Information Security IT Technical Secretariat ITTS Digital Oman




























































- Slides: 82

Information Security IT Technical Secretariat - ITTS Digital Oman Initiative Ministry of National Economy 13 June 2005

What is Information ? Where is it ? the communication or reception of knowledge or intelligence

What is an Information Security Management System What to protect? The protection of information assets from unauthorized access to or modification of information, whether in storage, processing, or transit, and against the denial of service to authorized users or the provision of service to unauthorized users, including those measures necessary to detect, document, and counter such threats. From Whom to Protect ? How to Protect ?

Security = The CIA Triangle Confidentiality Integrity Availability Confidentiality • Protecting sensitive info from unauthorized disclosure or intelligible interpretation − High: Personal Data as defined under Legal Regulatory boards, privacy related, medical records, and strategic information − Medium: Internal, must not go outside the Organisation − Low: External, everything that would be allowed to go outside the Organisation Integrity • Safeguarding the accuracy and completeness of info and S/W − High: Financial transactions, software, personal data − Medium: Measurement data, name & address data − Low: No specific requirements Availability • Ensuring that info and vital IT services are available when required − High: 24 hours per day, 99. 9 % − Medium: from 07. 00 to 19. 00, 99. 5 % − Low: Not critical and tolerable downtime allowed

Security Strategy Questions • What is to be protected? • Why does it need to be protected? • What is the link to business drivers? • Which security requirements are most important? • Why is it important? • What happens if it is not protected? • What is the organization’s risk tolerance? • Which requirements, if unmet for any reason, would impact the organization? • What is the organization’s impact tolerance?

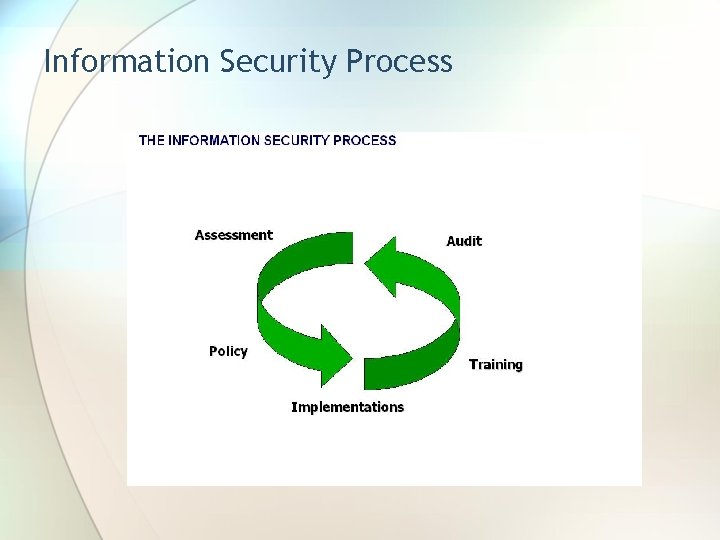
Information Security Process

Risk, Asset, Threat and Vulnerabilities Threats Increase Protect Against Controls Met By Exploit Indicate Security Requirements Expose Increase Risks Reduce Vulnerabilities • Accept • Avoid • Transfer • Reduce Increases Assets Have Asset Value

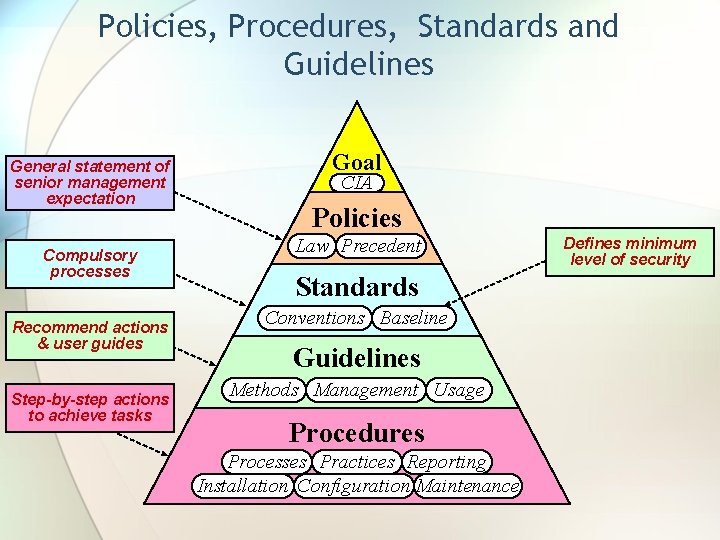
Policies, Procedures, Standards and Guidelines General statement of senior management expectation Compulsory processes Recommend actions & user guides Step-by-step actions to achieve tasks Goal CIA Policies Law Precedent Standards Conventions Baseline Guidelines Methods Management Usage Procedures Processes Practices Reporting Installation Configuration Maintenance Defines minimum level of security

Policy Framework Definitions Policies • Define why information security is important to your organization • Describe high-level information security philosophy and topical coverage • Are brief, technology and solution-independent documents • Rarely change (in response to new technology or threats) Procedures • Describe how to implement the standard • Detailed, step-by-step instructions • Subject to regular change. Must be maintained

Policy Framework Definitions Standards • Define acceptable level of security for a specific policy area • May be technology or solution-specific • Provide more measurable criteria for satisfying higher level policy objectives Guidelines • Provide interim guidance. A temporary standard. • Enables guidance for new technology or vulnerability or threat during creation of formal governance

Policies & Procedures based on • BS 7799 - Information Security • ITIL – IT Service Delivery & Support • COBIT – IT Governance, Control Framework & Maturity Model • NIST – Standards, Checklists, Guidelines

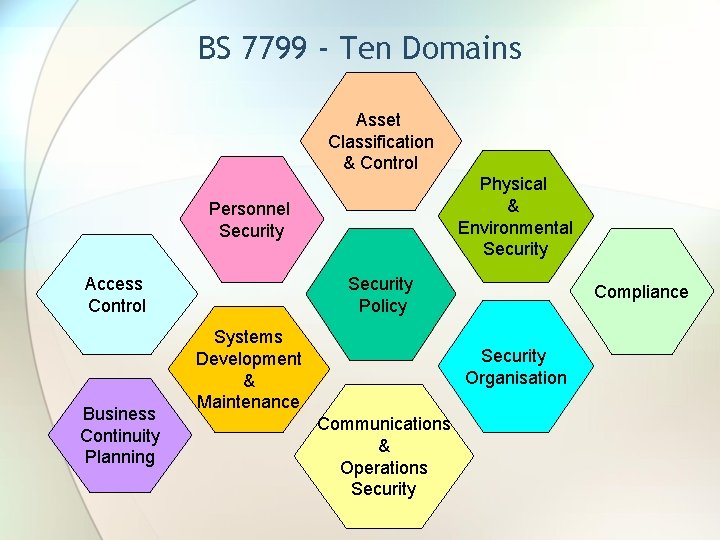
BS 7799 - Ten Domains Asset Classification & Control Physical & Environmental Security Personnel Security Policy Access Control Business Continuity Planning Systems Development & Maintenance Compliance Security Organisation Communications & Operations Security

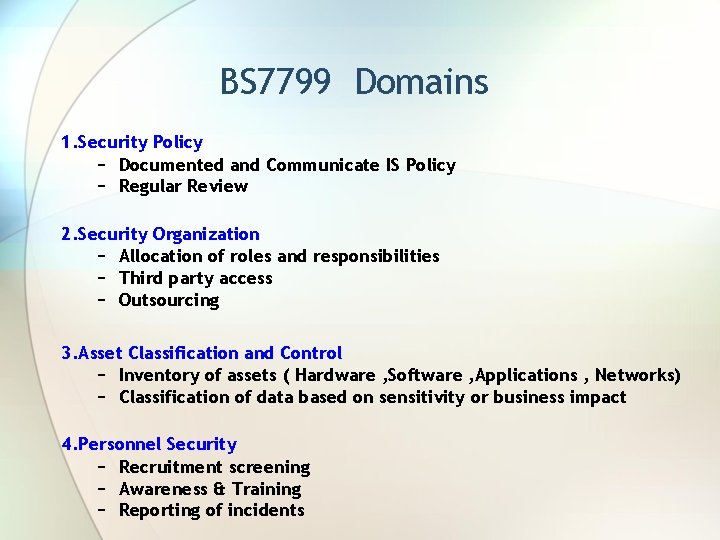
BS 7799 Domains 1. Security Policy − Documented and Communicate IS Policy − Regular Review 2. Security Organization − Allocation of roles and responsibilities − Third party access − Outsourcing 3. Asset Classification and Control − Inventory of assets ( Hardware , Software , Applications , Networks) − Classification of data based on sensitivity or business impact 4. Personnel Security − Recruitment screening − Awareness & Training − Reporting of incidents

BS 7799 Domains 5. Physical and Environmental Security − Physical Security Perimeters − Equipment siting − Clear Desk , Clear Screen 6. Communication & Operations Management − System Planning and Acceptance − Segregation of duties − Email controls 7. Access Control − Application level − Operating System level − Network level

BS 7799 Domains 8. Systems Development and Maintenance − Change Control procedures − Segregation of Test & Production environments 9. Business Continuity Planning − BCP Plans − BCP Team Roles & Responsibilities − Testing BCP Plan − Maintaining and Updating Continuity plans 10. Compliance − Copyright controls − Retention of records − Compliance with Legislation − Compliance with Company policy

Web Server Security

Total number of Web sites –Aug 1995 to April 2005 Source : Netcraft Survey

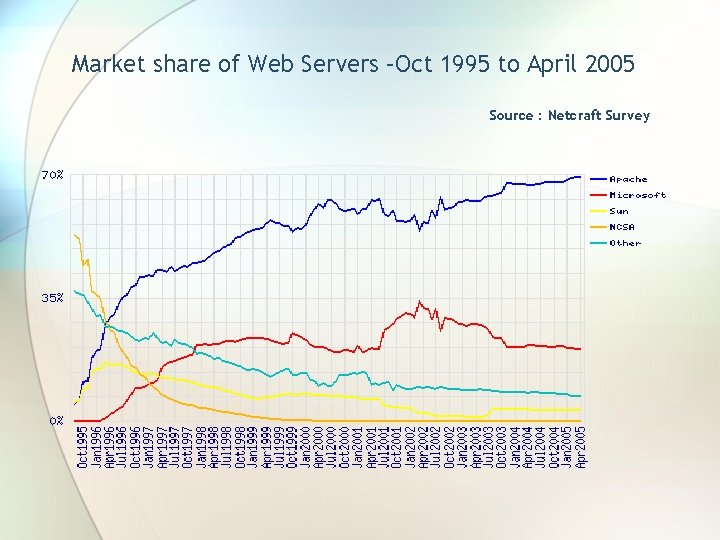
Market share of Web Servers –Oct 1995 to April 2005 Source : Netcraft Survey

What do you need to have your Website on the Internet ? • URL – Universal Resource Locator Address Example http: //www. itec. gov. om • Web Server with Hard disk Space for hosting Content • Internet Connectivity & Bandwidth

What is a Domain Name ? • A domain name is a way of addressing , used for identifying and locating computers on the Internet. • • While computers use Internet Protocol (IP) numbers to locate each other on the Internet, it's not easy for people to remember the IP address. Therefore, domain names were used as easily remembered words and phrases to identify Internet addresses IP. • Domain Name to Public IP Address Mapping • Example : http: //212. 72. 10. 2 to http: //www. itec. gov. om

Domain Name Registration • Domain Registrar – Oman. NIC for. om country domain name • Oman Network Information Center , OMNIC is the authorized body for registering a domain name under. om Top Level Domain. • For more information visit www. omnic. om

Options for hosting your Web site • Within your Own premises or Outside • Within the Country or Outside the Country • Hosting with your Internet Service Provider • Hosting with your Web Hosting Service Provider • Hosting done on Dedicated / Shared Web servers

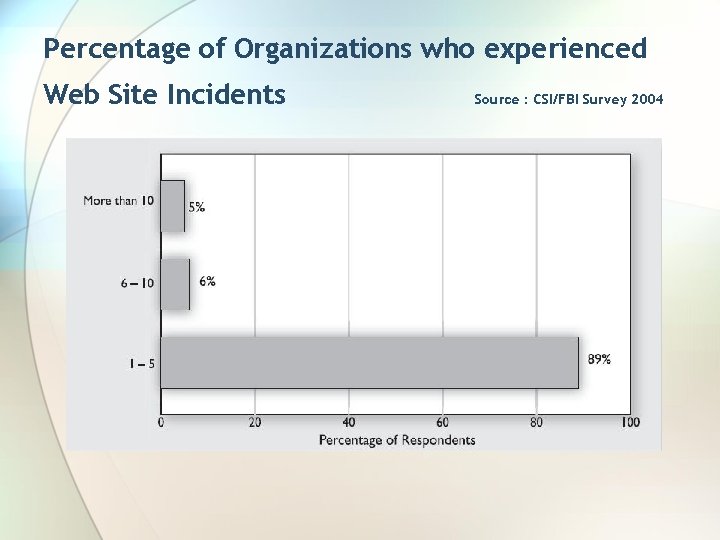
Percentage of Organizations who experienced Web Site Incidents Source : CSI/FBI Survey 2004

Type of Attacks and Dollar Amount of Losses by Type Source : CSI/FBI Survey 2004

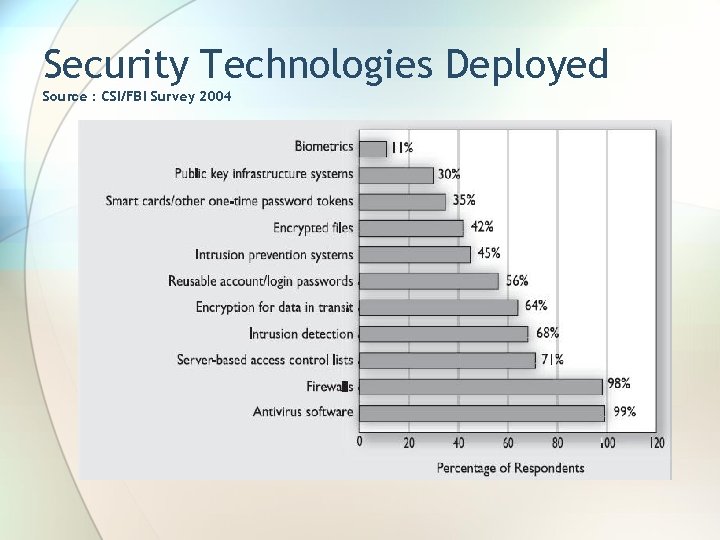
Security Technologies Deployed Source : CSI/FBI Survey 2004

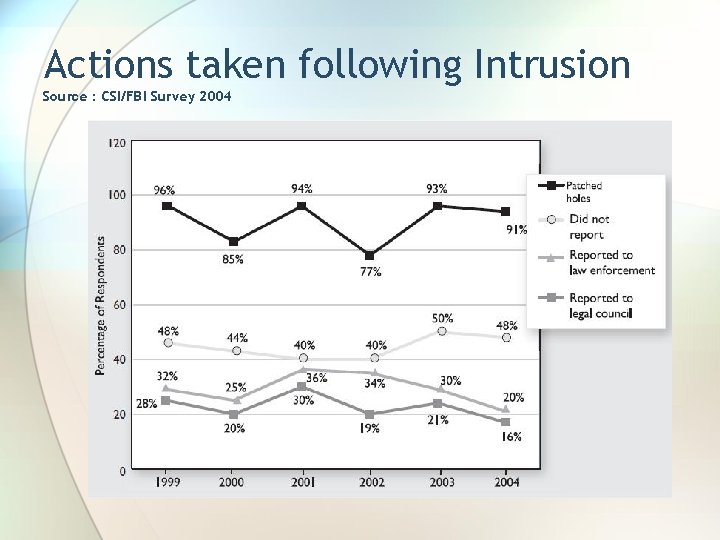
Actions taken following Intrusion Source : CSI/FBI Survey 2004

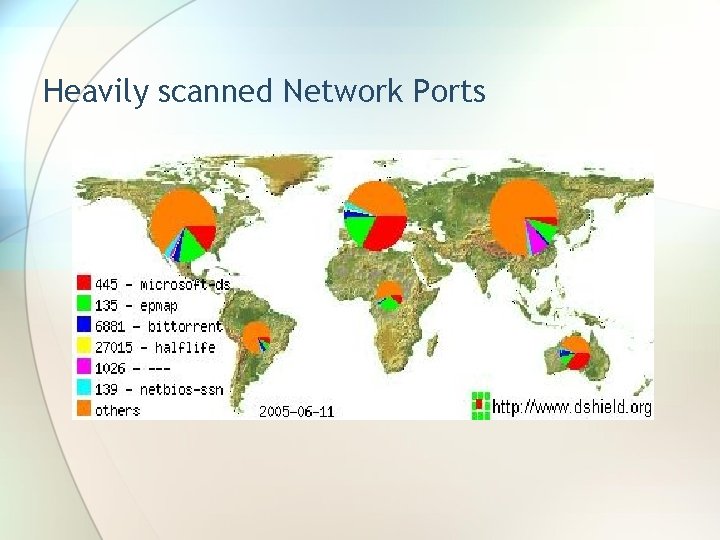
Heavily scanned Network Ports

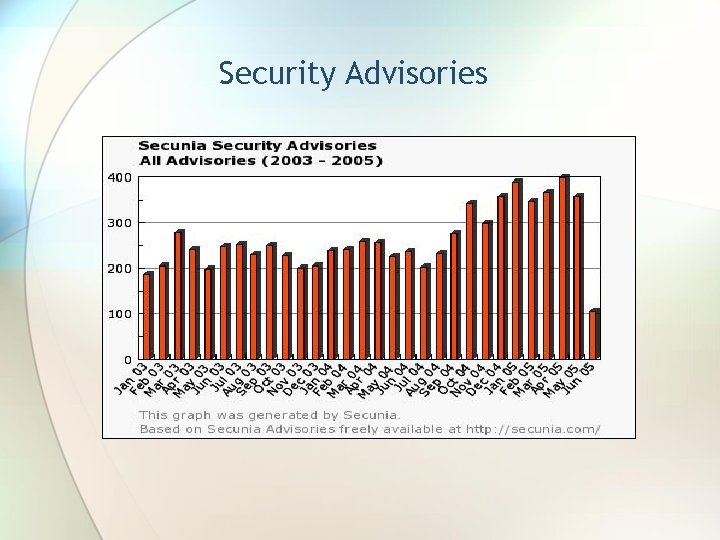
Security Advisories

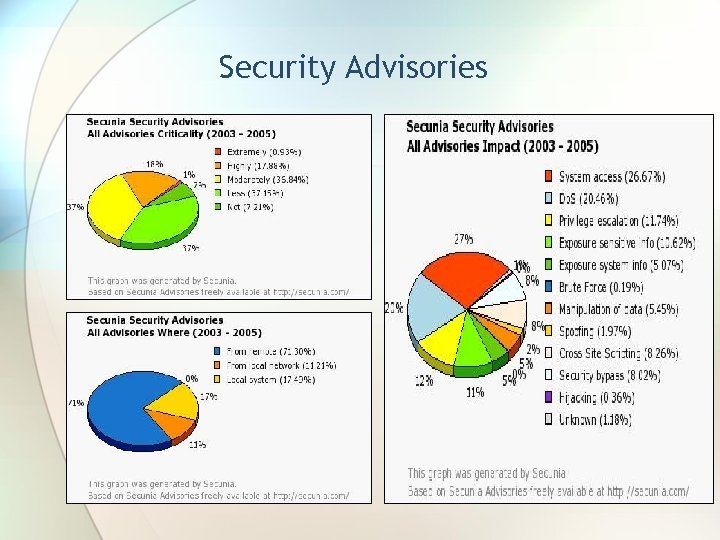
Security Advisories

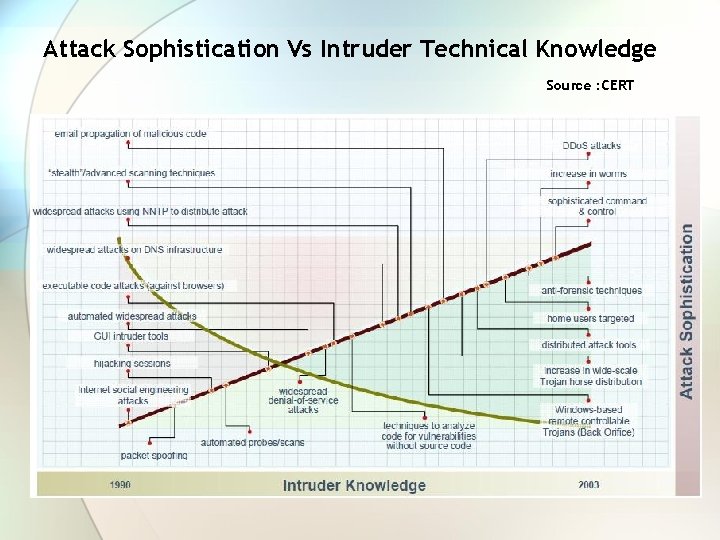
Attack Sophistication Vs Intruder Technical Knowledge Source : CERT

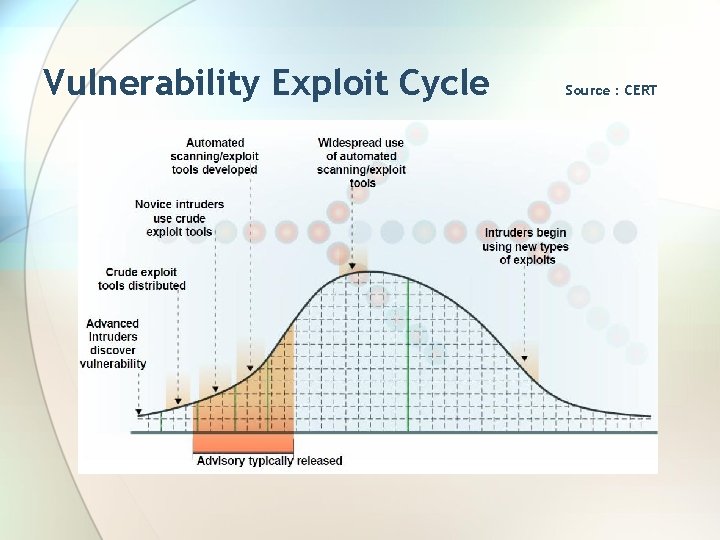
Vulnerability Exploit Cycle Source : CERT

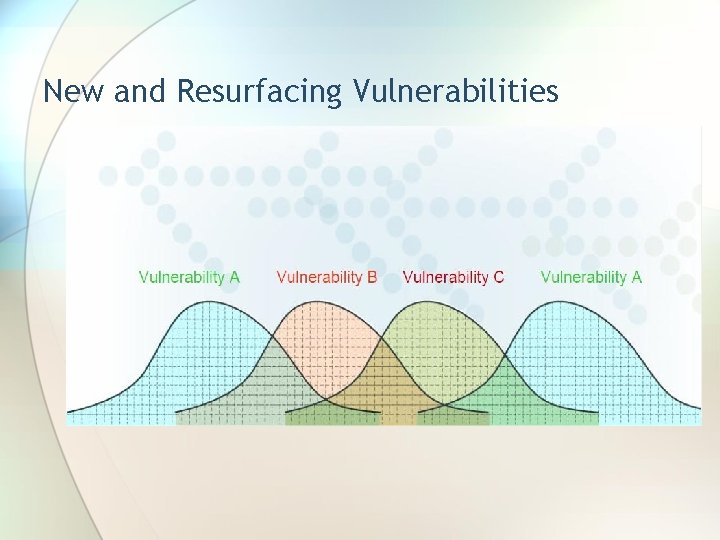
New and Resurfacing Vulnerabilities

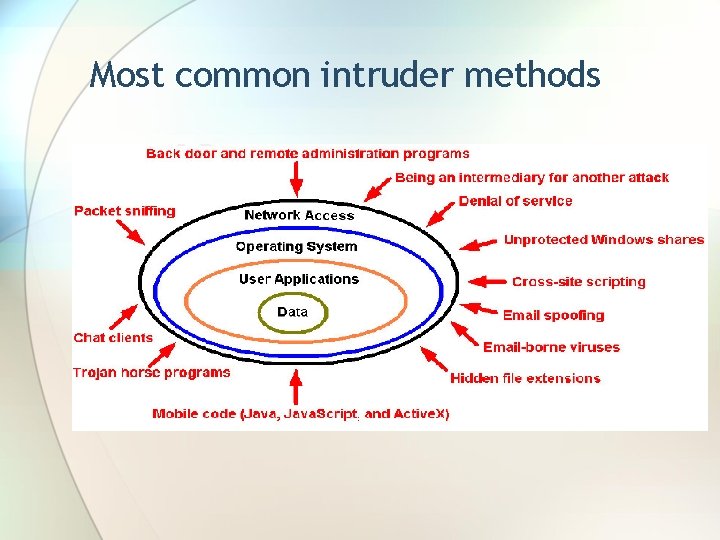
Most common intruder methods

Hackers , Crackers , Snoops • Hackers are content just to get into a system to say they’ve been there, much like mountaineers who climb a mountain “because it’s there. ” • Crackers are more malicious and intentionally do damage once they get into an organization’s computer network, often by modifying a Web page or by stealing or damaging data. • Snoops are generally employees who access private information because they are curious or mischievous.

Typical Characteristics of Hackers are categorized into three groups : • Some focus on a particular operating system. • Some master the workings of individual applications. • Some focus on a particular type of attack. Few hackers master more than one of the above issues, BUT only few have a great deal of experience in ALL.

Typical Characteristics of Hackers • First group of hackers are programmers who have the ability to find unique vulnerabilities in existing software and to create working exploit code. • Second group of hackers have technical skill level equivalent to that of system administrators. • The last groups of hackers are known as script kiddies. Security professionals use the term cracker to refer to malicious computer hackers. The media have given the term hacker a negative description.

What is the Motive ? • • Source : Australia. CERT - 2004 To demonstrate skill (40%) Malicious damage (34%) To anonymise further attacks (26%) Financial gain (18%) Unknown reason (18%) Personal grievance (14%) Political hacktivism (9%) Competitor commercial attack (4%).

What is the Motive ? Source : Australia. CERT - 2004 • Casual Hacker motives − − Monetary gain Intellectual challenge Power Self-expression and peer recognition (often focusing on military and other secure targets) − Youth, frivolity, mischief or curiosity (unleashing unknown consequences). • Criminal Hacker motives − − Vengeance and vindictiveness Attacking the 'system' Terrorism Self-justification through minimization of harm (often ignoring remedial costs, inconvenience, collateral damage and resource waste) − ‘Testing' computer security.

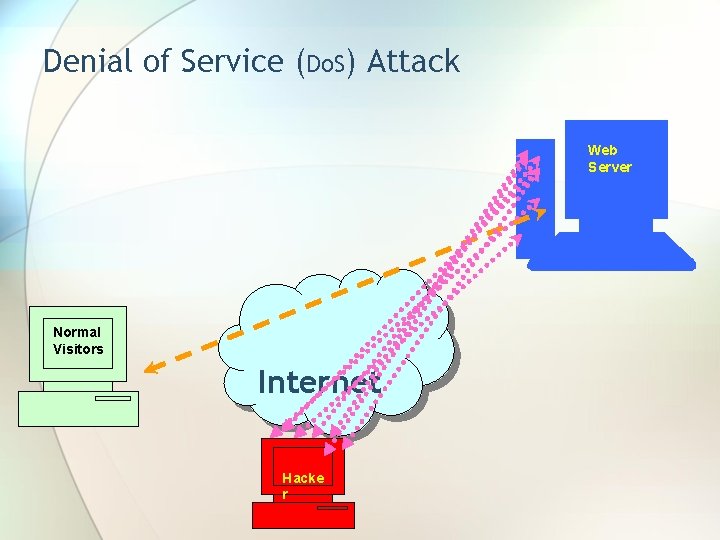
Three basic forms of Network Attacks • Reconnaissance attacks are information-gathering activities in which intruders collect data to later compromise a network. • Access attacks exploit weaknesses in network access points. • Denial-of-service attacks send large numbers of requests to a server, essentially creating a traffic jam and rendering the server inaccessible by legitimate users.

Denial of Service (Do. S) Attack Web Server Normal Visitors Internet Hacke r

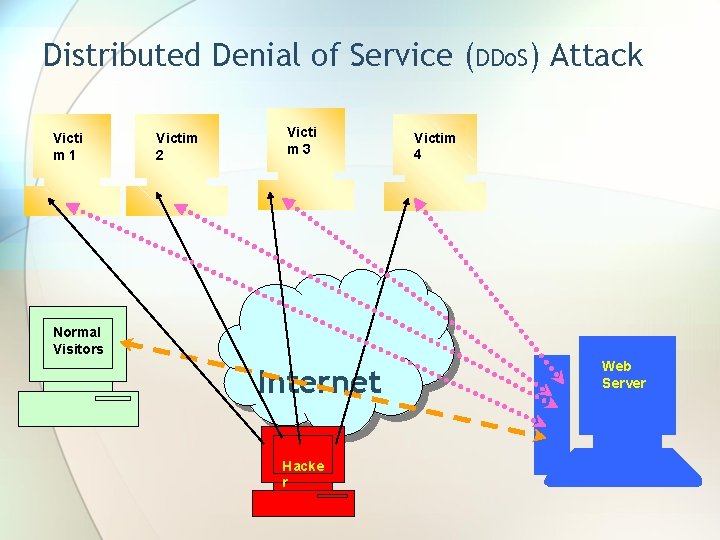
Distributed Denial of Service (DDo. S) Attack Victi m 1 Victim 2 Victi m 3 Victim 4 Normal Visitors Internet Hacke r Web Server

Phases of Hacking 1. Reconnaissance 2. Scanning 3. Gaining Access 4. Maintaining Access 5. Clearing Tracks

1. Reconnaissance • Preparatory phase • Attacker gathers as much information as possible • Passive – Observe patterns , clues pointers − Publicly available info , social engineering , dumpster diving • Active – Probe the network further focus − Tools to detect open ports, router locations , details of Operating systems and applications

2. Scanning • Focused pre-attack phase where attacker used results of reconnaissance phase to get more information about the network • Hackers aim to get a “one point access” through which they will penetrate the network • Highly tool based vulnerability scanners , war dialers, network mapping , sweeping • Classified as High risk from risk perspective

3. Gaining Access • Real Attack phase • Exploits can be over LAN , Internet , Intranet , dialup connection • Concept of exploiting a vulnerability • Numerous factors – Architecture of the system , Skill of the attacker , Long miles for entry • Risk ranked Highest • Example – Password filtering , Denial of service , system hacking, stack based buffer overflows, session hijacking

4. Maintaining Access • Distinguishes between professional hacker and script kiddy • Hacker acquires and retain ownership of the compromised system • Hackers often aim at exclusivity in acquisition and retention of access • Actually the System is under the Hackers control • Backdoors, Rootkits, Trojans • Hackers harden the system from other hackers

5. Clearing Tracks • Hackers aim at working without being detected • Motivation includes prolong stay , continued use of resources , avoiding evidence and consequential actions • The longer they stay , they can launch attacks on other systems on same network • Practices include disable auditing , log alterations, tunneling , Steganography

Short Break

Frequently Asked Questions

My web server has SSL Certificate. Am I not completely safe ? NO • Using an SSL certificate means that the traffic to and from your site using the SSL service is encrypted. • It says nothing about the security of the site or its web applications. • Many SSL sites have serious vulnerabilities that could be identified and fixed

Secure Sockets Layer (SSL) • The SSL protocol establishes a temporary, private, Browser based, point-to-point connection on the public Internet. Widely used in consumer and B 2 B transactions, SSL encrypts data as it moves across the Internet but does not protect the records of completed transactions.

Our web server is protected by Firewall. Am I not completely safe ? NO • A correctly configured firewall can eliminate attacks against services that you do not need to make visible to the Internet. • However, many attacks are against critical services such as HTTP, SSL, SMTP, and DNS, which you need to allow through your firewall in order to operate your normal business. • When you need to make changes to your firewall configuration, penetration testing will give you confidence that you have not opened up more of your services than you intended.

My Network is secure. Is my Web server safe ? NO • Network security is good but it is just only one of the layers in the “Defense in Depth” strategy. • Application & Database layers still pose a threat. • Application testing is very important because even machines that are well administered, and correctly port filtered with no well known vulnerabilities, can be vulnerable to a direct attack on the application's own functionality.

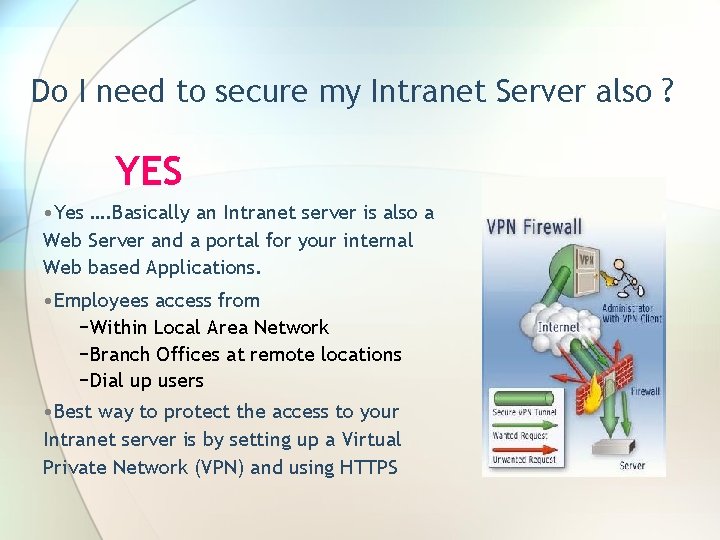
Do I need to secure my Intranet Server also ? YES • Yes …. Basically an Intranet server is also a Web Server and a portal for your internal Web based Applications. • Employees access from −Within Local Area Network −Branch Offices at remote locations −Dial up users • Best way to protect the access to your Intranet server is by setting up a Virtual Private Network (VPN) and using HTTPS

Virtual Private Networking (VPN) A VPN encrypts data transmitted over the public Internet, enabling remote users such as distributors, suppliers, partners, and teleworking employees to securely access a Organization's network. Combined with firewalls, intrusion detection, proper authentication, and other security tools, VPNs provide robust, scalable, low-cost security.

Can you give 100% assurance that all security problems will be found? NO • Even with all the right security layers in place, and best practices followed, new vulnerabilities are discovered every day. • By definition, a testing service can only find vulnerabilities. • And cannot prove the absence of vulnerabilities.

Who is responsible for Security ? YOU • • Content Developers Web Administrators System Administrators Network Administrators Web Hosting Service Provider Internet Service Provider Upstream Bandwidth Provider

How to secure ? BE ALERT & AWARE ! • Security Guidelines & Checklists available • Technology Watch – subscribe to vulnerabilities database and Vendor security bulletins • Test …. Test…Test. . on Development Server before porting to the Production / Live Web Server • Secure the application by design • Follow secure coding principles.

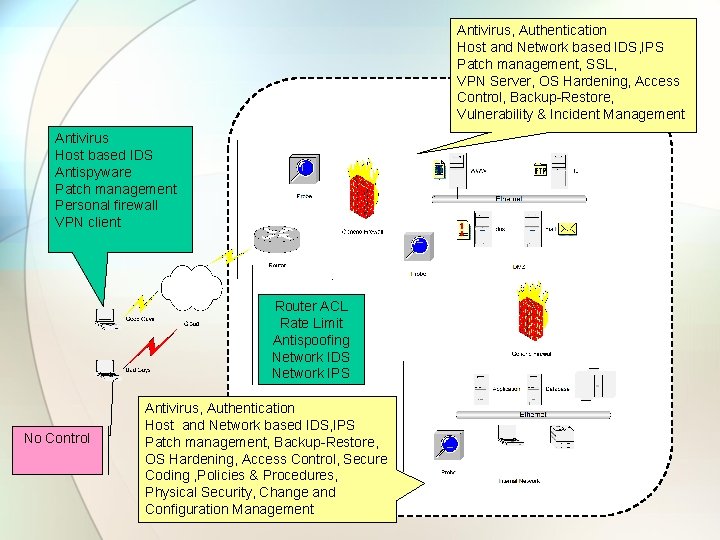
Defensive Wall 1 Blocking Attacks: Network Based • Intrusion Prevention • Intrusion Detection • Spyware Removal • Firewalls • Secure Web Filtering • Secure Email • Managed Security Services

Defensive Wall 2 Blocking Attacks: Host Based • Personal Antivirus • Host Intrusion Prevention System • Personal Firewall • Personal Malware Removal • Scan & Block/Quarantine Systems

Defensive Wall 3 Eliminating Security Vulnerabilities • Vulnerability Management • Patch Management • Configuration Management • Security Configuration Compliance • Application Security Testing

Defensive Wall 4 Safely Support Authorized Users • ID & Access Management • File Encryption • Secure Communication • PKI • SSL Virtual Private Network • Secure Remote Access

Defensive Wall 5: Tools for People Processes and Recovery • Security Information Management • Security Skills Development • Forensics Tools • Regulatory Compliance Tools • Business Recovery • Back-Up

Antivirus, Authentication Host and Network based IDS, IPS Patch management, SSL, VPN Server, OS Hardening, Access Control, Backup-Restore, Vulnerability & Incident Management Antivirus Host based IDS Antispyware Patch management Personal firewall VPN client Router ACL Rate Limit Antispoofing Network IDS Network IPS No Control Antivirus, Authentication Host and Network based IDS, IPS Patch management, Backup-Restore, OS Hardening, Access Control, Secure Coding , Policies & Procedures, Physical Security, Change and Configuration Management

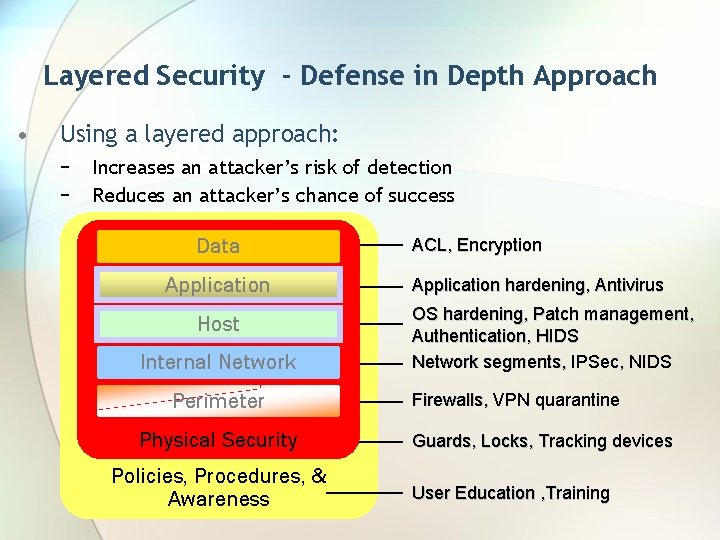
Layered Security - Defense in Depth Approach • Using a layered approach: − − Increases an attacker’s risk of detection Reduces an attacker’s chance of success Data Application Host Internal Network Perimeter Physical Security Policies, Procedures, & Awareness ACL, Encryption Application hardening, Antivirus OS hardening, Patch management, Authentication, HIDS Network segments, IPSec, NIDS Firewalls, VPN quarantine Guards, Locks, Tracking devices User Education , Training

Benefits of Web Application Testing • Web application testing will reveal − Configuration errors − Application loopholes in server code or scripts − Advice on data that could have been exposed due to past errors − Testing for known vulnerabilities − Reducing the risk and enticement to attack − Advice on fixes and future security plans

Typical issues discovered in Application testing • Back doors and debug options • Cross-site scripting • Broken ACLs/Weak passwords • Weak session management • Buffer overflows • Forceful browsing • CGI-BIN manipulation • Form/hidden field manipulation

Typical issues discovered in an Application test include (contd. . ) • • Command injection Insecure use of cryptography Cookie poisoning Risk reduction to zero day exploits SQL injection Server misconfigurations Well-known platform vulnerabilities Errors triggering sensitive information leak

How to protect ? • Apply the latest service packs and security updates or the HTTP service as well as for the Operating System and any applications loaded on this same host. Once the patches are up-to-date, consider using the automatic update feature to enable a higher level of security. • Install host-based anti-virus and Intrusion Detection software. Be sure to keep both current on patches and review the log files frequently. • Disable unused script interpreters and remove their binaries. For example; perl, perlscript, vbscript, javascript, and php. • Enable logging if it is an option and review the logs frequently, preferably through an automated process that summarizes the events and reports exceptions and suspicious events. • Use a syslog-like system to store Operating System and HTTPd logs safely on another system.

How to protect ? (contd. . ) • Remove or restrict the system tools that are commonly used by attackers to assist with both the initial compromise and expansion beyond the initial victim host. For example; tftp(. exe), cmd. exe, bash, net. exe, remote. exe, and telnet(. exe). • Limit the applications running on the host to the HTTP service/daemon and its supporting services. • Be aware of and minimize any vectors into the inner network that enter through public web server(s). For example, Net. BIOS shares or trust relationships. • Use different account naming conventions and unique passwords on public facing systems than on internal systems. Any information leakage from a public facing system should not aid an attack on the internal systems.

Penetration Testing • The goal of a Penetration Test is to "connect the dots" between an asset and its value to the organization, the associated threats or vulnerabilities, and how that translates into a quantifiable risk in hard dollars or intangibles, such as the company's reputation. • Depending upon the level of vulnerabilities found and the potential impact to the environment, a level of risk is assigned to the results and Action Plan drawn and implemented. • Penetration Testing can be done with − Full or Partial knowledge ( White Box approach ) − Null or Zero knowledge ( Black Box approach)

Vulnerability Assessment • Vulnerability Assessment examines vulnerabilities at the various layers and levels. • Various tools which can be used are − − − Nessus (Open-source) SARA (Open-source) Nikto (Open-source) e. Eye Free Utilities & Commercial Scanners Microsoft Baseline Security Analyzer (which has many security benefits and features that are not just IIS-specific) • It is recommended that remote vulnerability assessment tools be run on a network-wide basis, rather than just against known servers, to assess potential vulnerability of "rogue" web server installations

Ethical Hacking • Same as what the unethical hacker does BUT • Done with approval of the Owner of the system /network • Often done under supervision • Has clear time and network window

Honeynets / Honeypots • Mimics actual systems or networks • Attacker does not realize he/she’s on a honeypot • Does not provide Defense • Provides basis for learning Hackers methods • Should not provide path to production system • Designed to be compromised

Forensics • Application of computer investigation and analysis techniques in determining potential legal evidence − Incident Handling − Forensic Investigation − Evidence analysis − Prosecution

Forensics • What happened? • How did it happen? • Who is coming across the network? • Where are they coming from? • Legally-supportable evidence • What did that software do? • Automated analysis of attacks

What To Do Next ? • Security threats and the technology to minimize them are constantly evolving. • Successful protection requires an ongoing, processoriented approach, including the following: − Conduct periodic reviews of security policies and security assessments. − Deploy security technologies that provide secure connectivity, threat defense, and identity management capabilities when and where appropriate. − Patch and protect endpoints, servers, and desktops against known and unknown threats.

Security is a Path and not a Destination • There is no single product , person or policy which can provide Security. • Security can be improved Incrementally. • Closed loop for Improvement - PDCA −Develop policies & requirements −Deploy / Implement solutions −Audit the results

More Information • Visit Security pages of Product - Vendor sites • http: //www. nist. gov • http: //www. cert. org • http: //www. secunia. com • http: //www. sans. org • http: //www. securityfocus. com • http: //www. bsi-global. com

Summary • Awareness Session • Ensure one person from each Ministry/Agency takes responsibility for Information Security. • Copy of the slides available on ITTS website http: //www. itec. gov. om • Take a copy of the Handouts (Checklists, Guideline documents) • Contact ITTS for more information and support

Q&A

Thank you