Digital Signatures Ch 13 u Digital signatures u









- Slides: 22

Digital Signatures (Ch. 13) u Digital signatures u El. Gamal digital signature scheme u Schnorr digital signature scheme u Digital signature standard u Summary Cryptograpgy and Network Security 13 - 1 Anthony J. T. Lee Dept. of Information Management, NTU

Requirements of digital signatures u The signature must be a bit-pattern that depends on the message being signed. u The signature must use some information unique to the sender, to prevent both forgery and denial. u It must be relatively easy to produce the digital signature. u It must be relatively easy to recognize and verify the digital signature. u It must be computationally infeasible to forge a digital signature. u It must be practical to retain a copy of the digital signature in storage. Cryptograpgy and Network Security 13 - 2 Anthony J. T. Lee Dept. of Information Management, NTU

Digital Signatures u Have – looked at message authentication but does not address issues of lack of trust u Digital – – – signatures provide the ability to: verify author, date & time of signature authenticate message contents be verified by third parties to resolve disputes u Hence include authentication function with additional capabilities Cryptograpgy and Network Security 13 - 3 Anthony J. T. Lee Dept. of Information Management, NTU

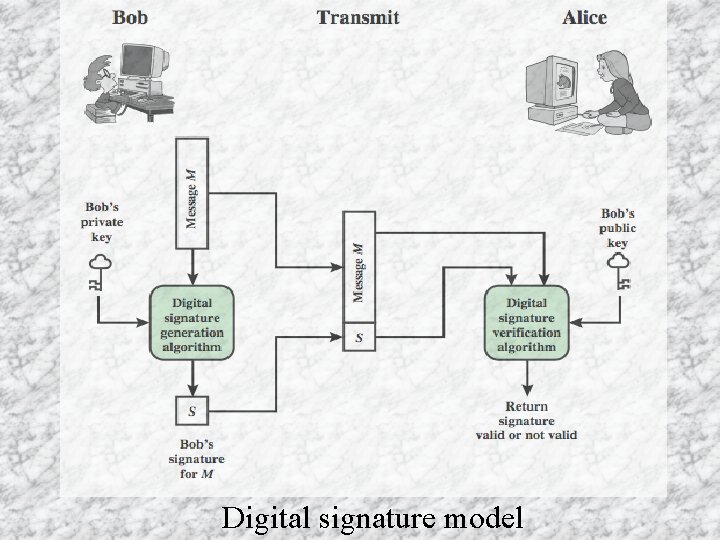
Digital signature model

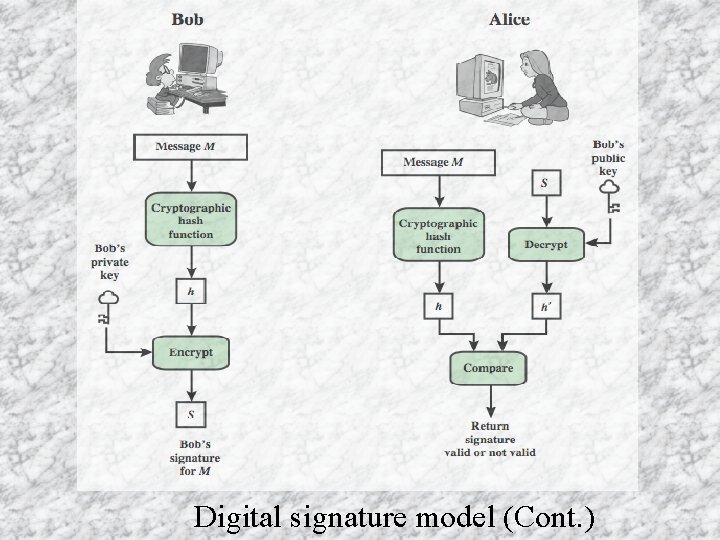
Digital signature model (Cont. )

Attacks and forgeries u Attacks – – – key-only attack known message attack generic chosen message attack directed chosen message attack adaptive chosen message attack u Break – – – success levels total break selective forgery existential forgery Cryptograpgy and Network Security 13 - 6 Anthony J. T. Lee Dept. of Information Management, NTU

Digital signature requirements u Must depend on the message signed u Must use information unique to sender u to prevent both forgery and denial u Must be relatively easy to produce u Must be relatively easy to recognize & verify u Be computationally infeasible to forge u with new message for existing digital signature u with fraudulent digital signature for given message u Be practical save digital signature in storage Cryptograpgy and Network Security 13 - 7 Anthony J. T. Lee Dept. of Information Management, NTU

Direct digital signatures u Involve only sender & receiver u Assumed receiver has sender’s public-key u Digital signature made by sender signing entire message or hash with private-key u Can encrypt using receivers public-key u Important that sign first then encrypt message & signature u Security depends on sender’s private-key Cryptograpgy and Network Security 13 - 8 Anthony J. T. Lee Dept. of Information Management, NTU

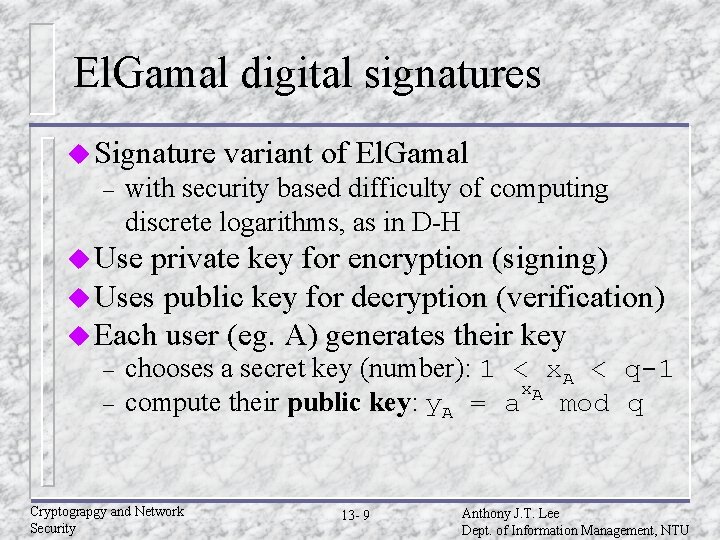
El. Gamal digital signatures u Signature – variant of El. Gamal with security based difficulty of computing discrete logarithms, as in D-H u Use private key for encryption (signing) u Uses public key for decryption (verification) u Each user (eg. A) generates their key – – chooses a secret key (number): 1 < x. A < q-1 x. A compute their public key: y. A = a mod q Cryptograpgy and Network Security 13 - 9 Anthony J. T. Lee Dept. of Information Management, NTU

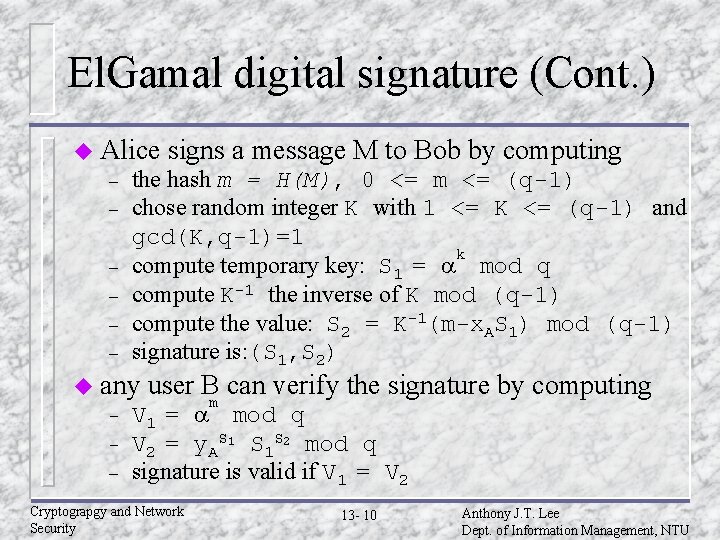
El. Gamal digital signature (Cont. ) u Alice – – – the hash m = H(M), 0 <= m <= (q-1) chose random integer K with 1 <= K <= (q-1) and gcd(K, q-1)=1 k compute temporary key: S 1 = a mod q compute K-1 the inverse of K mod (q-1) compute the value: S 2 = K-1(m-x. AS 1) mod (q-1) signature is: (S 1, S 2) u any – – – signs a message M to Bob by computing user Bm can verify the signature by computing V 1 = a mod q V 2 = y. AS 1 S 1 S 2 mod q signature is valid if V 1 = V 2 Cryptograpgy and Network Security 13 - 10 Anthony J. T. Lee Dept. of Information Management, NTU

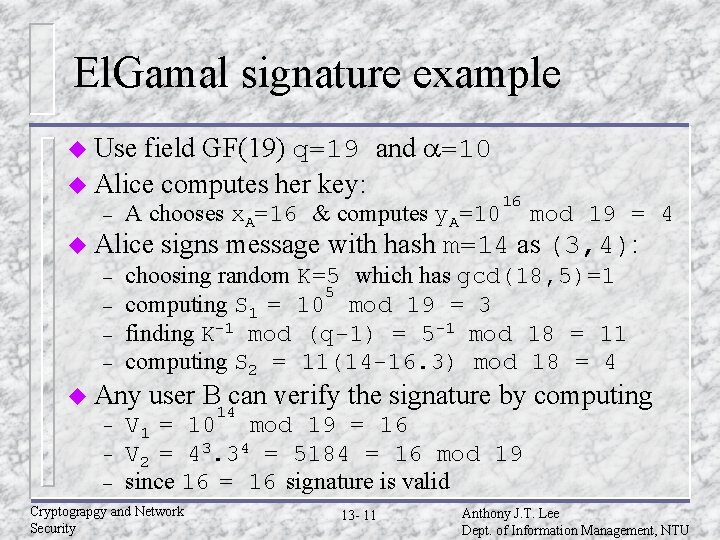
El. Gamal signature example field GF(19) q=19 and a=10 u Alice computes her key: u Use – A chooses x. A=16 & computes y. A=10 u Alice – – – mod 19 = 4 signs message with hash m=14 as (3, 4): choosing random K=5 which has gcd(18, 5)=1 5 computing S 1 = 10 mod 19 = 3 finding K-1 mod (q-1) = 5 -1 mod 18 = 11 computing S 2 = 11(14 -16. 3) mod 18 = 4 u Any – 16 user B 14 can verify the signature by computing V 1 = 10 mod 19 = 16 V 2 = 43. 34 = 5184 = 16 mod 19 since 16 = 16 signature is valid Cryptograpgy and Network Security 13 - 11 Anthony J. T. Lee Dept. of Information Management, NTU

Schnorr digital signatures u Security based on discrete logarithms u Minimizes message dependent computation – multiplying a 2 n-bit integer with an n-bit integer u Main u Have – – work can be done in idle time using a prime modulus p p– 1 has a prime factor q of appropriate size typically p 1024 -bit and q 160 -bit numbers Cryptograpgy and Network Security 13 - 12 Anthony J. T. Lee Dept. of Information Management, NTU

Schnorr key setup u Choose suitable primes p , q q u Choose a such that a = 1 mod p u (a, p, q) are global parameters for all u Each user (eg. A) generates a key – – chooses a secret key (number): 0 < s. A < q -s. A compute their public key: v. A = a mod q Cryptograpgy and Network Security 13 - 13 Anthony J. T. Lee Dept. of Information Management, NTU

Schnorr signature u User signs message by choosing random r with 0<r<q and computing x = ar mod p – concatenate message with x and hash result to computing: e = H(M || x) – computing: y = (r + se) mod q – signature is pair (e, y) u Any other user can verify the signature as follows: – computing: x' = ayve mod p – verifying that: e = H(M || x’) – Cryptograpgy and Network Security 13 - 14 Anthony J. T. Lee Dept. of Information Management, NTU

Digital signature standard (DSS) u US Govt approved signature scheme u Designed by NIST & NSA in early 90's u Published as FIPS-186 in 1991 u Revised in 1993, 1996 & then 2000 u Uses the SHA hash algorithm u DSS is the standard, DSA is the algorithm u FIPS 186 -2 (2000) includes alternative RSA & elliptic curve signature variants u DSA is digital signature only unlike RSA u a public-key technique Cryptograpgy and Network Security 13 - 15 Anthony J. T. Lee Dept. of Information Management, NTU

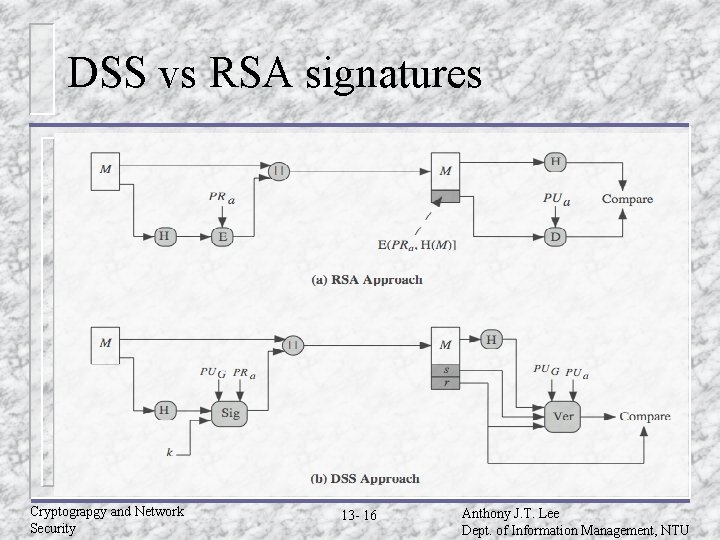
DSS vs RSA signatures Cryptograpgy and Network Security 13 - 16 Anthony J. T. Lee Dept. of Information Management, NTU

Digital signature algorithm (DSA) u Creates a 320 bit signature u With 512 -1024 bit security u Smaller and faster than RSA u A digital signature scheme only u Security depends on difficulty of computing discrete logarithms u Variant of El. Gamal & Schnorr schemes Cryptograpgy and Network Security 13 - 17 Anthony J. T. Lee Dept. of Information Management, NTU

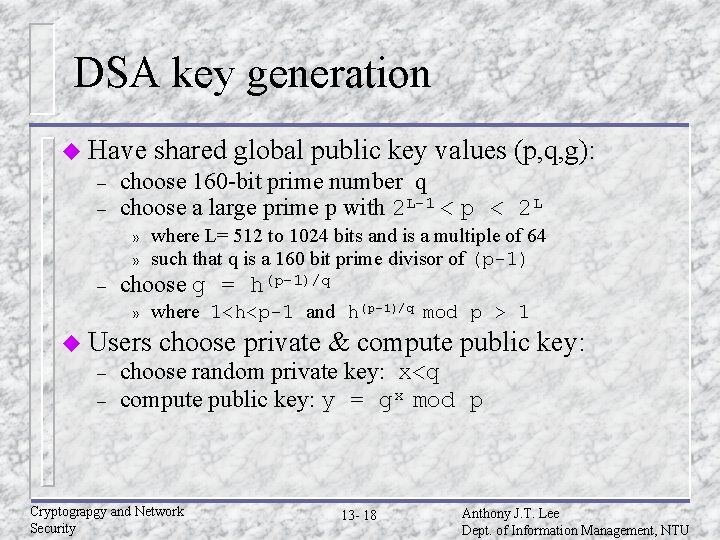
DSA key generation u Have – – choose 160 -bit prime number q choose a large prime p with 2 L-1 < p < 2 L » » – shared global public key values (p, q, g): where L= 512 to 1024 bits and is a multiple of 64 such that q is a 160 bit prime divisor of (p-1) choose g = h(p-1)/q » where 1<h<p-1 and h(p-1)/q mod p > 1 u Users – – choose private & compute public key: choose random private key: x<q compute public key: y = gx mod p Cryptograpgy and Network Security 13 - 18 Anthony J. T. Lee Dept. of Information Management, NTU

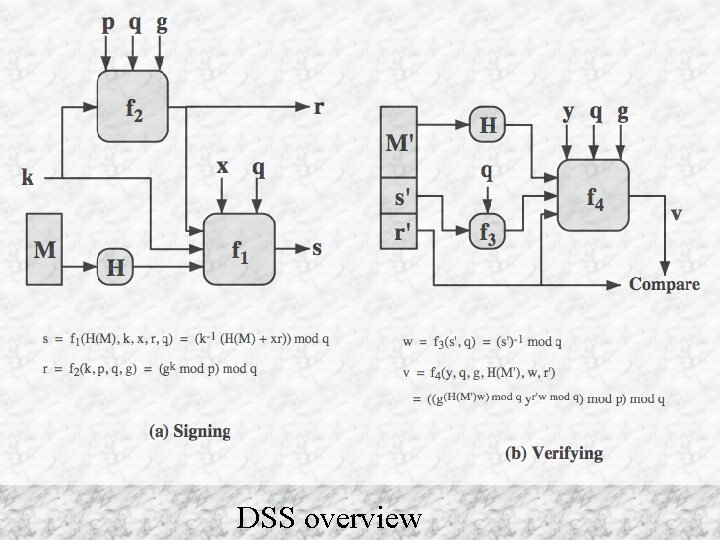
DSA signature creation u To – – sign a message M the sender: generates a random signature key k, k<q nb. k must be random, be destroyed after use, and never be reused u Then computes signature pair: r = (gk mod p)mod q s = [k-1(H(M)+ xr)] mod q u Sends signature (r, s) with message M Cryptograpgy and Network Security 13 - 19 Anthony J. T. Lee Dept. of Information Management, NTU

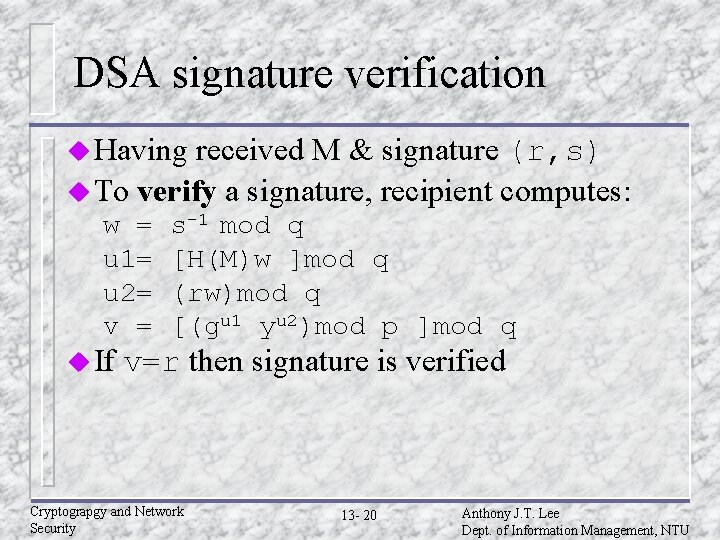
DSA signature verification u Having received M & signature (r, s) u To verify a signature, recipient computes: w = u 1= u 2= v = u If s-1 mod q [H(M)w ]mod q (rw)mod q [(gu 1 yu 2)mod p ]mod q v=r then signature is verified Cryptograpgy and Network Security 13 - 20 Anthony J. T. Lee Dept. of Information Management, NTU

DSS overview

Homework u P 431 (Chapter 13) 13. 4 13. 5 13. 8 Cryptograpgy and Network Security 13 - 22 Anthony J. T. Lee Dept. of Information Management, NTU