HIPAA Privacy Security Overview Agenda 1 HIPAA Overview





















- Slides: 26

HIPAA Privacy & Security Overview

Agenda 1. HIPAA Overview 6. Security incidents 2. Privacy Practices 7. Sanctions 3. Security definitions 8. Breach notification 4. Security standards 9. Enforcement update 5. Security safeguards

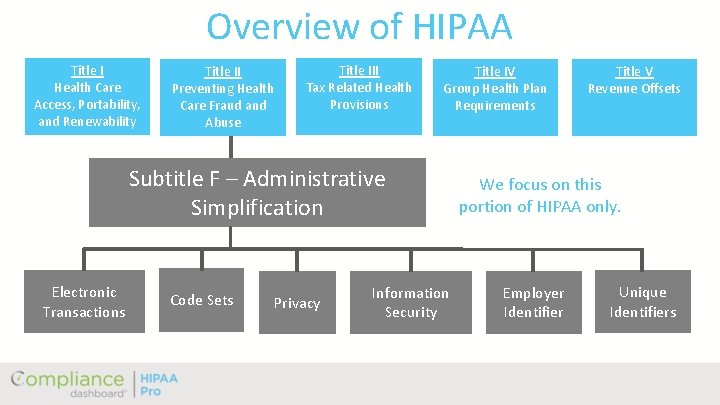
Overview of HIPAA Title I Health Care Access, Portability, and Renewability Title II Preventing Health Care Fraud and Abuse Title III Tax Related Health Provisions Title IV Group Health Plan Requirements Subtitle F – Administrative Simplification Electronic Transactions Code Sets Privacy Information Security Title V Revenue Offsets We focus on this portion of HIPAA only. Employer Identifier Unique Identifiers

Who does HIPAA Impact? • HIPAA applies to all “Covered Entities, ” including: – Health Care Providers – Health Care Clearinghouses – Health Plans • Health Plans offered by Insurance Companies • Employer-sponsored health plans (e. g. , medical, dental, prescription, vision, health FSAs, EAPs, wellness, HRAs) – Business Associates: firms working with covered entities (billing services, transcription services, TPAs, brokers)

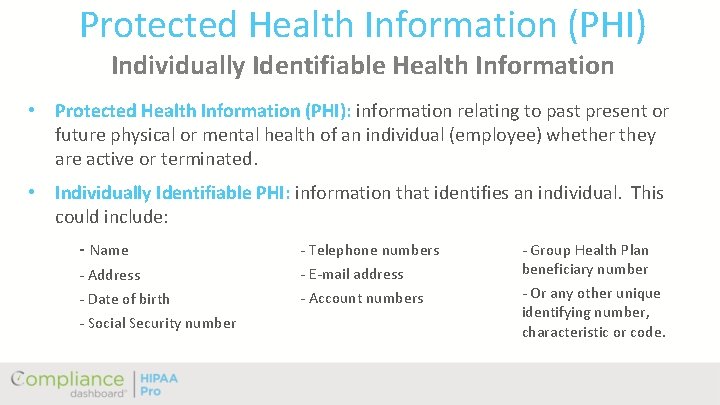
Protected Health Information (PHI) Individually Identifiable Health Information • Protected Health Information (PHI): information relating to past present or future physical or mental health of an individual (employee) whether they are active or terminated. • Individually Identifiable PHI: information that identifies an individual. This could include: - Name - Telephone numbers - Address - E-mail address - Date of birth - Account numbers - Social Security number - Group Health Plan beneficiary number - Or any other unique identifying number, characteristic or code.

Privacy Rule • Applies to paper/oral/electronic records • Sets boundaries on the Use and Disclosure of health information • Gives “individuals” more control over their own health information • Establishes safeguards for protecting the privacy of health information. • Holds covered entities accountable for violations of privacy requirements.

Privacy Regulation Some requirements that a covered entity must comply with include, but is not limited to the following: • Designating a Privacy Official. • Designating a Contact for handling Complaints. • Developing policies and procedures on the use and disclosure of individually identifiable health information. • Providing training to all workforce members on the policies and procedures that affect their job duties. • Providing a Notice of Privacy Practices to individuals

How Does Covered Entity Use Protected Health Information? • They share this information with other healthcare providers. They are permitted to use and/or disclose information for treatment, payment or health care operations without getting permission from an individual. • To use information for any other reason or to disclose it to any one other than the patient or Covered Entity may require a signed and verified authorization.

Authorizations • What is an authorization? – Used to allow PHI disclosures • When is it used? – Disclosure to spouse/family member – Marketing purposes – Research – Fund Raising

Other Aspects of HIPAA Administration Individual has the right to: • Access their protected health information • Receive an accounting, amendment their protected health information • File a complaint • Request confidential communications • Restrict access to their protected health information.

Confidentiality • All Covered Entity employees that have access to protected health information agree that at no time, during or after their employment with Covered Entity, will they use, access or disclose protected health information to anyone except as required or permitted in the course and scope of their duties. • Unauthorized use/disclosure may result in disciplinary action up to and including termination. • Civil or criminal penalties may also apply

Safeguards Covered entities must implement appropriate safeguards to protect an individual’s protected health information. Remember to do the following: • Records that contain protected health information should be maintained in a secure location or locked away. • Records that contain protected health information should be shredded before discarding the information. • Passwords should not be shared with anyone. Electronic protected health information needs to be safeguarded as well.

HIPAA Security • May 21, Purdue University • March 17, Boston College • May 21, Jackson Community College (Michigan) • March 17, Chico State University • May 19, Westborough Bank (Florida) • March 16, Kaiser Permanente • May, Business Week On-line forum • March 8, DSW • May 14, MTSU • March, Lexis. Nexis (Seisint) • May 5, Wharton school (MSU) • February 15, Bell v. Michigan Council 25 • May 2, Time Warner • February, Bank of America • April 28, Bank of America, • February, Choice Point Commerce Bankorp, PNC Bank • February, Pay. Maxx • April 21, Carnegie Mellon University • November, Wells Fargo • April 20, Ameri. Trade • November, Gibson Sentencing US District Court • April 8, San Jose Medical Group • November, Minneapolis School District • March 28, University of California, Berkley

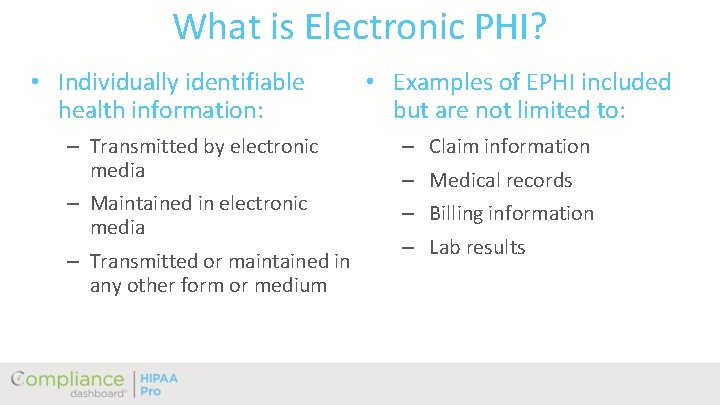
What is Electronic PHI? • Individually identifiable health information: • Examples of EPHI included but are not limited to: – Transmitted by electronic media – Claim information – Maintained in electronic media – Billing information – Transmitted or maintained in any other form or medium – Medical records – Lab results

Security Standards • Only those that need access – Physical access – Technical access • The covered entity is responsible for the confidentiality, integrity and availability of EPHI • The covered entities safeguards are the first line of defense

Security Management Process • Risk Analysis • Risk Management • Sanction Policy • Information System Activity Review

Safeguards • Workforce security • Device & Media controls • Information access • Access controls (technical) • Facility Security plan • Administrative requirements • Workstation use

Security Awareness • Training • Security reminders • Protection against malicious software • Password management

Contingency Plans (Availability) • Data backups • Disaster recovery • Emergency operation plan • May have: – Critical applications and data – Testing and revisions

Workforce Security Training • Who: anyone who has access to EPHI • When: as close as possible to deadline • New employees or contractors: as part of org training. • Due to changes

Events Requiring Action • Security Incidents • Sanctions • Breach Notification

Security Incidents • What are they? • What should you do? – Actions depend on the incident – Who was responsible, third party? – Are Sanctions required?

Sanctions/Violations • Workforce members who violate health plans Privacy or Security Policies may be subject to disciplinary actions, up to and including termination. • The amount and type of corrective action used in any particular situation will depend on the facts and circumstances. The company maintains the discretion to determine whether corrective action is appropriate.

Specifics • Notification to individuals • Notification to the media • Notification to the Secretary • Notification by a business associate • Law enforcement delay • Burden of proof

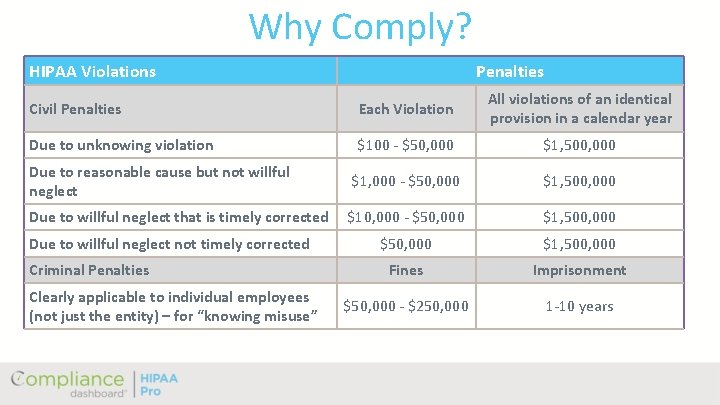
Why Comply? HIPAA Violations Penalties Civil Penalties Each Violation All violations of an identical provision in a calendar year Due to unknowing violation $100 - $50, 000 $1, 500, 000 Due to reasonable cause but not willful neglect $1, 000 - $50, 000 $1, 500, 000 Due to willful neglect that is timely corrected $10, 000 - $50, 000 $1, 500, 000 Fines Imprisonment $50, 000 - $250, 000 1 -10 years Due to willful neglect not timely corrected Criminal Penalties Clearly applicable to individual employees (not just the entity) – for “knowing misuse”

Questions?