MINIMIZE SECRETS ECONOMY OF MECHANISM MINIMIZE SECRETS ONLY










- Slides: 11

MINIMIZE SECRETS & ECONOMY OF MECHANISM

MINIMIZE SECRETS

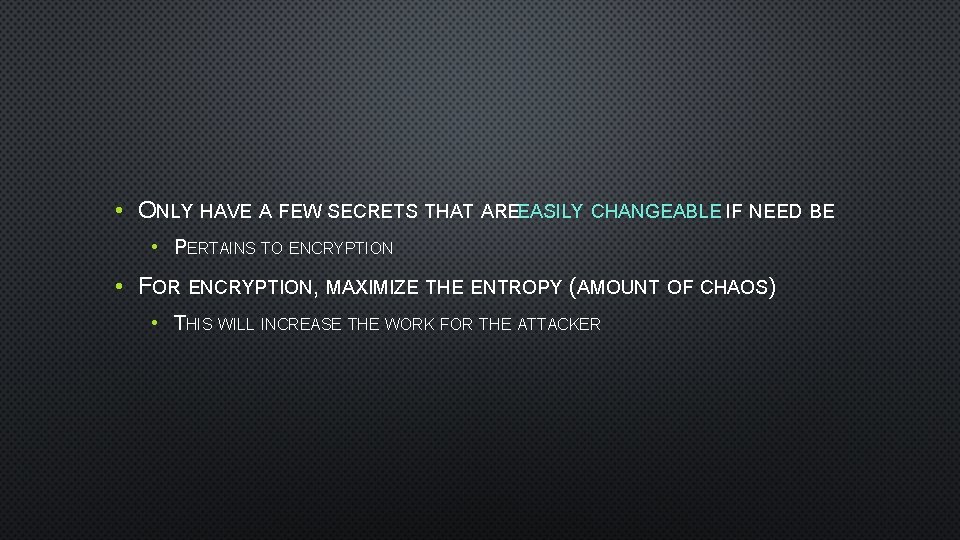
• ONLY HAVE A FEW SECRETS THAT AREEASILY CHANGEABLE IF NEED BE • PERTAINS TO ENCRYPTION • FOR ENCRYPTION, MAXIMIZE THE ENTROPY (AMOUNT OF CHAOS) • THIS WILL INCREASE THE WORK FOR THE ATTACKER

• THE SECRETS PROBABLY WON’T BE SECRET FOR LONG ANYWAY SO MAKE IT EASIER TO CHANGE THE SECRETS IN CASE THE DATA GETS COMPROMISED • HAVING SEVERAL SECRETS WILL INCREASE ADMINISTRATIVE BURDEN AS WELL • THUS, THE FEW SECRETS YOU HAVE SHOULD FOCUS ON DIFFERENTIATING PEOPLE WHO ARE ATTACKING WITH PEOPLE WHO ARE GOOD • EVERYTHING ELSE SHOULD BE PUBLIC

ECONOMY OF MECHANISM

ECONOMY OF MECHANISM PRINCIPLE MEANS SECURITY MECHANISMS SHOULD BE AS SIMPLE AS POSSIBLE. • KEEPING IT SIMPLE MEANS FEWER COMPONENTS AND CASES TO TEST. • COMPLEX SECURITY MECHANISMS TEND TO MAKE ASSUMPTIONS ABOUT THE SYSTEM WHICH OFTEN LEADS TO VULNERABILITIES.

• COMPLEX MECHANISMS CAN BE INCORRECTLY: • UNDERSTOOD • CONFIGURED • IMPLEMENTED • BY KEEPING THE SECURITY MECHANISM SIMPLE IN DESIGN AND IMPLEMENTATION, IT IS EASIER TO TEST, ANALYZE, AND VERIFY • FLAWS IN THE PROGRAM ARE MORE EASILY DETECTED WHEN THE CODE IS SMALLER • A SMALL SECURITY KERNEL CAN BE VALIDATED • SECURITY KERNEL IMPLEMENTS THE ACCESS CONTROL POLICY • SIMPLER MEANS LESS CAN GO WRONG WHEREAS COMPLEXITY MEANS MORE VULNERABILITIES TO EXPLOIT

EXAMPLE: IPSEC (INTERNET PROTOCOL SECURITY) • IPSEC IS A FRAMEWORK FOR NETWORK PROTOCOLS INVOLVED IN SECURITY BY AUTHENTICATING AND ENCRYPTING PACKETS OF DATA AKA ( KA A SECURITY MECHANISM) A • DUE TO THE COMPLEXITY OF THEIPSEC SPECIFICATION, BUGS AND PARTIAL IMPLEMENTATIONS ARE COMMONLY PRESENT • SO WHY IS THIS STILL USED? • COMPATIBLE WITH SEVERAL HARDWARE DEVICES • CHEAP/BUDGET-FRIENDLY FOR COMPANIES

EXAMPLE: HTTP REQUEST SMUGGLING • AN ATTACK BETWEEN TWO HTTP DEVICES TO SMUGGLE A REQUEST TO THE SECOND DEVICE FROM THE FIRST DEVICE • THE ATTACKER WILL SEND ONE SET OF REQUESTS TO THE FIRST DEVICE AND ANOTHER SET TO THE SECOND DEVICE • THIS WILL ENABLE SEVERAL EXPLOITATIONS TO BE TAKEN ADVANTAGE OF SUCH AS PARTIAL CACHE POISONING AND BYPASSING THE FIREWALL

HOW TO IMPLEMENT ECONOMY OF MECHANISM • AVOID COMPLEX SECURITY MECHANISMS IF A SIMPLER ONE WILL DO THE JOB • AVOID COMPLEX DATA MODELS AND UNNEEDED COMPLEX OPERATIONS • BASICALLY, AVOID COMPLEXITY

THINGS TO READ • MORE IN-DEPTH INFO ON ECONOMY OF MECHANISM (OPTIONAL) • HTTPS: //WWW. US-CERT. GOV/BSI/ARTICLES/KNOWLEDGE/PRINCIPLES/ECONOMY-OF-MECHANISM • REAL WORLD VULNERABILITY IN IPSEC HTTP: //WWW. PCWORLD. COM/ARTICLE/3032497/CRITICAL-VPN-KEY-EXCHANGE-FLAWEXPOSES-CISCO-SECURITY-APPLIANCES-TO-REMOTE-HACKING. HTML