INSTRUCTION SET ARCHITECTURE CHAP 9 INSTRUCTION SET ARCHITECTURE


![Stack Instructions PUSH R 1 SP – 1 M[SP] R 1 POP R 1 Stack Instructions PUSH R 1 SP – 1 M[SP] R 1 POP R 1](https://slidetodoc.com/presentation_image_h2/95c76044258f7b8d153625517409a593/image-15.jpg)






![Processing external interrupts Microinstructions to implement an interrupt SP – 1 M[SP] PC SP Processing external interrupts Microinstructions to implement an interrupt SP – 1 M[SP] PC SP](https://slidetodoc.com/presentation_image_h2/95c76044258f7b8d153625517409a593/image-36.jpg)
- Slides: 36

INSTRUCTION SET ARCHITECTURE CHAP 9

INSTRUCTION SET ARCHITECTURE • COMPLEX INSTRUCTION SET COMPUTERS (CISCs) – Provide hardware support for high-level language – Have compact programs • REDUCED INSTRUCTION SET COMPUTERS (RISCs) – Simple instructions – Flexibility – Faster execution

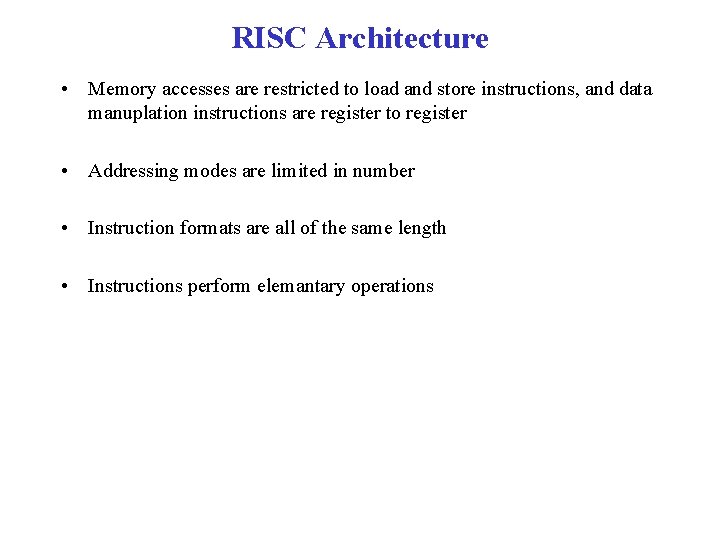
RISC Architecture • Memory accesses are restricted to load and store instructions, and data manuplation instructions are register to register • Addressing modes are limited in number • Instruction formats are all of the same length • Instructions perform elemantary operations

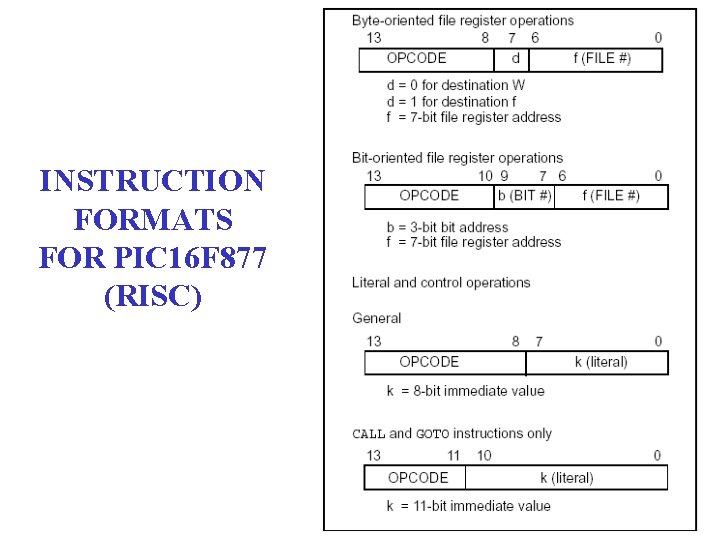
INSTRUCTION FORMATS FOR PIC 16 F 877 (RISC)

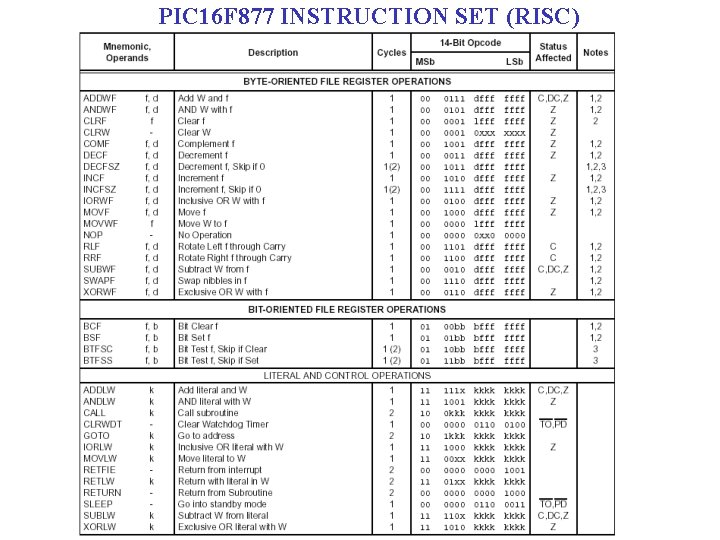
PIC 16 F 877 INSTRUCTION SET (RISC)

CISC Architecture • Memory access is directly available to most types of instruction • Addressing modes are substantial in number • Instruction formats are of different lenghts • Instructions perform both elemantary and complex operations

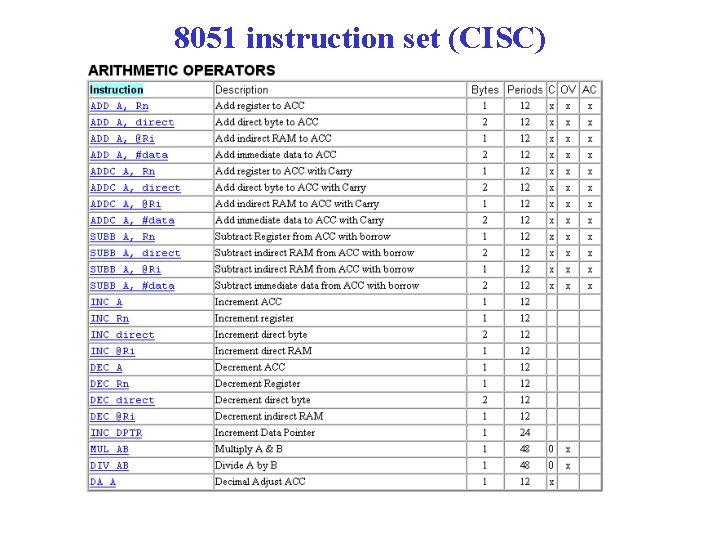
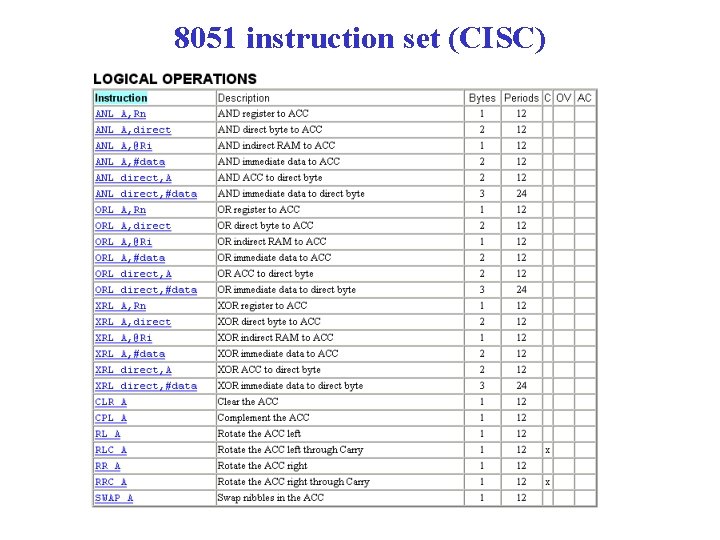
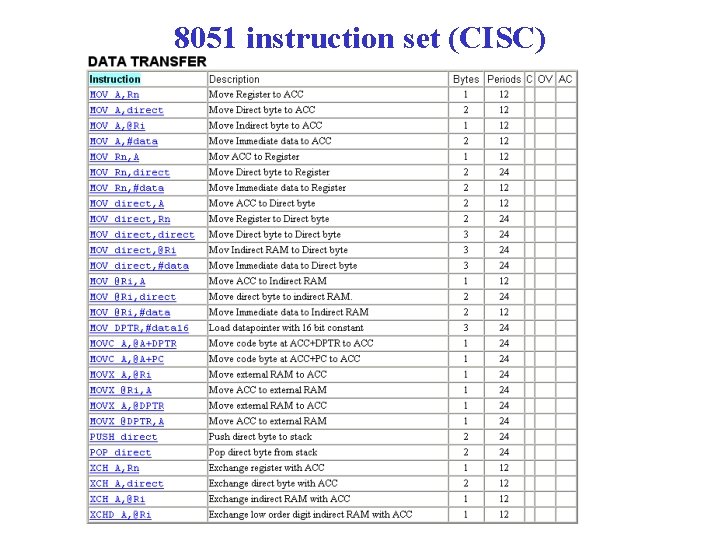
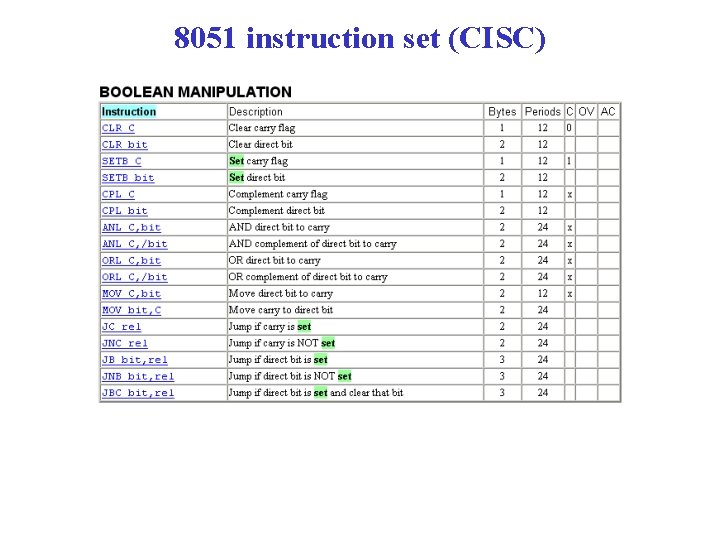
8051 instruction set (CISC)

8051 instruction set (CISC)

8051 instruction set (CISC)

8051 instruction set (CISC)

Instruction set architectures • CISC – Compact programs and conserve memory – Efficiencies in performance may result through a reductionin the number of instruction fetches from memory, compared to the number of elementary operations performed. – Because of the high memory accessibility, the register files in a CISC are smaller than in a RISC – Because of complexity of the instructions and the variability of the instruction formats, microprogrammed control is often used. – For speed, a pipelined control is used. – CISC instructions are converted to a sequence of RISC-like operations that are procesed by the RISC like pipeline.

Elementary computer instructions • There is a basic set of elementary operations that most computers include them • Basic set instructions categories: – Data transfer instructions – Data manupulation instructions – Program control instructions

Data Transfer Instructions • Moving data from one place in the computer to another without changing the content of the data. – Registers Memory – Registers Register – Memory • Assembly language abbreviation recommended by an IEEE standart. Different computers, however, may use different mnemonics for the same instruction name.

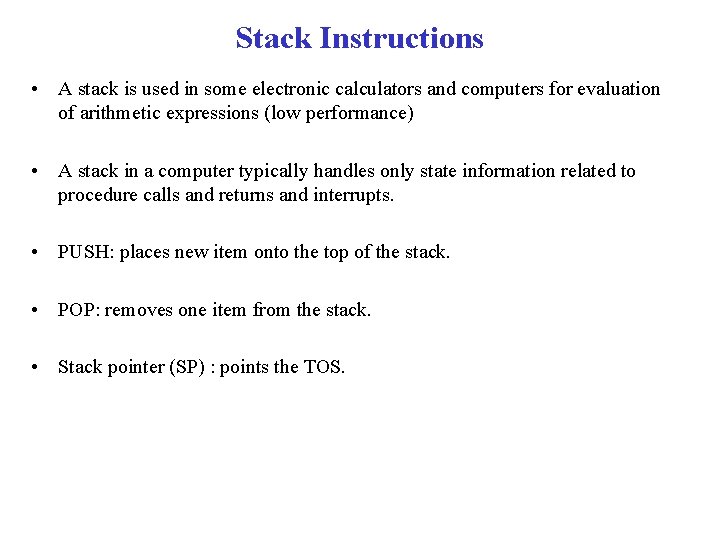
Stack Instructions • A stack is used in some electronic calculators and computers for evaluation of arithmetic expressions (low performance) • A stack in a computer typically handles only state information related to procedure calls and returns and interrupts. • PUSH: places new item onto the top of the stack. • POP: removes one item from the stack. • Stack pointer (SP) : points the TOS.
![Stack Instructions PUSH R 1 SP 1 MSP R 1 POP R 1 Stack Instructions PUSH R 1 SP – 1 M[SP] R 1 POP R 1](https://slidetodoc.com/presentation_image_h2/95c76044258f7b8d153625517409a593/image-15.jpg)
Stack Instructions PUSH R 1 SP – 1 M[SP] R 1 POP R 1 M[SP] SP +1 Two microinstruction needed for PUSH and POP

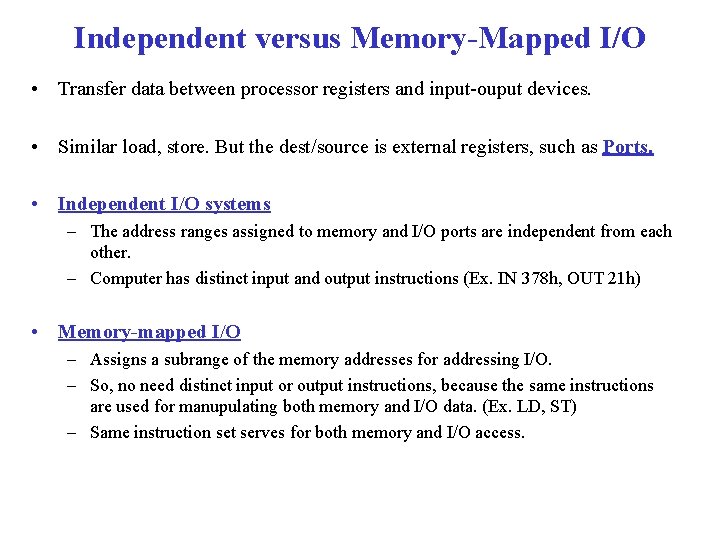
Independent versus Memory-Mapped I/O • Transfer data between processor registers and input-ouput devices. • Similar load, store. But the dest/source is external registers, such as Ports. • Independent I/O systems – The address ranges assigned to memory and I/O ports are independent from each other. – Computer has distinct input and output instructions (Ex. IN 378 h, OUT 21 h) • Memory-mapped I/O – Assigns a subrange of the memory addresses for addressing I/O. – So, no need distinct input or output instructions, because the same instructions are used for manupulating both memory and I/O data. (Ex. LD, ST) – Same instruction set serves for both memory and I/O access.

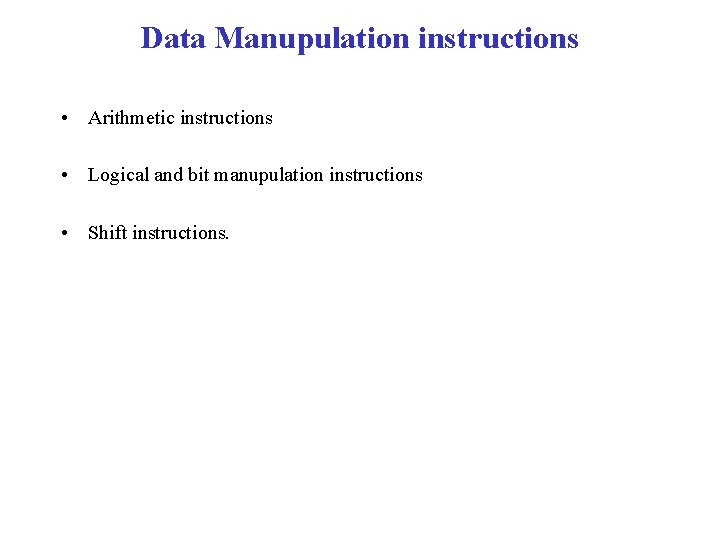
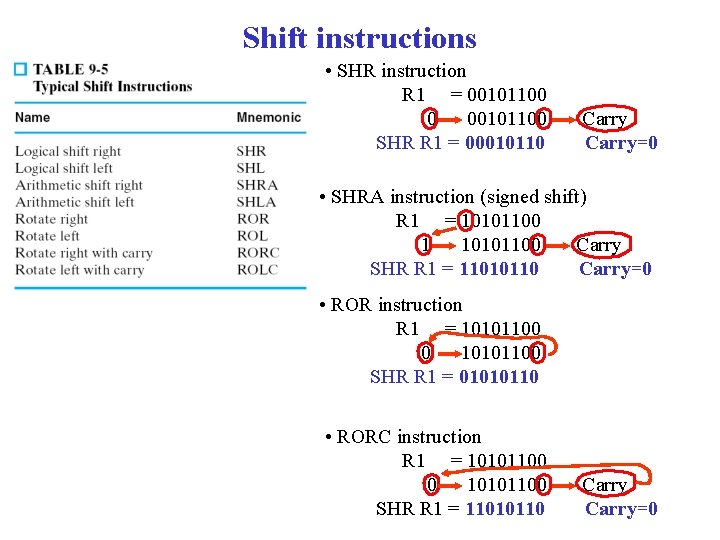
Data Manupulation instructions • Arithmetic instructions • Logical and bit manupulation instructions • Shift instructions.

Arithmetic instructions • Double precision arithmetic • “Add with carry” instructions

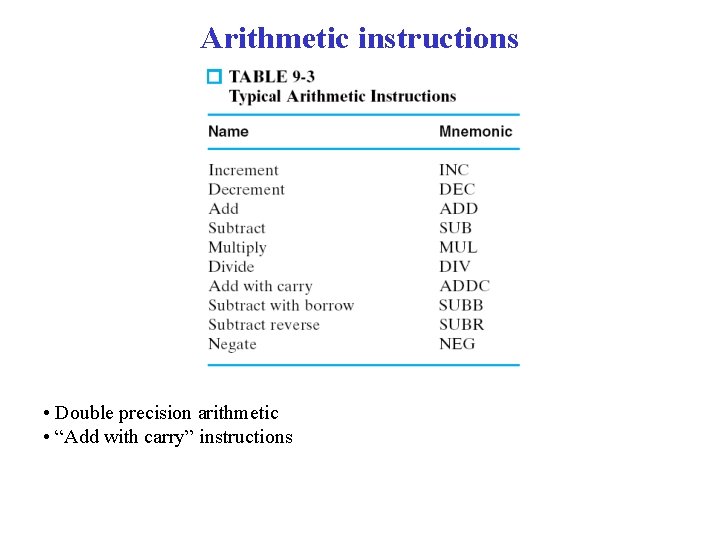
Logical and bit manupulation instructions • AND instruction also called a “mask”. R 1 = 00101100 Mask = 00001111 R 1 AND Mask = 00001100 • OR instruction also called a “bit set”. R 1 = 00101100 Mask = 00001111 R 1 AND Mask = 00101111 • XOR instruction also called a “bit complement”. R 1 = 00101100 Mask = 00001111 R 1 AND Mask = 00100011

Shift instructions • SHR instruction R 1 = 00101100 0 00101100 SHR R 1 = 00010110 Carry=0 • SHRA instruction (signed shift) R 1 = 10101100 1 10101100 Carry SHR R 1 = 11010110 Carry=0 • ROR instruction R 1 = 10101100 0 10101100 SHR R 1 = 01010110 • RORC instruction R 1 = 10101100 0 10101100 SHR R 1 = 11010110 Carry=0

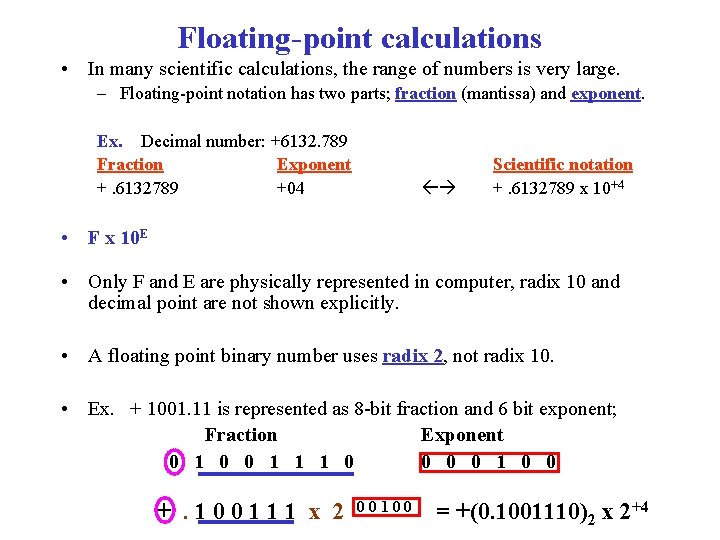
Floating-point calculations • In many scientific calculations, the range of numbers is very large. – Floating-point notation has two parts; fraction (mantissa) and exponent. Ex. Decimal number: +6132. 789 Fraction Exponent +. 6132789 +04 Scientific notation +. 6132789 x 10+4 • F x 10 E • Only F and E are physically represented in computer, radix 10 and decimal point are not shown explicitly. • A floating point binary number uses radix 2, not radix 10. • Ex. + 1001. 11 is represented as 8 -bit fraction and 6 bit exponent; Fraction Exponent 0 1 0 0 1 1 1 0 0 +. 100111 x 2 00100 = +(0. 1001110)2 x 2+4

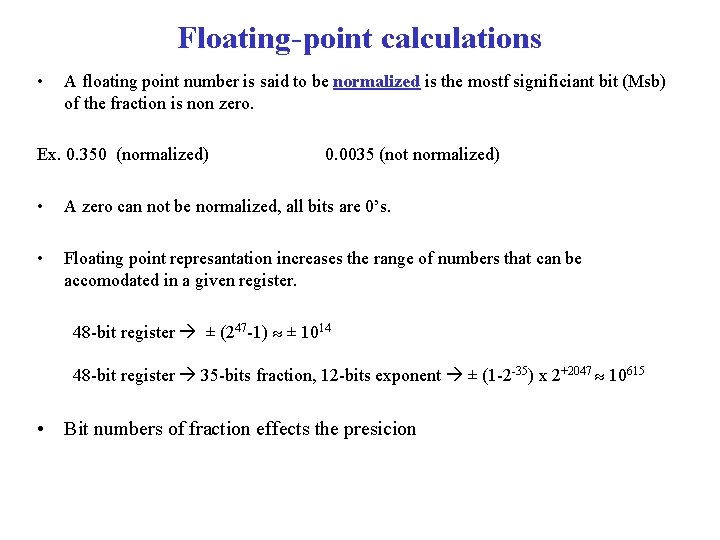
Floating-point calculations • A floating point number is said to be normalized is the mostf significiant bit (Msb) of the fraction is non zero. Ex. 0. 350 (normalized) 0. 0035 (not normalized) • A zero can not be normalized, all bits are 0’s. • Floating point represantation increases the range of numbers that can be accomodated in a given register. 48 -bit register ± (247 -1) ± 1014 48 -bit register 35 -bits fraction, 12 -bits exponent ± (1 -2 -35) x 2+2047 10615 • Bit numbers of fraction effects the presicion

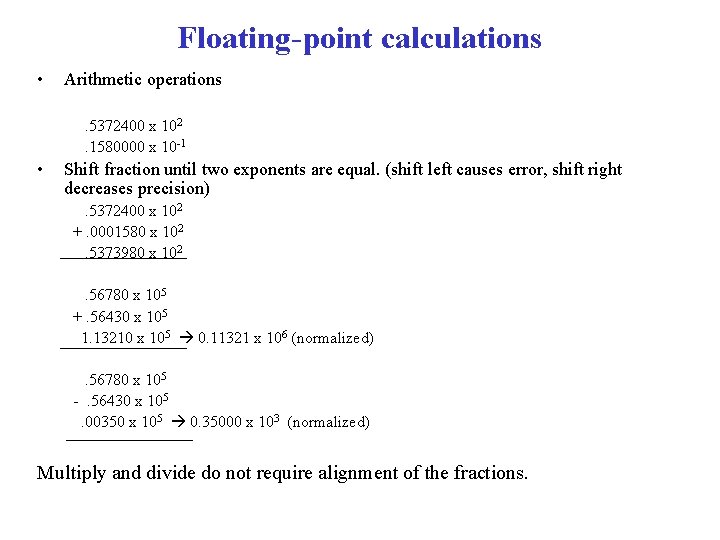
Floating-point calculations • Arithmetic operations. 5372400 x 102. 1580000 x 10 -1 • Shift fraction until two exponents are equal. (shift left causes error, shift right decreases precision). 5372400 x 102 +. 0001580 x 102. 5373980 x 102. 56780 x 105 +. 56430 x 105 1. 13210 x 105 0. 11321 x 106 (normalized). 56780 x 105 -. 56430 x 105. 00350 x 105 0. 35000 x 103 (normalized) Multiply and divide do not require alignment of the fractions.

Floating-point calculations • Biased Exponent – The sign and fraction part of a floating point number is usually a signedmagnitude representetion. The exponent representation emplyoed in most computers is known as a biased exponent. e = E + bias Ex. Decimal exponent is – 99 to +99. e = - 99 + 99 = 0 for – 99 e = 99 + 99 = 198 for +99 Then bias is 99. • Floating point number contain only positive exonents. • It is then simpler to compare without concerning signs.

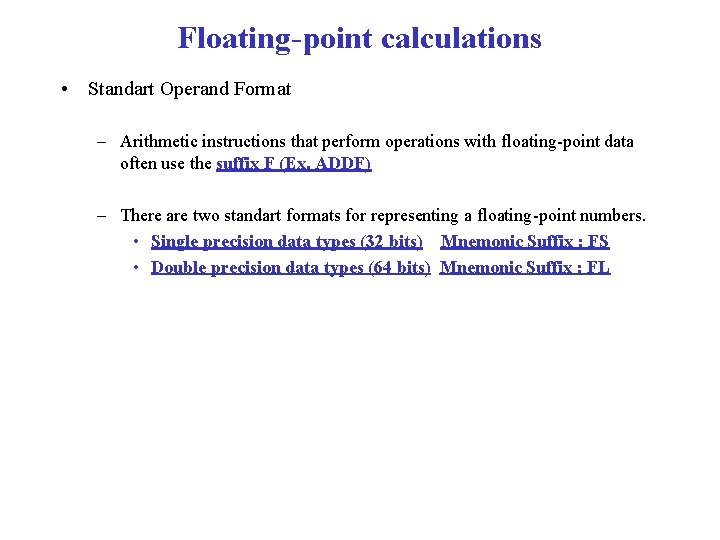
Floating-point calculations • Standart Operand Format – Arithmetic instructions that perform operations with floating-point data often use the suffix F (Ex. ADDF) – There are two standart formats for representing a floating-point numbers. • Single precision data types (32 bits) Mnemonic Suffix : FS • Double precision data types (64 bits) Mnemonic Suffix : FL

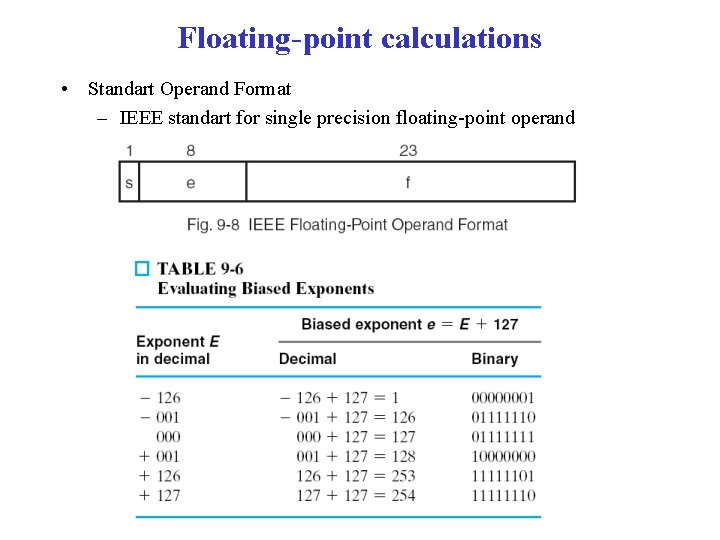
Floating-point calculations • Standart Operand Format – IEEE standart for single precision floating-point operand

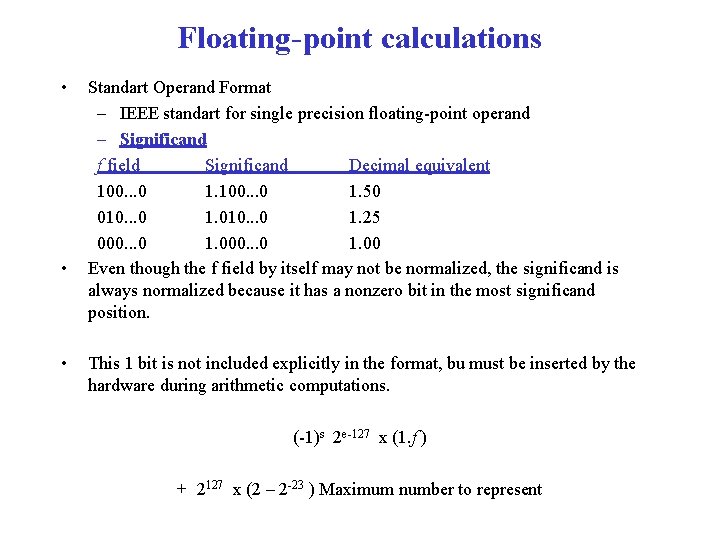
Floating-point calculations • • • Standart Operand Format – IEEE standart for single precision floating-point operand – Significand f field Significand Decimal equivalent 100. . . 0 1. 50 010. . . 0 1. 25 000. . . 0 1. 00 Even though the f field by itself may not be normalized, the significand is always normalized because it has a nonzero bit in the most significand position. This 1 bit is not included explicitly in the format, bu must be inserted by the hardware during arithmetic computations. (-1)s 2 e-127 x (1. f ) + 2127 x (2 – 2 -23 ) Maximum number to represent

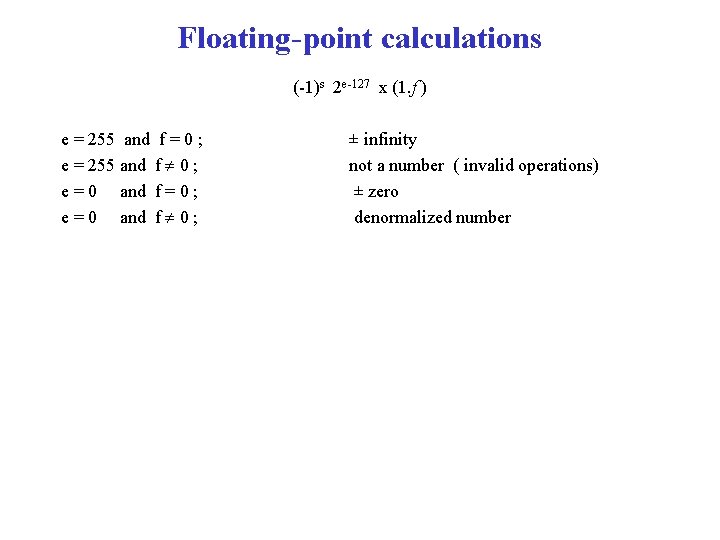
Floating-point calculations (-1)s 2 e-127 x (1. f ) e = 255 and f = 0 ; e = 255 and f 0 ; e = 0 and f = 0 ; e = 0 and f 0 ; ± infinity not a number ( invalid operations) ± zero denormalized number

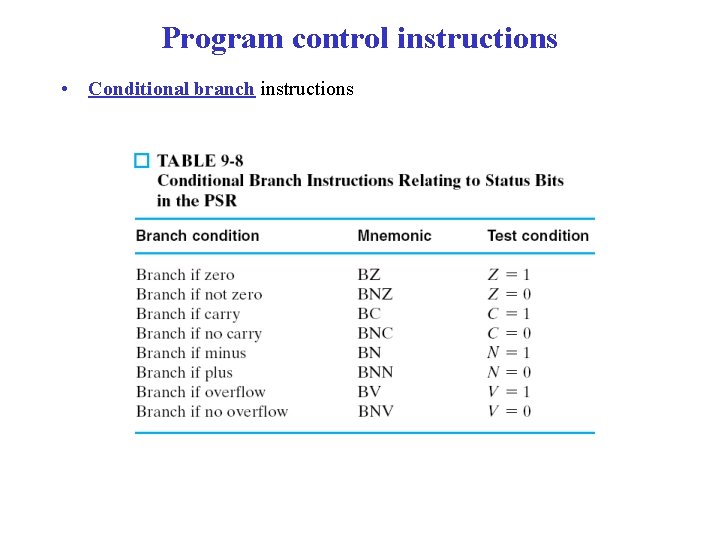
Program control instructions

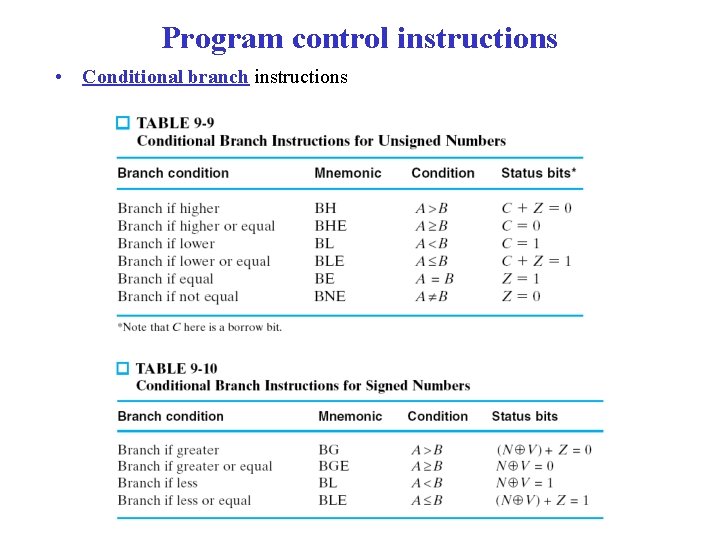
Program control instructions • Conditional branch instructions

Program control instructions • Conditional branch instructions

Program control instructions • Procedure Call and Return Instructions – A procedure is also called subroutine • Call procedure instructions performs two operations: – Stores PC value in temporary register (like stack) as a return address. – Load PC with the procedure address • Call SP - 1 M[SP] PC PC Efective address • Return PC M[SP] SP + 1

Program Interrupt • A program interrupt (kesme) is used to handle a variety of situations that require a departure from the normal program sequence. • A program interrupt transfers the control from a program that is currently running to another service program as a result of an externally- or internally generated request. • In principle interrupt procedure is similar to a call procedure – The interrupt usually initiated at an upredictable point in the program by an external or internal signal. – The address of the service program that processes the interrupt request is determined by a hardware procedure, rather than address field of an instruction – In response to interrupt, it is necessary to store information that defines all or part of the contents the register set, rather than storing only PC

Program Interrupt • After computer has been interrupted and the appropriate service program executed, the computer must return to exactly the same state that it was in before the interrupt occured. • Some computers store only the PC. Other storing operations must do by the user. • Most computers will not respond to an interrupt until the instruction which currently executed is completed. Then, just before going to fetch the next instruction, the control checks for any interut signals. If an interrupt has occured, control goes to a hardware interrupt cycle. During this cycle , the contents of some part or all of register set and PC are pushed onto stack.

Program interrupt • Types of Interrupts: – External interrupts • • Input output devices timing devices from a circuit monitoring power supply or any other external sources – Internal interrupts • Arises from illegal or erroneous use of an instruction or data • Called traps, overflow, divide by zero, stack overflow etc. – Software interrupts • Initiated by an instruction • A special call instruction that behaves like an interrupt rather than a procedure call. İt can be used by the programmer to initiate an interrupt procedure at any desired point in the program. • Example DOS interrupts functions (timer tick interrupt)
![Processing external interrupts Microinstructions to implement an interrupt SP 1 MSP PC SP Processing external interrupts Microinstructions to implement an interrupt SP – 1 M[SP] PC SP](https://slidetodoc.com/presentation_image_h2/95c76044258f7b8d153625517409a593/image-36.jpg)
Processing external interrupts Microinstructions to implement an interrupt SP – 1 M[SP] PC SP SP-1 M[SP] PSR EI 0 INTACK 1 PC IVAD