SSH SSH Secure Shell SSH is a cryptographic











- Slides: 18

SSH

SSH – Secure Shell • SSH is a cryptographic protocol – Implemented in software originally for remote login applications – One most popular software implementing SSH is Pu. TTY – Download and test for free – http: //www. chiark. greenend. org. uk/~sgtatham/putty/downlo ad. html – You need a login account on a server (usually Linux) supporting logins through SSH • Servers usually operate SSH at TCP port 22 – What is a TCP port? 2

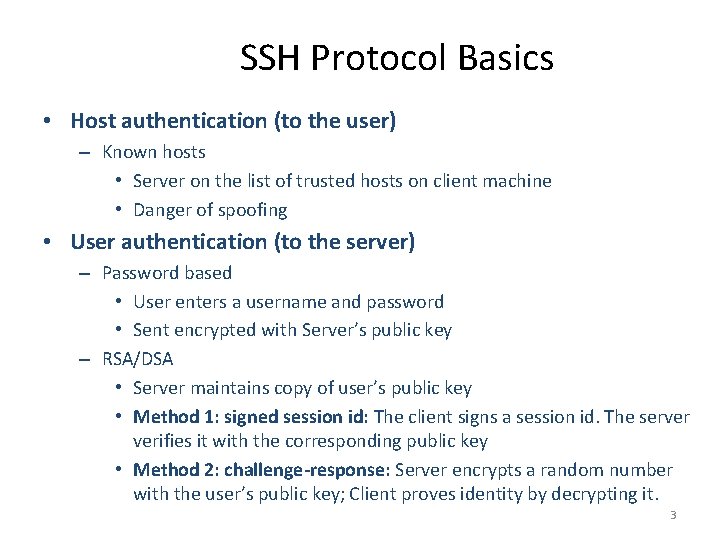
SSH Protocol Basics • Host authentication (to the user) – Known hosts • Server on the list of trusted hosts on client machine • Danger of spoofing • User authentication (to the server) – Password based • User enters a username and password • Sent encrypted with Server’s public key – RSA/DSA • Server maintains copy of user’s public key • Method 1: signed session id: The client signs a session id. The server verifies it with the corresponding public key • Method 2: challenge-response: Server encrypts a random number with the user’s public key; Client proves identity by decrypting it. 3

Uses and Advantages of SSH • SSH Overcomes limitation of Telnet – Of transmitting passwords in clear on networks on the way to the server • Originally designed for remote login – But can also be used for encrypted file transfer • Increasingly used to transport other applications – This is called SSH port forwarding or tunnelling 4

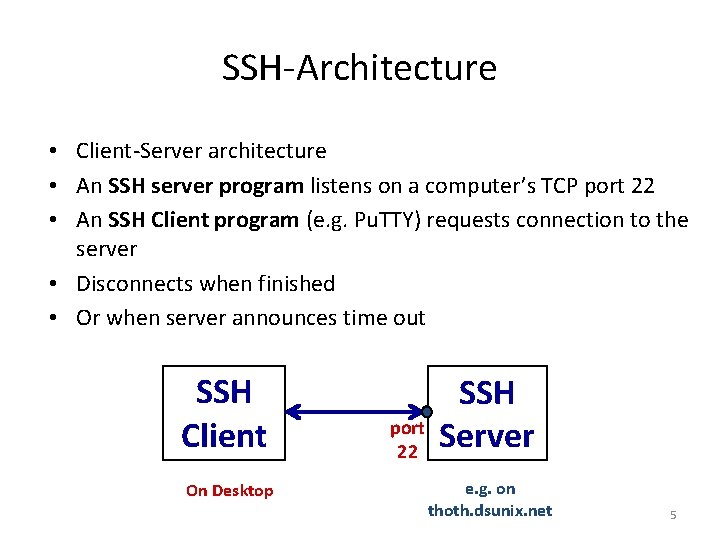
SSH-Architecture • Client-Server architecture • An SSH server program listens on a computer’s TCP port 22 • An SSH Client program (e. g. Pu. TTY) requests connection to the server • Disconnects when finished • Or when server announces time out SSH Client On Desktop port 22 SSH Server e. g. on thoth. dsunix. net 5

SSH - Software • Several implementations for both SSH Client and Servers exist – Pu. TTY is just one of them (and the most popular) • Linux: – Client: Open. SSH Client (most popular) • Run at the command line with the command “ssh” – Server: Open. SSH Server (most popular) • Either starts automatically at startup or by typing command “sshd” (stands for ssh daemon) • Windows: – Client: Pu. TTY (most popular)-Has a GUI – Server: SSH Server by Open. SSH • Uncommon but not impossible to have SSH Server on Desktop machine 6

User Agent Role • S/MIME uses Public-Key Certificates - X. 509 version 3 signed by Certification Authority • Functions: – Key Generation - Diffie-Hellman, DSS, and RSA key-pairs. – Registration - Public keys must be registered with X. 509 CA. – Certificate Storage - Local (as in browser application) for different services. – Signed and Enveloped Data - Various orderings for encrypting and signing. 7

SSH Software usage • SSH provides a virtual terminal – User almost feels as if she is using the remote system – In reality, she is only connected to the remote system • Same in Telnet too but there transmitted data is unencrypted – In SSH, all data is encrypted • SSH can also be used for remote command execution – Syntax: ssh –l username hostname command – E. g. ssh –l malladis thoth. dsunix. net ‘rm index. html’ 8

User Agent Role • Example: Verisign (www. verisign. com) – Class-1: Buyer’s email address confirmed by emailing vital info. – Class-2: Postal address is confirmed as well, and data checked against directories. – Class-3: Buyer must appear in person, or send notarized documents. 9

File transfer with SSH • FTP transfers files in the clear – SSH can be used to do encrypted file transfer – Also termed SCP (Secure Copy) • Win. SCP is a software that implements SCP – available for free download – Has a GUI • Command line SCP tools require the command – pscp malladis@dsunix. net: syllabus. txt teaching 10

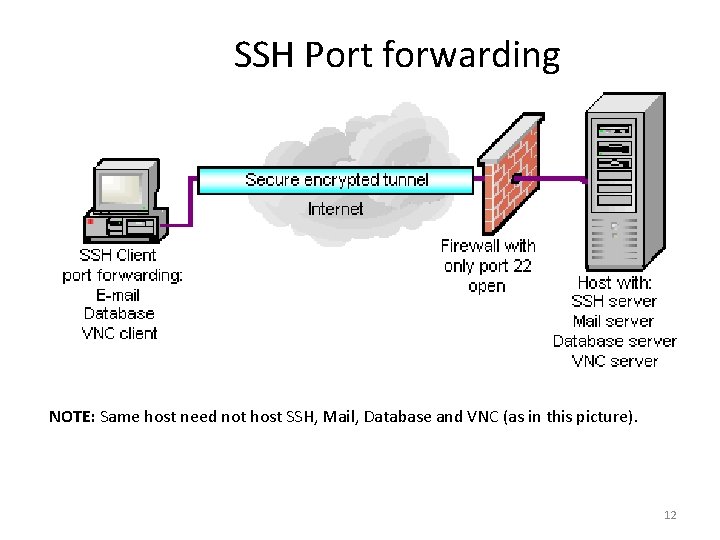
Port Forwarding in SSH • Use of SSH from a different port • Enables the use of SSH for insecure TCP/IP applications (such as email, web browsing etc. ) • Also to bypass firewalls – How? • Port forwarding can solve problems – See next slide 11

SSH Port forwarding NOTE: Same host need not host SSH, Mail, Database and VNC (as in this picture). 12

A Problem • Consider the situation – Say an employee at a company is away from office – Wants to access her IMAP email by connecting to an internal host in the corporate network, remotely – But the IMAP port (143) is blocked by the corporate firewall • Normally this would mean she cant read her email 13

A Problem ( continued) • But say the SSH port (22) is open on the firewall • And she has an account on an internal machine that runs SSH server • She can then set up a “SSH tunnel” from a local port on her client PC, through the SSH server and on to the desired application (in this case, the mail server on port 143). • Next she can connect her mail client on the local port (from which she set up an SSH tunnel to port 22) – The connection is forwarded to the desired application (the mail server) 14

Secure Tunnel Firewall Port 1143 Port 22 Company Network Internet Port 143 Secure SSH Tunnel Set up command (also possible in Pu. TTY): ssh –l loginname –L 1143: mailserver: 143 sshserver. company. com (user is prompted for password) 15

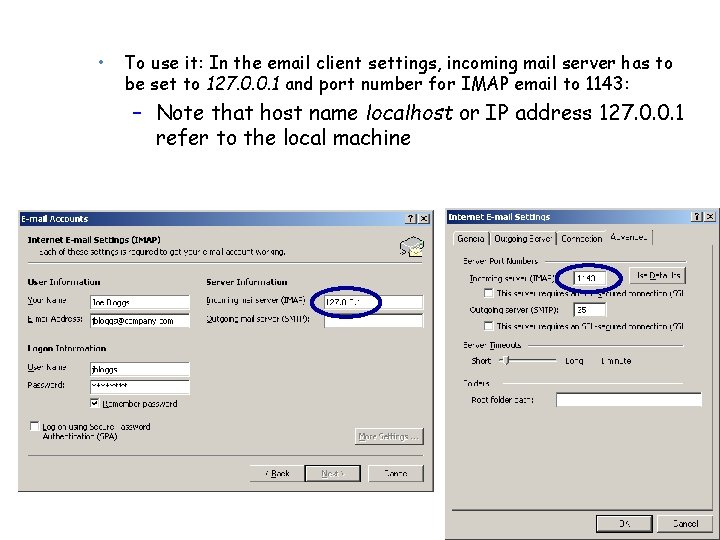
• To use it: In the email client settings, incoming mail server has to be set to 127. 0. 0. 1 and port number for IMAP email to 1143: – Note that host name localhost or IP address 127. 0. 0. 1 refer to the local machine 16

Port forwarding – more examples • Say your academic institution subscribed to journals and articles from various websites – Where authentication is based on the institution’s IP address range – Meaning that only people within the institution (physically) can get access • But if you can forward a local port on the Web Proxy via a SSH server accessible from outside, you can appear to websites as though you are accessing from within your institution 17

Security of port forwarding • Good aspects of port forwarding – Secure access to insecure services • Can transport any kind of application – email, web browsing, file transfer etc. – Bypassing firewalls • Forces users to only access internal services securely • Bad aspects – Gives users (consequently attackers) means to access arbitrary internal services – Since only password authentication is used, all an attacker is need is password of any one user on SSH • And then for example, browse the company’s intranet 18