Multiple Access Techniques Waheed ur Rehman wahrehmangmail com




































![Bit 0 bit 0 -1 c 1 [+1+1] c 2 1 -1 [+1 -1] Bit 0 bit 0 -1 c 1 [+1+1] c 2 1 -1 [+1 -1]](https://slidetodoc.com/presentation_image_h2/74b79f8e9ba51161ee3535046b9971b6/image-69.jpg)

- Slides: 70

Multiple Access Techniques Waheed ur Rehman wahrehman@gmail. com

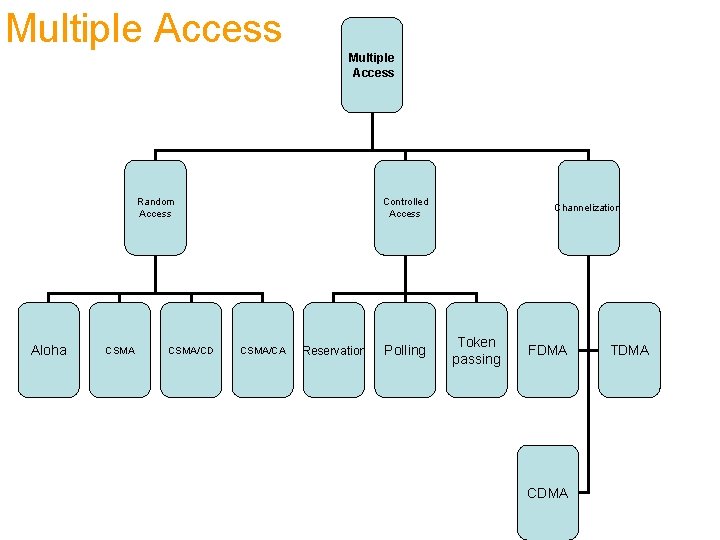
Multiple Access Random Access Aloha CSMA/CD Controlled Access CSMA/CA Reservation Polling Channelization Token passing FDMA CDMA TDMA

Random Access • • • No station is superior to another None is assigned control over other No schedule time for a station to transmit Transmission is random among the station Collision may occur in case if two stations tries to transmit at the same time

Random Access Aloha: • Earliest random access method • Developed at university of hawaii in 1970 • Designed for wireless LANs • But can be used by any shared medium • Pure and slotted aloha

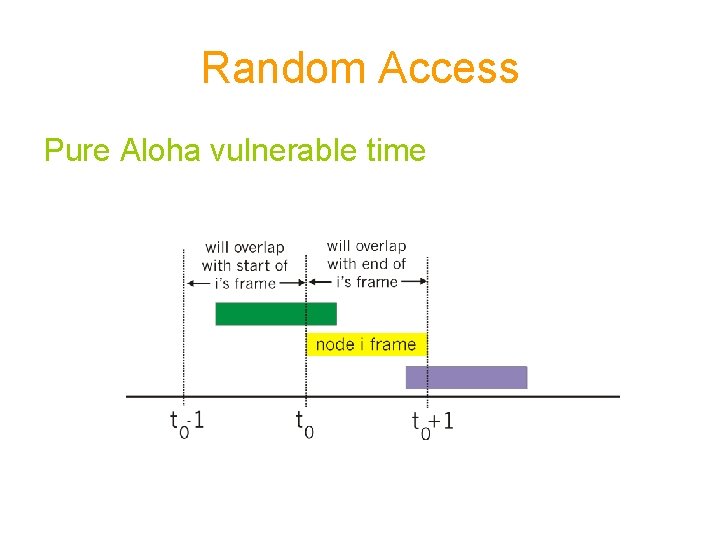
Random Access Pure Aloha: • The original aloha protocol is called pure aloha • Any station can transmit when they have something to send • Requires an ACK • A frame needs to be retransmitted in case of no ACK • In case of collision, each station has to wait for random amount of time before retransmission.

Random Access Pure Aloha vulnerable time

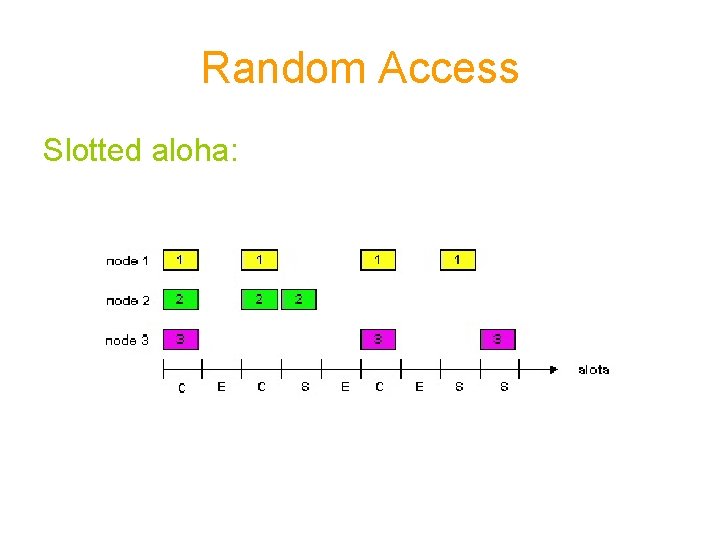
Random Access Slotted aloha: • Fixed size transmission slots • A station only transmit at the beginning of the slot • Collision can occur if two station tries to send in same time slot • In case of collision stations has to wait for a random amount of time • Random time is calculated using backoff algorithm

Random Access Slotted aloha:

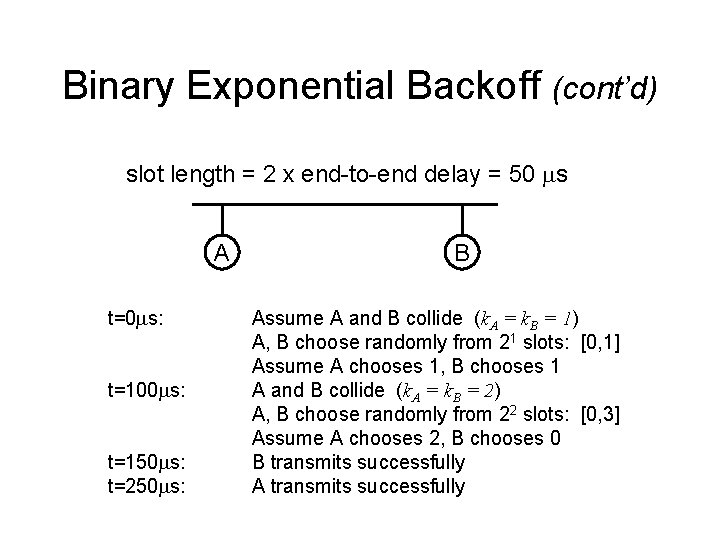
Random Access Backoff Algorithm: • In case of collision an algorithm is devised for retransmission • In case of collision random number N is selected between 0. . [2 K-1], where k is the number of collision • That random number N is then multiplied with maximum propagation delay Tp • Time to wait = N * Tp • If k=1 then N =0, 1 • If k=2 then N = 0, 1, 2, 3

Binary Exponential Backoff (cont’d) slot length = 2 x end-to-end delay = 50 ms A t=0 ms: t=100 ms: t=150 ms: t=250 ms: B Assume A and B collide (k. A = k. B = 1) A, B choose randomly from 21 slots: [0, 1] Assume A chooses 1, B chooses 1 A and B collide (k. A = k. B = 2) A, B choose randomly from 22 slots: [0, 3] Assume A chooses 2, B chooses 0 B transmits successfully A transmits successfully

Random Access • Maximum number of collisions allowed are 16 • After collision number 10 the random number selected between 0. . 1023 • After 16 collision the transmission is aborted and can be retransmitted some other time • The typical time for Tp can be around 51. 2 microseconds

Random Access CSMA: • Carrier sense multiple access • Listen to the medium first • Sense before transmit • Listen before talk • Reduce collisions but cannot eliminate it • Can be persistent and non persistent

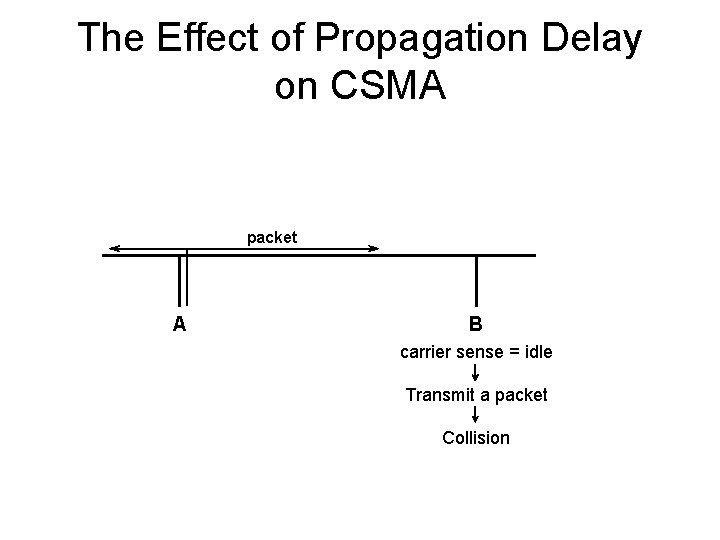
The Effect of Propagation Delay on CSMA packet A B carrier sense = idle Transmit a packet Collision

Propagation Delay and CSMA • Contention (vulnerable) period in Pure ALOHA – two packet transmission times • Contention period in Slotted ALOHA – one packet transmission time • Contention period in CSMA – up to 2 x end-to-end propagation delay Performance of CSMA > Performance of Slotted ALOHA > Performance of Pure ALOHA

Random Access CSMA: • There are several types of CSMA protocols: – 1 -Persistent CSMA – Non-Persistent CSMA – P-Persistent CSMA

Random Access 1 -Persistent : 1. If the medium is idle, transmit otherwise goto 2 2. if the medium is busy continue to listen until channel is sensed idle, then transmit immediately. - Highest chance of collision because two stations might find the medium idle and might transmit simultaneously The protocol is called 1 -persistent because the host transmits with a probability of 1 whenever it finds the channel idle.

Random Access Non persistent CSMA 1. If the medium is idle, transmit otherwise goto 2 2. If the medium is busy, wait for random amount of time and repeat step 1 - Problem , capacity is wasted since medium is idle following the end of transmission

Tradeoff between 1 - and Non. Persistent CSMA • If B and C become ready in the middle of A’s transmission, – 1 -Persistent: • B and C collide – Non-Persistent: • B and C probably do not collide • If only B becomes ready in the middle of A’s transmission, – 1 -Persistent: • B succeeds as soon as A ends – Non-Persistent: • B may have to wait

Random Access P-Persistent CSMA • Optimal strategy: use P-Persistent CSMA • Assume channels are slotted • One slot = contention period (i. e. , one round trip propagation delay)

Random Access P-Persistent CSMA (cont’d) 1. Sense the channel – If channel is idle, transmit a packet with probability p • if a packet was transmitted, go to step 2 • if a packet was not transmitted, wait one slot and go to step 1 – If channel is busy, wait one slot and go to step 1. 2. Detect collisions – If a collision occurs, wait a random amount of time and go to step 1

P-Persistent CSMA (cont’d) • Consider p-persistent CSMA with p=0. 5 – When a host senses an idle channel, it will only send a packet with 50% probability – If it does not send, it tries again in the next slot.

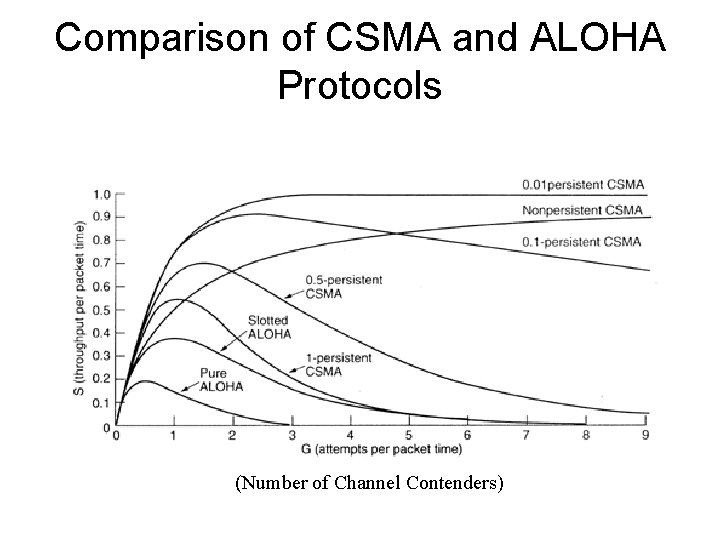
Comparison of CSMA and ALOHA Protocols (Number of Channel Contenders)

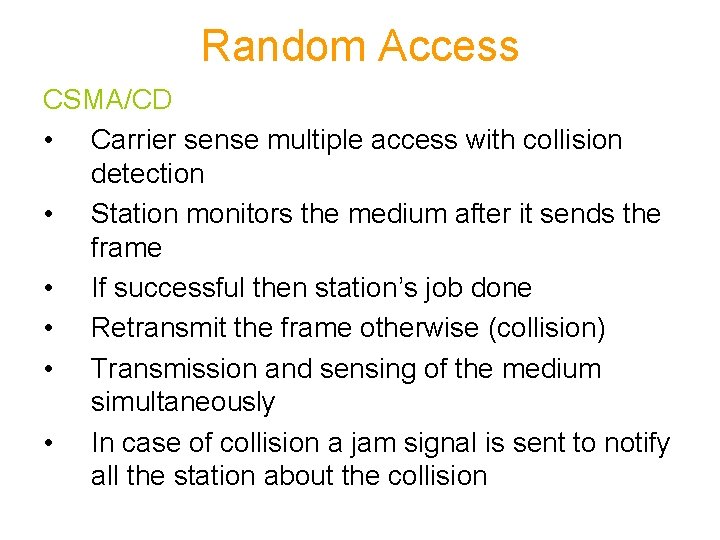
CSMA/CD • In CSMA protocols – If two stations begin transmitting at the same time, each will transmit its complete packet, thus wasting the channel for an entire packet time • In CSMA/CD protocols – The transmission is terminated immediately upon the detection of a collision – CD = Collision Detect

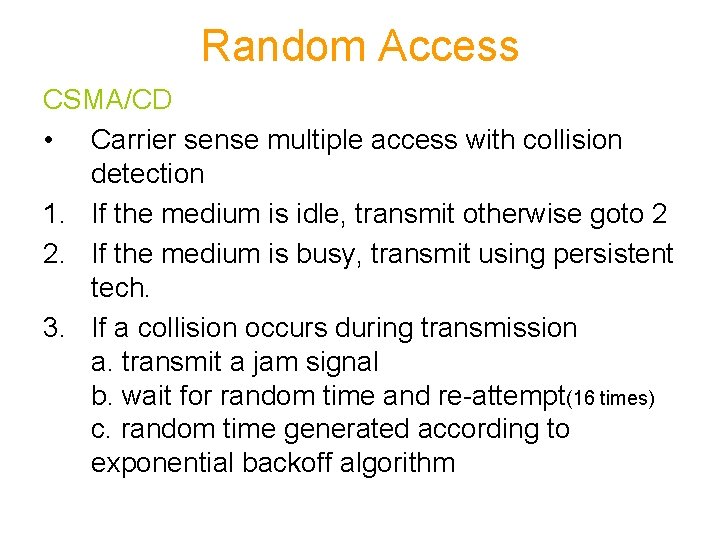
Random Access CSMA/CD • Carrier sense multiple access with collision detection • Station monitors the medium after it sends the frame • If successful then station’s job done • Retransmit the frame otherwise (collision) • Transmission and sensing of the medium simultaneously • In case of collision a jam signal is sent to notify all the station about the collision

Random Access CSMA/CD • Carrier sense multiple access with collision detection 1. If the medium is idle, transmit otherwise goto 2 2. If the medium is busy, transmit using persistent tech. 3. If a collision occurs during transmission a. transmit a jam signal b. wait for random time and re-attempt(16 times) c. random time generated according to exponential backoff algorithm

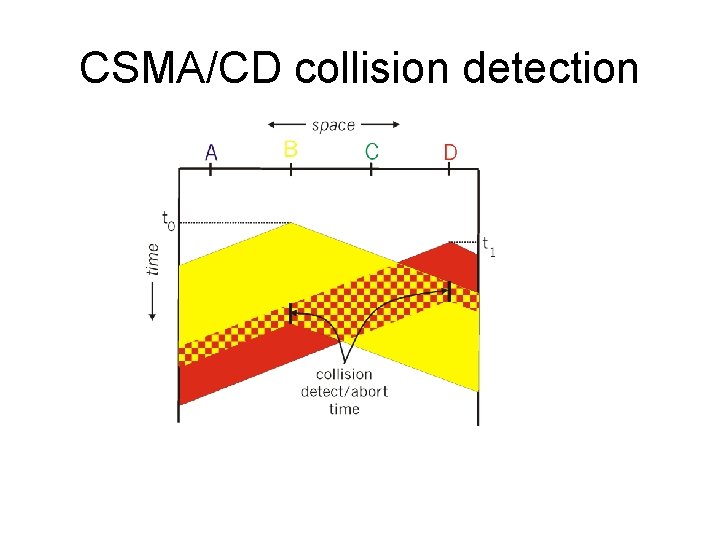
CSMA/CD collision detection

CSMA/CD (cont’d) • Carrier sense – reduces the number of collisions • Collision detection – reduces the effect of collisions, making the channel ready to use sooner

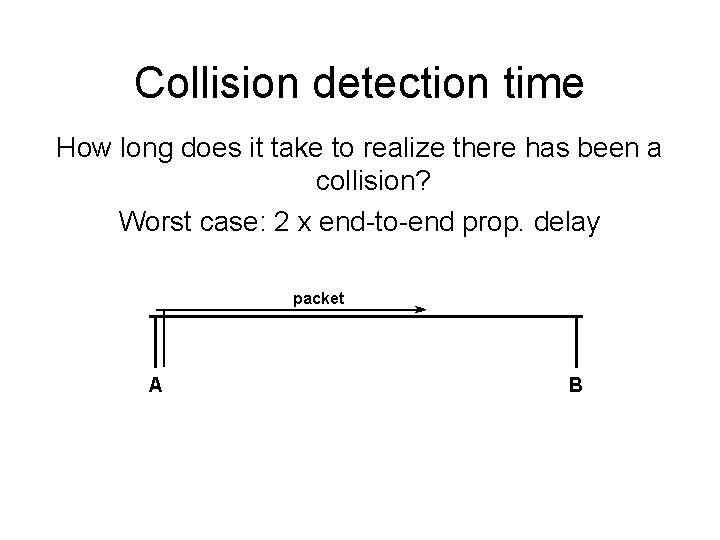
Collision detection time How long does it take to realize there has been a collision? Worst case: 2 x end-to-end prop. delay packet A B




Random Access CSMA/CD Minimum Frame Size: • Minimum frame restriction apply • Before sending last bit of the frame, sending station must detect a collision(if. Any) • Once the frame is sent, sending station doesn’t keep the copy • Tfr = 2 Tp


Random Access Difference between aloha and CSMA/CD • In addition to the persistent process the medium needs to be sensed first • In aloha first the frame is transmitted and then wait for ACK. In CSMA/CD station receives and transmit continuously (on two different ports) • Sending of the jam signal that enforce the collision in case other stations have not yet sensed the collision.

Random Access Question: How can the station detect the medium?

Random Access Energy Levels: • Three values • 0, normal and abnormal • 0 means line is idle • Normal means successful capture of the channel for transmission • Abnormal means that collision occurs

Random Access CSMA/CA • Carrier sense multiple access with collision avoidance • Three strategies Interframe Space (IFS) • Sense the channel, if it is idle don’t transmit wait for period of time called interframe space • If the medium is idle even after IFS, still needs to wait for time equal to contention window • IFS can also be used to define the priority of a station or a frame • For example, a station that is assigned a shorter IFS has a higher priority

Random Access Contention Window: • Amount of time divided into slots • A station that is ready to send choose a random number of slot as its wait time • The time slot in the window changes according to the backoff algorithm • Station needs to sense after each time slot • If station finds the channel idle then continue, if busy, then halt and continue when idle • Station needs to sense the channel after each time slot • If the station finds the channel busy, it doesn’t restart the process ; it just stops the timer and restart it when the channel is sensed as idle. ACK: • ACK is needed for ensuring the successful delivery of the transmission

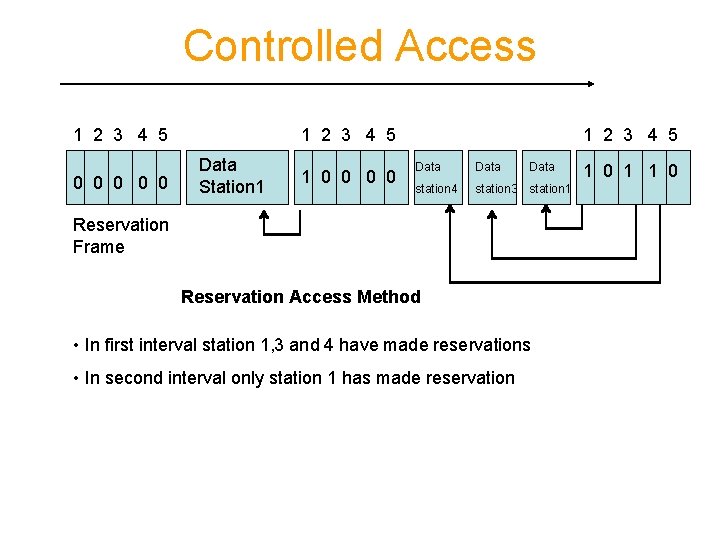
Controlled Access Reservation: • a station needs to make a reservation before sending data • Time is divided into intervals • In each interval a reservation frame is proceeds the data frames sent in that interval • If there are N stations in the system there are exactly N reservation minislots in the reservation frame. • Each mini slot belongs to a station • When a station needs to send data it makes reservation into its own mini slot • The station that have made reservation can send their data frames after the reservation frames

Controlled Access 1 2 3 4 5 0 0 0 1 2 3 4 5 Data Station 1 1 0 0 1 2 3 4 5 Data station 4 station 3 station 1 Reservation Frame Reservation Access Method • In first interval station 1, 3 and 4 have made reservations • In second interval only station 1 has made reservation 1 0 1 1 0


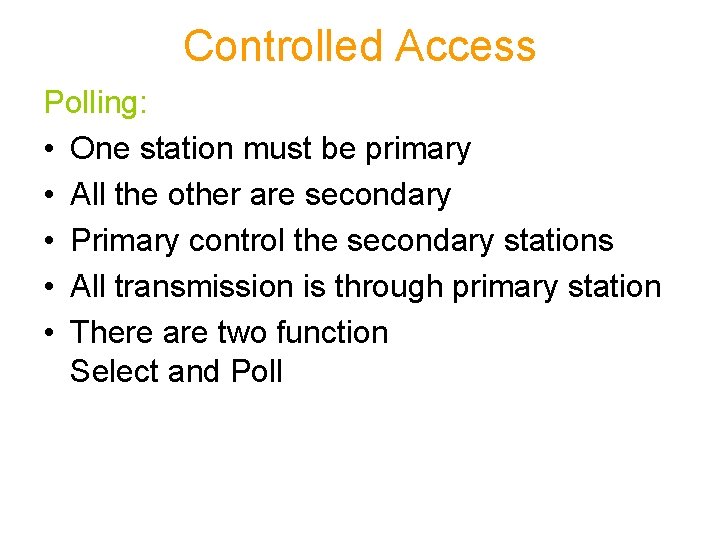
Controlled Access Polling: • One station must be primary • All the other are secondary • Primary control the secondary stations • All transmission is through primary station • There are two function Select and Poll

Controlled Access Select: • Used when primary device has something to send • Primary station send select frame to alert the secondary receiver of incoming transmission • After select , , wait for ACK • After ACK sends data • Wait for ACK again to ensure successful delivery


Controlled Access Poll: • Used when secondary station needs to send • Primary station send poll to ask if there is anything to send • Secondary stations might reply with either NAK or with data frames • If NAK the primary station sends poll to the next station • If data frame then primary ACK the receipt


Controlled Access Token Passing • Each station has a predecessor and successor • Token gives right to a station to send data • When a station has something to send it waits until it gets the token • When the station has no data to send it release the token • Token management is required for 1. amount of time a station can hold token 2. monitoring to ensure the token is not destroyed

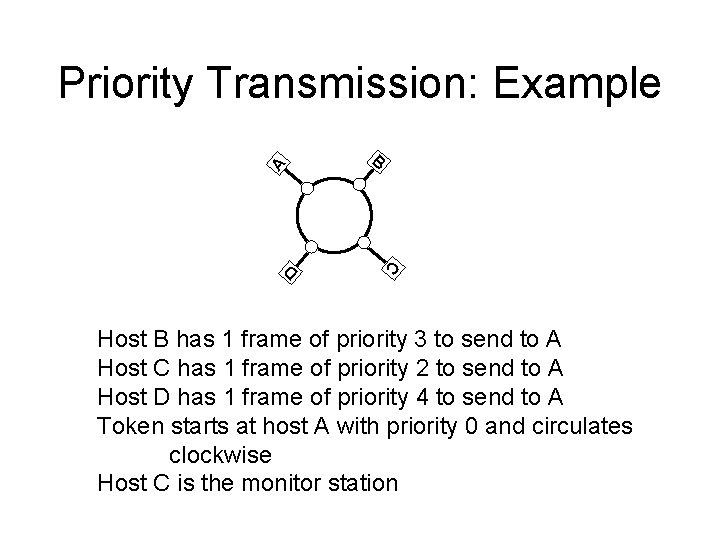
Priority Transmission: Example A B C D Host B has 1 frame of priority 3 to send to A Host C has 1 frame of priority 2 to send to A Host D has 1 frame of priority 4 to send to A Token starts at host A with priority 0 and circulates clockwise Host C is the monitor station

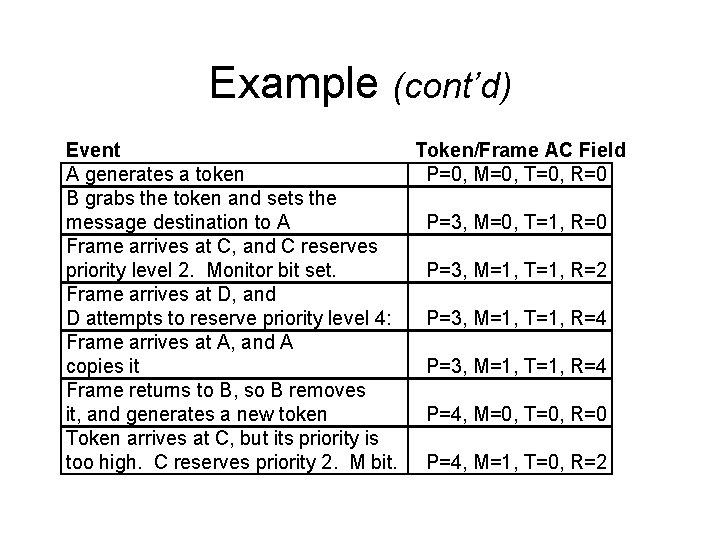
Example (cont’d) Event Token/Frame AC Field A generates a token P=0, M=0, T=0, R=0 B grabs the token and sets the message destination to A P=3, M=0, T=1, R=0 Frame arrives at C, and C reserves priority level 2. Monitor bit set. P=3, M=1, T=1, R=2 Frame arrives at D, and D attempts to reserve priority level 4: P=3, M=1, T=1, R=4 Frame arrives at A, and A copies it P=3, M=1, T=1, R=4 Frame returns to B, so B removes it, and generates a new token P=4, M=0, T=0, R=0 Token arrives at C, but its priority is too high. C reserves priority 2. M bit. P=4, M=1, T=0, R=2

Example (cont’d) Event Token/Frame AC Field Token arrives at D, and D grabs it, sending a message to A P=4, M=0, T=1, R=2 Frame arrives at A, and A copies it P=4, M=0, T=1, R=2 Frame arrives at B, which does nothing to it P=4, M=0, T=1, R=2 Frame arrives at C, which sets the monitor bit P=4, M=1, T=1, R=2 Frame returns to D, so D removes it and generates a new token with P=2, M=0, T=0, R=0 etc… Attempt to complete this scenario on your own.



Channelization • Available bandwidth of a link is shared in time, frequency or through code between different stations • FDMA, TDMA, CDMA FDMA • Available bandwidth is divided into frequency bands • Each station is assigned a band to send data • i. e. each band is reserved for a specific station and is there all the time • To prevent interference the allocated bands are separated by guard bands


Channelization FDMA • FDMA is usually used when fairly large bandwidth is available like radio, coax or fiber optic • Use of guard bands means that in practice whole range of frequency band cannot be used • Guard band reduces the efficiency of the system • Number of bands increase results in width of each band reduced • Its also proportional to number of guard band intervals • FDMA is conceptually simple system

Channelization Problems with FDMA • Each link takes up one frequency band require one transmitter and receiver. • For full duplex link, we need to have active transmitter and receiver, which makes circuitry more complex • If variable data rate transmission is desirable then two methods, – Either widen each frequency band • Result in wastage of resource for those who don’t need fast links – Combine several bands • Increase complexity • FDMA is ideal where data rate is constant like in voice and analog TV signals.

Channelization TDMA • Stations share bandwidth of a channel in time • Each station is allocated a time slot during which it can send data • Each station transmit its data in its assigned time slot • The main problem can be synchronization • Each station must follow the beginning of its time slot and its location • This is difficult because of propagation delay among distant stations • To overcome guard time are introduced


Channelization TDMA • If a signal is transmitted @ 1000 bits per second, means 1 bit after each millisecond arrives • If we transmit as a burst, there will be no need to transmit a bit after every millisecond • E. g. 10 bit burst could be sent after each 10 millisecond • In this case we need to pause the transmission for some time and transmit after specified time, in the form of bursts

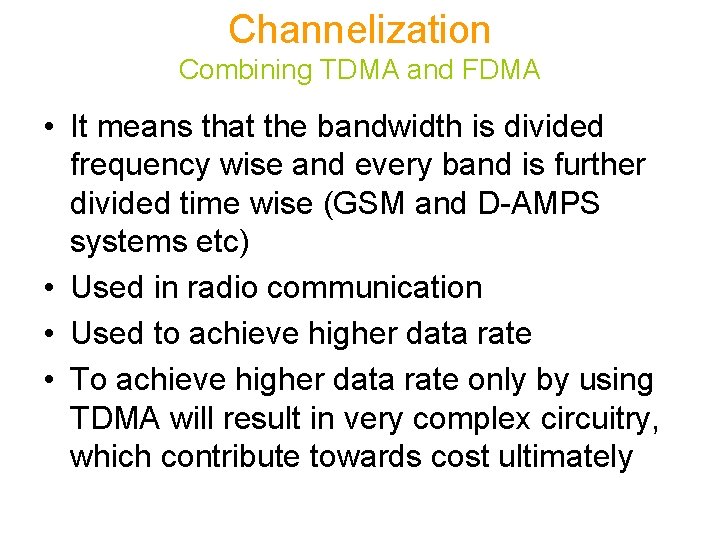
Channelization Combining TDMA and FDMA • It means that the bandwidth is divided frequency wise and every band is further divided time wise (GSM and D-AMPS systems etc) • Used in radio communication • Used to achieve higher data rate • To achieve higher data rate only by using TDMA will result in very complex circuitry, which contribute towards cost ultimately

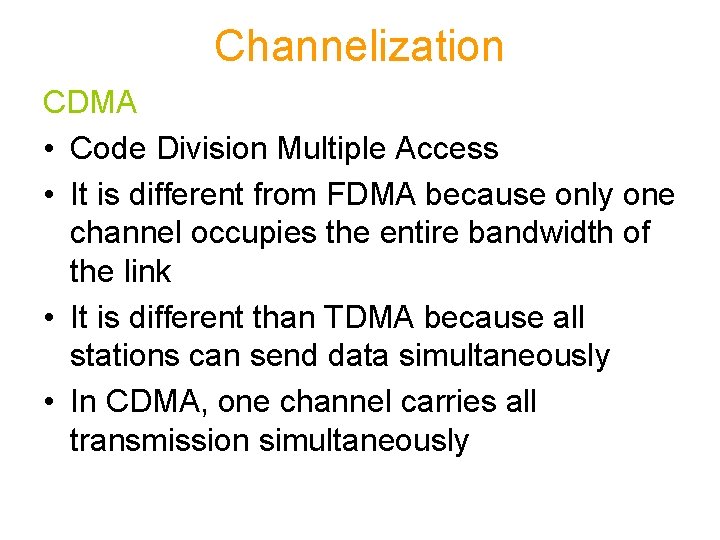
Channelization CDMA • Code Division Multiple Access • It is different from FDMA because only one channel occupies the entire bandwidth of the link • It is different than TDMA because all stations can send data simultaneously • In CDMA, one channel carries all transmission simultaneously

Channelization An analogy • CDMA simply means communicating with different codes • For example in a big room people are sitting. • In TDMA every body has to speak but on their own turn • In FDMA we can think of them speaking to each others in some small separations • In CDMA they all can speak to each other simultaneously but in different language (code) • E. g. two people talk in French and reject everything else as noise if its not in French

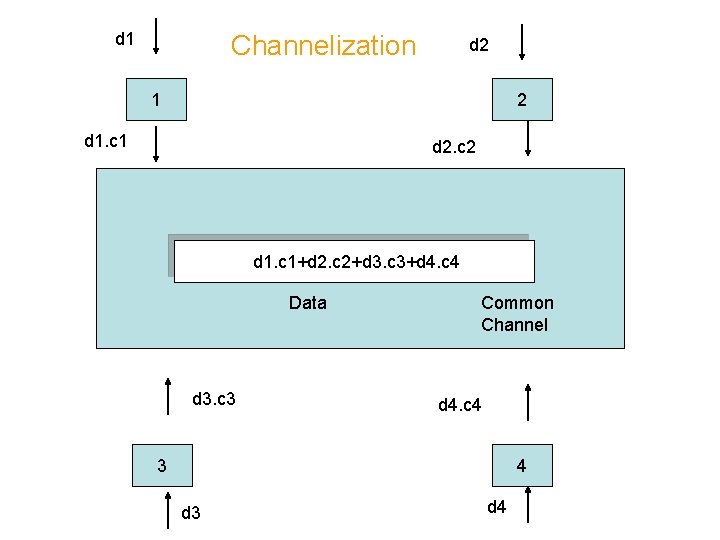
Channelization • Lets assume we have four stations 1, 2, 3 and 4 connected to the same channel • Data from station 1 is d 1 and so on • The code assign to the station 1 is c 1 and so on • We assume that the assigned codes have two properties 1. if we multiply each code by another, we get 0 2. if we multiply each code by itself, we get 4 ( the number of stations) • With these properties in mind, all four stations wants to send data on a shared channel • Station 1 multiplies its data by its code to get d 1. c 1, station 2 gets d 2. c 2 and so on • The data that go on the channel is the sum of all these terms • d 1. c 1 + d 2. c 2 + d 3. c 3 + d 4. c 4

d 1 Channelization d 2 1 2 d 1. c 1 d 2. c 2 d 1. c 1+d 2. c 2+d 3. c 3+d 4. c 4 Data d 3. c 3 Common Channel d 4. c 4 3 4 d 3 d 4

Channelization • E. g. station 2 wants to extract information sent by station 1 • Station 2 multiplies c 1 by the data on the channel • Data = (d 1. c 1 + d 2. c 2 + d 3. c 3 + d 4. c 4). c 1 d 1. c 1 + d 2. c 1 + d 3. c 1 + d 4. c 1 4. d 1 as c 1. c 2=c 3. c 1=c 4. c 1=0 and c 1= 4 • Station divide it by 4 to get data.

Channelization Chips • CDMA is based on coding theory • Each station is assigned a code • That code is a sequence of numbers called chips • To code for previous example are • C 1 = +1 +1 C 2= +1 -1 C 3 = +1 +1 -1 -1 C 4= +1 -1 -1 +1 • The codes are not selected randomly they are selected carefully • The are called orthogonal sequences

Channelization Properties of orthogonal sequences 1. Each sequence is made of N elements, where N is the number of stations 2. If we multiply a sequence by a number, every element in the sequence is multiplied by that element. This is call multiplication of a sequence by a scalar. For example 2. [+1 +1 -1 -1] = [+2 +2 -2 -2] 3. If we multiply two equal sequences, elements by elements, and then add the results, we get N, where N is the number of elements in the each sequence. This is called the inner product of two equal sequence. For example [+1 +1 -1 -1] = 1+1+1+1 =4 4. If we multiply two different sequences, element by element, and add the results, we get 0. this is called inner product of two different sequence. For example [+1 +1 -1 -1]. [+1 +1] = 1+1 -1 -1 = 0 5. Adding two sequences means adding the corresponding elements. The result is another sequence. For example [+1 +1 -1 -1] + [+1 +1] = [+2 +2 0 0]

Channelization Data Representation • If a station needs to send 0 bit; it encodes it as -1 • If it is to send 1 bit; it encodes it as +1 • When a station is idle; it sends no signal, which is interpreted as 0 Data bit 0 -1 Data bit 1 +1 Silence 0
![Bit 0 bit 0 1 c 1 11 c 2 1 1 1 1 Bit 0 bit 0 -1 c 1 [+1+1] c 2 1 -1 [+1 -1]](https://slidetodoc.com/presentation_image_h2/74b79f8e9ba51161ee3535046b9971b6/image-69.jpg)
Bit 0 bit 0 -1 c 1 [+1+1] c 2 1 -1 [+1 -1] 2 [-1+1] d 2. c 2 [-1 -1] d 1. c 1 [-1 -1 -3 +1] Data [0 0 0 0] c 1 [+1+1 -1 -1] 3 Common Channel [+1 -1 -1+1] d 4. c 4 d 3. c 3 c 1 0 Silent [+1 -1 -1+1] 4 +1 Bit 1

Questions • What is difference of FDM and FDMA ? • What is difference of TDM and TDMA ?