CSC 3050 Computer Architecture Instruction Set Architecture ISA








![Memory Operand Example (1) l C code g = h + A[8]; – g Memory Operand Example (1) l C code g = h + A[8]; – g](https://slidetodoc.com/presentation_image/1b93eb47d0d6092b356ba6f058399a99/image-17.jpg)
![Memory Operand Example (2) l C code A[12] = h + A[8]; – h Memory Operand Example (2) l C code A[12] = h + A[8]; – h](https://slidetodoc.com/presentation_image/1b93eb47d0d6092b356ba6f058399a99/image-18.jpg)


![Translating C Code to Machine Code (1) l C code: A[300] = h + Translating C Code to Machine Code (1) l C code: A[300] = h +](https://slidetodoc.com/presentation_image/1b93eb47d0d6092b356ba6f058399a99/image-30.jpg)


![Compiling Loop Statements l C code: while (save[i] == k) i += 1; – Compiling Loop Statements l C code: while (save[i] == k) i += 1; –](https://slidetodoc.com/presentation_image/1b93eb47d0d6092b356ba6f058399a99/image-40.jpg)






- Slides: 67

CSC 3050 – Computer Architecture Instruction Set Architecture (ISA) Prof. Yeh-Ching Chung School of Science and Engineering Chinese University of Hong Kong, Shenzhen National Tsing Hua University ® copyright OIA 1

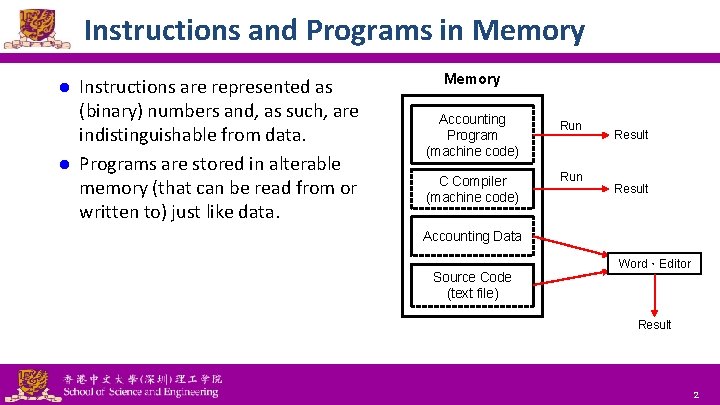
Instructions and Programs in Memory Instructions are represented as (binary) numbers and, as such, are indistinguishable from data. l Programs are stored in alterable memory (that can be read from or written to) just like data. l Memory Accounting Program (machine code) C Compiler (machine code) Run Result Accounting Data Source Code (text file) Word,Editor Result National Tsing Hua University ® copyright OIA 2

Stored-Program Concept l Programs can be shipped as files of binary numbers – binary- code compatibility. l Computers can inherit ready-made software provided they are compatible with an existing ISA – leads industry to align around a small number of ISAs. National Tsing Hua University ® copyright OIA 3

Assembly Language Instructions l The language of the machine – Want an ISA that makes it easy to build the hardware and the compiler while maximizing performance and minimizing cost. l Our target: the MIPS ISA – Similar to other ISAs developed since the 1980’s – Used by Broadcom, Cisco, NEC, Nintendo, Sony, etc. l Design Goals: – Maximize performance, minimize cost, reduce design time (time-to -market), minimize memory space (embedded systems), minimize power consumption (mobile systems). National Tsing Hua University ® copyright OIA 4

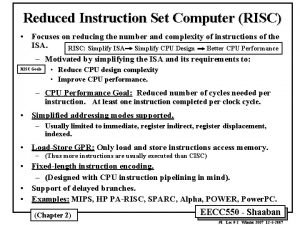
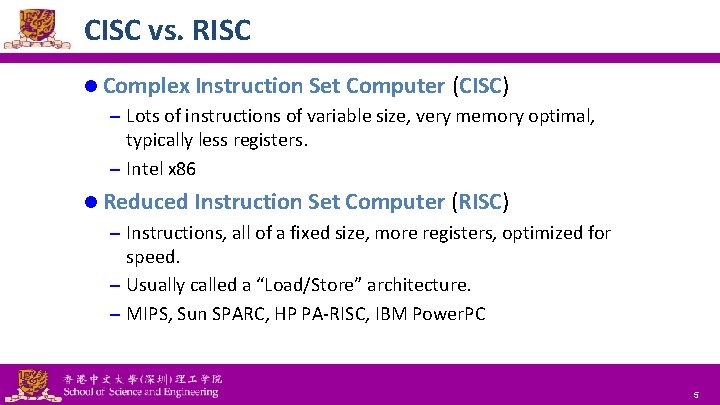
CISC vs. RISC l Complex Instruction Set Computer (CISC) – Lots of instructions of variable size, very memory optimal, typically less registers. – Intel x 86 l Reduced Instruction Set Computer (RISC) – Instructions, all of a fixed size, more registers, optimized for speed. – Usually called a “Load/Store” architecture. – MIPS, Sun SPARC, HP PA-RISC, IBM Power. PC National Tsing Hua University ® copyright OIA 5

RISC – Reduced Instruction Set Computer l RISC Philosophy – fixed instruction lengths – load-store instruction sets – limited number of addressing modes – limited number of operations l Instruction sets are measured by how well compilers use them as opposed to how well assembly language programmers use them. National Tsing Hua University ® copyright OIA 6

MIPS (RISC) Design Principles l Simplicity favors regularity – Fixed size instructions – Small number of instruction formats – Opcode always the first 6 bits l Smaller is faster – Limited instruction set – Limited number of registers – Limited number of addressing modes l Make the common case fast – Arithmetic operands from the registers (load-store machine) – Allow instructions to contain immediate operands l Good design demands good compromises – Three instruction formats National Tsing Hua University ® copyright OIA 7

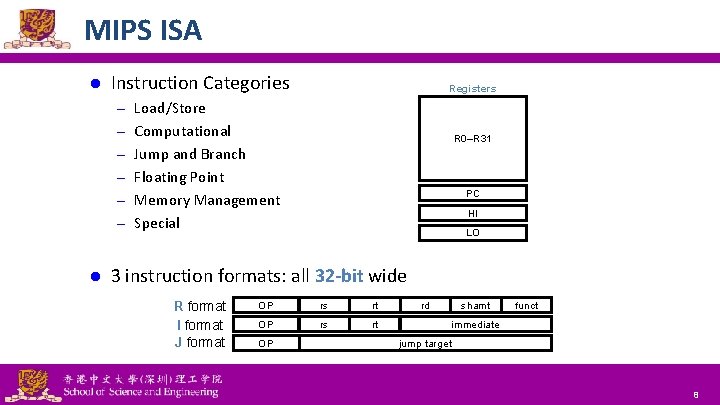
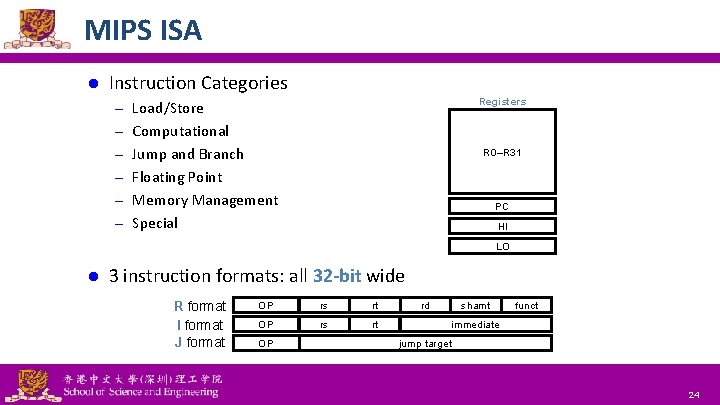
MIPS ISA l Instruction Categories Registers – Load/Store – Computational R 0–R 31 – Jump and Branch – Floating Point PC – Memory Management HI – Special l LO 3 instruction formats: all 32 -bit wide R format I format J format National Tsing Hua University ® copyright OIA OP rs rt OP rd shamt funct immediate jump target 8

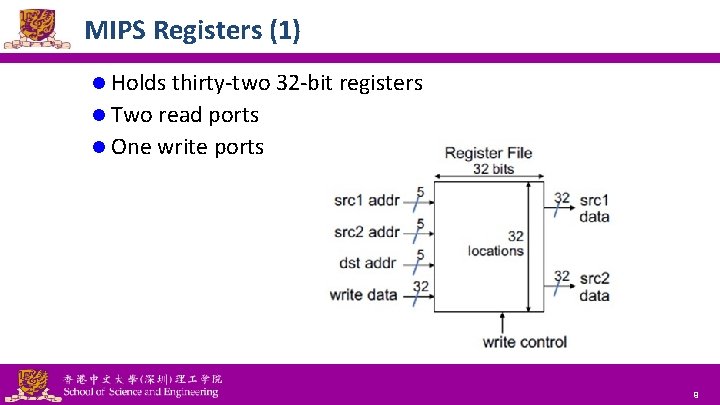
MIPS Registers (1) l Holds thirty-two 32 -bit registers l Two read ports l One write ports National Tsing Hua University ® copyright OIA 9

MIPS Registers (2) l Registers are – Faster than main memory • But registers with more locations are slower • Read/write port increase impacts speed quadratically – Easier for a complier to use • E. g. , (A*B) – (C*D) – (E*F) can do multiplications in any order vs. stack – Can hold variables • So that code density improves (since register are named with fewer bits than a memory location). National Tsing Hua University ® copyright OIA 10

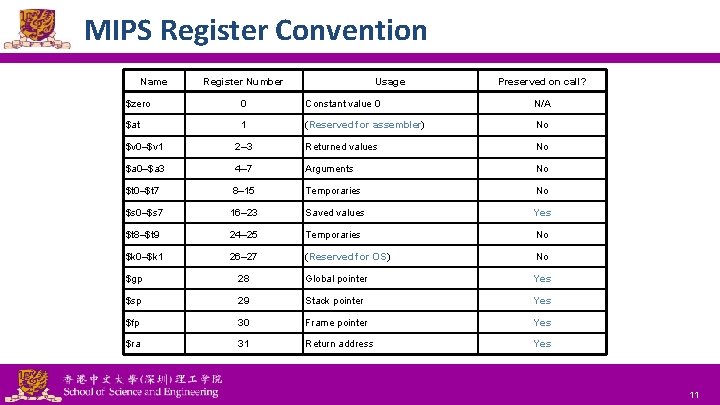
MIPS Register Convention Name Register Number Usage Preserved on call? $zero 0 Constant value 0 N/A $at 1 (Reserved for assembler) No $v 0–$v 1 2– 3 Returned values No $a 0–$a 3 4– 7 Arguments No $t 0–$t 7 8– 15 Temporaries No $s 0–$s 7 16– 23 Saved values Yes $t 8–$t 9 24– 25 Temporaries No $k 0–$k 1 26– 27 (Reserved for OS) No $gp 28 Global pointer Yes $sp 29 Stack pointer Yes $fp 30 Frame pointer Yes $ra 31 Return address Yes National Tsing Hua University ® copyright OIA 11

Arithmetic Operations l Add and subtract, three operands – Two sources and one destination add a, b, c # a gets b + c – All arithmetic operations have this form l Design Principle 1: Simplicity favors regularity – Regularity makes implementation simpler – Simplicity enables higher performance at lower cost National Tsing Hua University ® copyright OIA 12

Arithmetic Example l C code: f = (g + h) - (i + j); l Compiled MIPS code: add t 0, g, h add t 1, i, j sub f, t 0, t 1 # temp t 0 = g + h # temp t 1 = i + j # f = t 0 - t 1 l Using registers (f–j are stored in $s 0–$s 4): add $t 0, $s 1, $s 2 add $t 1, $s 3, $s 4 sub $s 0, $t 1 National Tsing Hua University ® copyright OIA # $t 0 = g + h # $t 1 = i + j # f = $t 0 - $t 1 13

Register Operands Arithmetic instructions use register operands l MIPS has 32 × 32 -bit registers l – Use for frequently accessed data – Numbered 0 to 31 – 32 -bit data called a “word” l Assembler names (convention) – $t 0, $t 1, …, $t 9 for temporary values – $s 0, $s 1, …, $s 7 for saved variables National Tsing Hua University ® copyright OIA 14

Memory Operands l Design Principle 2: Smaller is faster – (main memory: millions of locations) l Main memory used for composite data – Arrays, structures, dynamic data l To apply arithmetic operations – Load values from memory into registers – Store result from register to memory l Memory is byte addressed – Each address identifies an 8 -bit byte l Words are aligned in memory – Address must be a multiple of 4 l MIPS is Big Endian National Tsing Hua University ® copyright OIA 15

Big Endian / Little Endian l Big Endian: The leftmost byte stores at the starting address of a word – IBM 360/370, Motorola 68 k, MIPS, Sparc, HP PA l Little Endian: The rightmost byte stores at the starting address of a word – Intel 80 x 86, DEC Vax, DEC Alpha l Example: 0 x 1234 abcd National Tsing Hua University ® copyright OIA Memory Big-Endian Little-Endian 0 x 0000 0 x 12 0 xcd 0 x 0001 0 x 34 0 xab 0 x 0002 0 xab 0 x 34 0 x 0003 0 xcd 0 x 12 16
![Memory Operand Example 1 l C code g h A8 g Memory Operand Example (1) l C code g = h + A[8]; – g](https://slidetodoc.com/presentation_image/1b93eb47d0d6092b356ba6f058399a99/image-17.jpg)
Memory Operand Example (1) l C code g = h + A[8]; – g in $s 1, h in $s 2, base address of A in $s 3 l Compiled MIPS code Index 8 requires offset of 32 (4 bytes × 8 words) lw add $t 0, 32($s 3) $s 1, $s 2, $t 0 Offset National Tsing Hua University ® copyright OIA # load word Base register 17
![Memory Operand Example 2 l C code A12 h A8 h Memory Operand Example (2) l C code A[12] = h + A[8]; – h](https://slidetodoc.com/presentation_image/1b93eb47d0d6092b356ba6f058399a99/image-18.jpg)
Memory Operand Example (2) l C code A[12] = h + A[8]; – h in $s 2, base address of A in $s 3 l Compiled MIPS code – Index 8 requires offset of 32 (4 bytes × 8 words) lw add sw $t 0, 32($s 3) $t 0, $s 2, $t 0, 48($s 3) National Tsing Hua University ® copyright OIA # load word # store word 18

Registers vs. Memory l Registers are faster to access than memory l Operating on memory data requires loads and stores – More instructions to be executed l Compiler must use registers for variables as much as possible – Only spill to memory for less frequently used variables – Register optimization is important! National Tsing Hua University ® copyright OIA 19

Immediate Operands l Constant data specified in an instruction addi $s 3, 4 l No subtract immediate instruction – Just use a negative constant addi $s 2, $s 1, -1 National Tsing Hua University ® copyright OIA 20

The Constant Zero l Design Principle 3: Make the common case fast – Small constants are common – Immediate operand avoids a load instruction l MIPS register 0 ($zero) is the constant 0 – Cannot be overwritten l Useful for common operations – E. g. , move between registers add $t 2, $s 1, $zero National Tsing Hua University ® copyright OIA 21

Binary Integers l Unsigned Binary Integers – Range: 0 to 2 n – 1 – 32 bit: 0 to 4, 294, 967, 295 l 2’s-Complement Signed Integers – – Range: – 2(n – 1) to +2(n – 1) – 1 32 bits: – 2, 147, 483, 648 to +2, 147, 483, 647 Bit 31 is sign bit: 1 is negative, 0 is positive Some specific numbers • 0: 0000 … 0000 • – 1: 1111 … 1111 • Most-negative: 1000 0000 … 0000 • Most-positive: 0111 1111 … 1111 National Tsing Hua University ® copyright OIA 22

Sign Extension l Representing a number using more bits – Preserve the numeric value l In MIPS instruction set – addi: extend immediate value – lb, lh: extend loaded byte/halfword – beq, bne: extend the displacement l Replicate the sign bit to the left – compare unsigned values: extend with 0 s l Examples: 8 -bit to 16 -bit – +2: 0000 0010 => 0000 0010 – – 2: 1111 1110 => 1111 1110 National Tsing Hua University ® copyright OIA 23

MIPS ISA l Instruction Categories Registers – Load/Store – Computational – Jump and Branch R 0–R 31 – Floating Point – Memory Management PC – Special HI LO l 3 instruction formats: all 32 -bit wide R format I format J format National Tsing Hua University ® copyright OIA OP rs rt OP rd shamt funct immediate jump target 24

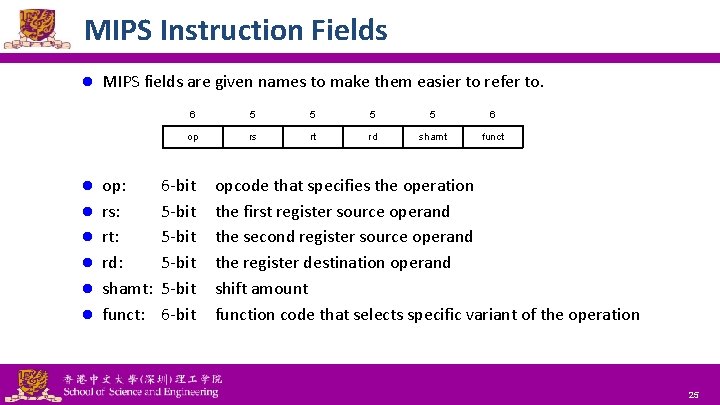
MIPS Instruction Fields l l l l MIPS fields are given names to make them easier to refer to. op: rs: rt: rd: shamt: funct: 6 5 5 6 op rs rt rd shamt funct 6 -bit 5 -bit 6 -bit opcode that specifies the operation the first register source operand the second register source operand the register destination operand shift amount function code that selects specific variant of the operation National Tsing Hua University ® copyright OIA 25

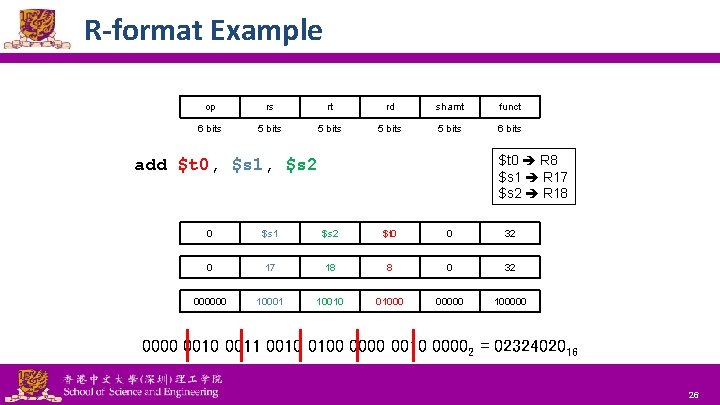
R-format Example op rs rt rd shamt funct 6 bits 5 bits 6 bits $t 0 R 8 $s 1 R 17 $s 2 R 18 add $t 0, $s 1, $s 2 0 $s 1 $s 2 $t 0 0 32 0 17 18 8 0 32 000000 10001 10010 01000 00000 100000 0010 0011 0010 0100 0010 00002 = 0232402016 National Tsing Hua University ® copyright OIA 26

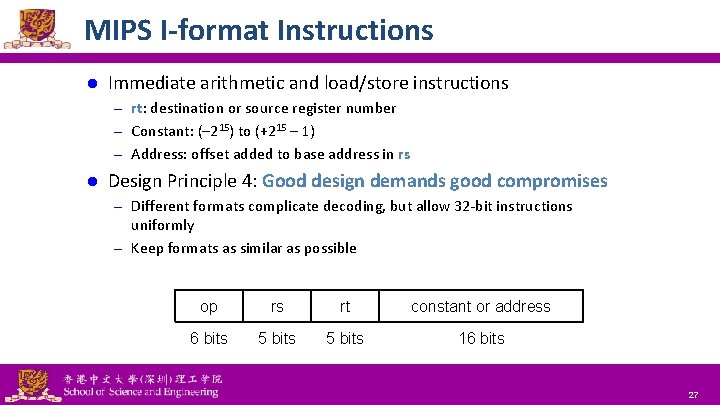
MIPS I-format Instructions l Immediate arithmetic and load/store instructions – rt: destination or source register number – Constant: (– 215) to (+215 – 1) – Address: offset added to base address in rs l Design Principle 4: Good design demands good compromises – Different formats complicate decoding, but allow 32 -bit instructions uniformly – Keep formats as similar as possible op rs rt constant or address 6 bits 5 bits 16 bits National Tsing Hua University ® copyright OIA 27

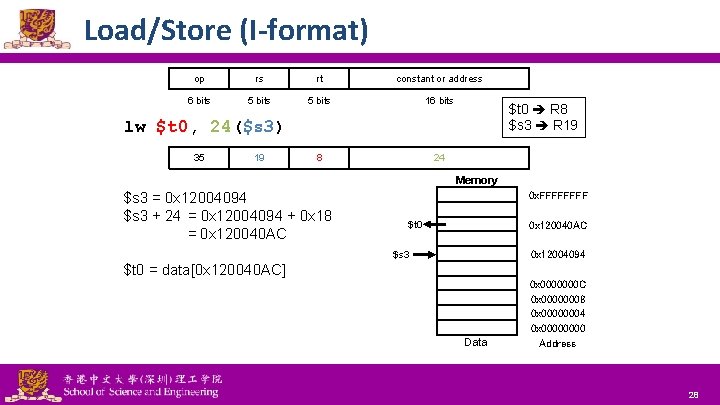
Load/Store (I-format) op rs rt constant or address 6 bits 5 bits 16 bits 8 24 $t 0 R 8 $s 3 R 19 lw $t 0, 24($s 3) 35 19 Memory $s 3 = 0 x 12004094 $s 3 + 24 = 0 x 12004094 + 0 x 18 = 0 x 120040 AC 0 x. FFFF $t 0 0 x 120040 AC $s 3 0 x 12004094 $t 0 = data[0 x 120040 AC] Data National Tsing Hua University ® copyright OIA 0 x 0000000 C 0 x 00000008 0 x 00000004 0 x 0000 Address 28

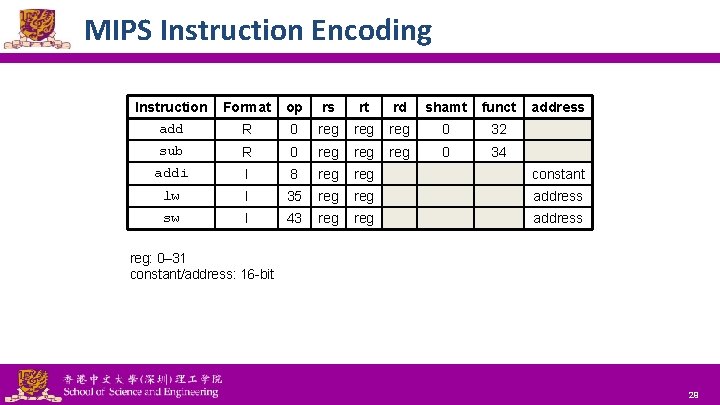
MIPS Instruction Encoding Instruction add Format op rs rt rd shamt funct address R 0 reg reg 0 32 sub R 0 reg reg 0 34 addi I 8 reg constant lw I 35 reg address sw I 43 reg address reg: 0– 31 constant/address: 16 -bit National Tsing Hua University ® copyright OIA 29
![Translating C Code to Machine Code 1 l C code A300 h Translating C Code to Machine Code (1) l C code: A[300] = h +](https://slidetodoc.com/presentation_image/1b93eb47d0d6092b356ba6f058399a99/image-30.jpg)
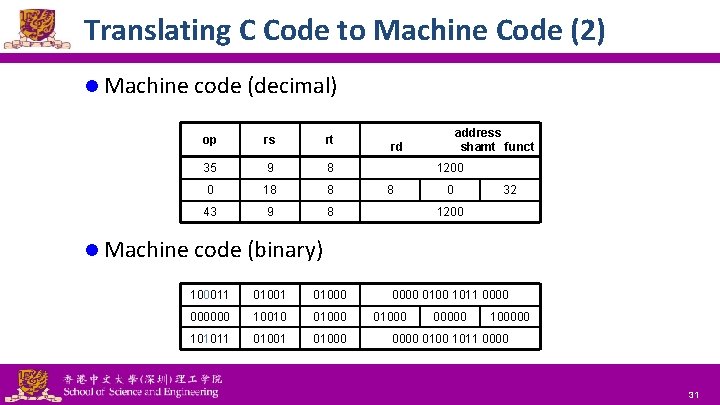
Translating C Code to Machine Code (1) l C code: A[300] = h + A[300]; – h in $s 2, base address of A in $t 1 l Compiled MIPS code: lw add sw l $t 0, 1200($t 1) $t 0, $s 2, $t 0, 1200($t 1) # $t 0 = A[300] # $t 0 = h + A[300] # A[300] = $t 0 Machine code: op rs rt 35 9 8 0 18 8 43 9 8 National Tsing Hua University ® copyright OIA rd address shamt funct 1200 8 0 32 1200 30

Translating C Code to Machine Code (2) l Machine code (decimal) address shamt funct op rs rt 35 9 8 0 18 8 43 9 8 1200 0000 0100 1011 0000 rd 1200 8 0 32 l Machine code (binary) 100011 01000 000000 10010 01000 101011 01000 National Tsing Hua University ® copyright OIA 01000 00000 100000 0100 1011 0000 31

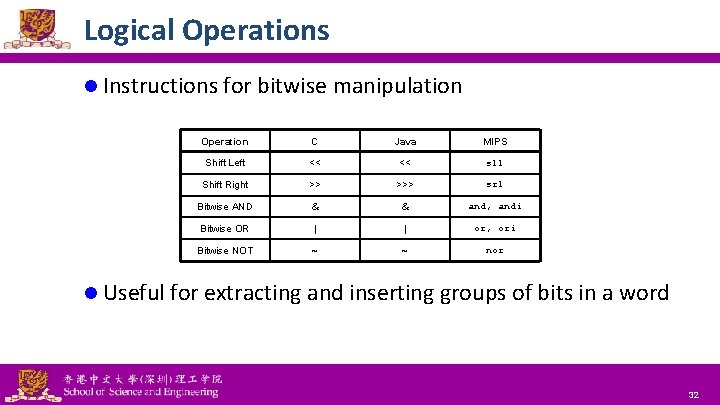
Logical Operations l Instructions for bitwise manipulation Operation C Java MIPS Shift Left << << sll Shift Right >> >>> srl Bitwise AND & & and, andi Bitwise OR | | or, ori Bitwise NOT ~ ~ nor l Useful for extracting and inserting groups of bits in a word National Tsing Hua University ® copyright OIA 32

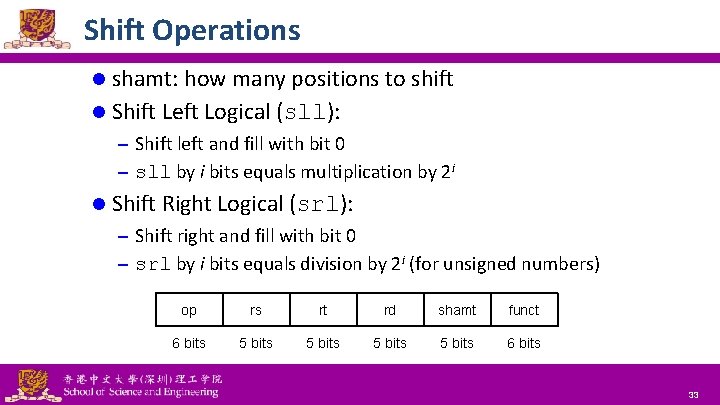
Shift Operations l shamt: how many positions to shift l Shift Left Logical (sll): – Shift left and fill with bit 0 – sll by i bits equals multiplication by 2 i l Shift Right Logical (srl): – Shift right and fill with bit 0 – srl by i bits equals division by 2 i (for unsigned numbers) op rs rt rd shamt funct 6 bits 5 bits 6 bits National Tsing Hua University ® copyright OIA 33

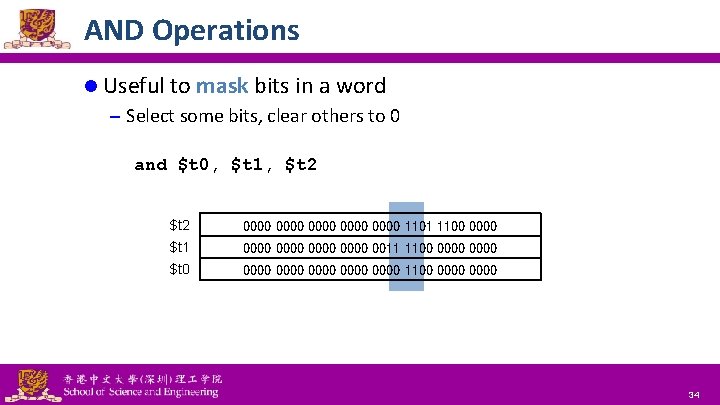
AND Operations l Useful to mask bits in a word – Select some bits, clear others to 0 and $t 0, $t 1, $t 2 0000 0000 1101 1100 0000 $t 1 0000 0011 1100 0000 $t 0 0000 0000 1100 0000 National Tsing Hua University ® copyright OIA 34

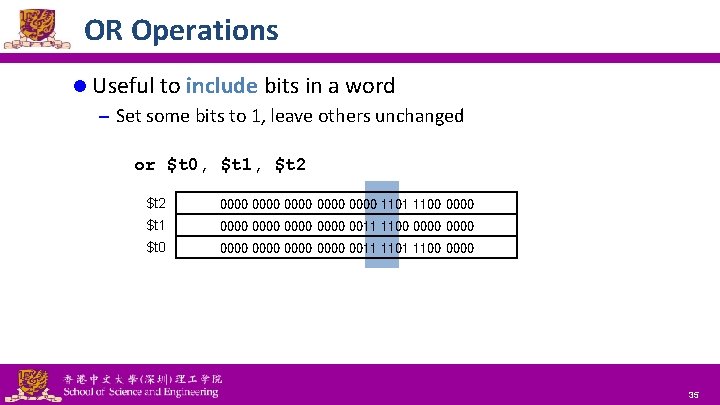
OR Operations l Useful to include bits in a word – Set some bits to 1, leave others unchanged or $t 0, $t 1, $t 2 0000 0000 1101 1100 0000 $t 1 0000 0011 1100 0000 $t 0 0000 0011 1100 0000 National Tsing Hua University ® copyright OIA 35

NOT Operations l Useful to invert bits in a word – Change 0 to 1, and 1 to 0 l MIPS has NOR 3 -operand instruction – a NOR b == NOT (a OR b) nor $t 0, $t 1, $zero $t 1 0000 0011 1100 0000 $t 0 1111 1100 0011 1111 National Tsing Hua University ® copyright OIA 36

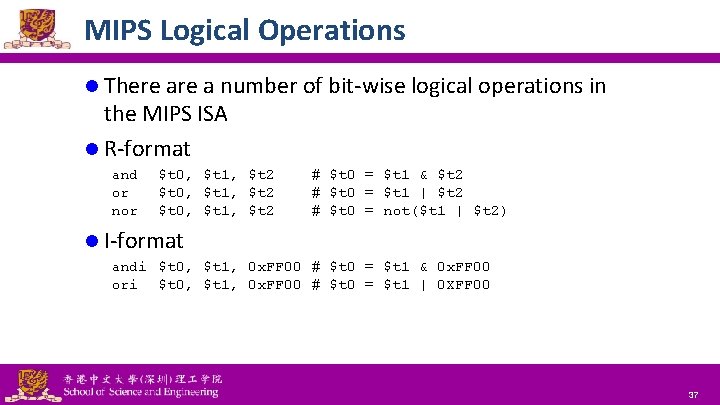
MIPS Logical Operations l There a number of bit-wise logical operations in the MIPS ISA l R-format and or nor $t 0, $t 1, $t 2 # $t 0 = $t 1 & $t 2 # $t 0 = $t 1 | $t 2 # $t 0 = not($t 1 | $t 2) l I-format andi $t 0, $t 1, 0 x. FF 00 # $t 0 = $t 1 & 0 x. FF 00 ori $t 0, $t 1, 0 x. FF 00 # $t 0 = $t 1 | 0 XFF 00 National Tsing Hua University ® copyright OIA 37

Conditional Operations l Branch to a labeled instruction if a condition is true – Otherwise, continue sequentially l beq rs, rt, L 1 – if (rs == rt) branch to instruction labeled L 1 l bne rs, rt, L 1 – if (rs != rt) branch to instruction labeled L 1 lj L 1 – unconditional jump to instruction labeled L 1 National Tsing Hua University ® copyright OIA 38

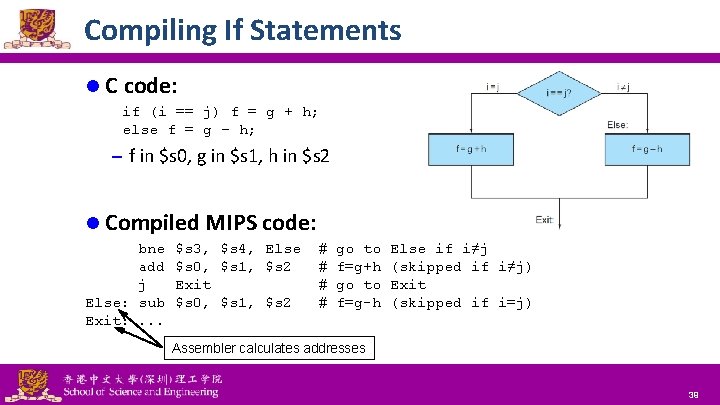
Compiling If Statements l C code: if (i == j) f = g + h; else f = g – h; – f in $s 0, g in $s 1, h in $s 2 l Compiled MIPS code: bne add j Else: sub Exit: . . . $s 3, $s 4, Else $s 0, $s 1, $s 2 Exit $s 0, $s 1, $s 2 # # go to f=g+h go to f=g-h Else if i≠j (skipped if i≠j) Exit (skipped if i=j) Assembler calculates addresses National Tsing Hua University ® copyright OIA 39
![Compiling Loop Statements l C code while savei k i 1 Compiling Loop Statements l C code: while (save[i] == k) i += 1; –](https://slidetodoc.com/presentation_image/1b93eb47d0d6092b356ba6f058399a99/image-40.jpg)
Compiling Loop Statements l C code: while (save[i] == k) i += 1; – i in $s 3, k in $s 5, address of save in $s 6 l Compiled MIPS code: Loop: sll add lw bne addi j Exit: . . . $t 1, $t 0, $s 3, Loop $s 3, 2 $t 1, $s 6 0($t 1) $s 5, Exit $s 3, 1 National Tsing Hua University ® copyright OIA # # # $t 1 = i * 4 $t 1 = addr of save[i] $t 0 = save[i] Exit if save[i]≠k i = i+1 go to Loop 40

Basic Blocks l A basic block is a sequence of instructions with – No embedded branches (except at end) – No branch targets (except at beginning) l A compiler identifies basic blocks for optimization National Tsing Hua University ® copyright OIA 41

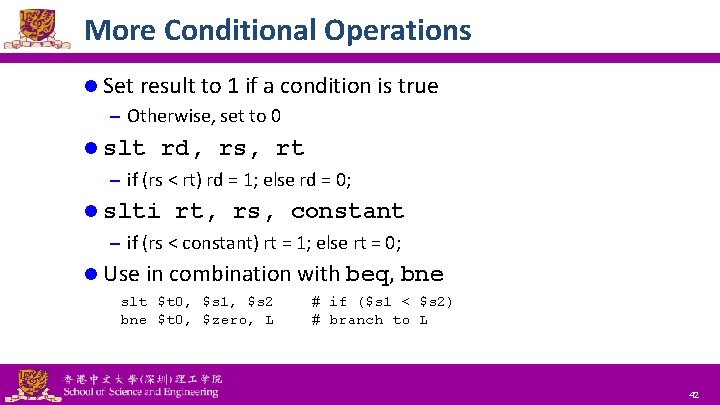
More Conditional Operations l Set result to 1 if a condition is true – Otherwise, set to 0 l slt rd, rs, rt – if (rs < rt) rd = 1; else rd = 0; l slti rt, rs, constant – if (rs < constant) rt = 1; else rt = 0; l Use in combination with beq, bne slt $t 0, $s 1, $s 2 bne $t 0, $zero, L National Tsing Hua University ® copyright OIA # if ($s 1 < $s 2) # branch to L 42

Branch Instruction Design l Why not blt, bge, etc? l Hardware for <, ≥, … slower than =, ≠ – Combining with branch involves more work per instruction, requiring a slower clock – All instructions penalized! l beq and bne are the common case l This is a good design compromise National Tsing Hua University ® copyright OIA 43

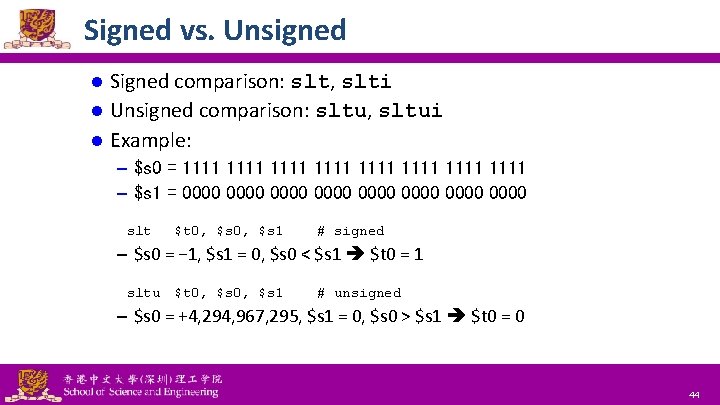
Signed vs. Unsigned Signed comparison: slt, slti l Unsigned comparison: sltu, sltui l Example: l – $s 0 = 1111 1111 – $s 1 = 0000 0000 slt $t 0, $s 1 # signed – $s 0 = − 1, $s 1 = 0, $s 0 < $s 1 $t 0 = 1 sltu $t 0, $s 1 # unsigned – $s 0 = +4, 294, 967, 295, $s 1 = 0, $s 0 > $s 1 $t 0 = 0 National Tsing Hua University ® copyright OIA 44

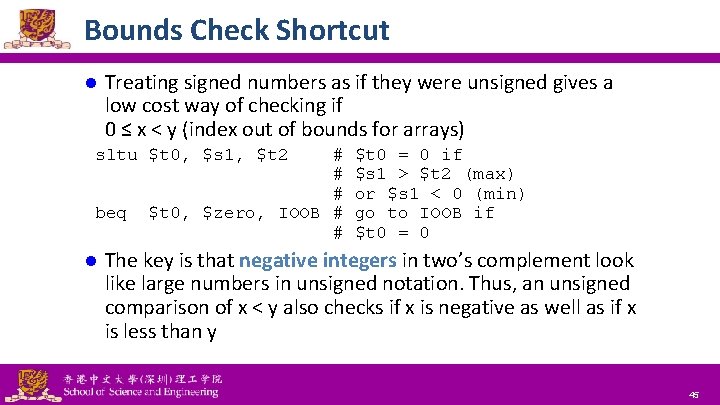
Bounds Check Shortcut l Treating signed numbers as if they were unsigned gives a low cost way of checking if 0 ≤ x < y (index out of bounds for arrays) sltu $t 0, $s 1, $t 2 beq l # # # $t 0, $zero, IOOB # # $t 0 = 0 if $s 1 > $t 2 (max) or $s 1 < 0 (min) go to IOOB if $t 0 = 0 The key is that negative integers in two’s complement look like large numbers in unsigned notation. Thus, an unsigned comparison of x < y also checks if x is negative as well as if x is less than y National Tsing Hua University ® copyright OIA 45

Procedure Calling 1. Main routine (caller) places parameters in a place where the procedure (callee) can access them – $a 0–$a 3: four argument registers Caller transfers control to the callee 3. Callee acquires the storage resources needed 4. Callee performs the desired task 5. Callee places the result value in a place where the caller can access it 2. – $v 0–$v 1: two value registers for result values 6. Callee returns control to the caller – $ra: one return address register to return to the point of origin National Tsing Hua University ® copyright OIA 46

Register Usage $a 0–$a 3: arguments (reg 4– 7) l $v 0, $v 1: result values (reg 2 and 3) l $t 0–$t 9: temporaries l – Can be overwritten by callee l $s 0–$s 7: saved – Must be saved/restored by callee $gp: global pointer for static data (reg 28) l $sp: stack pointer (reg 29) l $fp: frame pointer (reg 30) l $ra: return address (reg 31) l National Tsing Hua University ® copyright OIA 47

Procedure Call Instructions l Procedure call: jump and link (jal) jal Procedure. Label – Address of following instruction is put in $ra – Jumps to target address l Procedure return: jump register (jr) jr $ra – Copies $ra to program counter National Tsing Hua University ® copyright OIA 48

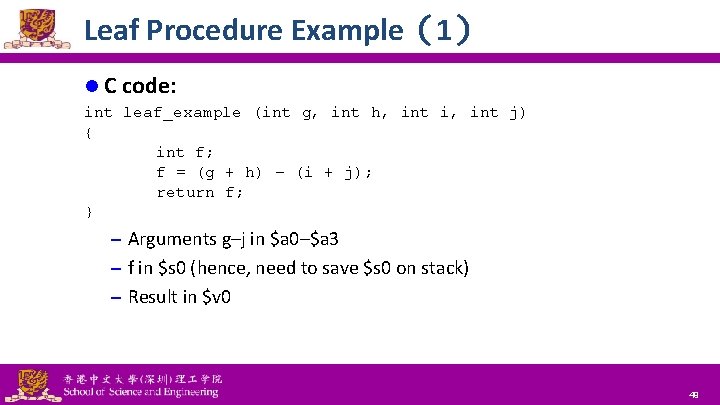
Leaf Procedure Example(1) l C code: int leaf_example (int g, int h, int i, int j) { int f; f = (g + h) – (i + j); return f; } – Arguments g–j in $a 0–$a 3 – f in $s 0 (hence, need to save $s 0 on stack) – Result in $v 0 National Tsing Hua University ® copyright OIA 49

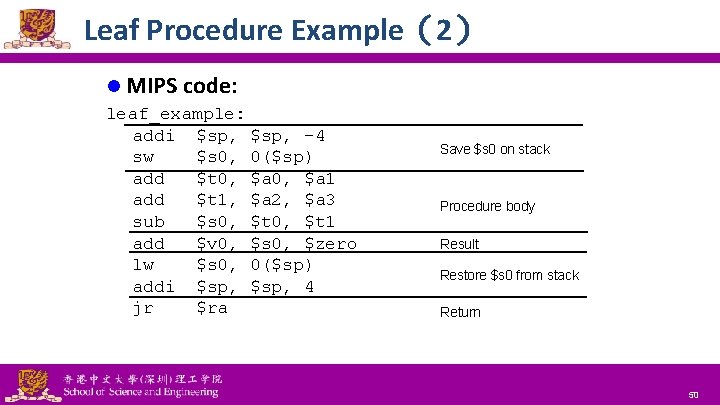
Leaf Procedure Example(2) l MIPS code: leaf_example: addi $sp, -4 sw $s 0, 0($sp) add $t 0, $a 1 add $t 1, $a 2, $a 3 sub $s 0, $t 1 add $v 0, $s 0, $zero lw $s 0, 0($sp) addi $sp, 4 jr $ra National Tsing Hua University ® copyright OIA Save $s 0 on stack Procedure body Result Restore $s 0 from stack Return 50

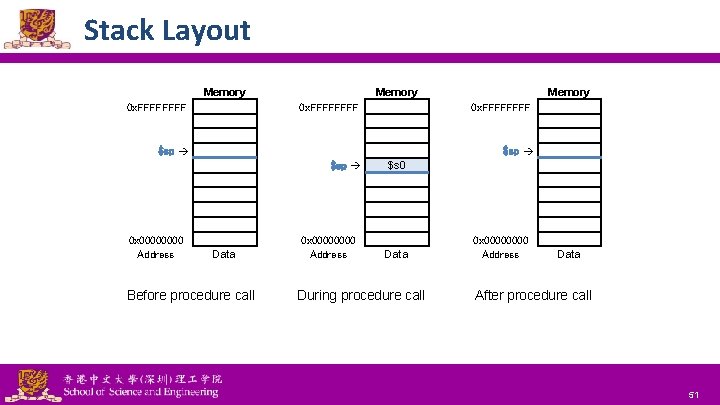
Stack Layout Memory 0 x. FFFFFFFF 0 x. FFFF $sp 0 x 0000 Address Memory Data Before procedure call National Tsing Hua University ® copyright OIA 0 x 0000 Address $s 0 Data During procedure call 0 x 0000 Address Data After procedure call 51

Non-Leaf Procedures l Procedures that call other procedures l For nested call, caller needs to save on the stack: – Its return address – Any arguments and temporaries needed after the call l Restore from the stack after the call National Tsing Hua University ® copyright OIA 52

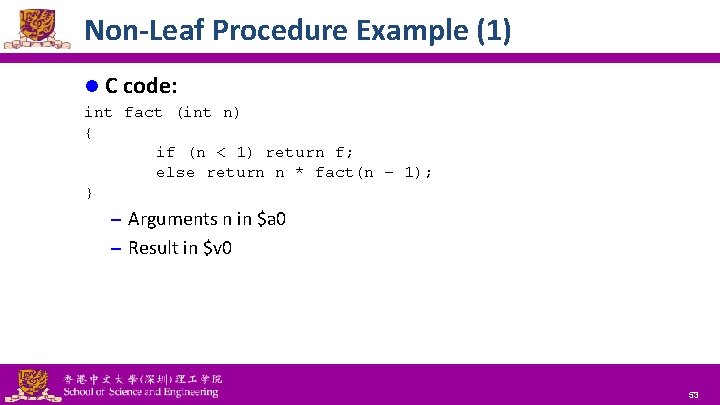
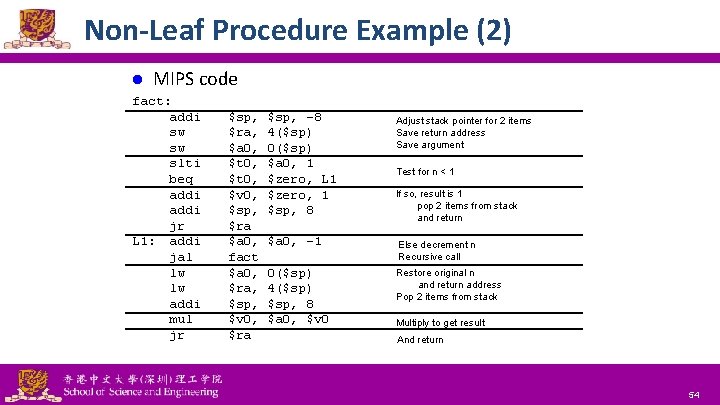
Non-Leaf Procedure Example (1) l C code: int fact (int n) { if (n < 1) return f; else return n * fact(n – 1); } – Arguments n in $a 0 – Result in $v 0 National Tsing Hua University ® copyright OIA 53

Non-Leaf Procedure Example (2) l MIPS code fact: addi sw sw slti beq addi jr L 1: addi jal lw lw addi mul jr $sp, $ra, $a 0, $t 0, $v 0, $sp, $ra $a 0, fact $a 0, $ra, $sp, $v 0, $ra National Tsing Hua University ® copyright OIA $sp, -8 4($sp) 0($sp) $a 0, 1 $zero, L 1 $zero, 1 $sp, 8 Adjust stack pointer for 2 items Save return address Save argument Test for n < 1 If so, result is 1 pop 2 items from stack and return $a 0, -1 Else decrement n Recursive call 0($sp) 4($sp) $sp, 8 $a 0, $v 0 Restore original n and return address Pop 2 items from stack Multiply to get result And return 54

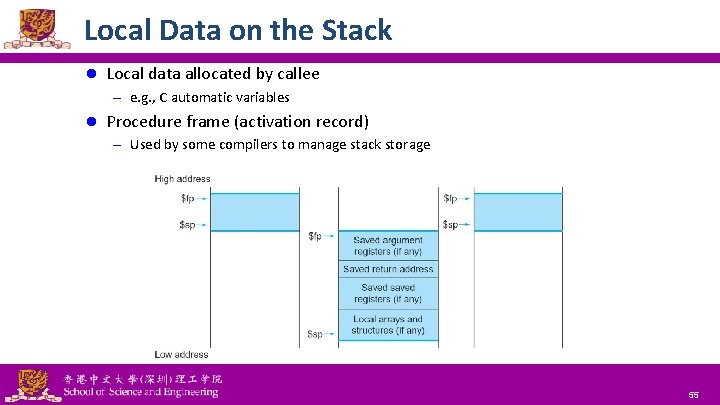
Local Data on the Stack l Local data allocated by callee – e. g. , C automatic variables l Procedure frame (activation record) – Used by some compilers to manage stack storage National Tsing Hua University ® copyright OIA 55

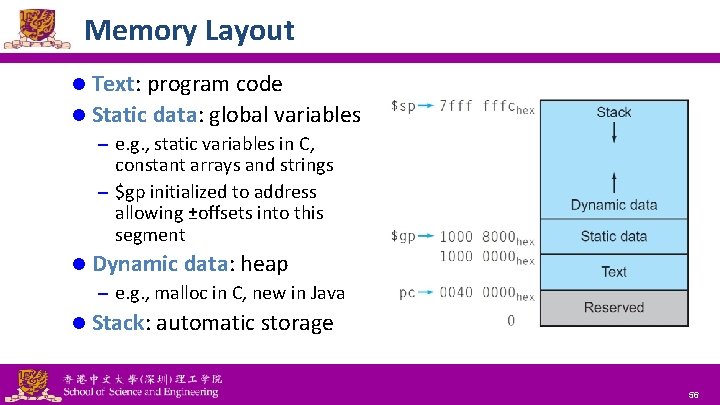
Memory Layout l Text: program code l Static data: global variables – e. g. , static variables in C, constant arrays and strings – $gp initialized to address allowing ±offsets into this segment l Dynamic data: heap – e. g. , malloc in C, new in Java l Stack: automatic storage National Tsing Hua University ® copyright OIA 56

Character Data l Byte-encoded character sets – ASCII: 128 characters • 95 graphic, 33 control – Latin-1: 256 characters • ASCII, +96 more graphic characters l Unicode: 32 -bit character set – Used in Java, C++ wide characters, … – Most of the world’s alphabets, plus symbols – UTF-8, UTF-16: variable-length encodings National Tsing Hua University ® copyright OIA 57

Byte/Halfword Operations l Could use bitwise operations l MIPS byte/halfword load/store – String processing is a common case lb rt, offset(rs) lh rt, offset(rs) – Sign extend to 32 bits in rt lbu rt, offset(rs) lhu rt, offset(rs) – Zero extend to 32 bits in rt sb rt, offset(rs) sh rt, offset(rs) – Store just rightmost byte/halfword National Tsing Hua University ® copyright OIA 58

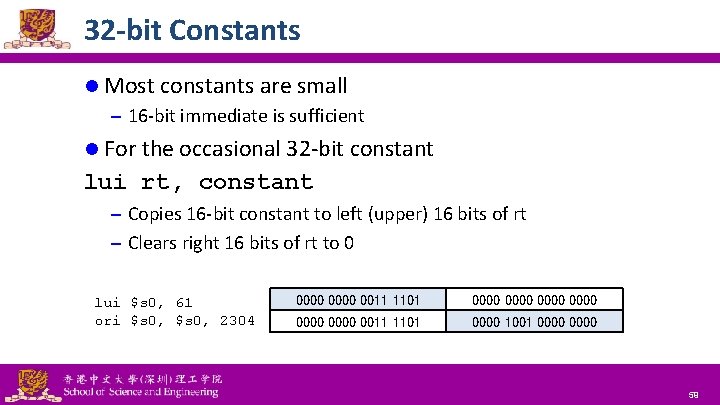
32 -bit Constants l Most constants are small – 16 -bit immediate is sufficient l For the occasional 32 -bit constant lui rt, constant – Copies 16 -bit constant to left (upper) 16 bits of rt – Clears right 16 bits of rt to 0 lui $s 0, 61 ori $s 0, 2304 National Tsing Hua University ® copyright OIA 0000 0011 1101 0000 0000 0011 1101 0000 1001 0000 59

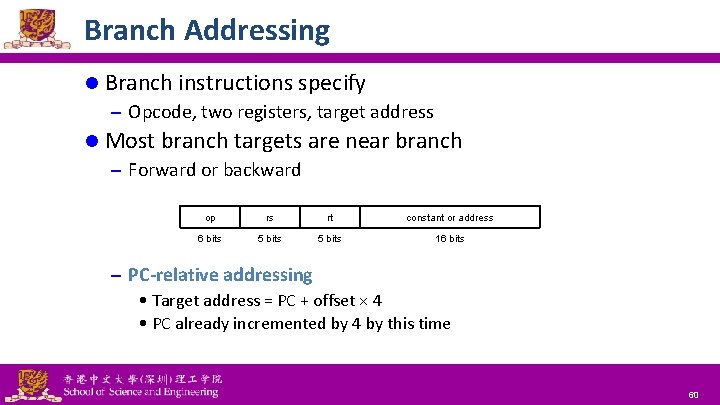
Branch Addressing l Branch instructions specify – Opcode, two registers, target address l Most branch targets are near branch – Forward or backward op rs rt constant or address 6 bits 5 bits 16 bits – PC-relative addressing • Target address = PC + offset × 4 • PC already incremented by 4 by this time National Tsing Hua University ® copyright OIA 60

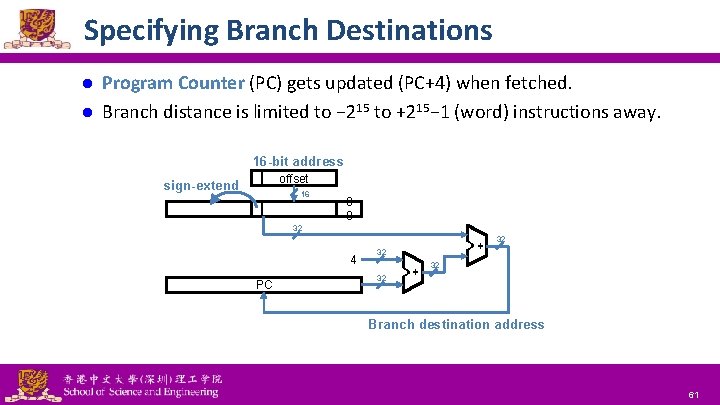
Specifying Branch Destinations Program Counter (PC) gets updated (PC+4) when fetched. l Branch distance is limited to − 215 to +215− 1 (word) instructions away. l 16 -bit address offset sign-extend 16 0 0 PC 32 32 + 4 + 32 32 32 Branch destination address National Tsing Hua University ® copyright OIA 61

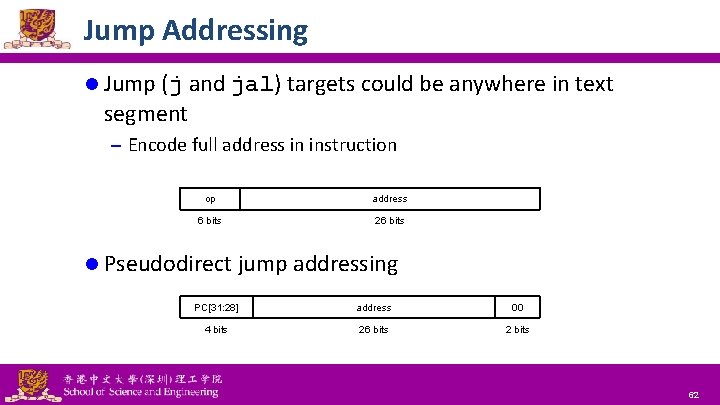
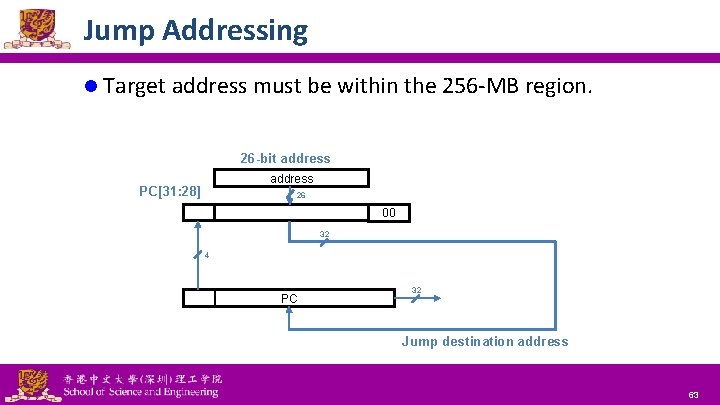
Jump Addressing l Jump (j and jal) targets could be anywhere in text segment – Encode full address in instruction op address 6 bits 26 bits l Pseudodirect jump addressing PC[31: 28] address 00 4 bits 26 bits 2 bits National Tsing Hua University ® copyright OIA 62

Jump Addressing l Target address must be within the 256 -MB region. 26 -bit address PC[31: 28] 26 00 32 4 PC 32 Jump destination address National Tsing Hua University ® copyright OIA 63

Branching Far Away l If branch target is too far to encode with 16 -bit offset, assembler rewrites the code: beq $s 0, $s 1, L 1 may be replaced by bne $s 0, $s 1, L 2 j L 1 L 2: . . . National Tsing Hua University ® copyright OIA 64

Addressing Mode Summary National Tsing Hua University ® copyright OIA 65

C Code Translation Hierachy National Tsing Hua University ® copyright OIA 66

MIPS Organization So Far National Tsing Hua University ® copyright OIA 67
 Isa meaning computer
Isa meaning computer 3050 in words
3050 in words Instruction set architecture in computer organization
Instruction set architecture in computer organization Total set awareness set consideration set
Total set awareness set consideration set Training set validation set test set
Training set validation set test set Lmc code examples
Lmc code examples Cisc complex instruction set computer
Cisc complex instruction set computer Risc instruction set example
Risc instruction set example Marie architecture
Marie architecture Mips instruction set architecture
Mips instruction set architecture Arm instruction set architecture
Arm instruction set architecture Which instruction set architecture is used in beaglebone?
Which instruction set architecture is used in beaglebone? Instruction set architecture
Instruction set architecture 430830
430830 Mips code
Mips code Riscv instruction set
Riscv instruction set Microarchitecture vs isa
Microarchitecture vs isa Isa 88 and isa 95
Isa 88 and isa 95 Wide isa vs narrow isa
Wide isa vs narrow isa Instruction format in computer architecture
Instruction format in computer architecture Instruction cycle in computer architecture
Instruction cycle in computer architecture Instruction pipelining in computer architecture
Instruction pipelining in computer architecture Instruction level parallelism in computer architecture
Instruction level parallelism in computer architecture Instruction format in computer architecture
Instruction format in computer architecture Instruction count is determined by isa and cpu hardware.
Instruction count is determined by isa and cpu hardware. Differentiated instruction vs individualized instruction
Differentiated instruction vs individualized instruction Direct vs indirect instruction
Direct vs indirect instruction Ax 86s
Ax 86s 8051 boolean processor
8051 boolean processor What are the two versions of sic?
What are the two versions of sic? Set instruksi
Set instruksi Xch instruction in 8051
Xch instruction in 8051 Assembly language
Assembly language Intel simd instructions
Intel simd instructions 8088 instruction set
8088 instruction set Ror instruction in 8086
Ror instruction in 8086 Classify instruction set of 8086
Classify instruction set of 8086 Data formats of ibm 360
Data formats of ibm 360 Ece 430
Ece 430 Lc3 opcodes
Lc3 opcodes Lc-3 isa
Lc-3 isa When bsr instruction is executed in 68k
When bsr instruction is executed in 68k Str lc3
Str lc3 Atmel avr 8 bit instruction set
Atmel avr 8 bit instruction set Sic xe instruction set
Sic xe instruction set Ia-64
Ia-64 Picoblaze instruction set
Picoblaze instruction set Data transfer instructions of 8085
Data transfer instructions of 8085 Dlx architecture
Dlx architecture Arquitetura risc e cisc
Arquitetura risc e cisc Instruction set
Instruction set Define instruction set
Define instruction set 8087 instruction set
8087 instruction set Sap-1 instruction set
Sap-1 instruction set Pic instruction set
Pic instruction set Instruction set of 8085
Instruction set of 8085 Arc instruction set
Arc instruction set Assembly language instruction set
Assembly language instruction set Motorola 68000 instruction set
Motorola 68000 instruction set 8086 instruction set
8086 instruction set Dlx instruction set
Dlx instruction set What is mips in computer architecture
What is mips in computer architecture Motorola 68k assembly
Motorola 68k assembly Atmel avr instruction set
Atmel avr instruction set Atmel avr instruction set
Atmel avr instruction set Semaphores
Semaphores Atmega32 instruction set
Atmega32 instruction set Instruction set characteristics
Instruction set characteristics