Dynamic Access Control Overview Matthias Wollnik Program Manager



























- Slides: 43

Dynamic Access Control Overview Matthias Wollnik Program Manager, File Server Microsoft Corporation






demo Data Classification demo Location based classification Automatic content based classification

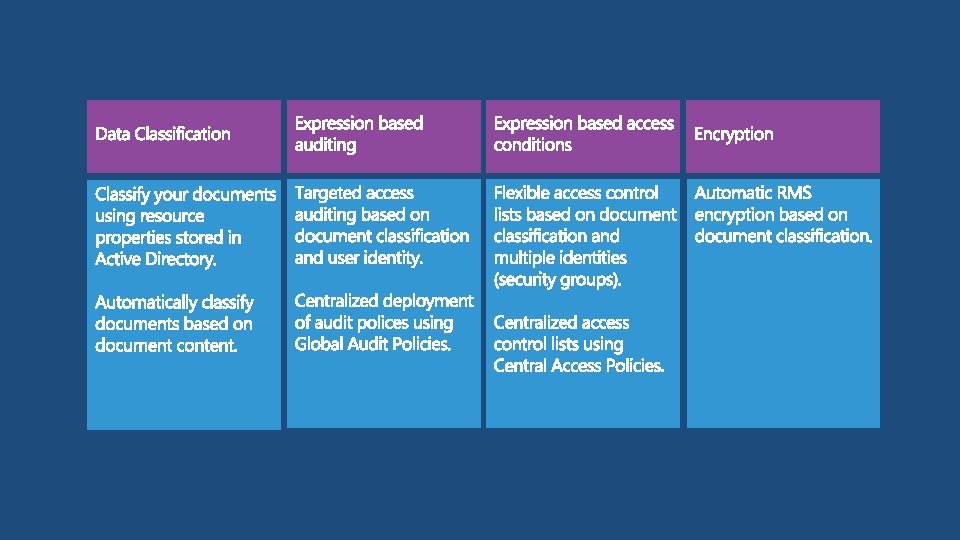
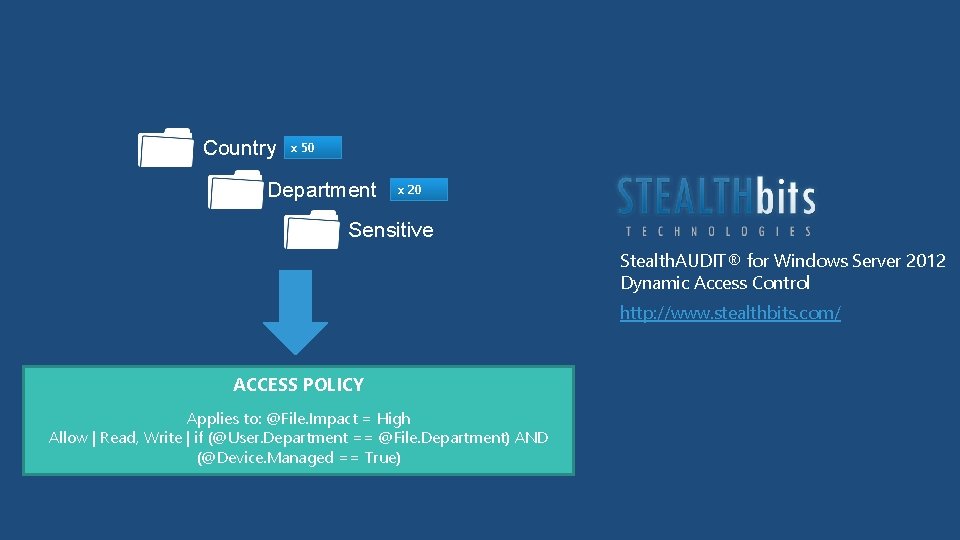
50 Groups Department 1000 Groups Sensitive 2000 Groups! Country x 50 x 20

demo Expression based ACL demo Country based central access rule

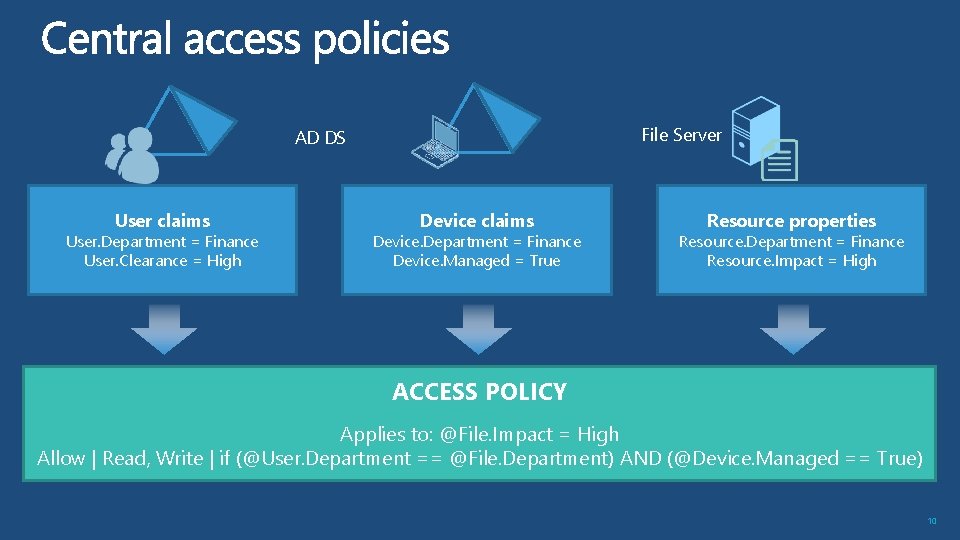
File Server AD DS User claims User. Department = Finance User. Clearance = High Device claims Device. Department = Finance Device. Managed = True Resource properties Resource. Department = Finance Resource. Impact = High ACCESS POLICY Applies to: @File. Impact = High Allow | Read, Write | if (@User. Department == @File. Department) AND (@Device. Managed == True) 10

demo Central Access Policy with user claims Country based central access rule

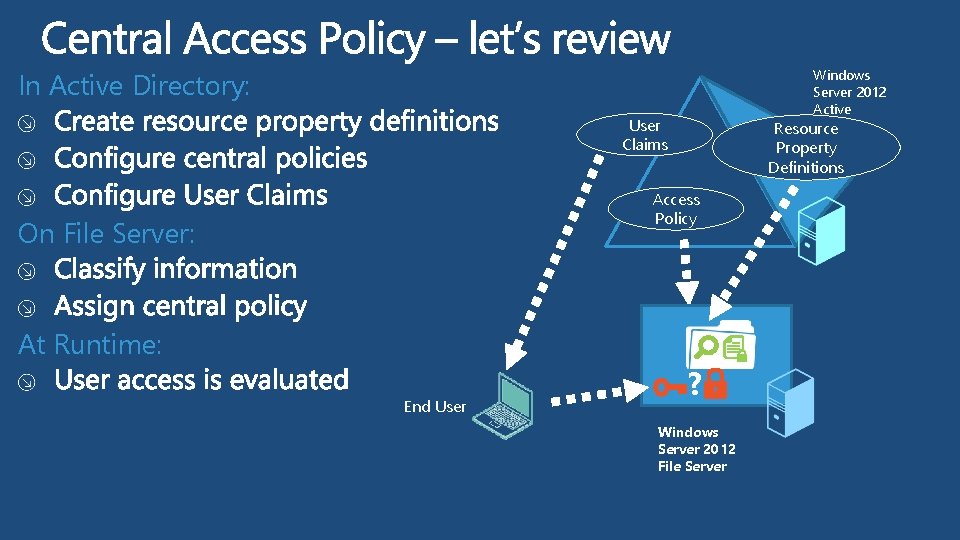
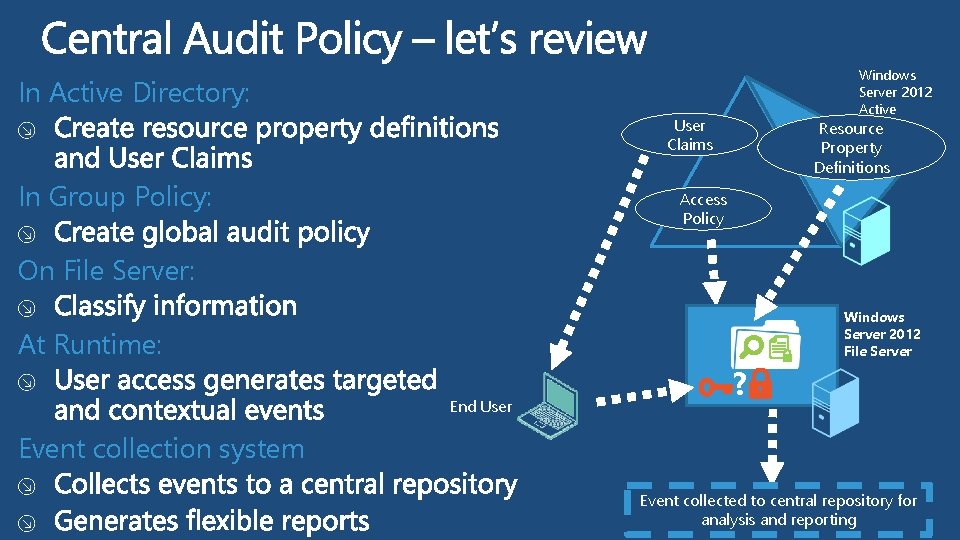
Windows Server 2012 Active Directory Resource In Active Directory: User Claims Property Definitions Access Policy On File Server: At Runtime: End User ? Windows Server 2012 File Server

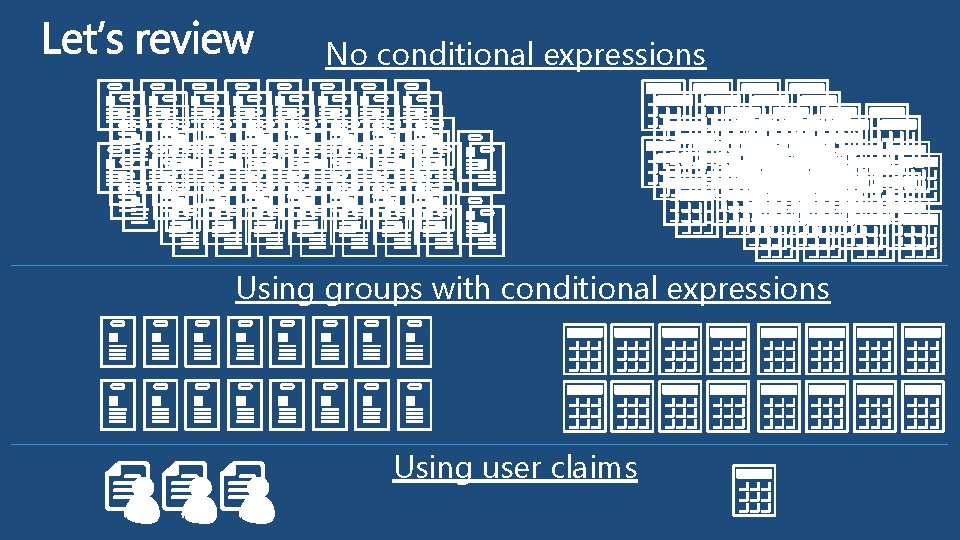
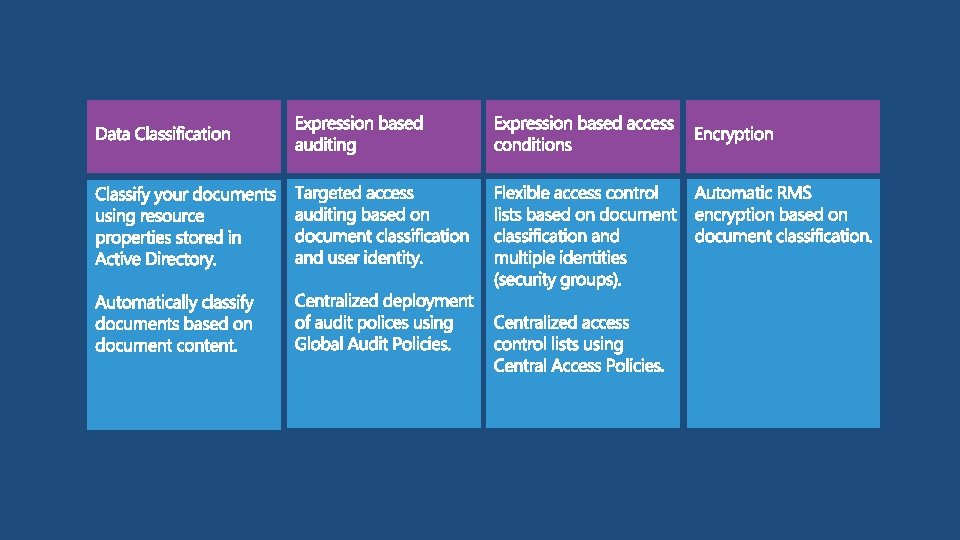
No conditional expressions Using groups with conditional expressions Using user claims




demo Automatic Rights Management Protection


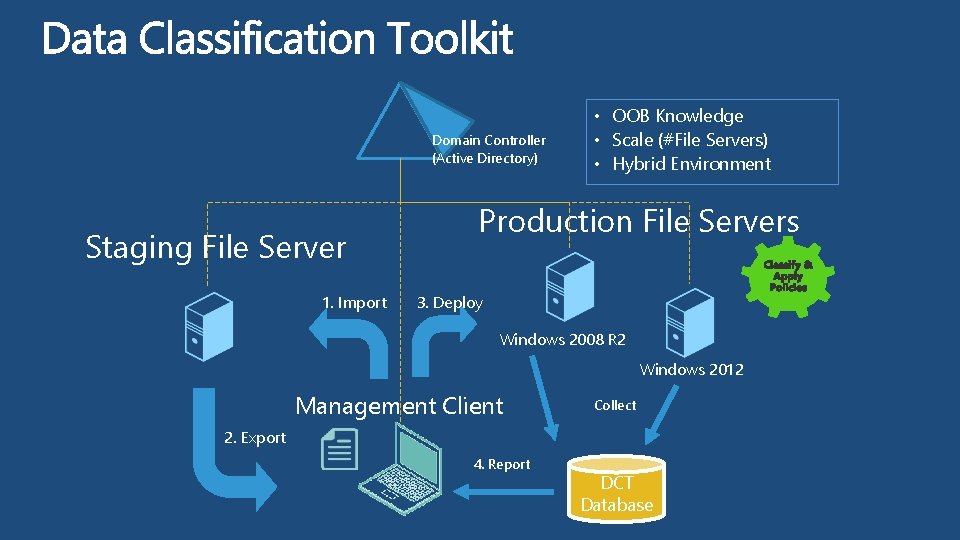
Domain Controller (Active Directory) Staging File Server 1. Import • OOB Knowledge • Scale (#File Servers) • Hybrid Environment Production File Servers 3. Deploy Windows 2008 R 2 Windows 2012 Management Client Collect 2. Export 4. Report DCT Database




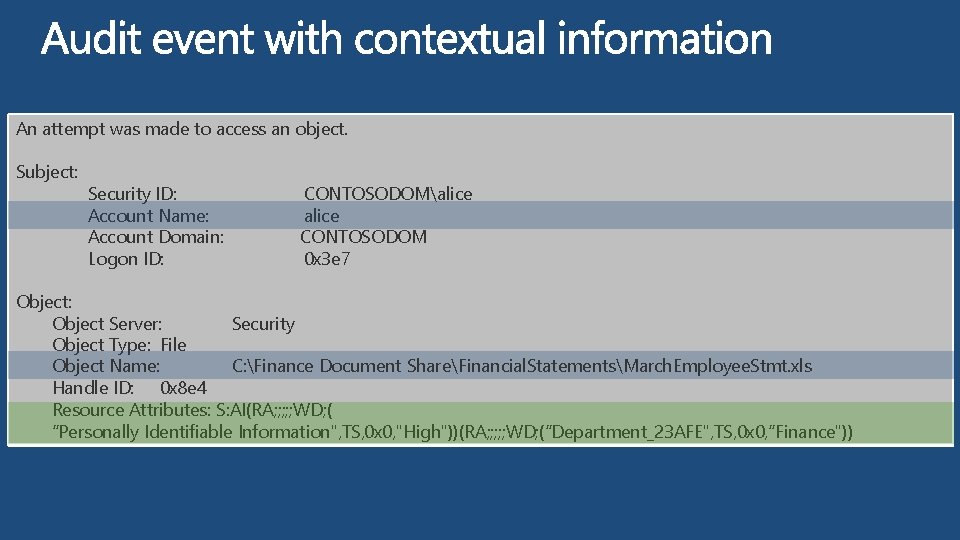
An attempt was made to access an object. Subject: Security ID: CONTOSODOMalice Account Name: alice Account Domain: CONTOSODOM Logon ID: 0 x 3 e 7 Object: Object Server: Security Object Type: File Object Name: C: Finance Document ShareFinancial. StatementsMarch. Employee. Stmt. xls Handle ID: 0 x 8 e 4 Resource Attributes: S: AI(RA; ; ; WD; ( “Personally Identifiable Information", TS, 0 x 0, "High"))(RA; ; ; WD; (“Department_23 AFE", TS, 0 x 0, “Finance"))

demo Expression Based Auditing

Windows Server 2012 Active Directory Resource In Active Directory: User Claims In Group Policy: Property Definitions Access Policy On File Server: Windows Server 2012 File Server At Runtime: End User ? Event collection system Event collected to central repository for analysis and reporting


DAC Partners


Country x 50 Department x 20 Sensitive Stealth. AUDIT® for Windows Server 2012 Dynamic Access Control http: //www. stealthbits. com/ ACCESS POLICY Applies to: @File. Impact = High Allow | Read, Write | if (@User. Department == @File. Department) AND (@Device. Managed == True)

http: //www. jijitechnologies. com/dynamic-access-control-effective-permission-report. aspx

Data Loss Prevention dg classification http: //www. dynamicaccesscontrol. com http: //www. websense. com/content/ data-security-overview. aspx CA Data. Minder http: //www. ca. com/us/data-security-solutions. aspx

Dynamic Policy Enforcer http: //www. gigatrust. com

Titus Metadata Security for Share. Point http: //www. titus. com/ Control Center for Windows Server 2012 Dynamic Access Control http: //www. nextlabs. com/html/? q=microsoft_solutions Axiomatics Policy Server http: //www. axiomatics. com/dynamic-accesssddl-xacml-windows-server-2012

RSA Net. Witness http: //www. emc. com/security/rsa-netwitness. htm

In Summary…. .

Reduce group complexity

Simplify access control

Implement effective access control

SIA 207 – Windows Server 2012 Dynamic Access Control Overview SIA 341 – Windows Server 2012 Dynamic Access Control Deep Dive for Active Directory and Central Authorization Policies SIA 316 – Windows Server 2012 Dynamic Access Control Best Practices and Case Study Deployments in Microsoft IT SIA 21 -HOL – Using Dynamic Access Conrol to Automatically and Centrally Secure Data in Windows Server 2012 SIA 02 -TLC – Windows Server 2012 Active Directory and Dynamic Access Control Find Me Later At the Windows Server booth

Learning Connect. Share. Discuss. Microsoft Certification & Training Resources http: //europe. msteched. com www. microsoft. com/learning Tech. Net Resources for IT Professionals Resources for Developers http: //microsoft. com/technet http: //microsoft. com/msdn

Evaluations Submit your evals online http: //europe. msteched. com/sessions


Required Slide *delete this box when your slide is finalized Resource 1 Resource 2 Resource 3 Resource 4 Track PMs will supply the content for this slide, which will be inserted during the final scrub.