Representing Identity CSSE 490 Computer Security Mark Ardis









- Slides: 13

Representing Identity CSSE 490 Computer Security Mark Ardis, Rose-Hulman Institute April 19, 2004 1

Overview l l l 2 Certificates Network identities Remailers

What is Identity? l l 3 Def: A principal is a unique entity. An identity specifies a principal. A principal may be a person, an organization, or an object

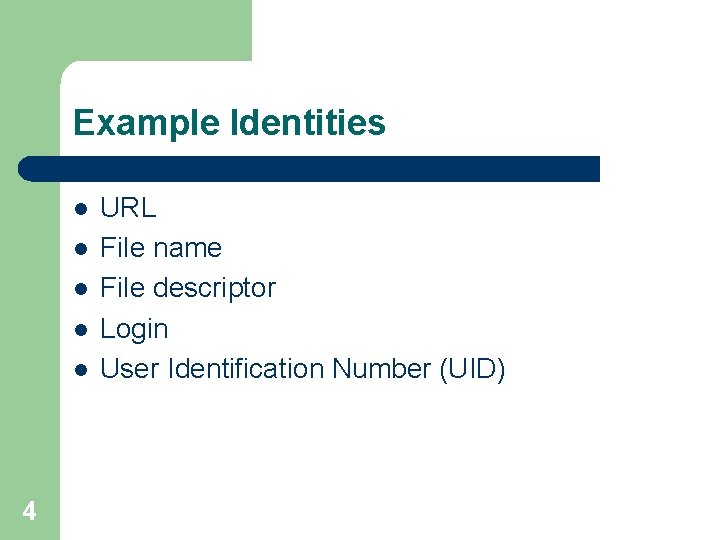
Example Identities l l l 4 URL File name File descriptor Login User Identification Number (UID)

Certificates l l 5 Used to bind crypto keys to identifiers Certification Authority (CA) vouches for identity of principal to which certificate is issued CA authentication policy describes level of authentication required to identify principal when certificate issued CA issuance policy describes principals to whom CA will issue certificates

Internet Policy Registration Authority (IPRA) l l Sets policies for all subordinate CAs Certifies Policy Certification Authorities (PCAs) – – l l 6 each may have their own authentication and issuance policy may not conflict with IPRA PCAs issue certificates to organizations and individuals

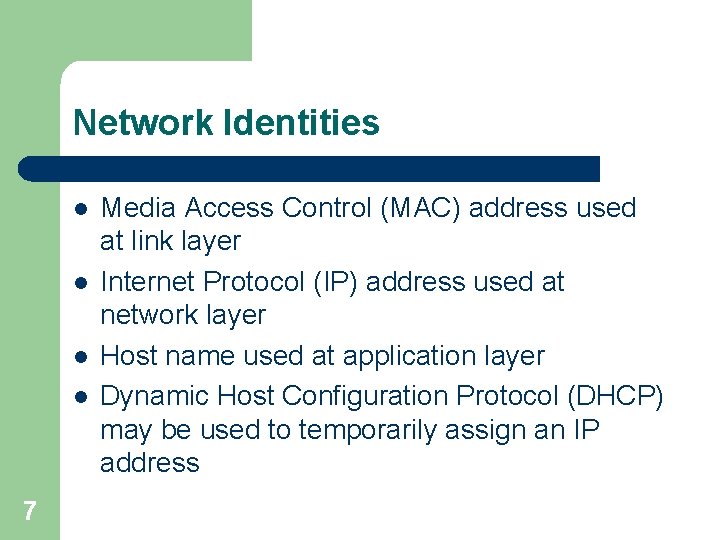
Network Identities l l 7 Media Access Control (MAC) address used at link layer Internet Protocol (IP) address used at network layer Host name used at application layer Dynamic Host Configuration Protocol (DHCP) may be used to temporarily assign an IP address

Domain Name System (DNS) Records l l l 8 Forward: map host name to IP address Reverse: map IP addresses to host names May compare forward and reverse mappings in order to determine whether to trust a host name

Cookies l l Used to represent state of a web session Fields: – – – 9 Name, value: bind value to name Expires: delete at end of session or at specified time Domain: to whom cookie may be sent, must have embedded ". " Path: restricts domain Secure: whether to use SSL

Anonymity on the Web l l Pseudo-anonymous remailer - replaces originating email address before forwarding, keeps mapping of anonymous identities and associated origins Cypherpunk remailer (type 1) - deletes header of incoming message and forwards remainder – – 10 typically used in chain typically enciphered messages

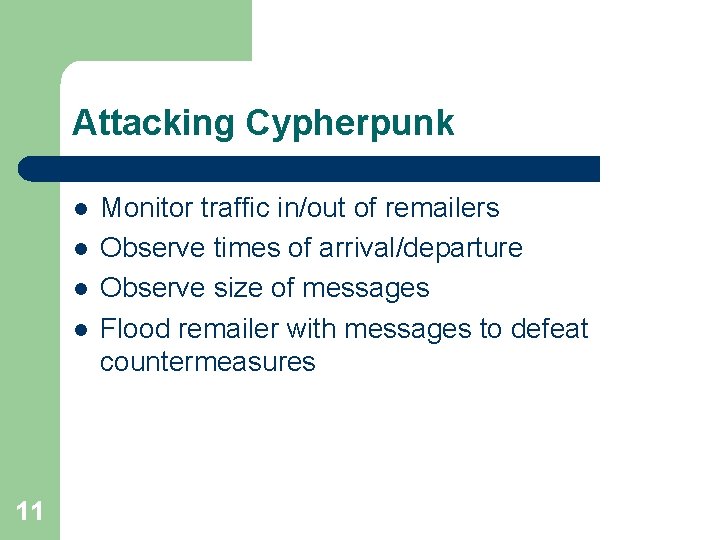
Attacking Cypherpunk l l 11 Monitor traffic in/out of remailers Observe times of arrival/departure Observe size of messages Flood remailer with messages to defeat countermeasures

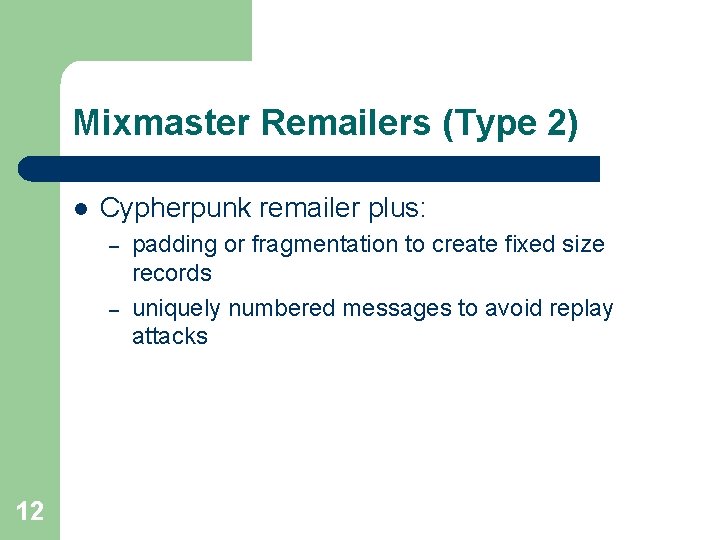
Mixmaster Remailers (Type 2) l Cypherpunk remailer plus: – – 12 padding or fragmentation to create fixed size records uniquely numbered messages to avoid replay attacks

Why is Anonymity Needed? l l l 13 Whistleblowing Protection of privacy ? ? ?