Effective Network Planning and Defending Strategies to Minimize
























- Slides: 73

Effective Network Planning and Defending Strategies to Minimize Attackers’ Success Probabilities by Deception and Dynamic Topology Reconfiguration in Cloud Environment 於雲端環境下考量誘捕系統及動態拓樸調整 達到攻擊者成功機率最小化之有效網路建置 與防禦策略 Advisor: Frank, Y. S. Lin Presented by M. Y. Huang

Agenda �Problem description �Mathematical formulation 2020/11/5 OPLab@IM, NTU 2

Agenda �Problem description �Mathematical formulation 2020/11/5 OPLab@IM, NTU 3

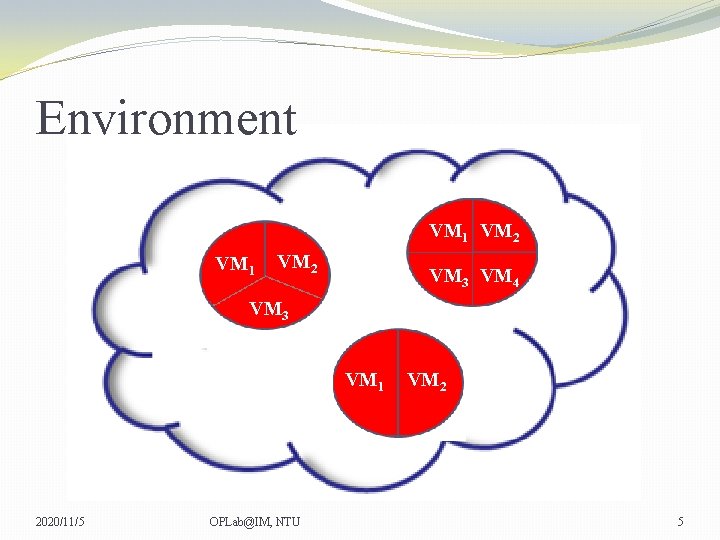
Environment Cloud 2020/11/5 OPLab@IM, NTU 4

Environment VM 1 VM 2 VM 3 VM 4 VM 3 VM 1 2020/11/5 OPLab@IM, NTU VM 2 5

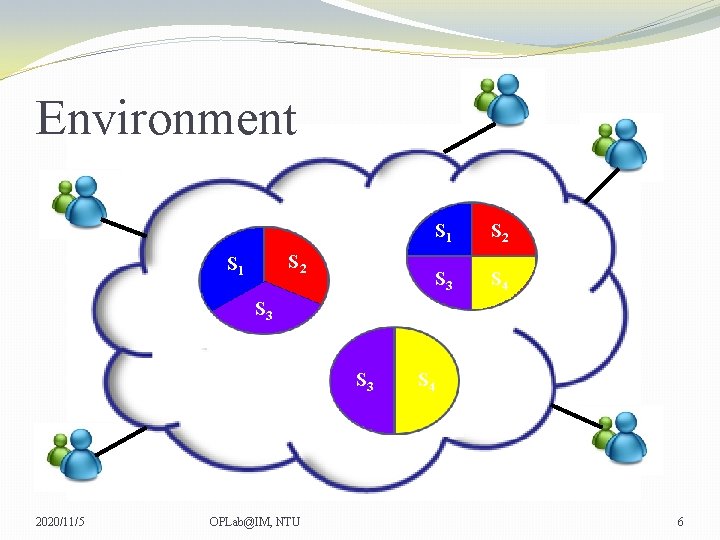
Environment S 2 S 1 S 2 S 3 S 4 S 3 2020/11/5 OPLab@IM, NTU S 4 6

Defender �Defense strategies �Deterrence ─ firewall or other defense mechanisms �Early warning ─ IDS or other detection techniques � Consider false positive and false negative case. � Only deployed on the general nodes. � Nodes that providing service � The defender will be notified as soon as they are compromised. � Honeypot � lower false positive and false negative rate than general nodes with detection techniques. 2020/11/5 OPLab@IM, NTU 7

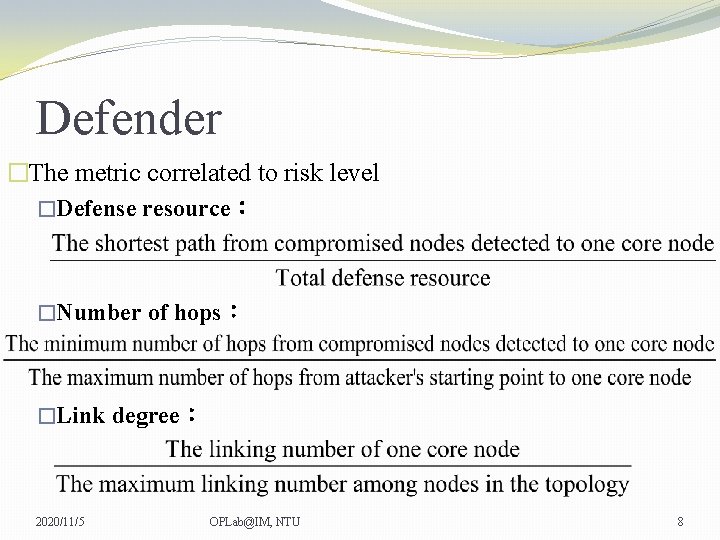
Defender �The metric correlated to risk level �Defense resource: �Number of hops: �Link degree: 2020/11/5 OPLab@IM, NTU 8

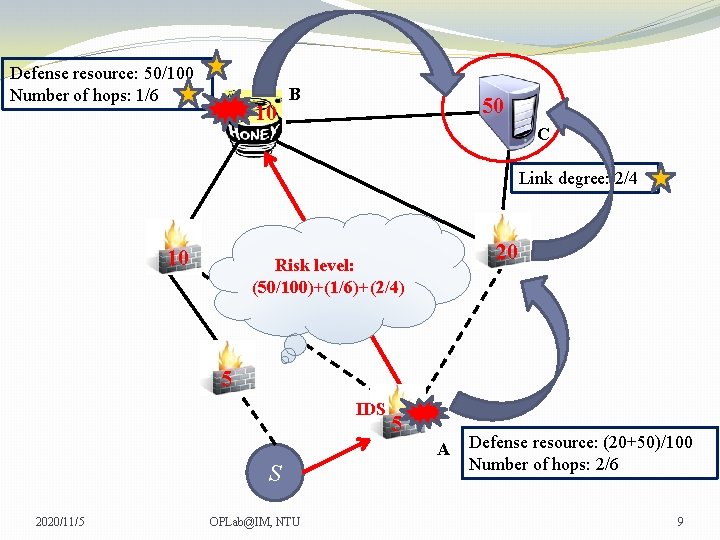
Defense resource: 50/100 Number of hops: 1/6 10 B 50 C Link degree: 2/4 10 20 Risk level: (50/100)+(1/6)+(2/4) 5 IDS 5 A S 2020/11/5 OPLab@IM, NTU Defense resource: (20+50)/100 Number of hops: 2/6 9

Defender � Defense strategies � Deception ─ Honeypots can be equipped with false target and fake traffic generating functions � False target � � � The price is correlated to the interactive capability and the number of simulating services. Distraction ─ honeypots equipped with false target function Fake traffic generator � � The price is correlated to the achievable throughput of fake traffic and the number of simulating services. Misleading ─ honeypots equipped with fake traffic generating function � � 2020/11/5 Distance Direction � The weight of services is determined by the defender. � The price of two functions honeypot is cheaper than buying two single function honeypots. OPLab@IM, NTU 10

Defender �Defense strategies �Resource concentration─ Dynamic Topology Reconfiguration � Choose one candidate node around the risky core node with the minimum defense resource to start the dynamic topology reconfiguration mechanism. � Choose one candidate node around the reconfiguration starting node with the maximum defense resource and which is not the neighbor of the core node. 2020/11/5 OPLab@IM, NTU 11

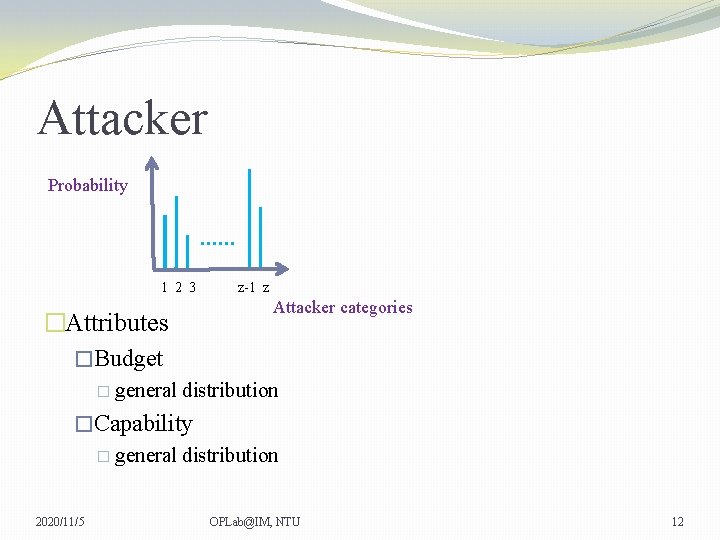
Attacker Probability …… 1 2 3 �Attributes �Budget � general z-1 z Attacker categories distribution �Capability � general distribution 2020/11/5 OPLab@IM, NTU 12

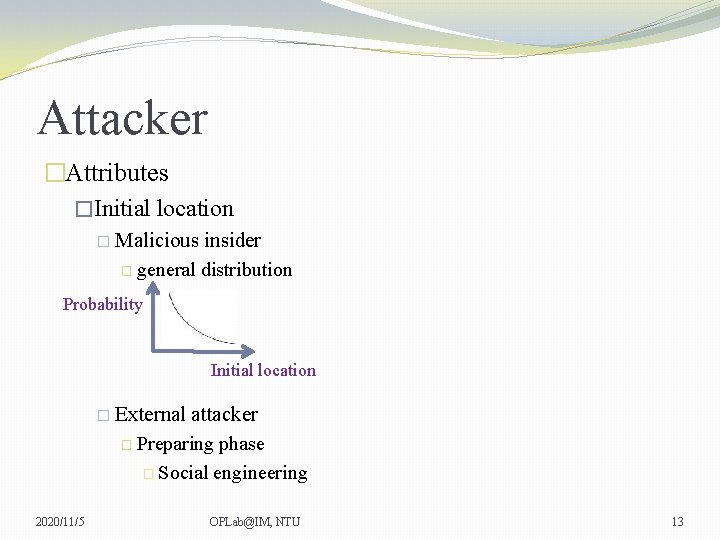
Attacker �Attributes �Initial location � Malicious insider � general distribution Probability Initial location � External attacker � Preparing phase � Social engineering 2020/11/5 OPLab@IM, NTU 13

Attacker �Goals: �Steal sensitive information � Select one or multiple services to compromise � Evaluating criteria of an attacker targeting multiple services is based on each service. � Node that providing service � Lower probability to compromise VMM after seeing through the node is virtualized. � Next hop selection criteria : Maximum defense resource � Minimum defense resource � � Random 2020/11/5 OPLab@IM, NTU 14

Attacker �Goals: �Service disruption � Blind attack � Node that providing service � Higher probability to compromise VMM after seeing through the node is virtualized. � Next hop selection criteria : Prefer higher link utilization :aggressive � Prefer lower link utilization :stealthy � � Random 2020/11/5 OPLab@IM, NTU 15

Attacker �Goals: �Service disruption � Specific target � Single service � multiple services 2020/11/5 � Node that providing service � Higher probability to compromise VMM after seeing through the node is virtualized. � Next hop selection criteria : � The portion of certain service packet � Random OPLab@IM, NTU 16

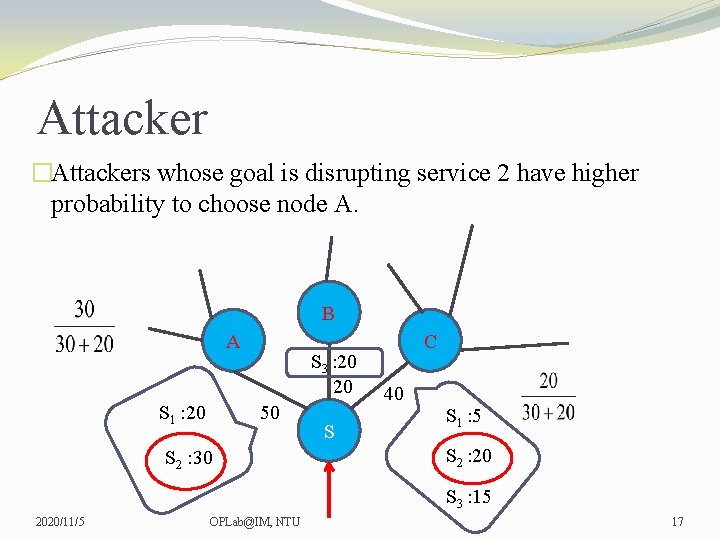
Attacker �Attackers whose goal is disrupting service 2 have higher probability to choose node A. B A S 1 : 20 S 3 : 20 20 50 S 2 : 30 S C 40 S 1 : 5 S 2 : 20 S 3 : 15 2020/11/5 OPLab@IM, NTU 17

Attacker Attacking phase 2020/11/5 OPLab@IM, NTU 18

Attacker �Attackers can see through the VM only when they have penetrated the honeypot. �After seeing through the honeypot, attackers’ may apply one of the following strategies: �False target function � Totally ignore the information from the honeypot. � With higher probability to choose candidate nodes of the honeypot. �Fake traffic generating function � Totally ignore the information from the honeypot. � Reverse the attacking probability of the honeypot indicated. 2020/11/5 OPLab@IM, NTU 19

Attacker �False target and fake traffic generating function � Any function of a honeypot is saw through means the rest function is also saw through. � The probability of seeing through a honeypot with two functions is lower than the single function honeypot. � Totally ignore the information from the honeypot. � Apply single or multiple reaction strategies. 2020/11/5 OPLab@IM, NTU 20

Scenario 2020/11/5 OPLab@IM, NTU 21

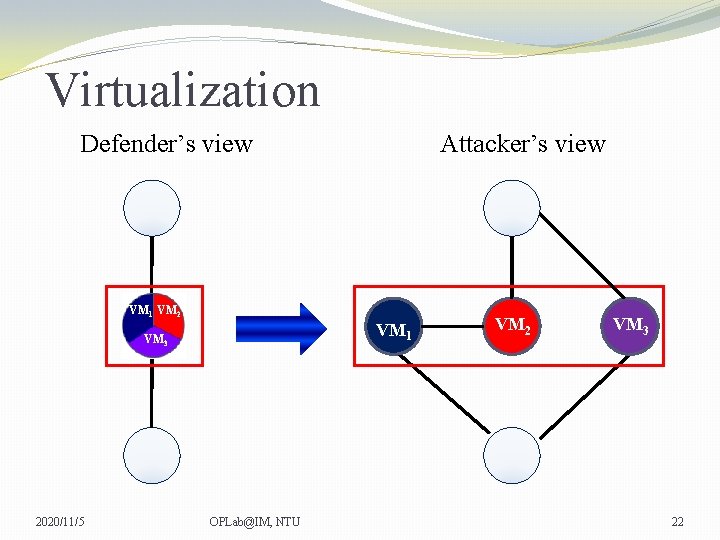
Virtualization Defender’s view Attacker’s view VM 1 VM 2 VM 1 VM 3 2020/11/5 OPLab@IM, NTU VM 2 VM 3 22

VM VM VM 2020/11/5 OPLab@IM, NTU 23

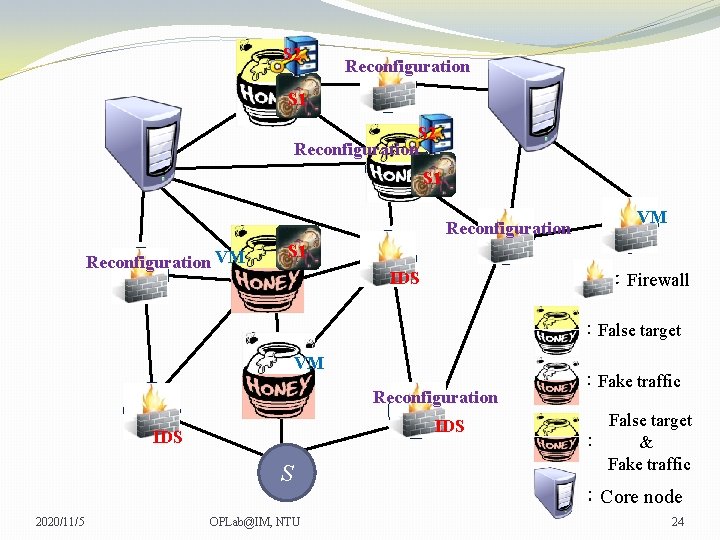
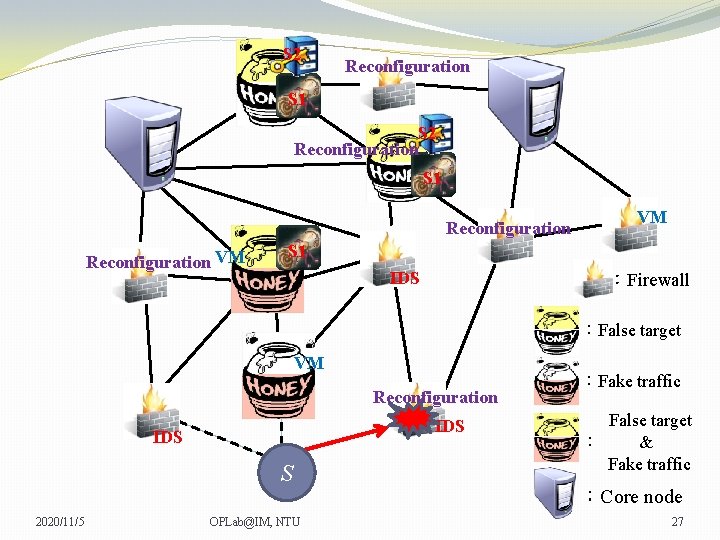
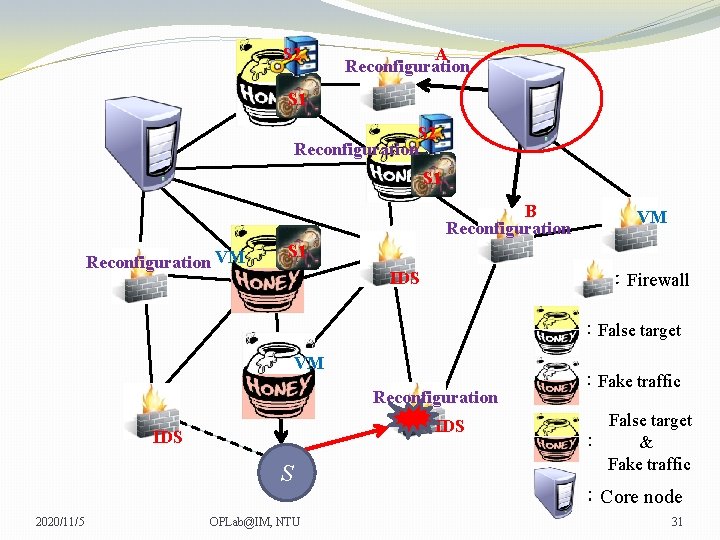
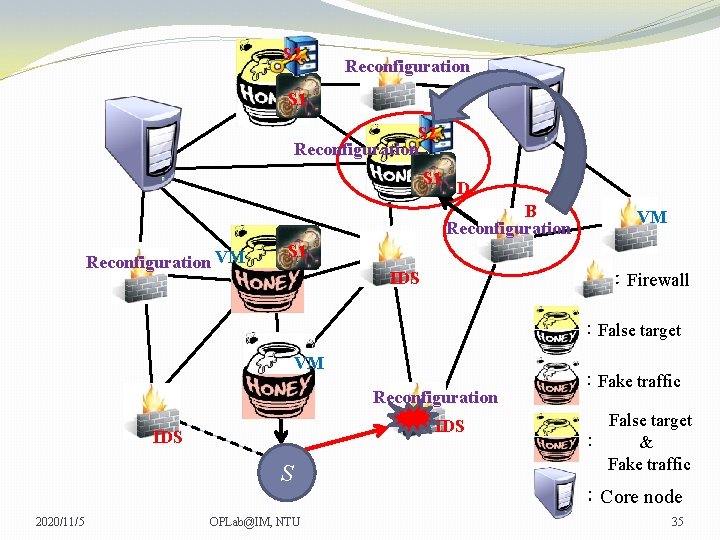
S 2 Reconfiguration S 1 Reconfiguration VM VM VM S 1 VM IDS :Firewall :False target VM VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 24

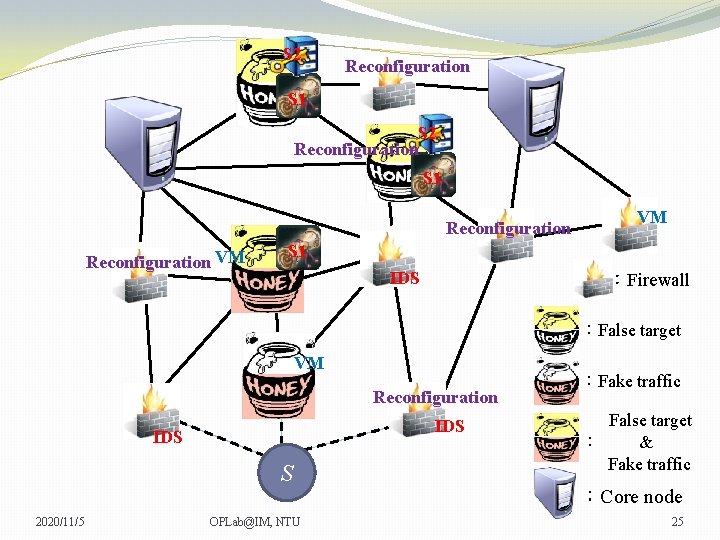
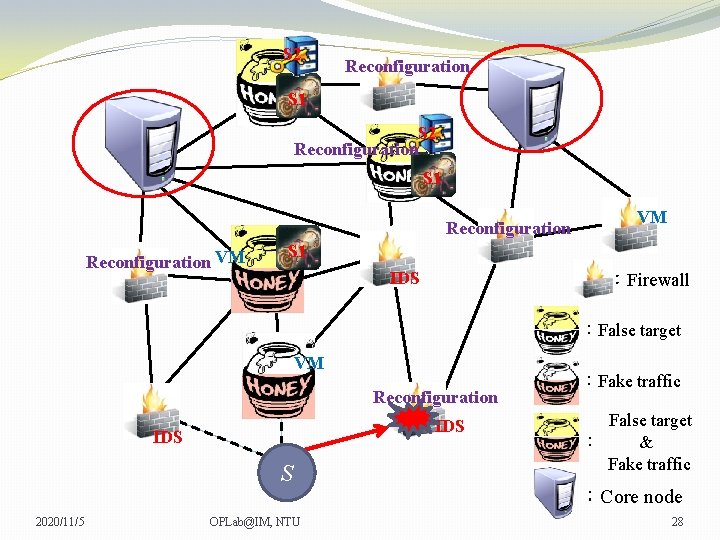
S 2 Reconfiguration S 1 Reconfiguration VM VM VM S 1 IDS :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 25

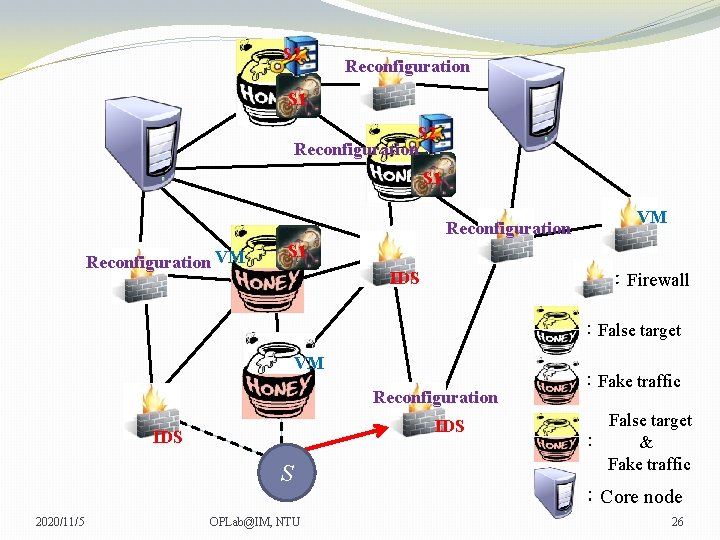
S 2 Reconfiguration S 1 Reconfiguration VM VM VM S 1 IDS :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 26

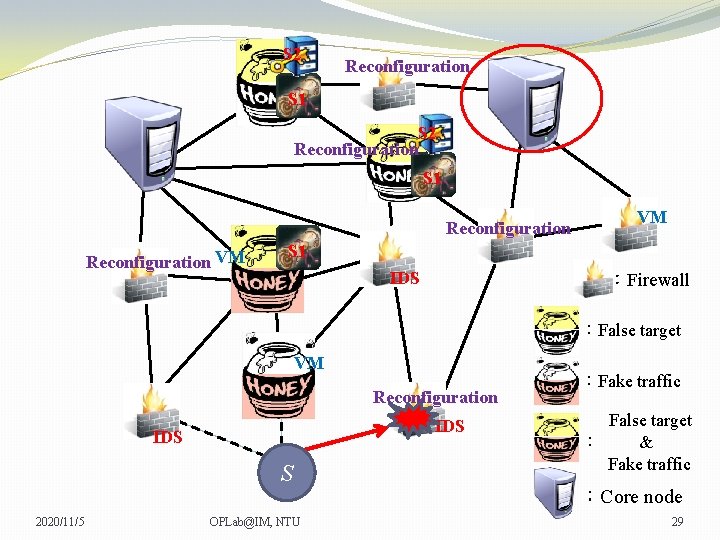
S 2 Reconfiguration S 1 Reconfiguration VM VM VM S 1 IDS :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 27

S 2 Reconfiguration S 1 Reconfiguration VM VM VM S 1 IDS :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 28

S 2 Reconfiguration S 1 Reconfiguration VM VM VM S 1 IDS :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 29

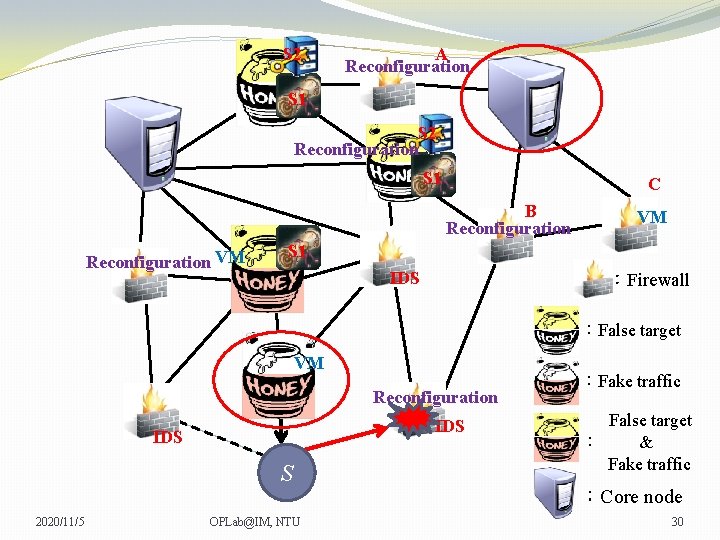
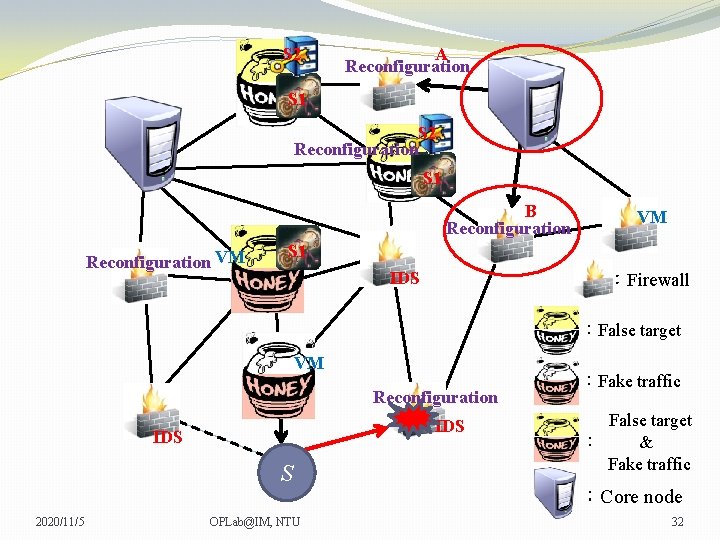
S 2 A Reconfiguration S 1 S 2 Reconfiguration S 1 C B Reconfiguration VM VM VM S 1 IDS :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 30

S 2 A Reconfiguration S 1 S 2 Reconfiguration S 1 B Reconfiguration VM VM VM S 1 IDS :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 31

S 2 A Reconfiguration S 1 S 2 Reconfiguration S 1 B Reconfiguration VM VM VM S 1 IDS :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 32

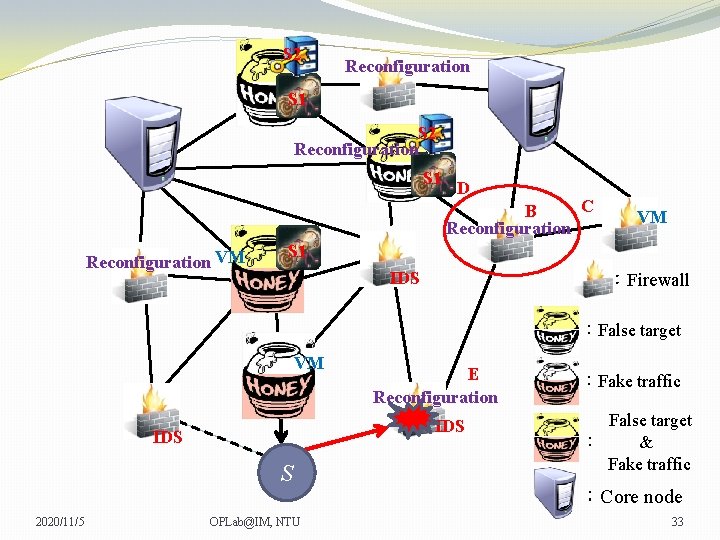
S 2 Reconfiguration S 1 D C B Reconfiguration VM VM VM S 1 IDS :Firewall :False target VM IDS S 2020/11/5 E Reconfiguration OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 33

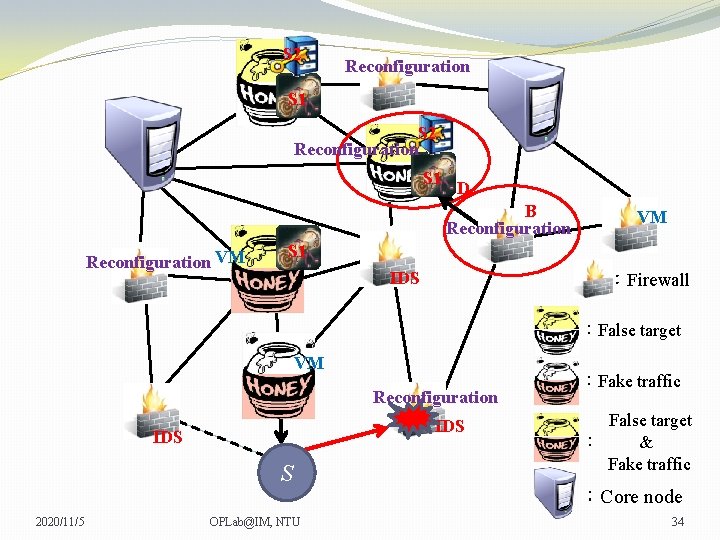
S 2 Reconfiguration S 1 D B Reconfiguration VM VM VM S 1 IDS :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 34

S 2 Reconfiguration S 1 D B Reconfiguration VM VM VM S 1 IDS :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 35

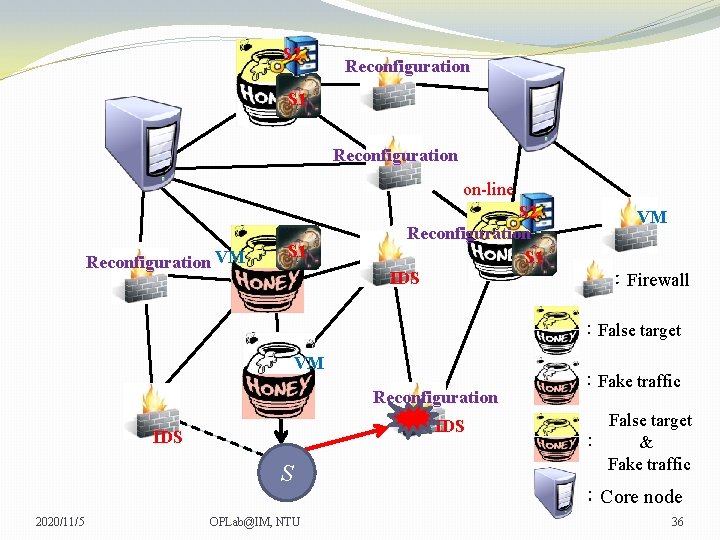
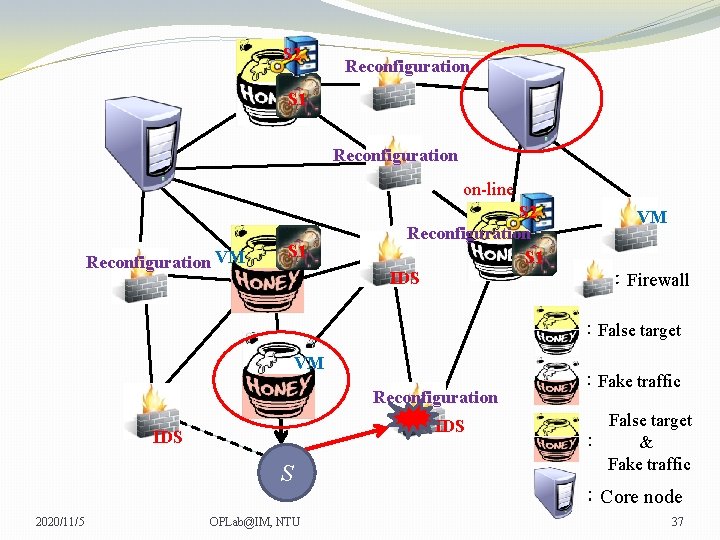
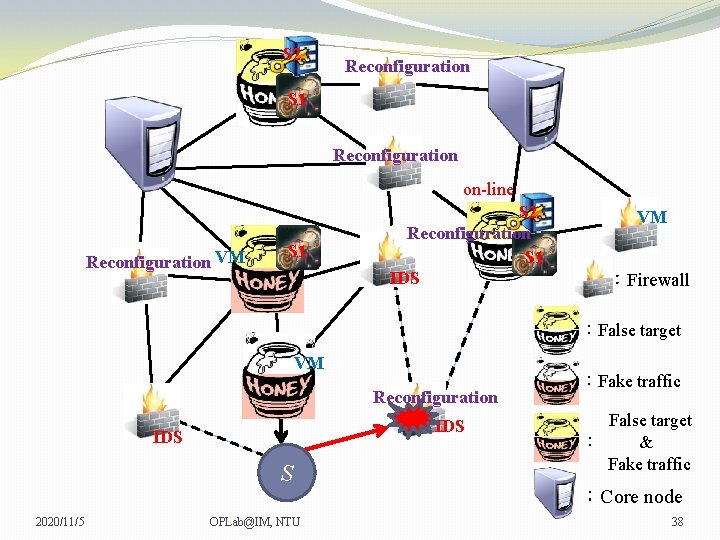
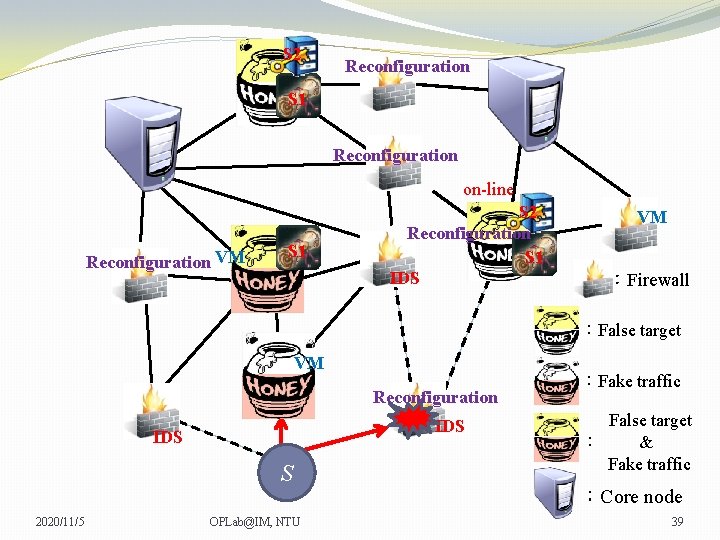
S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 36

S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 37

S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 38

S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 39

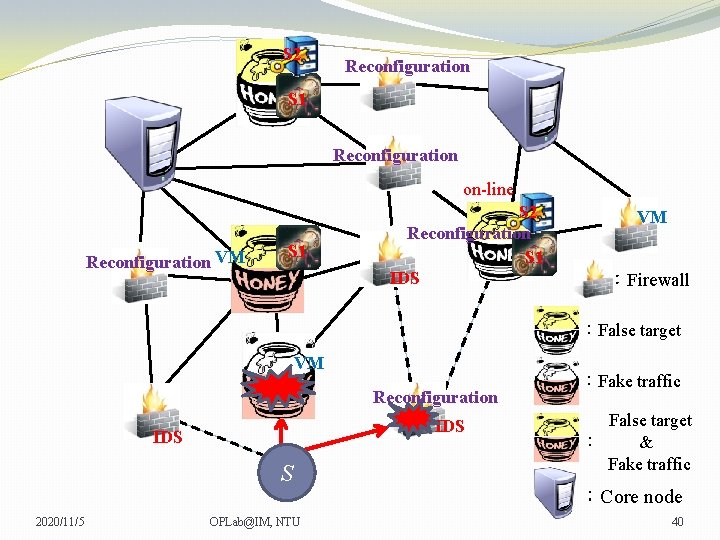
S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 40

S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 41

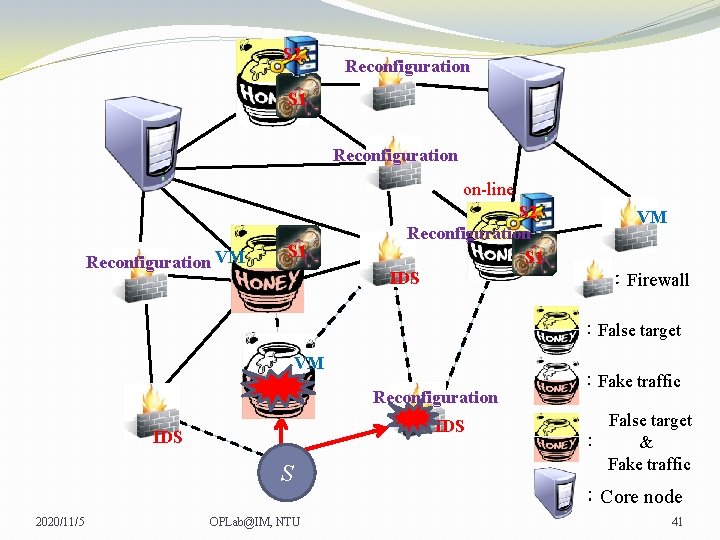
S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 42

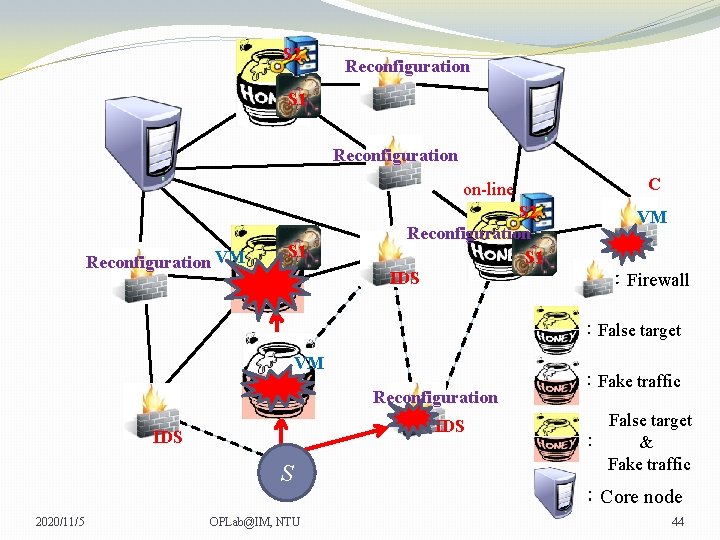
S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 43

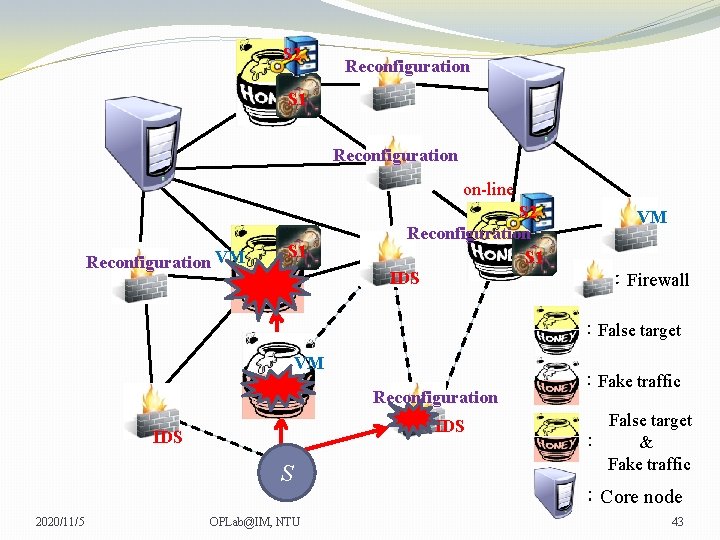
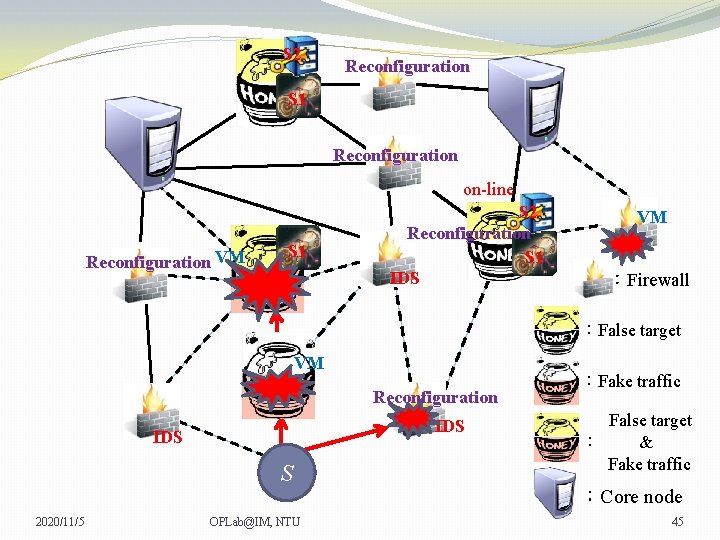
S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS C VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 44

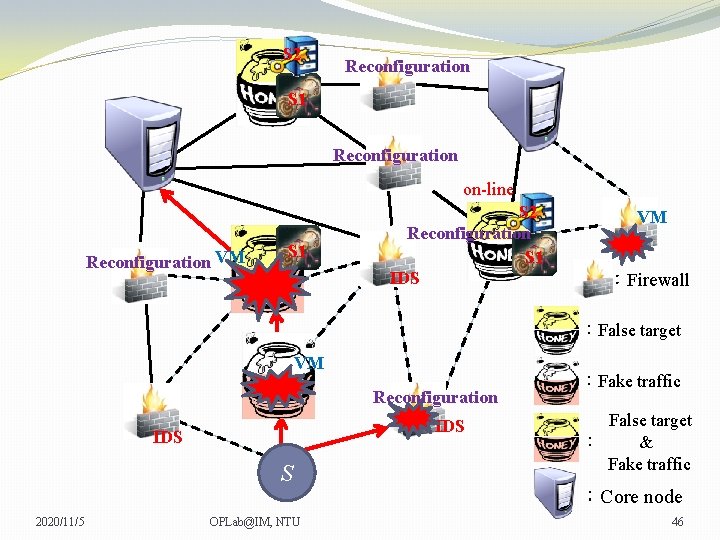
S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 45

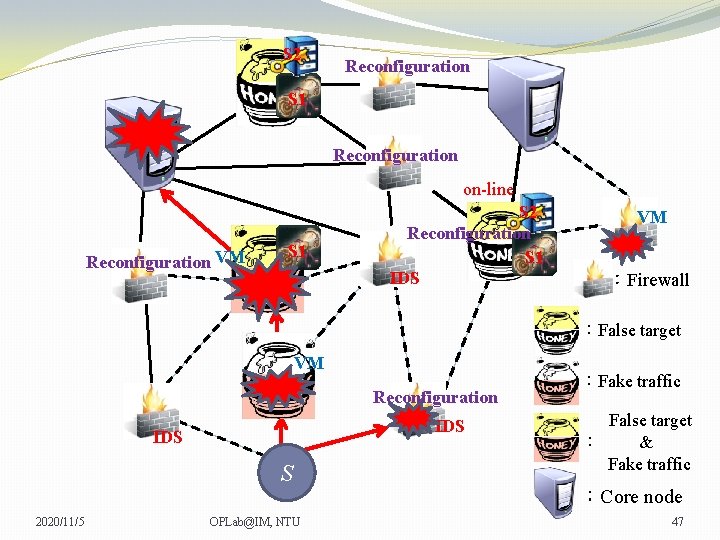
S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 46

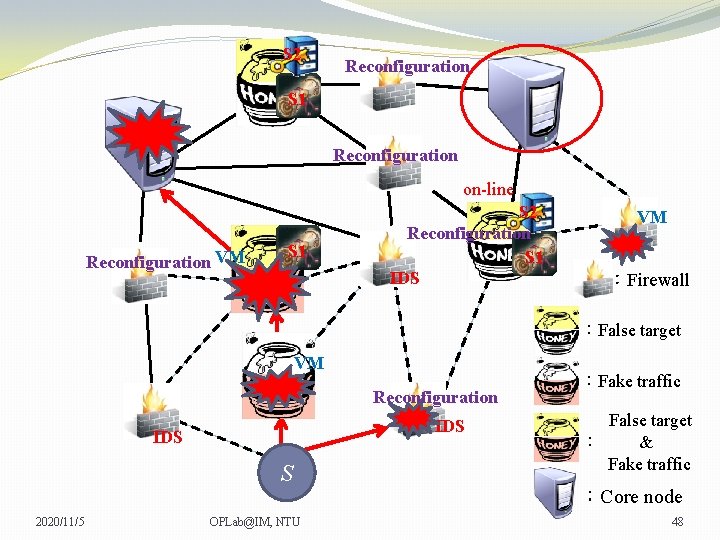
S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 47

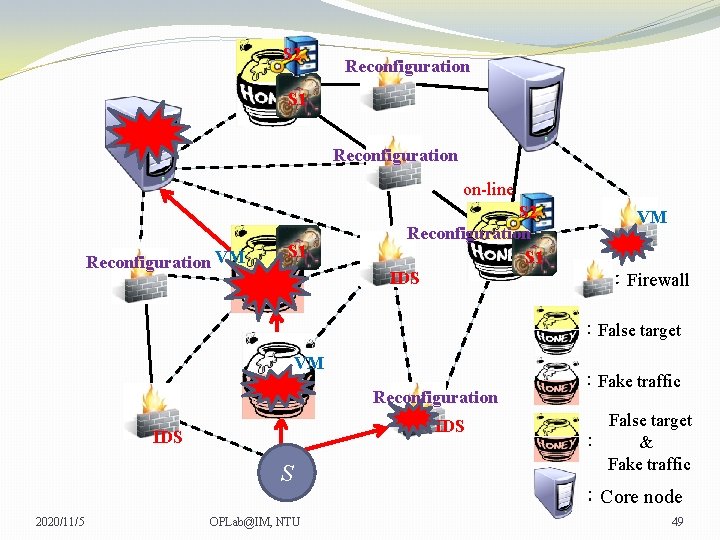
S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 48

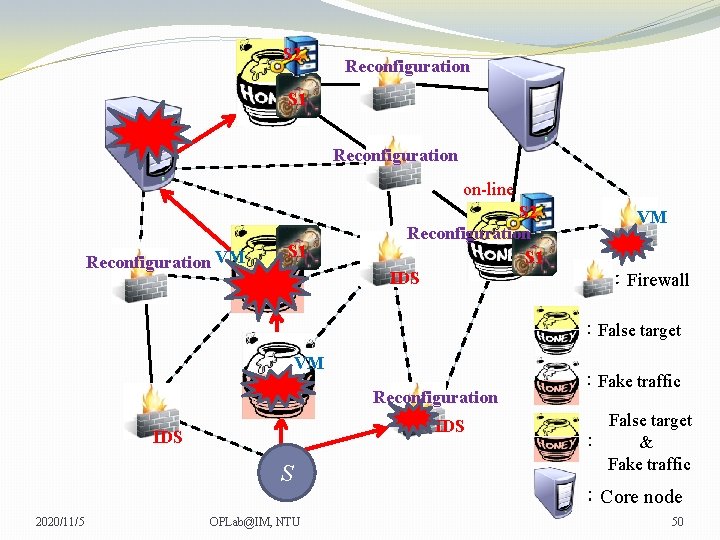
S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 49

S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 50

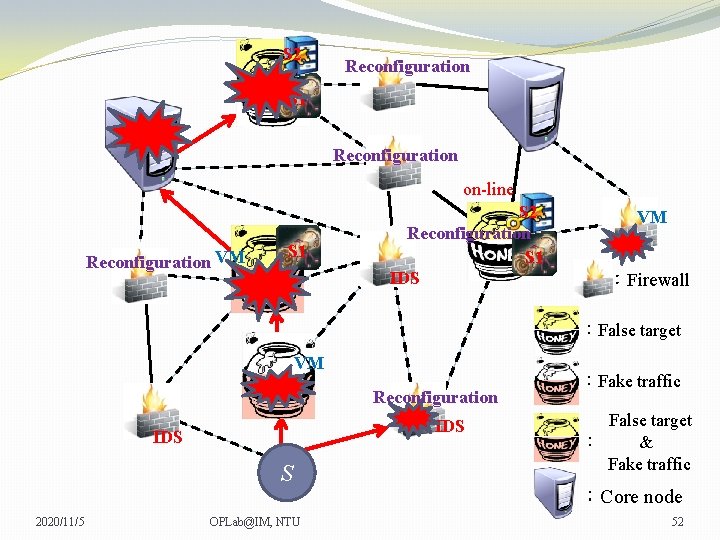
S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 51

S 2 Reconfiguration S 1 Reconfiguration on-line Reconfiguration VM S 1 S 2 Reconfiguration S 1 IDS VM VM :Firewall :False target VM Reconfiguration IDS S 2020/11/5 OPLab@IM, NTU :Fake traffic False target : & Fake traffic :Core node 52

Agenda �Problem description �Mathematical formulation 2020/11/5 OPLab@IM, NTU 53

Assumptions �The defender has complete information about the network, for example, topology, defense resource allocation, node attribute. �Attackers have incomplete information about the network. �There are multiple core nodes providing a service in the network. �Each service has different weight determined by the defender. �One virtual machine only provides one service. �Only malicious nodal attacks are considered. �Evaluate whether the attack is success or not is determined by the Contest Success Function (CSF). �Fake traffic only has one hop effect. 2020/11/5 OPLab@IM, NTU 54

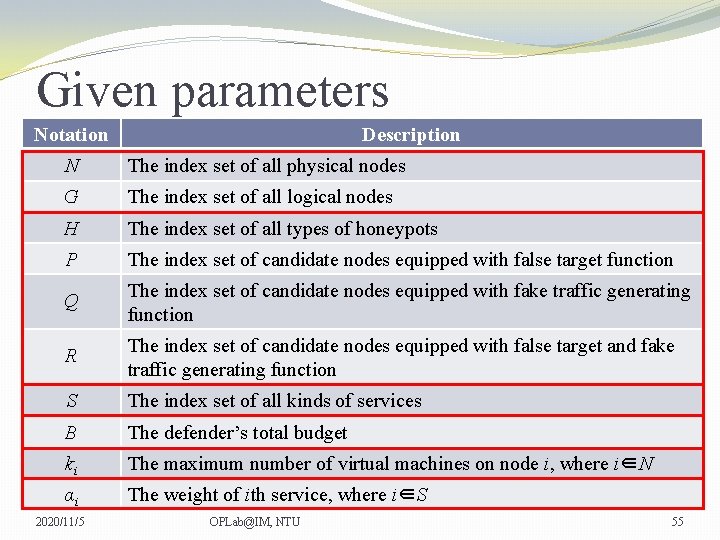
Given parameters Notation Description N The index set of all physical nodes G The index set of all logical nodes H The index set of all types of honeypots P The index set of candidate nodes equipped with false target function Q The index set of candidate nodes equipped with fake traffic generating function R The index set of candidate nodes equipped with false target and fake traffic generating function S The index set of all kinds of services B The defender’s total budget ki The maximum number of virtual machines on node i, where i∈N αi The weight of ith service, where i∈S 2020/11/5 OPLab@IM, NTU 55

Given parameters Notation Description E All possible defense configurations, including defense resource allocation and defending strategies Z All possible attack configurations, including attacker attributes, corresponding strategies and transition rules An attack configuration, including the attributes, corresponding strategies and transition rules of the attacker launches jth attack on ith service, where i∈S, 1≤ j ≤ Fi Fi The total attacking times on ith service for all attackers, where i∈S d The cost of constructing a detection technique to one node r The cost of constructing a reconfiguration function to one node λ The minimum number of hops from core node attackers can start to compromise ci The number of hops from core node category i attacker start to compromise, where i∈Z 2020/11/5 OPLab@IM, NTU 56

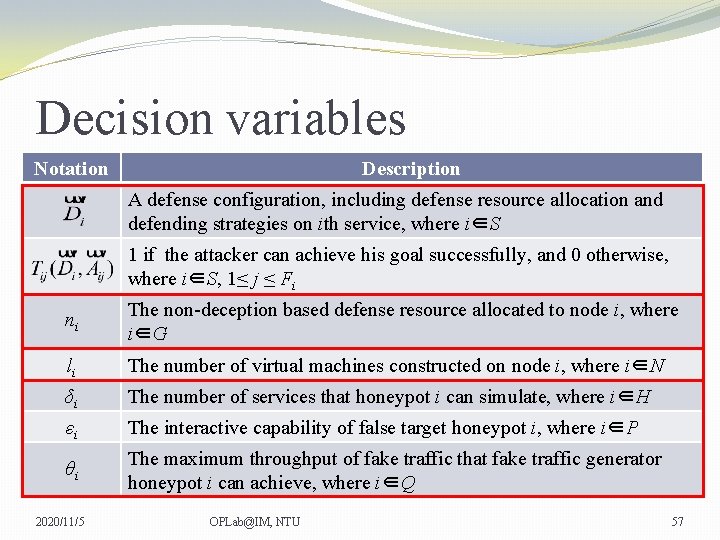
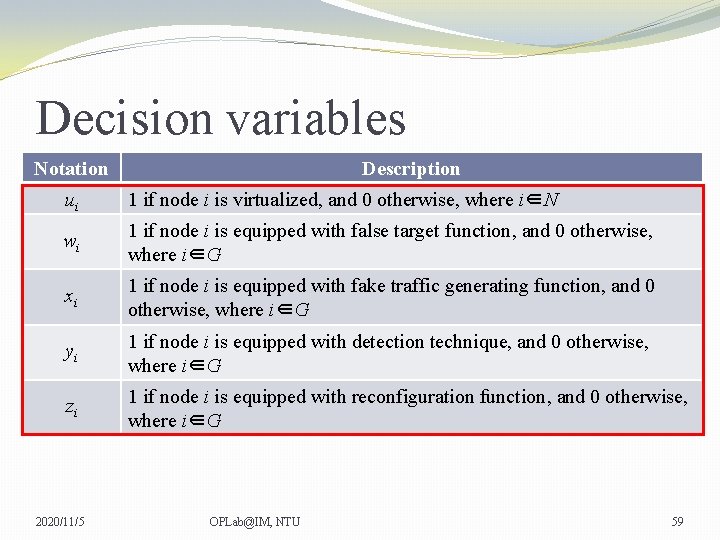
Decision variables Notation Description A defense configuration, including defense resource allocation and defending strategies on ith service, where i∈S 1 if the attacker can achieve his goal successfully, and 0 otherwise, where i∈S, 1≤ j ≤ Fi ni The non-deception based defense resource allocated to node i, where i∈G li The number of virtual machines constructed on node i, where i∈N δi The number of services that honeypot i can simulate, where i∈H εi The interactive capability of false target honeypot i, where i∈P θi The maximum throughput of fake traffic that fake traffic generator honeypot i can achieve, where i∈Q 2020/11/5 OPLab@IM, NTU 57

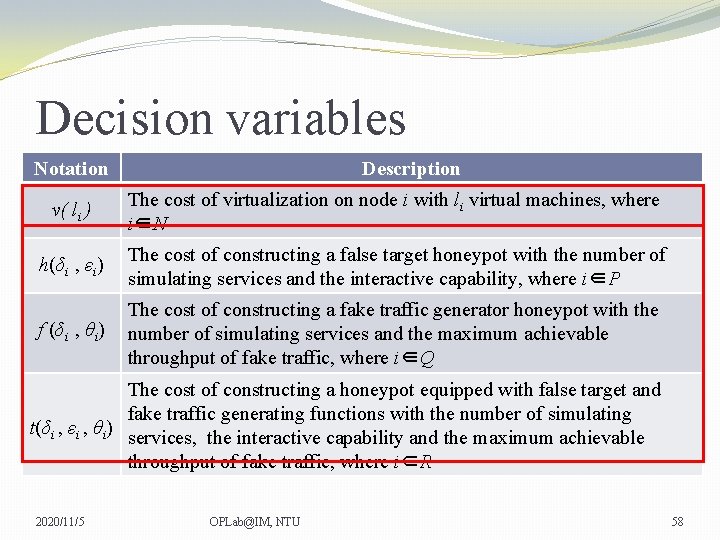
Decision variables Notation Description v( li ) The cost of virtualization on node i with li virtual machines, where i∈N h(δi , εi) The cost of constructing a false target honeypot with the number of simulating services and the interactive capability, where i∈P f (δi , θi) The cost of constructing a fake traffic generator honeypot with the number of simulating services and the maximum achievable throughput of fake traffic, where i∈Q The cost of constructing a honeypot equipped with false target and fake traffic generating functions with the number of simulating t(δi , εi , θi) services, the interactive capability and the maximum achievable throughput of fake traffic, where i∈R 2020/11/5 OPLab@IM, NTU 58

Decision variables Notation Description ui 1 if node i is virtualized, and 0 otherwise, where i∈N wi 1 if node i is equipped with false target function, and 0 otherwise, where i∈G xi 1 if node i is equipped with fake traffic generating function, and 0 otherwise, where i∈G yi 1 if node i is equipped with detection technique, and 0 otherwise, where i∈G zi 1 if node i is equipped with reconfiguration function, and 0 otherwise, where i∈G 2020/11/5 OPLab@IM, NTU 59

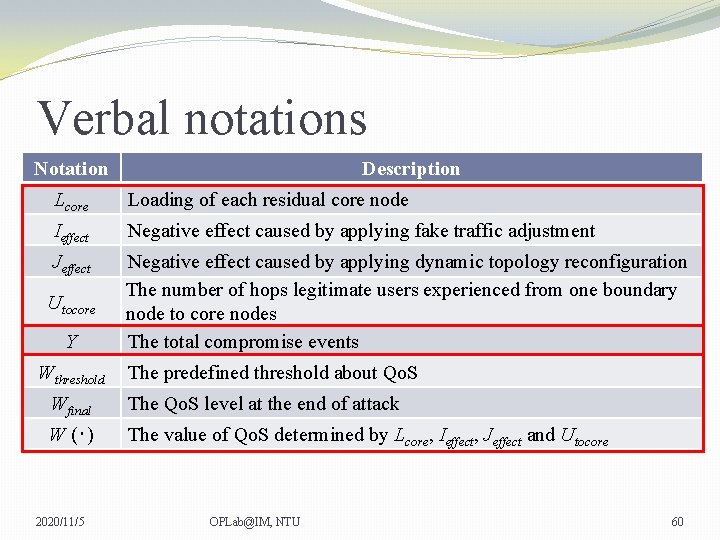
Verbal notations Notation Description Lcore Loading of each residual core node Ieffect Negative effect caused by applying fake traffic adjustment Jeffect Negative effect caused by applying dynamic topology reconfiguration The number of hops legitimate users experienced from one boundary node to core nodes The total compromise events Utocore Y Wthreshold The predefined threshold about Qo. S Wfinal The Qo. S level at the end of attack W (‧) The value of Qo. S determined by Lcore, Ieffect, Jeffect and Utocore 2020/11/5 OPLab@IM, NTU 60

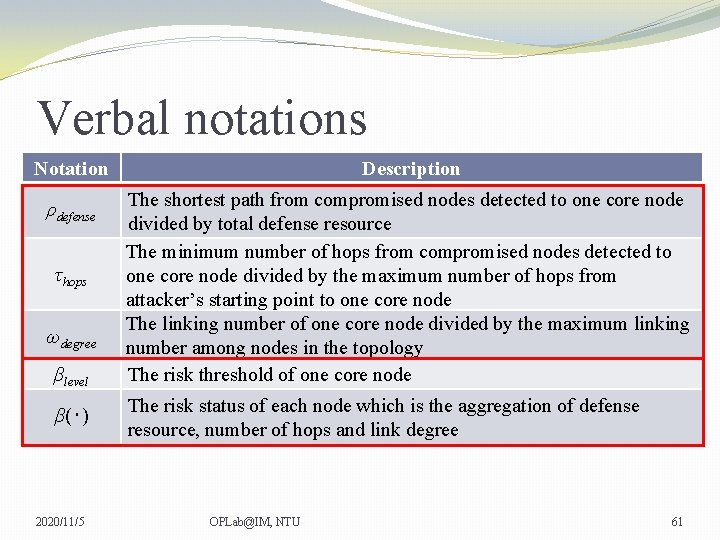
Verbal notations Notation Description ρdefense The shortest path from compromised nodes detected to one core node divided by total defense resource The minimum number of hops from compromised nodes detected to one core node divided by the maximum number of hops from attacker’s starting point to one core node The linking number of one core node divided by the maximum linking number among nodes in the topology The risk threshold of one core node τhops ωdegree βlevel β(‧) 2020/11/5 The risk status of each node which is the aggregation of defense resource, number of hops and link degree OPLab@IM, NTU 61

Objective function (IP 1) 2020/11/5 OPLab@IM, NTU 62

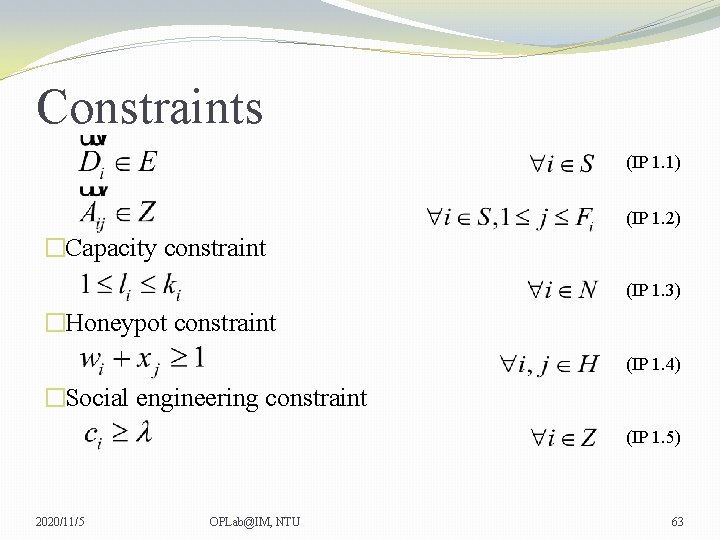
Constraints (IP 1. 1) (IP 1. 2) �Capacity constraint (IP 1. 3) �Honeypot constraint (IP 1. 4) �Social engineering constraint (IP 1. 5) 2020/11/5 OPLab@IM, NTU 63

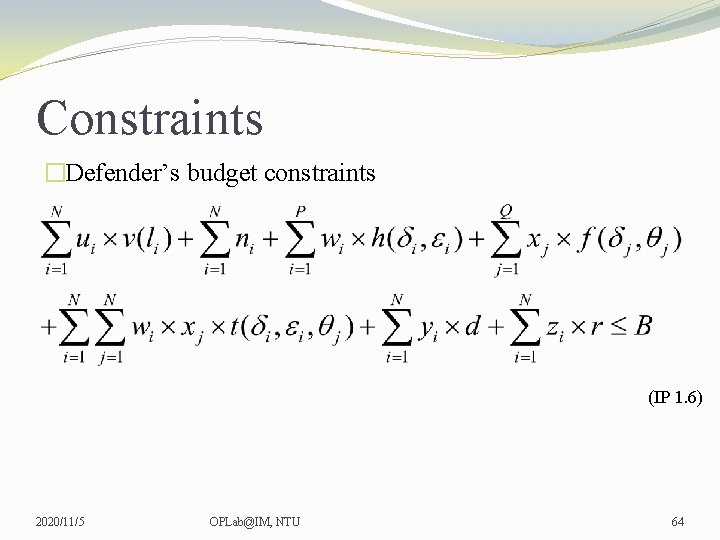
Constraints �Defender’s budget constraints (IP 1. 6) 2020/11/5 OPLab@IM, NTU 64

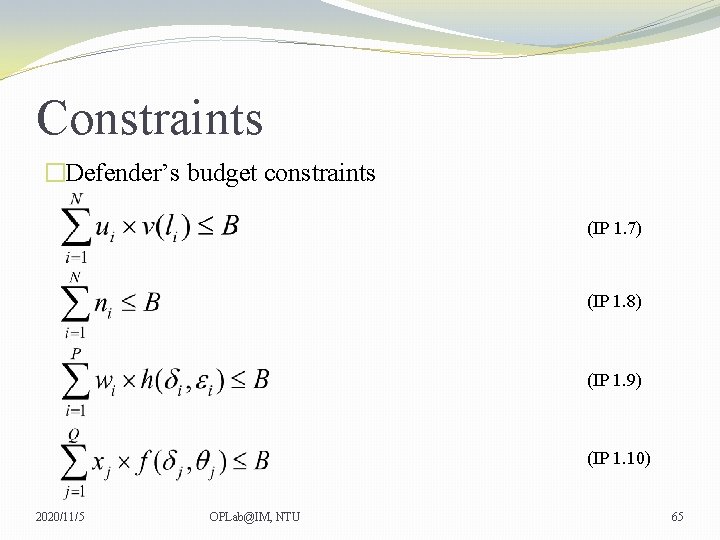
Constraints �Defender’s budget constraints (IP 1. 7) (IP 1. 8) (IP 1. 9) (IP 1. 10) 2020/11/5 OPLab@IM, NTU 65

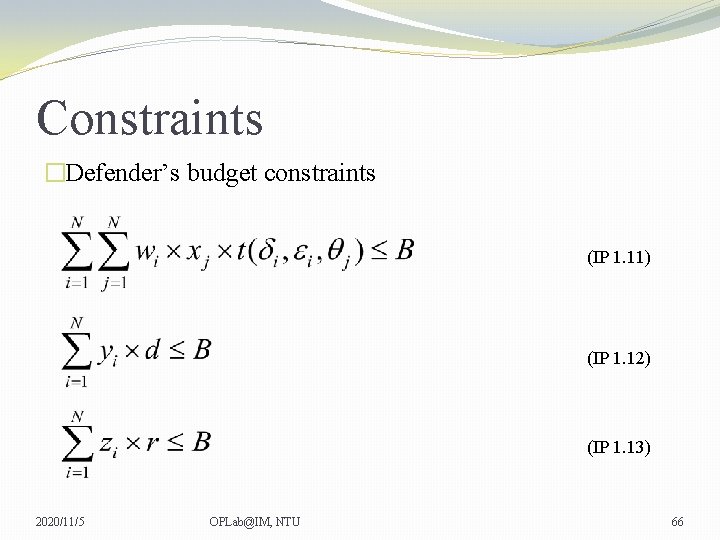
Constraints �Defender’s budget constraints (IP 1. 11) (IP 1. 12) (IP 1. 13) 2020/11/5 OPLab@IM, NTU 66

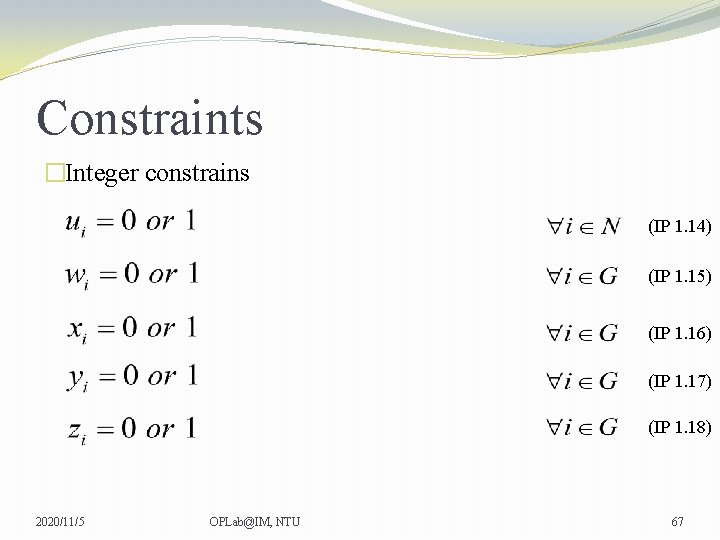
Constraints �Integer constrains (IP 1. 14) (IP 1. 15) (IP 1. 16) (IP 1. 17) (IP 1. 18) 2020/11/5 OPLab@IM, NTU 67

Constraints �Qo. S constraints �Qo. S is a function of : � Core node loading, fake traffic effect, reconfiguration effect, and hops to core node �At the end of attack, the following constraint must be satisfied. (IP 1. 19) �The performance reduction caused by compromised core nodes should not violate IP 1. 19. �The performance reduction caused by fake traffic should not violate IP 1. 19. 2020/11/5 OPLab@IM, NTU (IP 1. 20) (IP 1. 21) 68

Constraints �Qo. S constraints �The performance reduction cause by dynamic topology reconfiguration should not violate IP 1. 19. �Legitimate users’ Qo. S satisfaction with the maximum number of hops from attacking initial point to core node should not violate IP 1. 19. �Wfinal should not lower than Wthreshold at the end of attack. �The defender has to guarantee at least one core node is not compromised at any time. 2020/11/5 OPLab@IM, NTU (IP 1. 22) (IP 1. 23) (IP 1. 24) (IP 1. 25) 69

Constraints �Reconfiguration constraints �For each core node, when , the defender can activate this mechanism. �The reconfiguration initial point and the reconfigured node must be equipped with reconfiguration function. �The reconfiguration initial point must be the neighbor of core node detected risky. �The defense resource of reconfiguration initial point should be the minimum one among all neighbors of core node detected risky. 2020/11/5 OPLab@IM, NTU (IP 1. 26) (IP 1. 27) (IP 1. 28) (IP 1. 29) 70

Constraints �Reconfiguration constraints �The reconfigured node must be the neighbor of reconfiguration initial point. (IP 1. 30) �The reconfigured node must not be the neighbor of core node detected risky. (IP 1. 31) �The defense resource of reconfigured node should be the maximum one among all neighbors of reconfiguration initial node. (IP 1. 32) 2020/11/5 OPLab@IM, NTU 71

Constraints �Traffic adjustment constraints �For each core node, when , the defender can activate this mechanism. �The honeypot must be equipped with fake traffic generating function. �The fake traffic generating honeypot must be one hop away from one of the compromised nodes detected. �The throughput of fake traffic delivered by one fake traffic generating honeypot should not greater than the maximum achievable throughput. 2020/11/5 OPLab@IM, NTU (IP 1. 33) (IP 1. 34) (IP 1. 35) (IP 1. 36) 72

Thanks for your listening 2020/11/5 OPLab@IM, NTU 73
 Advantages of self defending networks
Advantages of self defending networks Cisco self defending network
Cisco self defending network Attacking a castle
Attacking a castle Why is it important to defend your faith
Why is it important to defend your faith Defending and non defining relative clauses
Defending and non defining relative clauses Effective training systems strategies and practices
Effective training systems strategies and practices Was magellan worth defending?
Was magellan worth defending? What is maycombs usual disease
What is maycombs usual disease Defending the faith verses
Defending the faith verses Covetous antisocial
Covetous antisocial Defending sola scriptura
Defending sola scriptura Firm level consequences of market globalization
Firm level consequences of market globalization 10 effective dap teaching strategies
10 effective dap teaching strategies Interpersonal communication chapter 6
Interpersonal communication chapter 6 Effective academic advising strategies
Effective academic advising strategies 4500/800000
4500/800000 Don't care condition in k map
Don't care condition in k map Maximize learning opportunities
Maximize learning opportunities Savchgobj
Savchgobj Minimize dfa
Minimize dfa Minimize dfa
Minimize dfa Waiting lines operations management
Waiting lines operations management Advantages and disadvantages of aggregate planning
Advantages and disadvantages of aggregate planning Process of preparing effective business message
Process of preparing effective business message Principles of effective planning
Principles of effective planning Sales and operations planning
Sales and operations planning Aggregate planning strategies in supply chain management
Aggregate planning strategies in supply chain management Level chase and hybrid strategies
Level chase and hybrid strategies Aggregate planning strategies
Aggregate planning strategies Department strategic plan
Department strategic plan Inactivism planning
Inactivism planning Short medium and long term planning in education
Short medium and long term planning in education Language planning slideshare
Language planning slideshare Virtual circuit network uses
Virtual circuit network uses Features of peer to peer network and client server network
Features of peer to peer network and client server network Network centric computing
Network centric computing Strategic planning vs tactical planning
Strategic planning vs tactical planning Goal achievement matrix
Goal achievement matrix Role segmentation workforce planning
Role segmentation workforce planning Perencanaan agregat ppt
Perencanaan agregat ppt List the strategic objectives of aggregate planning
List the strategic objectives of aggregate planning Examples of aggregate planning
Examples of aggregate planning Simbol network planning
Simbol network planning Simbol anak panah putus-putus dalam network planning adalah
Simbol anak panah putus-putus dalam network planning adalah Planning a wireless network
Planning a wireless network Network planning techniques
Network planning techniques Network planning proyek
Network planning proyek Planning a network upgrade
Planning a network upgrade Planning phase for network security design
Planning phase for network security design Hierarchical task network planning
Hierarchical task network planning Topology in computer
Topology in computer Network systems design using network processors
Network systems design using network processors Circuit switched vs packet switched
Circuit switched vs packet switched Systematic arrangement
Systematic arrangement Explicit instruction effective and efficient teaching
Explicit instruction effective and efficient teaching Steps in designing hrd programs
Steps in designing hrd programs Listening objectives
Listening objectives Speaking and listening: effective group discussions
Speaking and listening: effective group discussions Ineffective praise examples
Ineffective praise examples Effective support for children and families in essex
Effective support for children and families in essex Communication theories in health and social care
Communication theories in health and social care System integration plan
System integration plan Maritime energy conservation
Maritime energy conservation Therblig
Therblig Bed making position
Bed making position Effective body mechanics and bed making
Effective body mechanics and bed making To establish effective short- and long-term goals ____.
To establish effective short- and long-term goals ____. Effective salespeople anticipate and handle
Effective salespeople anticipate and handle Types of bed making
Types of bed making Effective teaching evidence and practice
Effective teaching evidence and practice Calculate the effective resistance between a and b
Calculate the effective resistance between a and b The effective capacitance between a and b is
The effective capacitance between a and b is Effective group discussion defines human communication as
Effective group discussion defines human communication as Designing and developing effective hrd programs
Designing and developing effective hrd programs