Computer Networks Internet protocols and network hardware Protocols












































- Slides: 68

Computer Networks

Internet protocols and network hardware Protocols are sets of rules or standards that are used for communication. They work together to help devices to communicate. The rules apply to different layers used for communication purposes. A network protocol is a standard method for transmitting data from one computer to another.

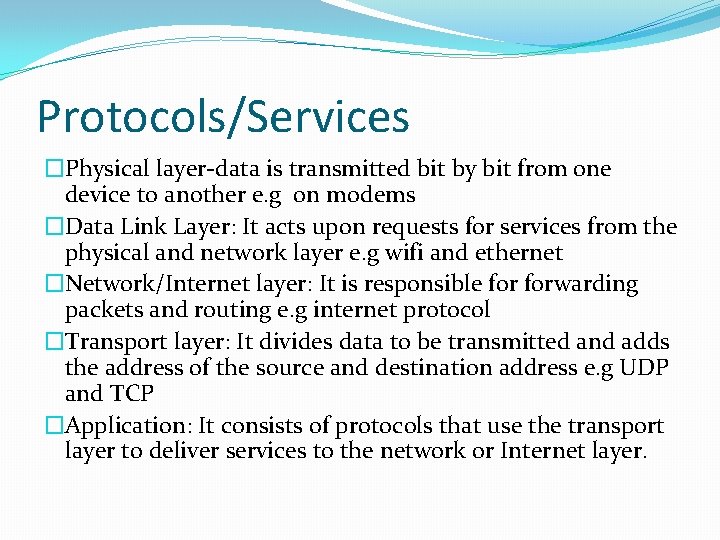
Protocols/Services �Physical layer-data is transmitted bit by bit from one device to another e. g on modems �Data Link Layer: It acts upon requests for services from the physical and network layer e. g wifi and ethernet �Network/Internet layer: It is responsible forwarding packets and routing e. g internet protocol �Transport layer: It divides data to be transmitted and adds the address of the source and destination address e. g UDP and TCP �Application: It consists of protocols that use the transport layer to deliver services to the network or Internet layer.

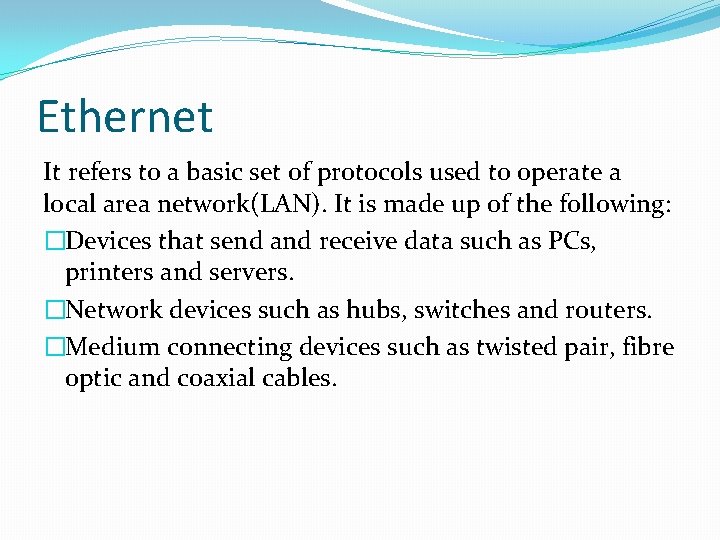
Ethernet It refers to a basic set of protocols used to operate a local area network(LAN). It is made up of the following: �Devices that send and receive data such as PCs, printers and servers. �Network devices such as hubs, switches and routers. �Medium connecting devices such as twisted pair, fibre optic and coaxial cables.

TCP/IP �Transmission Control Protocol(TCP) ensures that data is delivered correctly �Internet Protocol(IP) ensures that the data is delivered to the correct address. An IP address consists of 4 bytes which are given in decimal form �Techniques such as subnetting and local addressing are used to increase the number of addresses

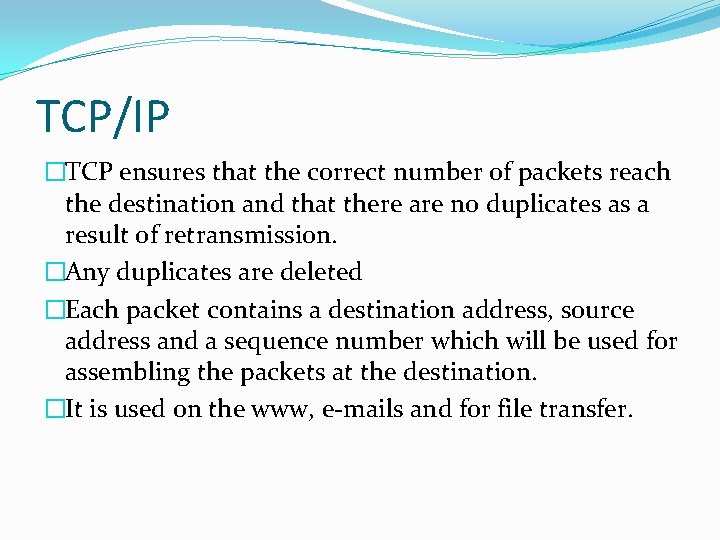
TCP/IP �TCP ensures that the correct number of packets reach the destination and that there are no duplicates as a result of retransmission. �Any duplicates are deleted �Each packet contains a destination address, source address and a sequence number which will be used for assembling the packets at the destination. �It is used on the www, e-mails and for file transfer.

Handshaking �It refers to the exchange of signals between devices to establish a communication channel eg the rate of transfer, parity checking and interrupts to be used. �Parity can be odd or even. It refers to the total number of bits within a transmitted message. �The number of bits is checked to make sure that there are no errors in transmission

UDP The UDP is a basic protocol. It is considered to be a connectionless service. No handshaking is required. It has no congestion control mechanisms. It is unreliable because packets of data may fail to reach the destination. It is still better suited for real-time transmissions e. g video on demand systems

FTP is used for the transfer of files when downloading and uploading files. FTP makes use of client-server systems. Clients have to log on in order to download files. SSL and SSH are used to enable encryption of files during transmission.

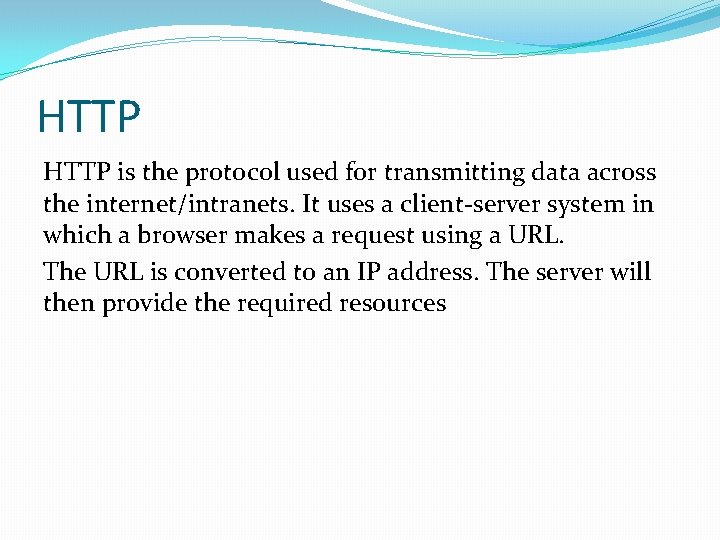
HTTP is the protocol used for transmitting data across the internet/intranets. It uses a client-server system in which a browser makes a request using a URL. The URL is converted to an IP address. The server will then provide the required resources

Telnet �Telnet is a network protocol used on the internet or within local area networks. It is used to enable a user to gain access to another computer and use the resources provided there. �It works at the same layer as FTP. The remote compter should have telnet client/server software. �Telnet has major security problems which has decreased its popularity. �It is still used for network diagnostics and troubleshooting problems.

SSH �It allows data to be shared between two computers. It allows users to log in remotely and also uses encryption. �It uses public-key authentication. �Its main purpose is to log into a machine remotely and execute commands. It is therefore used by administrators.

Network Hardware

Network Hardware Devices used in a computer network

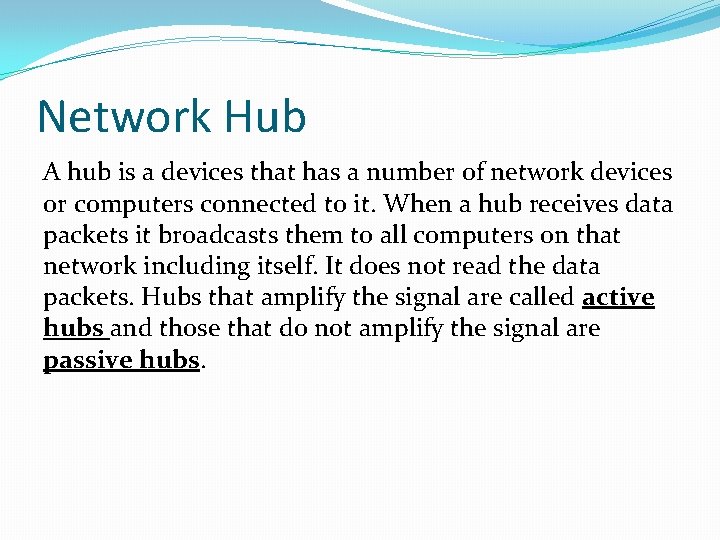
Network Hub A hub is a devices that has a number of network devices or computers connected to it. When a hub receives data packets it broadcasts them to all computers on that network including itself. It does not read the data packets. Hubs that amplify the signal are called active hubs and those that do not amplify the signal are passive hubs.

Switches A switch is more advanced than a hub. When hubs are used congestion may occur when several computers are transmitting data at the same time. The same packet of data is send to all the ports on the hub. In a switch the data from any computer is sent directly to its destination port without congesting the other ports unnecessarily. A switch uses address tables to find the correct port to send data packets. It stores the Media Access Control(MAC) address. It is used for connecting local computers and devices.

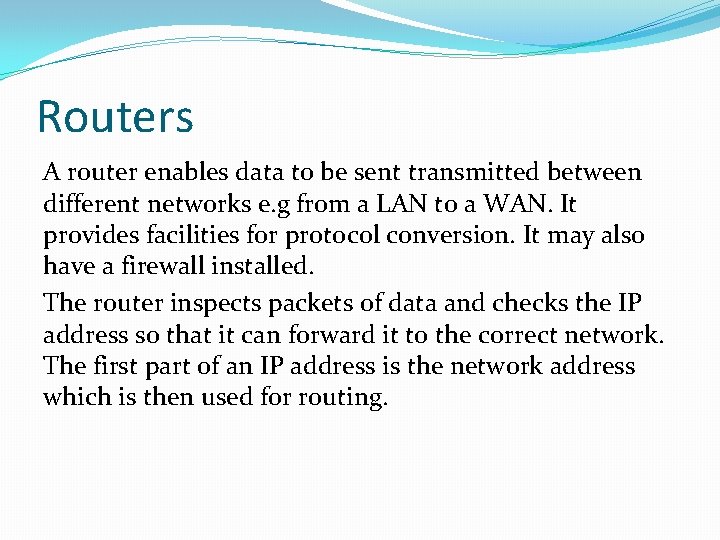
Routers A router enables data to be sent transmitted between different networks e. g from a LAN to a WAN. It provides facilities for protocol conversion. It may also have a firewall installed. The router inspects packets of data and checks the IP address so that it can forward it to the correct network. The first part of an IP address is the network address which is then used for routing.

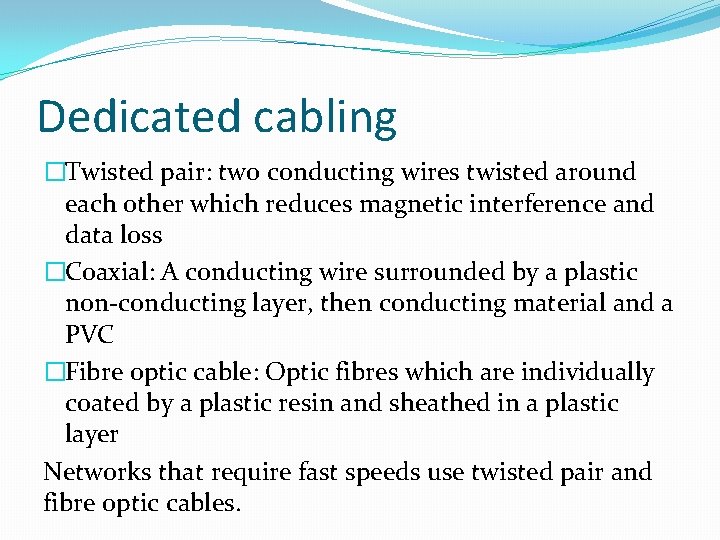
Dedicated cabling �Twisted pair: two conducting wires twisted around each other which reduces magnetic interference and data loss �Coaxial: A conducting wire surrounded by a plastic non-conducting layer, then conducting material and a PVC �Fibre optic cable: Optic fibres which are individually coated by a plastic resin and sheathed in a plastic layer Networks that require fast speeds use twisted pair and fibre optic cables.

Servers File Servers- Store user data. Users must log on to use the servers. Application Server-Distribute application software to client machines e. g the isams servers Other servers include print servers, e-mail servers, proxy servers etc One computer can be used as multiple servers. File servers make use of groups and access rights in order to manage security.

Network cards A network interface card is a card that fits onto a computer’s motherboard. A network interface card may allow both wired and wireless communication.

Network Types �Local Area Networks- These are house within a building or the same geographical area e. g schools, offices etc �The networks normally use switches/hubs �The switch is in turn connected to a broadband modem in order to connect to the internet.

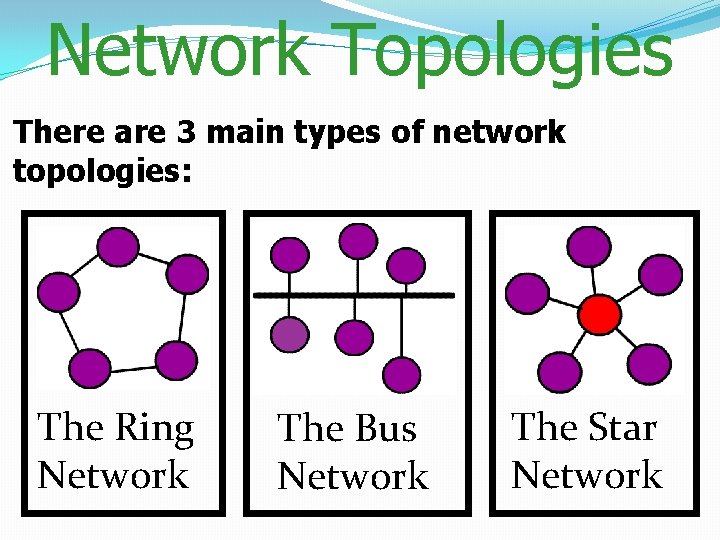
Network Topologies There are 3 main types of network topologies: The Ring Network The Bus Network The Star Network

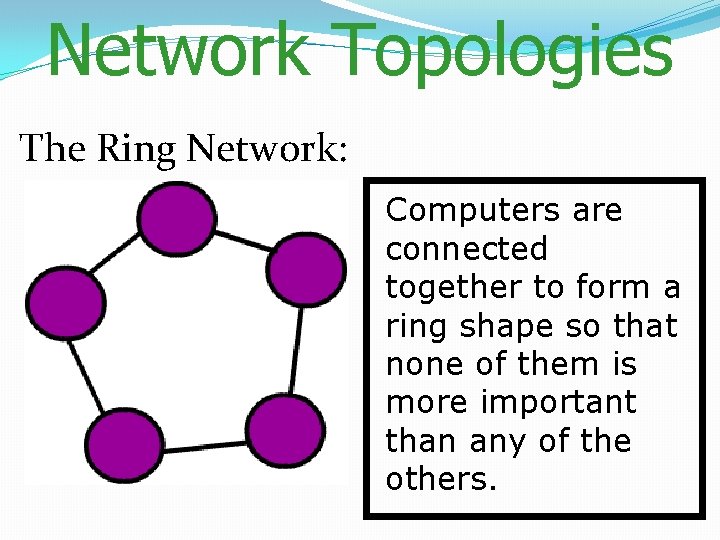
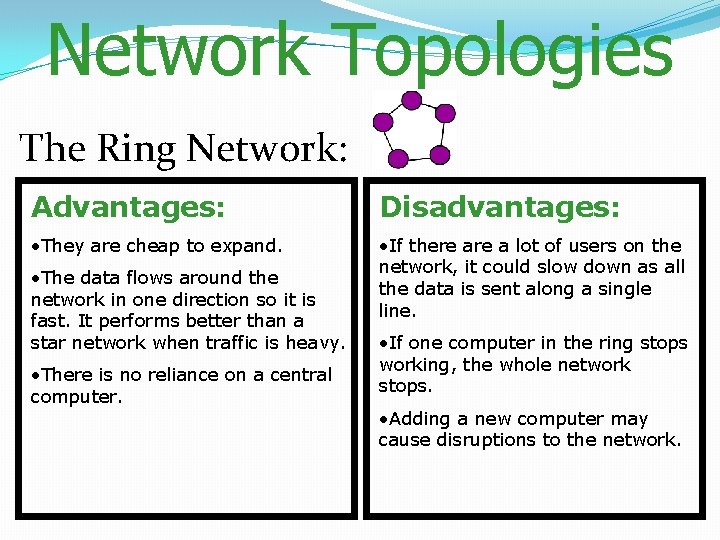
Network Topologies The Ring Network: Computers are connected together to form a ring shape so that none of them is more important than any of the others.

Network Topologies The Ring Network: Advantages: Disadvantages: • They are cheap to expand. • If there a lot of users on the network, it could slow down as all the data is sent along a single line. • The data flows around the network in one direction so it is fast. It performs better than a star network when traffic is heavy. • There is no reliance on a central computer. • If one computer in the ring stops working, the whole network stops. • Adding a new computer may cause disruptions to the network.

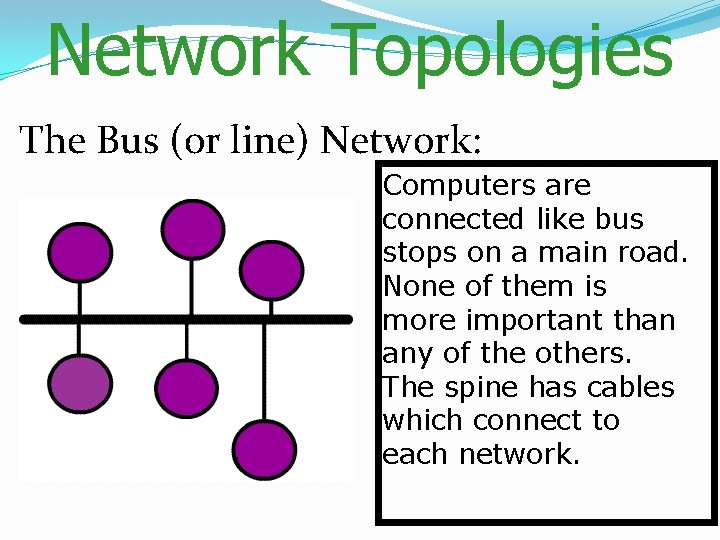
Network Topologies The Bus (or line) Network: Computers are connected like bus stops on a main road. None of them is more important than any of the others. The spine has cables which connect to each network.

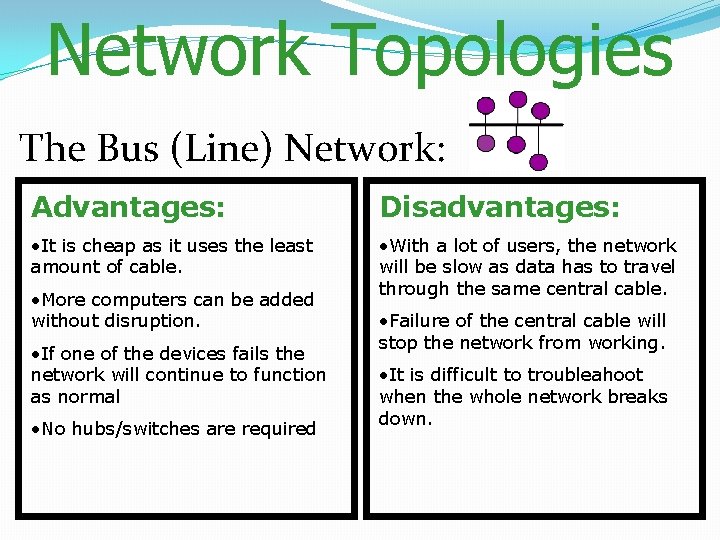
Network Topologies The Bus (Line) Network: Advantages: Disadvantages: • It is cheap as it uses the least amount of cable. • With a lot of users, the network will be slow as data has to travel through the same central cable. • More computers can be added without disruption. • If one of the devices fails the network will continue to function as normal • No hubs/switches are required • Failure of the central cable will stop the network from working. • It is difficult to troubleahoot when the whole network breaks down.

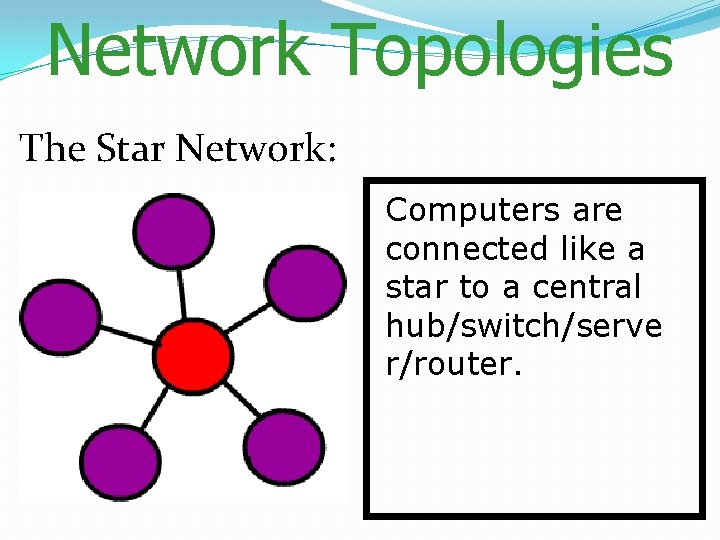
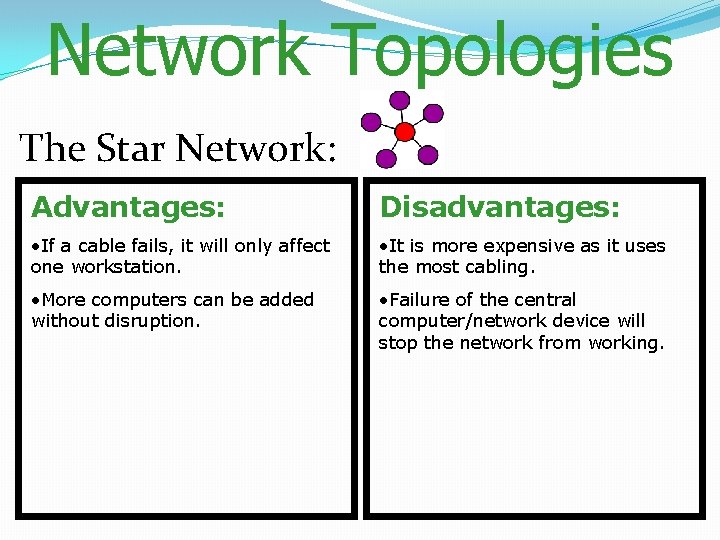
Network Topologies The Star Network: Computers are connected like a star to a central hub/switch/serve r/router.

Network Topologies The Star Network: Advantages: Disadvantages: • If a cable fails, it will only affect one workstation. • It is more expensive as it uses the most cabling. • More computers can be added without disruption. • Failure of the central computer/network device will stop the network from working.

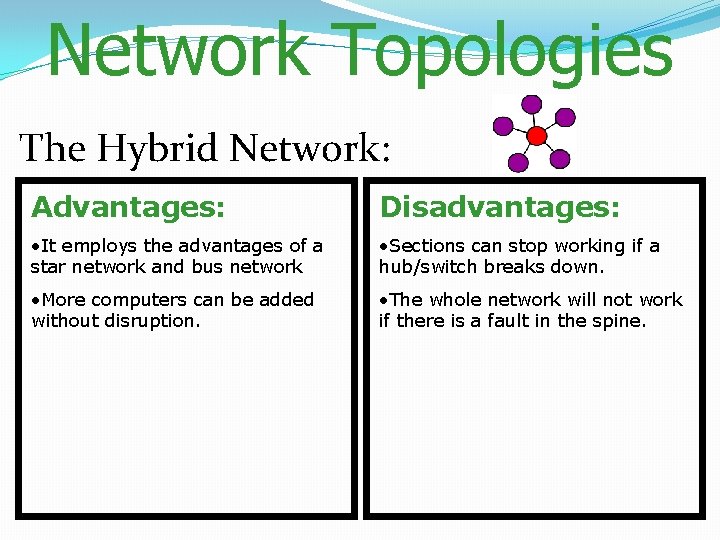
Hybrid Networks It is made up of star networks where each hub/switch is connected to one backbone. The backbone cable forms a bus-type network. The switches may also connect to each other forming multiple interconnected star networks.

Network Topologies The Hybrid Network: Advantages: Disadvantages: • It employs the advantages of a star network and bus network • Sections can stop working if a hub/switch breaks down. • More computers can be added without disruption. • The whole network will not work if there is a fault in the spine.

Intranets Local Area Networks are used for creating intranets. An intranet can be defined as a private company network that makes use of internet technology. It is for the use of members of that organisation. Users are given usernames and passwords Dedicated telecommunication links may also be used for linking different locations such as fibre optic cable and telephone lines. It uses internet protocols.

Uses of Intranets �Providing local e-mail �Video conferences �Sharing information �Fast access to documents and statistics �Sharing diaries �Organising meetings �Discussion forums �Policy information

Local e-mail and Business Networks �Intranets are very secure and businesses use them put up information that employees need to access. �Intranets reduce paper costs �Lan-based e-mail reduces the cost of printing �An ISP can be used for providing the e-mail service

WLANs A WLAN uses either spread spectrum( a signal with an initially low bandwidth is spread to have a wider bandwidth) radio waves or infrared signals for communication. Computers or devices must have WNICs Devices can be added easily to the network problems with the WLANs include security issues, interference and poor speeds

Wi-fi Wifi is short for wireless fidelity. Data is transmitted into radio signals and then transmitted. The wireless router decodes the signal. The following hardware devices are used: Wireless Network Cards Wireless Routers Wireless Access Points

Wireless Network Cards �It transmits data as radio waves. Most laptops a fitted with WNICs by manufacturers �Desktop computers can also have these fitted �Most mobile devices have wireless NICs

Wireless Router It converts data signals into radio signals as well as radio signals back to data signals. Features include: �Wifi protected access(WPA), a complexi encryption system �MAC address filtering and IP address filtering �Invisible mode

Wireless Access Points They are used for connecting wireless devices to a wired network. They cover a limited area and number of computers. List Devices that have wireless capabilities:

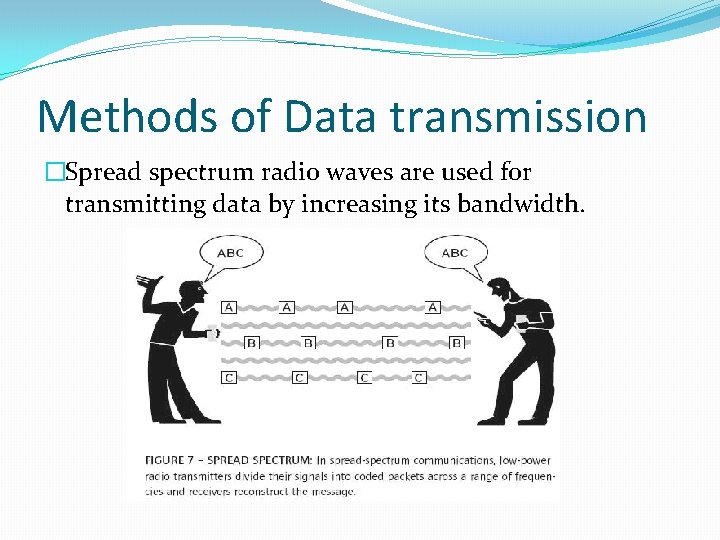
Methods of Data transmission �Spread spectrum radio waves are used for transmitting data by increasing its bandwidth.

Methods of Data transmission contd. The same random number generators are used by the receiver and sender to generate random frequencies and stay synchronised. It allows computers and other devices to communicate through walls. Another method is to use infrared signals. As it pulses on and off it willl be transmitting data in bits. It is secure because it cannot be used across walls. There is also no interference. The main disadvantage of the system is the lack of range.

WPAN �Pg 141 -143 Don’t have to do network security.

Network Security Network security is there to ensure that unauthorised users do not view data or understand it if they manage to intercept/access the data.

Physical Security This prevents users from gaining physical access to computers. This can be achieved by: -Securing Computer Rooms- All doors and windows should be locked when computers are not in use. Burglar alarms may also be used. Some Servers are lockable. CCTVs can also be used for deterring thieves. Pass cards can be used for giving users different times and levels of access. -Security Guards for patrolling and responding to alarms.

Software Security Most computer threats come from hackers who access computer systems remotely. The following methods may be used for preventing access: Firewall Encryption Digital Certification Authentication Techniques Anti-virus Software

Firewalls A firewall can be in the form of hardware or software or a combination of both. Firewalls prevent unwanted network traffic from accessing a computer network. Packets of data are inspected and if their ip address/network address is not wanted then they are prevented from accessing the computer network. Domains, words, phrases can be filtered out. Packets with these phrases are prevented from entering the system. At school we have a firewall that does this.

Encryption refers to encoding data by scrambling or encoding it. This is for preveting hackers from understanding data sfter intercepting it. The sending computer uses an encryption key for encoding data. The receiving computer has a decryption key for decoding it. Public key/Private key encryption is used. The sender computer uses the public key for encrypting data and the receiver will use a private key for decoding it.

Digital Certification Digital certificates are issued by a certification authority. The authority certifies that both receiving and sending computers are who they say they are. Once certified each one may get the public key of the other.

Authentication Techniques This can be achieved by using a for example a username and password, card and pin code, biometrics such as facial recognition and finger print scanners.

Anti-virus software It is used to find viruses and remove them. The anti-virus software has a database to remove known viruses. One way is to scan the hard disk or monitor ports for suspicious behaviour. Actions taken by viruses include the following: -Repair the files -Quarantine the file by not allowing any program to access it. -Delete the file Anti-virus software must be updated regularly. Antivirus definitions are becoming longer

Other Types Of Viruses �Trojan horses �Worms

User ID �These are used for identifying users and must match a password in the database. Users can also be grouped and be given privileges. �Users are given a limited number of attempts when logging in usually three attempts �Good password policies must be maintained such as ?

Chip and PIN cards �Chip and pin card readers are slotted into keyboards

Anti-spam �This is software for rejecting unsolicited e-mails

Anti-pop-up software Pop up blockers are usually incorporated into the browser. It identifies part of html code that will open another window and prevents it from being executed.

Anti-spyware software Spyware software allows people to access and control your computer. It allows pop ups, changes browser settings. In its worst form it searches for user names and passwords. Anti-spyware software searches the hard disk for known spyware software and removes it. It needs constant updating. Key logging software may also be used to detect the keys presssed.

Wired Equivalent Privacy of information(WEP) and Wi-fi Protected Access(WPA) �WEP is used for encrypting data on wireless networks but uses a weak key �WPA uses stronger encryption keys and also includes user authentication

Electronic conferencing Hardware Requirements Electronic conferencing requires additional hardware such as microphones, earphones/speakers, webcams including in some cases phone handsets.

Software Requirements �Conference Software �VOIP software �Instant messaging

Coference Software �Compression Decompression software is used to reduce the size of the packets of data transmitted. The packets of data must be transmitted in real time. �Echo cancellation software is used for keeping communication synchronised �VOIP software may also be used for conducting telephone conferences.

VOIP Software �It is cheaper than using conventional telephone lines. The software coverts the speech into digital data and compresses the audio data so that it can be transmitted in real time.

Instant Messaging It is the exchange of text messages across the internet in real time. Businesses and Institutions can also make use of IM on Local Area Networks.

Video Conferencing Advantages Meetings can be called at short notice No time spend on travelling No money spend on booking facilities It is environmentally friendly Meetings are kept shorter It is safer No payments for travelling time

Video Conferencing Disadvantages Confidential documents may need to be seen in their original form There is no direct eye contact Delegates may be put off by the camera Quality of the video depends on the bandwidth Transmission breakdowns may occur Environmental factors such as power cuts may also affect the video conference

Phone Conference Advantages Cheaper than a video conference because there are no webcams ot large screens Less bandwidth No need to worry about appearance

Phone Conference Disadvantages Documents cannot be seen Facial expressions cannot be seen Number of participants is limited Power cuts may interrup services

Instant messaging Advantages It is instant Saves time and money when resolving problems Easy to use

Instant messaging Disadvantages Users may be exposed to dangerous people It may lead to obescity It is disruprive in workplaces when used for socialising It may also pose a security risk when files are sent.

Uses Of Electronic Conferencing Businesses Schools Research Meetings