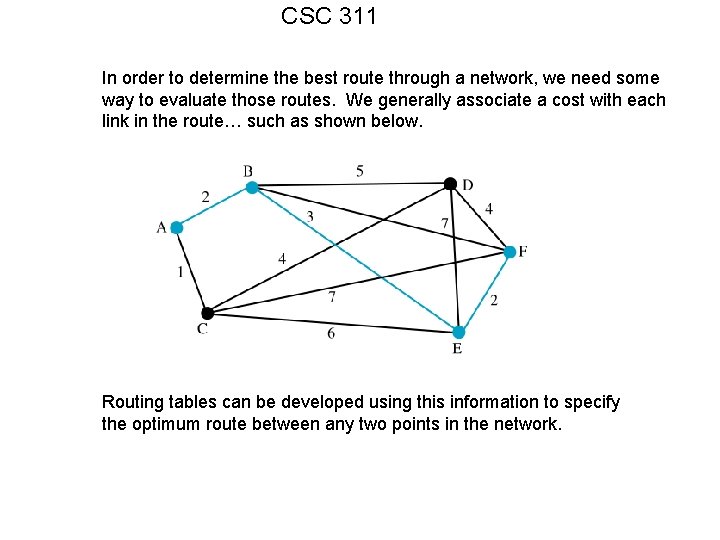
CSC 311 In order to determine the best route through a network, we need some way to evaluate those routes. We generally associate a cost with each link in the route… such as shown below. Routing tables can be developed using this information to specify the optimum route between any two points in the network.

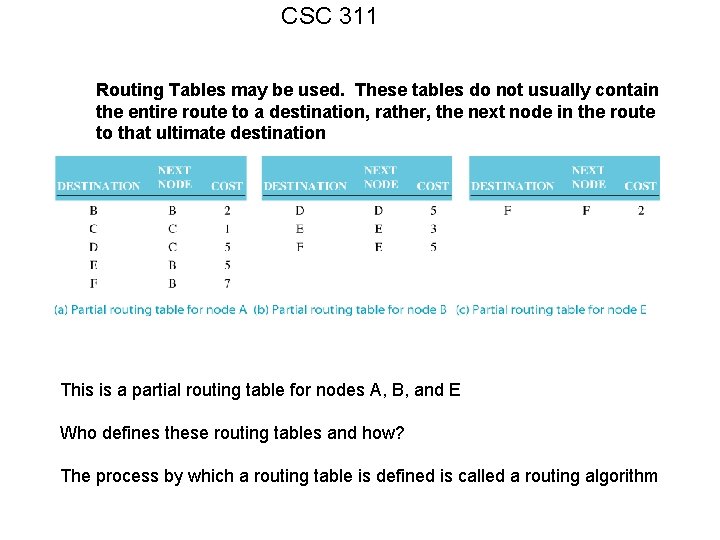
CSC 311 Routing Tables may be used. These tables do not usually contain the entire route to a destination, rather, the next node in the route to that ultimate destination This is a partial routing table for nodes A, B, and E Who defines these routing tables and how? The process by which a routing table is defined is called a routing algorithm

CSC 311 Routing Strategies • Centralized • Distributed • Static • Adaptive

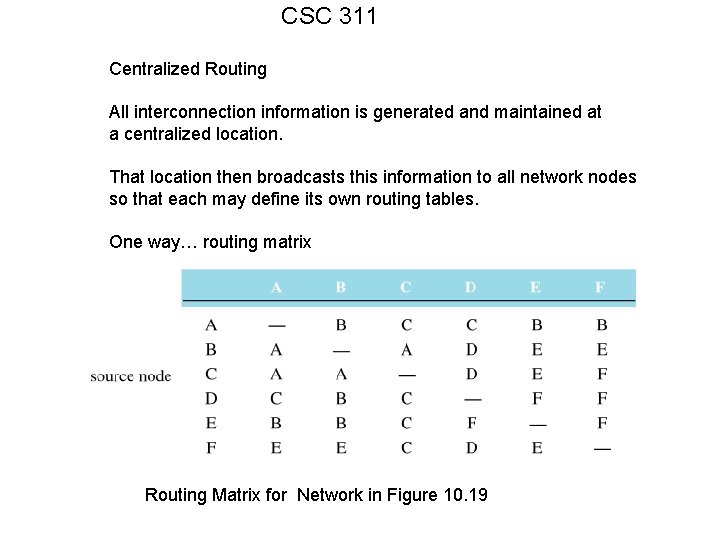
CSC 311 Centralized Routing All interconnection information is generated and maintained at a centralized location. That location then broadcasts this information to all network nodes so that each may define its own routing tables. One way… routing matrix Routing Matrix for Network in Figure 10. 19

CSC 311 Distributed Routing: No centralized control. Each node determines and maintains its routing information Nodes exchange control information

CSC 311 Static Routing: Once a node determines its routing table, the node does not change it. Adaptive Routing: Nodes respond to changes in the network and update their routing tables accordingly.

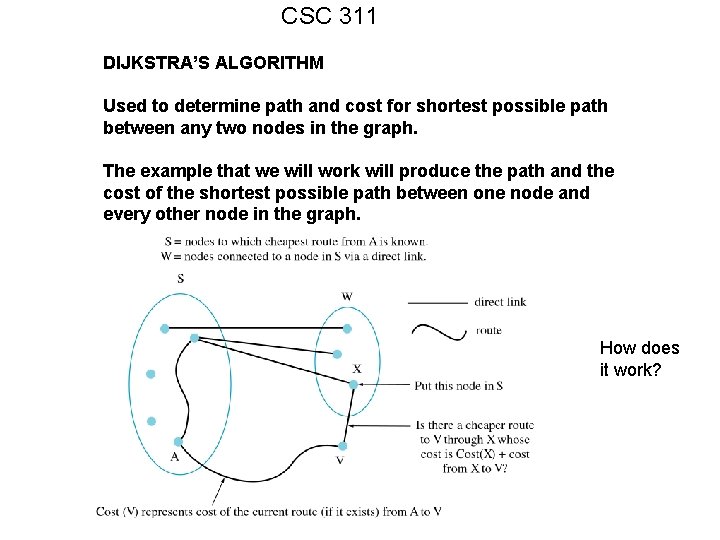
CSC 311 DIJKSTRA’S ALGORITHM Used to determine path and cost for shortest possible path between any two nodes in the graph. The example that we will work will produce the path and the cost of the shortest possible path between one node and every other node in the graph. How does it work?

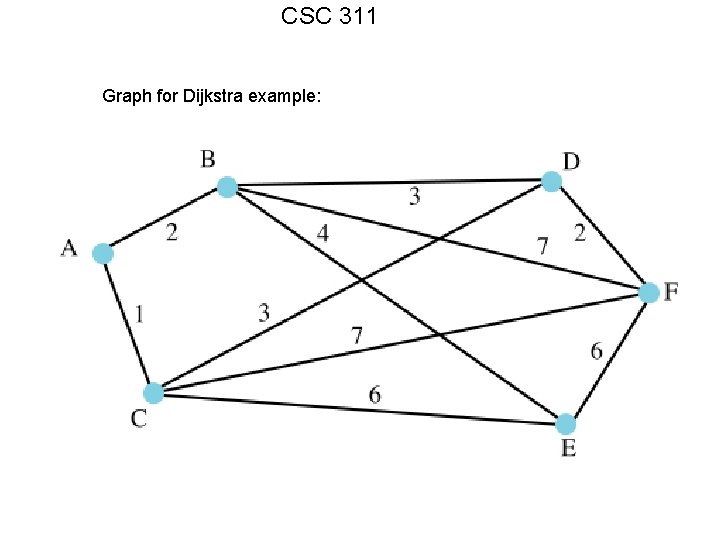
CSC 311 Graph for Dijkstra example:

CSC 311 Skip Bellman-Ford

CSC 311 Additional Routing Methods: Link state routing: • Each node communicates what it knows to its neighbors 1. bit rate 2. delay 3. queue length 4. reliability • a node builds a link state packet for each link • nodes receiving link state packets forward them to neighbors • as these packets are exchanged , nodes learns about the network

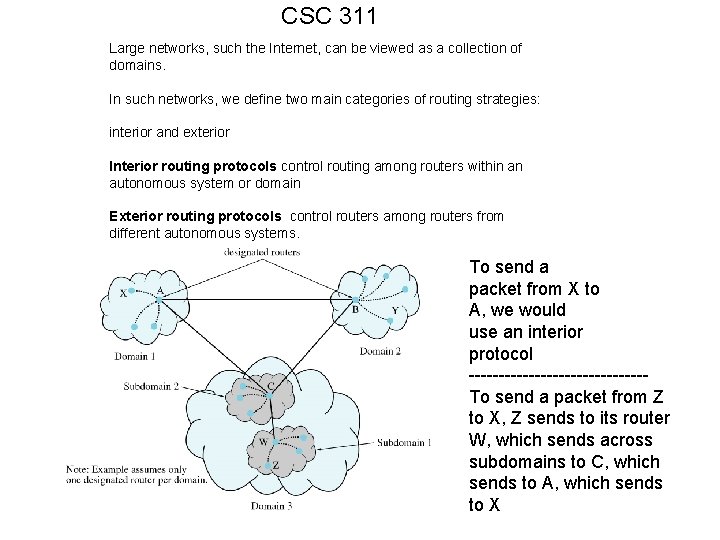
CSC 311 Hierarchical Routing • Nodes are divided into groups, called domains • routes between two nodes in the domain are determine by than networks protocols • each domain has one or more designated routers • a large domain may have multiple subdomains. The “Internet” uses such a hierarchical addressing scheme.

CSC 311 Large networks, such the Internet, can be viewed as a collection of domains. In such networks, we define two main categories of routing strategies: interior and exterior Interior routing protocols control routing among routers within an autonomous system or domain Exterior routing protocols control routers among routers from different autonomous systems. To send a packet from X to A, we would use an interior protocol ---------------To send a packet from Z to X, Z sends to its router W, which sends across subdomains to C, which sends to A, which sends to X

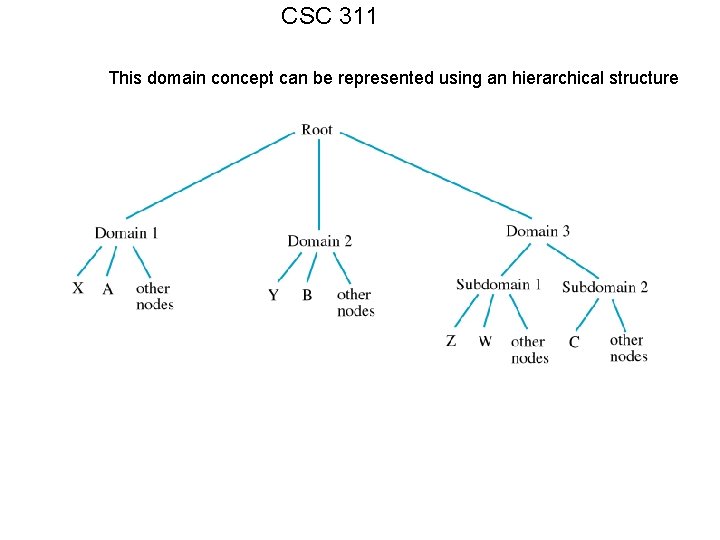
CSC 311 This domain concept can be represented using an hierarchical structure

CSC 311 IPv 4 Internet Addressing Internet addresses are 32 bit numbers, usually shown in dotted decimal notation 143. 200. 128. 3 is an example, each of the decimal numbers can be represented by 8 bits. The Internet uses a class address system, each such address can be interpreted as having two parts: an Internet Protocol (IP) address which is assigned to the network and a local device address. The address above is an example of a class B address, the first 16 bits (143. 200), is the IP network address and the other 16 bits (128. 3) represents the address of the particular device on that network. A class B address provides addresses for over 65, 000 possible users, so it is quite common to further subdivide these users into subnets. Using subnet addressing, the local management might designate part of the lower 16 bits to represent a subnet address.

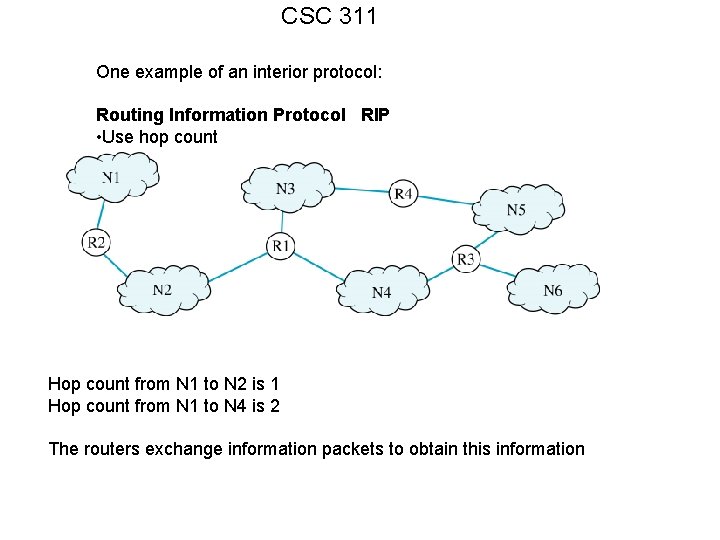
CSC 311 One example of an interior protocol: Routing Information Protocol RIP • Use hop count Hop count from N 1 to N 2 is 1 Hop count from N 1 to N 4 is 2 The routers exchange information packets to obtain this information

CSC 311 Another interior routing protocol: Open Shortest Path First (OSPF) In this case, the “open” means the algorithm is not proprietary can also use other factors in determining best route such as delay, bit rates, actual dollar cost.

CSC 311 Exterior Protocols Border Gateway Protocol: current version is BGP-4 used in the Internet to establish paths among routers in different autonomous systems. Often concerned with just getting to destination, not necessarily the cheapest route. There may be other considerations, such as avoiding a particular country in international traffic.

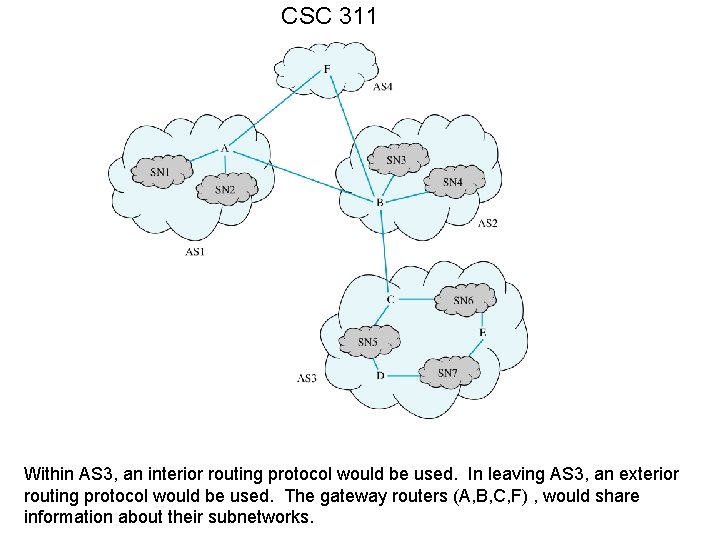
CSC 311 Within AS 3, an interior routing protocol would be used. In leaving AS 3, an exterior routing protocol would be used. The gateway routers (A, B, C, F) , would share information about their subnetworks.

CSC 311 Congestion and Deadlock: We have already discussed congestion and flow control. The routing strategies must deal with the problem of congestion. As congestion increases the efficiency of the network declines: How to deal with it? • Packet elimination • Flow control • Buffer allocation • Choke packets

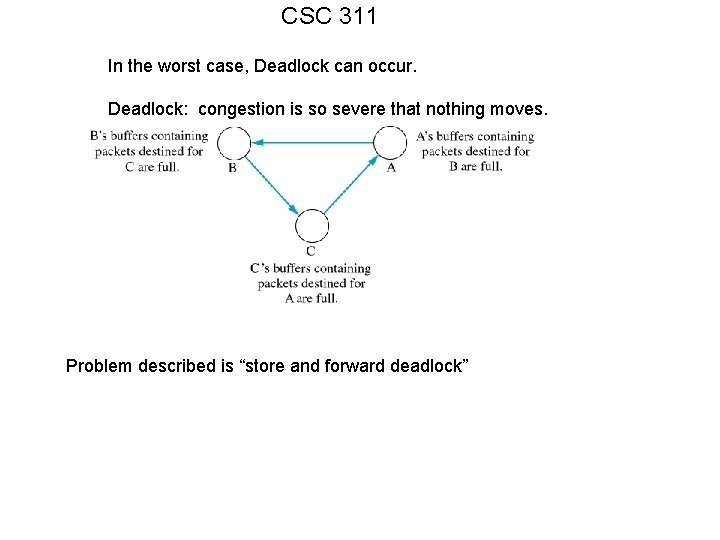
CSC 311 In the worst case, Deadlock can occur. Deadlock: congestion is so severe that nothing moves. Problem described is “store and forward deadlock”

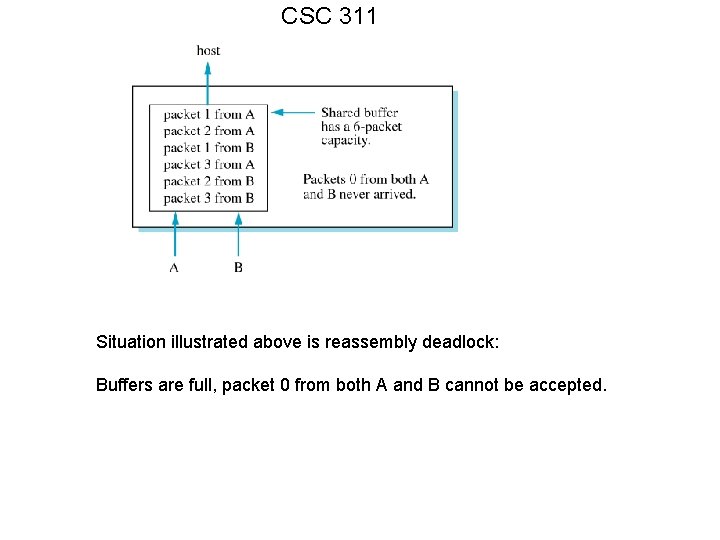
CSC 311 Situation illustrated above is reassembly deadlock: Buffers are full, packet 0 from both A and B cannot be accepted.

CSC 311 Deadlock prevention: Reassembly deadlock can be prevented by establishing and reserving sufficient buffer space to handle the window size for a particular communication Store and forward is handled by allocating sufficient buffer space, but… how much buffer space is enough? One approach to deadlock is to allow it to occur and then deal with it. It might be more cost effective to either prevent deadlock or take steps to reduce the probability of occurrence.

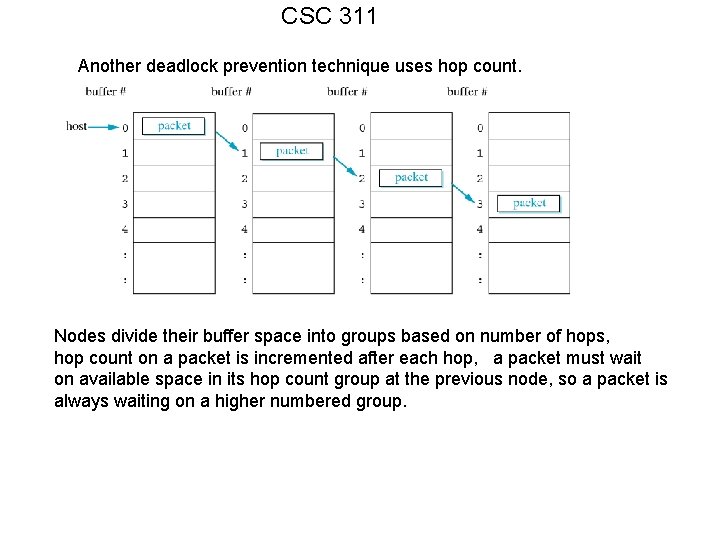
CSC 311 Another deadlock prevention technique uses hop count. Nodes divide their buffer space into groups based on number of hops, hop count on a packet is incremented after each hop, a packet must wait on available space in its hop count group at the previous node, so a packet is always waiting on a higher numbered group.

CSC 311

CSC 311