Cisco LAN Switches Cisco 2960 Catalyst Switch Series




















- Slides: 51

Cisco LAN Switches

Cisco 2960 Catalyst Switch Series

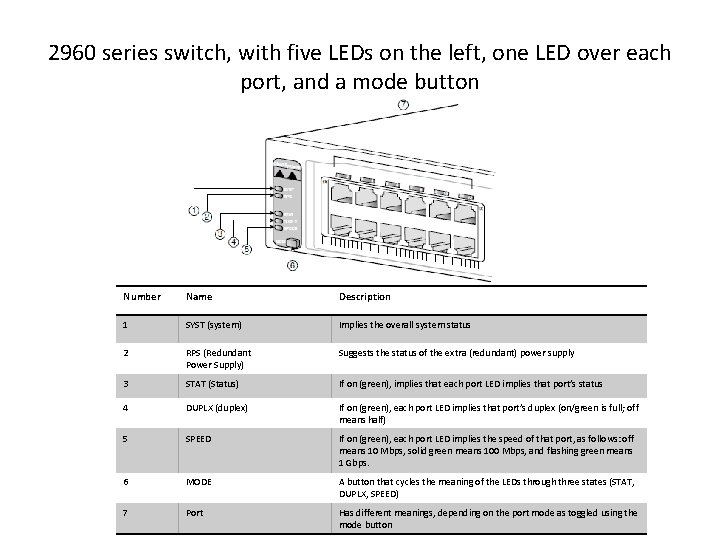
2960 series switch, with five LEDs on the left, one LED over each port, and a mode button Number Name Description 1 SYST (system) Implies the overall system status 2 RPS (Redundant Power Supply) Suggests the status of the extra (redundant) power supply 3 STAT (Status) If on (green), implies that each port LED implies that port’s status 4 DUPLX (duplex) If on (green), each port LED implies that port’s duplex (on/green is full; off means half) 5 SPEED If on (green), each port LED implies the speed of that port, as follows: off means 10 Mbps, solid green means 100 Mbps, and flashing green means 1 Gbps. 6 MODE A button that cycles the meaning of the LEDs through three states (STAT, DUPLX, SPEED) 7 Port Has different meanings, depending on the port mode as toggled using the mode button

Tera Term Pro • The default console port settings on a switch are as follows – 9600 bits/second – No hardware flow control – 8 -bit ASCII – No parity bits – 1 stop bit

Tera Term Pro

Accessing the CLI with Telnet and SSH • Telnet uses an IP network to send and receive the data, rather than a specialized cable and physical port on the device • The switch runs Telnet server software by default, but the switch does need to have an IP address configured so that it can send and receive IP packets • Secure Shell (SSH) does the same things as Telnet, but in a more secure manner by using encryption.

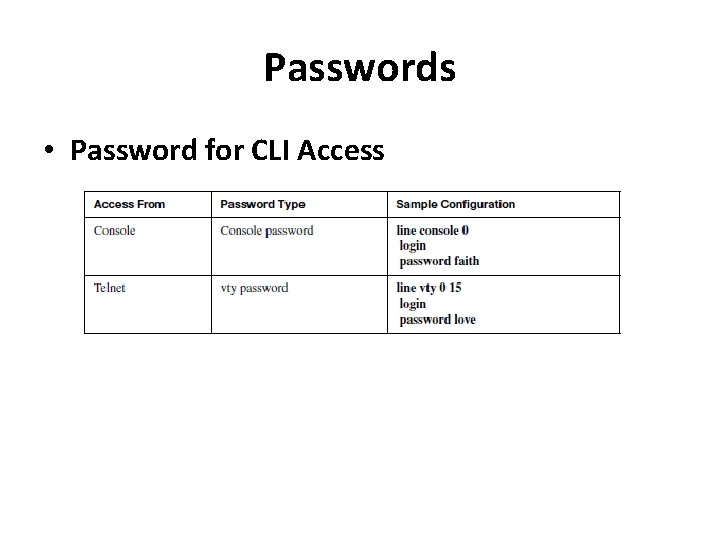
Passwords • Password for CLI Access

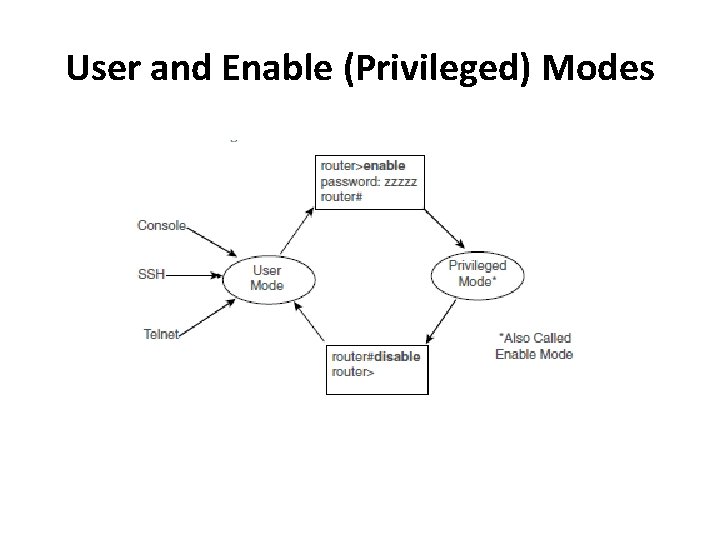
User and Enable (Privileged) Modes

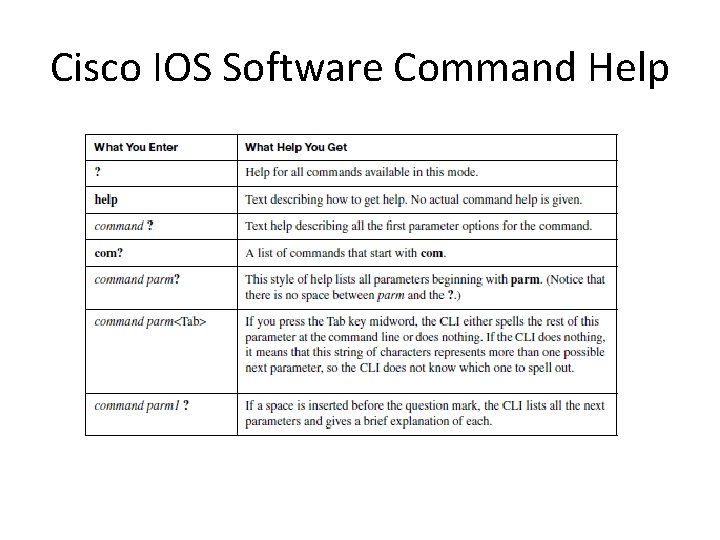
Cisco IOS Software Command Help

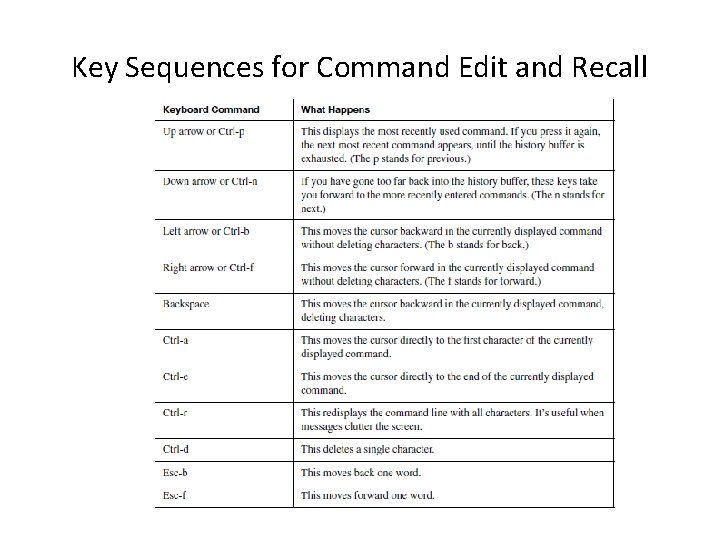
Key Sequences for Command Edit and Recall

debug and show Commands • The show command has a large variety of options, and with those options, you can find the status of almost every feature of Cisco IOS • The Debug command asks the switch to continue monitoring different processes in the switch

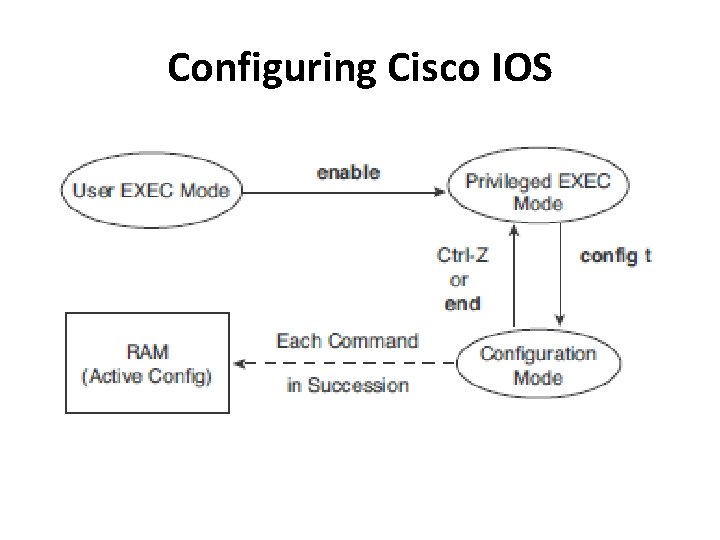
Configuring Cisco IOS

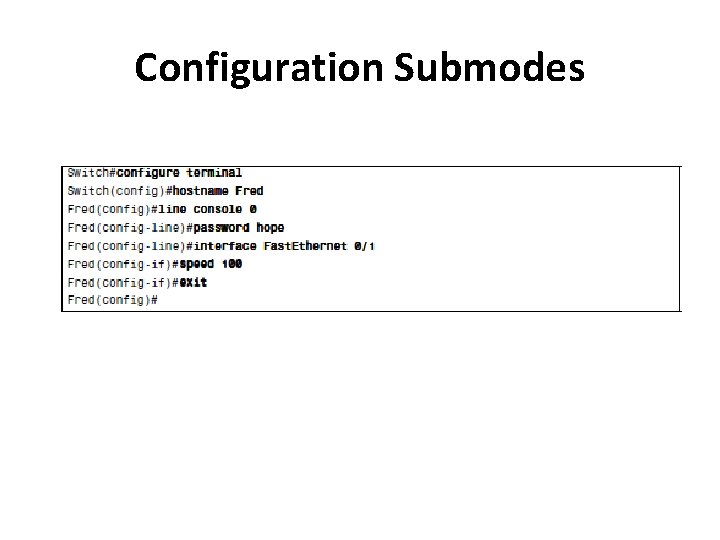
Configuration Submodes

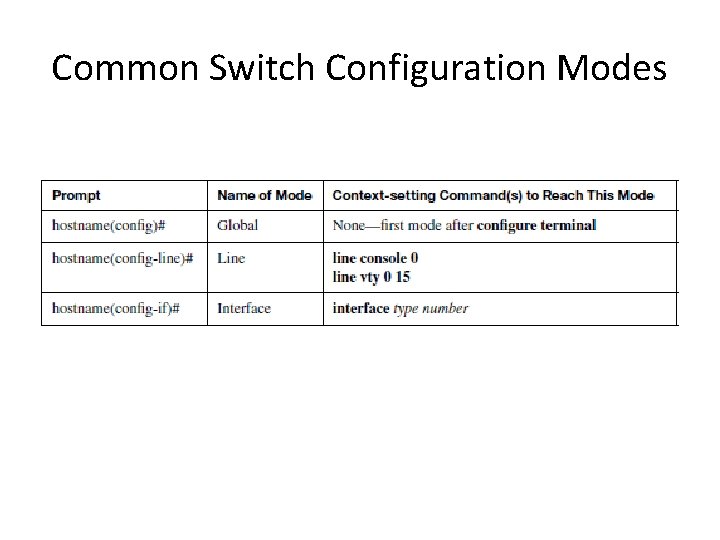
Common Switch Configuration Modes

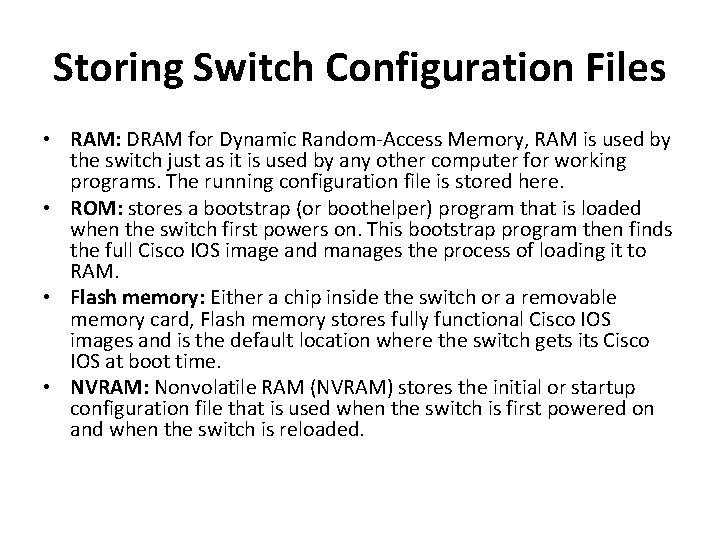
Storing Switch Configuration Files • RAM: DRAM for Dynamic Random-Access Memory, RAM is used by the switch just as it is used by any other computer for working programs. The running configuration file is stored here. • ROM: stores a bootstrap (or boothelper) program that is loaded when the switch first powers on. This bootstrap program then finds the full Cisco IOS image and manages the process of loading it to RAM. • Flash memory: Either a chip inside the switch or a removable memory card, Flash memory stores fully functional Cisco IOS images and is the default location where the switch gets its Cisco IOS at boot time. • NVRAM: Nonvolatile RAM (NVRAM) stores the initial or startup configuration file that is used when the switch is first powered on and when the switch is reloaded.

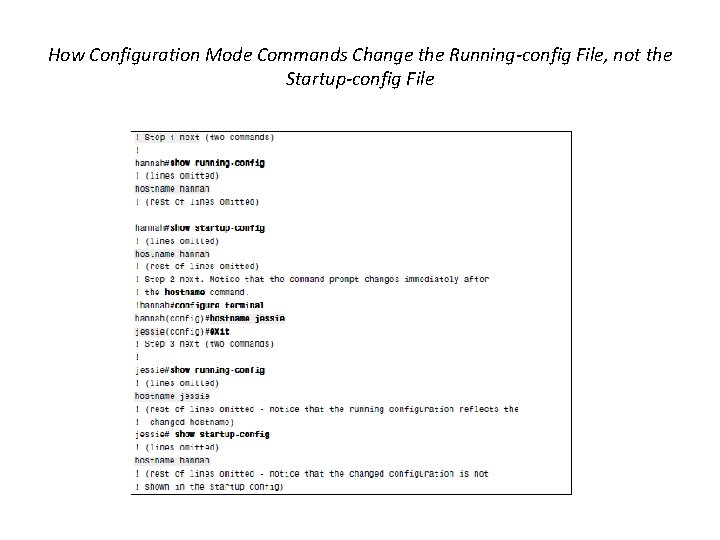
How Configuration Mode Commands Change the Running-config File, not the Startup-config File

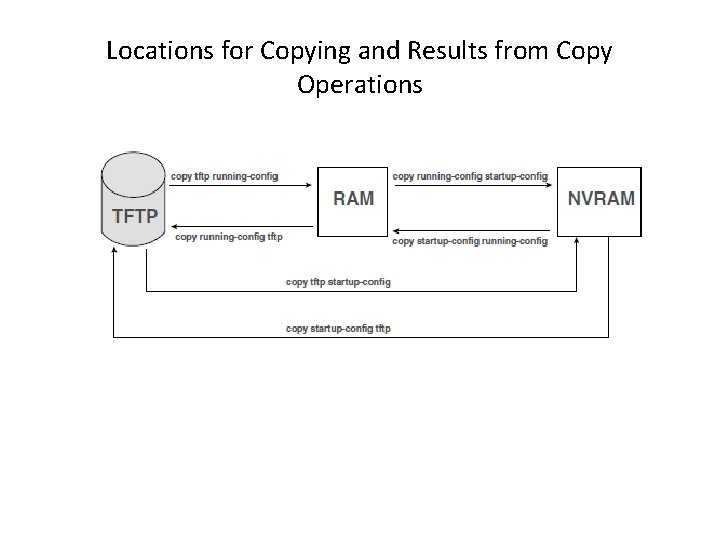
Locations for Copying and Results from Copy Operations

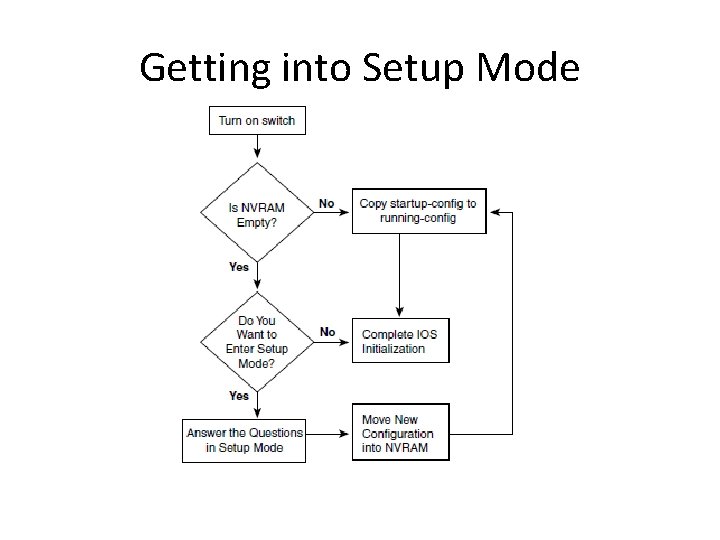
Getting into Setup Mode

Ethernet Switch Configuration

Configuring Basic Passwords and a Hostname

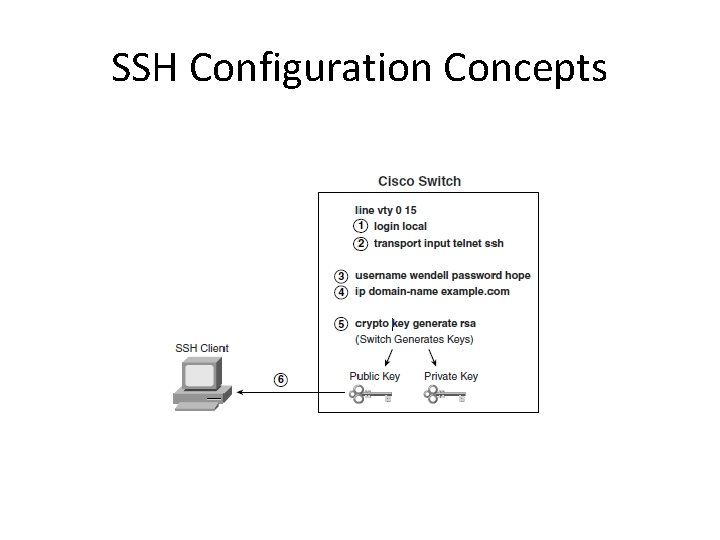
SSH Configuration Concepts Step 1 Change the vty lines to usernames, with either locally configured usernames or an AAA server. In this case, the login local subcommand defines the use of local usernames, replacing the login subcommand in vty configuration mode. Step 2 If formerly disabled, use either the transport input all or transport input telnet ssh command to tell the switch to accept both Telnet and SSH. Step 3 Add one or more username password pass-value global configuration commands to configure username/password pairs. Step 4 Configure a DNS domain name with the ip domain-name global configuration command. Step 5 Configure the switch to generate a matched public and private key pair, as well as a share encryption key, using the crypto key generate rsa global configuration command. Step 6 Although no switch commands are required, each SSH client needs a copy of the switch’s public key before the client can connect.

SSH Configuration Concepts

SSH Configuration

SSH Configuration

Password Encryption The presence or absence of the service password-encryption global configuration command dictates whether the passwords are encrypted as follows • When the service password-encryption command is configured, all existing console, vty, and username command passwords are immediately encrypted. • If the service password-encryption command has already been configured, any future changes to these passwords are encrypted. • If the no service password-encryption command is used later, the passwords remain encrypted, until they are changed—at which point they show up in clear text.

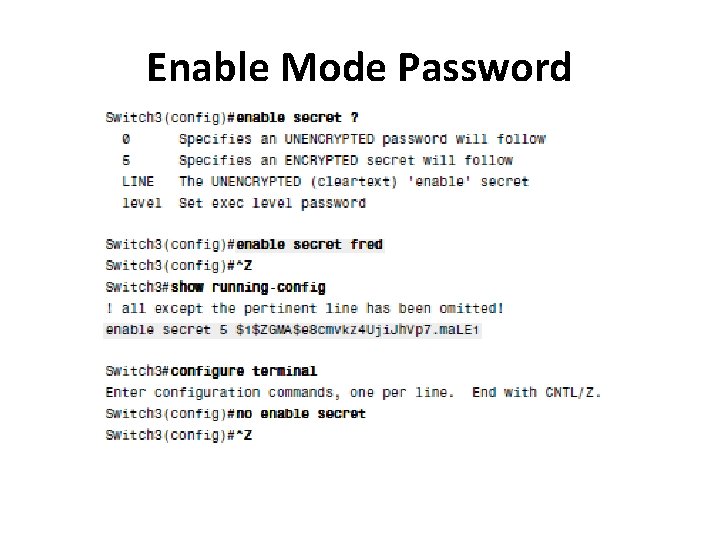
The Two Enable Mode Passwords A router or switch can be configured to require a password to reach enable mode according to the following rules: • If the global configuration command enable password actual-password is used, it defines the password required when using the enable EXEC command. This password is listed as clear text in the configuration file by default. • If the global configuration command enable secret actualpassword is used, it defines the password required when using the enable EXEC command. This password is listed as a hidden MD 5 hash value in the configuration file. • If both commands are used, the password set in the enable secret command defines which password is required.

Enable Mode Password

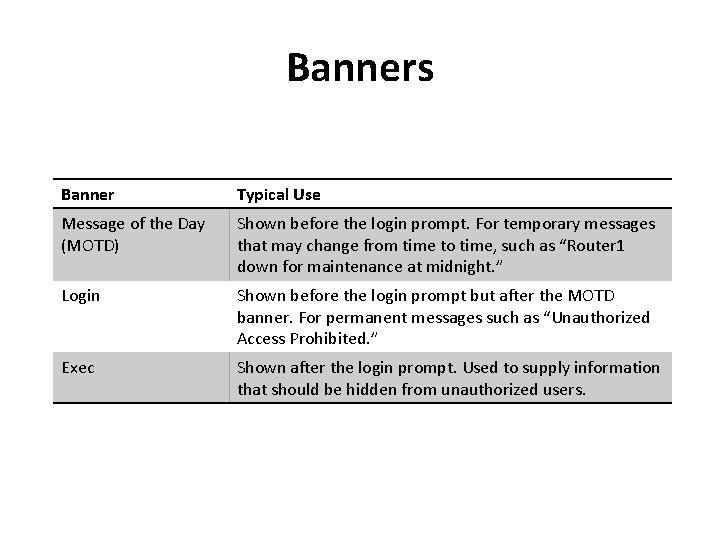
Banners Banner Typical Use Message of the Day (MOTD) Shown before the login prompt. For temporary messages that may change from time to time, such as “Router 1 down for maintenance at midnight. ” Login Shown before the login prompt but after the MOTD banner. For permanent messages such as “Unauthorized Access Prohibited. ” Exec Shown after the login prompt. Used to supply information that should be hidden from unauthorized users.

Banner Configuration

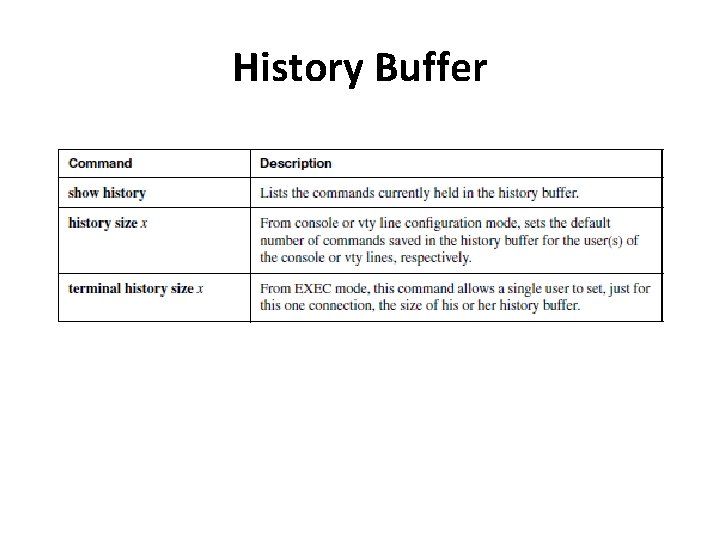
History Buffer

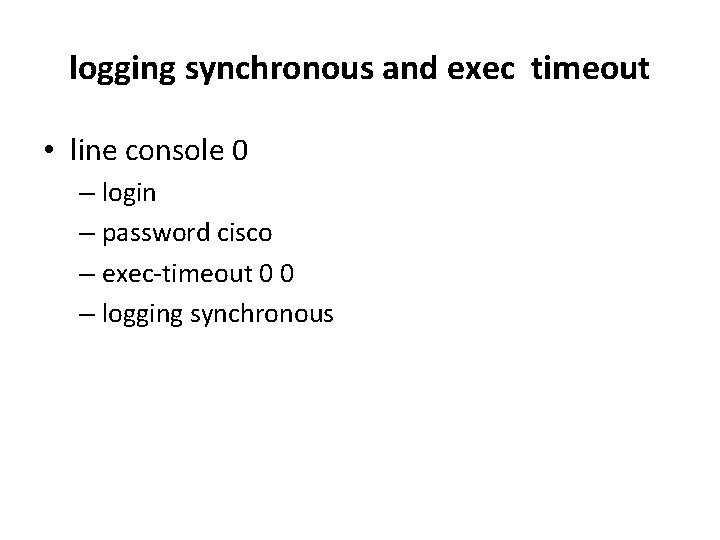
logging synchronous and exec timeout • line console 0 – login – password cisco – exec-timeout 0 0 – logging synchronous

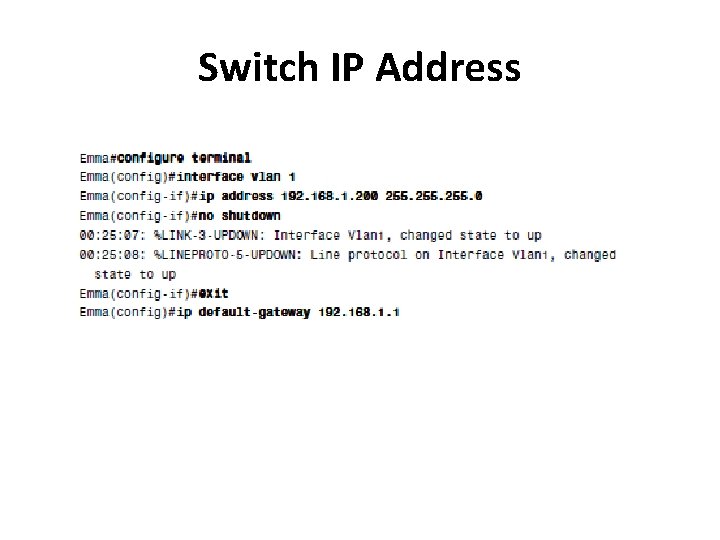
Switch IP Address Step 1 Enter VLAN 1 configuration mode using the interface vlan 1 global configuration command (from any config mode). Step 2 Assign an IP address and mask using the ip address ipaddress mask interface subcommand. Step 3 Enable the VLAN 1 interface using the no shutdown interface subcommand. Step 4 Add the ip default-gateway ip-address global command to configure the default gateway.

Switch IP Address

Switch IP Address DHCP

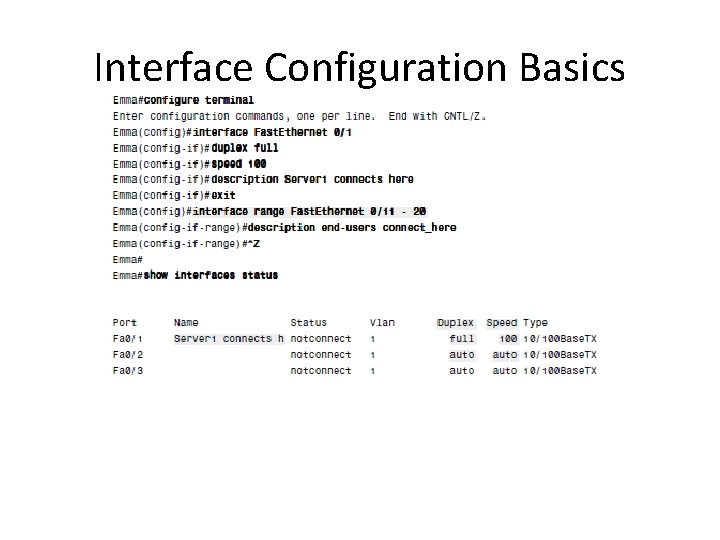
Interface Configuration Basics

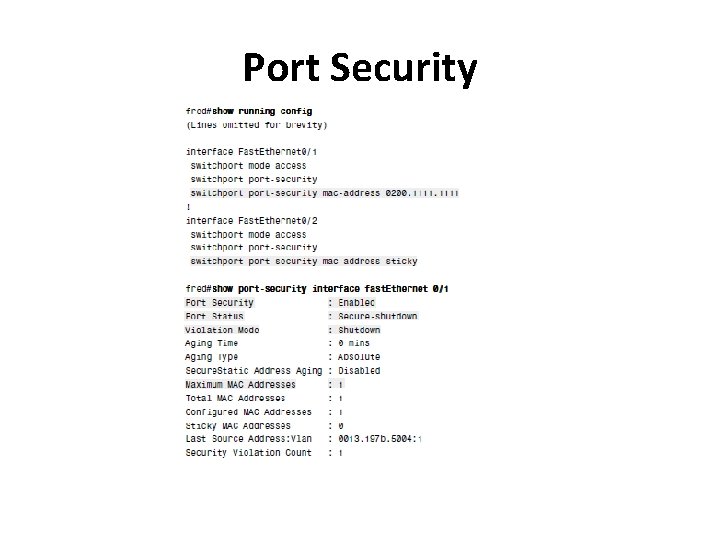
Port Security Step 1 Make the switch interface an access interface using the switchport mode access interface subcommand. Step 2 Enable port security using the switchport-security interface subcommand. Step 3 (Optional) Specify the maximum number of allowed MAC addresses associated with the interface using the switchport-security maximum number interface subcommand. (Defaults to one MAC address. ) Step 4 (Optional) Define the action to take when a frame is received from a MAC address other than the defined addresses using the switchport-security violation {protect | restrict | shutdown} interface ubcommand. (The default action is to shut down the port. ) Step 5 A Specify the MAC address(es) allowed to send frames into this interface using the switchport-security mac address mac-address command. Use the command multiple times to define more than one MAC address. Step 5 B Alternatively, instead of Step 5 A, use the “sticky learning” process to dynamically learn and configure the MAC addresses of currently connected hosts by configuring the switchport-security macaddress sticky interface subcommand.

Port Security

VLAN´s

VLAN´s Step 1 To configure a new VLAN: – a. From configuration mode, use the vlan-id global configuration command to create the VLAN and move the user into VLAN configuration mode. – b. (Optional) Use the name VLAN subcommand to list a name for the VLAN. If not configured, the VLAN name is VLANZZZZ, where ZZZZ is the four-digit decimal VLAN ID. Step 2 To configure a VLAN for each access interface: – a. Use the interface command to move into interface configuration mode for each desired interface. – b. Use the switchport access vlan id-number interface subcommand to specify the VLAN number associated with that interface. – c. (Optional) To disable trunking so that the switch will not dynamically decide to use trunking on the interface, and it will remain an access interface, use the switchport mode access interface subcommand.

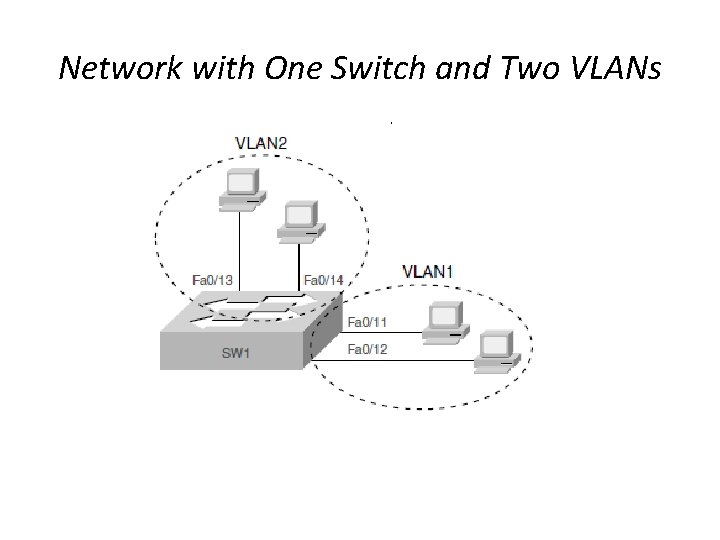
Network with One Switch and Two VLANs

Configuring VLANs and Assigning Them to Interfaces

Securing Unused Switch Interfaces • Administratively disable the interface using the shutdown interface subcommand. • Prevent VLAN trunking and VTP by making the port a nontrunking interface using the • switchport mode access interface subcommand. • Assign the port to an unused VLAN using the switchport access vlan number interface subcommand.

Ethernet Switch Troubleshooting

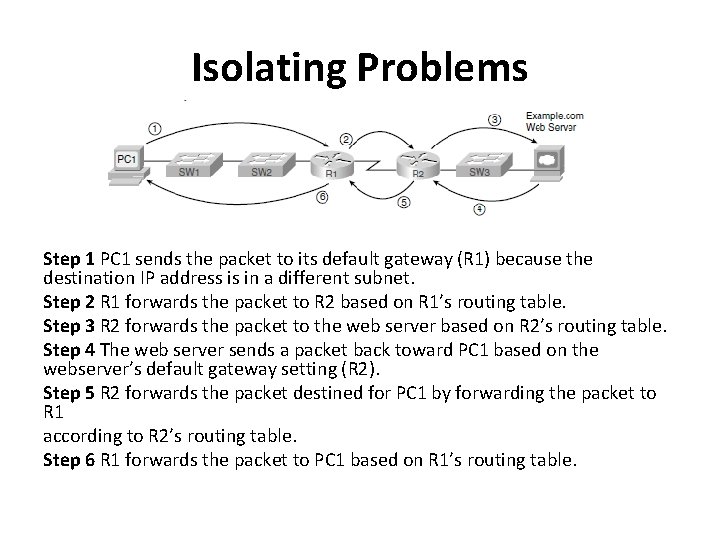
Isolating Problems Step 1 PC 1 sends the packet to its default gateway (R 1) because the destination IP address is in a different subnet. Step 2 R 1 forwards the packet to R 2 based on R 1’s routing table. Step 3 R 2 forwards the packet to the web server based on R 2’s routing table. Step 4 The web server sends a packet back toward PC 1 based on the webserver’s default gateway setting (R 2). Step 5 R 2 forwards the packet destined for PC 1 by forwarding the packet to R 1 according to R 2’s routing table. Step 6 R 1 forwards the packet to PC 1 based on R 1’s routing table.

Cisco Discovery Protocol CDP discovers several useful details from the neighboring Cisco devices: – Device identifier: Typically the hostname – Address list: Network and data-link addresses – Local interface: The interface on the router or switch issuing the show cdp command with which the neighbor was discovered – Port identifier: Text that identifies the port used by the neighboring device to send CDP messages to the local device – Capabilities list: Information on what type of device it is (for instance, a router or a switch) – Platform: The model and OS level running in the device

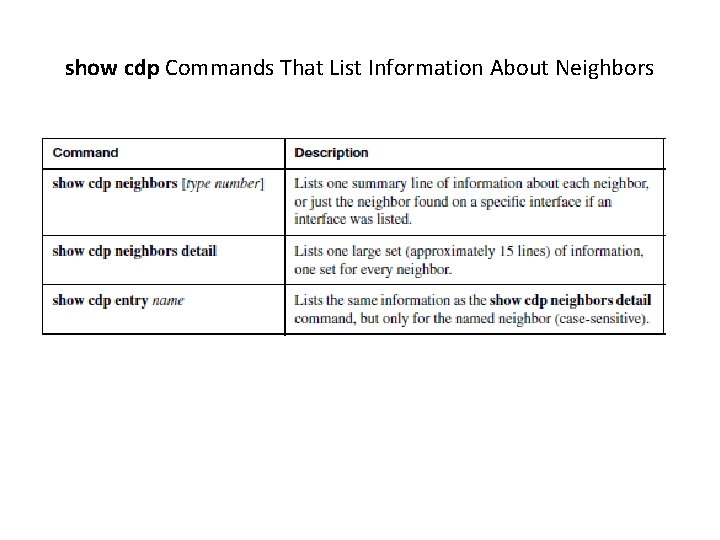
show cdp Commands That List Information About Neighbors

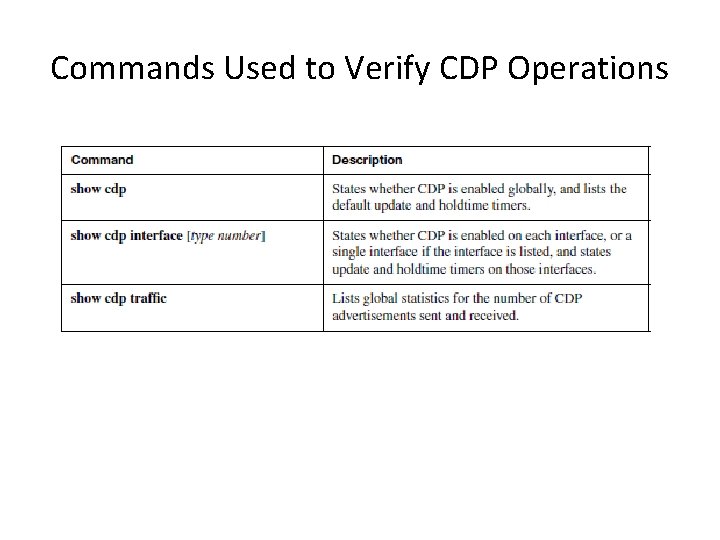
Commands Used to Verify CDP Operations

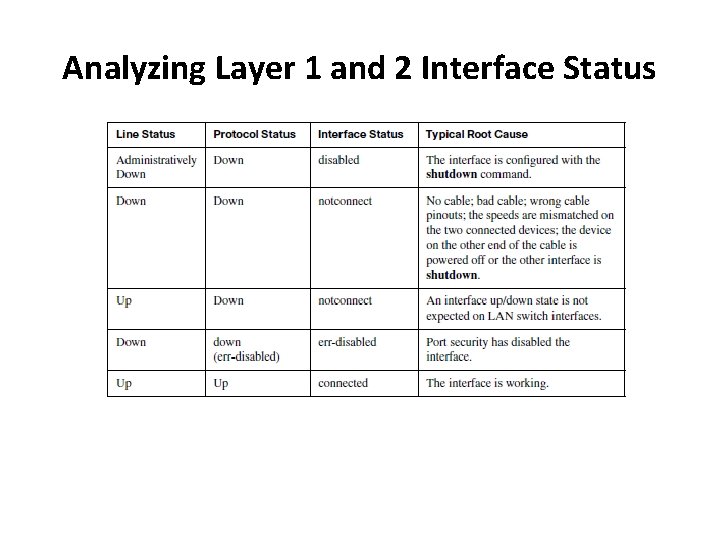
Analyzing Layer 1 and 2 Interface Status

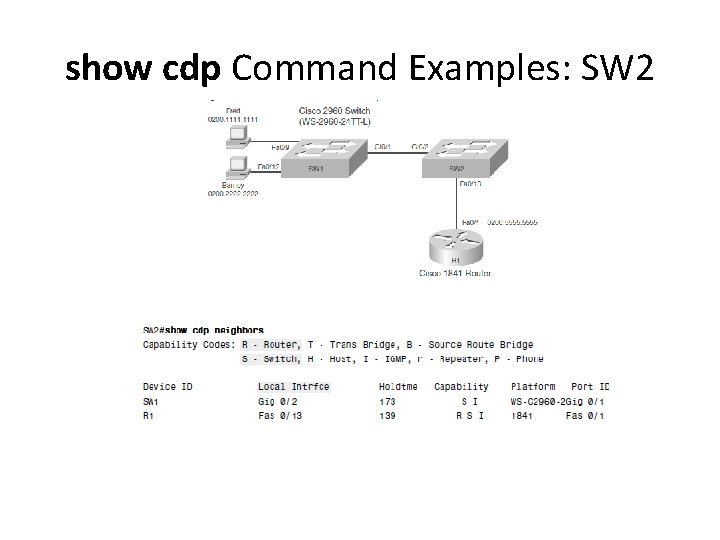
show cdp Command Examples: SW 2

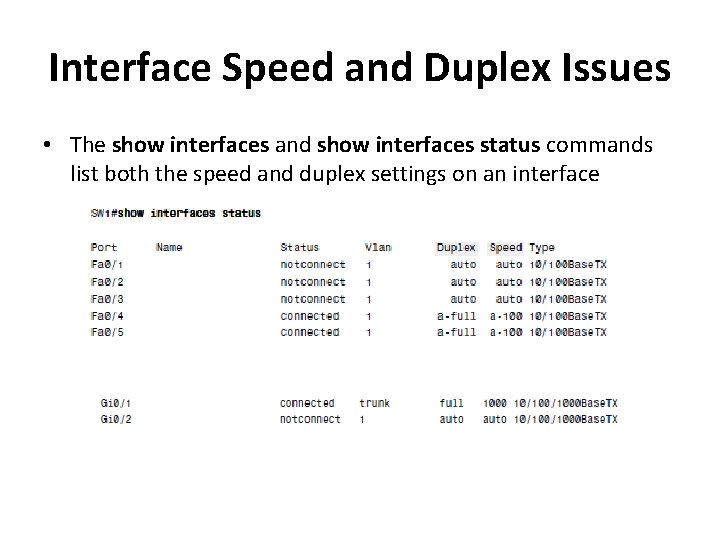
Interface Speed and Duplex Issues • The show interfaces and show interfaces status commands list both the speed and duplex settings on an interface

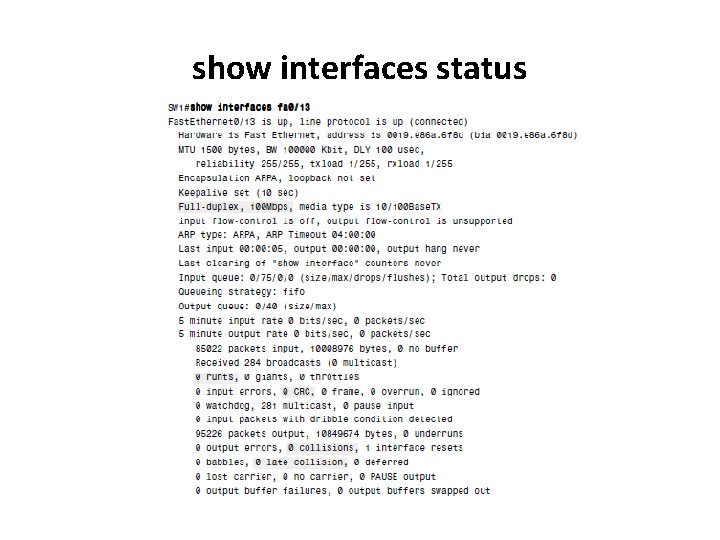
show interfaces status