VPN using SSH Implementing a secure Unix to























- Slides: 33

VPN using SSH Implementing a secure Unix to Unix Virtual Private Network Gary Stainburn Ringways Garages Ltd.

Andrew’s Talk • Excellent talk covering theory and history • Implemented pptp - most common use of VPN • However, my way is better.

Ssh is better, why? • Always secure - no need to patch kernel • true Unix to Unix connection. • Better for Lan to Lan. • Modular – ssh (zlib, ssl, ssh) – port redirector – pppd

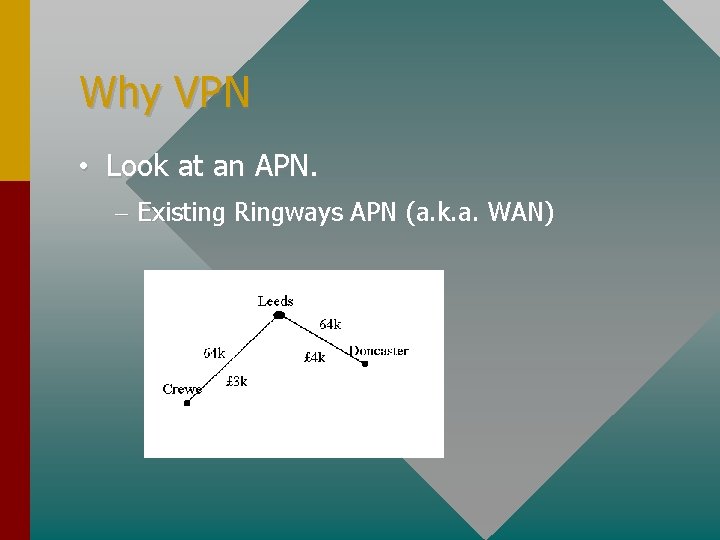
Why VPN • Look at an APN.

Why VPN • Look at an APN. – Existing Ringways APN (a. k. a. WAN)

Proposed Internet Link • Ringways were looking for an internet link

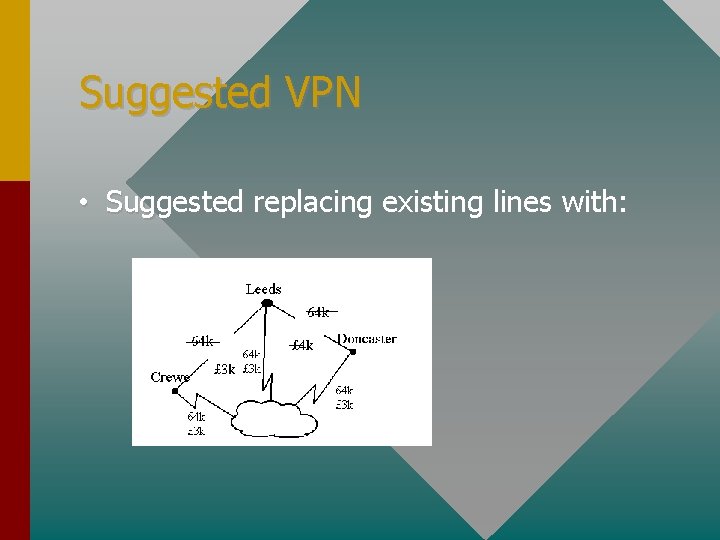
Suggested VPN • Suggested replacing existing lines with:

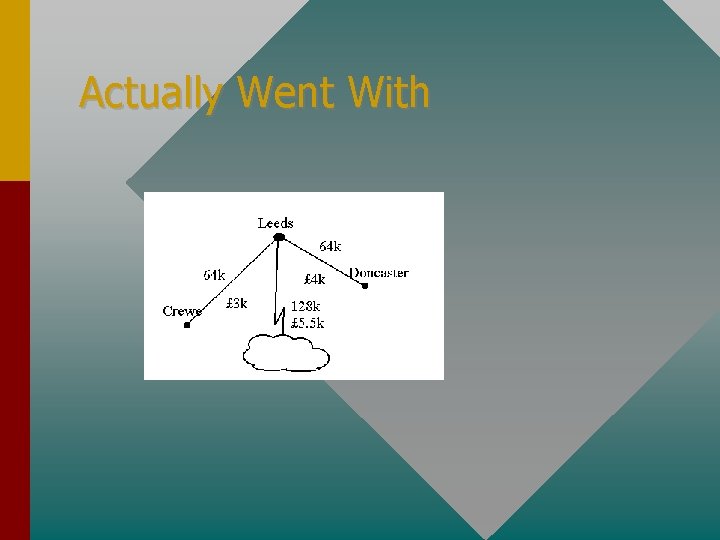
Actually Went With

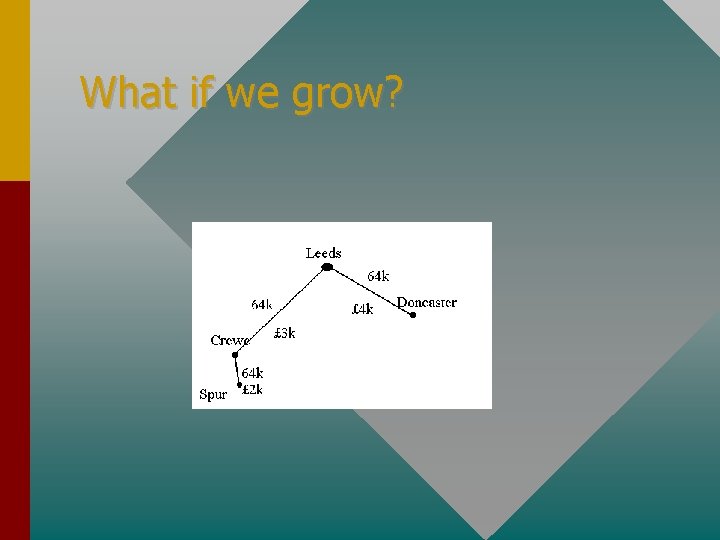
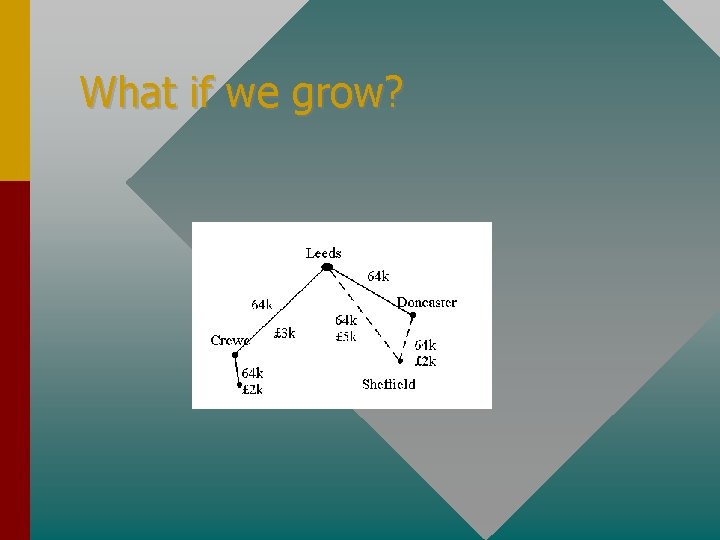
What if we grow?

What if we grow?

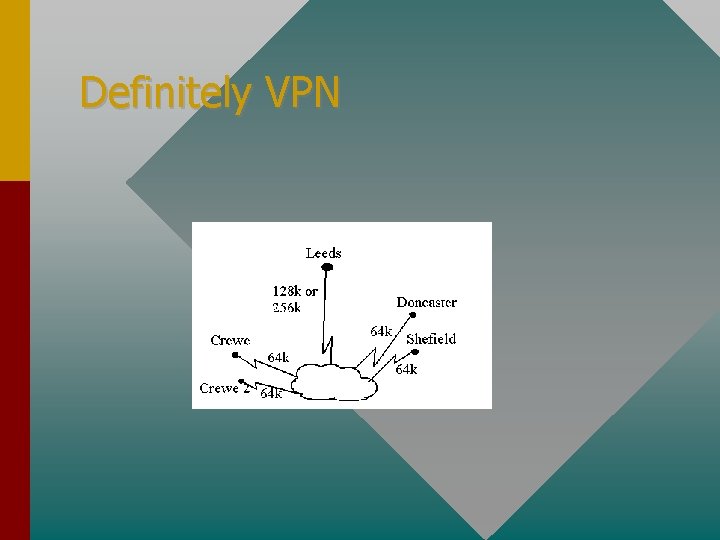
Definitely VPN

Points to Consider • APN – Cost of line vs Benefits received – Who meets costs? • VPN – No cost if link already available – Split cost if not already available

Implications • Lower costs = more uses • more uses = more connections • more connections = more access points

Security • Firewall - One point of access • Multiple access points • Weakness in remote end - Win 95? • Other people administrating • Treat VPN users as Notebook Users

Security - Server • When planning to set up a VPN server – Needs public access – Can be behind firewall - Ssh works over NAT – preferably no other access – Can be on firewall

So, how’s it work? • Uses an existing unsecured network • runs a Ssh session over that connection • redirects a pppd session over it.

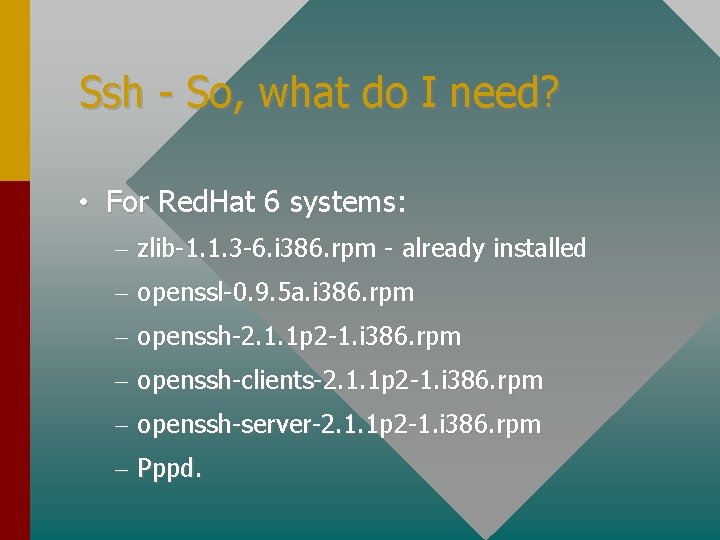
Ssh - So, what do I need? • For Red. Hat 6 systems: – zlib-1. 1. 3 -6. i 386. rpm - already installed – openssl-0. 9. 5 a. i 386. rpm – openssh-2. 1. 1 p 2 -1. i 386. rpm – openssh-clients-2. 1. 1 p 2 -1. i 386. rpm – openssh-server-2. 1. 1 p 2 -1. i 386. rpm – Pppd.

Ssh - So, what do I need? • For everything else: • zlib-1. 1. 3. tar. gz ftp: //ftp. cdrom. com/pub/infozip/zlib • openssl-0. 9. 5 a. tar. gz http: //www. openssl. org • openssh-2. 1. 1 p 2. tar. gz http: //www. openssh. com • Pppd

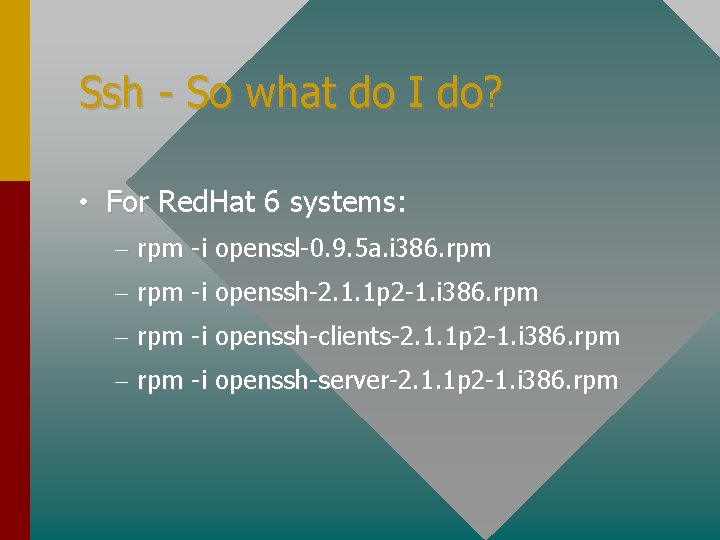
Ssh - So what do I do? • For Red. Hat 6 systems: – rpm -i openssl-0. 9. 5 a. i 386. rpm – rpm -i openssh-2. 1. 1 p 2 -1. i 386. rpm – rpm -i openssh-clients-2. 1. 1 p 2 -1. i 386. rpm – rpm -i openssh-server-2. 1. 1 p 2 -1. i 386. rpm

Ssh - So what do I do? • For everything else: – untar zlib-1. 1. 3. tar. gz –. /configure – make test – make install

Ssh - So what do I do? • For everything else: – untar openssl-0. 9. 5 a. tar. gz –. /config – make test – make install

Ssh - So what do I do? • For everything else: – untar openssh-2. 1. 1 p 2. tar. gz –. /configure – make install

Ssh - So what do I do? • As root run: – ssh-keygen • This creates. ssh directory. • This contains the private and public keys. • Create authorized_keys from public key

Ssh - So what do I do? • Copy the identity. pub from the client machine to the server machine – Client = makes call – Server = receives call • Append this file to /root/. ssh/authorized_keys • Make sure sshd is running on the server

Ssh - How do I test it • On the client – ssh <servername> • If you have done everything correctly you should now have a Ssh session open and the command prompt of the server machine on-screen.

So what’s next - Server • edit /etc/ppp/options to include: – ipcp-accept-local – ipcp-accept-remote – proxyarp – noauth

So what’s next - Server • Create a vpn-users group and user – add group vpnusers to /etc/groups • vpnusers: *: 504: – add user vpn-users to /etc/passwd • vpnuses: *: 504: 405: VPN User: /home/vpnusers: /usr/sbin/pppd – mkdir /home/vpn-users – chown vpnusers: vpnusers /home/vpnusers

So what’s next - Server • Create the /home/vpnusers/. ssh directory • Create the file. ssh/authorized_keys • Add the public keys of everyone who needs access.

So what’s next - Client • as root run: – mkdir /root/. ssh – ssh-keygen -f /root/. ssh/identity. vpn -P ”” – add the new file identity. vpn. pub to the authorized_keys on the server.

So what’s next - client – Get http: //www. shinythings. com/vpnd. tar. gz – Unzip it into /usr/local/vpn – copy pty-redir to /usr/sbin

So what’s next - client • as root run: – pty-redir ssh -t -e none -o ‘Batchmode yes’ -c blowfish -i /root/. ssh/identity. vpn -l vpnuser curly >/tmp/vpn-device – sleep 10 – /usr/sbin/pppd `cat /tmp/vpn-device`

And Finally • On the client and the server – Edit /etc/ppp/ip-up to add routes across the VPN – Edit/etc/ppp/ip-down to remove them afterwards. • What’s left – Modify the vpnd script match your configuration to make admin easier.

That’s it. • We’re done, so what have we done – We’ve got ssh working – We’ve configured a server to receive calls – We’ve configured a client to make a call – We’ve routed traffic across the VPN