INFS 766INFT 865 Internet Security Protocols Lectures 3










































- Slides: 76

INFS 766/INFT 865 Internet Security Protocols Lectures 3 and 4 Cryptography in network protocols Prof. Ravi Sandhu

CRYPTOGRAPHY

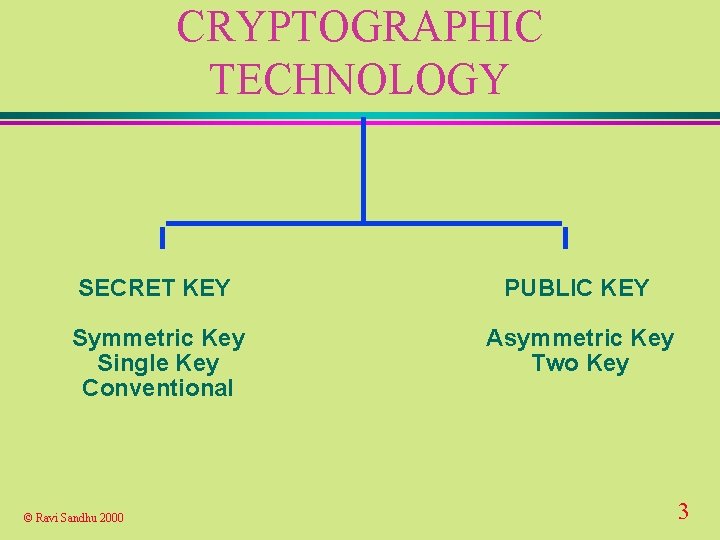
CRYPTOGRAPHIC TECHNOLOGY SECRET KEY PUBLIC KEY Symmetric Key Single Key Conventional Asymmetric Key Two Key © Ravi Sandhu 2000 3

CRYPTOGRAPHIC TECHNOLOGY u Secret-key encryption u Public-key digital signatures u Public-key agreement u Message digests u Message authentication codes u Challenge-response authentication u Public-key certificates © Ravi Sandhu 2000 4

CRYPTOGRAPHIC SERVICES u confidentiality l traffic flow confidentiality u integrity u authentication u non-repudiation © Ravi Sandhu 2000 5

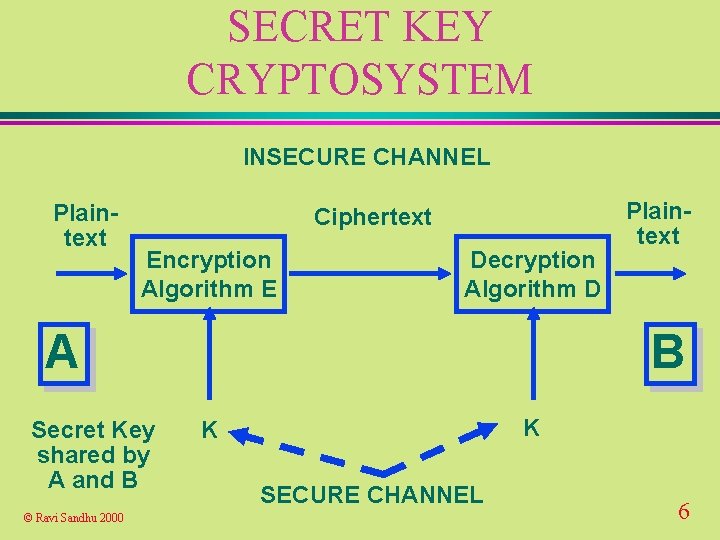
SECRET KEY CRYPTOSYSTEM INSECURE CHANNEL Plaintext Ciphertext Encryption Algorithm E Decryption Algorithm D A Secret Key shared by A and B © Ravi Sandhu 2000 Plaintext B K K SECURE CHANNEL 6

SECRET KEY CRYPTOSYSTEM u confidentiality depends only on secrecy of the key l size of key is critical u secret l u. A key systems do not scale well with N parties we need to generate and distribute N*(N-1)/2 keys and B can be people or computers © Ravi Sandhu 2000 7

MASTER KEYS AND SESSION KEYS u long-term l prolonged use increases exposure u session l or master keys short-term keys communicated by means of n long-term secret keys n public key technology © Ravi Sandhu 2000 8

CRYPTANALYSIS u ciphertext l cryptanalyst only knows ciphertext u known l only plaintext cryptanalyst knows some plaintextciphertext pairs u chosen plaintext u chosen ciphertext © Ravi Sandhu 2000 9

KNOWN PLAINTEXT ATTACK bit key requires 239 5 * 1011 trials on average (exportable from USA) u trials/second time required 1 20, 000 years 103 20 years 106 6 days 109 9 minutes 1012 0. 5 seconds u 40 © Ravi Sandhu 2000 10

KNOWN PLAINTEXT ATTACK bit key requires 255 3. 6 * 10^16 trials on average (DES) u trials/second time required 1 109 years 103 106 years 106 103 years 109 1 year 1012 10 hours u 56 © Ravi Sandhu 2000 11

KNOWN PLAINTEXT ATTACK bit key requires 279 6 * 1023 trials on average (SKIPJACK) u trials/second time required 1 1016 years 103 1013 years 106 1010 years 109 107 years 1012 104 years u 80 © Ravi Sandhu 2000 12

KNOWN PLAINTEXT ATTACK bit key requires 2127 2 * 1038 trials on average (IDEA) u trials/second time required 1 1030 years 103 1027 years 106 1024 years 109 1021 years 1012 1018 years u 128 © Ravi Sandhu 2000 13

DICTIONARY ATTACKS u if keys are poorly chosen known plaintext attacks can be very simple u often the user’s password is the key in a dictionary attack the cryptanalyst tries passwords from a dictionary, rather than all possible keys l for a 20, 000 word dictionary, 1 trial/second will crack a poor password in less than 3 hours l © Ravi Sandhu 2000 14

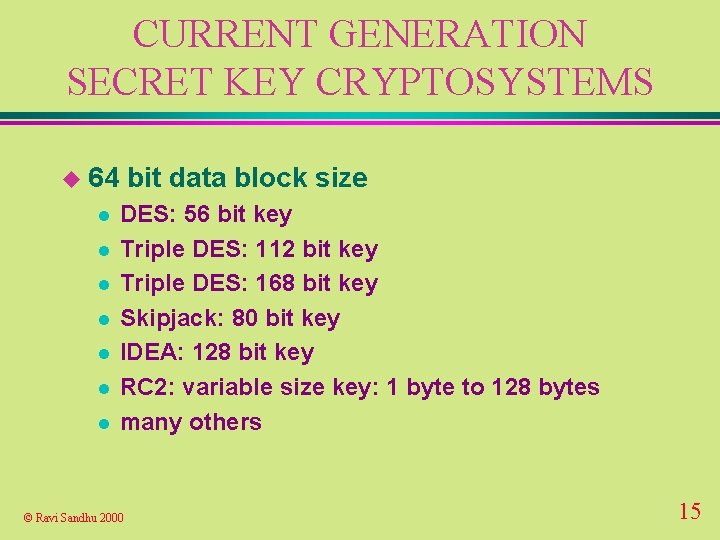
CURRENT GENERATION SECRET KEY CRYPTOSYSTEMS u 64 l l l l bit data block size DES: 56 bit key Triple DES: 112 bit key Triple DES: 168 bit key Skipjack: 80 bit key IDEA: 128 bit key RC 2: variable size key: 1 byte to 128 bytes many others © Ravi Sandhu 2000 15

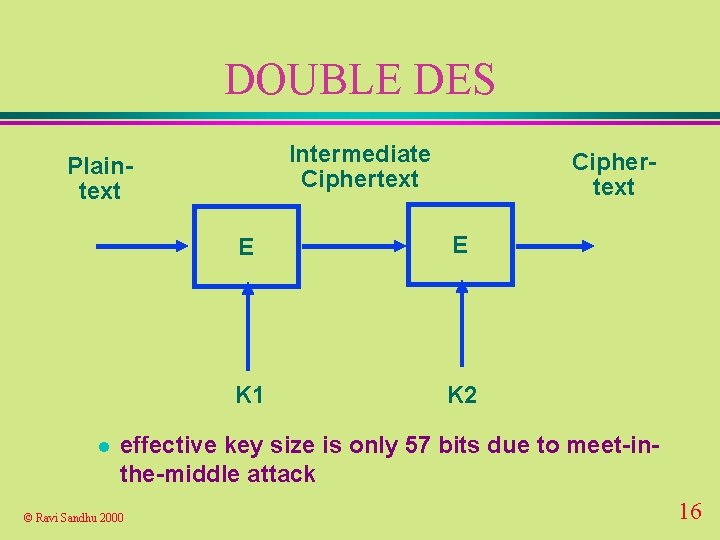
DOUBLE DES Intermediate Ciphertext Plaintext l Ciphertext E E K 1 K 2 effective key size is only 57 bits due to meet-inthe-middle attack © Ravi Sandhu 2000 16

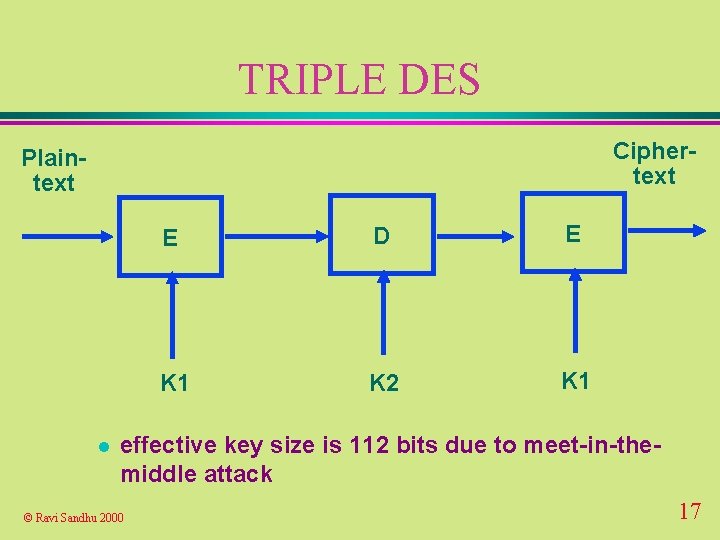
TRIPLE DES Ciphertext Plaintext l E D E K 1 K 2 K 1 effective key size is 112 bits due to meet-in-themiddle attack © Ravi Sandhu 2000 17

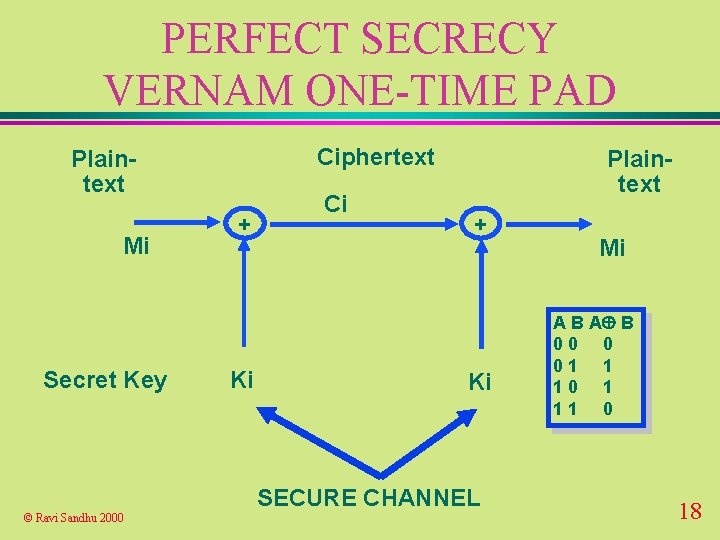
PERFECT SECRECY VERNAM ONE-TIME PAD Ciphertext Plaintext Mi Secret Key + Ki Ci Plaintext + Ki SECURE CHANNEL © Ravi Sandhu 2000 Mi A B 00 0 01 1 10 1 11 0 18

PERFECT SECRECY VERNAM ONE-TIME PAD u known plaintext reveals the portion of the key that has been used, but does not reveal anything about the future bits of the key u has been used u can be approximated © Ravi Sandhu 2000 19

NEXT GENERATION SECRET KEY CRYPTOSYSTEMS u new Advanced Encryption Standard under development by NIST l must support key-block combinations of 128 -128, 192 -128, 256 -128 l may support other combinations u ongoing international competition u will be in place in a couple of years © Ravi Sandhu 2000 20

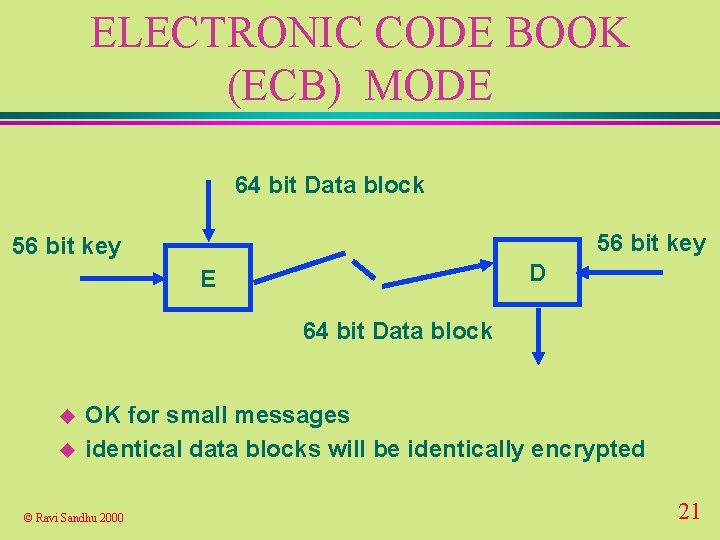
ELECTRONIC CODE BOOK (ECB) MODE 64 bit Data block 56 bit key D E 64 bit Data block u u OK for small messages identical data blocks will be identically encrypted © Ravi Sandhu 2000 21

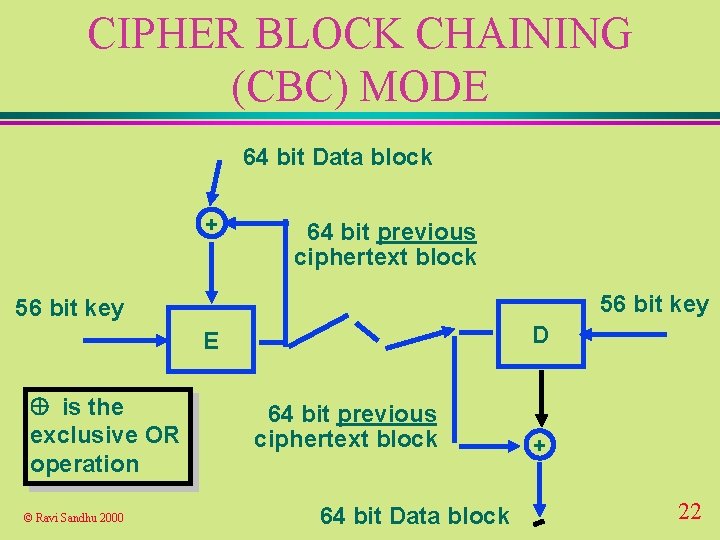
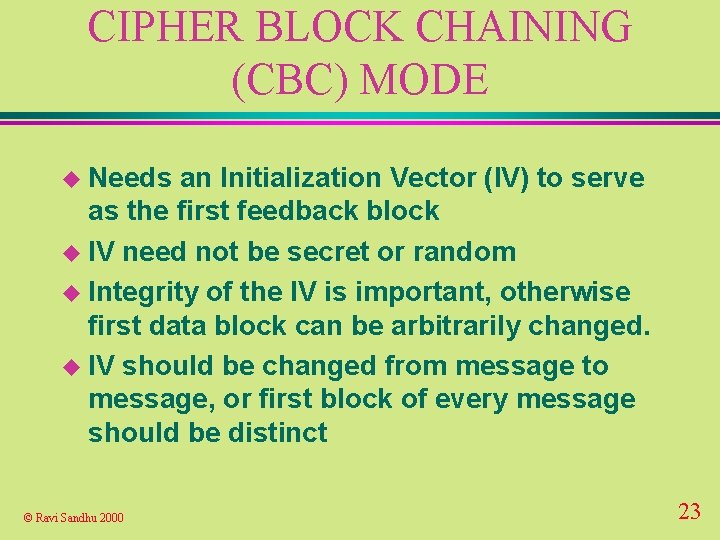
CIPHER BLOCK CHAINING (CBC) MODE 64 bit Data block + 64 bit previous ciphertext block 56 bit key D E is the exclusive OR operation © Ravi Sandhu 2000 64 bit previous ciphertext block 64 bit Data block + 22

CIPHER BLOCK CHAINING (CBC) MODE u Needs an Initialization Vector (IV) to serve as the first feedback block u IV need not be secret or random u Integrity of the IV is important, otherwise first data block can be arbitrarily changed. u IV should be changed from message to message, or first block of every message should be distinct © Ravi Sandhu 2000 23

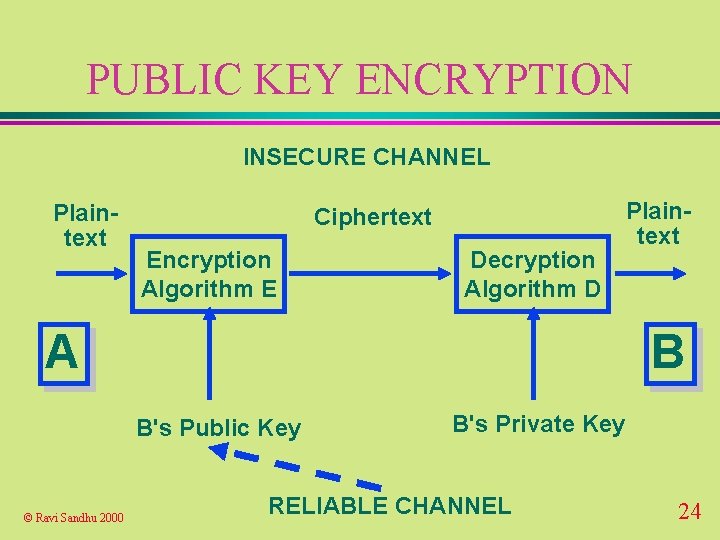
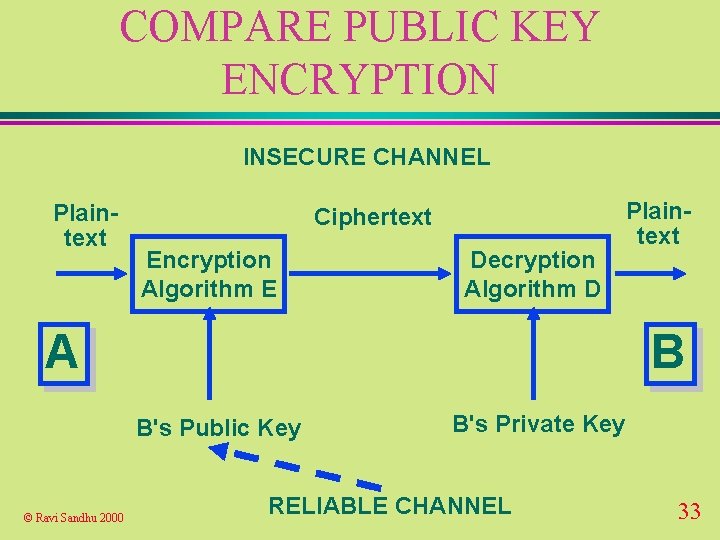
PUBLIC KEY ENCRYPTION INSECURE CHANNEL Plaintext Ciphertext Encryption Algorithm E Decryption Algorithm D A B B's Public Key © Ravi Sandhu 2000 Plaintext B's Private Key RELIABLE CHANNEL 24

PUBLIC KEY CRYPTOSYSTEM u solves the key distribution problem provided there is a reliable channel for communication of public keys u requires reliable dissemination of 1 public key/party u scales well for large-scale systems © Ravi Sandhu 2000 25

PUBLIC KEY ENCRYPTION u confidentiality based on infeasibility of computing B's private key from B's public key u key sizes are large (512 bits and above) to make this computation infeasible © Ravi Sandhu 2000 26

SPEED OF PUBLIC KEY VERSUS SECRET KEY u Public l key runs at kilobits/second think modem connection u Secret key runs at megabits/second and even gigabits/second l think LAN or disk connection u This large difference in speed is likely to remain independent of technology advances © Ravi Sandhu 2000 27

RSA u public key is (n, e) u private key is d u encrypt: C = Me mod n u decrypt: M = Cd mod n © Ravi Sandhu 2000 28

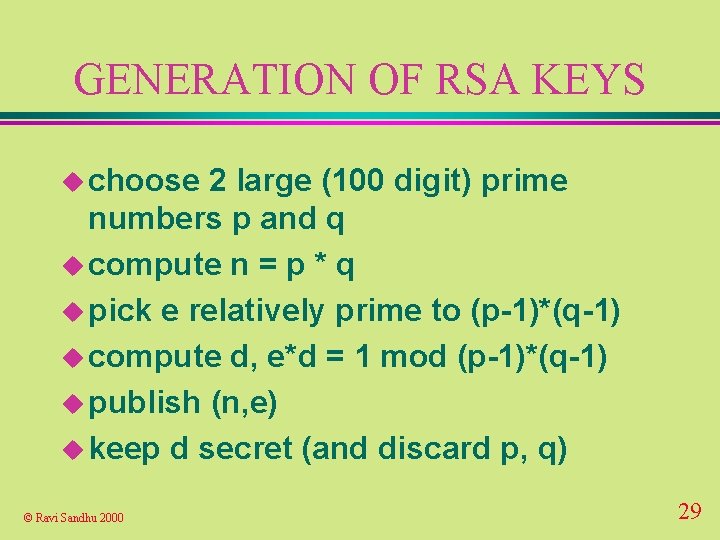
GENERATION OF RSA KEYS u choose 2 large (100 digit) prime numbers p and q u compute n = p * q u pick e relatively prime to (p-1)*(q-1) u compute d, e*d = 1 mod (p-1)*(q-1) u publish (n, e) u keep d secret (and discard p, q) © Ravi Sandhu 2000 29

PROTECTION OF RSA KEYS u compute l d, e*d = 1 mod (p-1)*(q-1) if factorization of n into p*q is known, this is easy to do u security of RSA is no better than the difficulty of factoring n into p, q © Ravi Sandhu 2000 30

RSA KEY SIZE u key size of RSA is selected by the user casual l “commercial” l “military” l © Ravi Sandhu 2000 384 bits 512 bits 1024 bits 31

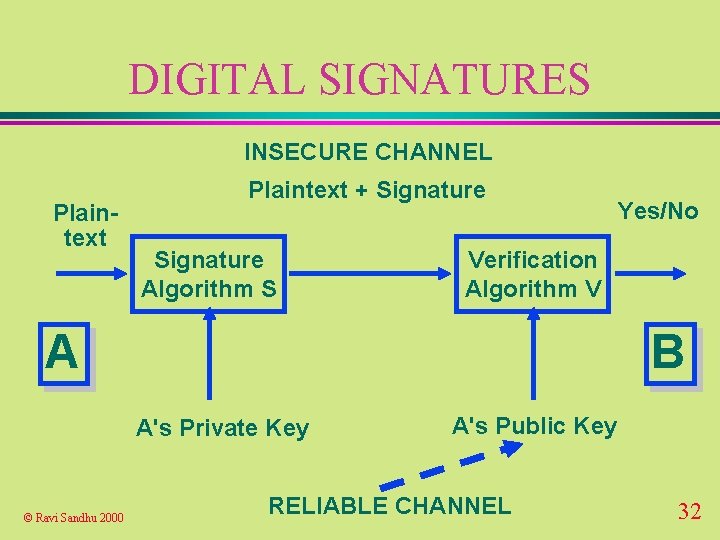
DIGITAL SIGNATURES INSECURE CHANNEL Plaintext + Signature Algorithm S Verification Algorithm V A B A's Private Key © Ravi Sandhu 2000 Yes/No A's Public Key RELIABLE CHANNEL 32

COMPARE PUBLIC KEY ENCRYPTION INSECURE CHANNEL Plaintext Ciphertext Encryption Algorithm E Decryption Algorithm D A B B's Public Key © Ravi Sandhu 2000 Plaintext B's Private Key RELIABLE CHANNEL 33

DIGITAL SIGNATURES IN RSA u RSA has a unique property, not shared by other public key systems u Encryption and decryption commute (Me mod n)d mod n = M l (Md mod n)e mod n = M l encryption signature u Same public key can be use for encryption and signature © Ravi Sandhu 2000 34

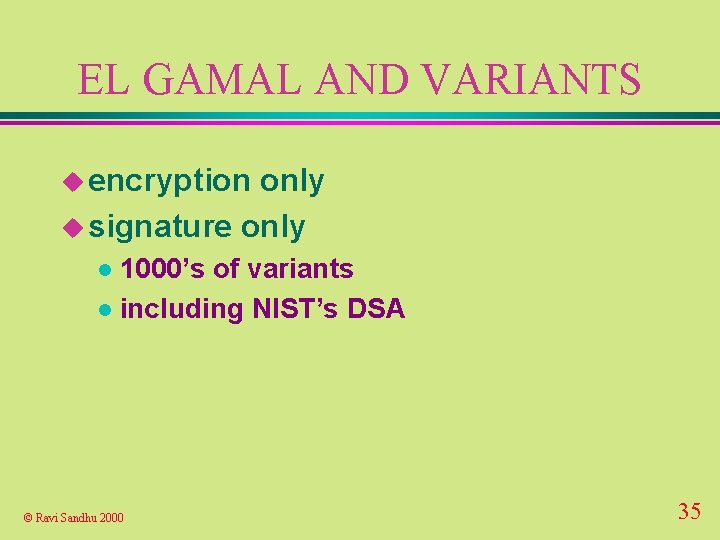
EL GAMAL AND VARIANTS u encryption only u signature only 1000’s of variants l including NIST’s DSA l © Ravi Sandhu 2000 35

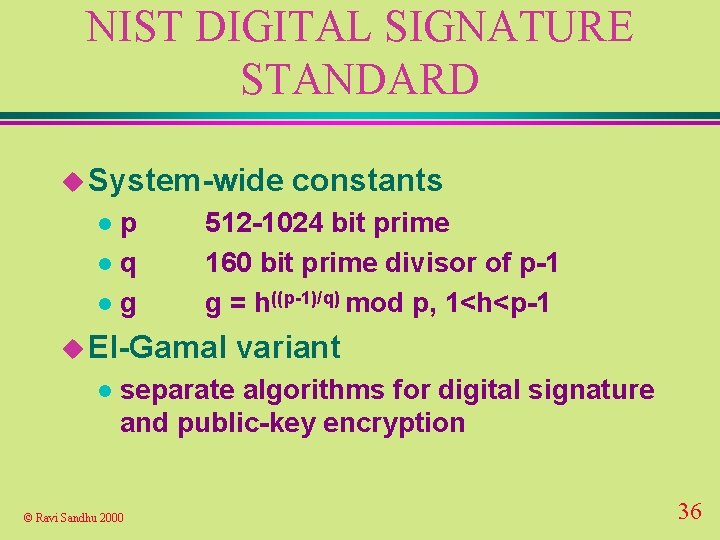
NIST DIGITAL SIGNATURE STANDARD u System-wide p lq lg l 512 -1024 bit prime 160 bit prime divisor of p-1 g = h((p-1)/q) mod p, 1<h<p-1 u El-Gamal l constants variant separate algorithms for digital signature and public-key encryption © Ravi Sandhu 2000 36

NIST DIGITAL SIGNATURE STANDARD u to l l l sign message m: private key x choose random r compute v = (gr mod p) mod q compute s = (m+xv)/k mod q signature is (s, v, m) verify signature: public key y compute u 1 = m/s mod q compute u 2 = v/s mod q verify that v = (gu 1*yu 2 mod p) mod q © Ravi Sandhu 2000 37

NIST DIGITAL SIGNATURE STANDARD u signature does not repeat, since r will be different on each occasion u if same random number r is used for two messages, the system is broken u message expands by a factor of 2 u RSA signatures do repeat, and there is no message expansion © Ravi Sandhu 2000 38

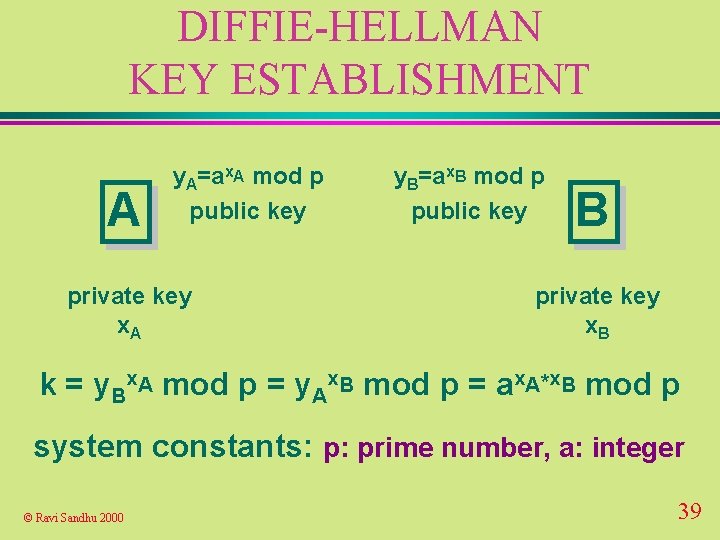
DIFFIE-HELLMAN KEY ESTABLISHMENT A y. A=ax. A mod p public key private key x. A y. B=ax. B mod p public key B private key x. B k = y. Bx. A mod p = y. Ax. B mod p = ax. A*x. B mod p system constants: p: prime number, a: integer © Ravi Sandhu 2000 39

DIFFIE-HELLMAN KEY ESTABLISHMENT u security depends on difficulty of computing x given y=ax mod p called the discrete logarithm problem © Ravi Sandhu 2000 40

CURRENT GENERATION PUBLIC KEY SYSTEMS u RSA (Rivest, Shamir and Adelman) l l u El. Gamal Encryption l l u the only one to provide digital signature and encryption using the same public-private key pair security based on factoring public-key encryption only security based on digital logarithm DSA signatures l l l public-key signature only one of many variants of El. Gamal signature security based on digital logarithm © Ravi Sandhu 2000 41

CURRENT GENERATION PUBLIC KEY SYSTEMS u DH (Diffie-Hellman) l l u secret key agreement only security based on digital logarithm ECC (Elliptic curve cryptography) l l security based on digital logarithm in elliptic curve field uses analogs of n n n El. Gamal encryption DH key agreement DSA digital signature © Ravi Sandhu 2000 42

ELLIPTIC CURVE CRYPTOGRAPHY u mathematics is more complicated than RSA or Diffie-Hellman u elliptic curves have been studied for over one hundred years u computation is done in a group defined by an elliptic curve © Ravi Sandhu 2000 43

ELLIPTIC CURVE CRYPTOGRAPHY u 160 bit ECC public key is claimed to be as secure as 1024 bit RSA or Diffie -Hellman key u good for small hardware implementations such as smart cards © Ravi Sandhu 2000 44

ELLIPTIC CURVE CRYPTOGRAPHY u ECDSA: Elliptic Curve digital signature algorithm based on NIST Digital Signature Standard u ECSVA: Elliptic Curve key agreement algorithm based on Diffie-Hellman u ECES: Elliptic Curve encryption algorithm based on El-Gamal © Ravi Sandhu 2000 45

PKCS STANDARDS u de facto standards initiated by RSA Data Inc. © Ravi Sandhu 2000 46

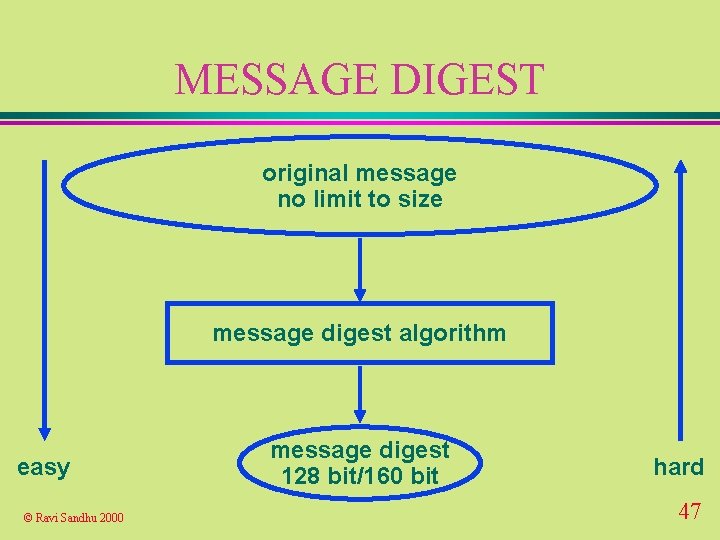
MESSAGE DIGEST original message no limit to size message digest algorithm easy © Ravi Sandhu 2000 message digest 128 bit/160 bit hard 47

MESSAGE DIGEST u for performance reasons sign the message digest l not the message l u one way function m=H(M) is easy to compute l M=H-1(m) is hard to compute l © Ravi Sandhu 2000 48

DESIRED CHARACTERISTICS u weak l hash function difficult to find M' such that H(M')=H(M) u given M, m=H(M) try messages at random to find M’ with H(M’)=m l 2 k trials on average, k=64 to be safe © Ravi Sandhu 2000 49

DESIRED CHARACTERISTICS u strong l hash function difficult to find any two M and M' such that H(M')=H(M) u try pairs of messages at random to find M and M’ such that H(M’)=H(M) 2 k/2 trials on average, k=128 to be safe l k=160 is better l © Ravi Sandhu 2000 50

CURRENTT GENERATION MESSAGE DIGEST ALGORITHMS u MD 5 (Message Digest 5) 128 bit message digest l falling out of favor l u SHA (Secure Hash Algorithm) 160 bit message digest l slightly slower than MD 5 but more secure l © Ravi Sandhu 2000 51

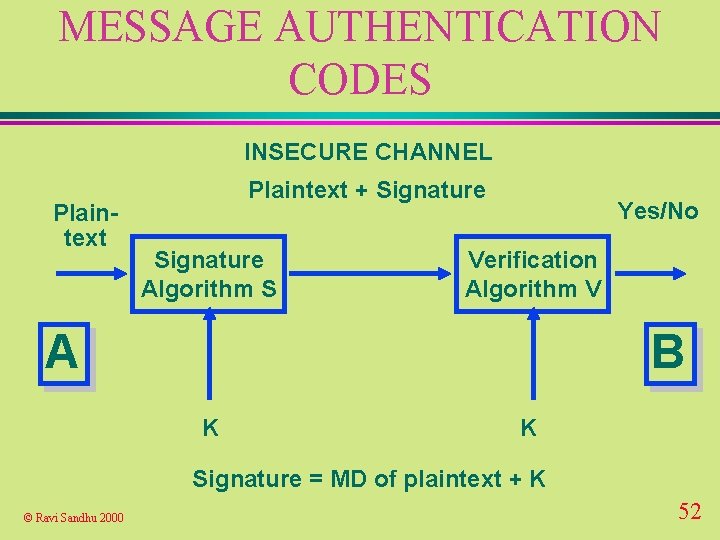
MESSAGE AUTHENTICATION CODES INSECURE CHANNEL Plaintext + Signature Algorithm S Yes/No Verification Algorithm V A B K K Signature = MD of plaintext + K © Ravi Sandhu 2000 52

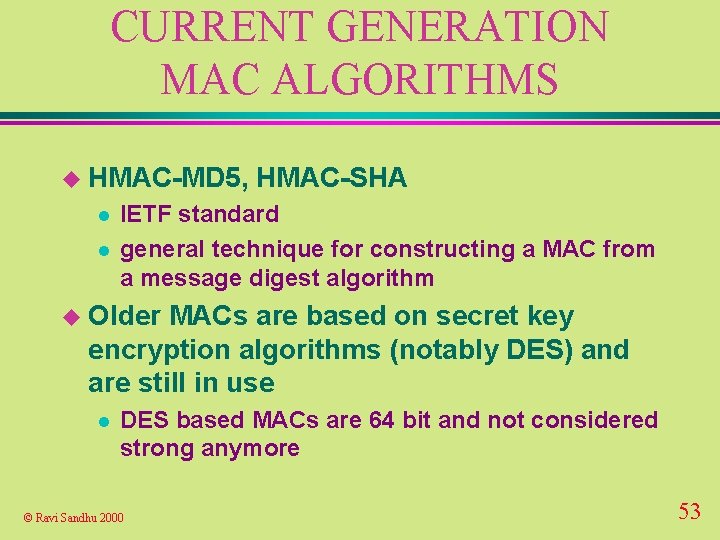
CURRENT GENERATION MAC ALGORITHMS u HMAC-MD 5, l l HMAC-SHA IETF standard general technique for constructing a MAC from a message digest algorithm u Older MACs are based on secret key encryption algorithms (notably DES) and are still in use l DES based MACs are 64 bit and not considered strong anymore © Ravi Sandhu 2000 53

HMAC u HMAC computation u HMACK(M) = h(K opad || h(K ipad || M) ) l h is any message digest function l M message l K secret key l opad, ipad: fixed outer and inner padding u HMAC-MD 5, © Ravi Sandhu 2000 HMAC-SHA 54

SAFE CRYPTOGRAPHY u Secret-key l encryption 128 bit or higher u Public-key l 1024 bit or higher u Message l digests 160 bit or higher u. A large portion of what is deployed is much weaker © Ravi Sandhu 2000 55

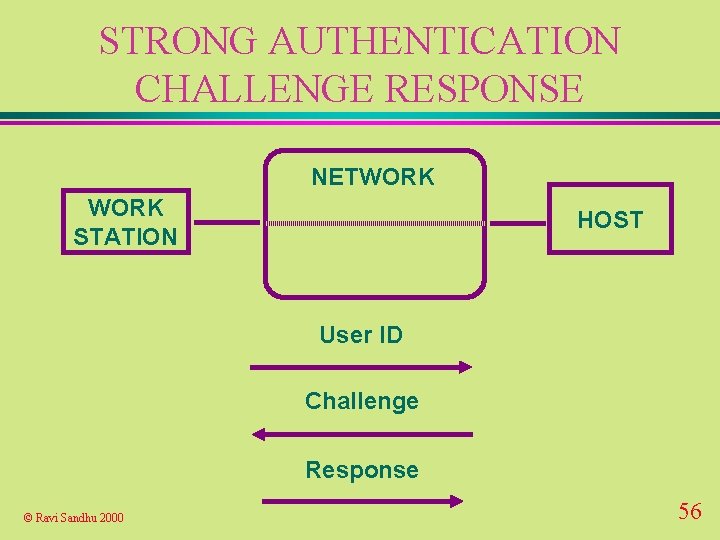
STRONG AUTHENTICATION CHALLENGE RESPONSE NETWORK STATION HOST User ID Challenge Response © Ravi Sandhu 2000 56

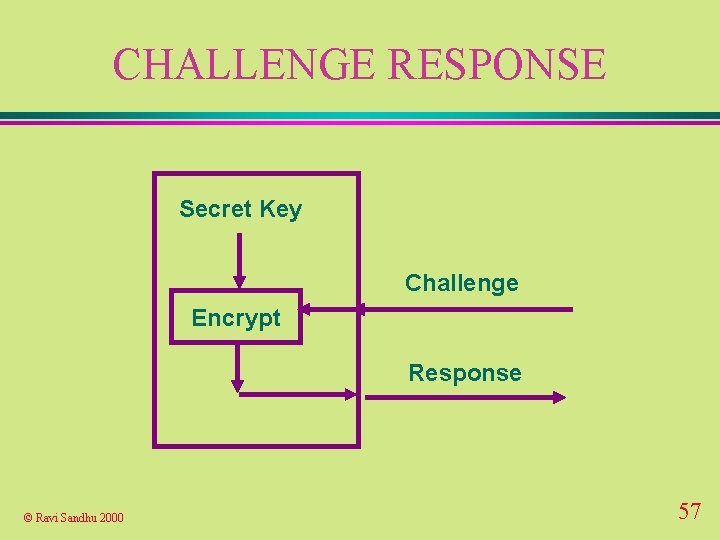
CHALLENGE RESPONSE Secret Key Challenge Encrypt Response © Ravi Sandhu 2000 57

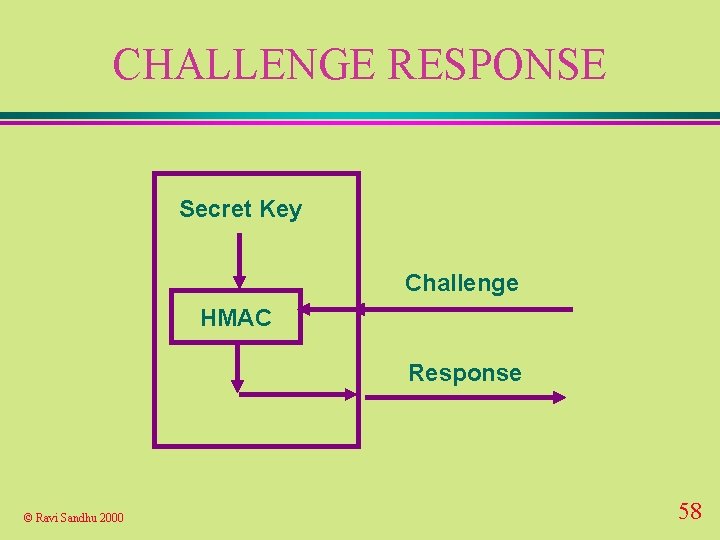
CHALLENGE RESPONSE Secret Key Challenge HMAC Response © Ravi Sandhu 2000 58

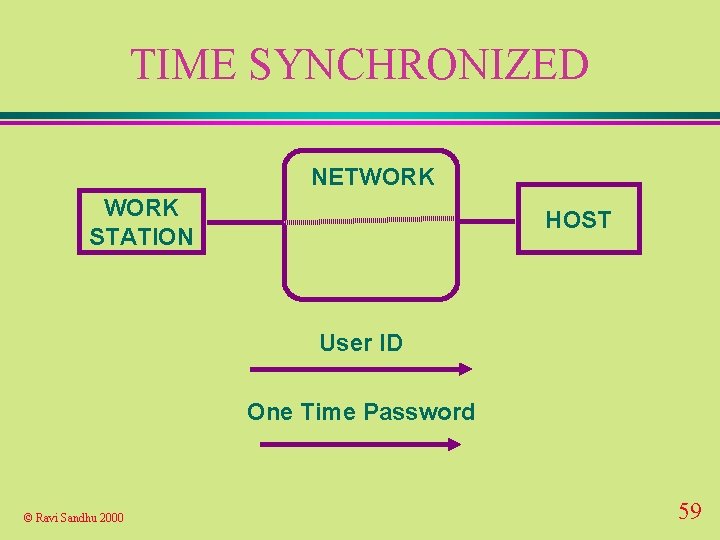
TIME SYNCHRONIZED NETWORK STATION HOST User ID One Time Password © Ravi Sandhu 2000 59

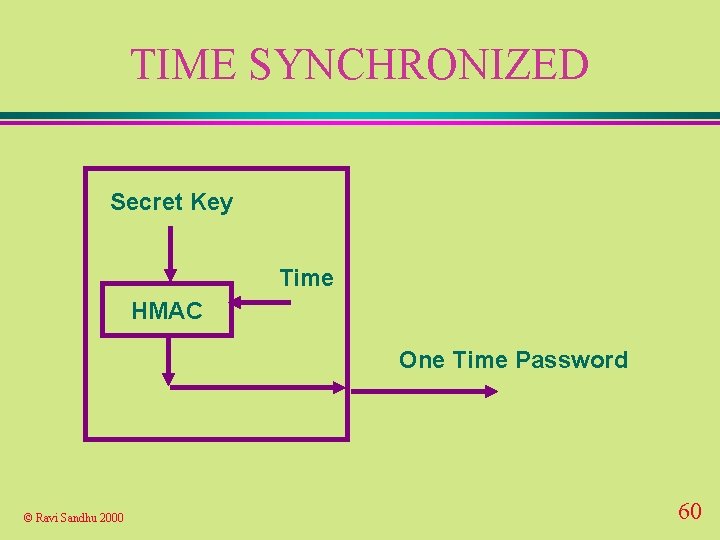
TIME SYNCHRONIZED Secret Key Time HMAC One Time Password © Ravi Sandhu 2000 60

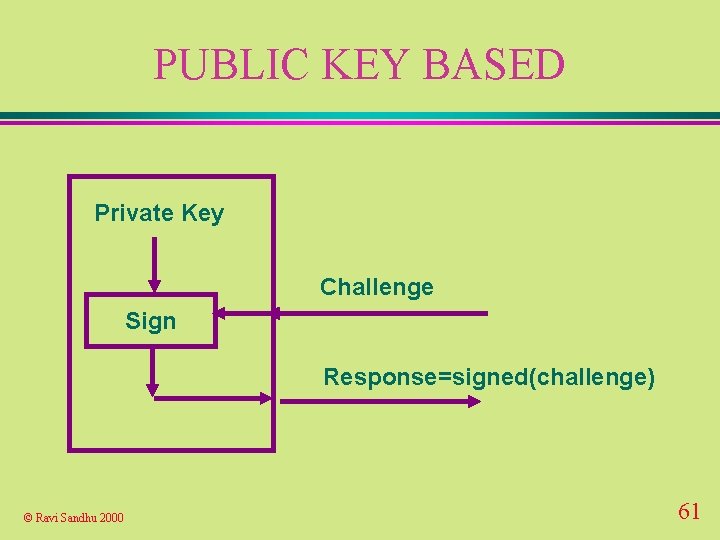
PUBLIC KEY BASED Private Key Challenge Sign Response=signed(challenge) © Ravi Sandhu 2000 61

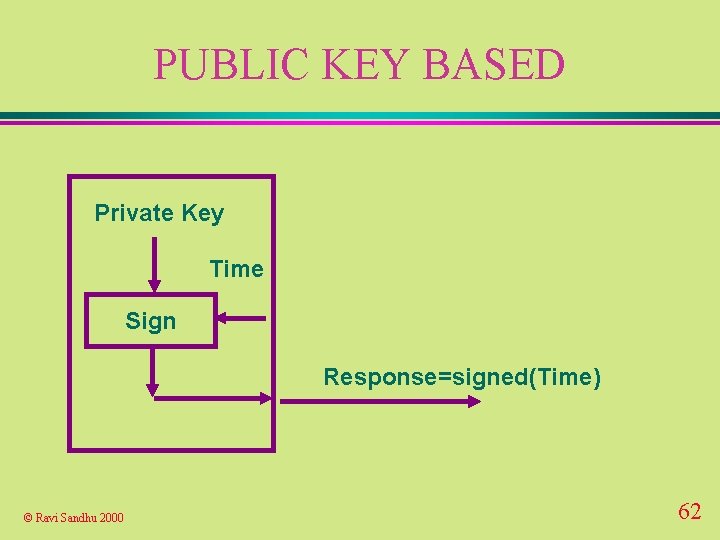
PUBLIC KEY BASED Private Key Time Sign Response=signed(Time) © Ravi Sandhu 2000 62

PUBLIC-KEY INFRASTRUCTURE

PUBLIC-KEY CERTIFICATES u reliable distribution of public-keys u public-key encryption l sender needs public key of receiver u public-key l receiver needs public key of sender u public-key l digital signatures key agreement both need each other’s public keys © Ravi Sandhu 2000 64

X. 509 CERTIFICATE VERSION SERIAL NUMBER SIGNATURE ALGORITHM ISSUER VALIDITY SUBJECT PUBLIC KEY INFO SIGNATURE © Ravi Sandhu 2000 65

X. 509 CERTIFICATE 1 1234567891011121314 RSA+MD 5, 512 C=US, S=VA, O=GMU, OU=ISSE 9/9/99 -1/1/1 C=US, S=VA, O=GMU, OU=ISSE, CN=Ravi Sandhu RSA, 1024, xxxxxxxxxxxxx SIGNATURE © Ravi Sandhu 2000 66

CERTIFICATE TRUST u how to acquire public key of the issuer to verify signature u whether or not to trust certificates signed by the issuer for this subject © Ravi Sandhu 2000 67

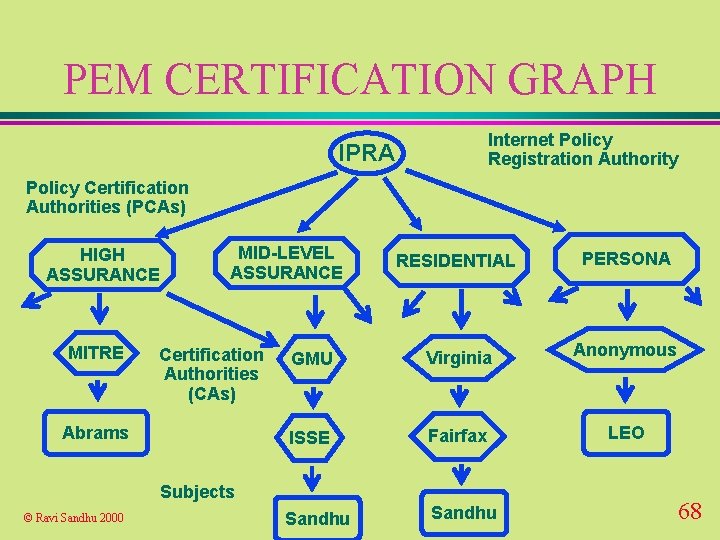
PEM CERTIFICATION GRAPH Internet Policy Registration Authority IPRA Policy Certification Authorities (PCAs) HIGH ASSURANCE MITRE MID-LEVEL ASSURANCE Certification Authorities (CAs) Abrams RESIDENTIAL PERSONA GMU Virginia Anonymous ISSE Fairfax LEO Sandhu Subjects © Ravi Sandhu 2000 68

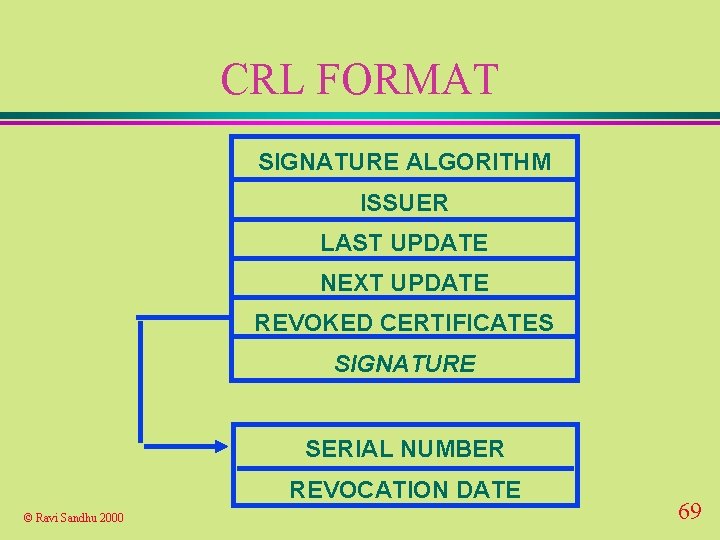
CRL FORMAT SIGNATURE ALGORITHM ISSUER LAST UPDATE NEXT UPDATE REVOKED CERTIFICATES SIGNATURE SERIAL NUMBER REVOCATION DATE © Ravi Sandhu 2000 69

X. 509 CERTIFICATES u X. 509 v 1 l very basic u X. 509 v 2 l adds unique identifiers to prevent against reuse of X. 500 names u X. 509 v 3 adds many extensions l can be further extended l © Ravi Sandhu 2000 70

X. 509 v 3 CERTIFICATE INNOVATIONS u distinguish various certificates l u identification info in addition to X. 500 name l u u good enough for casual email but not for signing checks limits on use of signature keys for further certification extensible l u internet names: email addresses, host names, URLs issuer can state policy and usage l u signature, encryption, key-agreement proprietary extensions can be defined and registered attribute certificates l ongoing work © Ravi Sandhu 2000 71

X. 509 v 2 CRL INNOVATIONS u CRL distribution points u indirect CRLs u delta CRLs u revocation reason u push CRLs © Ravi Sandhu 2000 72

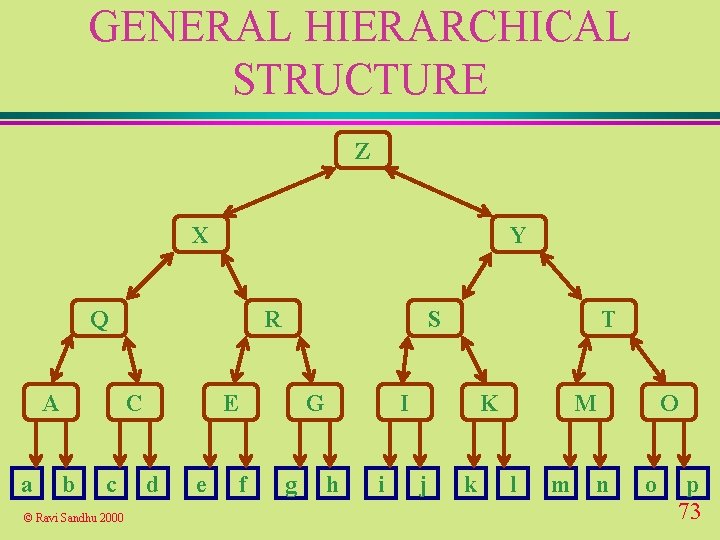
GENERAL HIERARCHICAL STRUCTURE Z X Y Q A a R C b c © Ravi Sandhu 2000 S E d e G f g T I h i K j k M l m O n o p 73

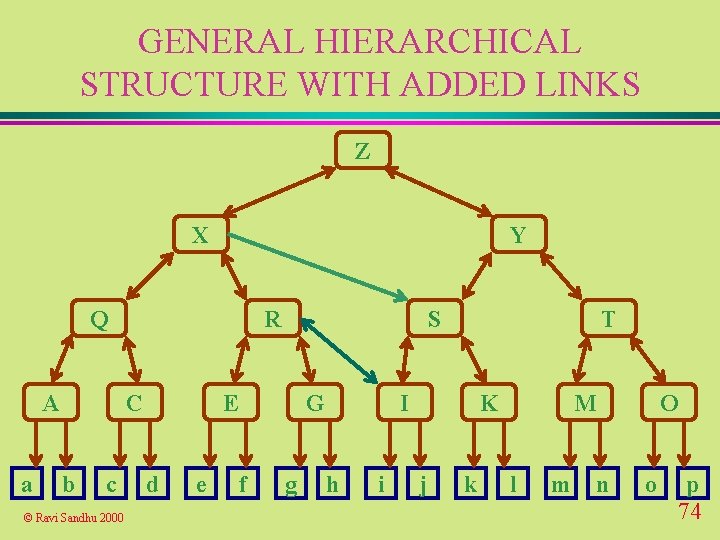
GENERAL HIERARCHICAL STRUCTURE WITH ADDED LINKS Z X Y Q A a R C b c © Ravi Sandhu 2000 S E d e G f g T I h i K j k M l m O n o p 74

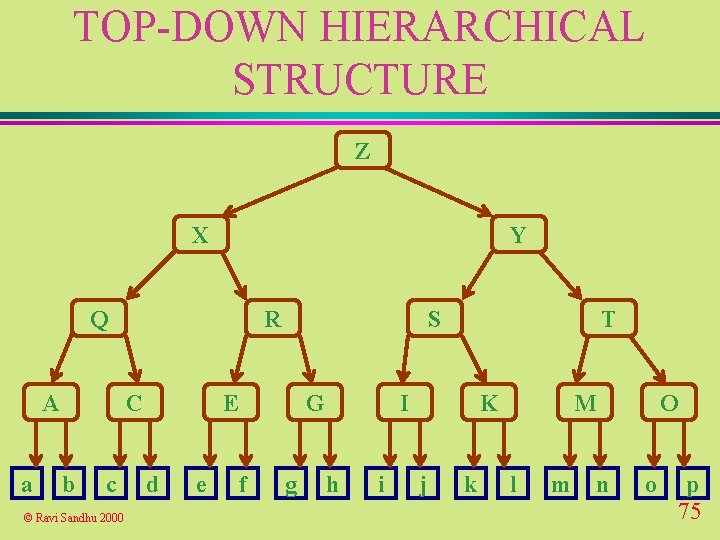
TOP-DOWN HIERARCHICAL STRUCTURE Z X Y Q A a R C b c © Ravi Sandhu 2000 S E d e G f g T I h i K j k M l m O n o p 75

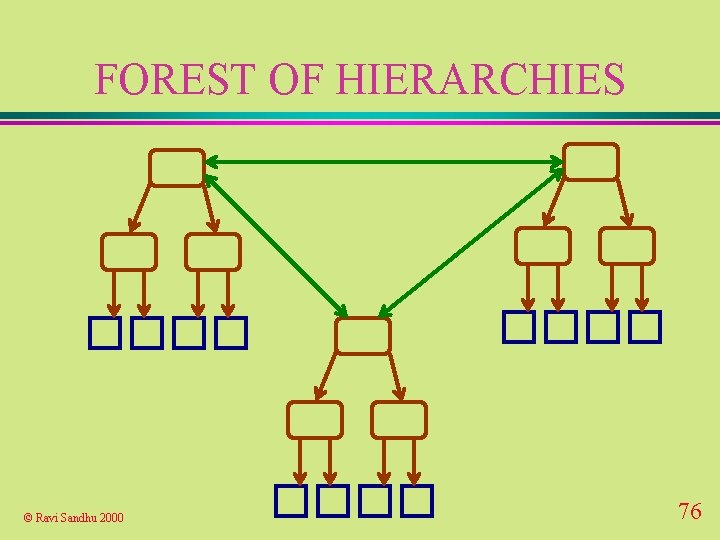
FOREST OF HIERARCHIES © Ravi Sandhu 2000 76