SSH SECURE SHELL Poll You need a password






- Slides: 20

SSH: SECURE SHELL

Poll: You need a password to ssh to another computer A. True B. False

overview • Purpose • Protocol specifics • Configuration • Security considerations • Other uses

ssh purpose • A network protocol • Uses public-key cryptography to establish a secure connection between hosts • Original intention to replace the clear-text telnet protocol • Client-server model • Requester is the client • Target is server • Commonly used to connect to a shell remotely • Also supports • Secure copying • Port forwarding • Tunneling • …

Important Note • Two programs needed to make a secure connection • SSH client • Typically ssh • Typically comes enabled on most systems • SSH server • Typically sshd • Typically needs to be installed • Configured • Running as a service • Allows a "one-way" secure connection from client to server • If a connection is required in the other direction another client and server pair is required

protocol • 2 versions (SSH-1, SSH-2) • Version 1 is deprecated • Did not use Diffie-Hellman key exchange • Server listens on TCP port 22 (default) • Authentication based on: • Passwords • RSA/DSA key pairs • Other keys are allowed • DSA and RSA are the most widely used algorithms • GSSAPI (Kerberos, NTLM)

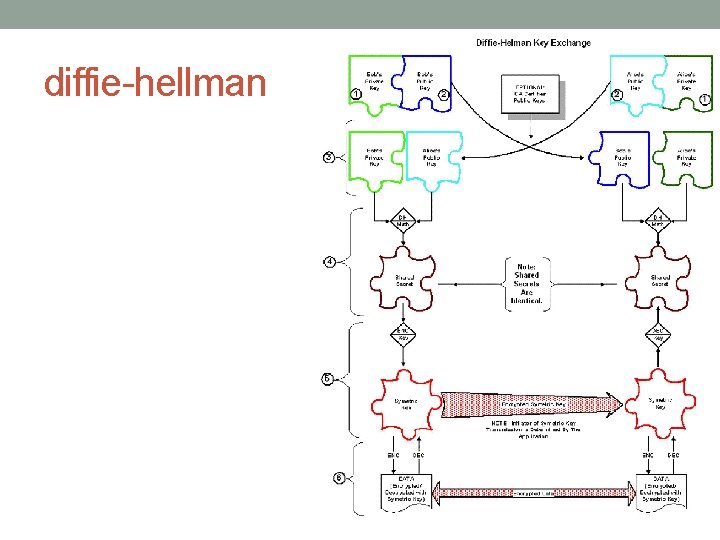
diffie-hellman

keys • For public cryptography each party has 2 keys: • 1 public, 1 private • Keeps private, distributes public • For each ID or client • Stored on client • Server public key(s): ~/. ssh/known_hosts • One key for each server you want to go to • Client private key: ~/. ssh/id_rsa • Stored on server • Server private key: /etc/ssh_host_rsa_key • Client public key(s): ~/. ssh/authorized_keys • One for each person allowed • Note: this is for one-way authentication • Another key pair is needed if want to connect the other direction

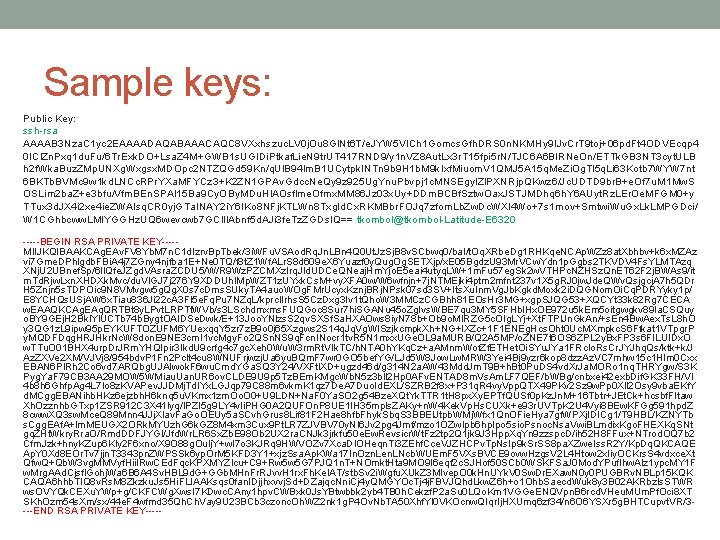
Sample keys: Public Key: ssh-rsa AAAAB 3 Nza. C 1 yc 2 EAAAADAQABAAACAQC 8 VXxhszuc. LV 0 j. Ou 8 Gl. Nt 6 T/e. JYW 5 VICh 1 Gomcs. Gfh. DRS 0 n. NKMHy 9 IJv. Cr. T 9 toj+06 pd. Ft 4 ODVEcqp 4 0 ICl. Zn. Pxq 1 du. Fu/6 Tr. Exk. DO+Lsa. Z 4 M+GWB 1 s. UGIDi. Ptkaf. Lie. N 9 tr. UT 417 RND 9/y 1 n. VZ 8 Aut. Lx 3 r. T 15 fpi 5 r. N/TJC 6 A 6 BIRNe. On/ETTk. GB 3 NT 3 cyt. ULB h 2 f. Wka. Buz. ZMp. UNXg. Wxgsx. MDOpc 2 NTZQGd 59 Kn/q. Ul. B 94 lm. B 1 UCytpk. INTn 9 b 9 H 1 b. M 9 k. Ixf. Miuom. V 1 QMJ 5 A 15 q. Me. Zi. Og. Tl 5 q. Li 63 Kotb 7 WYW 7 nt 6 BKTb. BVMc 9 w 1 kd. LNCc. RPr. YXa. MFYCz 3+K 2 ZN 1 GPAv. Gdcc. Ne. Qy 9 z 925 Ug. Ynu. Pbvpj 1 c. MNSEgyl. Zl. PXNRjp. QKwz 6/Jc. UDTD 9 br. B+e. Of 7 u. M 1 Mw. S OSLim 2 ba. Z+e 3 bfu/Vfm. BEn. SPAl 15 Ba 9 Cy. OBy. MDu. Hl. AOsflme. Ofmx. MM 86 Jz 03 x. Uy+DDm. BCBf. Sztw. Oax. JSTJMDhq 6 h. Y 6 AUyt. Rz. LEr. Oe. MFGM 0+y TTux 3 d. JX 4 i 2 xe 4 ie. ZWAlsq. CR 0 yj. GTa. INAY 2 i. Y 6 IKo 8 NFj. KTLWn 8 Txg. Id. Cx. RKMBbr. FOJq 7 zfom. Lb. Zw. Dc. WXl 4 Wo+7 s 1 mov+Smtwi. Wu. Gx. Lk. LMPGDci/ W 1 CGhbcww. LMIYGGHz. UQ 6 wevcwb 7 GCl. Il. Abnf 5 d. AJi 3 fe. Tz. ZGDs. IQ== tkombol@tkombol-Latitude-E 6320 -----BEGIN RSA PRIVATE KEY----MIIJKQIBAAKCAg. EAv. FV 8 Yb. M 7 n. C 1 d. Izrv. Bp. Tbek/3 i. WFu. VSAod. Rq. Jn. LBn 4 Q 0 Ut. Jz. Sj. B 8 v. SCbwq 0/ba. I/t. Oq. XRbe. Dg 1 RHKqe. NCAp. WZz 8 at. Xbhbv+k 6 x. MZAz vi 7 Gme. DPhlgdb. FBi. A 4 j 7 ZGny 4 njfba 1 E+Ne 0 TQ/f 8 t. Z 1 Wf. ALr. S 8 d 609 e. X 6 Yuazf 0 y. Qug. Og. SETXjp/x. E 05 Bgdz. U 93 Mr. VCw. Ydn 1 p. Ggbs 2 TKVDV 4 Fs. YLMTAzq XNj. U 2 UBnef. Sp/6 l. IQfe. JZgd. VAsra. ZCDU 5/W/R 9 Wz. PZCMXz. Irq. Jld. UDCe. QNeaj. Hm. Yjo. E 5 eai 4 utyq. LW+1 m. Fu 57 eg. Sk 2 w. VTHPc. NZHSz. Qn. ET 62 F 2 j. BWAs 9/it m. Td. Rjw. Lxn. XHDXk. Mvc/du. VIGJ 7 j 276 Y 9 XDDUh. IMp. WZT 1 z. UYxk. Cs. M+vy. XFA 0 w/W 6 wfnjn+7 j. NTMEjki 4 ptm 2 mfnt 237 v 1 X 5 g. RJ 0 jw. Jde. QWv. Qsjgcj. A 7 h 5 QDr H 5 Znjn 5 s. TDPOic 9 N 8 VMvgw 5 g. Qg. X 0 s 7 c. Dms. SUky. TA 4 auo. WOg. FMr. Ucyx. Kznj. BRj. NPsk 07 sd 3 SV+Its. Xu. Inm. Vg. Jb. Kgkd. Moxk 2 i. DQGNom. Oi. Cq. PDRYyky 1 p/ E 8 YCHQs. USj. AW 6 x. Tiau 836 Ji 22 c. A 3 Fl 5 e. Fq. Pu 7 NZq. L/kprc. Ilrhs. S 5 Cz. Dxg 3 Iv 1 t. Qho. W 3 MMCz. CGBhh 81 EOs. Hr 3 MG+xgp. SJQG 53+XQCYt 33 k 82 Rg 7 CECA w. EAAQKCAg. EAq. QRTBt 8 y. LPvt. LRPTt. WVb/s 3 LSchdmxms. FUQGoc 8 Sur 7 hi. SGANu 45 o. Zg. Ivs. WBE 7 qu 3 MY 5 SFHbl. Hx. OE 972 u 5 k. Em 5 oitgwgkv 89 la. CSQuy o. BY 9 GEj. H 2 Bkl. Yl. UCTb 74 b. Bygt. OAIDSe. Dwk/E+13 Joo. YNlzs. S 2 qv. SXSf. Sa. HXAOws 8 iy. N 78 b+Ob 9 o. MIRZG 5 c. OIg. LYj+Xt. FTPl. Jn. Gk. An/+s. En 4 Bw. Aex. Ts. L 8 h. O y 3 QG 1 z. L 9 ipw 95 p. EYKUFTOZUFM 6 YUexqq. Y 5 zr 7 z. B 9 o 0 j 65 Xzgws 2 S 14 q. Jq. Vg. WISzjkcmpk. Xh+NG+l. XZc+1 F 1 ENEg. Hcs. Oht 0 Uc. MXmpkc. S 6 Ffkat 1 VTpgr. P y. MQDFDqg. HRJHkr. Nc. W 8 don. E 9 NE 3 cm. I 1 vc. Mgy. Fo 2 QSn. NS 9 q. Fcn. INocr 1 tv. R 5 N 1 mxx. UGe. OL 9 a. MURB/Q 2 A 5 MP/o. ZNE 7 t 6 OS 6 ZPL 2 y. Bx. FP 3 s 6 FILUIDx. O w. TTu. O 01 BHX 4 urp. Dr. JRm. YHQIpir 3 Ikd. U 9 crfg 4 c 7 gc. Xeh 0 Wu. W 3 rm. Rt. VIk. TC/h. NTA 0 h. YKq. Cz+a. AMnm. Wof. Zf. ETHet. Oi. SYu. JYa 1 FRc. Io. Rs. Cr. JYJhq. Qs/ktk+k/J Az. ZXVe 2 XM/VJVj 8/954 bdv. P 1 Fn 2 Pclt 4 cu 8 WNUFrjwzj. Ua 6 yu. BQm. F 7 wr 0 GO 5 bef. YG/LJd 5 W 8 Jow. Lw. MRW 3 Yei 4 Bj 9 yzr 6 kop 8 dzz. Az. VC 7 mhw 15 c 1 Hlm 0 Cxx EBAN 6 Pl. Rh 2 Co 6 vd 7 ARQbg. UJAIwok. F 6 wu. Cmd. YGa. SQ 3 Y 24/VXFtl. XD+ugzd 46 d/g 314 N 2 a. AW 43 Mdd. Jm. T 9 B+h. Bt 0 Pu. DS 4 vd. Xr. Ja. MORo 1 nq. THRYgw/S 3 K Pyg. Ya. F 79 CB 3 AA 29 MOW 5 WMiau. Uan. UR 6 ov. CLDE 9 U 9 p 5 Tz. BEm. KMgc. Wb. N 5 z 3 bll 2 Hp 0 AFv. ENTAD 8 m. Vs. Am. LF 7 QEF/b. WBg/cnbxei 42 exb. Dif. GK 33 FH/VI 4 b 8 h 6 Ghfp. Ag 4 L 7 Io 8 z. KVAPev. JJDMj. Td. IYx. LGJqp 79 C 88 m 6 vkm. K 1 qz 7 De. A 7 Duo. Id. EXL/SZRB 2 f 8 x+P 31 q. R 4 vy. Vpp. QTX 49 PKv 2 Sz 9 w. Pp 0 Xll 2 Osy 9 vba. EKf. Y d. MCgg. EBANihb. HKz 6 ejzbh. H 6 knq 5 u. VKmx 1 zm. Oo. O 0+U 9 LDN+Na. F 0 Ya. SO 2 g 54 Bze. XQt. Yk. TTR 1 t. H 8 px. Xy. EPTf. QUSf 0 p. Kz. Jn. M+16 Tbtr+JEt. Ck+hcsbf. FItaw Xh. Ozznhb. GTxp 1 ZSR 912 C 3 X 41 lyq/IPZI 5 g 9 LY 4 vli. PHG 0 A 2 QUFOn. P 8 UE 1 IH 35 mpls. ZAKy+n. W 4 Kek. Vp. Hs. CUXk+e 93 r. UVTp. K 2 U 4 Vyi 8 BEw. KFGg 591 hpd. Z 8 cww. XQ 3 sw. Mce. Q 89 Mnn 4 JJj. Xlav. Fa. Go. OEUy 5 a. SCvh. Grus 8 Lif 81 F 2 Hae 8 hfb. Fhyk. Sbq. S 3 BBEl. Jtpb. WMj. Wfx 1 Qn. OFie. Hya 7 gf. WPXj. IDICg 1/T 9 HBL/KZNYTb s. Cgg. EAf. A+lm. MEUGX 2 ORk. MYUzh. G 6 k. GZ 8 M 4 xm 3 Cux 9 Pt. LR 7 ZJVBV 70 y. NI 6 Jv 2 pg 4 Jmf/mzo 1 OZw. Ipb 6 hp. Ipo 5 sio. Psnoc. Nsa. Vwi. BLmdix. Kgo. FHEXKq. SNt gq. ZHt. Wkry. Rra. O/Rmd. DDFJYGl/Jfd. Wr. LR 6 Sx. Zb. E 98 Ob 2 UX 2 ra. CNJk 3 jrkfu 50 e. Ew. Revsicr. Wt. Fz 2 tp 2 Q 1 jk 9 J 3 Hpp. Xq. Yn 9 zzspc. D/ih 52 H 8 FFux+NTrod. OQ 7 b 2 Cfm. Jzk+hny. KZup 6 Kly 2 F 6 xno/X 9 O 88 g. Oulj. Y+w. I 7 o 3 KJRq 9 HWVOZv 7 Xca. DIOHeqn. Ti 3 ZEhf. Cce. VJZHCPv. Tp. Ns. Ip 9 k. Sr. SS 8 pa. XZwe. Iss. R 2 Y/Kp. Dq. QKCAQE Ap. Y 0 Xd 8 EOr. Tv 7 jjn. T 3343 pn. ZWPSSk 6 yp. Or. M 5 KFD 3 Y 1+xjz. Ssa. Ap. KWa 17 In. Ozn. Len. LNcb. WUEm. F 5 VXs. BVCE 9 ovw. Hzgs. V 2 L 4 Htow 2 x. Iiy. OCKrs. S 4 vdxce. Xt Qfw. Q+Qb. W 3 vg. MMVyf. Hii. IRw. CEd. Fqc. KPXMYZlcu+C 9+Rw 5 w 5 G 7 PJQ 1 n. T+NOmkt. Hta 9 MO 9 I 6 eqf 2 c. SJHof 50 SCb 0 WSKFSa. J 0 Mod. YPuf. Ihw. Alz 1 ypc. MY 1 F w. Mrg. AAd. Cjsfl. Gohj. Wa 6 B 6 A 4 Sv. HBL 9 d. G+GGb. MHn. Fr. RJvv. H 1 rx. Fh. Ke. IAT/stb. Sv 2 i. Wgfu. XUk. Z 3 MIvep. O 0 k. Hn. UYk. V 0 Sw. Dr. EXaw. N 0 y 0 PUGBRv. NBLp 15 KQK CAQA 6 hhb. TIQ 8 v. Rs. M 8 Zkzku. Js 5 Hi. FLIAAKsqs 0 fan. IDjjhxvvj. Sd+DZajqc. Nni. Cj 4 y. QMGYOc. Tj 4 j. FBVJQhd. Lkw. Z 6 h+o 1 Ohb. Saecd. Wuk 8 y 3 B 02 AKRbzls. STWR ws. OVYQk. CEXu. YWp+g/CKFCWg. Xws. I 7 KDwc. CAny 1 hpv. CWBxk 0 Js. YBtwbbk 2 yb 4 TB 0 h. Cekzf. P 2 a. Su 0 LQo. Km 1 VGGe. ENQVpn. B 6 rcd. VHeu. MUm. Pf. Oci 8 XT SKh. Ozm 54 s. Xm/sx/44 e. F 4 wfmd 35 Qh. Ch. Vay 9 U 23 BCb 3 czonc. Oh. WZ 2 nk 1 g. P 4 Ov. Nb. TA 50 Xhf. Yl 0 VKOcnw. QIqr. Ij. HXUmq 6 zf 34/n 6 O 6 YSXr 5 g. BHTCupvt. VR/3 ----END RSA PRIVATE KEY-----

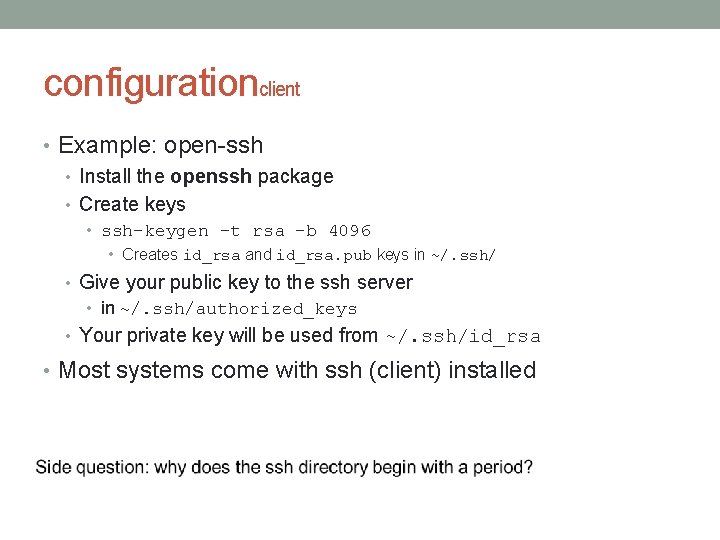
configurationclient • Example: open-ssh • Install the openssh package • Create keys • ssh-keygen -t rsa -b 4096 • Creates id_rsa and id_rsa. pub keys in ~/. ssh/ • Give your public key to the ssh server • in ~/. ssh/authorized_keys • Your private key will be used from ~/. ssh/id_rsa • Most systems come with ssh (client) installed

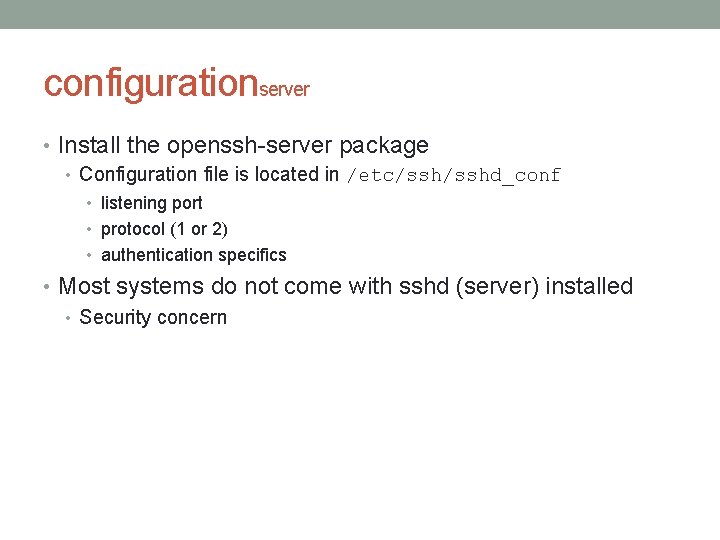
configurationserver • Install the openssh-server package • Configuration file is located in /etc/sshd_conf • listening port • protocol (1 or 2) • authentication specifics • Most systems do not come with sshd (server) installed • Security concern

configurationserver • Show config files on ajklinux 2 • /etc/ssh

Three common ways to authenticate • Userid/password • Must have a valid userid and pw on the target • Can be disabled on the target • Keypair • Must have the proper key data on the client and target • Identifies valid clients • Identifies valid targets • No need for a password if the keys are set up properly • If Userid/password is disabled on the server, then only users from specific clients can access that • Keypair and PW • For the really paranoid • Must have the keys set up properly • Must supply another password for the pair • Different than the normal UID/PW

Use example scp: Users can transfer files from client to server Generic source/destination syntax: user@computer: /path/to/file So, to copy a file (/home/johnny/file. txt) from Debian to Cent. OS (/home/alice/file. txt) what are the values for the command? scp username@<source_comp>: /path/to/file username@<dest_comp>: /path/to/file Note: this can copy from any computer to any computer (remote or local that has an appropriate key pair for each user on the computers

security considerations • ssh is often a target of (automated) attacks as outside parties try to gain access to a system • Brute-force attacks • target port 22 (default) • try to login using common usernames and passwords • (only effective against password-based authentication) • Prevention: • use key-based authentication (with >2048 bit length) • change the port sshd listens on • use tools to block access after n failed login attempts • (denyhosts, fail 2 ban)

Tool: denyhosts • One of many utilities to detect and block brute-force attacks against secure shell • IPS • Blocks attacker IP addresses using TCP wrappers • Capable of downloading and sharing attacker information with other users • Default configuration usually acceptable

tcp wrapper • Host-based Network ACL • Filters network access to network services • Services must be compiled against it • Most are these days • Files • /etc/hosts. allow • /etc/hosts. deny

other uses • X 11 forwarding • ssh -X user@host • SOCKS Proxy • ssh -ND 9999 user@host • File transfers (SSH FTP, Secure Copy) • sftp user@host (put/get/ls, etc. ) • scp src. File user@host: dir/dest. File

Hak 5 • SSH assignment: • Watch Hak 5 video: • https: //www. youtube. com/watch? v=S-G 9 yaxw 0 rc • 1 st segment SSH starts 2: 15 in (18: 01) • Ad 13: 30 -14: 00 • 2 nd segment continues to 5: 15 (19: 21) • At 7: 00 continues with Windows and Pu. TTY example to 18: 30 • 3 rd segment (22: 11) Linux example • Configuring SSH server • Done at 16: 45 (ads and wrap-up) • Show notes: • http: //hak 5. org/episodes/hak 5 -1109 • Video: fair game for the test

A PW is not required for ssh if: A. Using scp B. A key pair for a valid user has been setup on the client and server C. TCP is used D. A PW is always required to be typed in on the client 0% 0% A. B. C. D.