CA Privileged Access Management Summer Lunch and Learn







- Slides: 17

CA Privileged Access Management Summer Lunch and Learn Series Steve Mc. Cullar Market Focused Advisor Terrence Hooker Principal Consultant July 22, 2016

Summer Lunch and Learn Series Friday June 24 th Friday July 8 th Friday July 15 th Friday July 22 nd 1: Privileged Access Management: Breaking the Breach Kill Chain Friday July 29 th 5: Privileged Access Management: Fine-grained Host controls 2: Privileged Access Management: Simplicity Matters 3: Privileged Access Management: Not Just a Credential Vault 4: Privileged Access Management: It’s for Applications too Friday August 5 th 6: Privileged Access Management: Securing the Cloud

Notable Security and Privacy Incidents Privileged Access A Common Thread for Hacktivism, Cybercrime, and Espionage “For digital businesses, privileged identity management becomes both incredibly important and challenging. It’s important because one administrator with malicious intent or theft of administrator credentials can have a disastrous effect on your customers, revenues and long-term reputation. ” - Forrester Research 3 “Critical Questions To Ask Your Privileged Identity Management Solution Provider", Forrester Research, September 9, 2014. § Home Depot – – § Anthem – – § 80 million records (personal data) Database access via theft of at least five employees credentials U. S. Office of Personnel Management – – § 109 million records (56 million credit/debit cards and 53 million customer email addresses Initial network access via a third-party vendor’s stolen credentials 25. 7 million records (extremely detailed personal data) Initial network access via compromised third-party credential Ashley Madison – – Over 30 million records (personal data) Source code reveals hard-coded credentials (AWS tokens, database passwords, SSH keys) © 2016 CA. ALL RIGHTS RESERVED.

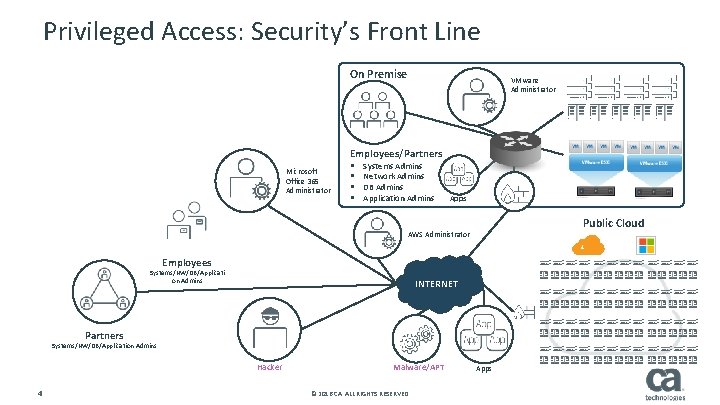
Privileged Access: Security’s Front Line On Premise VMware Administrator Employees/Partners Microsoft Office 365 Administrator § § Systems Admins Network Admins DB Admins Application Admins Apps Public Cloud AWS Administrator Employees Systems/NW/DB/Applicati on Admins INTERNET Partners Systems/NW/DB/Application Admins Hacker 4 Malware/APT © 2016 CA. ALL RIGHTS RESERVED. Apps

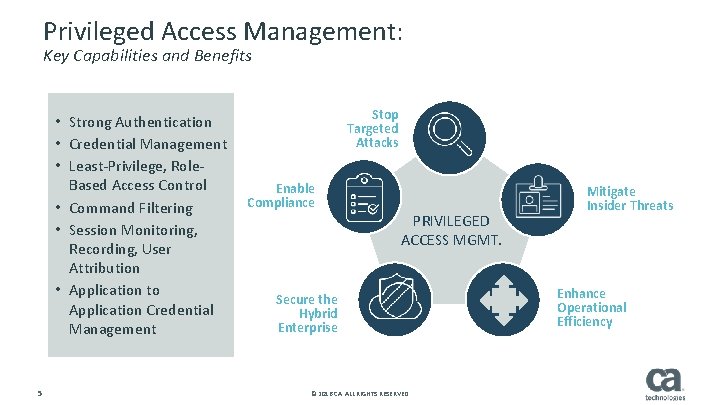
Privileged Access Management: Key Capabilities and Benefits • Strong Authentication • Credential Management • Least-Privilege, Role. Based Access Control • Command Filtering • Session Monitoring, Recording, User Attribution • Application to Application Credential Management 5 Stop Targeted Attacks Enable Compliance PRIVILEGED ACCESS MGMT. Secure the Hybrid Enterprise © 2016 CA. ALL RIGHTS RESERVED. Mitigate Insider Threats Enhance Operational Efficiency

Controlling Privileged Identities to Manage Risk 6 © 2016 CA. ALL RIGHTS RESERVED.

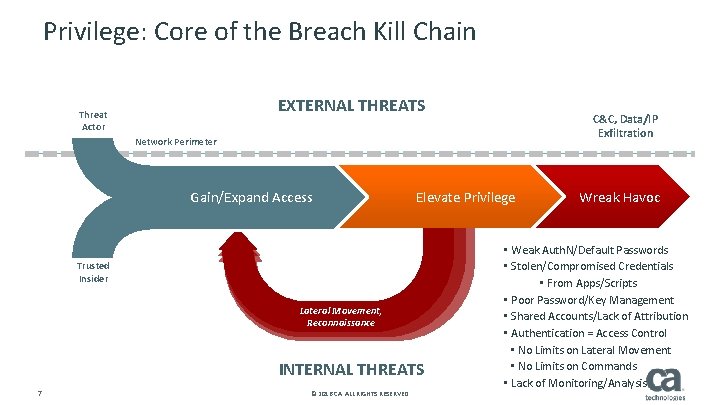
Privilege: Core of the Breach Kill Chain EXTERNAL THREATS Threat Actor C&C, Data/IP Exfiltration Network Perimeter Gain/Expand Access Elevate Privilege Trusted Insider Lateral Movement, Reconnaissance INTERNAL THREATS 7 © 2016 CA. ALL RIGHTS RESERVED. Wreak Havoc • Weak Auth. N/Default Passwords • Stolen/Compromised Credentials • From Apps/Scripts • Poor Password/Key Management • Shared Accounts/Lack of Attribution • Authentication = Access Control • No Limits on Lateral Movement • No Limits on Commands • Lack of Monitoring/Analysis

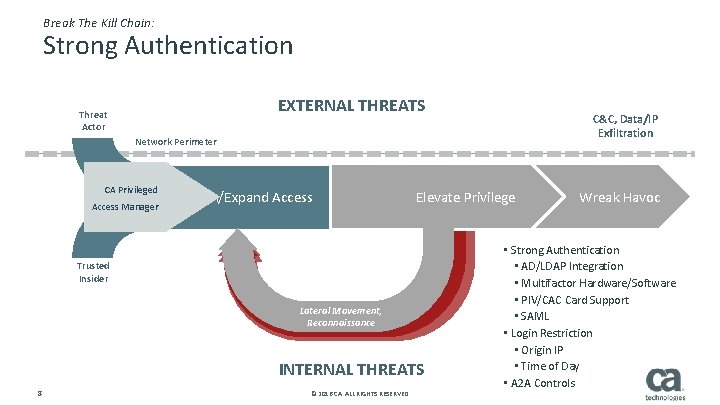
Break The Kill Chain: Strong Authentication EXTERNAL THREATS Threat Actor C&C, Data/IP Exfiltration Network Perimeter CA Privileged Access Manager Gain/Expand Access Elevate Privilege Trusted Insider Lateral Movement, Reconnaissance INTERNAL THREATS 8 © 2016 CA. ALL RIGHTS RESERVED. Wreak Havoc • Strong Authentication • AD/LDAP Integration • Multifactor Hardware/Software • PIV/CAC Card Support • SAML • Login Restriction • Origin IP • Time of Day • A 2 A Controls

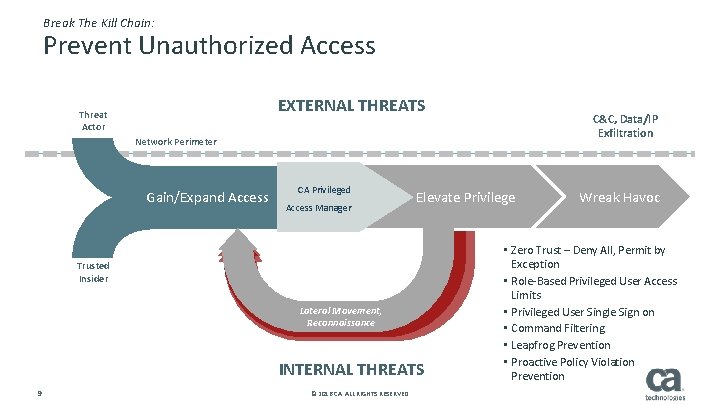
Break The Kill Chain: Prevent Unauthorized Access EXTERNAL THREATS Threat Actor C&C, Data/IP Exfiltration Network Perimeter Gain/Expand Access CA Privileged Access Manager Elevate Privilege Trusted Insider Lateral Movement, Reconnaissance INTERNAL THREATS 9 © 2016 CA. ALL RIGHTS RESERVED. Wreak Havoc • Zero Trust – Deny All, Permit by Exception • Role-Based Privileged User Access Limits • Privileged User Single Sign on • Command Filtering • Leapfrog Prevention • Proactive Policy Violation Prevention

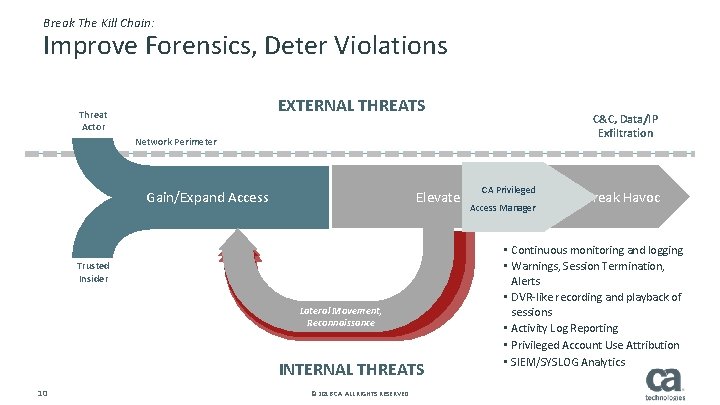
Break The Kill Chain: Improve Forensics, Deter Violations EXTERNAL THREATS Threat Actor C&C, Data/IP Exfiltration Network Perimeter CA Privileged Gain/Expand Access Elevate Privilege Access Manager Trusted Insider Lateral Movement, Reconnaissance INTERNAL THREATS 10 © 2016 CA. ALL RIGHTS RESERVED. Wreak Havoc • Continuous monitoring and logging • Warnings, Session Termination, Alerts • DVR-like recording and playback of sessions • Activity Log Reporting • Privileged Account Use Attribution • SIEM/SYSLOG Analytics

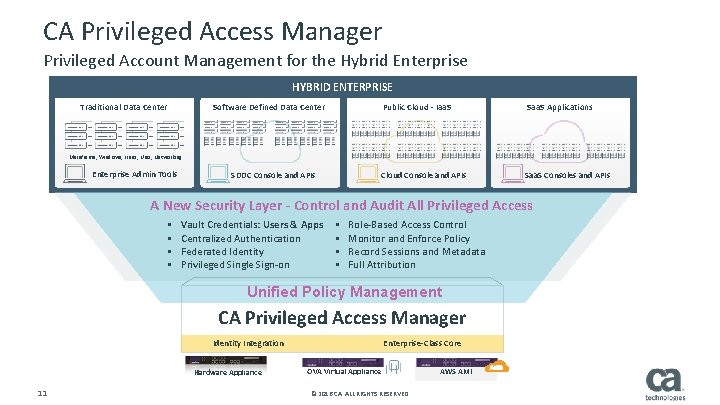
CA Privileged Access Manager Privileged Account Management for the Hybrid Enterprise HYBRID ENTERPRISE Traditional Data Center Software Defined Data Center Public Cloud - Iaa. S Saa. S Applications Cloud Console and APIs Saa. S Consoles and APIs Mainframe, Windows, Linux, Unix, Networking Enterprise Admin Tools SDDC Console and APIs A New Security Layer - Control and Audit All Privileged Access § § Vault Credentials: Users & Apps Centralized Authentication Federated Identity Privileged Single Sign-on § § Role-Based Access Control Monitor and Enforce Policy Record Sessions and Metadata Full Attribution Unified Policy Management CA Privileged Access Manager Identity Integration Hardware Appliance 11 Enterprise-Class Core OVA Virtual Appliance © 2016 CA. ALL RIGHTS RESERVED. AWS AMI

Understanding Application Credential Management § Applications require privileged credentials – Vulnerability: Credentials are stored in clear text: Scripts, config files, include files, etc. – Vulnerability: Credentials are established one time and rarely or never changed – Risk: Credentials may be compromised simply by reading the file § CA Privileged Access Manager Solution: Secure App Credentials – Remove credentials from Apps, replace with an “Alias” – Programmatically Retrieve credentials at run time – Validation checks to ensure authorization and integrity – Support for many OS, Programming Languages and Application Servers 12 © 2016 CA. ALL RIGHTS RESERVED.

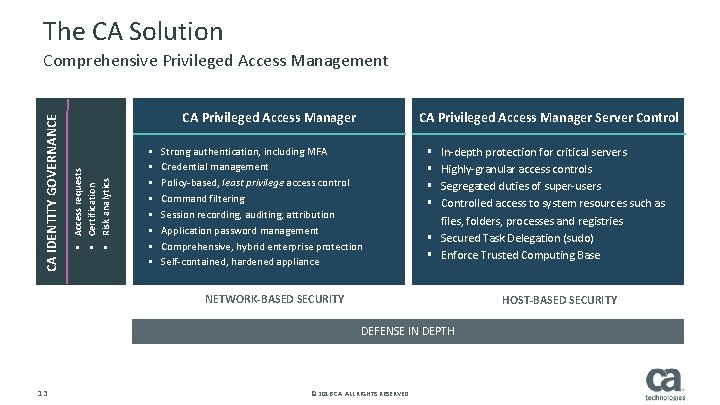
The CA Solution CA Privileged Access Manager § Access requests § Certification § Risk analytics CA IDENTITY GOVERNANCE Comprehensive Privileged Access Management § § § § CA Privileged Access Manager Server Control Strong authentication, including MFA Credential management Policy-based, least privilege access control Command filtering Session recording, auditing, attribution Application password management Comprehensive, hybrid enterprise protection Self-contained, hardened appliance In-depth protection for critical servers Highly-granular access controls Segregated duties of super-users Controlled access to system resources such as files, folders, processes and registries § Secured Task Delegation (sudo) § Enforce Trusted Computing Base § § NETWORK-BASED SECURITY § HOST-BASED SECURITY DEFENSE IN DEPTH 13 © 2016 CA. ALL RIGHTS RESERVED.

Product Demonstration Terrence Hooker, Principal Consultant

Legal Copyright © 2016 CA. All rights reserved. All trademarks, trade names, service marks and logos referenced herein belong to their respective companies. This document is for your informational purposes only. CA assumes no responsibility for the accuracy or completeness of the information. To the extent permitted by applicable law, CA provides this document “as is” without warranty of any kind, including, without limitation, any implied warranties of merchantability, fitness for a particular purpose, or noninfringement. In no event will CA be liable for any loss or damage, direct or indirect, from the use of this document, including, without limitation, lost profits, business interruption, goodwill or lost data, even if CA is expressly advised in advance of the possibility of such damages. CA does not provide legal advice. Neither this document nor any CA software product referenced herein shall serve as a substitute for your compliance with any laws (including but not limited to any act, statute, regulation, rule, directive, policy, standard, guideline, measure, requirement, administrative order, executive order, etc. (collectively, “Laws”)) referenced in this document. You should consult with competent legal counsel regarding any Laws referenced herein. 15 © 2016 CA. ALL RIGHTS RESERVED.

Privileged Access Management: Not Just a Credential Vault Q&A

Steve Mc. Cullar, CISSP Market Focused Advisor Privileged Access Management @smccullarca Steven. Mc. Cullar@ca. com