Information Protection 15 0 New Approach Information Centric












- Slides: 17

Information Protection 15. 0

New Approach: Information Centric Security

New Approach to Security “How do I ensure my sensitive data is protected wherever it goes and only the right people are accessing it? ” Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 3

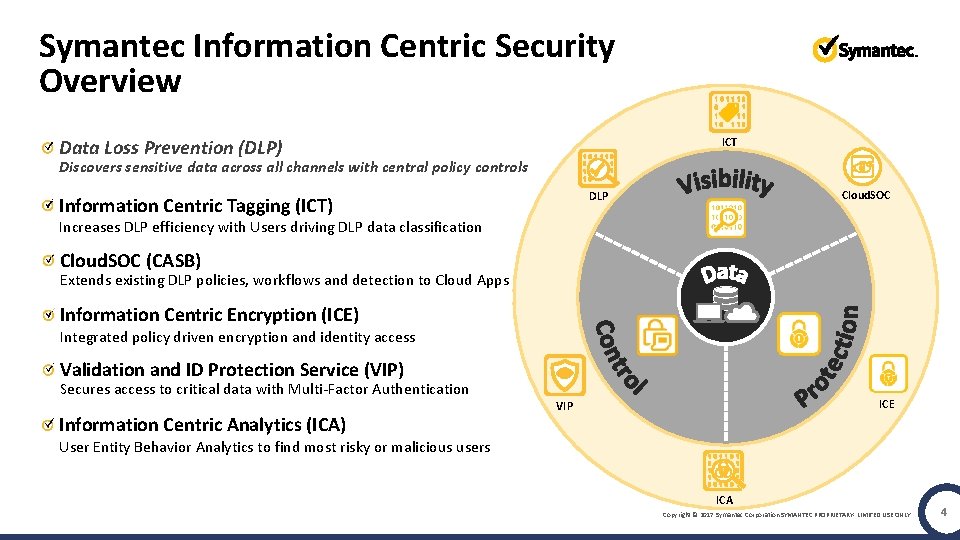
Symantec Information Centric Security Overview ICT Data Loss Prevention (DLP) Discovers sensitive data across all channels with central policy controls Cloud. SOC DLP Information Centric Tagging (ICT) Increases DLP efficiency with Users driving DLP data classification Cloud. SOC (CASB) Extends existing DLP policies, workflows and detection to Cloud Apps Information Centric Encryption (ICE) Integrated policy driven encryption and identity access Validation and ID Protection Service (VIP) Secures access to critical data with Multi-Factor Authentication Information Centric Analytics (ICA) ICE VIP User Entity Behavior Analytics to find most risky or malicious users ICA Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 4

Information Protection with DLP, ICS, and ICA Information Centric Security Suite On Prem & Cloud protection DLP 15. 0 with ICE & ICT DLP CLOUD with ICE & ICT Information Centric Security Module Information Centric Encryption (ICE) Information Centric Analytics (ICA) Information Centric Tagging (ICT) Data Loss Prevention 15. 0 (On-Premises & Cloud) • DLP policy integration with Encryption (ICE) and Tagging (ICT) Information Centric Security Module (ICT + ICE) • Information Centric Encryption: User-driven classification and watermarking • Information Centric Tagging: Tagging drives encryption • w/DLP 15 - DLP policy drives encryption • w/DLP 15 – Tagging driven DLP protection Information Centric Analytics (ICA) • Analyzes telemetry of ICS to predict malicious activity • Simplify incident management Copyright (c) 2017 Symantec Corporation - Internal Use Only Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 5

Demo 6

TEMP – Place. Holder for Video • Go To Demo Video File Demo Story: • Show tagging at point of creation with ICT (Saving a Office Documents) • Show DLP block content based on ICT Tag. • Show DLP Apply ICE on copy to Box based on classification • Show ICA identify the malicious behavior • Show ICE console locking down sensitive document access (revoke) Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 7

DLP 15 Highlights

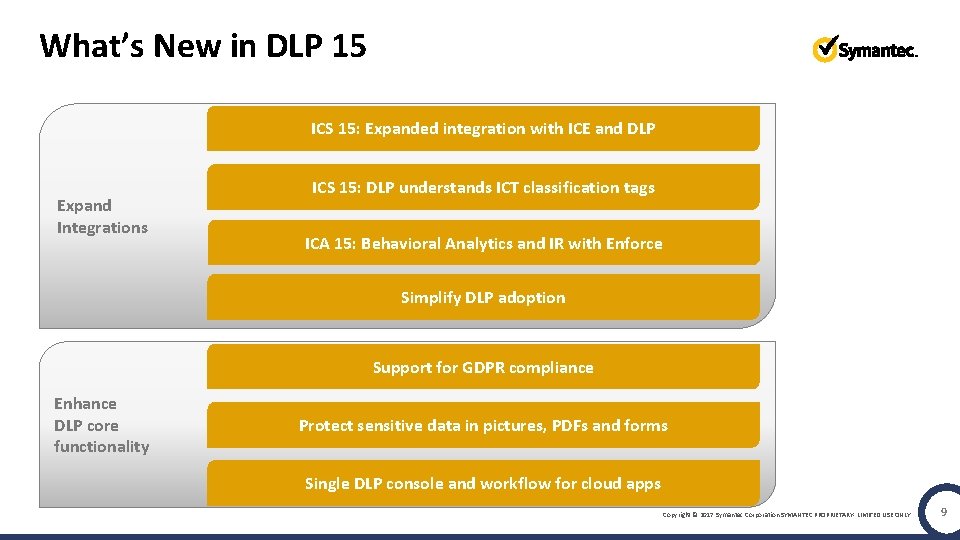
What’s New in DLP 15 ICS 15: Expanded integration with ICE and DLP Expand Integrations ICS 15: DLP understands ICT classification tags ICA 15: Behavioral Analytics and IR with Enforce Simplify DLP adoption Support for GDPR compliance Enhance DLP core functionality Protect sensitive data in pictures, PDFs and forms Single DLP console and workflow for cloud apps Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 9

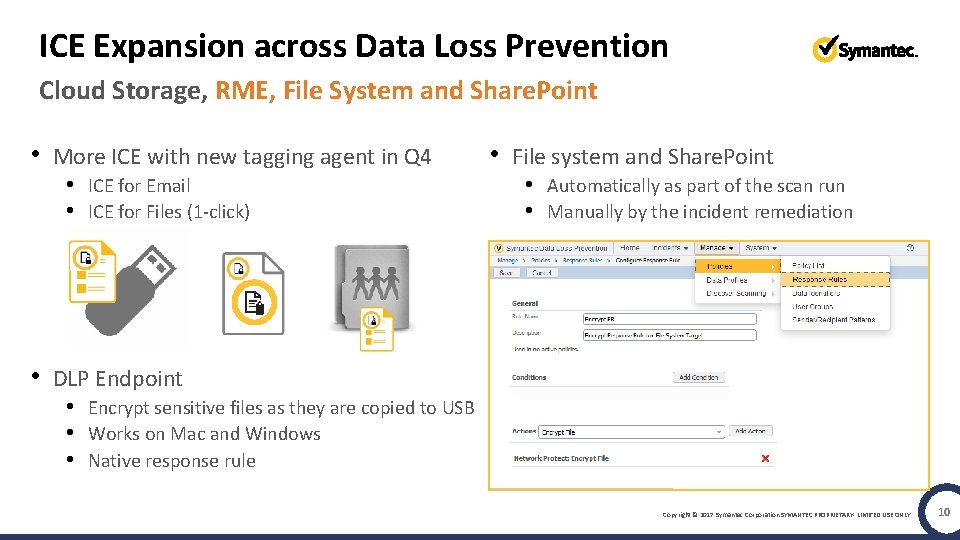
ICE Expansion across Data Loss Prevention Cloud Storage, RME, File System and Share. Point • More ICE with new tagging agent in Q 4 • ICE for Email • ICE for Files (1 -click) • File system and Share. Point • Automatically as part of the scan run • Manually by the incident remediation • DLP Endpoint • Encrypt sensitive files as they are copied to USB • Works on Mac and Windows • Native response rule Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 10

DLP + CASB on a single console How do I consolidate all my policies? Symantec Data Loss Prevention Symantec Cloud. SOC The Gold Standard in DLP Leading-Edge Cloud Access Security Broker Extend DLP to capture ALL sensitive data at rest and in motion the cloud Leverage existing policies and workflows without compromising performance Gain full cloud access security broker functionality Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 11

DLP + Symantec Information Centric Tagging (ICT) How can I leverage my biggest knowledge asset, my employees, to detect what is truly sensitive? DLP STORAGE DLP ICT EMAIL TAGGING DLP ENDPOINT DLP NETWORK CONTENT BASED DETECTION USER BASED CLASSIFICATION OFFICE/PDF DOC TAGGING MOBILE TAGGING DLP CLOUD 101011 0110101 Combining state of the art DLP technology with user-driven classification to identify and protect sensitive data Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 12 12

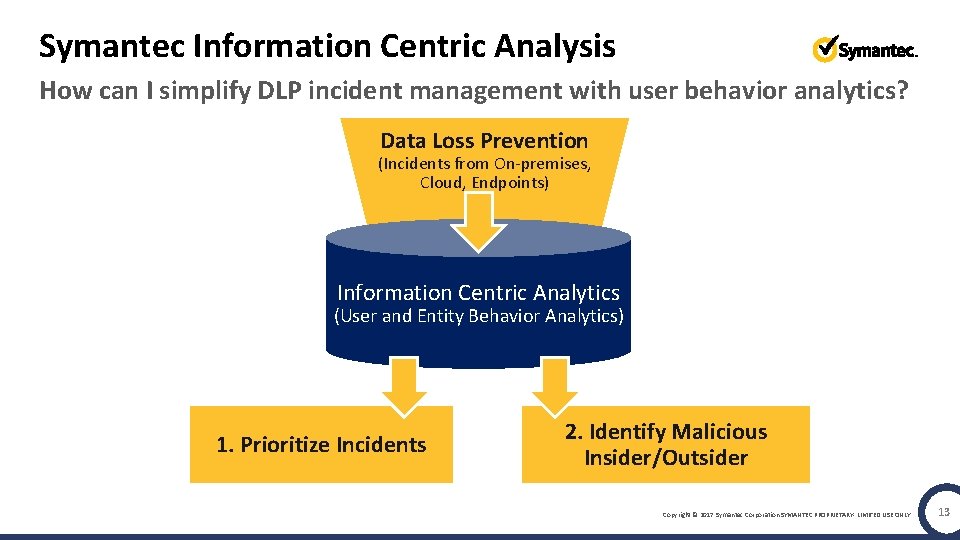
Symantec Information Centric Analysis How can I simplify DLP incident management with user behavior analytics? Data Loss Prevention (Incidents from On-premises, Cloud, Endpoints) Information Centric Analytics (User and Entity Behavior Analytics) 1. Prioritize Incidents 2. Identify Malicious Insider/Outsider Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 13

Data Protection for GDPR How can use my Data Protection to help become GDPR compliant? • DLP Risk assessment for GDPR • Proactive tools: Information Centric • • Security (data classification, analytics, and encryption service) Detect PII in scanned forms, pictures and images (passports, credit cards, SSN) GDPR breach detection & response: analysis to respond to data breach via Information Centric Analytics https: //www. brighttalk. com/we bcast/13361/274657/the-fourstages-of-gdpr-readiness Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 14

Summary 1 Cloud DLP: DLP in the cloud for the cloud (single pane of glass) 2 ICE: Data protection for mobile & collaboration with DLP-Driven ICE 3 Tagging: DLP to enable data classification everywhere 4 Analytics: simplification and expansion through UBA 5 More: Out-of-the-box GDPR policies, OCR, DLP appliance Copyright © 2017 Symantec Corporation SYMANTEC PROPRIETARY- LIMITED USE ONLY 15

Q&A

Thank You!