The Hierarchy of Key Evolving Signatures and a










- Slides: 30

The Hierarchy of Key Evolving Signatures and a Characterization of Proxy Signatures Tal Malkin (Columbia Univ. ) Satoshi Obana (NEC and Columbia Univ. ) Moti Yung (Columbia Univ. )

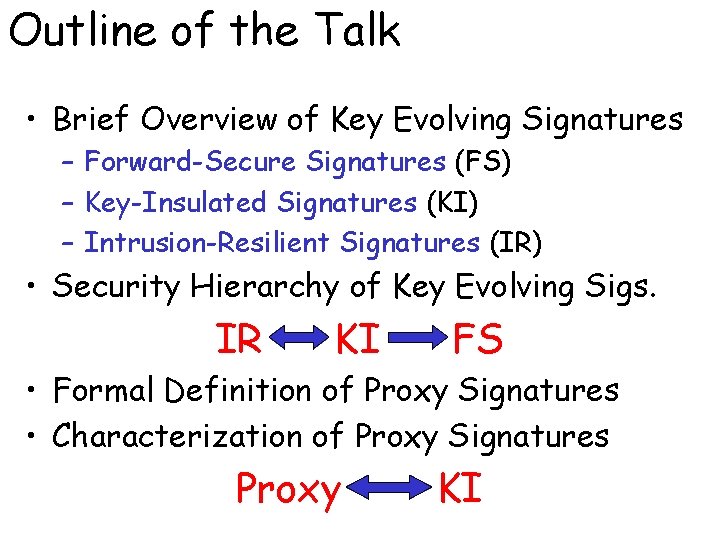
Outline of the Talk • Brief Overview of Key Evolving Signatures – Forward-Secure Signatures (FS) – Key-Insulated Signatures (KI) – Intrusion-Resilient Signatures (IR) • Security Hierarchy of Key Evolving Sigs. IR KI FS • Formal Definition of Proxy Signatures • Characterization of Proxy Signatures Proxy KI

The Hierarchy of Key Evolving Signatures

Key Evolving Signatures • Localize damage of secret key exposure – Splitting time into periods: 0, 1, …, T – Updating secret (signing) key for each period without changing public (verification) key • Several models exist (for different settings and different security goals) – Forward-Secure Signatures (FS) [And 97, BM 99] – Key-Insulated Signatures (KI) [DKXY 02] – Intrusion-Resilient Signatures (IR) [IR 02]

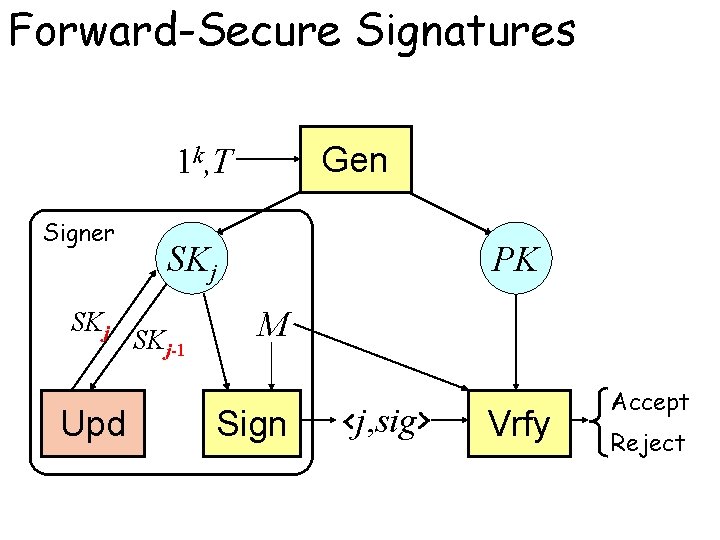
Forward-Secure Signatures Gen 1 k, T Signer SKj Upd SK SKj-1 0 j SKj-1 PK M Sign <j, sig> Vrfy Accept Reject

Security of FS Signature • The adversary has access to – The signing oracle Osig(M, i) outputs the valid signature for the message M in the time period i – The key exposure oracle Osec(“s”, j) outputs the secret key SKj of the time period j • The adversary successfully breaks the scheme if it outputs (M, <i, s>) s. t. – (M, i) is never queried to the signing oracle – (“s”, i’) is never queried to the key exposure oracle such that i’< i

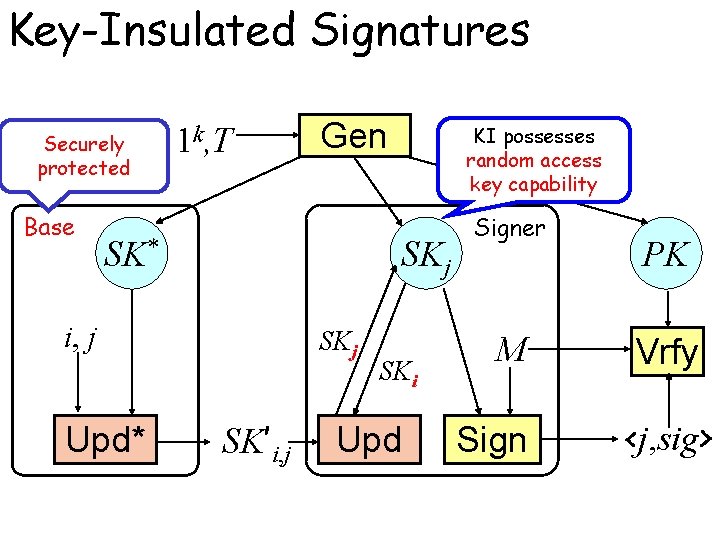
Key-Insulated Signatures Securely protected Base 1 k, T Gen SK* SK 0 ji i, j Upd* KI possesses random access key capability SKj SK’i, j SKi Upd Signer M Sign PK Vrfy <j, sig>

Security of KI Signature • The adversary has access to – The signing oracle Osig(M, i) outputs the valid signature for the message M in the time period i – The key exposure oracle Osec(“s”, j) outputs the secret key SKj of the time period j • The adversary successfully breaks the scheme if it outputs (M, <i, s>) s. t. – (M, i) is never queried to the signing oracle – (“s”, i) is never queried to the key exposure oracle

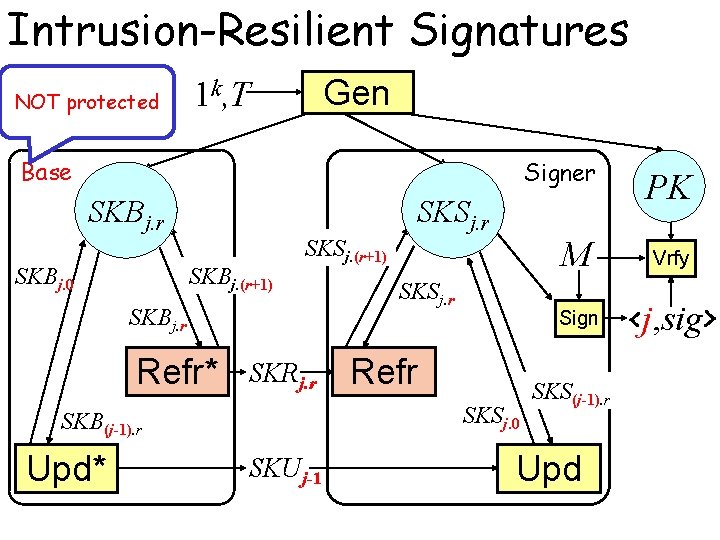
Intrusion-Resilient Signatures NOT protected Gen 1 k, T Base Signer SKB SKB j. (r+1) (j-1). r 0. 0 j. r SKBj. 0 SKS SKS j. (r+1) (j-1). r 0. 0 j. r SKBj. (r+1) SKSj. (r+1) SKBj. r Refr* SKRj. r Refr SKSj. 0 SKB(j-1). r Upd* SKSj. r SKUj-1 PK M Vrfy Sign <j, sig> SKS(j-1). r Upd

Security of IR Signature • The adversary has access to – The signing oracle Osig(M, i. r) outputs Sign(SKSi, r, M) – The key exposure oracle Osec(query) outputs • SKSj, r if query=(“s”, j. r) • SKBj. r if query=(“b”, j. r) • SKUj and SKRj+1. 0 if query=(“u”, j) • SKRj. r if query=(“r”, j. r) • The adversary successfully breaks the scheme if it outputs (M, <i, s>) s. t. – (M, i) is never queried to the signing oracle – SKSi, r is not exposed by the oracle calls – No SKSi’. r’ and SKBi’. r’ are exposed by the oracle calls for any i’<i

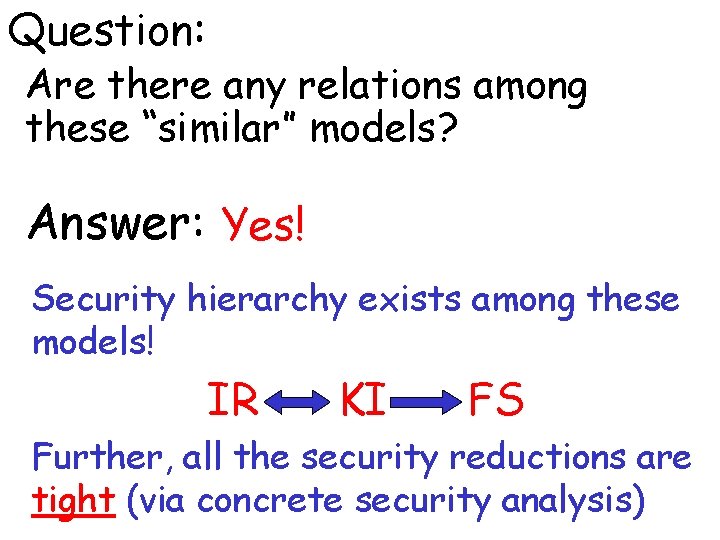
Question: Are there any relations among these “similar” models? Answer: Yes! Security hierarchy exists among these models! IR KI FS Further, all the security reductions are tight (via concrete security analysis)

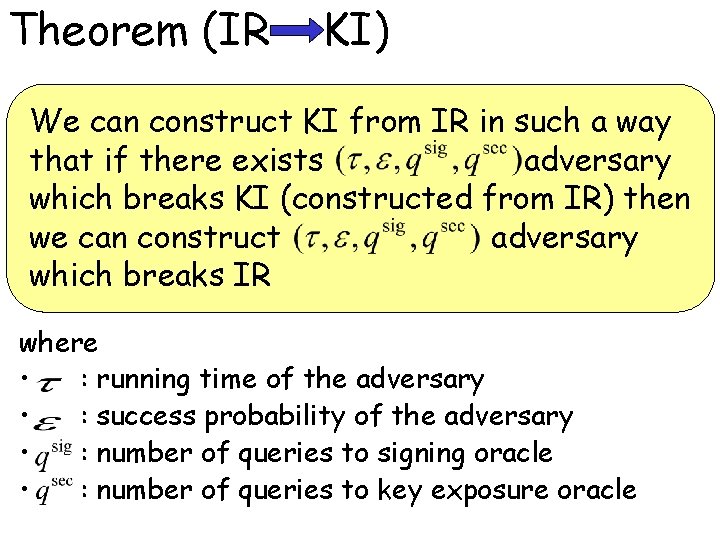
Theorem (IR KI) We can construct KI from IR in such a way that if there exists adversary which breaks KI (constructed from IR) then we can construct adversary which breaks IR where • : running time of the adversary • : success probability of the adversary • : number of queries to signing oracle • : number of queries to key exposure oracle

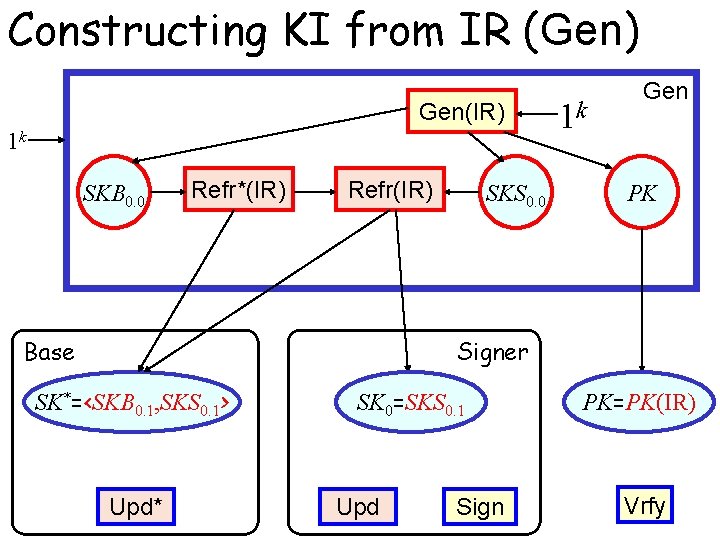
Constructing KI from IR (Gen) Gen(IR) 1 k SKB 0. 0 Refr*(IR) Refr(IR) Base SKS 0. 0 1 k Gen PK Signer SK*=<SKB 0. 1, SKS 0. 1> Upd* SK 0=SKS 0. 1 Upd Sign PK=PK(IR) Vrfy

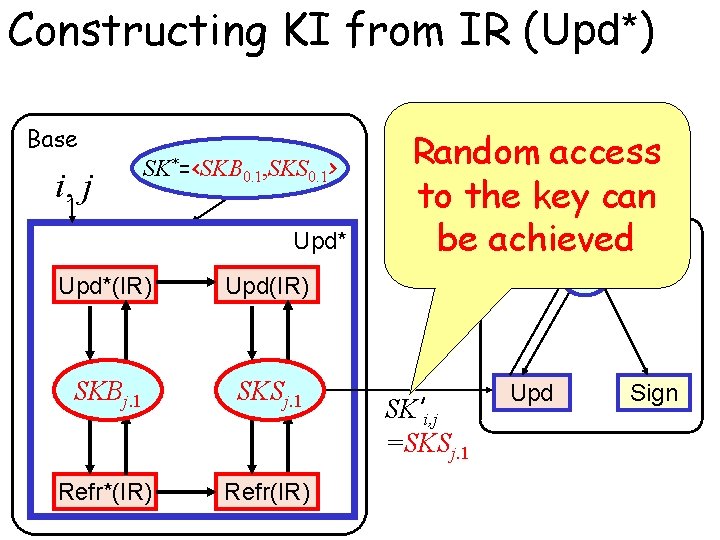
Constructing KI from IR (Upd*) Base i, j SK*=<SKB 0. 1, SKS 0. 1> Upd*(IR) Upd(IR) SKB 3. 1 0. 1 1. 0 1. 1 2. 0 2. 1 3. 0 j. 1 SKS 3. 1 0. 1 1. 0 1. 1 2. 0 2. 1 3. 0 j. 1 Refr*(IR) Refr(IR) Random access to the key can Signer be achieved SKi SK’i, j =SKSj. 1 Upd Sign

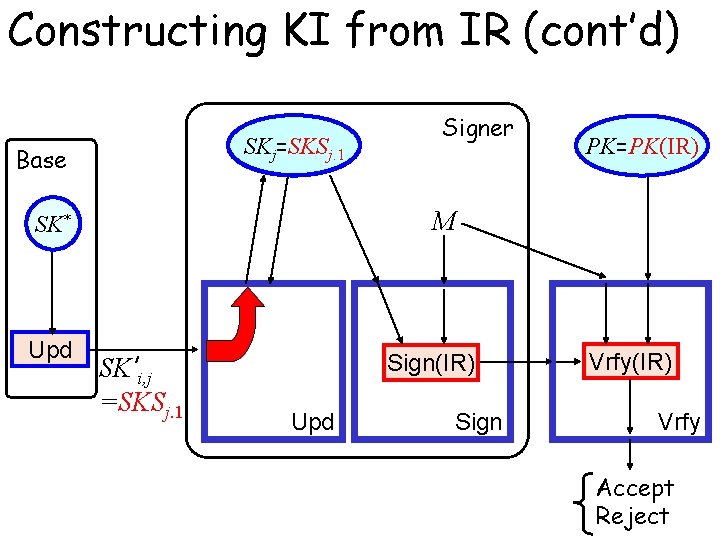
Constructing KI from IR (cont’d) SKji=SKSj. 1 i. 1 Base PK=PK(IR) M SK* Upd Signer SK’i, j =SKSj. 1 Sign(IR) Upd Sign Vrfy(IR) Vrfy Accept Reject

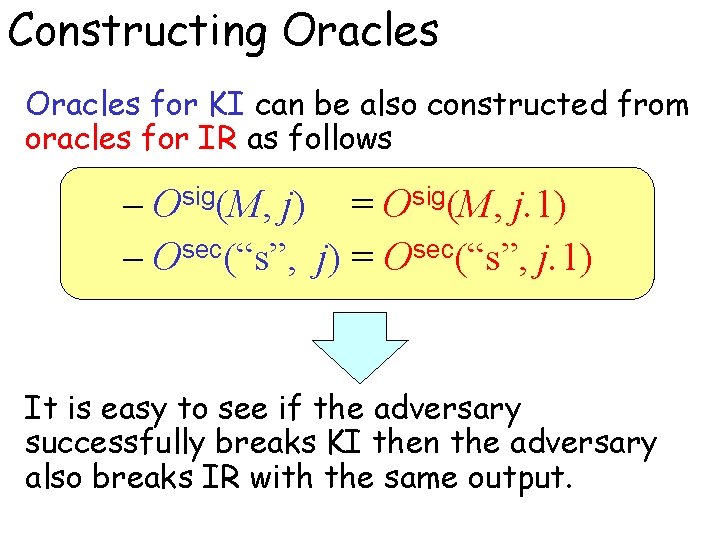
Constructing Oracles for KI can be also constructed from oracles for IR as follows – Osig(M, j) = Osig(M, j. 1) – Osec(“s”, j) = Osec(“s”, j. 1) It is easy to see if the adversary successfully breaks KI then the adversary also breaks IR with the same output.

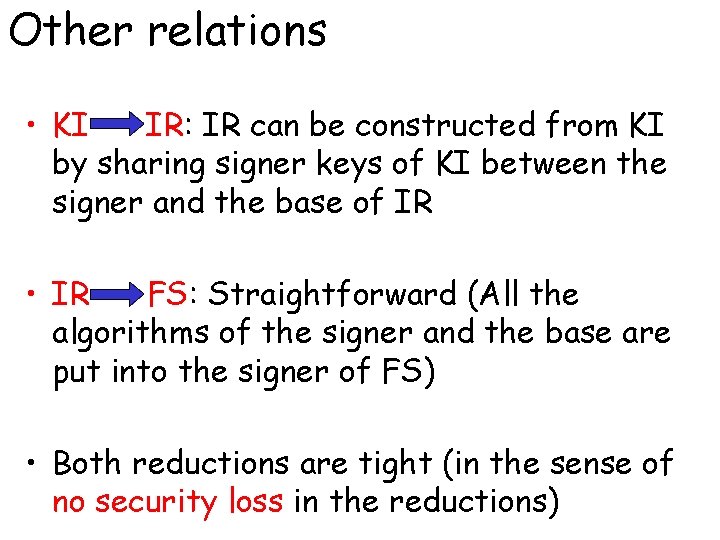
Other relations • KI IR: IR can be constructed from KI by sharing signer keys of KI between the signer and the base of IR • IR FS: Straightforward (All the algorithms of the signer and the base are put into the signer of FS) • Both reductions are tight (in the sense of no security loss in the reductions)

A Characterization of Proxy Signatures

Proxy Signatures • Method of giving (partial) signing right of an entity (delegator) to the others (proxy signer) • A lot of schemes have been proposed so far but a few of them are proven to be secure • No formal model exists (except [BPW 03] which gives a formal model for one-level delegation)

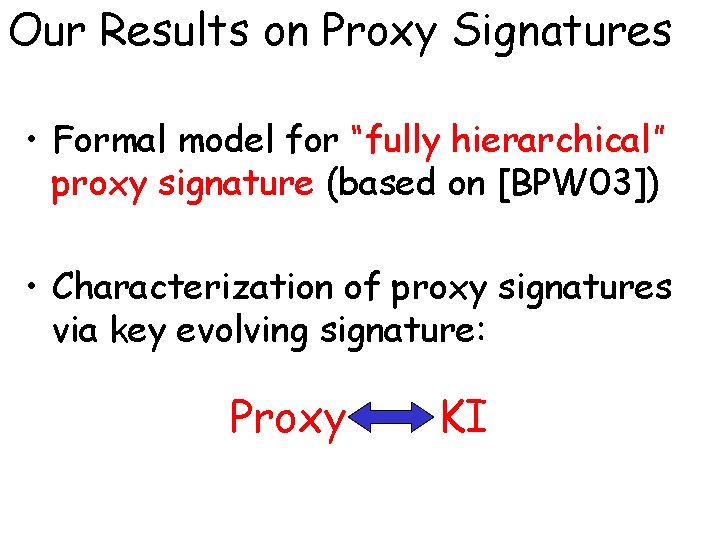
Our Results on Proxy Signatures • Formal model for “fully hierarchical” proxy signature (based on [BPW 03]) • Characterization of proxy signatures via key evolving signature: Proxy KI

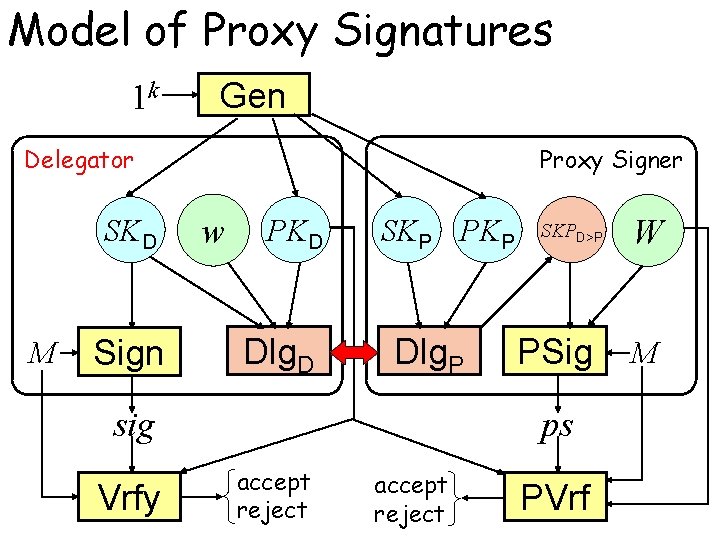
Model of Proxy Signatures 1 k Gen Delegator SKD M Sign Proxy Signer w PKD Dlg. D SKP PKP Dlg. P sig Vrfy SKPD>P PSig ps accept reject PVrf W M

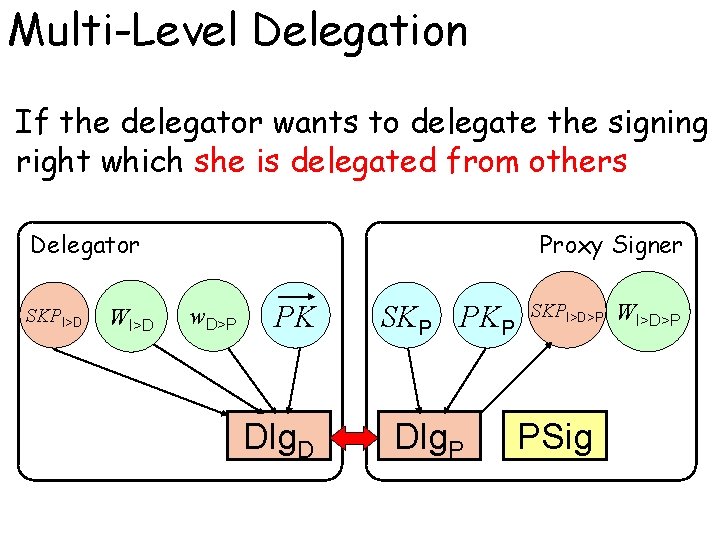
Multi-Level Delegation If the delegator wants to delegate the signing right which she is delegated from others Delegator SKPI>D WI>D Proxy Signer w. D>P PK Dlg. D SKP PKP Dlg. P SKPI>D>P PSig WI>D>P

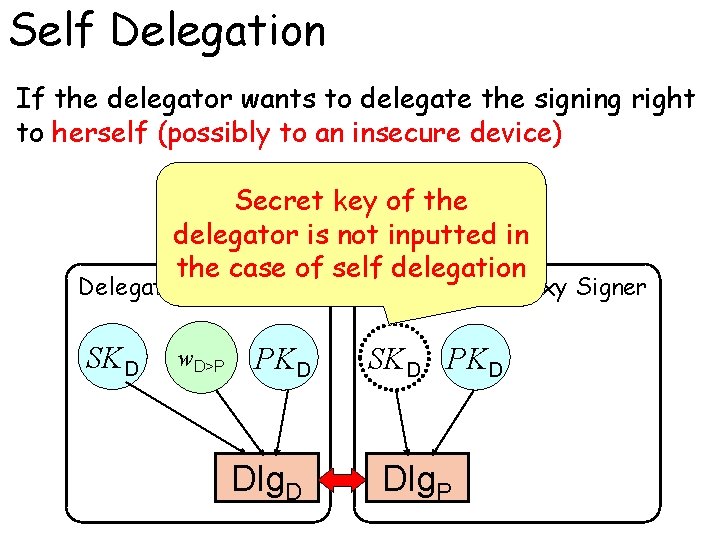
Self Delegation If the delegator wants to delegate the signing right to herself (possibly to an insecure device) Secret key of the delegator is not inputted in the case of self delegation Delegator SKD w. D>P Proxy Signer PKD Dlg. D SKD PKD Dlg. P

Security def. of Proxy Signatures The adversary has access to – Signing Oracle Osig – Key exposure Oracle Osec – Delegation Oracle ODlg interacts with the adversary on behalf of Dlg. D or Dlg. P Proxy signature is secure if the adversary cannot forge a proxy signature (non-proxy signature) when the adversary cannot compute the proxy signing key and the warrant (signing key) through the queries to the oracles

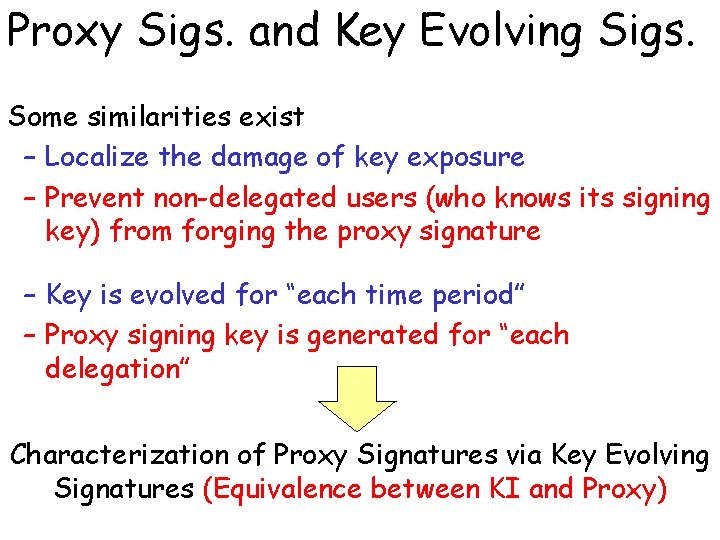
Proxy Sigs. and Key Evolving Sigs. Some similarities exist – Localize the damage of key exposure – Prevent non-delegated users (who knows its signing key) from forging the proxy signature – Key is evolved for “each time period” – Proxy signing key is generated for “each delegation” Characterization of Proxy Signatures via Key Evolving Signatures (Equivalence between KI and Proxy)

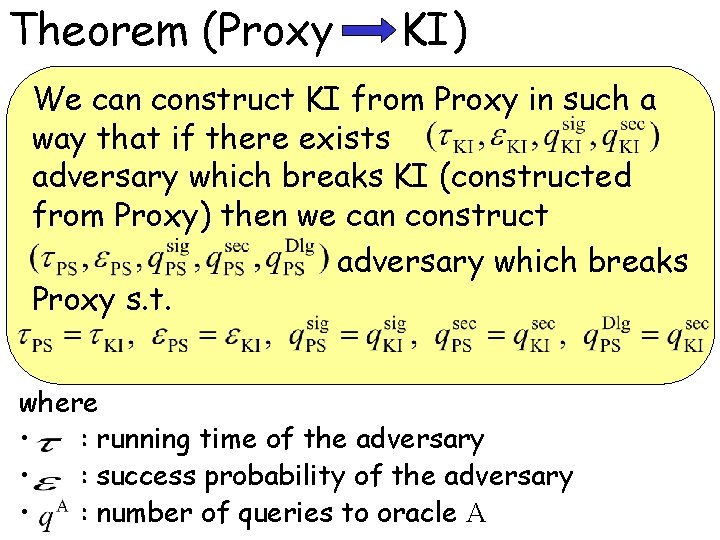
Theorem (Proxy KI) We can construct KI from Proxy in such a way that if there exists adversary which breaks KI (constructed from Proxy) then we can construct adversary which breaks Proxy s. t. where • : running time of the adversary • : success probability of the adversary • : number of queries to oracle A

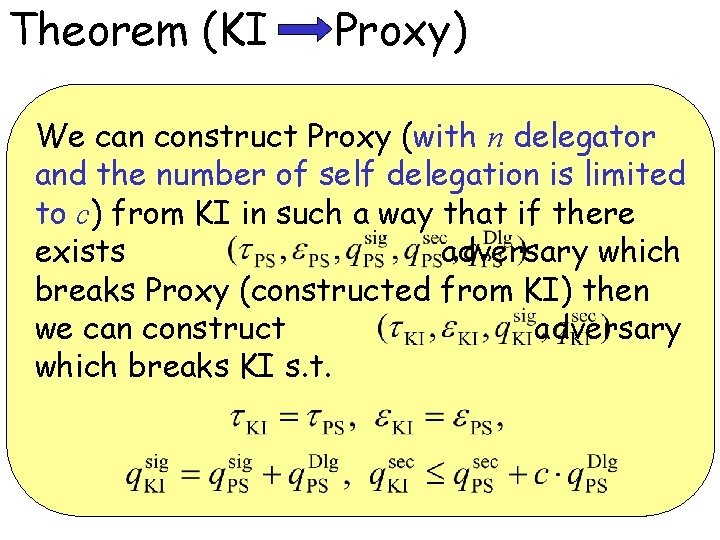
Theorem (KI Proxy) We can construct Proxy (with n delegator and the number of self delegation is limited to c) from KI in such a way that if there exists adversary which breaks Proxy (constructed from KI) then we can construct adversary which breaks KI s. t.

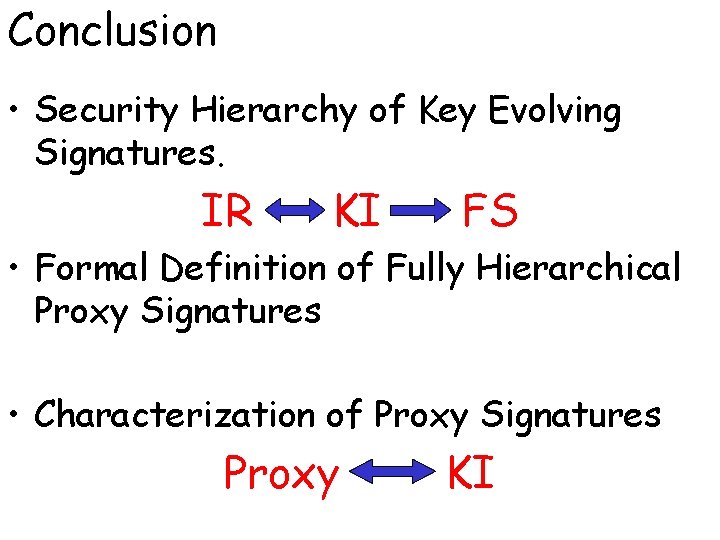
Conclusion • Security Hierarchy of Key Evolving Signatures. IR KI FS • Formal Definition of Fully Hierarchical Proxy Signatures • Characterization of Proxy Signatures Proxy KI

Thank you!

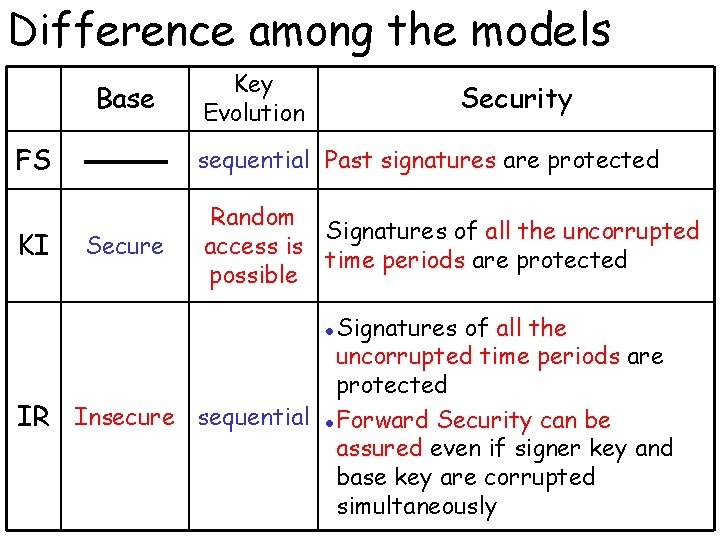
Difference among the models Base Key Evolution Security FS sequential Past signatures are protected KI Random Signatures of all the uncorrupted access is time periods are protected possible Secure Signatures of all the uncorrupted time periods are protected Insecure sequential l Forward Security can be assured even if signer key and base key are corrupted simultaneously l IR
 Key evolving signature
Key evolving signature Parallel key signatures
Parallel key signatures 15 key signatures
15 key signatures Evolving design
Evolving design A framework for clustering evolving data streams
A framework for clustering evolving data streams Evolving
Evolving El gamal signature
El gamal signature Spectral signatures
Spectral signatures Compact multi-signatures for smaller blockchains
Compact multi-signatures for smaller blockchains Exchange 2007 signatures
Exchange 2007 signatures Uncitral model law on electronic transferable records
Uncitral model law on electronic transferable records Intruders use virus signatures fabricate
Intruders use virus signatures fabricate Uncitral model law on international commercial arbitration
Uncitral model law on international commercial arbitration Ocaml signatures
Ocaml signatures Martin kreitman
Martin kreitman Example of business model canvas
Example of business model canvas Key partners
Key partners Hát kết hợp bộ gõ cơ thể
Hát kết hợp bộ gõ cơ thể Bổ thể
Bổ thể Tỉ lệ cơ thể trẻ em
Tỉ lệ cơ thể trẻ em Gấu đi như thế nào
Gấu đi như thế nào Thang điểm glasgow
Thang điểm glasgow Chúa sống lại
Chúa sống lại Các môn thể thao bắt đầu bằng tiếng nhảy
Các môn thể thao bắt đầu bằng tiếng nhảy Thế nào là hệ số cao nhất
Thế nào là hệ số cao nhất Các châu lục và đại dương trên thế giới
Các châu lục và đại dương trên thế giới Công thức tính độ biến thiên đông lượng
Công thức tính độ biến thiên đông lượng Trời xanh đây là của chúng ta thể thơ
Trời xanh đây là của chúng ta thể thơ Cách giải mật thư tọa độ
Cách giải mật thư tọa độ Làm thế nào để 102-1=99
Làm thế nào để 102-1=99