Lect 15 Digital Signatures RSA El Gamal DSA




- Slides: 13

Lect. 15 : Digital Signatures RSA, El. Gamal, DSA, KCDSA, Schnorr 1

Digital Signature v Digital Signature Ø Electronic version of handwritten signature on electronic document Ø Signing using private key (only by the signer) Ø Verification using public key (by everyone) v Hash then sign: sig(h(m)) v Efficiency in computation and communication 2

Digital Signature v Security requirements for digital signature Ø Unforgeability (위조 방지) Ø User authentication (사용자 인증) Ø Non-repudiation (부인 방지) Ø Unalterability (변조 방지) Ø Non-reusability (재사용 방지) v Services provided by digital signature v Authentication v Data integrity v Non-Repudiation 3

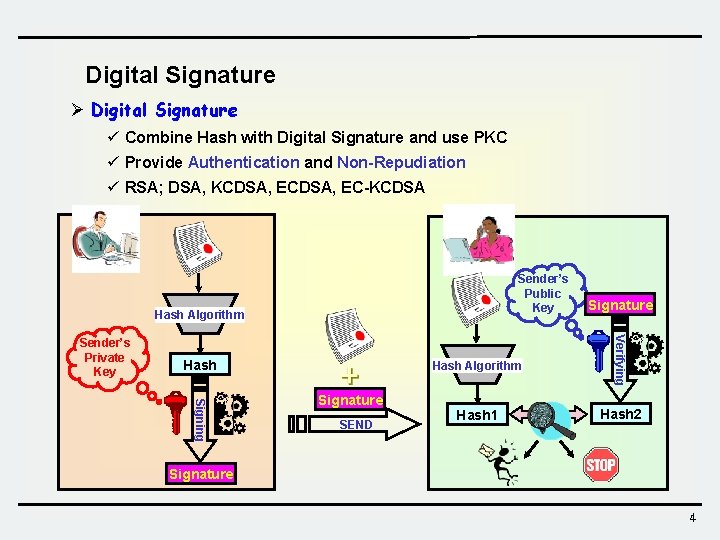
Digital Signature Ø Digital Signature ü Combine Hash with Digital Signature and use PKC ü Provide Authentication and Non-Repudiation ü RSA; DSA, KCDSA, EC-KCDSA Sender’s Public Key Hash Algorithm Hash Signing Signature SEND Hash Algorithm Verifying Sender’s Private Key Signature Hash 1 Hash 2 Signature 4

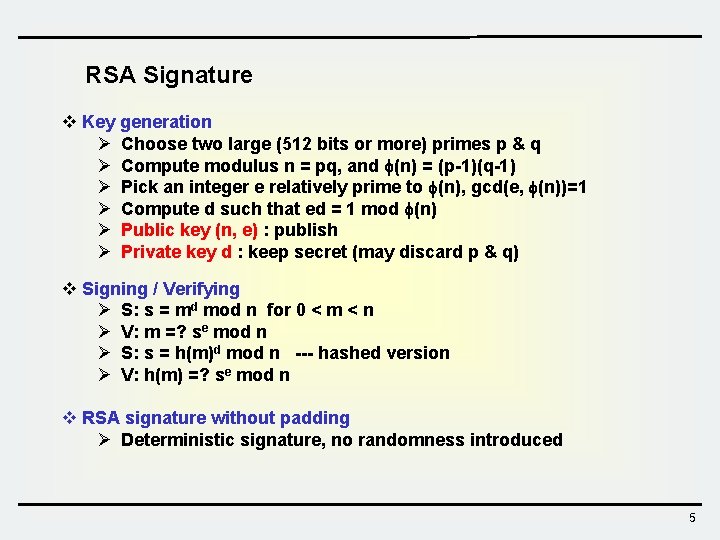
RSA Signature v Key generation Ø Choose two large (512 bits or more) primes p & q Ø Compute modulus n = pq, and (n) = (p-1)(q-1) Ø Pick an integer e relatively prime to (n), gcd(e, (n))=1 Ø Compute d such that ed = 1 mod (n) Ø Public key (n, e) : publish Ø Private key d : keep secret (may discard p & q) v Signing / Verifying Ø S: s = md mod n for 0 < m < n Ø V: m =? se mod n Ø S: s = h(m)d mod n --- hashed version Ø V: h(m) =? se mod n v RSA signature without padding Ø Deterministic signature, no randomness introduced 5

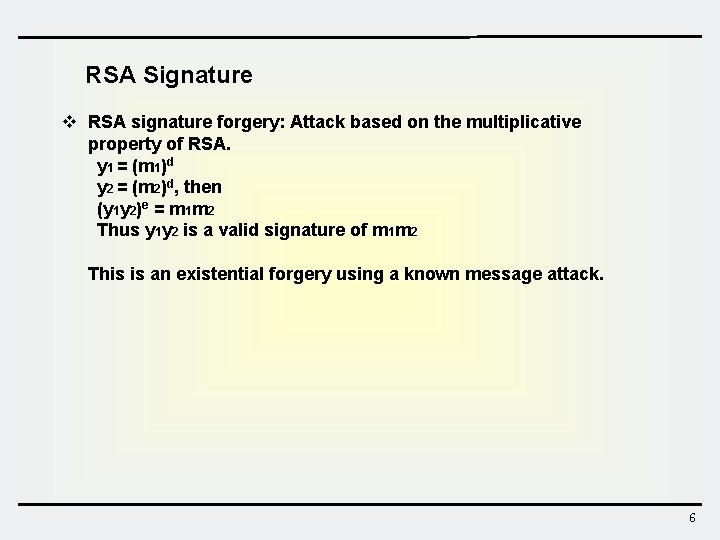
RSA Signature v RSA signature forgery: Attack based on the multiplicative property of RSA. y 1 = (m 1)d y 2 = (m 2)d, then (y 1 y 2)e = m 1 m 2 Thus y 1 y 2 is a valid signature of m 1 m 2 This is an existential forgery using a known message attack. 6

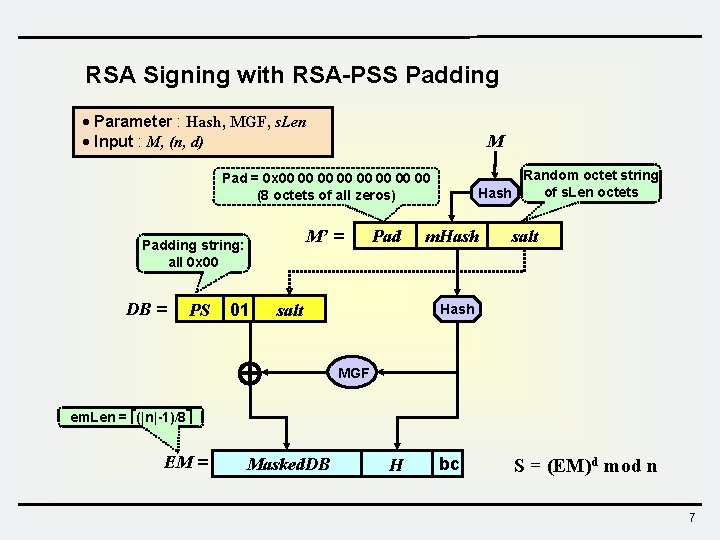
RSA Signing with RSA-PSS Padding · Parameter : Hash, MGF, s. Len · Input : M, (n, d) M Random octet string of s. Len octets Hash Pad = 0 x 00 00 (8 octets of all zeros) M’ = Padding string: all 0 x 00 DB = PS 01 Pad salt m. Hash salt Hash MGF em. Len = (|n|-1)/8 EM = Masked. DB H bc S = (EM)d mod n 7

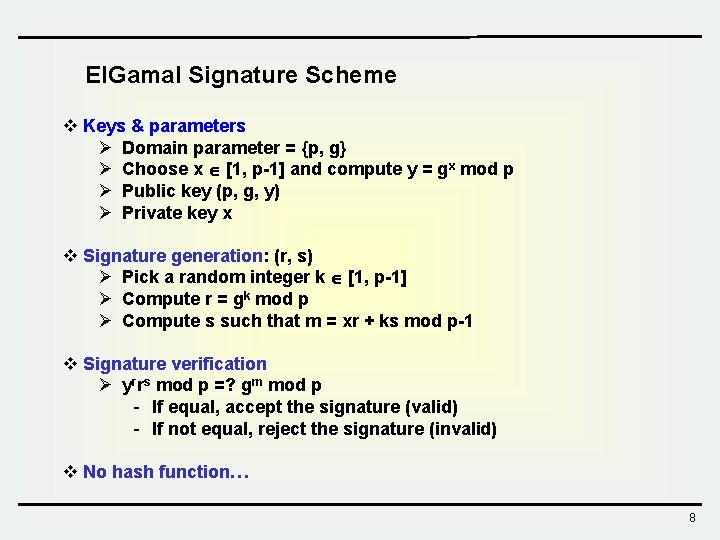
El. Gamal Signature Scheme v Keys & parameters Ø Domain parameter = {p, g} Ø Choose x [1, p-1] and compute y = gx mod p Ø Public key (p, g, y) Ø Private key x v Signature generation: (r, s) Ø Pick a random integer k [1, p-1] Ø Compute r = gk mod p Ø Compute s such that m = xr + ks mod p-1 v Signature verification Ø yrrs mod p =? gm mod p - If equal, accept the signature (valid) - If not equal, reject the signature (invalid) v No hash function… 8

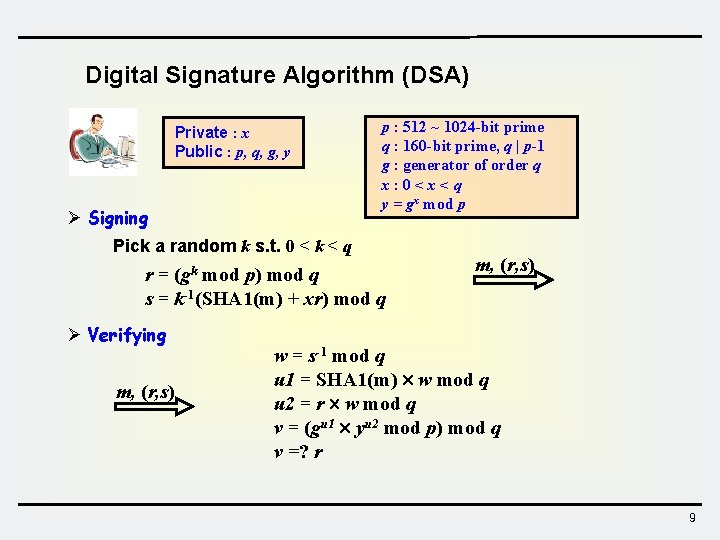
Digital Signature Algorithm (DSA) Private : x Public : p, q, g, y Ø Signing p : 512 ~ 1024 -bit prime q : 160 -bit prime, q | p-1 g : generator of order q x: 0<x<q y = gx mod p Pick a random k s. t. 0 < k < q r = (gk mod p) mod q s = k-1(SHA 1(m) + xr) mod q Ø Verifying m, (r, s) w = s-1 mod q u 1 = SHA 1(m) w mod q u 2 = r w mod q v = (gu 1 yu 2 mod p) mod q v =? r 9

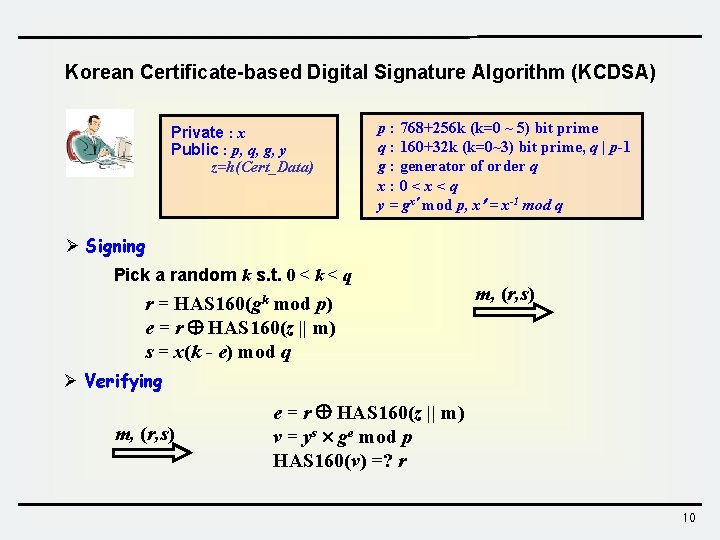
Korean Certificate-based Digital Signature Algorithm (KCDSA) Private : x Public : p, q, g, y z=h(Cert_Data) p : 768+256 k (k=0 ~ 5) bit prime q : 160+32 k (k=0~3) bit prime, q | p-1 g : generator of order q x: 0<x<q y = gx mod p, x = x-1 mod q Ø Signing Pick a random k s. t. 0 < k < q r = HAS 160(gk mod p) e = r HAS 160(z || m) s = x(k - e) mod q m, (r, s) Ø Verifying m, (r, s) e = r HAS 160(z || m) v = ys ge mod p HAS 160(v) =? r 10

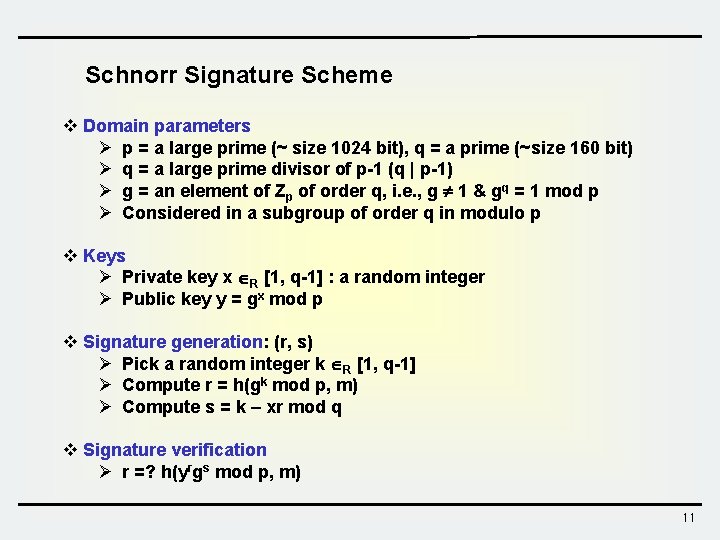
Schnorr Signature Scheme v Domain parameters Ø p = a large prime (~ size 1024 bit), q = a prime (~size 160 bit) Ø q = a large prime divisor of p-1 (q | p-1) Ø g = an element of Zp of order q, i. e. , g 1 & gq = 1 mod p Ø Considered in a subgroup of order q in modulo p v Keys Ø Private key x R [1, q-1] : a random integer Ø Public key y = gx mod p v Signature generation: (r, s) Ø Pick a random integer k R [1, q-1] Ø Compute r = h(gk mod p, m) Ø Compute s = k – xr mod q v Signature verification Ø r =? h(yrgs mod p, m) 11

Security of Digital Signature Schemes v Security goals Ø Total break: adversary is able to find the secret for signing, so he can forge then any signature on any message. Ø Selective forgery: adversary is able to create valid signatures on a message chosen by someone else, with a significant probability. Ø Existential forgery: adversary can create a pair (message, signature), s. t. the signature of the message is valid. 12

Security of Digital Signature Schemes v Attack models Ø Key-only attack: Adversary knows only the verification function (which is supposed to be public). Ø Known message attack: Adversary knows a list of messages previously signed by Alice. Ø Chosen message attack: Adversary can choose what messages wants Alice to sign, and he knows both the messages and the corresponding signatures. 13