Operating Systems Protection Alok Kumar Jagadev Protection Protection



















- Slides: 30

Operating Systems Protection Alok Kumar Jagadev

Protection • Protection refers to a mechanism for controlling the access of programs, processes, or users to the resources defined by a computer system. • Protection ensures that the resources of the computer are used in a consistent way. • It also ensures that each object accessed correctly and only by those processes that are allowed to do so. 2

Goals of Protection • As computer systems have become more sophisticated and pervasive in their applications, the need to protect their integrity has also grown. • We need to provide protection for several reasons. The most obvious is the need to prevent the mischievous, intentional violation of an access restriction by user. • An unprotected resource cannot defend against use (or misuse) by an unauthorized or incompetent user. • A protection-oriented system provides means to distinguish between authorized and unauthorized usage. 3

Goals of Protection (Contd…) • The role of protection in a computer system is to provide a mechanism for the enforcement of the policies governing resource use. • These policies can be established in a variety of ways. • Some are fixed in the design of the system, while others are formulated by the management of a system. • Still others are defined by the individual users to protect their own files and programs. • A protection system must have the flexibility to enforce a variety of policies. 4

Principles of Protection • The time-tested guiding principle for protection is the Principle of least privilege. • It dictates that programs, users, and even systems be given just enough privileges to perform their tasks. • Consider the analogy of a security guard with a passkey. If this key allows the guard into just the public areas that he guards, then misuse of the key will result in minimal damage. • If, however, the passkey allows access to all areas, then damage from its being lost, stolen, misused, copied, or otherwise compromised will be much greater. 5

Principles of Protection (Contd…) • An operating system following the principle of least privilege implements its features, programs, system calls, and data structures so that failure or compromise of a component does the minimum damage and allows the minimum damage to be done. • The principle of least privilege can help produce a more secure computing environment. 6

Domain of Protection • A computer system is a collection of processes and objects. • By objects, we mean both hardware objects (such as the CPU, printer) and software objects(such as files, programs). • Each object has a unique name that differentiates it from all other objects in the system, and each can be accessed only through well-defined and meaningful operations. 7

Domain of Protection (Contd…) • A process should be allowed to access only those resources for which it has authorization. • Furthermore, at any time, a process should be able to access only those resources that it currently requires to complete its task. 8

Domain Structure • A process operates within a Protection Domain that specifies the resources that the process may access. • Each domain defines a set of objects and the types of operations that may be invoked on each object. • The ability to execute an operation on an object is an access right. 9

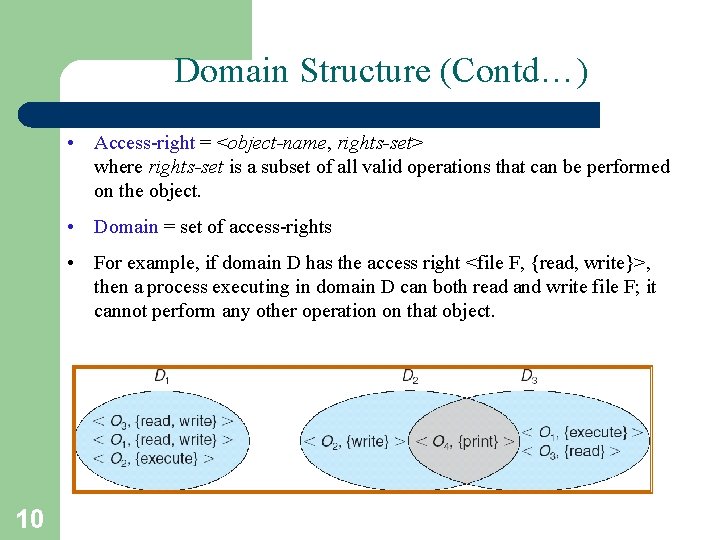
Domain Structure (Contd…) • Access-right = <object-name, rights-set> where rights-set is a subset of all valid operations that can be performed on the object. • Domain = set of access-rights • For example, if domain D has the access right <file F, {read, write}>, then a process executing in domain D can both read and write file F; it cannot perform any other operation on that object. 10

Domain Structure (Contd…) • A domain can be realized in a variety of ways: • Each user may be a domain. In this case, the set of objects that can be accessed depends on the identity of the user. • Each process may be a domain. In this case, the set of objects that can be accessed depends on the identity of the process. 11

Domain Implementation (UNIX) • System consists of 2 domains: – User – Supervisor • UNIX – Domain = user-id – Domain switch accomplished via file system. • Each file has associated with it a domain bit (setuid bit). • When file is executed and setuid = on, then user-id is set to owner of the file being executed. When execution completes user-id is reset. 12

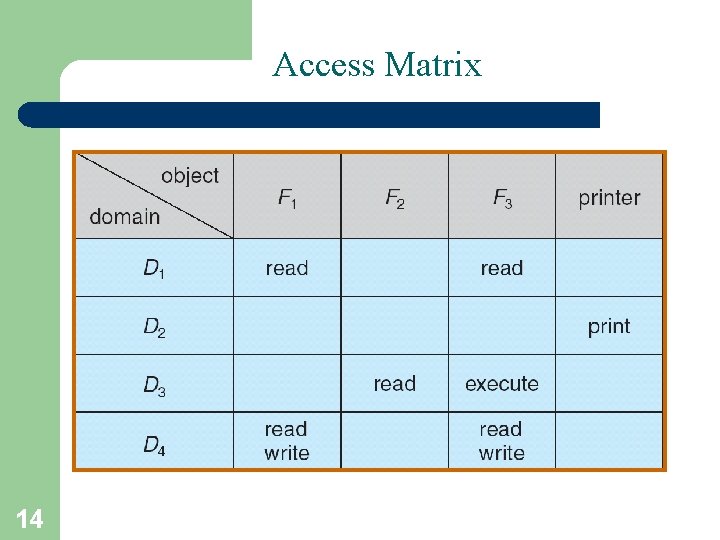
Access Matrix • The model of protection can be viewed abstractly as a matrix, called an Access Matrix. • The rows of the access matrix represent domains, and the columns represent objects. • Each entry in the matrix consists of a set of access rights. • Entry Access(i, j) is the set of operations that a process executing in Domaini can invoke on Objectj 13

Access Matrix 14

Use of Access Matrix • If a process in Domain Di tries to do “op” on object Oj, then “op” must be in the access matrix. • Can be expanded to dynamic protection. – Operations to add, delete access rights. – Special access rights: • owner of Oi • copy op from Oi to Oj • control – Di can modify Dj access rights • transfer – switch from domain Di to Dj 15

Use of Access Matrix (Cont. ) • Access matrix design separates mechanism from policy. – Mechanism • Operating system provides access-matrix + rules. • If ensures that the matrix is only manipulated by authorized agents and that rules are strictly enforced. – Policy • User dictates policy. • Who can access what object and in what mode. 16

Implementation of Access Matrix • Each column = Access-control list for one object Defines who can perform what operation. Domain 1 = Read, Write Domain 2 = Read Domain 3 = Read • Each Row = Capability List (like a key) For each domain, what operations allowed on what objects. Object 1 – Read Object 4 – Read, Write, Execute Object 5 – Read, Write, Delete, Copy 17

Access Matrix of Figure A With Domains as Objects • Domain switching can be easily supported under this model, simply by providing "switch" access to other domains 18 Figure B

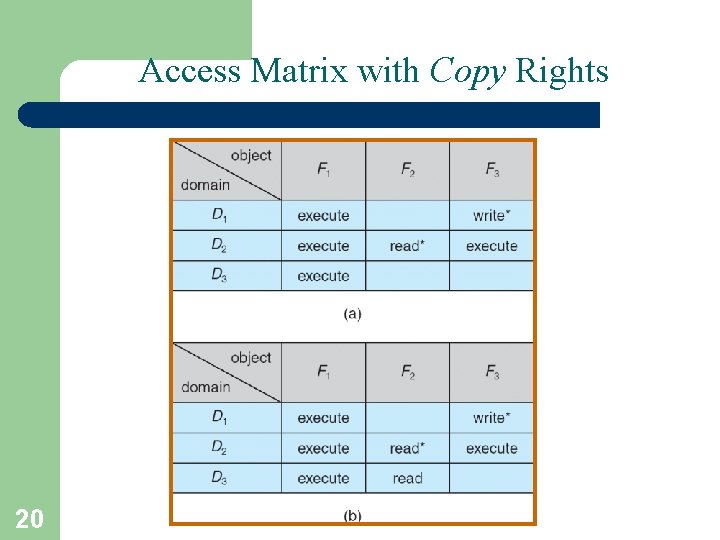
Access Matrix with Copy Rights • The ability to copy rights is denoted by an asterisk, indicating that processes in that domain have the right to copy that access within the same column, i. e. for the same object. • There are two important variations: If the asterisk is removed from the original access right, then the right is transferred, rather than being copied. This may be termed a transfer right as opposed to a copy right. • If only the right and not the asterisk is copied, then the access right is added to the new domain, but it may not be propagated further. That is the new domain does not also receive the right to copy the access. This may be termed a limited copy right. 19

Access Matrix with Copy Rights 20

Access Matrix With Owner Rights 21

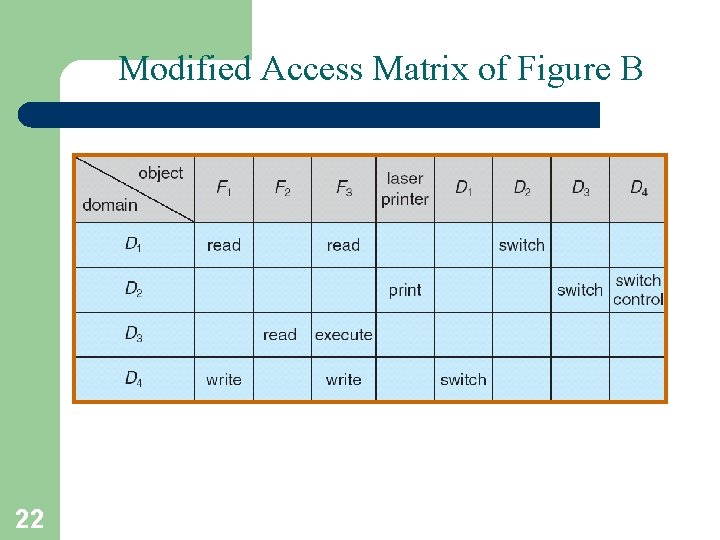
Modified Access Matrix of Figure B 22

Access Control • The basic problem of computer protection is to control which objects a given program can access, and in what ways. • Objects are things like files, sound cards, other programs, the network, modem etc. • Access means what kind of operations can be done on these objects. • Examples include reading a file, writing to a file and creating or deleting objects. 23

Access Control (Contd…) • When we talk about ``controlling access, '' we are really talking about four kinds of things: • Preventing access. • Limiting access. • Granting access. • Revoking access. • A good example of this is found in Solaris 10. • Solaris uses Role-based access control(RBAC) to adding the principle. 24

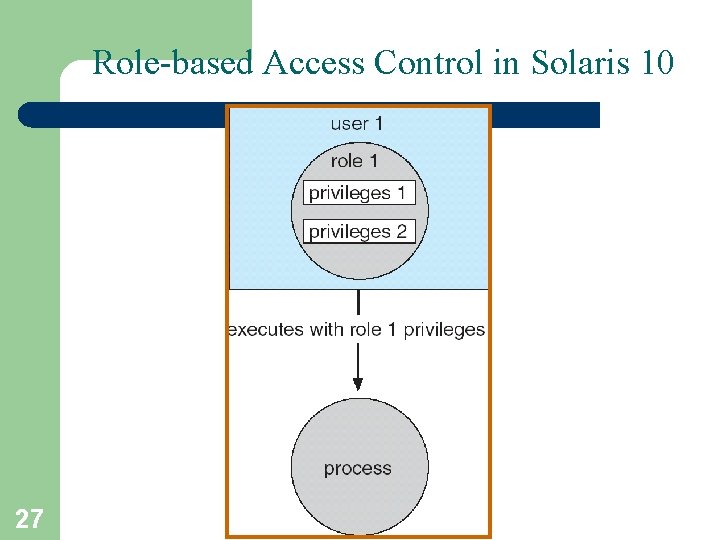
Access Control • Protection can be applied to non-file resources • Solaris 10 provides role-based access control to implement least privilege – Privilege is right to execute system call or use an option within a system call – Can be assigned to processes – Users assigned roles granting access to privileges and programs 25

A Role-based access control (RBAC) § Role-based access control (RBAC) is a security feature for controlling user access to tasks that would normally be restricted to the root user. § In conventional UNIX systems, the root user, also referred to as superuser. § The root user has the ability to read and write to any file, run all programs, and send kill signals to any process. 26

Role-based Access Control in Solaris 10 27

Revocation of Access Rights • Access List – Delete access rights from access list. – Simple – Immediate • Capability List – Scheme required to locate capability in the system before capability can be revoked. – Reacquisition – Back-pointers – Indirection – Keys 28

Capability-Based Systems • Hydra – Fixed set of access rights known to and interpreted by the system. – Interpretation of user-defined rights performed solely by user's program; system provides access protection for use of these rights. • Cambridge CAP System – Data capability - provides standard read, write, execute of individual storage segments associated with object. – Software capability - interpretation left to the subsystem, through its protected procedures. 29

Language-Based Protection • Specification of protection in a programming language allows the high -level description of policies for the allocation and use of resources. • Language implementation can provide software for protection enforcement when automatic hardware-supported checking is unavailable. • Interpret protection specifications to generate calls on whatever protection system is provided by the hardware and the operating system. 30