Intrusion Detection Firewalls and Intrusion Prevention CIS 4361


































- Slides: 52

Intrusion Detection, Firewalls, and Intrusion Prevention CIS 4361 Eng. Hector M Lugo-Cordero, MS April 2012

Most Slides are From Computer Security: Principles and Practice Chapter 6 – Intrusion Detection First Edition by William Stallings and Lawrie Brown Lecture slides by Lawrie Brown

Intruders Ø significant issue hostile/unwanted trespass l from benign to serious Ø user trespass l unauthorized logon, privilege abuse Ø software trespass l virus, worm, or trojan horse Ø classes of intruders: l masquerader, misfeasor, clandestine user

Examples of Intrusion remote root compromise Ø web server defacement Ø guessing / cracking passwords Ø copying viewing sensitive data / databases Ø running a packet sniffer Ø distributing pirated software Ø using an unsecured modem to access net Ø impersonating a user to reset password Ø using an unattended workstation Ø

Security Intrusion & Detection Security Intrusion a security event, or combination of multiple security events, that constitutes a security incident in which an intruder gains, or attempts to gain, access to a system (or system resource) without having authorization to do so. Intrusion Detection a security service that monitors and analyzes system events for the purpose of finding, and providing realtime or near real-time warning of attempts to access system resources in an unauthorized manner.

Intrusion Techniques Ø objective to gain access or increase privileges Ø initial attacks often exploit system or software vulnerabilities to execute code to get backdoor l e. g. buffer overflow Ø or to gain protected information l e. g. password guessing or acquisition

Hackers Ø motivated by thrill of access and status l l Ø hacking community a strong meritocracy status is determined by level of competence benign intruders might be tolerable l l do consume resources and may slow performance can’t know in advance whether benign or malign IDS / IPS / VPNs can help counter Ø awareness led to establishment of CERTs Ø l collect / disseminate vulnerability info / responses

Hacker Behavior Example 1. 2. 3. 4. 5. 6. 7. select target using IP lookup tools map network for accessible services identify potentially vulnerable services brute force (guess) passwords install remote administration tool wait for admin to log on and capture password use password to access remainder of network

Criminal Enterprise Ø organized groups of hackers now a threat l l corporation / government / loosely affiliated gangs typically young often Eastern European or Russian hackers common target credit cards on e-commerce server Ø criminal hackers usually have specific targets Ø once penetrated act quickly and get out Ø IDS / IPS help but less effective Ø sensitive data needs strong protection

Criminal Enterprise Behavior 1. 2. 3. 4. 5. 6. act quickly and precisely to make their activities harder to detect exploit perimeter via vulnerable ports use trojan horses (hidden software) to leave back doors for re-entry use sniffers to capture passwords do not stick around until noticed make few or no mistakes.

Insider Attacks among most difficult to detect and prevent Ø employees have access & systems knowledge Ø may be motivated by revenge / entitlement Ø l l Ø when employment terminated taking customer data when move to competitor IDS / IPS may help but also need: l least privilege, monitor logs, strong authentication, termination process to block access & mirror data

Insider Behavior Example 1. 2. 3. 4. 5. 6. 7. create network accounts for themselves and their friends access accounts and applications they wouldn't normally use for their daily jobs e-mail former and prospective employers conduct furtive instant-messaging chats visit web sites that cater to disgruntled employees, such as f'dcompany. com perform large downloads and file copying access the network during off hours.

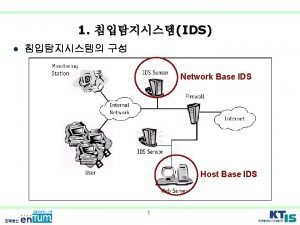
Intrusion Detection Systems Ø classify intrusion detection systems (IDSs) as: l l Host-based IDS: monitor single host activity Network-based IDS: monitor network traffic Ø logical components: l l l sensors - collect data analyzers - determine if intrusion has occurred user interface - manage / direct / view IDS

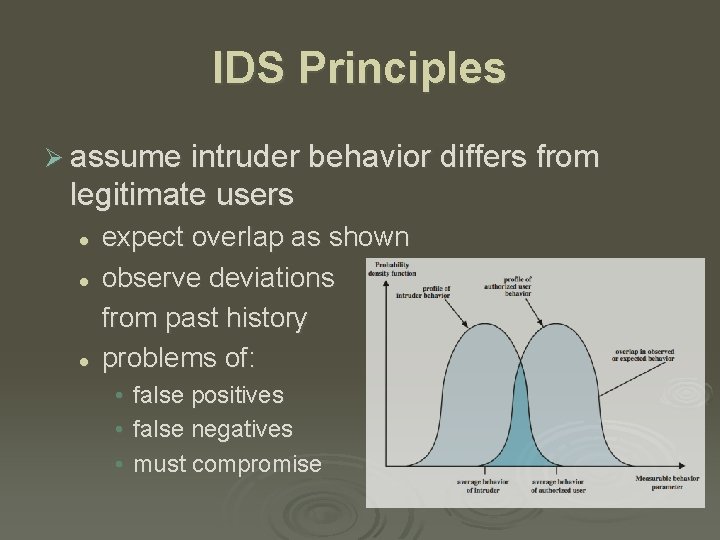
IDS Principles Ø assume intruder behavior differs from legitimate users l l l expect overlap as shown observe deviations from past history problems of: • • • false positives false negatives must compromise

IDS Requirements run continually Ø be fault tolerant Ø resist subversion Ø impose a minimal overhead on system Ø configured according to system security policies Ø adapt to changes in systems and users Ø scale to monitor large numbers of systems Ø provide graceful degradation of service Ø allow dynamic reconfiguration Ø

Host-Based IDS Ø specialized software to monitor system activity to detect suspicious behavior l l Ø primary purpose is to detect intrusions, log suspicious events, and send alerts can detect both external and internal intrusions two approaches, often used in combination: l anomaly detection - defines normal/expected behavior • threshold detection • profile based l signature detection - defines proper behavior

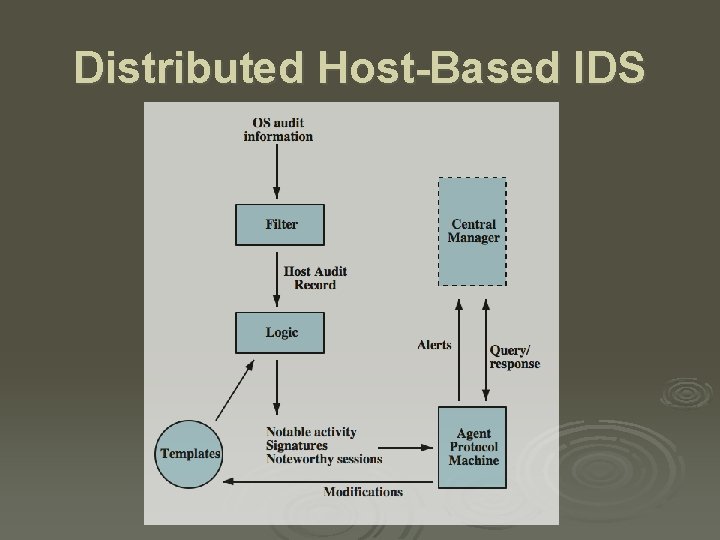
Audit Records Ø a fundamental tool for intrusion detection Ø two variants: l native audit records - provided by O/S • always available but may not be optimum l detection-specific audit records - IDS specific • additional overhead but specific to IDS task • often log individual elementary actions • e. g. may contain fields for: subject, action, object, exception-condition, resource-usage, time-stamp

Example of Audit Consider copy. exe game. exe <system>/game. exe Ø Several records may be generated for a single command Ø 1. 2. 3. Execute copy. exe Read game. exe Write <system>/game. exe

Anomaly Detection Ø threshold detection l l l Ø checks excessive event occurrences over time alone a crude and ineffective intruder detector must determine both thresholds and time intervals profile based l l l characterize past behavior of users / groups then detect significant deviations based on analysis of audit records • gather metrics: counter, guage, interval timer, resource utilization • analyze: mean and standard deviation, multivariate, markov process, time series, operational model

Examples of Anomaly

Examples of Anomaly

Signature Detection Ø observe events on system and applying a set of rules to decide if intruder Ø approaches: l rule-based anomaly detection • analyze historical audit records for expected behavior, then match with current behavior l rule-based penetration identification • • • rules identify known penetrations / weaknesses often by analyzing attack scripts from Internet supplemented with rules from security experts

Example of Signatures Users should not read files in other users’ personal directories Ø Users must not write other users’ files Ø Users who log in after hours often access the same files they user earlier Ø Users do not generally open disk devices but rely on higher-level operating system utilities Ø Users should not be logged in more than once to the system Ø Users do not make copies of system program Ø

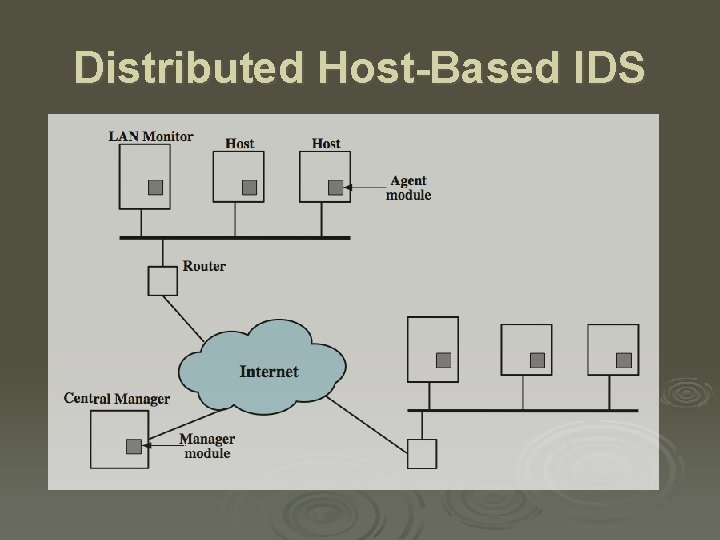
Distributed Host-Based IDS

Distributed Host-Based IDS

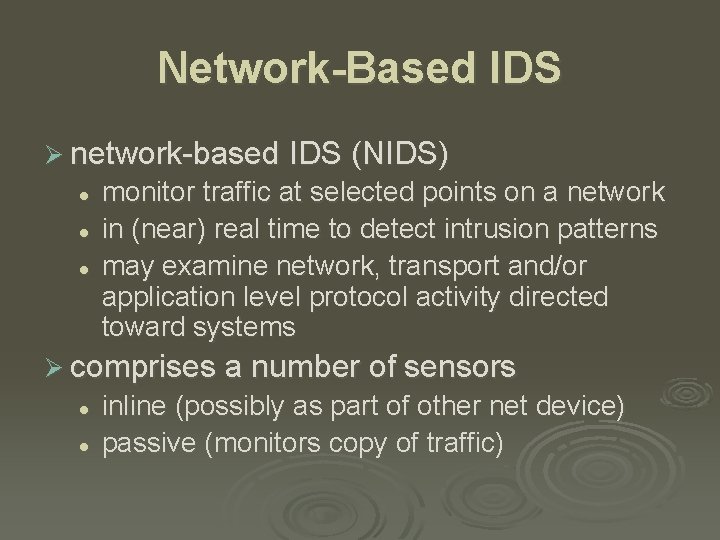
Network-Based IDS Ø network-based IDS (NIDS) l l l monitor traffic at selected points on a network in (near) real time to detect intrusion patterns may examine network, transport and/or application level protocol activity directed toward systems Ø comprises a number of sensors l l inline (possibly as part of other net device) passive (monitors copy of traffic)

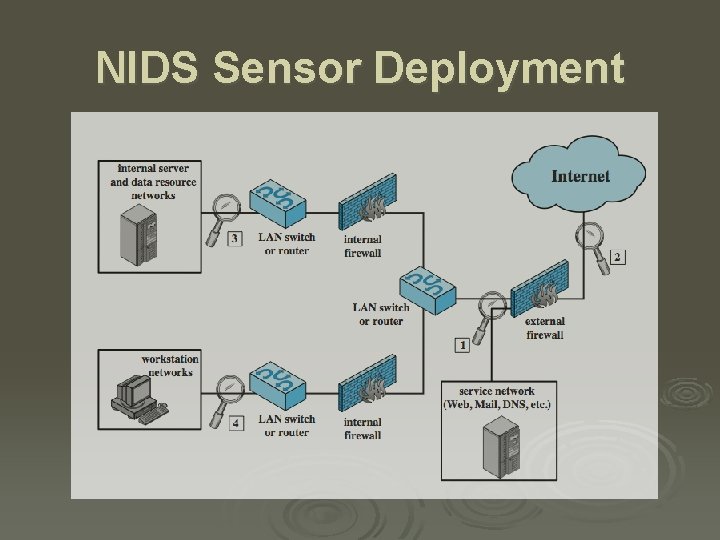
NIDS Sensor Deployment

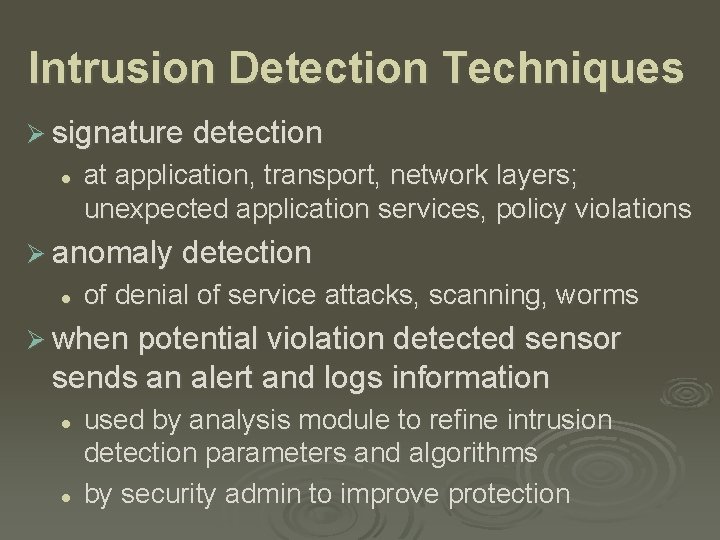
Intrusion Detection Techniques Ø signature detection l at application, transport, network layers; unexpected application services, policy violations Ø anomaly detection l of denial of service attacks, scanning, worms Ø when potential violation detected sensor sends an alert and logs information l l used by analysis module to refine intrusion detection parameters and algorithms by security admin to improve protection

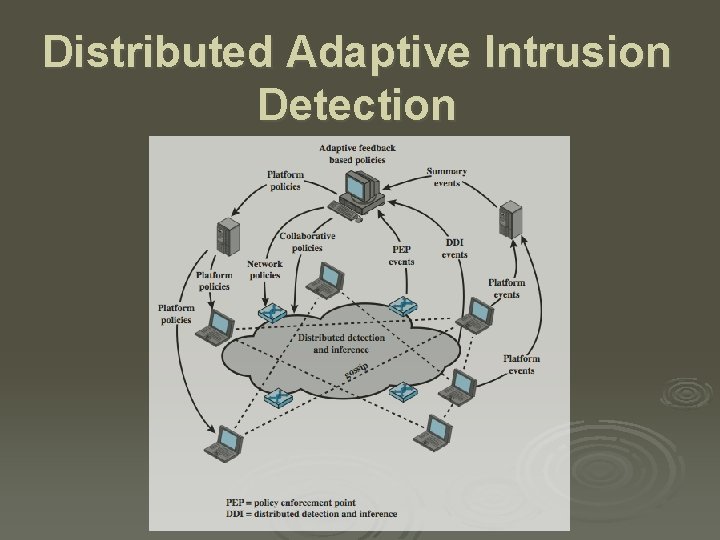
Distributed Adaptive Intrusion Detection

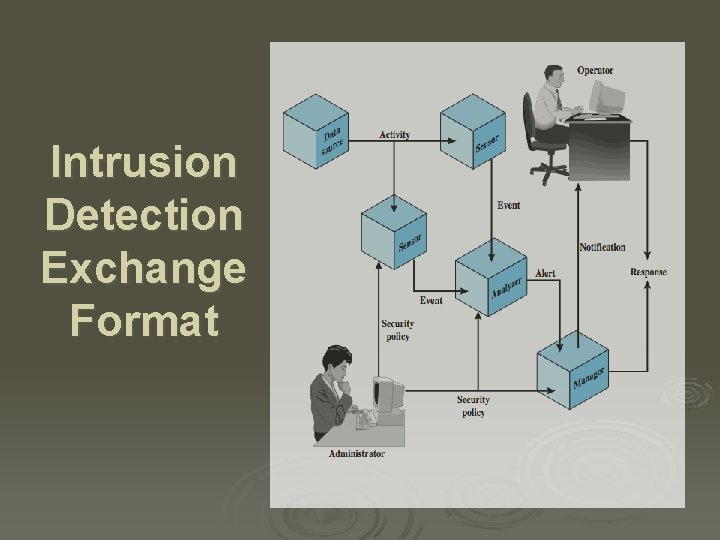
Intrusion Detection Exchange Format

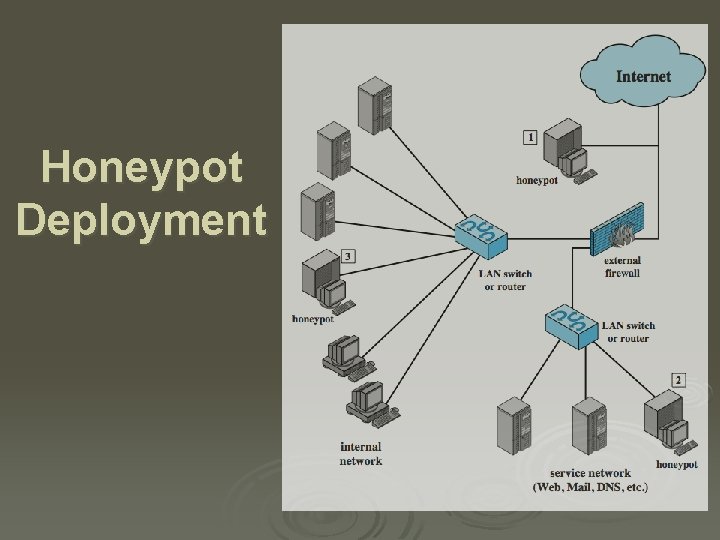
Honeypots Ø are decoy systems l l filled with fabricated info instrumented with monitors / event loggers divert and hold attacker to collect activity info without exposing production systems Ø initially were single systems Ø more recently are/emulate entire networks

Honeypot Deployment

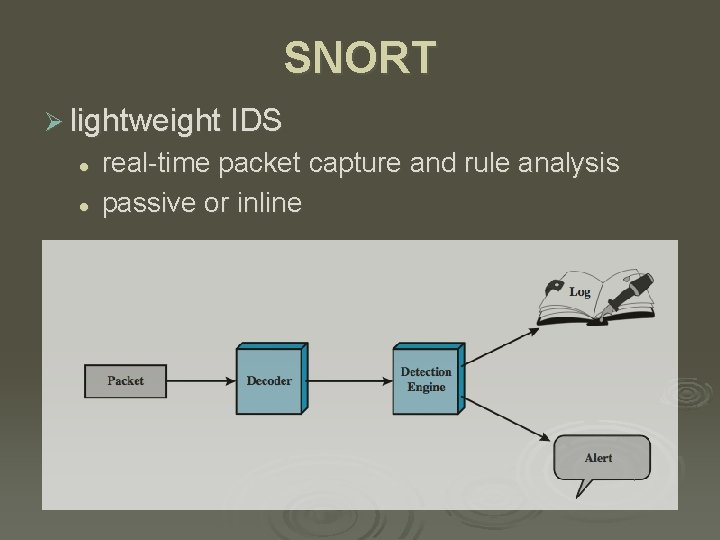
SNORT Ø lightweight IDS l l real-time packet capture and rule analysis passive or inline

SNORT Rules use a simple, flexible rule definition language Ø with fixed header and zero or more options Ø header includes: action, protocol, source IP, source port, direction, dest IP, dest port Ø many options Ø example rule to detect TCP SYN-FIN attack: Ø Alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg: "SCAN SYN FIN"; flags: SF, 12; reference: arachnids, 198; classtype: attempted-recon; )

Summary Ø introduced intruders & intrusion detection l Ø hackers, criminals, insiders intrusion detection approaches l l host-based (single and distributed) network distributed adaptive exchange format honeypots Ø SNORT example Ø

Most Slides are From Computer Security: Principles and Practice Chapter 9 – Firewalls and Intrusion Prevention Systems First Edition by William Stallings and Lawrie Brown Lecture slides by Lawrie Brown

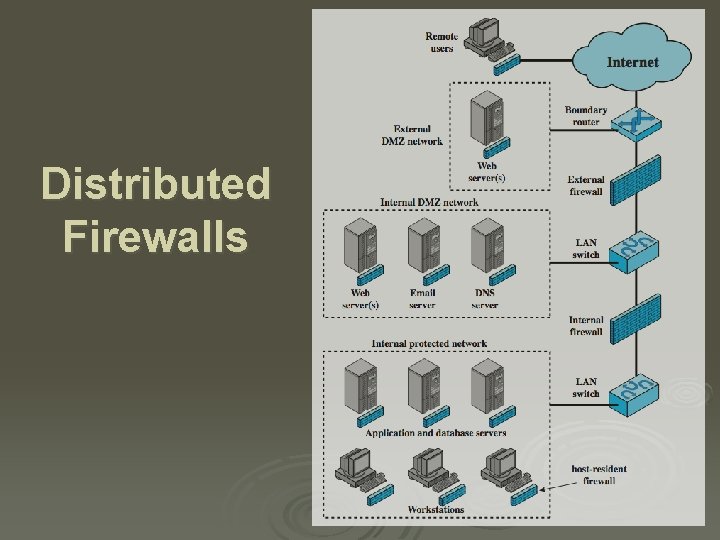
Firewall Capabilities & Limits Ø capabilities: l l l Ø defines a single choke point provides a location for monitoring security events convenient platform for some Internet functions such as NAT, usage monitoring, IPSEC VPNs limitations: l l cannot protect against attacks bypassing firewall may not protect fully against internal threats improperly secure wireless LAN laptop, PDA, portable storage device infected outside then used inside

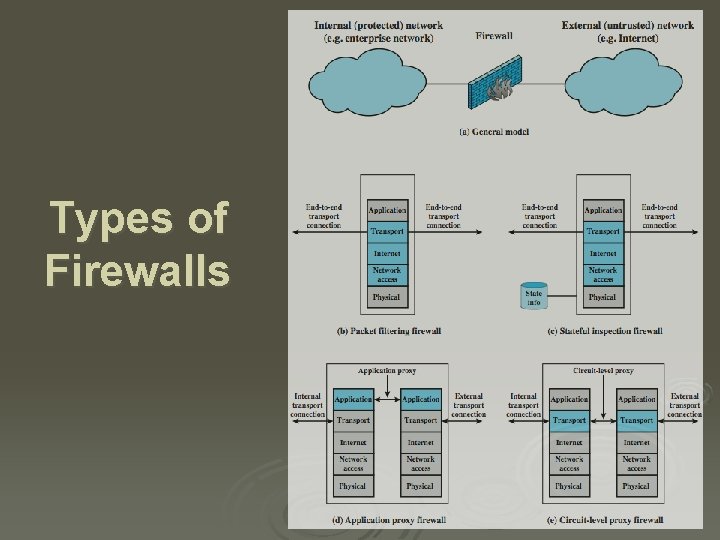
Types of Firewalls

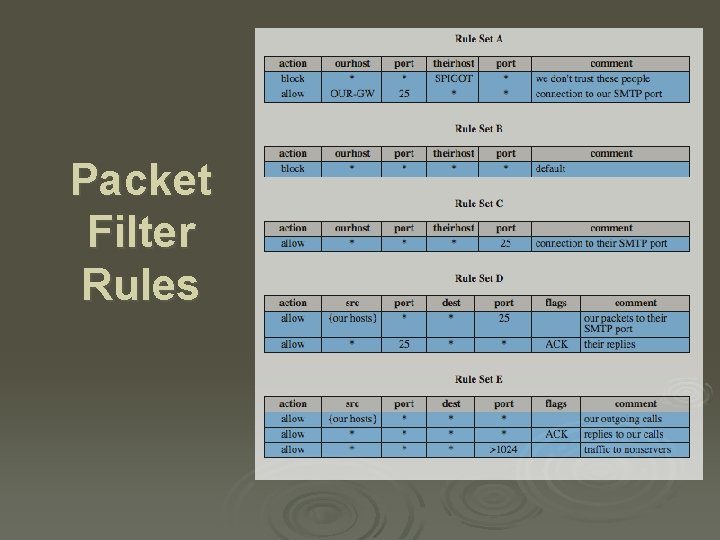
Packet Filtering Firewall Ø applies rules to packets in/out of firewall Ø based on information in packet header l src/dest IP addr & port, IP protocol, interface Ø typically a list of rules of matches on fields l if match rule says if forward or discard packet Ø two default policies: l discard - prohibit unless expressly permitted • more conservative, controlled, visible to users l forward - permit unless expressly prohibited • easier to manage/use but less secure

Packet Filter Rules

Packet Filter Weaknesses Ø weaknesses l l l cannot prevent attack on application bugs limited logging functionality do no support advanced user authentication vulnerable to attacks on TCP/IP protocol bugs improper configuration can lead to breaches Ø attacks l IP address spoofing, source route attacks, tiny fragment attacks

Stateful Inspection Firewall Ø reviews packet header information but also keeps info on TCP connections l l l typically have low, “known” port no for server and high, dynamically assigned client port no simple packet filter must allow all return high port numbered packets back in stateful inspection packet firewall tightens rules for TCP traffic using a directory of TCP connections only allow incoming traffic to high-numbered ports for packets matching an entry in this directory may also track TCP seq numbers as well

Application-Level Gateway Ø acts as a relay of application-level traffic l l l user contacts gateway with remote host name authenticates themselves gateway contacts application on remote host and relays TCP segments between server and user Ø must have proxy code for each application l may restrict application features supported Ø more secure than packet filters Ø but have higher overheads

Circuit-Level Gateway Ø sets up two TCP connections, to an inside user and to an outside host Ø relays TCP segments from one connection to the other without examining contents l l hence independent of application logic just determines whether relay is permitted Ø typically used when inside users trusted l l may use application-level gateway inbound and circuit-level gateway outbound hence lower overheads

Examples of Firewalls Ø Windows Defender (Application level) Ø IP Tables (Packet level) Ø SOCKS (circuit-level) Ø MAC OS X personal firewall Ø SNORT?

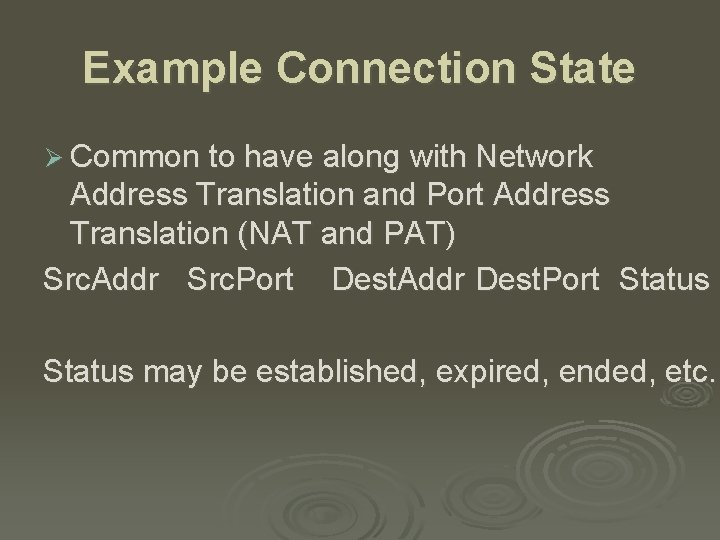
Example Connection State Ø Common to have along with Network Address Translation and Port Address Translation (NAT and PAT) Src. Addr Src. Port Dest. Addr Dest. Port Status may be established, expired, ended, etc.

Distributed Firewalls

Intrusion Prevention Systems (IPS) Ø recent addition to security products which l l inline net/host-based IDS that can block traffic functional addition to firewall that adds IDS capabilities Ø can block traffic like a firewall Ø using IDS algorithms Ø may be network or host based

Host-Based IPS Ø identifies attacks l using both: signature techniques • malicious application packets l anomaly detection techniques • behavior patterns that indicate malware Ø can be tailored to the specific platform l e. g. general purpose, web/database server specific Ø can also sandbox applets to monitor behavior Ø may give desktop file, registry, I/O protection

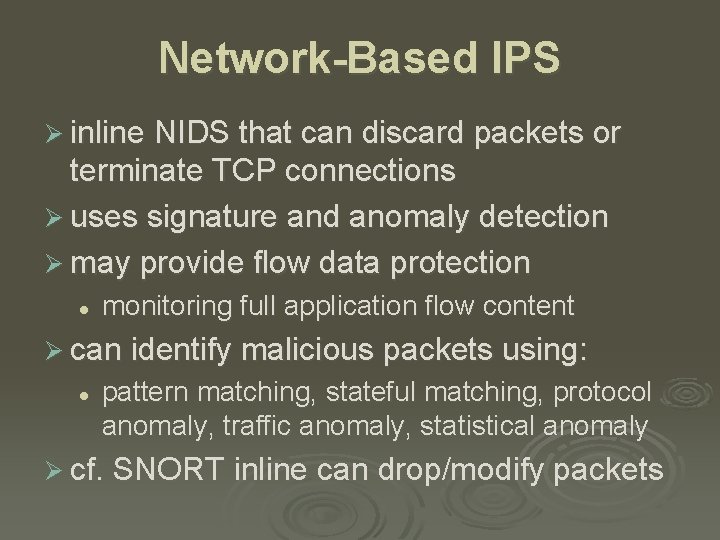
Network-Based IPS Ø inline NIDS that can discard packets or terminate TCP connections Ø uses signature and anomaly detection Ø may provide flow data protection l monitoring full application flow content Ø can identify malicious packets using: l pattern matching, stateful matching, protocol anomaly, traffic anomaly, statistical anomaly Ø cf. SNORT inline can drop/modify packets

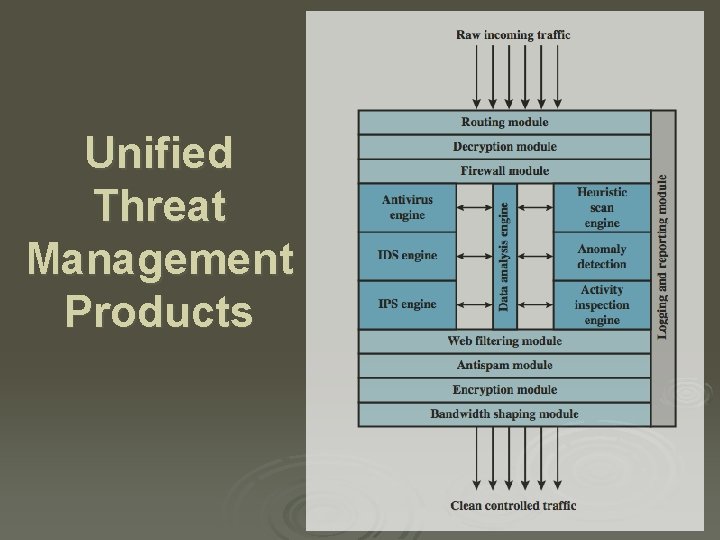
Unified Threat Management Products

Summary Ø introduced need for & purpose of firewalls Ø types of firewalls l packet filter, stateful inspection, application and circuit gateways Ø firewall hosting, locations, topologies Ø intrusion prevention systems
 Firewalls and intrusion detection systems
Firewalls and intrusion detection systems Cis 4361
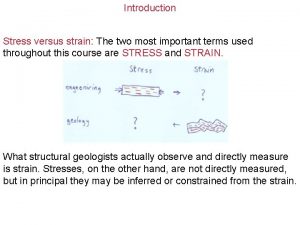
Cis 4361 Primary prevention secondary prevention tertiary prevention
Primary prevention secondary prevention tertiary prevention Intrusion detection system open source
Intrusion detection system open source Common intrusion detection framework
Common intrusion detection framework L
L Bro ids
Bro ids Fiber perimeter intrusion detection systems
Fiber perimeter intrusion detection systems Infrasonic intrusion detection
Infrasonic intrusion detection Datenkorrelation
Datenkorrelation Configure ios intrusion prevention system (ips) using cli
Configure ios intrusion prevention system (ips) using cli Ips intrusion
Ips intrusion Starvation deadlock
Starvation deadlock Deadlock prevention avoidance and detection
Deadlock prevention avoidance and detection Auditing firewalls
Auditing firewalls History of firewalls
History of firewalls Introduction of firewall
Introduction of firewall What are the two main types of firewall
What are the two main types of firewall Single homed bastion host
Single homed bastion host Linux firewalls
Linux firewalls Firewalls are used for what security principle
Firewalls are used for what security principle Firewall open source
Firewall open source Types of firewalls ppt
Types of firewalls ppt Dynamic firewalls
Dynamic firewalls Perimeter firewalls are the simplest type of firewall
Perimeter firewalls are the simplest type of firewall Firewalls computer science
Firewalls computer science Linux firewalls
Linux firewalls Kernel intrusion
Kernel intrusion What is intrusion? *
What is intrusion? * Intrusión dental definicion
Intrusión dental definicion Magmatic intrusion
Magmatic intrusion Giac certified intrusion analyst
Giac certified intrusion analyst Intrusion fantasy examples
Intrusion fantasy examples Intrusion.win.iis.unicode.a.exploit
Intrusion.win.iis.unicode.a.exploit Skewards
Skewards Intrusion budget
Intrusion budget Authorial intrusion definition
Authorial intrusion definition Intrusion movie
Intrusion movie Intrusion movie
Intrusion movie Risitic layering
Risitic layering Pearson
Pearson Detecting golden ticket attack
Detecting golden ticket attack Intrusion tolerance
Intrusion tolerance Analysis console for intrusion databases
Analysis console for intrusion databases Nonsuperposable
Nonsuperposable Dextrorotatory and levorotatory
Dextrorotatory and levorotatory Alkene structural formula
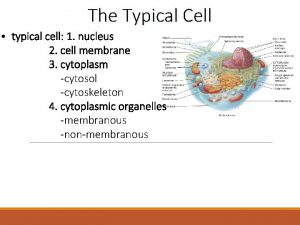
Alkene structural formula Phospholipid bilayer
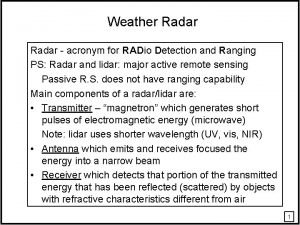
Phospholipid bilayer Radar is an acronym for radio detection and
Radar is an acronym for radio detection and Error detection and correction in computer networks
Error detection and correction in computer networks Hazard detection and resolution
Hazard detection and resolution Hazard detection and resolution
Hazard detection and resolution Deadlock detection and recovery
Deadlock detection and recovery