Cisco Self Defending Network SECURING THE INTELLIGENT INFORMATION




- Slides: 22

Cisco Self Defending Network SECURING THE INTELLIGENT INFORMATION NETWORK James Jones CCIE 1550, CISSP August 2005 © 2004 Cisco Systems, Inc. All rights reserved. 1

Agenda • Security evolves to become a business issue • Cisco’s unique architectural systems approach • Security is a business enabler © 2005 Cisco Systems, Inc. All rights reserved. 2

Key Issues Facing Customers Today SIMPLIFICATION THESE ISSUES ARE COMMON TO THE COMPUTE AND NETWORK LAYERS • • Scale Cost Staffing Integration and systems management APPLICATION AND SERVICE OPTIMIZATION • • • Enablers Awareness App management Performance/optimization Resilience SECURITY • • © 2005 Cisco Systems, Inc. All rights reserved. Threats Theft Loss Response time 3

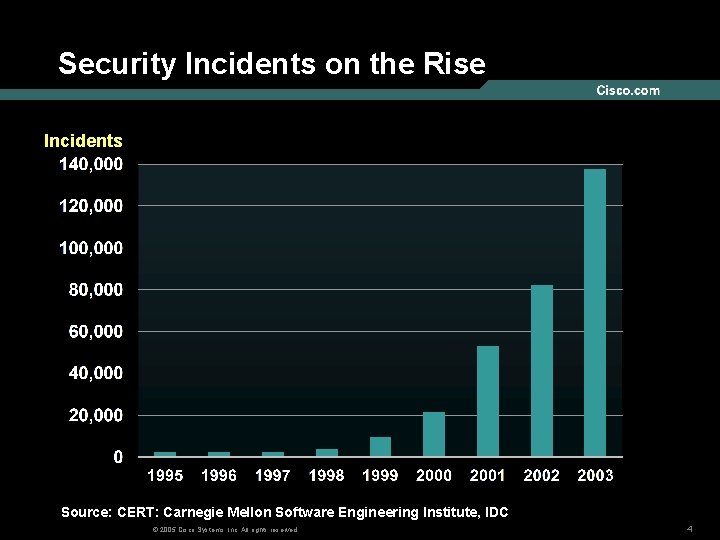
Security Incidents on the Rise Incidents Source: CERT: Carnegie Mellon Software Engineering Institute, IDC © 2005 Cisco Systems, Inc. All rights reserved. 4

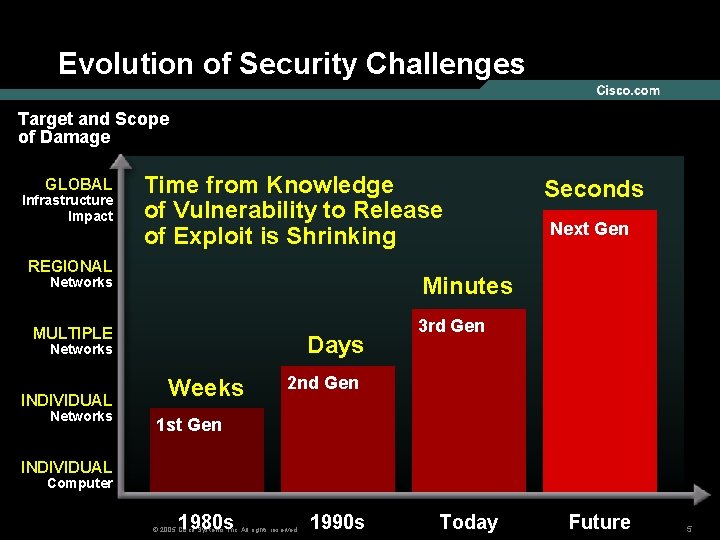
Evolution of Security Challenges Target and Scope of Damage GLOBAL Infrastructure Impact Time from Knowledge of Vulnerability to Release of Exploit is Shrinking REGIONAL MULTIPLE Days Networks Next Gen Minutes Networks INDIVIDUAL Seconds Weeks 3 rd Gen 2 nd Gen 1 st Gen INDIVIDUAL Computer 1980 s © 2005 Cisco Systems, Inc. All rights reserved. 1990 s Today Future 5

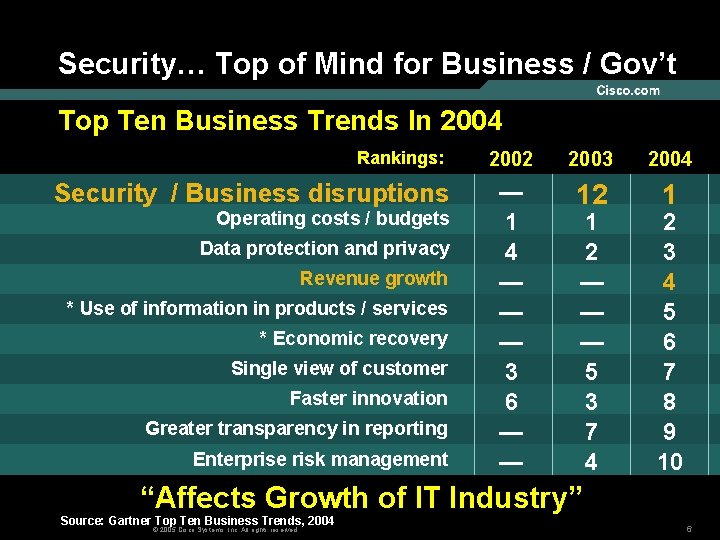
Security… Top of Mind for Business / Gov’t Top Ten Business Trends In 2004 Rankings: Security / Business disruptions Operating costs / budgets Data protection and privacy Revenue growth * Use of information in products / services * Economic recovery Single view of customer Faster innovation Greater transparency in reporting Enterprise risk management 2002 2003 2004 — 1 4 — — — 3 6 — — 12 1 1 2 — — — 5 3 7 4 2 3 4 5 6 7 8 9 10 “Affects Growth of IT Industry” Source: Gartner Top Ten Business Trends, 2004 © 2005 Cisco Systems, Inc. All rights reserved. 6

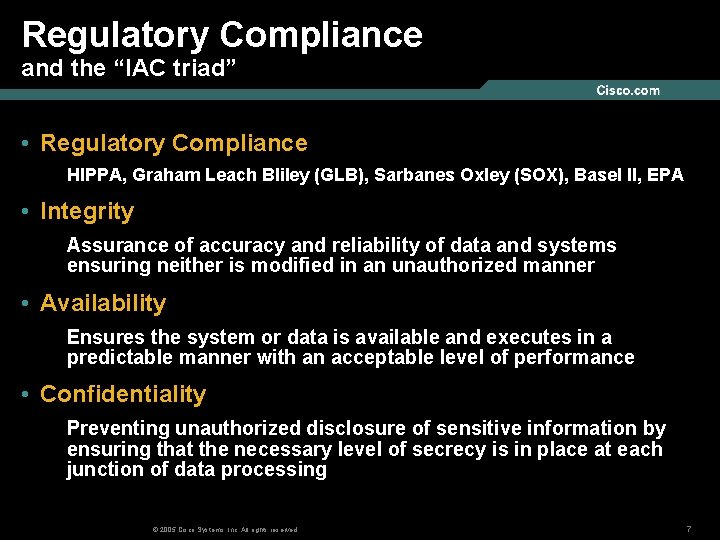
Regulatory Compliance and the “IAC triad” • Regulatory Compliance HIPPA, Graham Leach Bliley (GLB), Sarbanes Oxley (SOX), Basel II, EPA • Integrity Assurance of accuracy and reliability of data and systems ensuring neither is modified in an unauthorized manner • Availability Ensures the system or data is available and executes in a predictable manner with an acceptable level of performance • Confidentiality Preventing unauthorized disclosure of sensitive information by ensuring that the necessary level of secrecy is in place at each junction of data processing © 2005 Cisco Systems, Inc. All rights reserved. 7

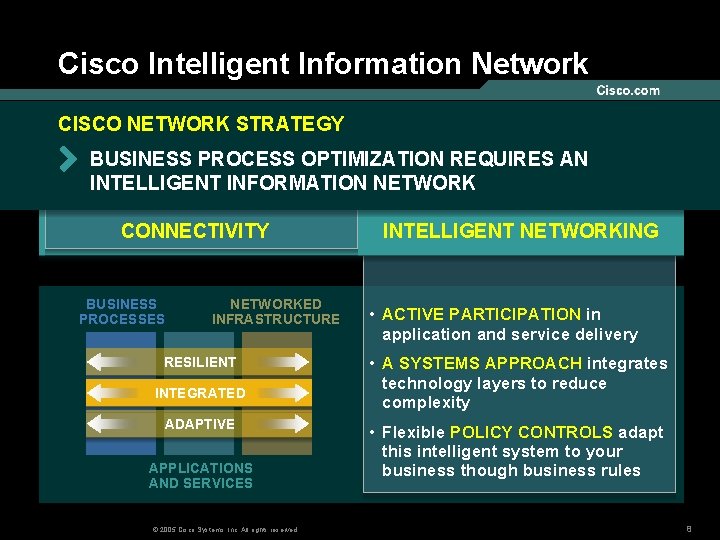
Cisco Intelligent Information Network CISCO NETWORK STRATEGY BUSINESS PROCESS OPTIMIZATION REQUIRES AN INTELLIGENT INFORMATION NETWORK CONNECTIVITY BUSINESS PROCESSES NETWORKED INFRASTRUCTURE RESILIENT INTEGRATED ADAPTIVE APPLICATIONS AND SERVICES © 2005 Cisco Systems, Inc. All rights reserved. INTELLIGENT NETWORKING • ACTIVE PARTICIPATION in application and service delivery • A SYSTEMS APPROACH integrates technology layers to reduce complexity • Flexible POLICY CONTROLS adapt this intelligent system to your business though business rules 8

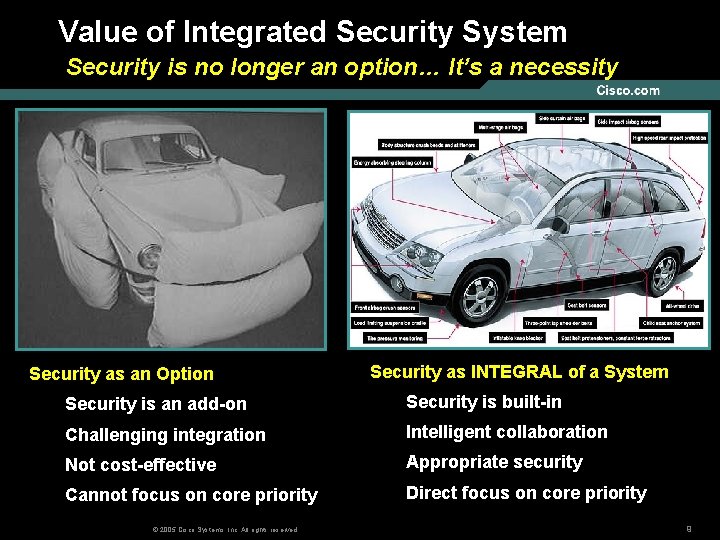
Value of Integrated Security System Security is no longer an option… It’s a necessity Security as an Option Security as INTEGRAL of a System Security is an add-on Security is built-in Challenging integration Intelligent collaboration Not cost-effective Appropriate security Cannot focus on core priority Direct focus on core priority © 2005 Cisco Systems, Inc. All rights reserved. 9

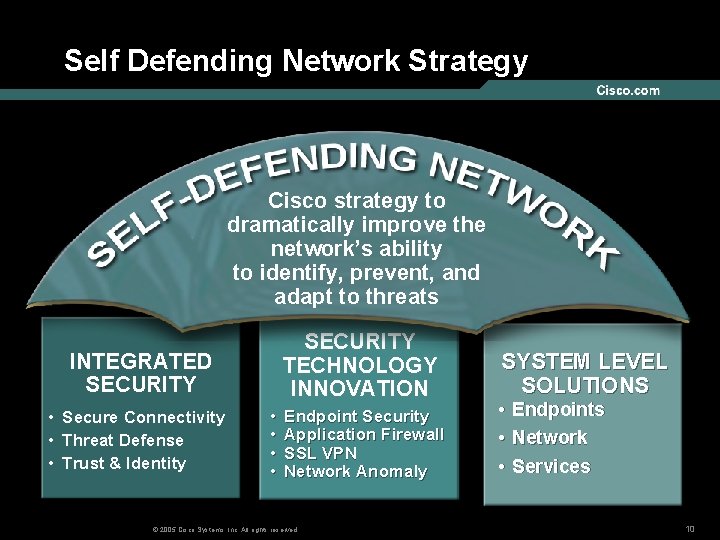
Self Defending Network Strategy Cisco strategy to An initiative to dramatically improve the network’s abilityand to identify, prevent, to identify, adapt toprevent, threats and adapt to threats SECURITY TECHNOLOGY INNOVATION INTEGRATED SECURITY • Secure Connectivity • Threat Defense • Trust & Identity • • Endpoint Security Application Firewall SSL VPN Network Anomaly © 2005 Cisco Systems, Inc. All rights reserved. SYSTEM LEVEL SOLUTIONS • • • Endpoints Network Services 10

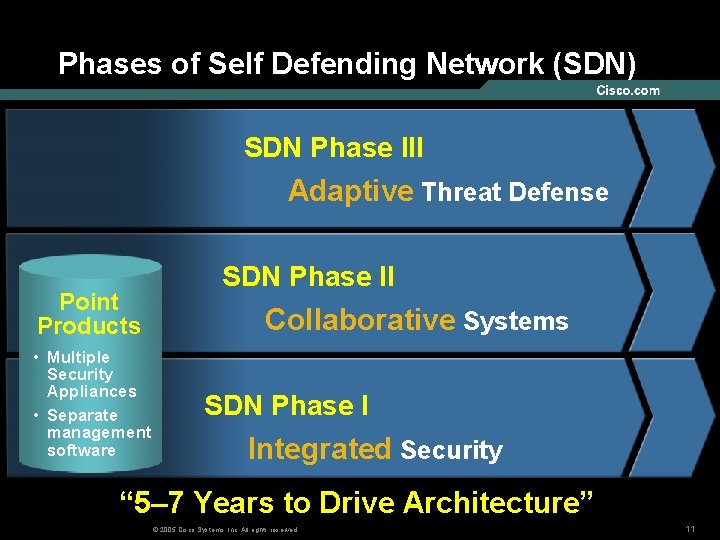
Phases of Self Defending Network (SDN) SDN Phase III Adaptive Threat Defense Point Products • Multiple Security Appliances • Separate management software SDN Phase II Collaborative Systems SDN Phase I Integrated Security “ 5– 7 Years to Drive Architecture” © 2005 Cisco Systems, Inc. All rights reserved. 11

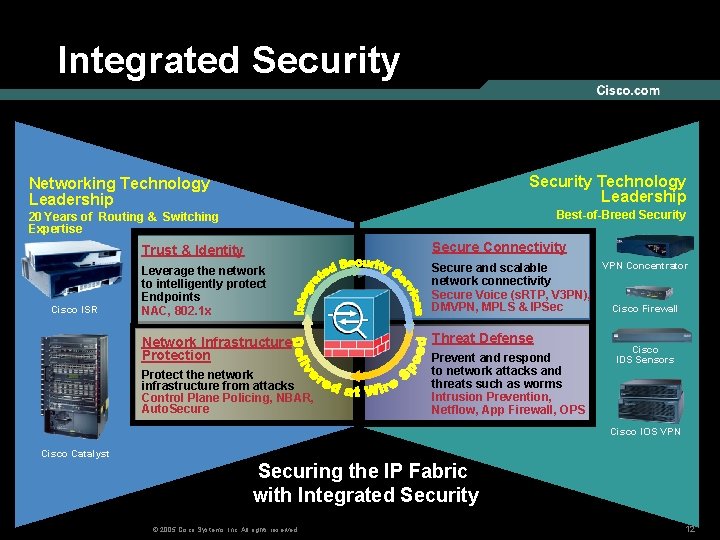
Integrated Security Technology Leadership Networking Technology Leadership Best-of-Breed Security 20 Years of Routing & Switching Expertise Cisco ISR Trust & Identity Secure Connectivity Leverage the network to intelligently protect Endpoints NAC, 802. 1 x VPN Concentrator Secure and scalable network connectivity Secure Voice (s. RTP, V 3 PN), DMVPN, MPLS & IPSec Cisco Firewall Network Infrastructure Protection Threat Defense Protect the network infrastructure from attacks Control Plane Policing, NBAR, Auto. Secure Prevent and respond to network attacks and threats such as worms Intrusion Prevention, Netflow, App Firewall, OPS Cisco IDS Sensors Cisco IOS VPN Cisco Catalyst Securing the IP Fabric with Integrated Security © 2005 Cisco Systems, Inc. All rights reserved. 12

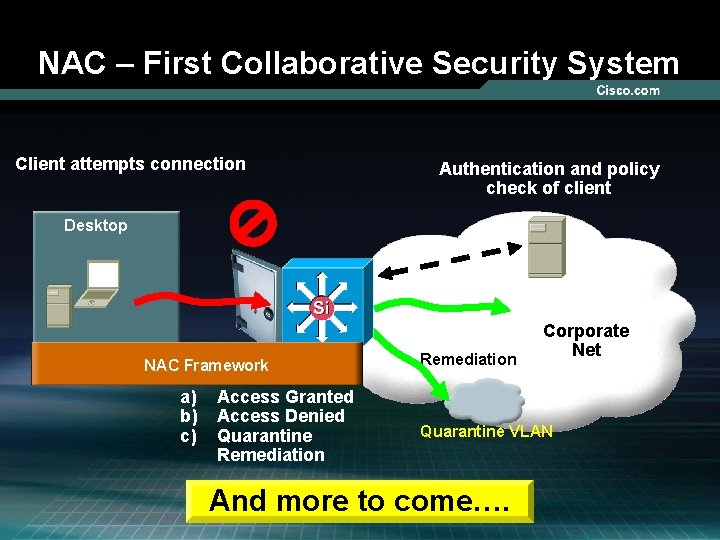
NAC – First Collaborative Security System Client attempts connection Authentication and policy check of client Desktop NAC Framework a) b) c) Access Granted Access Denied Quarantine Remediation Corporate Net Quarantine VLAN And more to come…. © 2005 Cisco Systems, Inc. All rights reserved. 13

Current NAC Program Participants http: //www. cisco. com/en/US/partners/pr 46/nac/partners. html ANTI VIRUS REMEDIATION CLIENT SECURITY © 2005 Cisco Systems, Inc. All rights reserved. 14

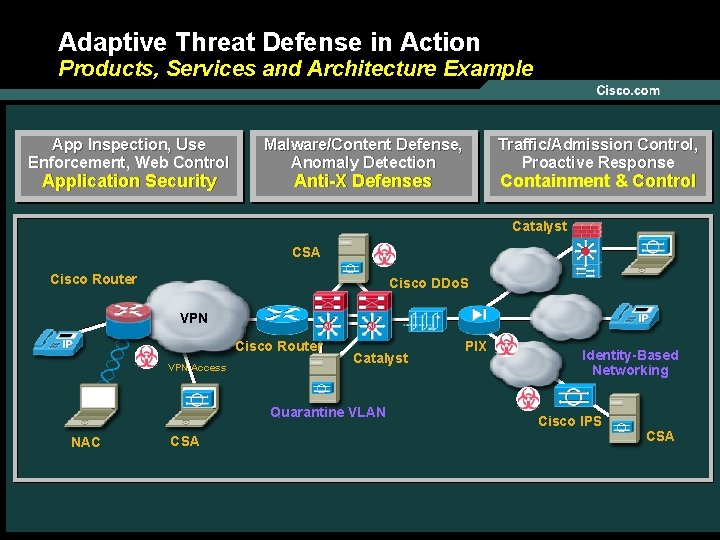
Adaptive Threat Defense in Action Products, Services and Architecture Example App Inspection, Use Enforcement, Web Control Application Security Malware/Content Defense, Anomaly Detection Traffic/Admission Control, Proactive Response Anti-X Defenses Containment & Control Catalyst CSA Cisco Router Cisco DDo. S VPN Cisco Router VPN Access Catalyst Quarantine VLAN NAC CSA © 2005 Cisco Systems, Inc. All rights reserved. PIX Identity-Based Networking Cisco IPS CSA 15

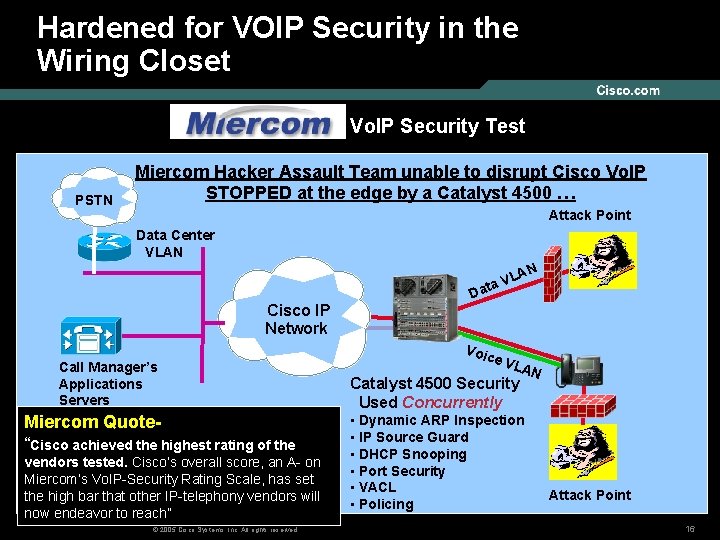
Hardened for VOIP Security in the Wiring Closet Vo. IP Security Test PSTN Miercom Hacker Assault Team unable to disrupt Cisco Vo. IP STOPPED at the edge by a Catalyst 4500 … Attack Point Data Center VLAN N LA V ta Cisco IP Network Call Manager’s Applications Servers Miercom Quote“Cisco achieved the highest rating of the vendors tested. Cisco’s overall score, an A- on Miercom’s Vo. IP-Security Rating Scale, has set the high bar that other IP-telephony vendors will now endeavor to reach” © 2005 Cisco Systems, Inc. All rights reserved. Da Voi ce V L Catalyst 4500 Security Used Concurrently AN • Dynamic ARP Inspection • IP Source Guard • DHCP Snooping • Port Security • VACL • Policing Attack Point 16

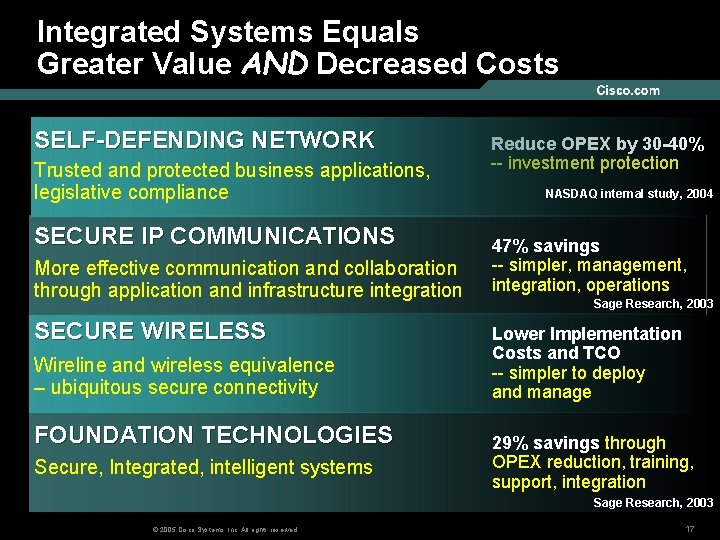
Integrated Systems Equals Greater Value AND Decreased Costs SELF-DEFENDING NETWORK Trusted and protected business applications, legislative compliance SECURE IP COMMUNICATIONS More effective communication and collaboration through application and infrastructure integration SECURE WIRELESS Wireline and wireless equivalence – ubiquitous secure connectivity FOUNDATION TECHNOLOGIES Secure, Integrated, intelligent systems Reduce OPEX by 30 -40% -- investment protection NASDAQ internal study, 2004 47% savings -- simpler, management, integration, operations Sage Research, 2003 Lower Implementation Costs and TCO -- simpler to deploy and manage 29% savings through OPEX reduction, training, support, integration Sage Research, 2003 © 2005 Cisco Systems, Inc. All rights reserved. 17

© 2004 Cisco Systems, Inc. All rights reserved. 18

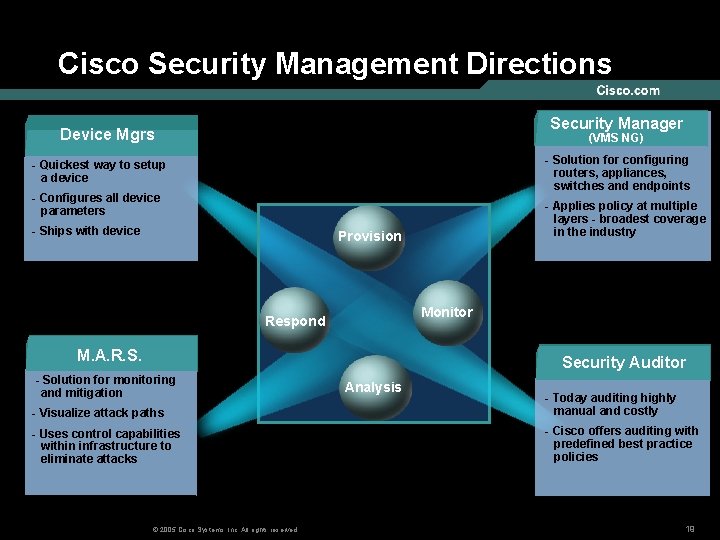
Cisco Security Management Directions Security Manager Device Mgrs (VMS NG) - Solution for configuring routers, appliances, switches and endpoints - Quickest way to setup a device - Configures all device parameters - Ships with device - Applies policy at multiple layers - broadest coverage in the industry Provision Monitor Respond M. A. R. S. Security Auditor - Solution for monitoring and mitigation Analysis - Visualize attack paths - Today auditing highly manual and costly - Uses control capabilities within infrastructure to eliminate attacks - Cisco offers auditing with predefined best practice policies © 2005 Cisco Systems, Inc. All rights reserved. 19

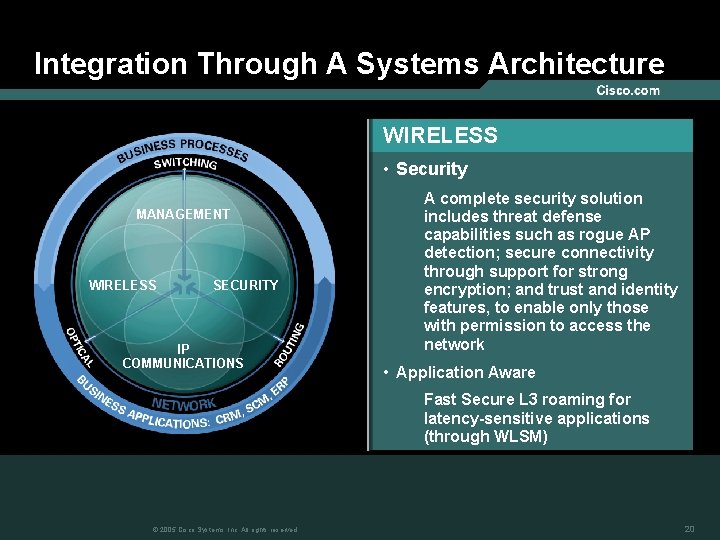
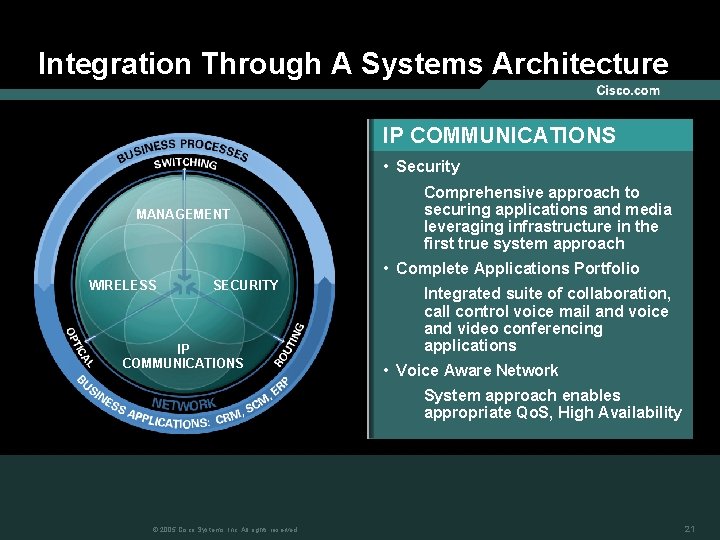
Integration Through A Systems Architecture WIRELESS • Security MANAGEMENT WIRELESS SECURITY IP COMMUNICATIONS A complete security solution includes threat defense capabilities such as rogue AP detection; secure connectivity through support for strong encryption; and trust and identity features, to enable only those with permission to access the network • Application Aware Fast Secure L 3 roaming for latency-sensitive applications (through WLSM) © 2005 Cisco Systems, Inc. All rights reserved. 20

Integration Through A Systems Architecture IP COMMUNICATIONS • Security MANAGEMENT Comprehensive approach to securing applications and media leveraging infrastructure in the first true system approach • Complete Applications Portfolio WIRELESS SECURITY IP COMMUNICATIONS Integrated suite of collaboration, call control voice mail and voice and video conferencing applications • Voice Aware Network System approach enables appropriate Qo. S, High Availability © 2005 Cisco Systems, Inc. All rights reserved. 21

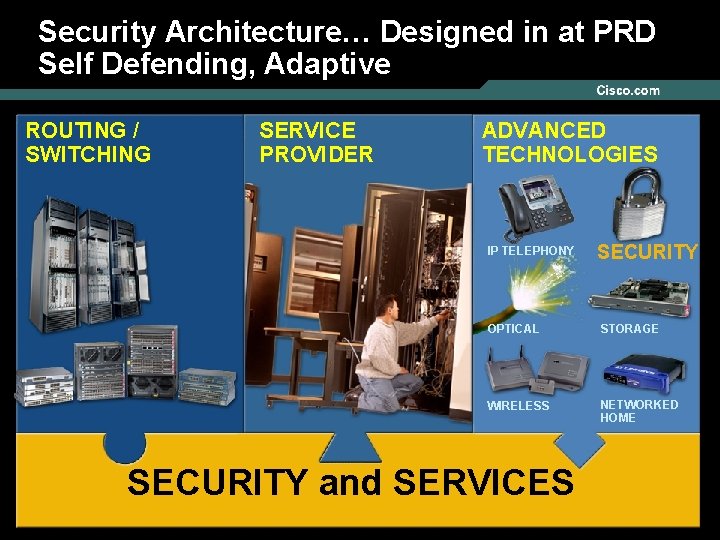
Security Architecture… Designed in at PRD Self Defending, Adaptive ROUTING / SWITCHING SERVICE PROVIDER ADVANCED TECHNOLOGIES IP TELEPHONY SECURITY OPTICAL STORAGE WIRELESS NETWORKED HOME SECURITY and SERVICES © 2005 Cisco Systems, Inc. All rights reserved. 22