Intrusion Protection Mark Shtern Protection systems Firewalls Intrusion

















- Slides: 27

Intrusion Protection Mark Shtern

Protection systems • • Firewalls Intrusion detection and protection systems Honeypots System Auditing

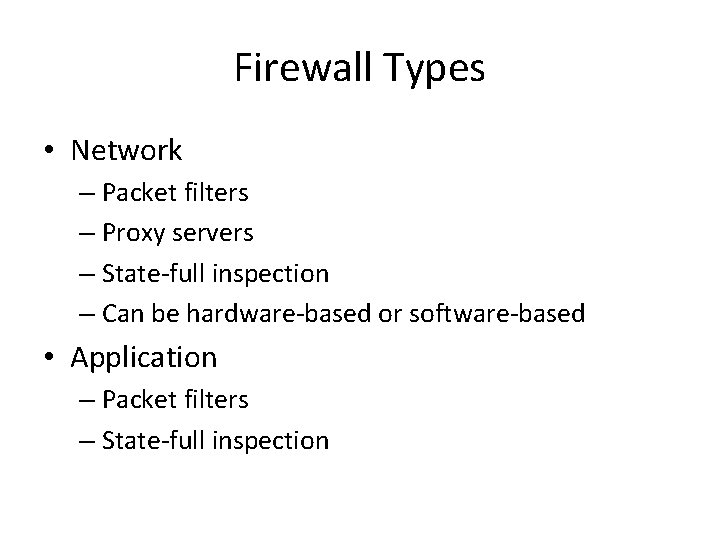
Firewall Types • Network – Packet filters – Proxy servers – State-full inspection – Can be hardware-based or software-based • Application – Packet filters – State-full inspection

Packet filtering Firewalls • Permits or denies packets based on socket pairs • Packet filters operate at layer 4 of the OSI model • Defined packet filters are applied to examine traffic attempting to enter or attempting to exit an interface • Packet filters do not maintain state

Proxy Server Firewalls • Clients configured to use a proxy server package • The proxy server completes client requests on behalf of the requesting clients, if permitted

Proxy Server Types • Circuit-level proxy servers only understand the socket portion of a request (IP address, port number, and protocol) • Application-level proxy servers also understand the internal commands for each type of application – for example, can recognize FTP commands for PUT, GET, MPUT, MGET, and so on

State-full Inspection Firewalls • Generally permits all outbound sessions initiated by internal clients (unless an ACL imposes restrictions) – a state table entry is created for each allowed connection • Allows return traffic belonging to the same session • Generally denies all inbound sessions initiated by external clients (unless an ACL allows exceptions) – a state table entry is created for each allowed connection

State-full Inspection Firewalls • State table entries track: – source and destination IP addresses – source and destination port numbers – protocol – TCP sequence numbers and acknowledgment numbers – TCP session state • SYN Received, SYN-ACK Sent, Established

Examples of Firewall • Network – Firestarter – Windows Firewall • Application – Mod_evasive – Mod_security_common

Intrusion Detection Systems • An IDS detects attempts at network intrusion – Host-based or network-based sensors collect data for local analysis or uploading to a centralized analysis engine – When intrusion is detected a log entry or alert can be generated

Detection methods • Signature analysis – discernable pattern of a previously seen attack – network scans, port scans, malicious payloads • Statistical anomaly – unusual usage patterns – log on at unusual hours, uncharacteristically high usage of a protocol • Protocol anomaly – an undefined or non-standard use of a protocol – IP header Protocol field value greater than 137 – TCP header Urgent field set to non-zero value with URG flag set to zero

IDS types • Network-based – Monitors entire network – NIC operates in promiscuous mode – Complicated sniffers that check all packets against signatures • Host-based – Protects only the host system on which it resides – Network card operates in non-promiscuous mode

Intrusion Prevention Systems • An IDS receives a copy of network traffic for analysis and reporting – malicious packets reach their targets – analysis and reporting is after the fact • An IPS is a pass-through device inline with the traffic – detected malicious packets are dropped at the IPS and do not reach their intended targets

Snort Intrusion protection and prevention system Rules-based detection engine Network sniffer Snort runs on various operating systems and hardware platforms, including many UNIX systems and Windows • Large default rule set (several thousand) • •

Snort Modes • Packet Sniffer Mode – In Packet Sniffer Mode Snort acts like tcpdump and is used for testing. – Type “snort –v” at command prompt to start snort in sniffer mode – Other switches • -d displays application layer -e displays data link layer • Packet Logger Mode – Same as Packet Sniffing Mode but it also logs the output. – Type “snort –dev –l /var/log/snort” where –l is switch for logging and /var/log/snort is directory to save output.

Snort Modes • Intrusion Detection Mode – In this mode snort applies signature rules on all captured packets – If packet matches rules, it is logged or an alert is generated

Writing Snort Rules • • • Figure out what is "bad" Capture traffic that includes the "bad" stuff Learn the protocol Figure out why the "bad stuff" is bad Write a rule Test the rule

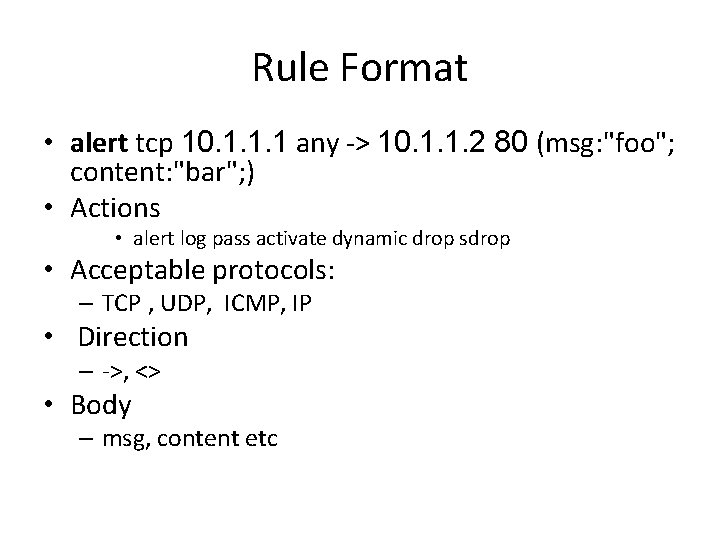
Rule Format - basic rule • alert tcp 10. 1. 1. 1 any -> 10. 1. 1. 2 80 (msg: "foo"; content: "bar"; )

Rule Format • alert tcp 10. 1. 1. 1 any -> 10. 1. 1. 2 80 (msg: "foo"; content: "bar"; ) • Actions • alert log pass activate dynamic drop sdrop • Acceptable protocols: – TCP , UDP, ICMP, IP • Direction – ->, <> • Body – msg, content etc

Honeypot • A monitored decoy to lure attackers away from critical resources – simulates various OSs and application servers • A tool to analyze an attacker’s methods and other characteristics

Honeypot Modes • Research mode – collecting data on attacker motivations, attack trends, and emerging threats • Production mode – to prevent, detect, and respond to attacks – impeding scans – diverting an attacker to the honeypot rather than critical files – capturing polymorphic code – acquiring attack signatures – providing attack information for analysis

Honeypot Software • Labrea • Honeyd

Legal issues • An organization may be liable if its honeypot is used to launch attacks against another network • Attacker might claim entrapment if apprehended through use of a honeypot – Never explicitly invite interaction with the honeypot

Auditing • Logs are the primary record keepers of system and network activity – Basis for fast recovery when service is modified illegally – Basis for tracking the break-in

System logs • Windows – Application, System and Security • Linux – Syslogs files /var/logs/*

Problem in Managing Logs • • No periodical review The log files may be modified by intrusion Log size constraint Failure to collect critical information

Audit tools • Syslog – log collection system • Audit – subsystem in Linux kernel that generates audit record (auditctl, ausearch, aureport ) • Logwatch – log analysis system • Lire - log analyzer system
 Firewalls and intrusion detection systems
Firewalls and intrusion detection systems Mark shtern
Mark shtern Mark shtern
Mark shtern Arpoison
Arpoison Intrusion detection systems (ids)
Intrusion detection systems (ids) Fiber optic perimeter intrusion detection systems
Fiber optic perimeter intrusion detection systems History of firewalls
History of firewalls Solf
Solf Mac layer firewall
Mac layer firewall List three design goals for a firewall.
List three design goals for a firewall. Linux firewalls
Linux firewalls Firewalls are used for what security principle
Firewalls are used for what security principle Firewall open source
Firewall open source Types of firewalls ppt
Types of firewalls ppt Dynamic firewalls
Dynamic firewalls Perimeter firewalls are the simplest type of firewall
Perimeter firewalls are the simplest type of firewall Firewall security audit
Firewall security audit Utulsa computer science
Utulsa computer science Linuxtricks
Linuxtricks Machine protection system
Machine protection system Machine protection system
Machine protection system The protection of information in computer systems
The protection of information in computer systems Rhino marking and protection systems
Rhino marking and protection systems Machine protection system
Machine protection system Nids open source
Nids open source Common intrusion detection framework
Common intrusion detection framework Temaline dw
Temaline dw Language meaning
Language meaning