Defending Your Network Identifying and Patrolling Your True






































































- Slides: 109

Defending Your Network: Identifying and Patrolling Your True Network Perimeter Bill Cheswick Chief Scientist, Lumeta Corp 110 slides

Pondering and Patrolling Perimeters Bill Cheswick ches@lumeta. com http: //www. lumeta. com 110 slides

Talk Outline • Outside: mapping the Internet • A discussion of perimeter defenses • Strong host security • Mapping and understanding intranets • The past and future of Microsoft host security: – my Dad’s computer Patrolling the Perimeter 3 of 110

The Internet Mapping Project An experiment in exploring network connectivity 110 slides

Motivations • Highlands “day after” • Curiosity about size • Panix DOS attacks – a way to trace • Databases for graph scenario anonymous packets back! and growth of the Internet theorists, grad students, etc. • Visualization experiments Patrolling the Perimeter 5 of 110

Methods - data collection • Single reliable host connected at the company perimeter • Daily full scan of Lucent • Daily partial scan of Internet, monthly full scan • One line of text per network scanned – Unix tools • Use a light touch, so we don’t bother Internet denizens Patrolling the Perimeter 6 of 110

Methods - network discovery (ND) • Obtain master network list – network lists from Merit, RIPE, APNIC, etc. – BGP data or routing data from customers – hand-assembled list of Yugoslavia/Bosnia • Run a traceroute-style scan towards each network • Stop on error, completion, no data – Keep the natives happy Patrolling the Perimeter 7 of 110

Intranet implications of Internet mapping • High speed technique, able to handle the largest networks • Light touch: “what are you going to do to my intranet? ” • Acquire and maintain databases of Internet network assignments and usage Patrolling the Perimeter 8 of 110

Related Work • See Martin Dodge’s cyber geography page • MIDS - John Quarterman • CAIDA - kc claffy • Mercator • “Measuring ISP topologies with rocketfuel” - 2002 – Spring, Mahajan, Wetherall • Enter “internet map” in your search engine Patrolling the Perimeter 9 of 110

TTL probes • Used by traceroute and other tools • Probes toward each target network with increasing TTL • Probes are ICMP, UDP, TCP to port 80, 25, 139, etc. • Some people block UDP, others ICMP Patrolling the Perimeter 10 of 110

Advantages • We don’t need access (I. e. SNMP) to the routers • It’s very fast • Standard Internet tool: it doesn’t break things • Insignificant load on the routers • Not likely to show up on IDS reports • We can probe with many packet types Patrolling the Perimeter 11 of 110

Limitations • View is from scanning host only – Multiple scan sources gives a better view • Outgoing paths only • Level 3 (IP) only – ATM networks appear as a single node • Not all routers respond – Some are silent – Others are “shy” (RFC 1123 compliant), limited to one response per second Patrolling the Perimeter 12 of 110

Data collection complaints • Australian parliament was the first to complain • List of whiners (25 nets) • On the Internet, these complaints are mostly a thing of the past – Internet background radiation predominates Patrolling the Perimeter 13 of 110

Intranet uses of Don’t Scan list • Hands off particular business partners • Hands off especially sensitive networks – Hanging ATMs – 3 B 2 s with broadcast storms – Wollongong software (!) on factory floor computers • Intranet vs. ISP customer networks Patrolling the Perimeter 14 of 110

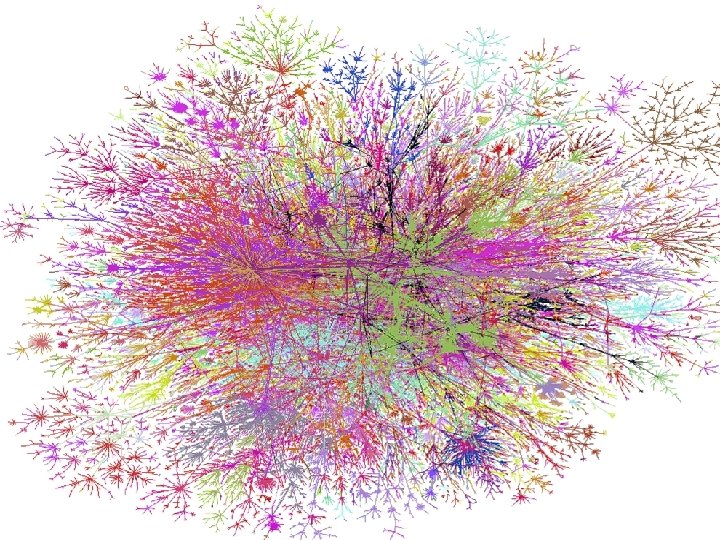
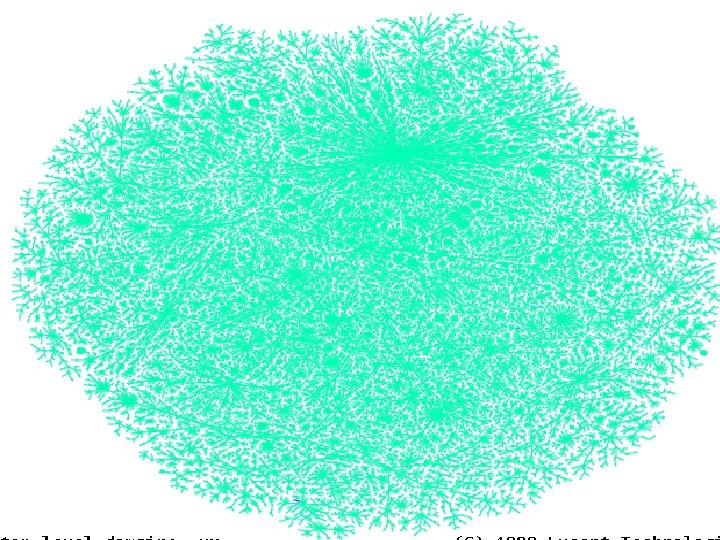
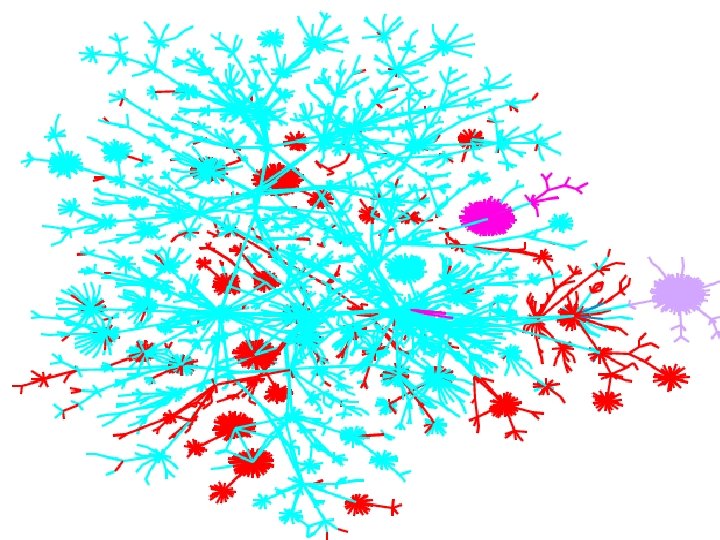
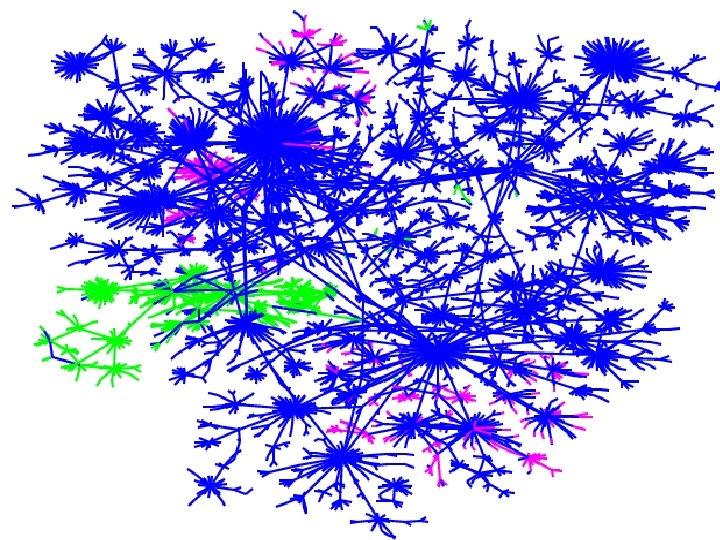
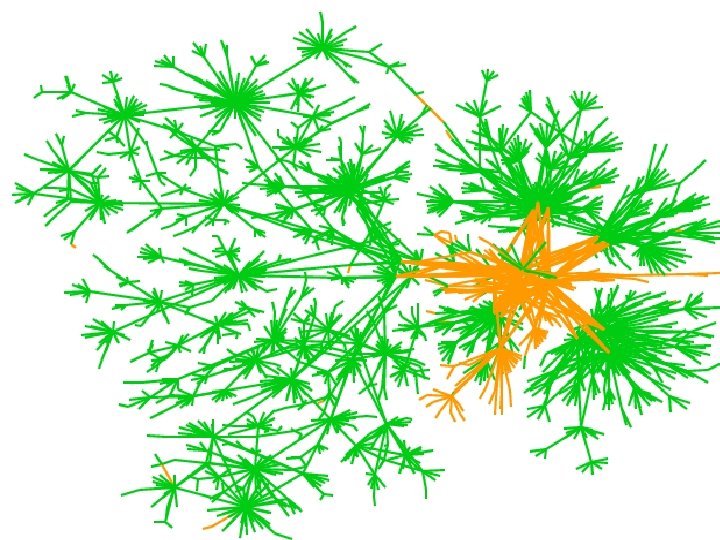
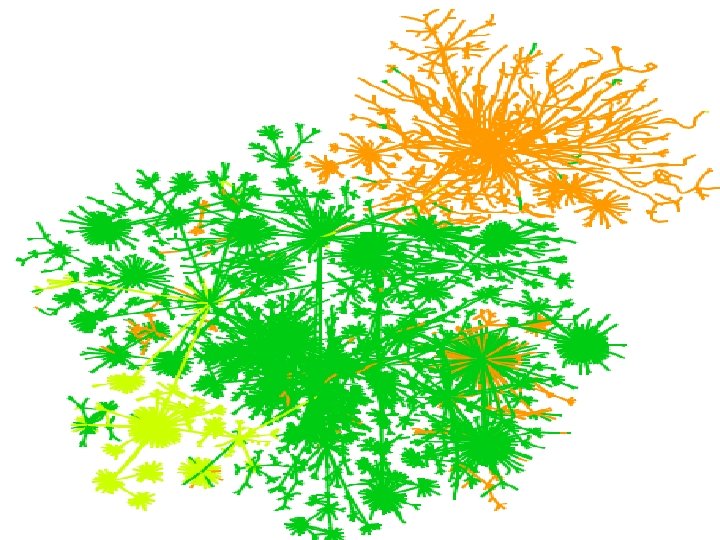
Visualization goals • make a map – show interesting features – debug our database and collection methods – hard to fold up • geography doesn’t matter • use colors to show further meaning Patrolling the Perimeter 15 of 110

Patrolling the Perimeter 16 of 110

Visualization of the layout algorithm Laying out the Internet graph 110 slides

Patrolling the Perimeter 18 of 110

Visualization of the layout algorithm Laying out an intranet 110 slides

Patrolling the Perimeter 20 of 110

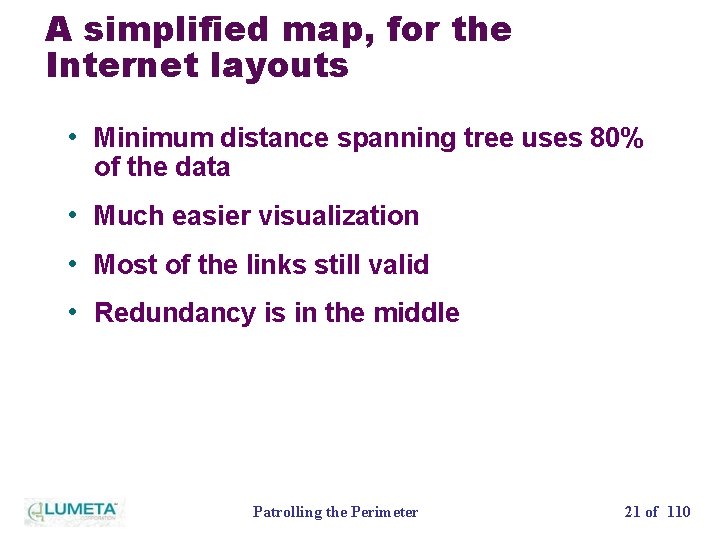
A simplified map, for the Internet layouts • Minimum distance spanning tree uses 80% of the data • Much easier visualization • Most of the links still valid • Redundancy is in the middle Patrolling the Perimeter 21 of 110

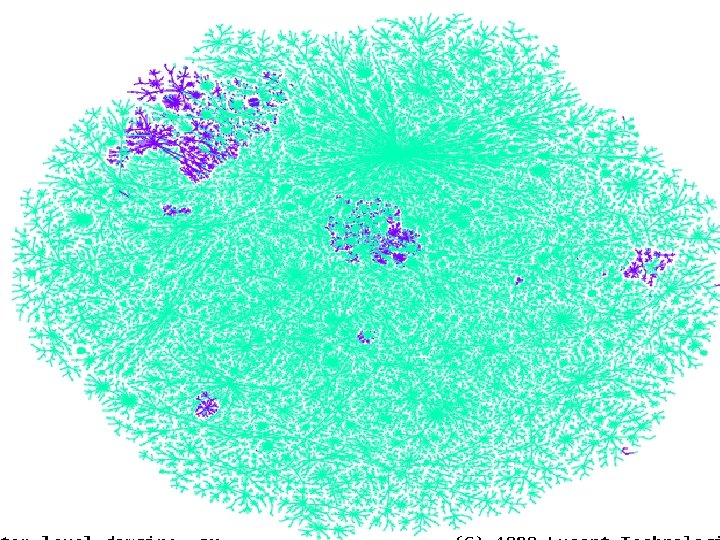
Colored by AS number Patrolling the Perimeter 22 of 110

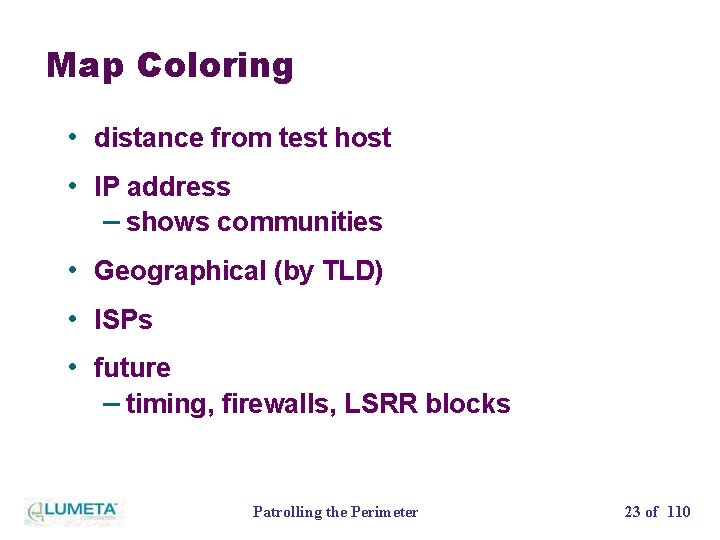
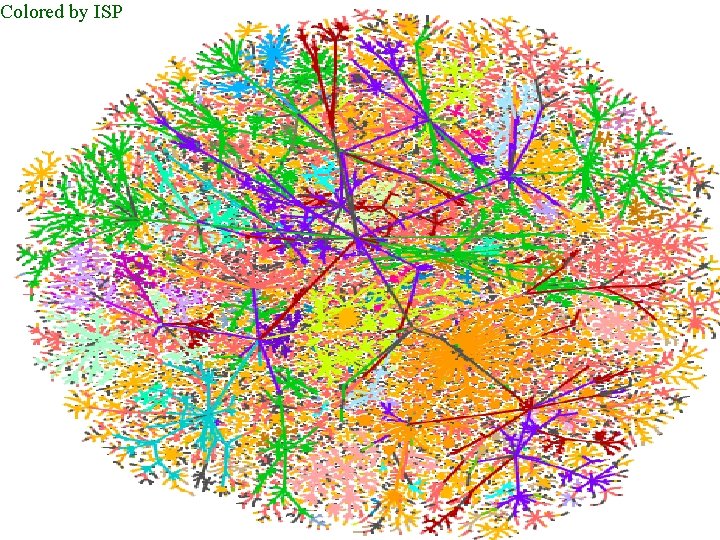
Map Coloring • distance from test host • IP address – shows communities • Geographical (by TLD) • ISPs • future – timing, firewalls, LSRR blocks Patrolling the Perimeter 23 of 110

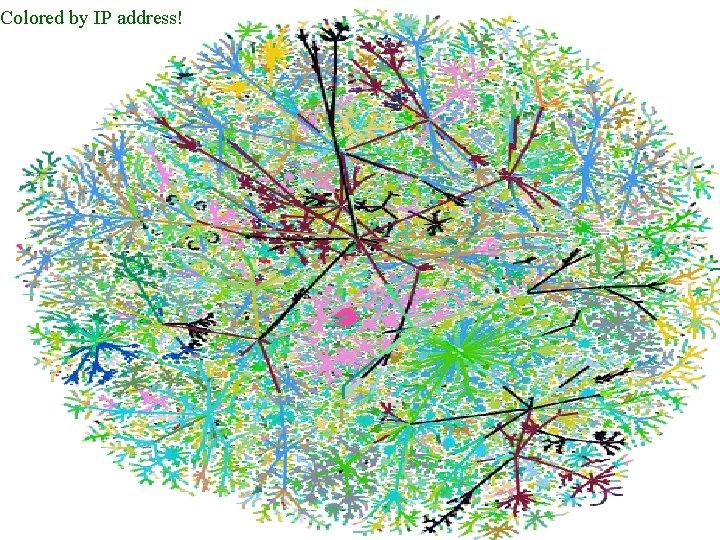
Colored by IP address! Patrolling the Perimeter 24 of 110

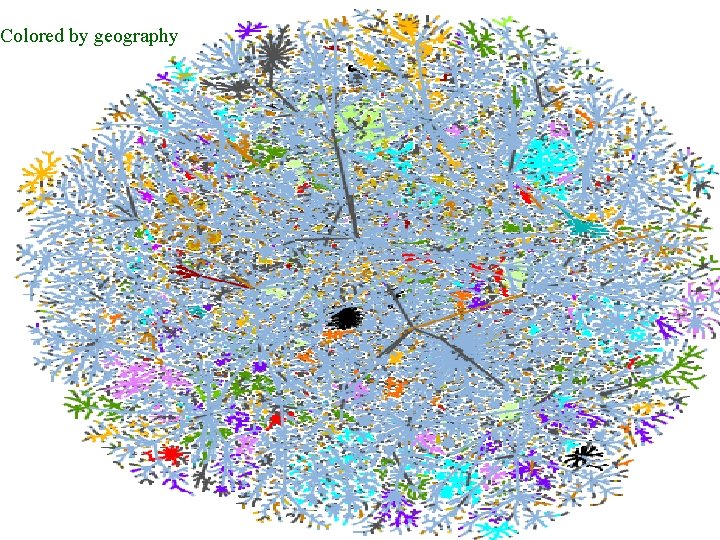
Colored by geography Patrolling the Perimeter 25 of 110

Colored by ISP Patrolling the Perimeter 26 of 110

Colored by distance from scanning host Patrolling the Perimeter 27 of 110

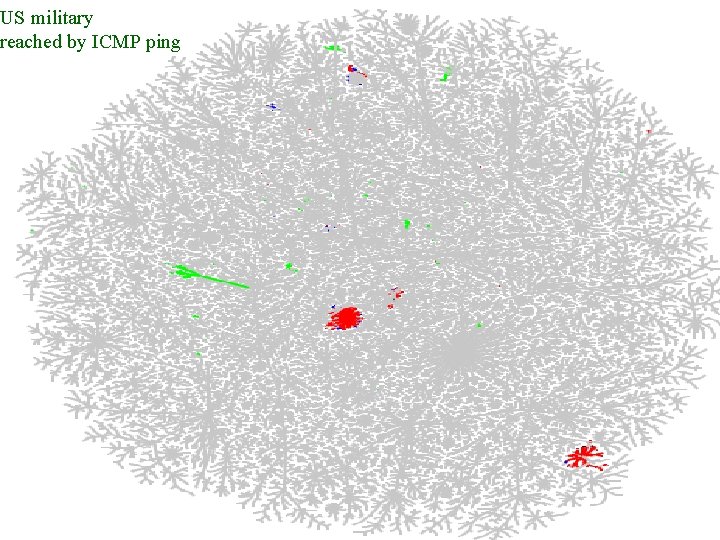
US military reached by ICMP ping Patrolling the Perimeter 28 of 110

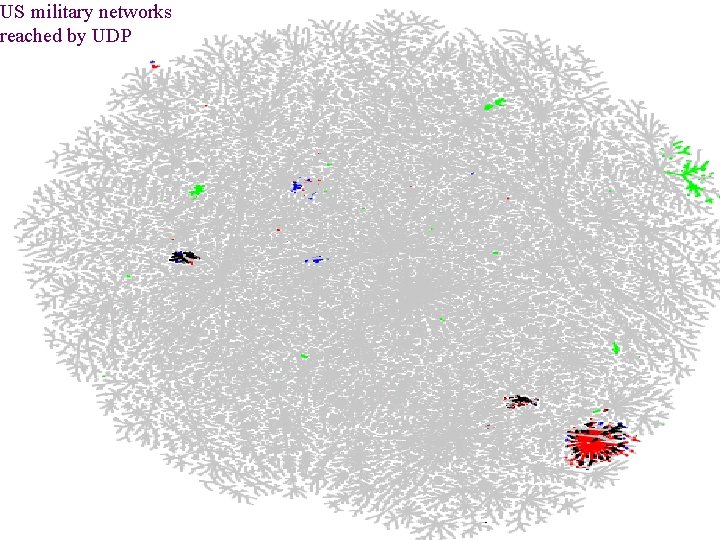
US military networks reached by UDP Patrolling the Perimeter 29 of 110

Patrolling the Perimeter 30 of 110

Patrolling the Perimeter 31 of 110

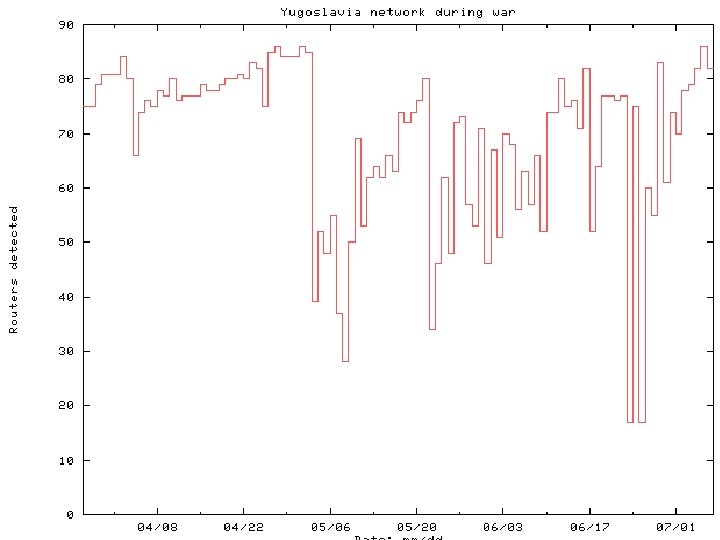
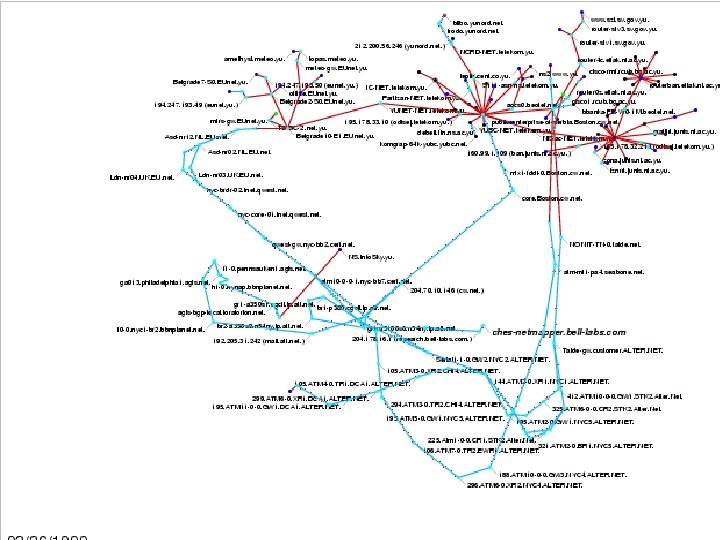
Yugoslavia An unclassified peek at a new battlefield 110 slides

Patrolling the Perimeter 33 of 110

Un film par Steve “Hollywood” Branigan. . . 110 slides

Patrolling the Perimeter 35 of 110

fin 110 slides

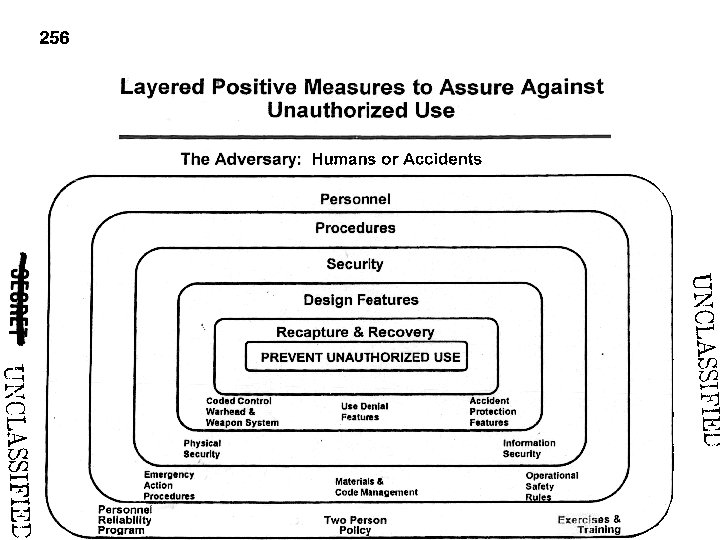
Perimeter defenses 110 slides

Perimeter defenses are a traditional means of protecting an area without hardening each of the things in that area Patrolling the Perimeter 38 of 110

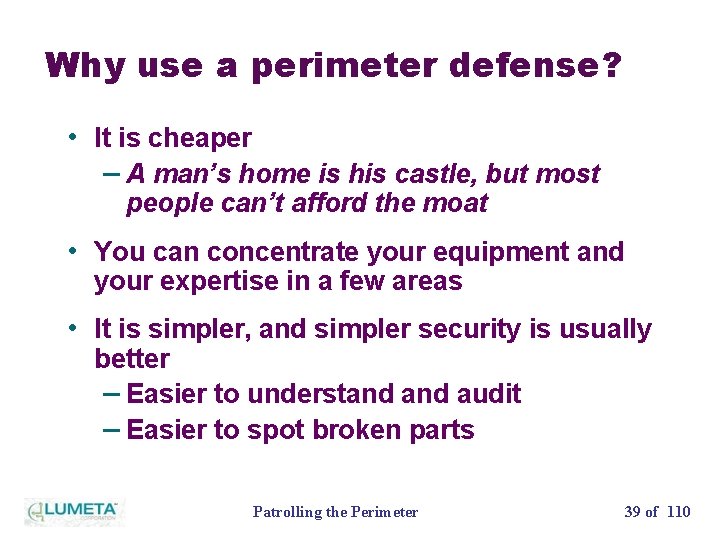
Why use a perimeter defense? • It is cheaper – A man’s home is his castle, but most people can’t afford the moat • You can concentrate your equipment and your expertise in a few areas • It is simpler, and simpler security is usually better – Easier to understand audit – Easier to spot broken parts Patrolling the Perimeter 39 of 110

Perimeter Defense of the US Capitol Building Patrolling the Perimeter 40 of 110

Flower pots Patrolling the Perimeter 41 of 110

Patrolling the Perimeter 42 of 110

Security doesn’t have to be ugly Patrolling the Perimeter 43 of 110

Patrolling the Perimeter 44 of 110

Patrolling the Perimeter 45 of 110

Patrolling the Perimeter 46 of 110

Patrolling the Perimeter 47 of 110

Delta barriers Patrolling the Perimeter 48 of 110

Parliament: entrance Patrolling the Perimeter 49 of 110

Parliament: exit Patrolling the Perimeter 50 of 110

What’s wrong with perimeter defenses • They are useless against insider attacks Patrolling the Perimeter 51 of 110

Edinburgh Castle • fell through a hole in its perimeter • fell to siege in three years in 16 th century – ran out of food and water • Unsuccessful attack by Bonnie Prince Charlie in 1745 • Devastated in 1544 by the Earl of Hertford Patrolling the Perimeter 52 of 110

What’s wrong with perimeter defenses • They are useless against insider attacks • They provide a false sense of security – You still need to toughen up the inside, at least some – You need to hire enough defenders Patrolling the Perimeter 53 of 110

Patrolling the Perimeter 54 of 110

Patrolling the Perimeter 55 of 110

What’s wrong with perimeter defenses • They are useless against insider attacks • They provide a false sense of security – You still need to toughen up the inside, at least some • They don’t scale well Patrolling the Perimeter 56 of 110

The Pretty Good Wall of China

Patrolling the Perimeter 58 of 110

Patrolling the Perimeter 59 of 110

Patrolling the Perimeter 60 of 110

Can we live without an intranet? Strong host security 110 slides

I can, but you probably can’t • “Skinny-dipping” on the Internet since the mid 1990 s • The exposure focuses one clearly on the threats and proactive security • It’s very convenient, for the services I dare to use • Many important network services are difficult to harden Patrolling the Perimeter 62 of 110

Skinny dipping rules • Only minimal services are offered to the general public – Ssh – Web server (jailed Apache) – DNS (self chrooted) – SMTP (postfix, not sendmail) • Children (like employees) and MSFT clients are untrustworthy • Offer hardened local services at home, like SAMBA (chroot), POP 3 (chroot) • I’d like to offer other services, but they are hard to secure Patrolling the Perimeter 63 of 110

Skinny dipping requires strong host security • Free. BSD and Linux machines • I am told that one can lock down an MSFT host, but there are hundreds of steps, and I don’t know how to do it. • This isn’t just about operating systems: the most popular client applications are, in theory, very dangerous and, in practice, very dangerous. – Web browsers and mail readers have many dangerous features Patrolling the Perimeter 64 of 110

Lately, I have been cheating • Backup hosts are unreachable from the Internet (which is a perimeter defense of sorts), and do not trust the exposed hosts • Public servers have lower privilege than my crown jewels • This means I can experiment a bit more with the exposed hosts Patrolling the Perimeter 65 of 110

Skinny dipping flaws • Less depth to the defense Patrolling the Perimeter 66 of 110

Patrolling the Perimeter 67 of 110

Skinny dipping flaws • Less defense in depth • No protection from denial-of-service attacks Patrolling the Perimeter 68 of 110

Hopes for Microsoft client security? • I’ll talk about it at the end of the talk. Patrolling the Perimeter 69 of 110

Intranets Networked perimeter defenses 110 slides

“Anything large enough to be called an ‘intranet’ is out of control” - me 110 slides

Intranets have been out of control since they were invented • This is not the fault of network administrators – The technology is amenable to abuse – Decentralization was a design goal of the Internet • CIO and CSOs want centralized control of their network • The legacy information is lost with rapid employee turnover • M&A breaks carefully-planned networking Patrolling the Perimeter 72 of 110

Perimeter security gives a false sense of security • “Crunchy outside, and a soft, chewy center” – Me • I think 40 hosts is about the most that I can control within a perimeter. – Others can probably do better • Internet worms are pop quizzes on perimeter security Patrolling the Perimeter 73 of 110

Intranets: the rest of the Internet 110 slides

History of the Project and Lumeta • Started in August 1998 at Bell Labs • April-June 1999: Yugoslavia mapping • July 2000: first customer intranet scanned • Sept. 2000: spun off Lumeta from Lucent/Bell Labs • June 2002: “B” round funding completed • 2003: sales >$4 MM • After three years of a service offering, we built IPSonar so you can run it yourself. Patrolling the Perimeter 75 of 110

Patrolling the Perimeter 76 of 110

Patrolling the Perimeter 77 of 110

Patrolling the Perimeter 78 of 110

Patrolling the Perimeter 79 of 110

Patrolling the Perimeter 80 of 110

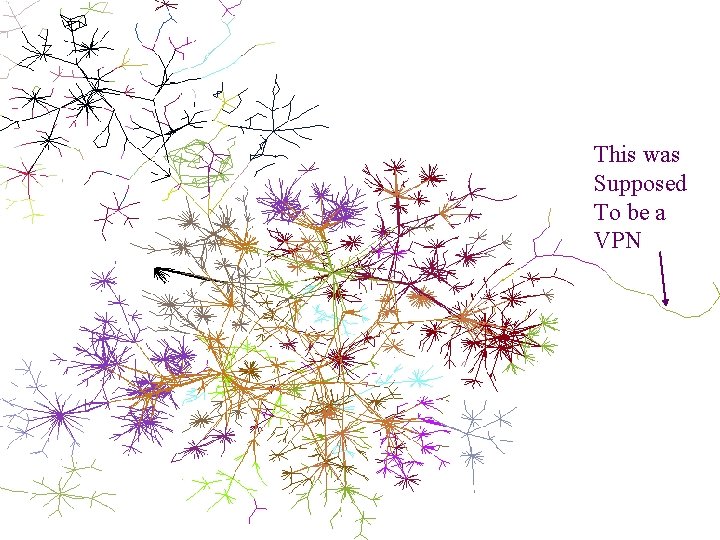
This was Supposed To be a VPN Patrolling the Perimeter 81 of 110

Patrolling the Perimeter 82 of 110

Patrolling the Perimeter 83 of 110

This is useful, but can we find hosts that have access across the perimeter? 110 slides

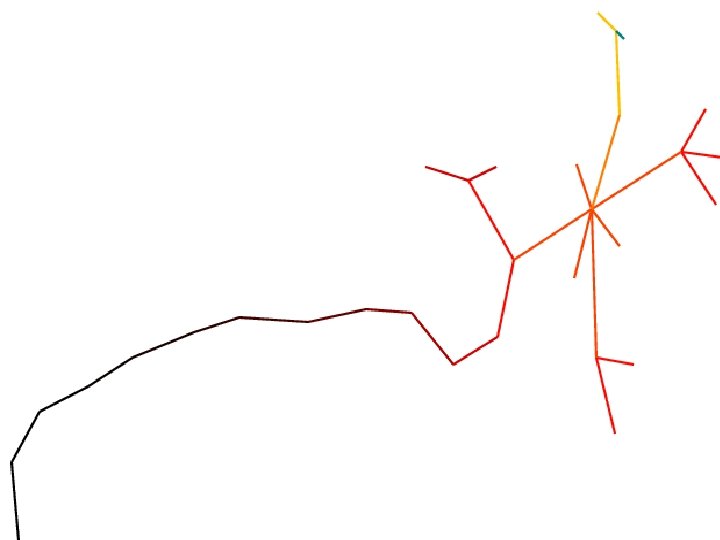
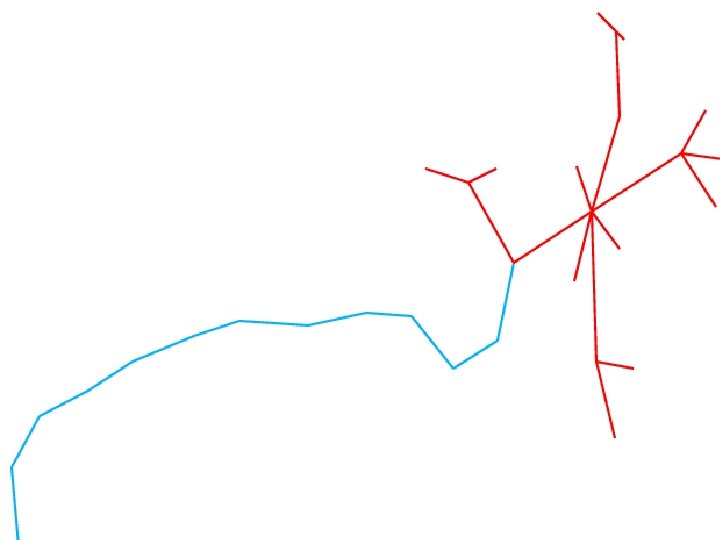
Leaks • We call the leaks shown in the maps “routing leaks” • Can we find hosts that don’t forward packets, but straddle the perimeter? • Yes: we call them “host leaks”, and detecting them is Lumeta’s “special sauce” Patrolling the Perimeter 85 of 110

How to find host leaks • Run a census with ICMP and/or UDP packets • Test each machine to see if it can receive a probe from one network, and reply on another • Not just dual-homed hosts • DMZ hosts, business partner machines, misconfigured VPN access Patrolling the Perimeter 86 of 110

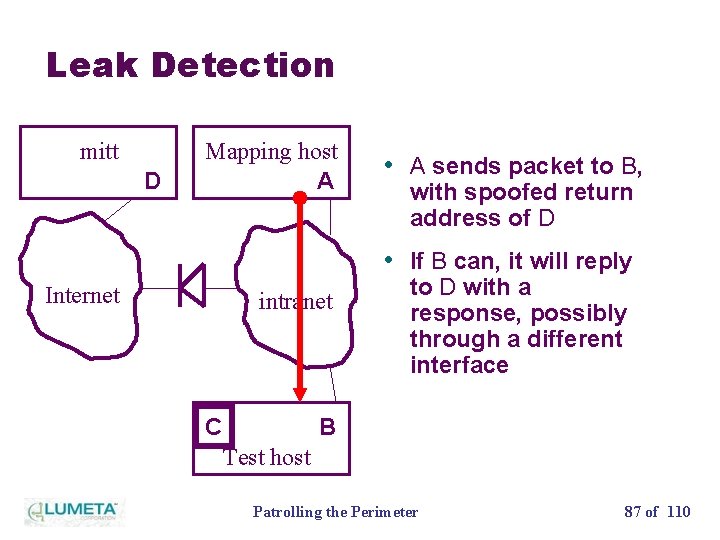
Leak Detection mitt D Mapping host A • A sends packet to B, with spoofed return address of D • If B can, it will reply Internet intranet C to D with a response, possibly through a different interface B Test host Patrolling the Perimeter 87 of 110

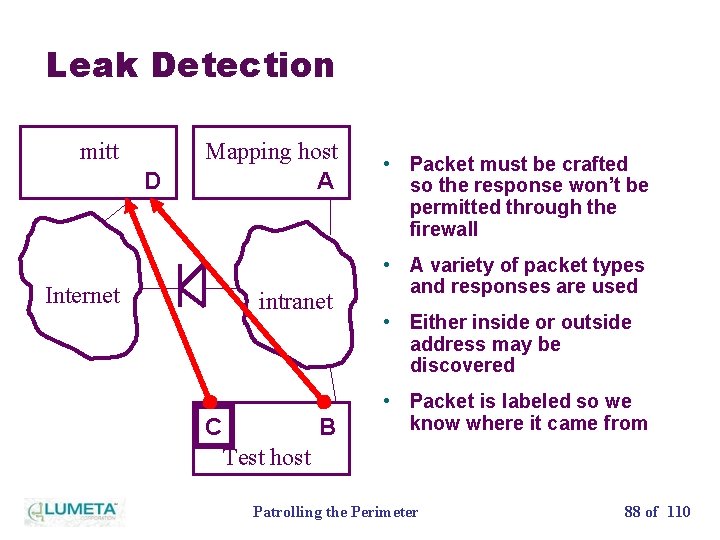
Leak Detection mitt D Mapping host A • Packet must be crafted so the response won’t be permitted through the firewall • A variety of packet types Internet intranet and responses are used • Either inside or outside address may be discovered • Packet is labeled so we C B know where it came from Test host Patrolling the Perimeter 88 of 110

Leaks are not always bad • Depends on the network policy • Often, outgoing leaks are ok • Sometimes our test packets get through, but not the services you are worrying about • “Please don’t call them leaks” • Until this test, there was no way for the CIO to detect them, good or bad • Patent pending… Patrolling the Perimeter 89 of 110

We developed lot of stuff • Leak detection (that’s the special sauce) • Route discovery • Host enumeration and identification • Server discovery • Lots of reports…the hardest part • Wireless base station discovery • And more…ask the sales people • The “zeroth step in network intelligence” – me Patrolling the Perimeter 90 of 110

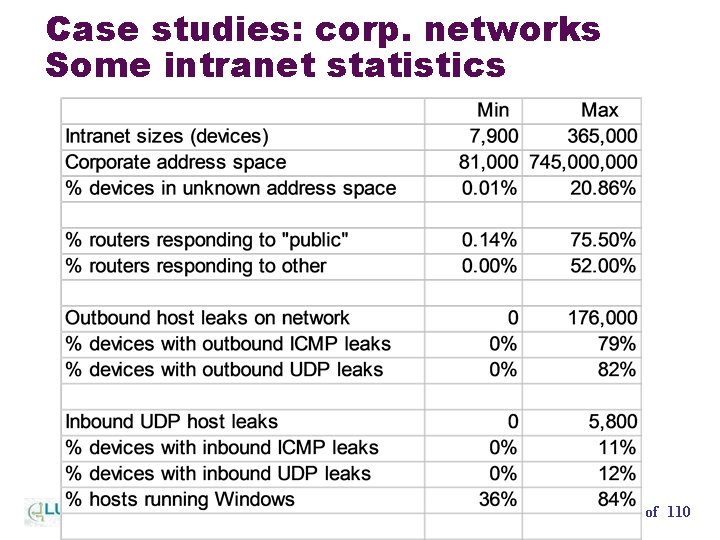
Case studies: corp. networks Some intranet statistics Patrolling the Perimeter 91 of 110

Some Lumeta lessons • Reporting is the really hard part – Converting data to information • “Tell me how we compare to other clients” • Offering a service was good practice, for a while • We have >70 Fortune-200 companies and government agencies as clients • Need-to-have vs. want-to-have Patrolling the Perimeter 92 of 110

Microsoft client security It has been getting worse 110 slides

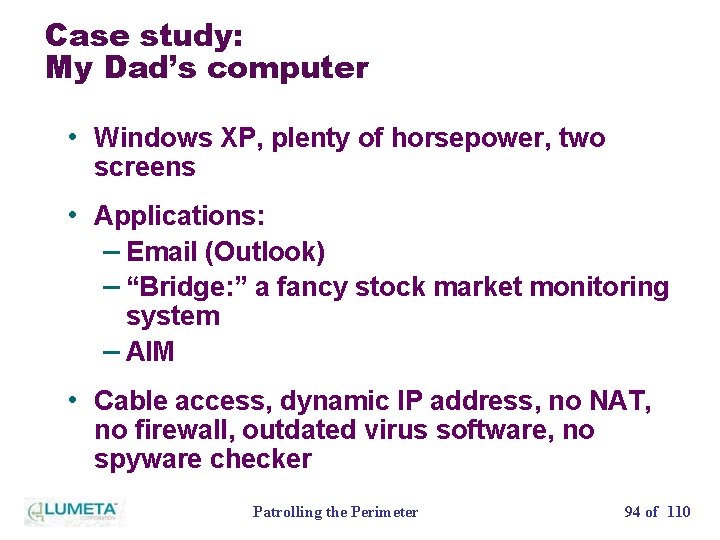
Case study: My Dad’s computer • Windows XP, plenty of horsepower, two screens • Applications: – Email (Outlook) – “Bridge: ” a fancy stock market monitoring system – AIM • Cable access, dynamic IP address, no NAT, no firewall, outdated virus software, no spyware checker Patrolling the Perimeter 94 of 110

This computer was a software toxic waste dump • It was burning a quart of software every 300 miles • The popups seemed darned distracting to me • But he thought it was fine – Got his work done – Didn’t want a system administrator to break his user interface somehow Patrolling the Perimeter 95 of 110

Microsoft’s Augean Stables • 3000 oxen, 30 years, that’s roughly one oxen -day per line of code in Windows Patrolling the Perimeter 96 of 110

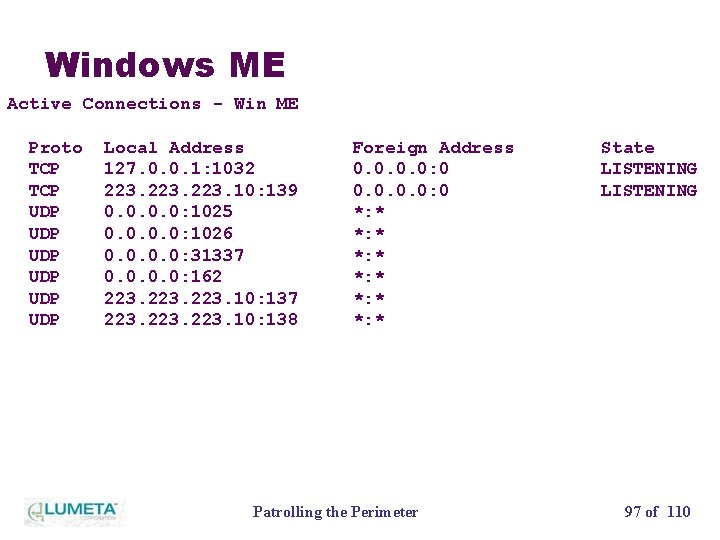
Windows ME Active Connections - Win ME Proto TCP UDP UDP UDP Local Address 127. 0. 0. 1: 1032 223. 10: 139 0. 0: 1025 0. 0: 1026 0. 0: 31337 0. 0: 162 223. 10: 137 223. 10: 138 Foreign Address 0. 0: 0 *: * *: * Patrolling the Perimeter State LISTENING 97 of 110

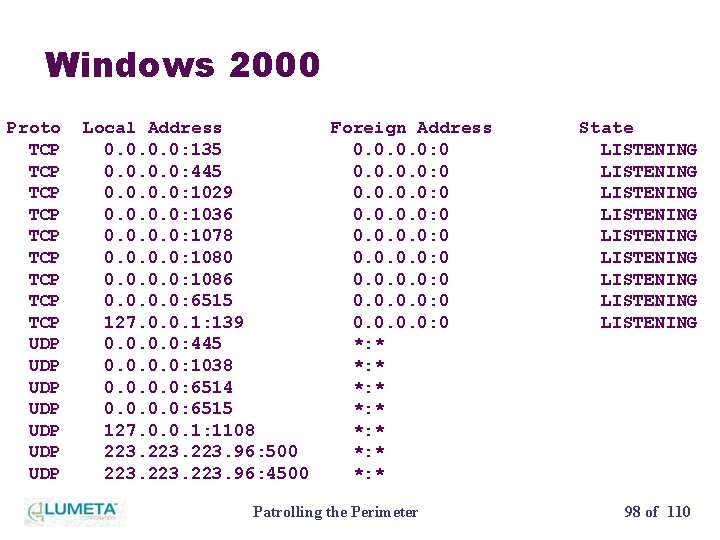
Windows 2000 Proto TCP TCP TCP UDP UDP Local Address 0. 0: 135 0. 0: 445 0. 0: 1029 0. 0: 1036 0. 0: 1078 0. 0: 1080 0. 0: 1086 0. 0: 6515 127. 0. 0. 1: 139 0. 0: 445 0. 0: 1038 0. 0: 6514 0. 0: 6515 127. 0. 0. 1: 1108 223. 96: 500 223. 96: 4500 Foreign Address 0. 0: 0 0. 0: 0 *: * *: * Patrolling the Perimeter State LISTENING LISTENING LISTENING 98 of 110

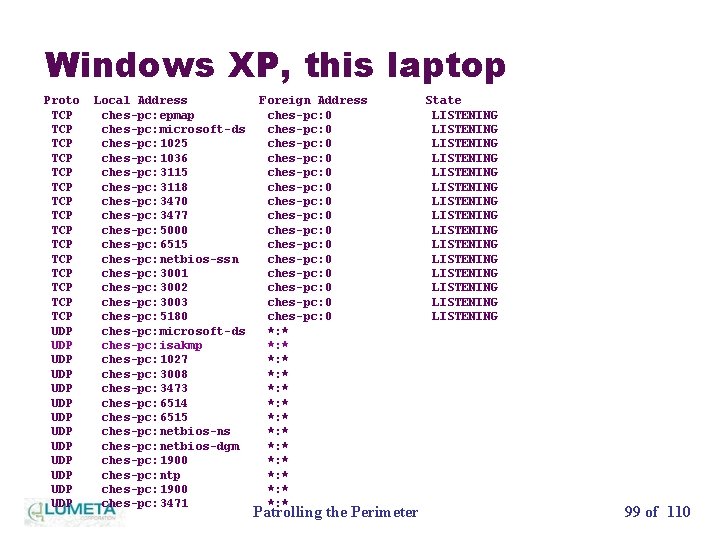
Windows XP, this laptop Proto TCP TCP TCP TCP UDP UDP UDP UDP Local Address ches-pc: epmap ches-pc: microsoft-ds ches-pc: 1025 ches-pc: 1036 ches-pc: 3115 ches-pc: 3118 ches-pc: 3470 ches-pc: 3477 ches-pc: 5000 ches-pc: 6515 ches-pc: netbios-ssn ches-pc: 3001 ches-pc: 3002 ches-pc: 3003 ches-pc: 5180 ches-pc: microsoft-ds ches-pc: isakmp ches-pc: 1027 ches-pc: 3008 ches-pc: 3473 ches-pc: 6514 ches-pc: 6515 ches-pc: netbios-ns ches-pc: netbios-dgm ches-pc: 1900 ches-pc: ntp ches-pc: 1900 ches-pc: 3471 Foreign Address ches-pc: 0 ches-pc: 0 ches-pc: 0 ches-pc: 0 *: * *: * *: * *: * Patrolling the Perimeter State LISTENING LISTENING LISTENING LISTENING 99 of 110

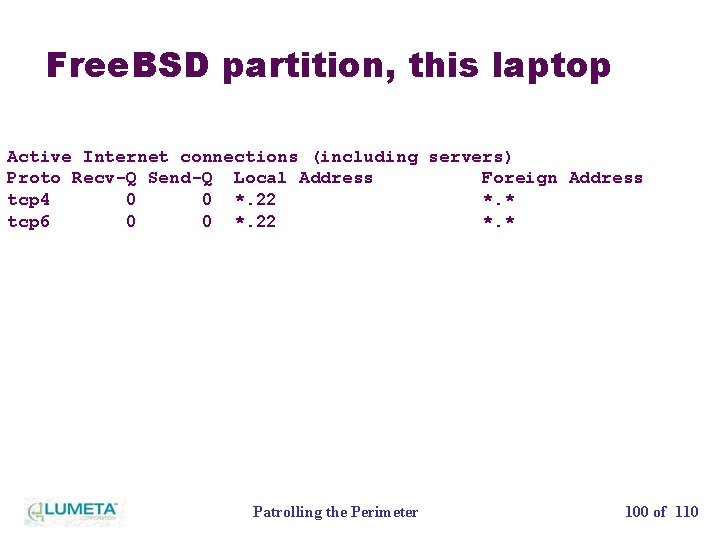
Free. BSD partition, this laptop Active Internet connections (including servers) Proto Recv-Q Send-Q Local Address Foreign Address tcp 4 0 0 *. 22 *. * tcp 6 0 0 *. 22 *. * Patrolling the Perimeter 100 of 110

Microsoft really means it about improving their security • Their security commitment appears to be real • It is a huge job • Opposing forces are unclear to me • It’s been a long time coming, and frustrating Patrolling the Perimeter 101 of 110

Microsoft really means it about improving their security • They need world-class sandboxes, many more layers in their security, and much safer defaults • A Microsoft “terminal” will benefit millions of users Patrolling the Perimeter 102 of 110

Windows OK • Thin client implemented with Windows • It would be fine for maybe half the Windows users – Students, consumers, many corporate and government users • It would be reasonable to skinny dip with this client – Without firewall or virus checking software Patrolling the Perimeter 103 of 110

Windows OK • No network listeners – None of those services are needed, except admin access for centrally-administered hosts • Default security settings, all available on the control panel security screen • Security settings can be locked Patrolling the Perimeter 104 of 110

Windows OK • Reduce privileges in servers and all programs • Sandbox programs – Belt and suspenders Patrolling the Perimeter 105 of 110

Windows OK (cont) • There should be nothing you can click on, in email or a web page, that can hurt your computer – No portable programs are executed ever, except… • Active. X from approved parties – MSFT and one or two others. List is lockable Patrolling the Perimeter 106 of 110

Office OK • No macros in Word or Power. Point. No executable code in Power. Point files • The only macros allowed in Excel perform arithmetic. They cannot create files, etc. Patrolling the Perimeter 107 of 110

Vulnerabilities in OK • Buffer overflows in processing of data (not from the network) • Stop adding new features and focus on bug fixes • Programmers can clean up bugs, if they don’t have a moving target – It converges, to some extent Patrolling the Perimeter 108 of 110

Defending Your Network: Identifying and Patrolling Your True Network Perimeter Bill Cheswick Chief Scientist, Lumeta Corp 110 slides