HIPAA Privacy The Impact of HIPAA on Sponsors





















- Slides: 34

HIPAA Privacy: The Impact of HIPAA on Sponsors of Medical Research Sybil Ingram-Muhammad, Ph. D. Sr. Practice Director, Healthcare Intelli. Mark I. T. Business Solutions June, 2003

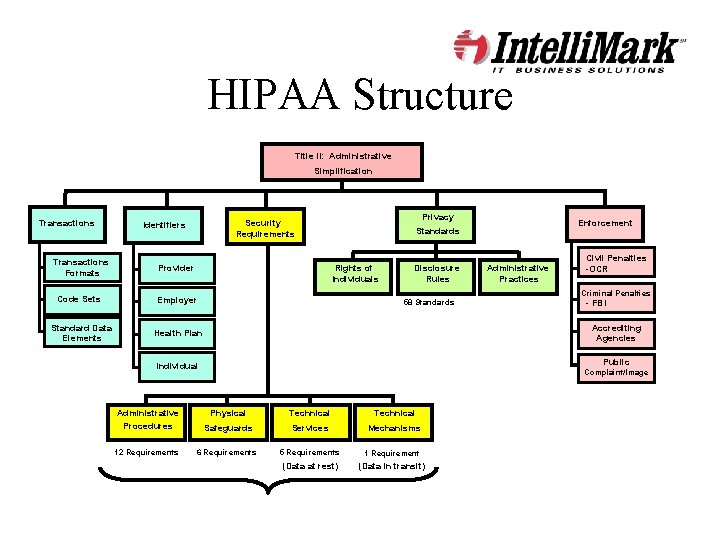
HIPAA Structure Title II: Administrative Simplification Transactions Privacy Security Requirements Identifiers Transactions Formats Provider Code Sets Employer Standard Data Elements Health Plan Enforcement Standards Rights of Individuals Disclosure Rules Administrative Practices Civil Penalties -OCR Criminal Penalties 58 Standards - FBI Accrediting Agencies Public Individual Complaint/Image Administrative Procedures Physical Technical Safeguards Services Mechanisms 12 Requirements 6 Requirements 5 Requirements 1 Requirement (Data at rest) (Data in transit)

CONFUSION

Research • • A systematic investigation, including research development, testing and evaluation designed to develop or contribute to general knowledge vs. Health Care Operations Conducting quality assessment and improvement activities including outcomes evaluation and development of clinical guidelines PROVIDED that the obtaining of generalizable knowledge is NOT the primary purpose of any studies resulting from such activities • ……Hmmmmm? ?

Which do you do? What does it mean if you do what you do? • Research; no treatment • Research with treatment; no bill/claim • Research with treatment, claim generated to be paid by third party • Research…with treatment…claim generated …to be paid by a “health plan” as define by HIPAA

Common Ownership Issues… Hybrid Entity Common Control Issues… A single legal entity that is a covered entity whose business activities include both covered and non-covered function and designates health care components that would meet the definition of a covered entity if it were a single legal entity.

Covered Functions • “Hybrid entities” with covered components-that is, an entity with one or more divisions that provide covered functions • Health Plans • Clearinghouses • Providers that conduct electronic transactions (billing, status queries, etc. )

What’s The Difference? ? ? Uses and Disclosures HI…IIHI…PHI OHCA vs. ACE Research vs. Health Care Operations Designated Record Set vs. Shadow Record Business Associate Contract vs. Data Use Agreement

Individually Identifiable Health Information (IIHI) Protected Health Information (PHI) Electronic-Written/Printed-Verbal (A) Names; (B) All geographic subdivisions smaller than a State, including street address, city, county, precinct, zip code, and their equivalent geocodes, except for the initial three digits of a zip code if, according to the current publicly available data from the Bureau of the Census: (1) The geographic unit formed by combining all zip codes with the same three initial digits contains more than 20, 000 people; and (2) The initial three digits of a zip code for all such geographic units containing 20, 000 or fewer people is changed to 000. (C) All elements of dates (except year) for dates directly related to an individual, including birth date, admission date, discharge date, date of death; and all ages over 89 and all elements of dates (including year) indicative of such age, except that such ages and elements may be aggregated into a single category of age 90 or older; (D) Telephone numbers; (E) Fax numbers; (F) Electronic mail addresses; (G) Social security numbers; (H) Medical record numbers; (I) Health plan beneficiary numbers; (J) Account numbers; (K) Certificate/license numbers; (L) Vehicle identifiers and serial numbers, including license plate numbers; (M) Device identifiers and serial numbers; (N) Web Universal Resource Locators (URLs) (O) Internet Protocol (IP) address numbers; (P) Biometric identifiers, including finger and voice prints; (Q) Full face photographic images and any comparable images; and (R) Any other unique identifying number, characteristic, or code

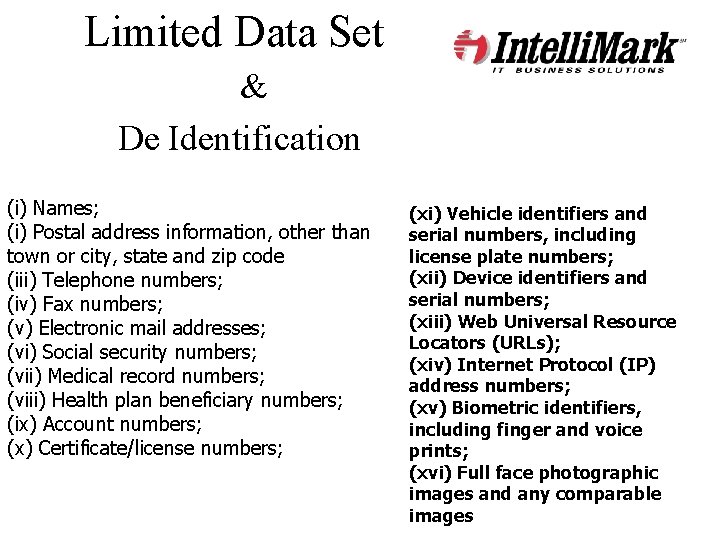
Limited Data Set - PHI that excludes specific, readily identifiable information, not only about the individual themselves but also their relatives, employers and members of their households. 16 IIHI must be excluded. Researchers may disclose information in the limited data set if the researcher's covered entity enters into a data use agreement with the recipient of the limited data set PHI in a limited data set may not be used to contact subjects

Limited Data Set & De Identification (i) Names; (i) Postal address information, other than town or city, state and zip code (iii) Telephone numbers; (iv) Fax numbers; (v) Electronic mail addresses; (vi) Social security numbers; (vii) Medical record numbers; (viii) Health plan beneficiary numbers; (ix) Account numbers; (x) Certificate/license numbers; (xi) Vehicle identifiers and serial numbers, including license plate numbers; (xii) Device identifiers and serial numbers; (xiii) Web Universal Resource Locators (URLs); (xiv) Internet Protocol (IP) address numbers; (xv) Biometric identifiers, including finger and voice prints; (xvi) Full face photographic images and any comparable images

Authorizations -Must be obtained for each use or disclosure of PHI for research purposes -Treatment that occur during research trial may be conditioned based upon the patient signing an authorization - May be combined with an informed consent to participate in the study, another authorization or any other legal permission related to research -Authorizations received from research study participants must include a statement that the authorization will have no expiration date

Permitted Disclosures without Authorization • • Required by law Public health activities Reporting abuse Health oversight Judicial or administrative proceedings Law enforcement Deceased patients Organ transplants • • • Threat or danger Specialized government functions Workers’ Compensation

Waiver Criteria • IRB or Privacy board must use the following when approving request for a waiver of written authorization: use of the PHI involves no more than minimal risk* to the privacy of the individual the research could not practically be conducted without the waiver the research could not practically be conducted without access to the PHI *= plans and assurances must be put in pace to protect identifiers from improper use or disclosures, will be destroyed at the earliest opportunity and will not be disclosed to a 3 rd party (EARBL)

Reviews Preparatory to Researcher must represent that: • Use or disclosure is sought solely to prepare research protocol or similar purpose • No protected information will be removed from the facility during review • Information being sought is necessary for the research purposes

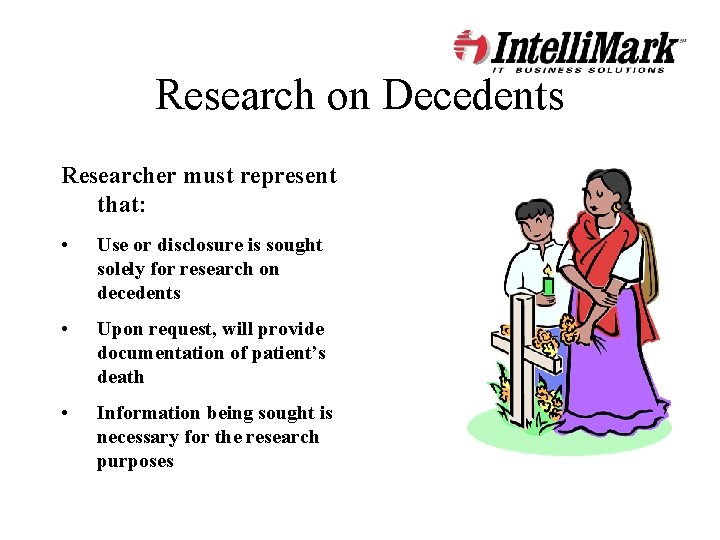
Research on Decedents Researcher must represent that: • Use or disclosure is sought solely for research on decedents • Upon request, will provide documentation of patient’s death • Information being sought is necessary for the research purposes

Business Associates • A business associate performs functions on behalf of the health care organization involving the use or disclosure of identifiable health information. • Examples include: billing or management companies, attorneys, accountants, consultants, and companies providing claims processing, data analysis or aggregation, accreditation, or financial services, among other services.

164. 530 (c) (1) Standard: safeguards. A covered entity must have in place appropriate administrative, technical, and physical safeguards to protect the privacy of protected health information. PAST DUE >>> APRIL 14, 2003 …research activities were not exempted from this duty

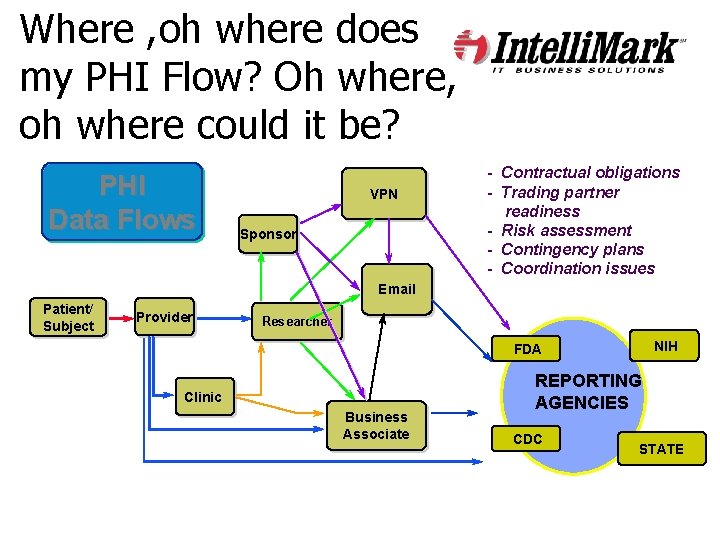
Where , oh where does my PHI Flow? Oh where, oh where could it be? PHI Data Flows VPN Sponsor - Contractual obligations - Trading partner readiness - Risk assessment - Contingency plans - Coordination issues Email Patient/ Subject Provider Researcher NIH FDA Clinic Business Associate REPORTING AGENCIES CDC STATE

CONSEQUENCES (Alan Goldberg, J. D. , November, 2002)

…a threat or a promise? “ They said they were going to come and get me before. Why should I believe they’ll come and get me now? ”

HIPAA Sanctions Civil penalties. Health plans, providers and clearinghouses that violate these standards will be subject to civil liability. Civil money penalties are $100 per violation, up to $25, 000 person, per year for each requirement or prohibition violated. Federal criminal penalties. Under HIPAA, Congress also established criminal penalties for knowingly violating patient privacy. • Up to $50, 000 and one year in prison for obtaining or disclosing protected health information; • Up to $100, 000 and up to five years in prison for obtaining protected health information under "false pretenses"; • Up to $250, 000 and up to 10 years in prison for obtaining or disclosing protected health information with the intent to sell, transfer or use it for commercial advantage, personal gain or malicious harm.

Who Goes To Jail? Page 82603 - Federal Register / Vol. 65, No. 250 / Thursday, December 28, 2000 / Rules and Regulations Extracted from the Preamble of the Final Privacy Rule: “However, we note that section 1128 A(1) of the Social Security Act, which applies to the imposition of civil monetary penalties under HIPAA, provides that a principal is liable for penalties for the actions of its agent acting within the scope of the agency. ”

OCR HIPAA Privacy Complaint Form (excerpts) (Alan Goldberg, J. D. , November, 2002) …mind answering a few questions please? • Are you filing this compliant for someone else? • Who ( or what agency or organization, eg. , provider, health plan) do you believe violated your (or someone else's) health information privacy rights or committed another violation of the Privacy Rule? • When do you believe that the violation of health privacy rights occurred? • Describe briefly what happened? How and why do you believe your (or someone else’s) health information privacy rights were violated, or the privacy rule otherwise was violated?

CONSENSUS (Alan Goldberg, J. D. , November, 2002)

Three Important Considerations How compliant do you want to be? …in the absence of a de facto check list, how will you determine when you’re done?

Three Important Considerations … How much risk are you willing to accept? The answers to the questions help drive your: budget process $$$$ policy and procedure development defining your HCO

Next Steps… What Do I Do?

Research Impact Assessment A Balancing Act

Expect Changes… § 160. 104 Modifications. (a) Except as provided in paragraph (b) of this section, the Secretary may (b) adopt a modification to a standard or implementation specification adopted (c) under this subchapter no more frequently than once every 12 months. (b) The Secretary may adopt a modification at any time during the first year after the standard or implementation specification is initially adopted, if the Secretary determines that the modification is necessary to permit compliance with the standard or implementation specification. (c) The Secretary will establish the compliance date for any standard or implementation specification modified under this section. (1) The compliance date for a modification is no earlier than 180 days after the (2) effective date of the final rule in which the Secretary adopts the modification. (2) The Secretary may consider the extent of the modification and the time needed to comply with the modification in determining the compliance date for the modification. (3) The Secretary may extend the compliance date for small health plans, as the Secretary determines is appropriate

Basic HIPAA Compliance Remediation Elements Senior Management Endorsement and Active Participation Budget HRT Leader HRT Team Composition Team SME’s General Counsel Involvement Documentation Education Implementation ***Compliance*** Monitoring and Enforcement

Remediation Plan Contents -Identify responsible parties for each task -Identify change management process -Identify communication process -Policy and procedure creation /modification -Forms creation/modification -Job description review minimum necessary/need to know -Training Material Preparation -Training -Re-assessment -Mock Sentinel Event/Review/Re-plan -Implement -Repeat, repeat, incorporate, repeat…

Informative Web Sites • www. snip. wedi. org- Strategic National Implementation Process/ Workgroup for Electronic Data Interchange • www. aspe. os. hhs. gov/admnsimp - Department of Health and Human Services • www. cms. gov/hipaa - Centers for Medicare and Medical Services • www. edipartners. com – X 12 N 4010 Training • www. wpc-edi. com - Washington Publishing Company – Implementation Guides • www. aamc. org – Association of American Medical Colleges • www. healthprivacy. org - Health Privacy Project • www. ahima. org - American Health Information Management Assoc

Thank You! Sybil Ingram-Muhammad, MT(ASCP), MBA, Ph. D. Senior Practice Director, Healthcare Intelli. Mark I. T. Business Solutions www. intellimark-it. com smuhammad@intellimark-it. com 1 -972 -304 -2260
 Privacy awareness and hipaa awareness training cvs
Privacy awareness and hipaa awareness training cvs Hipaa privacy and security awareness training
Hipaa privacy and security awareness training Hipaa training air force
Hipaa training air force Types of sponsors
Types of sponsors Medicare parts c and d sponsors are not required
Medicare parts c and d sponsors are not required Thanks to all our sponsors
Thanks to all our sponsors Jeopardy sponsors
Jeopardy sponsors Essendon fc sponsors
Essendon fc sponsors Coca-cola sponsorship proposal
Coca-cola sponsorship proposal Calgary flames sponsors
Calgary flames sponsors Thẻ vin
Thẻ vin Hát kết hợp bộ gõ cơ thể
Hát kết hợp bộ gõ cơ thể Phản ứng thế ankan
Phản ứng thế ankan Từ ngữ thể hiện lòng nhân hậu
Từ ngữ thể hiện lòng nhân hậu Diễn thế sinh thái là
Diễn thế sinh thái là Các môn thể thao bắt đầu bằng tiếng bóng
Các môn thể thao bắt đầu bằng tiếng bóng V cc cc
V cc cc Chó sói
Chó sói Một số thể thơ truyền thống
Một số thể thơ truyền thống Hổ sinh sản vào mùa nào
Hổ sinh sản vào mùa nào Lời thề hippocrates
Lời thề hippocrates Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ đại từ thay thế
đại từ thay thế Vẽ hình chiếu vuông góc của vật thể sau
Vẽ hình chiếu vuông góc của vật thể sau Frameset trong html5
Frameset trong html5 Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Thế nào là mạng điện lắp đặt kiểu nổi
Thế nào là mạng điện lắp đặt kiểu nổi Dạng đột biến một nhiễm là
Dạng đột biến một nhiễm là Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Vẽ hình chiếu đứng bằng cạnh của vật thể
Vẽ hình chiếu đứng bằng cạnh của vật thể Cái miệng xinh xinh thế chỉ nói điều hay thôi
Cái miệng xinh xinh thế chỉ nói điều hay thôi Khi nào hổ mẹ dạy hổ con săn mồi
Khi nào hổ mẹ dạy hổ con săn mồi Cách giải mật thư tọa độ
Cách giải mật thư tọa độ Tư thế worm breton là gì
Tư thế worm breton là gì điện thế nghỉ
điện thế nghỉ

























































