Topics in Cryptography Lecture 4 Topic Chosen Ciphertext



















- Slides: 41

Topics in Cryptography Lecture 4 Topic: Chosen Ciphertext Security Lecturer: Moni Naor

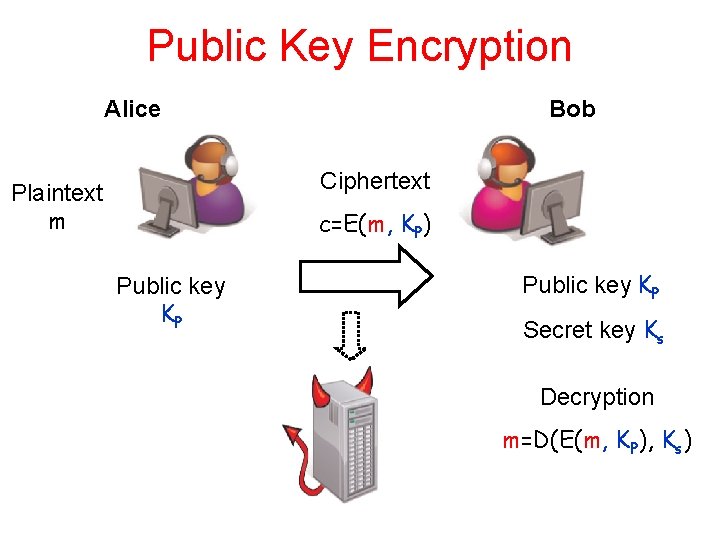
Public Key Encryption Alice Bob Ciphertext Plaintext m c=E(m, KP) Public key KP Secret key Ks Decryption m=D(E(m, KP), Ks)

Defining Security How do we know that an encryption scheme is secure? Are the following requirements sufficient? 1. Given E(m, KP), cannot compute m 2. Given E(m, KP), cannot compute ith bit of m 3. Given E(m, KP), cannot compute some f(m) Definition must be 1. “convincing” 2. “application independent”

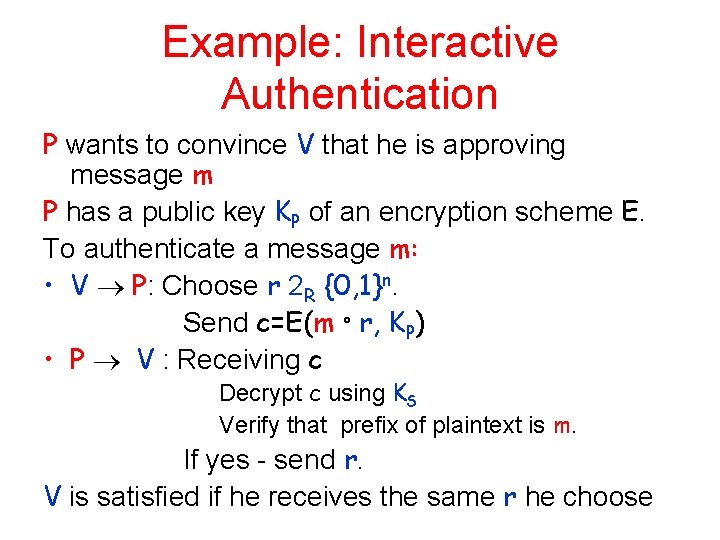
Example: Interactive Authentication P wants to convince V that he is approving message m P has a public key KP of an encryption scheme E. To authenticate a message m: • V P: Choose r 2 R {0, 1}n. Send c=E(m ° r, KP) • P V : Receiving c Decrypt c using KS Verify that prefix of plaintext is m. If yes - send r. V is satisfied if he receives the same r he choose

Is it Safe? Definition of security • Existential unforgeability against adaptive chosen message attack – Adversary can ask to authenticate any sequence m 1, m 2, … – Success: makes V accept a message m not authenticated – Complete control over the channels • V P: Choose r 2 R {0, 1}n. Send c=E(m ° r, KP) • P V : Receiving c Decrypt c using KS Verify prefix is m. If yes - send r Problems • Intuition: if E does not leak information about plaintext If E is “just” semantically secure against chosen plaintext attacks: is leaked about r – Nothing –Adversary might change c=E(m ° r, KP) into c’=E(m’ ° r, K P) • Malleability –not sufficient to verify correct form of ciphertext in simulation

Question • V P: Choose r 2 R {0, 1}n. Can you think of a an Send c=E(m ° r, KP) example of an encryption • P V : Receiving c scheme where Decrypt c using KS • Encrpytion scheme is Verify prefix is m. semantically secure If yes - send r against chosen plaintext attacks • Authentication scheme is forgeable Example: bit by bit encryption

Attacks and Security To define security of a system must specify: • The power of the adversary – both: – Computational – access to the system. • What constitute a failure of the system – Often via a game and probability of winning

Taxonomy of Signature-Schemes Goldwasser, Micali and Rivest (1984) Attacks • Key-only attacks • Generic chosen message attack: – key unknown when messages chosen • Non-Adaptive chosen message attack: – key known when messages chosen. What it means to break the scheme • Universal forgery ¼ keyrecovery • Selective forgery: target message chosen a priori. • Existential forgery - some message is forged. • Adaptive chosen message attack All combination of attacks/breaking are relevant

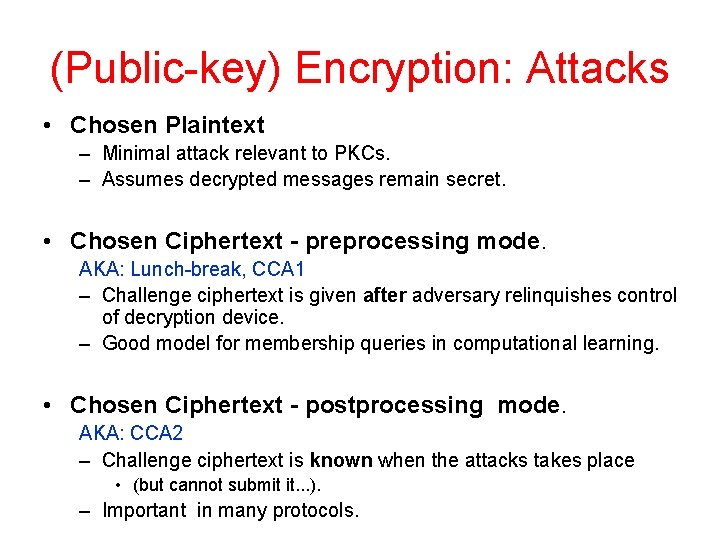
(Public-key) Encryption: Attacks • Chosen Plaintext – Minimal attack relevant to PKCs. – Assumes decrypted messages remain secret. • Chosen Ciphertext - preprocessing mode. AKA: Lunch-break, CCA 1 – There is a period where the device is handled by adversary – Should remain secure for ciphertext created afterwards • Chosen Ciphertext - postprocessing mode. AKA: CCA 2 – Challenge ciphertext is known when the attacks takes place

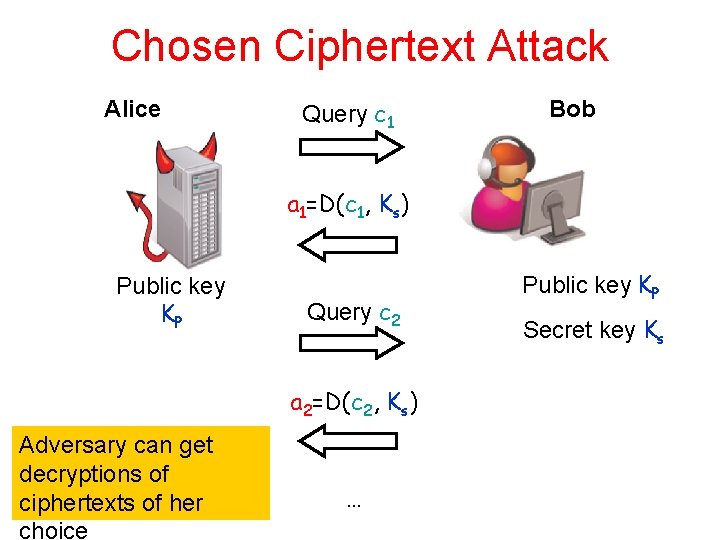
Chosen Ciphertext Attack Alice Query c 1 Bob a 1=D(c 1, Ks) Public key KP Query c 2 a 2=D(c 2, Ks) Adversary can get decryptions of ciphertexts of her choice … Public key KP Secret key Ks

Encryption - Notions of Breaking • Semantic Security – Whatever is computable about the plaintext given the ciphertext is computable without it. – Given E(m, kp) it is infeasible to produce related m’ – Can substitute with indistinguishability of encryption • Cannot distinguish E(m 0, kp) from E(m 1, kp) • Requires a proof in each setting • Non-malleable security m and m’ satify R(m, m’) R is poly time – Whatever is computable in an encrypted form about the plaintext given the ciphertext is computable without it. – Given E(m, kp) it is infeasible to produce E(m’, kp) for a “related” m’ – Important for achieving independence of messages.

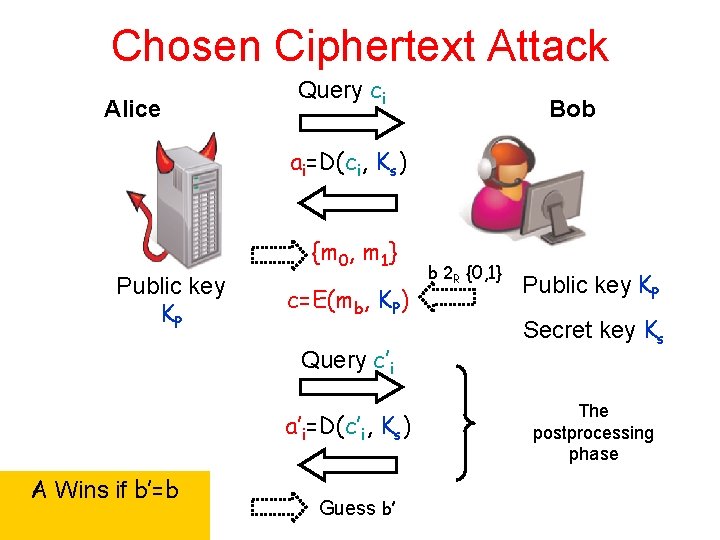
Indistinguishability under CCA Definition: An encryption scheme is secure under CCA if: no poly-time Adversary A can “win” with nonnegligible advantage: 1. 2. 3. 4. A is given the public key KP. A (adaptively) asks for decryptions under Ks. A produces two messages m 0 and m 1 A receives a “challenge” c = Epk(mb) for b ∈R {0, 1} 5. A “wins” if it guesses b correctly. CCA 1 – A only gets decryptions before challenge CCA 2 – A also gets decryptions after challenge

Chosen Ciphertext Attack Alice Query ci Bob ai=D(ci, Ks) {m 0, m 1} Public key KP c=E(mb, KP) Query c’i a’i=D(c’i, Ks) A Wins if b’=b Guess b’ b 2 R {0, 1} Public key KP Secret key Ks The postprocessing phase

(Public-key) Encryption: Attacks • Chosen Plaintext – Minimal attack relevant to PKCs. – Assumes decrypted messages remain secret. • Chosen Ciphertext - preprocessing mode. AKA: Lunch-break, CCA 1 – Challenge ciphertext is given after adversary relinquishes control of decryption device. – Good model for membership queries in computational learning. • Chosen Ciphertext - postprocessing mode. AKA: CCA 2 – Challenge ciphertext is known when the attacks takes place • (but cannot submit it. . . ). – Important in many protocols.

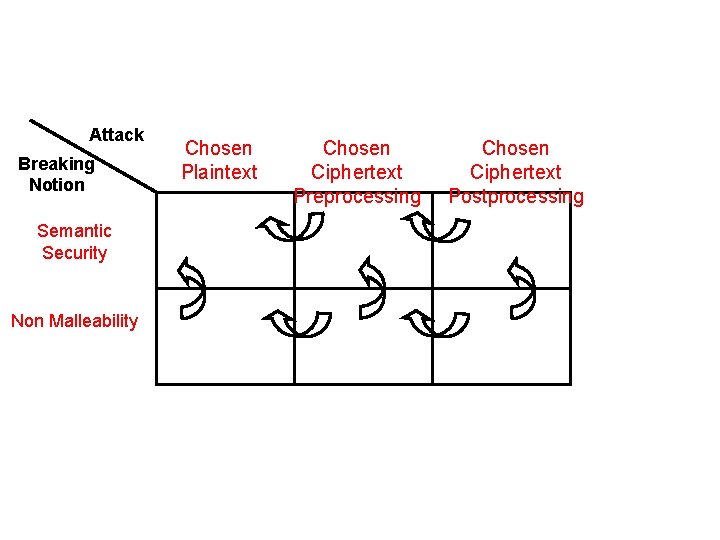
Attack Breaking Notion Semantic Security Non Malleability Chosen Plaintext Chosen Ciphertext Preprocessing Chosen Ciphertext Postprocessing

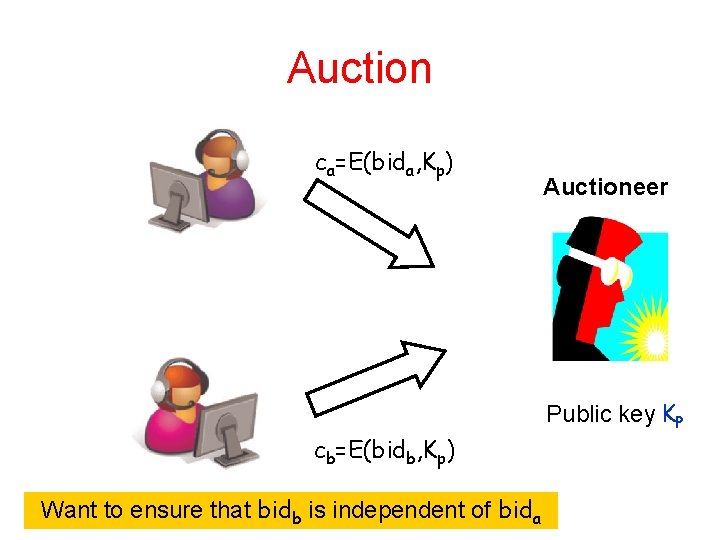
Auction ca=E(bida, Kp) cb=E(bidb, Kp) Want to ensure that bidb is independent of bida Auctioneer Public key KP

Example: Auctions Different requirements - different notions. Semantic security is not sufficient for guaranteeing the independence of bids. • If key is used for a single auction and secrecy is not required after the auction is over – Non-malleable security against chosen plaintext attacks. • If key is used for many auctions and secrecy is not required after the auction is over: Non-malleable security against chosen ciphertext attack in the preprocessing mode. • If key is used for many auctions and secrecy is required after the auction is over Non-malleable security against chosen ciphertext attack in the postprocessing mode.

Attack Breaking Notion Chosen Plaintext Chosen Ciphertext Preprocessing Chosen Ciphertext Postprocessing Semantic Security Non Malleability All other implications: proper Open problem: construct a more secure version from the less secure one. Is it possible to constrcut a CCA 2 from

Approaches for CCA-Security Redundancy + verification of well-formedness • The “Naor-Yung paradigm” [NY’ 90, DDN’ 91, Sahai, Lindell] – CPA-secure scheme + NIZK • Smooth projective hashing [Cramer Shoup ’ 98, CS ’ 02, . . . ] – “Designated verifier” proofs – Simplified: [Kiltz, Pietrzak, Stam, Yung, 2009] • Lossy trapdoor functions [Peikert Waters ’ 08] • Correlated Products [Rosen Segev’ 09] Identity-based encryption [BCHK ’ 04, . . . ] • IBE (CPA) IBE(CCA)

Ideas for achieving resistance to CCA • Add redundancy - hard to generate frivolous ciphertexts • Add methods to check consistency – This is the trickiest part: • Non interactive zero-knowledge • Specific schemes • Decrypt only if given ciphertext passes the consistency checks Could be Important point: may decrypt with several NIZK different private keys based C 1 C 2 Proof of consistency

Min-Entropy Probability distribution X over {0, 1}n H 1(X) = - log maxx Pr[X = x] Represents the probability of the most likely value of X X is a k-source if H 1(X) ¸ k (i. e. , Pr[X = x] · 2 -k for all x) Statistical distance: ¢(X, Y) = a |Pr[X=a] – Pr[Y=a]| 21

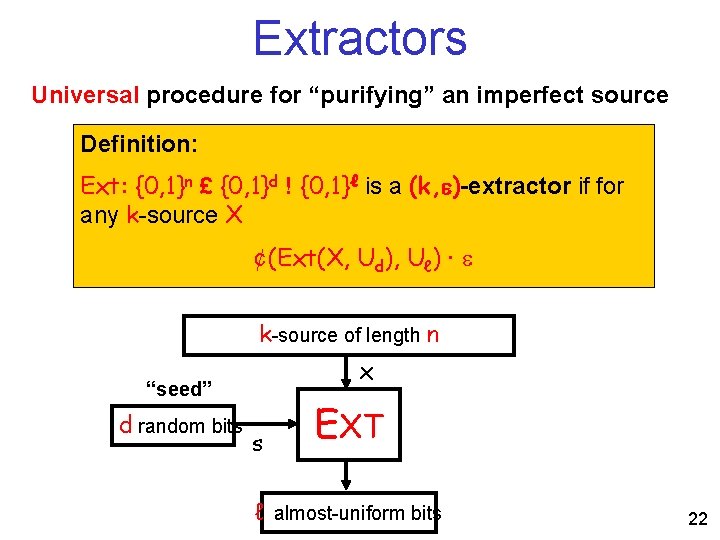
Extractors Universal procedure for “purifying” an imperfect source Definition: Ext: {0, 1}n £ {0, 1}d ! {0, 1}ℓ is a (k, )-extractor if for any k-source X ¢(Ext(X, Ud), Uℓ) · k-source of length n x “seed” d random bits s EXT ℓ almost-uniform bits 22

Strong Extractors Output looks random even after seeing the seed Definition: Ext: {0, 1}n £ {0, 1}d ! {0, 1}ℓ is a (k, )-strong extractor if Ext’(x, s) = s ◦ Ext(x, s) is a (k, )-extractor Leftover hash lemma [ILL 89]: Pairwise independent hash functions are strong extractors Example: Ext(x, (a, b)) = first ℓ bits of ax+b over GF[2 n] n n Output length ℓ = k – 2 log(1/ ) Seed length d = 2 n, almost pairwise independence d = O(log n + 23

The One Time Problem With shared keys • Alice and Bob share a secret key • Alice wants to send a message m {0, 1}n to Bob • Secrecy and authentication is maintained • They want to prevent Eve from interfering – Bob should be sure that the message m’ he receives is equal to the message m Alice sent – For secrecy: one-time pad – For authentication: can use Universal 2 hash

Authentication using hash functions

Session Key Encryption Alice Bob Ciphertext Plaintext m c=EA(m, K) Shared key K Decryption and Verification m=DV(E(m, K)

Structure of Construction: “Hybrid” Encryption: • Use public key to generate shared session key • Use shared key to encrypt + authenticate with one time scheme Decryption: • Use secret key to obtain session key • Use session decryption. Check authentication. • If fails reject. Ow output message.

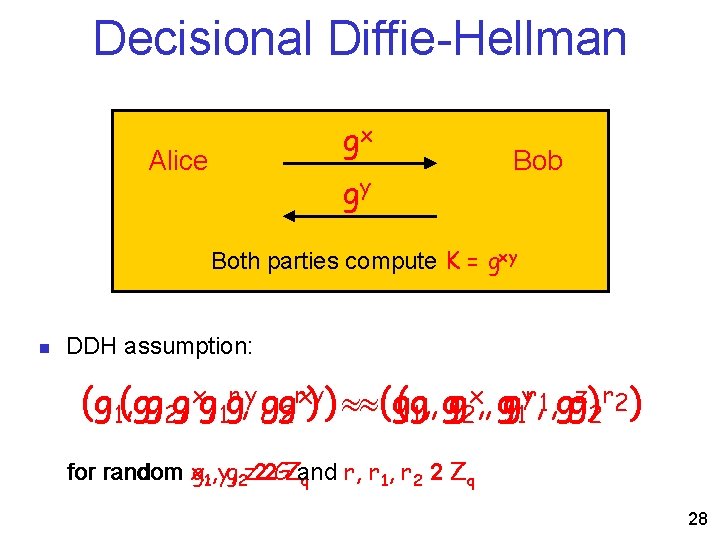
Decisional Diffie-Hellman gx Alice gy Bob Both parties compute K = gxy n DDH assumption: x, , g yr, 1, gg z) r 2 ) (g 1(g, , g 2 g, xg, 1 gr, y, gg 2 rxy) ) (g(g, , g g g 1 2 for random x, g 1, y, g 2 z 22 GZand r, r 1, r 2 2 Zq q 28

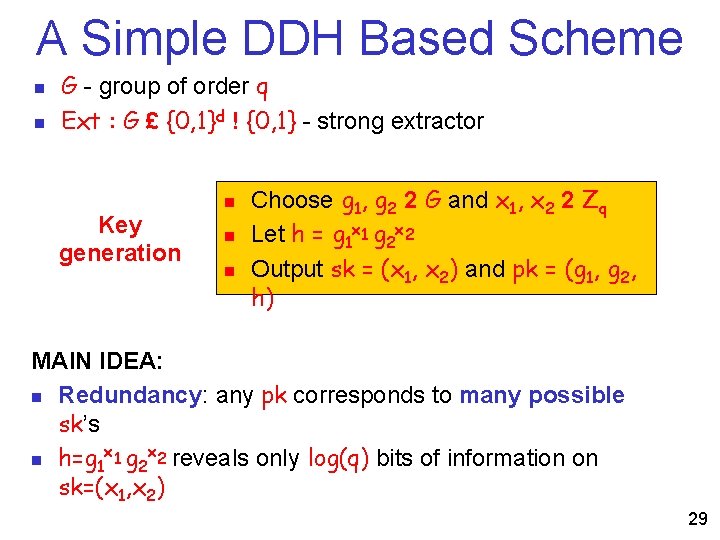
A Simple DDH Based Scheme n n G - group of order q Ext : G £ {0, 1}d ! {0, 1} - strong extractor Key generation n Choose g 1, g 2 2 G and x 1, x 2 2 Zq Let h = g 1 x 1 g 2 x 2 Output sk = (x 1, x 2) and pk = (g 1, g 2, h) MAIN IDEA: n Redundancy: any pk corresponds to many possible sk’s x x n h=g 1 1 g 2 2 reveals only log(q) bits of information on sk=(x 1, x 2) 29

A Simple Scheme n n G - group of order q Ext : G £ {0, 1}d ! {0, 1} - strong extractor n Key generation n Encpk(m) n Decsk(u 1, u 2, e) n Choose g 1, g 2 2 G and x 1, x 2 2 Zq Let h = g 1 x 1 g 2 x 2 Output sk = (x 1, x 2) and pk = (g 1, g 2, h) Choose r 2 Zq Output (g 1 r, g 2 r, AE(m, hr) Let k= u 1 x 1 u 2 x 2. Output DV(e, k) u 1 x 1 u 2 x 2 = g 1 rx 1 g 2 rx 2 = (g 1 x 1 g 2 x 2)r = hr 30

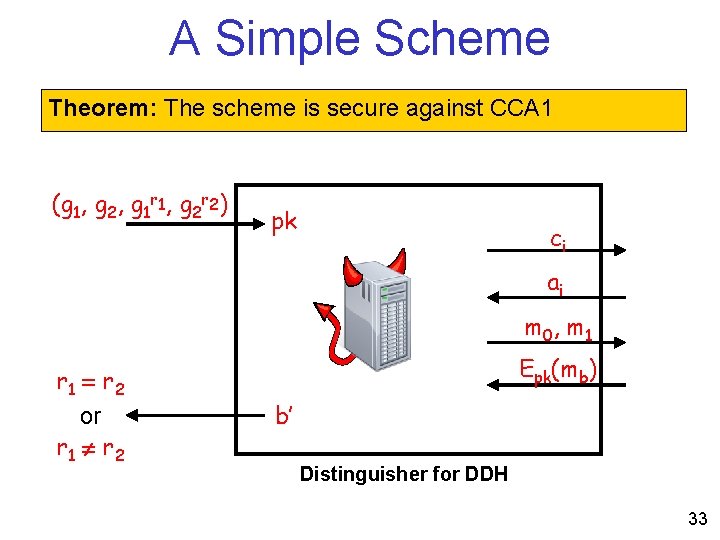
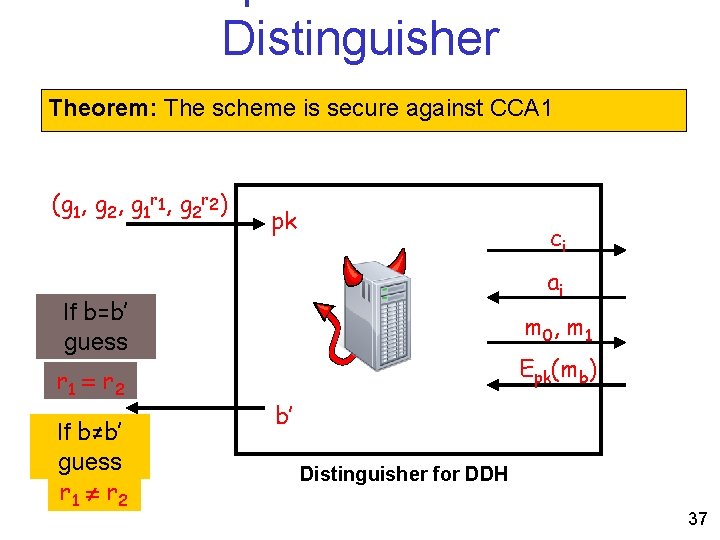
A Simple Scheme Theorem: The scheme is secure against CCA 1 Proof by reduction: Adversary for the encryption scheme Distinguisher for decisional Diffie. Hellman 31

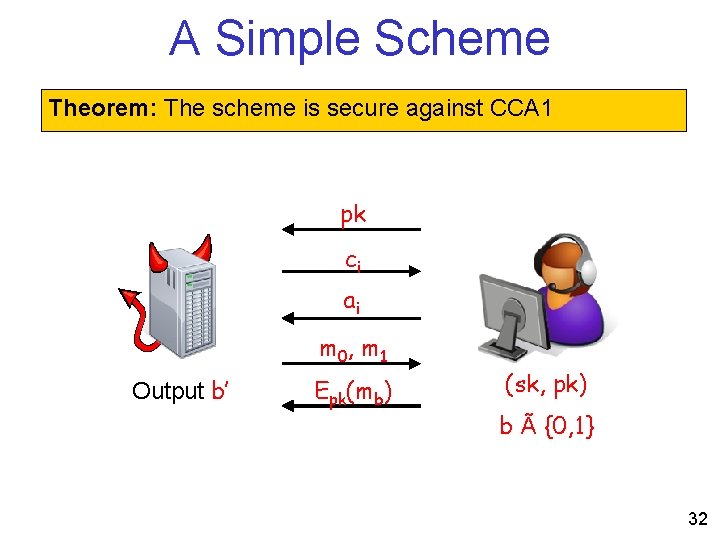
A Simple Scheme Theorem: The scheme is secure against CCA 1 pk ci ai m 0, m 1 Output b’ Epk(mb) (sk, pk) b à {0, 1} 32

A Simple Scheme Theorem: The scheme is secure against CCA 1 (g 1, g 2, g 1 r 1, g 2 r 2) pk ci ai m 0, m 1 r 1 = r 2 or r 1 r 2 Epk(mb) b’ Distinguisher for DDH 33

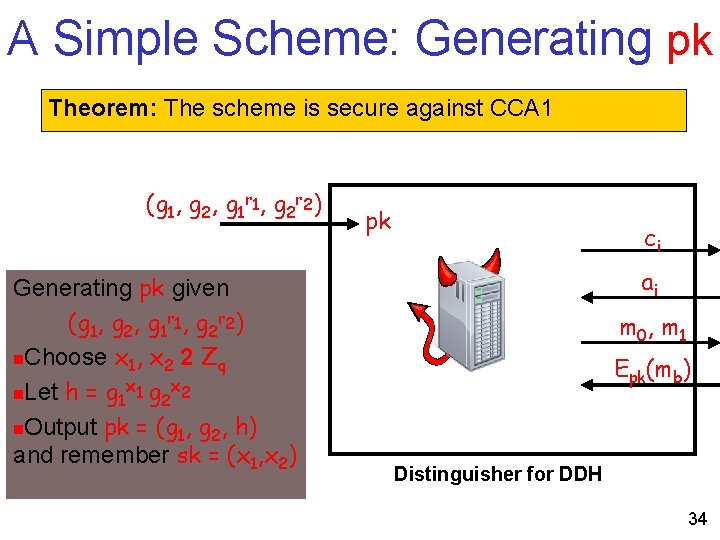
A Simple Scheme: Generating pk Theorem: The scheme is secure against CCA 1 (g 1, g 2, g 1 r 1, g 2 r 2) Generating pk given (g 1, g 2, g 1 r 1, g 2 r 2) n. Choose x 1, x 2 2 Zq x x n. Let h = g 1 1 g 2 2 n. Output pk = (g 1, g 2, h) and remember sk = (x 1, x 2) pk ci ai m 0, m 1 Epk(mb) Distinguisher for DDH 34

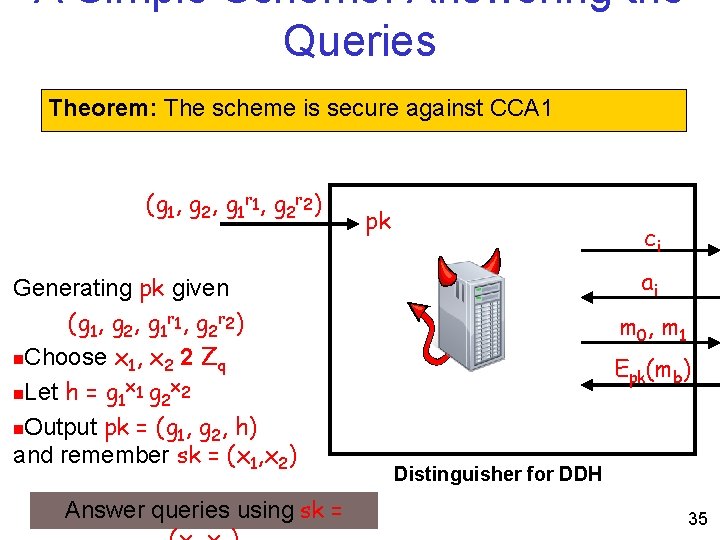
A Simple Scheme: Answering the Queries Theorem: The scheme is secure against CCA 1 (g 1, g 2, g 1 r 1, g 2 r 2) Generating pk given (g 1, g 2, g 1 r 1, g 2 r 2) n. Choose x 1, x 2 2 Zq x x n. Let h = g 1 1 g 2 2 n. Output pk = (g 1, g 2, h) and remember sk = (x 1, x 2) Answer queries using sk = pk ci ai m 0, m 1 Epk(mb) Distinguisher for DDH 35

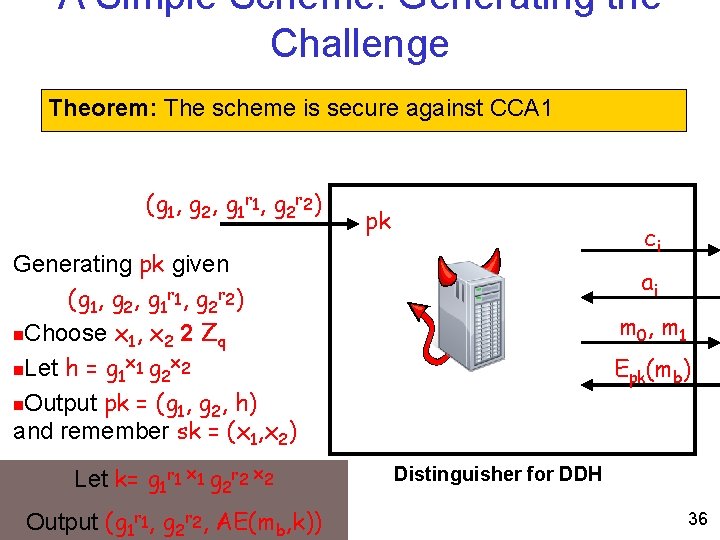
A Simple Scheme: Generating the Challenge Theorem: The scheme is secure against CCA 1 (g 1, g 2, g 1 r 1, g 2 r 2) pk ci Generating pk given (g 1, g 2, g 1 r 1, g 2 r 2) n. Choose x 1, x 2 2 Zq x x n. Let h = g 1 1 g 2 2 n. Output pk = (g 1, g 2, h) and remember sk = (x 1, x 2) Let k= g 1 r 1 x 1 g 2 r 2 x 2 Output (g 1 r 1, g 2 r 2, AE(mb, k)) ai m 0, m 1 Epk(mb) Distinguisher for DDH 36

Distinguisher Theorem: The scheme is secure against CCA 1 (g 1, g 2, g 1 r 1, g 2 r 2) pk ci ai If b=b’ guess r 1 = r 2 If b≠b’ guess r 1 r 2 m 0, m 1 Epk(mb) b’ Distinguisher for DDH 37

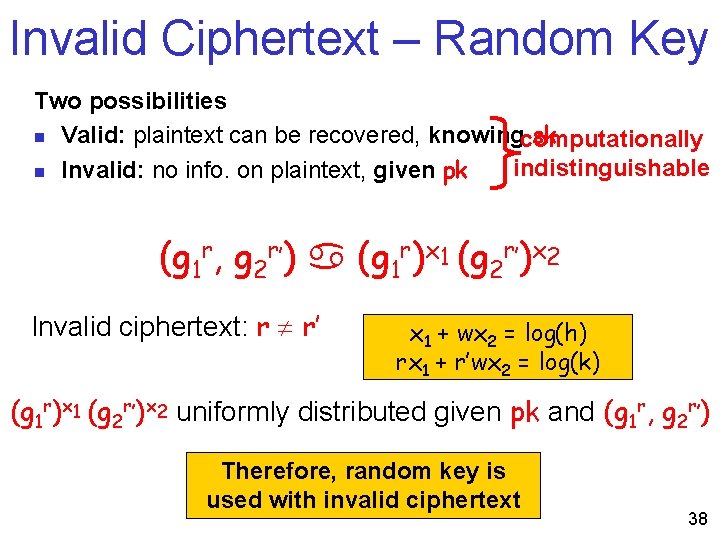
Invalid Ciphertext – Random Key Two possibilities n Valid: plaintext can be recovered, knowingcomputationally sk indistinguishable n Invalid: no info. on plaintext, given pk (g 1 r, g 2 r’) (g 1 r)x 1 (g 2 r’)x 2 Invalid ciphertext: r r’ x 1 + wx 2 = log(h) rx 1 + r’wx 2 = log(k) (g 1 r)x 1 (g 2 r’)x 2 uniformly distributed given pk and (g 1 r, g 2 r’) Therefore, random key is used with invalid ciphertext 38

Proof: nothing leaked about x 1, x 2 n Given the public key pk = (g 1, g 2, h) one linear equation is known on x 1, x 2 n n Given h = g 1 x 1 g 2 x 2. Still log q entropy Claim: this entropy is kept during the query-attack phase n In legitimate query ciphertexts: (v 1=g 1 r, v 2=g 2 r) and AE(m, k)) and the decryption is independent of x 1, n x 2 In invalid query ciphertexts: (v 1=g 1 r, v 2=g 2 r’) and AE(m, k)) is rejected whp

Proof: when input not DDH – challenge ciphertext independent of message For the original input (g 1, g 2, g 1 r 1, g 2 r 2): challenge ciphertext – Let k = g 1 r 1 x 1 g 2 r 2 x 2 – Output (g 1 r 1, g 2 r 2, AE(mb, k)) n if r 1 r 2 then k is random and hence independent of mb n n Even an all powerful adversary cannot guess b with probability better than ½. if r 1 = r 2 then challenge ciphertex is “normal”. n Adversary should guess b with probability better than ½+

Proof: summing up During the attack: • Chance for invalid ciphertext not labeled as such: q ¢ Pr[forgery in AE] • Entropy of x 1, x 2 decreased by this amount Challenge ciphertext valid or not depending on whether the input is in DDH or not. • If original adversary wins the game with probability ½+ • Advantage in distinguishing DDH from non-DDH is