Firewalls Intrusion Detection Systems Communications Networking Computer Security
























- Slides: 46

Firewalls & Intrusion Detection Systems Communications, Networking & Computer Security Sanjay Goel University at Albany 1 *

Outline • Firewall – – • Definition Types Configuration Lab Exercise (Kerio Personal Firewall) IDS – Definition – Operation – Lab Exercises 2 *

Firewall What is a Firewall? • A firewall is any device used to prevent outsiders from gaining access to your network. • It checks each packet against a list of rules to permit or deny its transmission • Firewalls commonly implement exclusionary schemes or rules that sort out wanted and unwanted addresses. – They filter all traffic between a protected (“inside”) network and a less trustworthy (“outside”) network 3 *

Firewall Composition? • Firewalls can be composed of software, hardware, or, most commonly, both. – The software components can be either proprietary, shareware, or freeware. – The hardware is typically any hardware that supports the firewall software. 4 *

Firewall Design Goals • All traffic in both direction must pass through the firewall • Only authorized traffic should be allowed to pass • Firewall should itself be immune to penetration – Compromised firewall can completely undermine the network security • Tradeoff between security and productivity – Internal network could be completely secure, but employees may not be able to communicate 5 *

Firewall Types • There are different kinds of firewalls, and each type has its advantages & disadvantages. • Firewalls can be classified in two broad categories – Network Level Firewalls – Personal Firewalls 6 *

Firewall Network Level Firewalls • Network-level firewalls are usually router based. – Rules of who & what can access your network is applied at router level. • Scheme is applied through a technique called packet filtering • Network Level Firewalls can be classified as – Packet-Filtering Firewalls • The simplest and most effective type of firewalls – Stateful Inspection Firewalls • Maintain state info from a packet to another in the input stream – Application-Level Firewalls (Proxies) • Proxy server, a relay of application-level traffic 10/7/2020 7

Firewall Packet Filtering • Packet Filtering is the process of examining the packets that come to the router from the outside world. • Packet headers are inspected by a firewall or router to make a decision to block the packet or allow access • Two Approaches: – Stateless (a. k. a. static) – Stateful 8 *

Firewall Stateless Packet Filtering • Ignores the “state” of the connection • Each packet header is examined individually and compared to a “rule base” – Packet data is ignored • Common criteria to filter on: – Protocol Type – IP address – Port Number – Message Type 9 *

Firewall Stateful Packet Filtering • Maintains a record of the state of the connection (referred to as state table) • Packet is compared against both rule base and state table • Some stateful filters can examine both packet header and content • Called “stateful” because it permits outgoing sessions while denying incoming sessions 10 *

Firewall Application Gateway Firewall • When a remote user contacts a network running an application gateway, the gateway blocks the remote connection. • Instead of passing the connection along, the gateway examines various fields in the request. • If these meet a set of predefined rules, the gateway creates a bridge between the remote host and the internal host. 11 *

Firewall Access Policy • A list of rules describing which packets are to be forwarded • Each packet is compared against this list • The longer the list the greater the latency (delay) • Examples: – From any to any port 80 permit – From any to any PORT any deny – From *. albany. edu to any PORT any DENY 10/7/2020 12

Firewall Limitations • Firewalls are not a complete solution to all computer security problems, limitations: – The firewall cannot protect against attacks that bypass the firewall – The firewall does not protect against internal threats – The firewall cannot protect against the transfer of virus-infected programs or files 10/7/2020 13

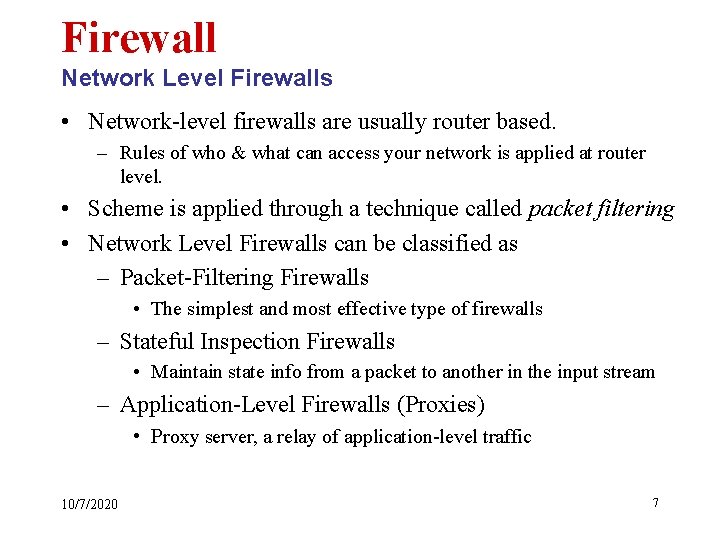
Firewall Configuration Strategies Screening Router • Simple • Filters traffic to internal computers • Provides minimal security Source: Guide To Firewalls and Network Security 14 *

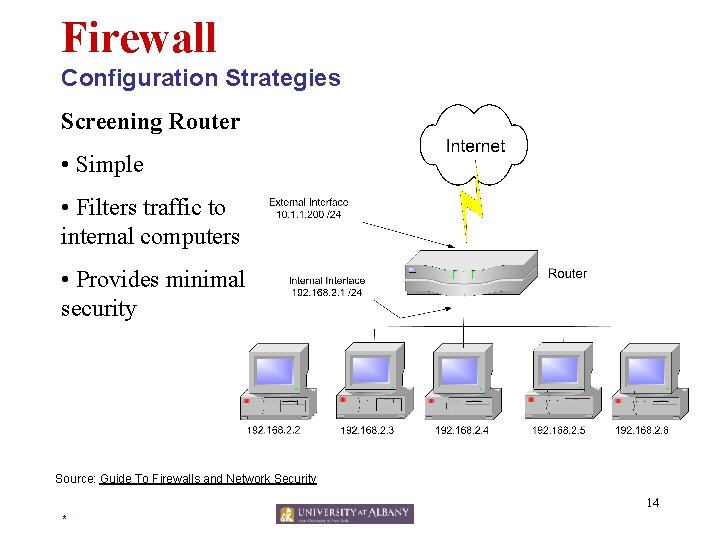
Firewall Configuration Strategies Screening Host • Host makes Internet request • Gateway receives client request and makes a request on behalf of the client • Host IP address never displayed to public Source: Guide To Firewalls and Network Security 15 *

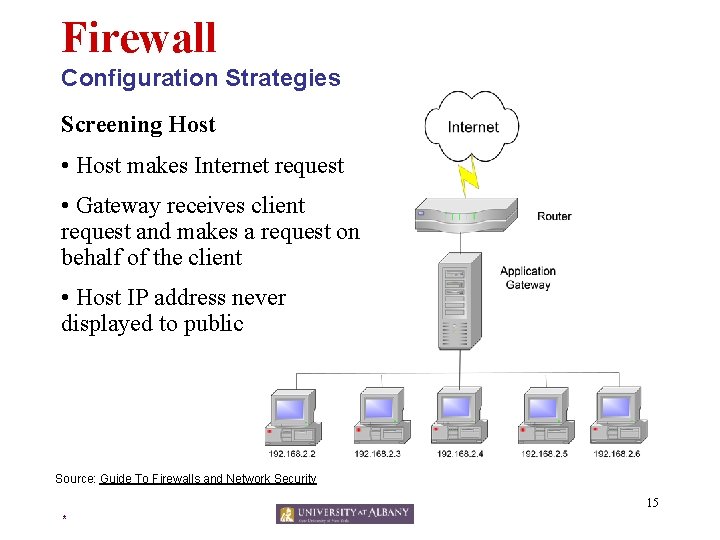
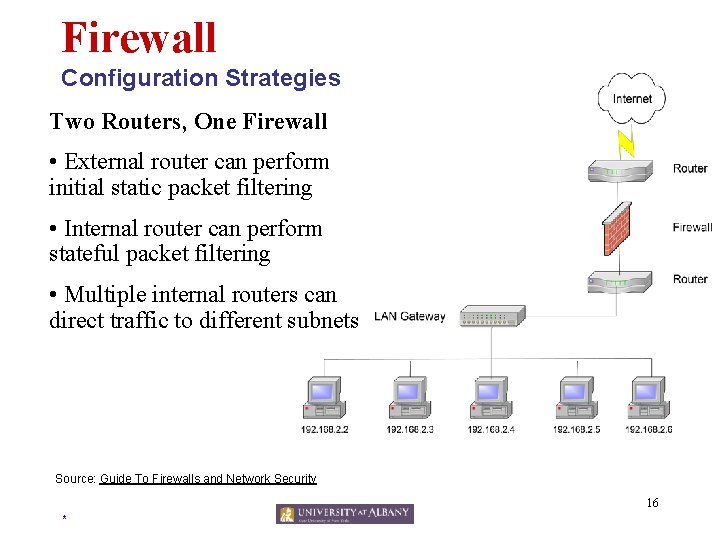
Firewall Configuration Strategies Two Routers, One Firewall • External router can perform initial static packet filtering • Internal router can perform stateful packet filtering • Multiple internal routers can direct traffic to different subnets Source: Guide To Firewalls and Network Security 16 *

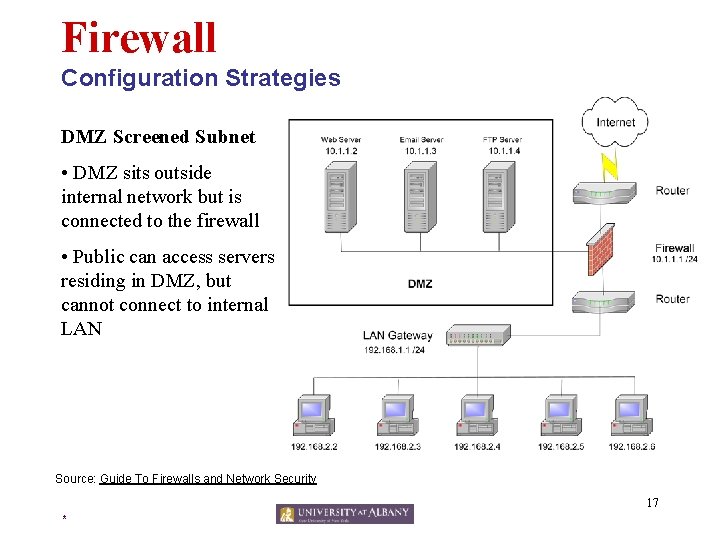
Firewall Configuration Strategies DMZ Screened Subnet • DMZ sits outside internal network but is connected to the firewall • Public can access servers residing in DMZ, but cannot connect to internal LAN Source: Guide To Firewalls and Network Security 17 *

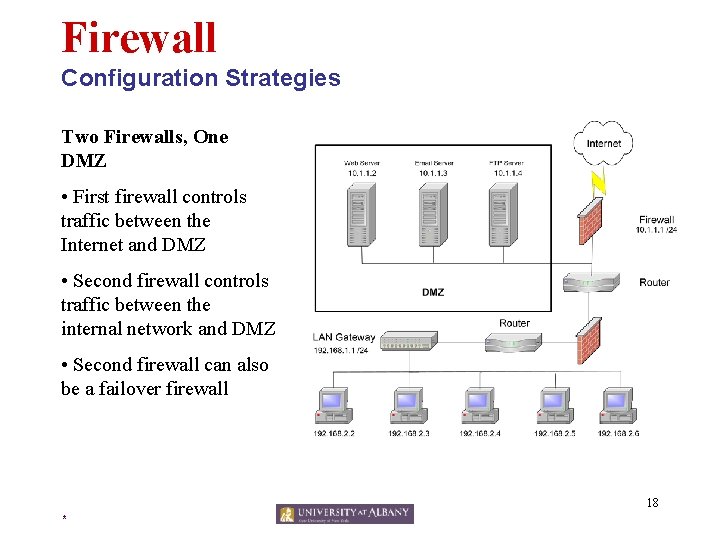
Firewall Configuration Strategies Two Firewalls, One DMZ • First firewall controls traffic between the Internet and DMZ • Second firewall controls traffic between the internal network and DMZ • Second firewall can also be a failover firewall 18 *

Firewall Kerio Personal Firewall (KPF) • What’s KPF? A software agent builds a barrier between PC and the Internet, to protect PC against hacker attacks and data leaks. • Why KPF? – KPF is designed to protect PC against attacks from both the Internet, and other computers in the local network. – KPF controls all data flow in both directions – from the Internet to your computer and vice versa – KPF can block all attempted communication allowing only what you choose to permit. 19 *

Lab Exercise Configure Kerio Personal Firewall 20 *

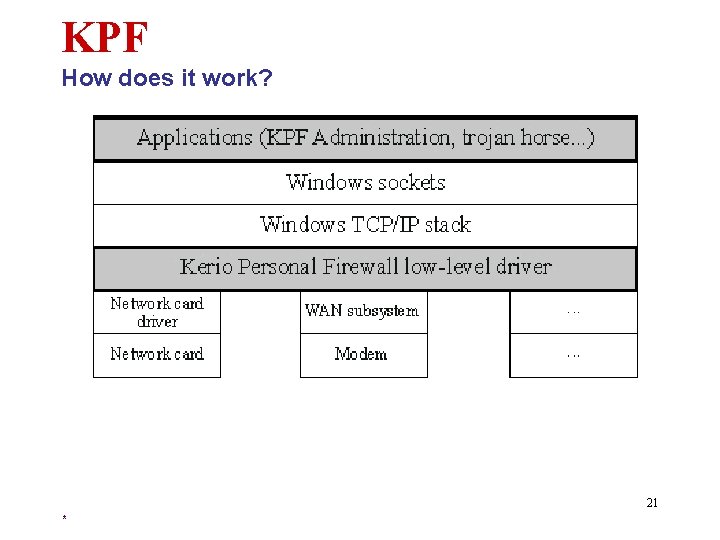
KPF How does it work? 21 *

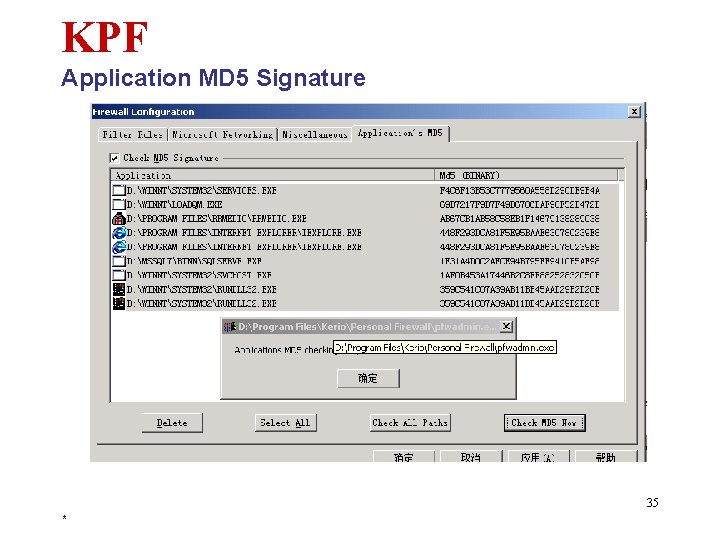
KPF Features • Blocks all externally originated IP traffic • Three security settings for easy configuration • MD 5 signature verification protects the computer from Trojan horses • Protecting from Denial of Service (DOS) attacks to applications or services • Connections dialog clearly displays each application's activity at any given moment 22 *

KPF Features Cont’d. • Availability (KPF version 4. 1. 3): – Available for trial for home use (limited free version) http: //www. kerio. com/kpf_download. html – Manual is available at the following site http: //download. kerio. com/dwn/kpf 41 -en-v 3. pdf – Business and institutional customers are encouraged to download this software for evaluation purposes. • Platform: – For Windows 98, Me, NT, 2000 and XP – (Win 95 not available any more) 23 *

KPF Installation • System requirements: • CPU Intel Pentium or 100% compatible • 64 MB RAM • 8 MB hard drive space (for installation only; at least 10 MB of additional space is recommended for logging) • Installation: • Executing the installation archive (kerio-pf-201 -en-win. exe) • Choose the directory KPF be installed, or leave the default setting (C: Program FilesKerioPersonal Firewall) • Restart system after installation in order for the low-lever driver to be loaded 24 *

KPF Configuration • Overview — list of active and open ports, statistics, user preferences. • Network Security — rules for network communication of individual applications, Packet filtering, trusted area definitions • System Security — rules for startup of individual applications • Intrusions — configuration of parameters which will be used for detection of known intrusion types • Web - web content rules (URL filter, pop-ups blocking, control over sent data) • Logs & Alters -- logs viewing and settings 25 *

KPF Firewall Engine • The Firewall Engine takes care of all KPF functions • It runs as a background application • It is represented by an icon in the System Tray • Right click the icon: – Stop All Traffic – Firewall Status – Administration 26 *

KPF Configuration Window 27 *

KPF Administration Test 28 *

KPF Status Window 29 *

KPF Security Settings • Level of Security: (KPF allows 3 security levels) – Permit Unknown: minimum security – Ask Me First: all communication is denied implicitly at this level – Deny Unknown: all communication is denied which is not explicitly permitted by the existing filter rules 30 *

KPF Security Settings Cont’d. • Test 31 *

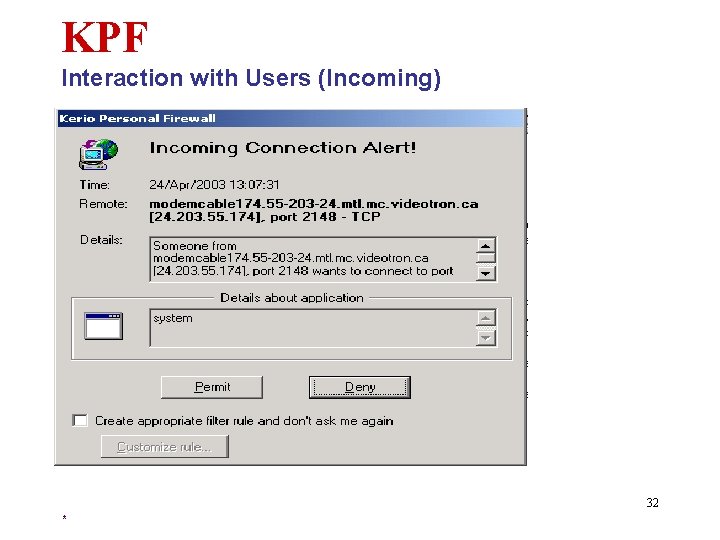
KPF Interaction with Users (Incoming) 32 *

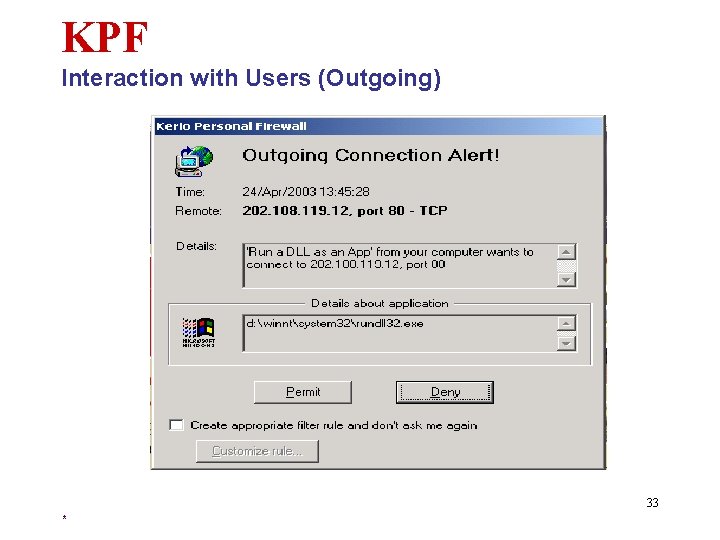
KPF Interaction with Users (Outgoing) 33 *

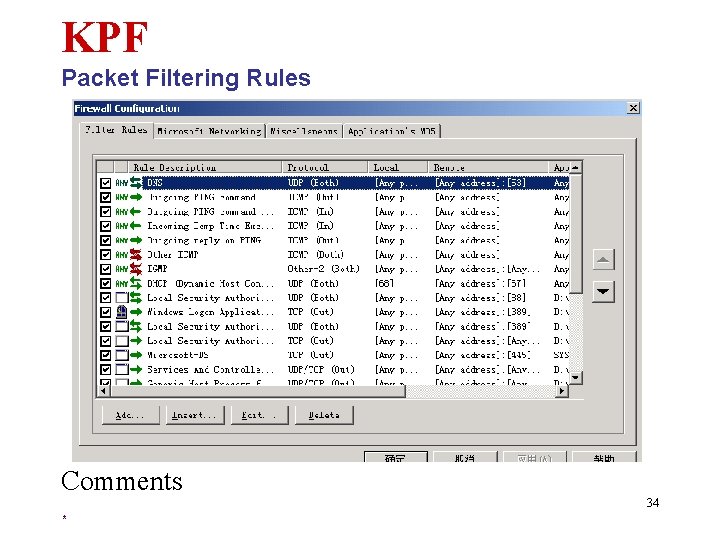
KPF Packet Filtering Rules Comments 34 *

KPF Application MD 5 Signature 35 *

KPF Filter. log File • The filter. log file is used for logging KPF actions on a local computer • Filter. log is a text file where each record is placed on a new line. It has the following format: – 1, [08/Jun/2001 16: 52: 09] Rule 'Internet Information Services': Blocked: In TCP, richard. kerio. cz [192. 168. 2. 38: 3772]->localhost: 25, Owner: G: WINNTSYSTEM 32INETSRVINETINFO. EXE • How to read this log file? 36 *

Intrusion Detection Systems 37 *

IDS What Does it Do? • An intrusion detection system (IDS) monitors systems and analyzes network traffic to detect signs of intrusion. • An IDS can detect a variety of attacks in progress as well as attempts to scan a network for weaknesses. • An IDS can be a dedicated network appliance or a software solution installed on a host computer. • Two kinds of IDS Systems – Client Based (On a single node) – Network Based (Protecting the entire network) 38 *

IDS How does it work? • If configured correctly, a network intrusion detection system (NIDS) can monitor all traffic on a network segment. • A NIDS is most effective when used in conjunction with a firewall solution, and having all of its dependent components being properly connected and functioning. 39 *

IDS Configuration • NIDS can be installed on the external routers, the internal routers, or both. • Placing NIDS on external routers enables detection of attacks from the Internet • Placing NIDS on internal routers enables detection of internal hosts attempting to access the Internet on suspicious ports. 40 *

IDS Methods of Detection • A NIDS/IDS mainly use anomaly or pattern detection to identify an intrusion or intrusion attempt. • An anomaly example: This involves monitoring resource use, network traffic, user behavior and comparing it against normal levels. • If a user that normally only accesses the system between 9 am – 5 pm, suddenly logs on at 3 am then this may indicate that an intruder has compromised the user’s account. A NIDS/IDS would then alert administrators to this suspicious activity. • A NIDS/IDS can detect hacker attempts to scan your network for intelligence gathering purposes. 41 *

IDS Network Packet Checking • Sits On Network location and “checks” packets that travel across the network. • If a packet contains a certain “footprint”, then it triggers an alert • Audit logs are generated and kept as records of alerts. 42 *

IDS Commonly Used IDS Systems (Windows) • ISS Internet Security Systems (Black Ice Guardian) – Used by individuals and small business networks. – Looks for common algorithms concealed or “wrapped” in wrappers i. e. TCP Wrapper. – Can be configured as an IDS and a Firewall. – Can track unauthorized traffic and block the ports the intruding script/software is using. 43 *

IDS Vendor Firewalls & Versions (Hardware Based) • • Axent: Raptor v 6. 5 Checkpoint: FW 1 v 4. 1 Cisco: PIX v 525 MS: Proxy v 2. 0 44 *

Zone Alarm Pro! View Demo 45 *

Firewalls & IDS Contributors • Edward Zhang • Michael La. Barge • Christopher Brown 46 *