Government of Oman ITTS Security Audit Office Dr








- Slides: 23

Government of Oman ITTS Security & Audit Office Dr Salim Al-Ruzaiqi 1 November 2002

What is Information security Protection of Information & Information assets from a wide range of threats against – Ø Confidentiality Ø Integrity Ø Availability For the internal use of the Government of Oman

Definition Confidentiality It concerns the protection of sensitive information from unauthorized disclosure Integrity It relates to the accuracy and completeness of information as well as to its validity in accordance with business values and expectations Availability It relates to information being available when required by the business process now and in the future. It also concerns the safeguarding of necessary resources and associated capabilities For the internal use of the Government of Oman

What is Information and where does it exist? Ø Ø Ø Financial data Budgetary records Police records Tender documents HR Records Health records For the internal use of the Government of Oman

Classification of information Information can be broadly classified as under – Ø Ø Public Internal Restricted Confidential For the internal use of the Government of Oman

Oman’s Critical Infrastructure dependent on IT Ø Ø Ø Oil & Gas Production, Storage & Delivery facilities Electric Power & Water Banking and Finance Telecommunications Emergency Services Government Services In the networked world the traditional lines of defense no longer protect Businesses from those who would want to harm them. For the internal use of the Government of Oman

Threats to IT Infrastructure Threats to IT infrastructure include: Ø Unauthorized copying of sensitive & confidential Information Ø Intentional or Unintentional changes to confidential and sensitive Information Ø Unauthorized copying of software Ø Viruses, Worms & Trojan Horses Any threat which can be materialized against government IT resources may have a direct impact on national security For the internal use of the Government of Oman

Vulnerabilities of IT infrastructure Vulnerabilities in the IT infrastructure can be classified under 3 categories • Process • Lack of security policies and directives • Procedures • Monitoring • Corrective actions • People • Awareness • Incompetent personnel • lack of training for personnel • Technology • Use of un-suitable products / systems • Improperly configured products and systems For the internal use of the Government of Oman

How can one achieve information security? Ø Implementing an Information security framework Ø Implementing a suitable set of controls – Policies, Processes, Procedures, Organizational structures, Software and Hardware functions. Ø Controls need to be – Established, implemented, monitored, reviewed and improved. For the internal use of the Government of Oman

What is ITTS Doing For the internal use of the Government of Oman

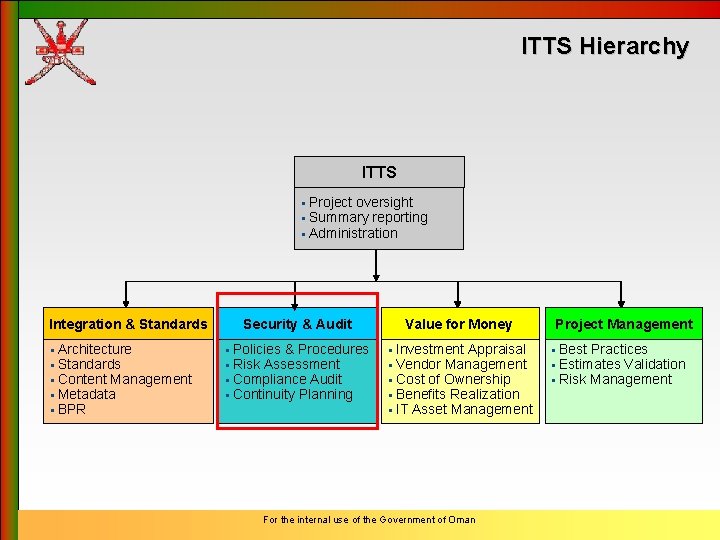
ITTS Hierarchy ITTS § Project oversight § Summary reporting § Administration Integration & Standards § Architecture § Standards § Content Management § Metadata § BPR Security & Audit Value for Money § Policies & Procedures § Risk Assessment § Compliance Audit § Continuity Planning § Investment Appraisal § Vendor Management § Cost of Ownership § Benefits Realization § IT Asset Management For the internal use of the Government of Oman Project Management § Best Practices § Estimates Validation § Risk Management

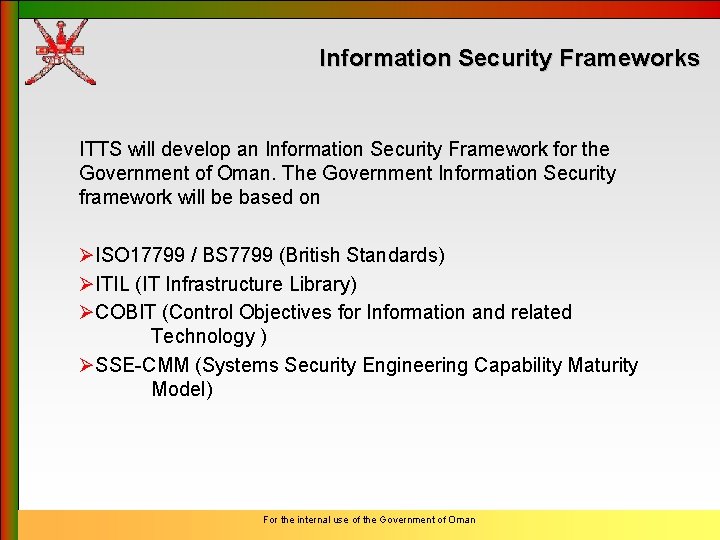
Information Security Frameworks ITTS will develop an Information Security Framework for the Government of Oman. The Government Information Security framework will be based on ØISO 17799 / BS 7799 (British Standards) ØITIL (IT Infrastructure Library) ØCOBIT (Control Objectives for Information and related Technology ) ØSSE-CMM (Systems Security Engineering Capability Maturity Model) For the internal use of the Government of Oman

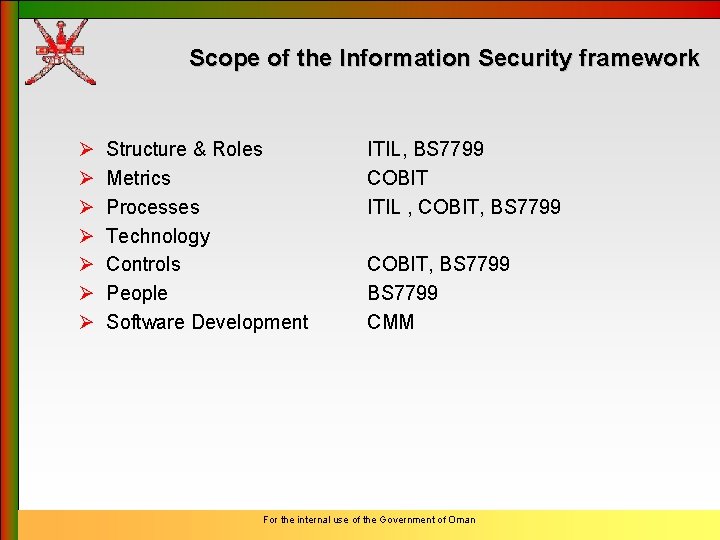
Scope of the Information Security framework Ø Ø Ø Ø Structure & Roles Metrics Processes Technology Controls People Software Development ITIL, BS 7799 COBIT ITIL , COBIT, BS 7799 CMM For the internal use of the Government of Oman

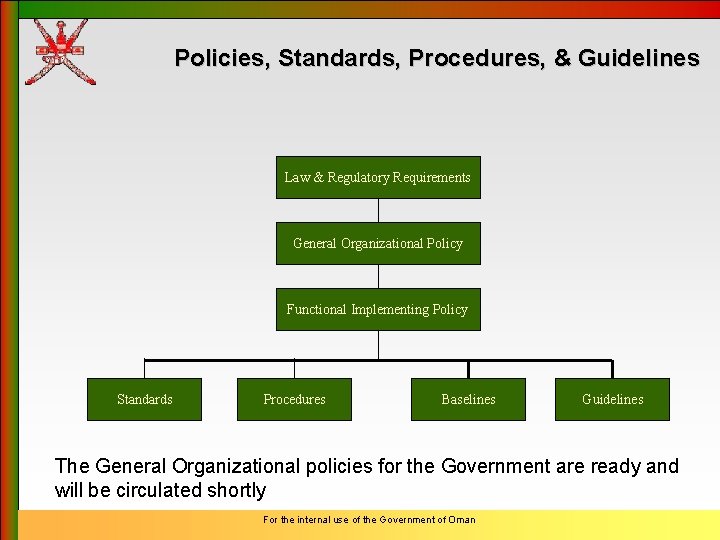
Policies, Standards, Procedures, & Guidelines Law & Regulatory Requirements General Organizational Policy Functional Implementing Policy Standards Procedures Baselines Guidelines The General Organizational policies for the Government are ready and will be circulated shortly For the internal use of the Government of Oman

Responsibilities of Security & Audit Office Ø Assist in creating and maintaining a security conscious culture within the ministries Ø Assist ministries in information security policies and practices Ø Ensure that the government’s/ministries information security activities meet the needs of the government Ø Promote the visibility of business support for information security throughout government Ø Ensure that security is part of the information systems planning process Ø Approve and support major initiatives to enhance information security Ø Monitor business requirements to identify changing and emerging information security needs Ø Establish document classification standards for the Government For the internal use of the Government of Oman

Cyber Emergency Response Team ITTS is planning a cyber emergency response team for the Sultanate of Oman, the functions of the Cyber Emergency Response Team will be to provide computer incident prevention, response and mitigation strategies for ministries, an alerting mechanism and an incident reporting scheme Ø Provide technical assistance in responding to incidents, or provide information of sites where assistance can be got Ø Notify the ministries about the reported incidents Ø Notify the ministries about newly released vulnerabilities, viruses, and worms Ø Use the incidents reported to create and distribute statistics of intruder activity Ø Maintain a database of Security officers within each ministry to whom notifications can be sent For the internal use of the Government of Oman

Training and Awareness Ø ITTS conducts continuous training and awareness campaigns for Government staff on Information Security to ensure that Government employees fully understand the implications of security Ø Some of the trainings conducted by ITTS Ø Web server Security Ø Computer Incident response Ø Trainings planned in the near future Ø Training on risk assessment and risk management Ø Training on Government Policies Ø Training on Business Continuity planning and Disaster recovery planning Ø Training on Auditing Information Systems For the internal use of the Government of Oman

Technical Infrastructure Planned For the internal use of the Government of Oman

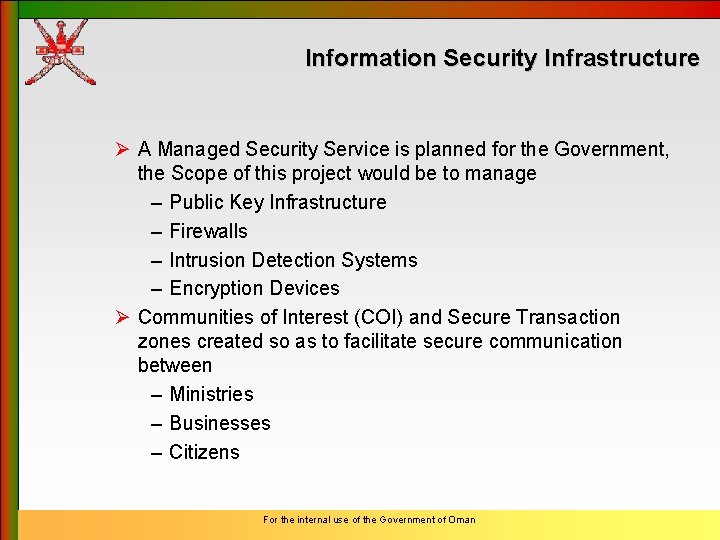
Information Security Infrastructure Ø A Managed Security Service is planned for the Government, the Scope of this project would be to manage – Public Key Infrastructure – Firewalls – Intrusion Detection Systems – Encryption Devices Ø Communities of Interest (COI) and Secure Transaction zones created so as to facilitate secure communication between – Ministries – Businesses – Citizens For the internal use of the Government of Oman

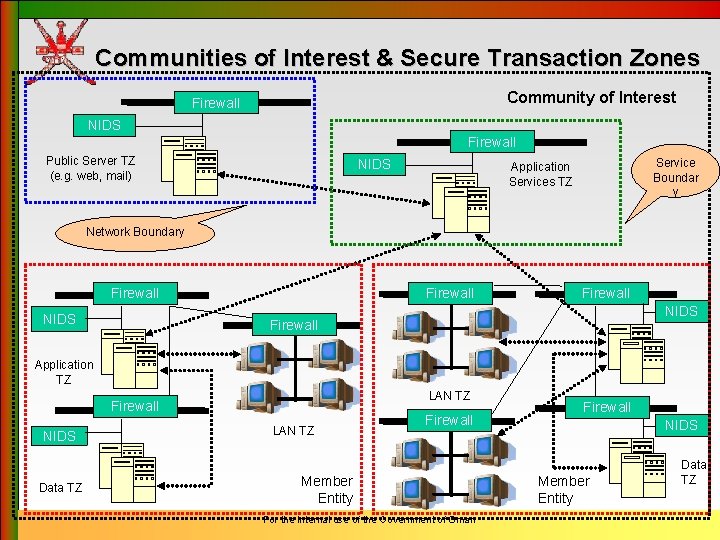
Communities of Interest & Secure Transaction Zones Community of Interest Firewall NIDS Firewall Public Server TZ (e. g. web, mail) NIDS Service Boundar y Application Services TZ Network Boundary Firewall NIDS Firewall Application TZ LAN TZ Firewall NIDS Data TZ LAN TZ Firewall Member Entity For the internal use of the Government of Oman Firewall NIDS Member Entity Data TZ

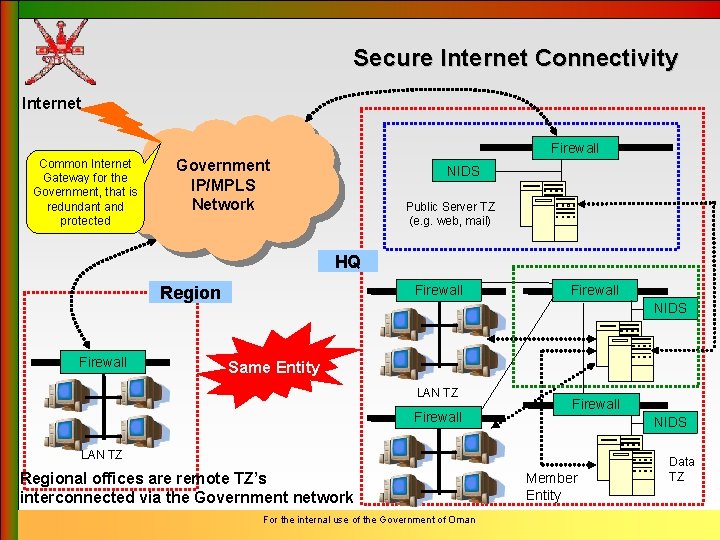
Secure Internet Connectivity Internet Firewall Common Internet Gateway for the Government, that is redundant and protected Government IP/MPLS Network NIDS Public Server TZ (e. g. web, mail) HQ Region Firewall NIDS Same Entity LAN TZ Firewall NIDS LAN TZ Regional offices are remote TZ’s interconnected via the Government network For the internal use of the Government of Oman Member Entity Data TZ

Benefits of a common internet gateway Ø Centrally controlled Secure Internet access Ø Redundant connections to the internet Ø Common security infrastructure for the government Ø Monitored and Managed 24 x 7 Ø Cost saving to the individual ministries Ø Personnel will be well trained and governed by the government security framework For the internal use of the Government of Oman

Who is responsible for Information Security? Every One For the internal use of the Government of Oman
 Moodle volta
Moodle volta Itts caracas
Itts caracas Itts gritti
Itts gritti Private secruity
Private secruity Research council oman
Research council oman Oman drydock company logo
Oman drydock company logo Oaaa oman
Oaaa oman Oman mobile number digits
Oman mobile number digits Mateja oman
Mateja oman Ras sticker oman
Ras sticker oman Al manzifat
Al manzifat Central java map
Central java map Oman driving side
Oman driving side Oman chemicals
Oman chemicals Pdo hse documents
Pdo hse documents Oman physical features
Oman physical features Summer training report on marketing
Summer training report on marketing Lakbi oman
Lakbi oman Oman cartina
Oman cartina Mgi vision
Mgi vision Najveca planina u srbiji
Najveca planina u srbiji Sme development fund oman
Sme development fund oman National centre for statistics and information oman
National centre for statistics and information oman Ministry of national economy oman
Ministry of national economy oman