Cryptanalysis of and improvement on the HwangChen multiproxy














- Slides: 28

Cryptanalysis of and improvement on the Hwang–Chen multi-proxy multi-signature schemes Yuh-Dauh Lyuu, Ming-Luen Wu 報告者: 資碩一 林士正 1

Outline • • • Introduction Review of the Hwang–Chen schemes Insider attack Modifications to foil the attack Discussions 2

Introduction • A proxy signature scheme allows an authorized person called the proxy signer to sign messages on behalf of the original signer. • Hwang and Chen proposed a new type of group-oriented proxy signature scheme called multi-proxy multi-signature scheme. 3

multi-proxy multi-signature scheme(1/2) • only the cooperation of all the members in the original signer group can authorize a proxy signer group. • only the cooperation of all the members in the proxy signer group can sign messages. 4

multi-proxy multi-signature scheme(2/2) • The original signers and proxy signers all cooperate to create a proxy certificate. • Afterwards, the proxy certificate enables the proxy signers to work together in generating the multi-proxy multi-signatures of any messages. 5

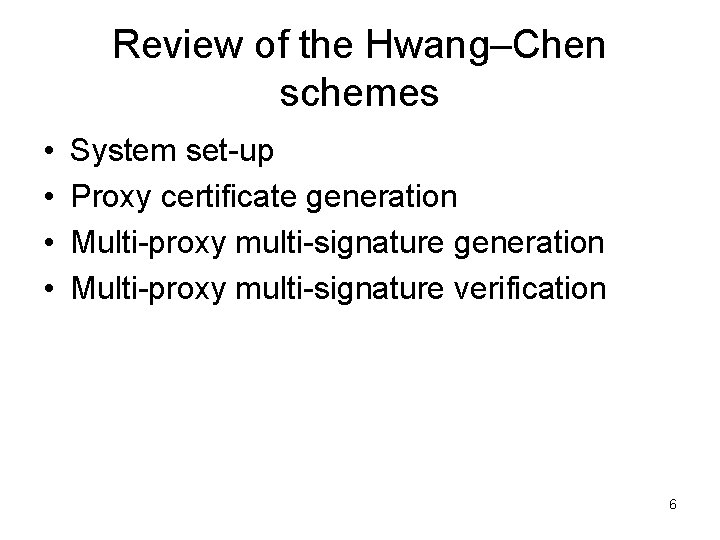
Review of the Hwang–Chen schemes • • System set-up Proxy certificate generation Multi-proxy multi-signature verification 6

System set-up 7

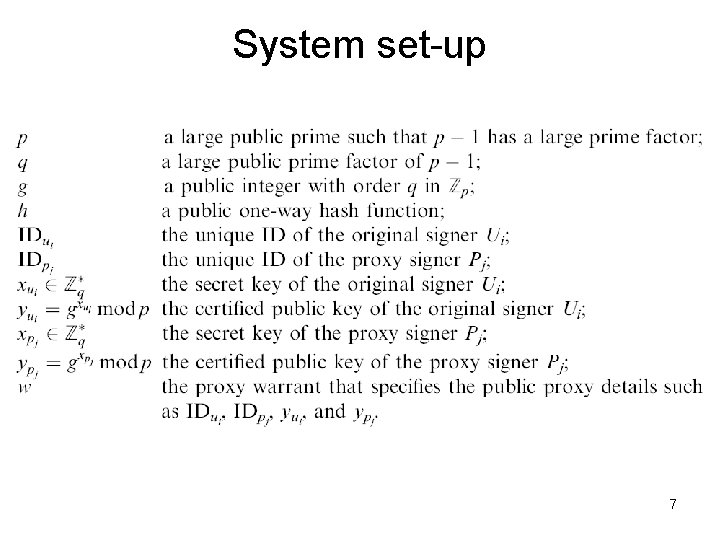
Proxy certificate generation(1/2) 8

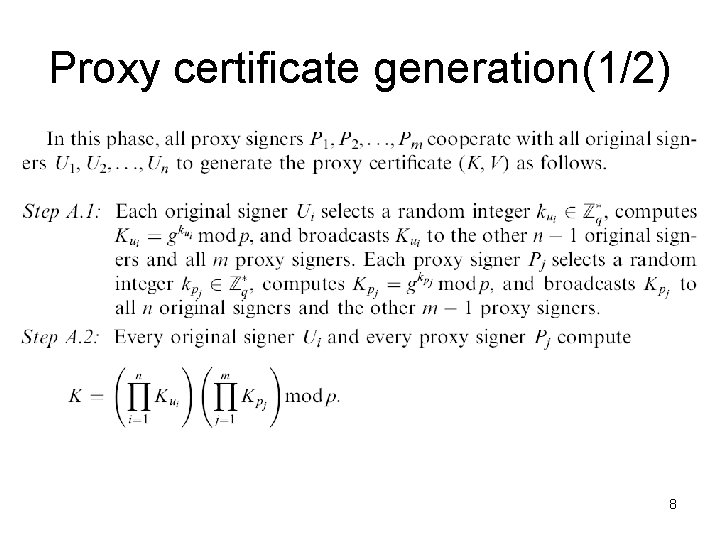
Proxy certificate generation(2/2) 9

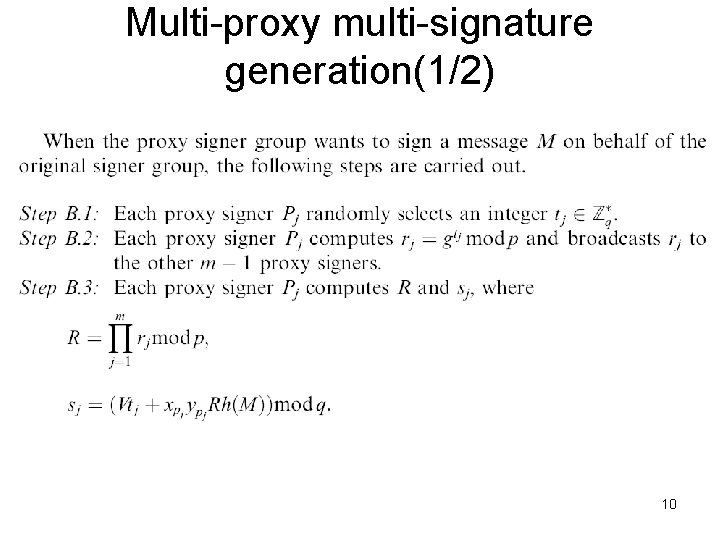
Multi-proxy multi-signature generation(1/2) 10

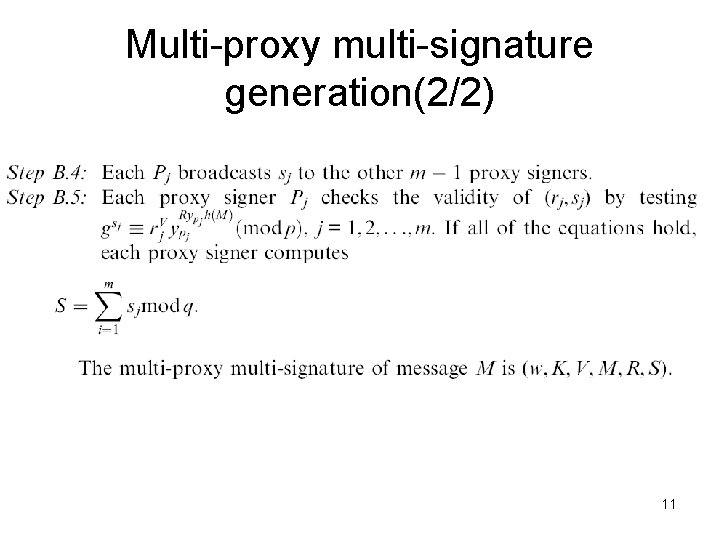
Multi-proxy multi-signature generation(2/2) 11

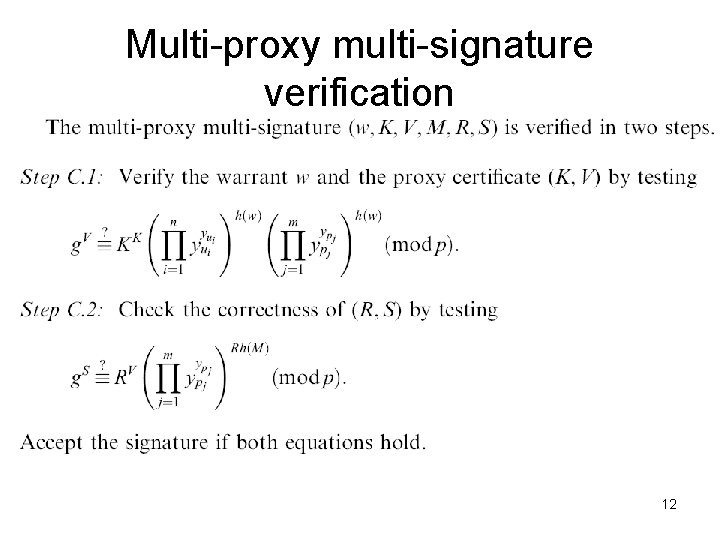
Multi-proxy multi-signature verification 12

Insider attack(1/4) • The proxy signer P 1 be malicious throughout. • P 1 can forge a multi-proxy multi-signature for a secret message M’ while participating with the other proxy signers in signing another message M. 13

Insider attack(2/4) 14

Insider attack(3/4) 15

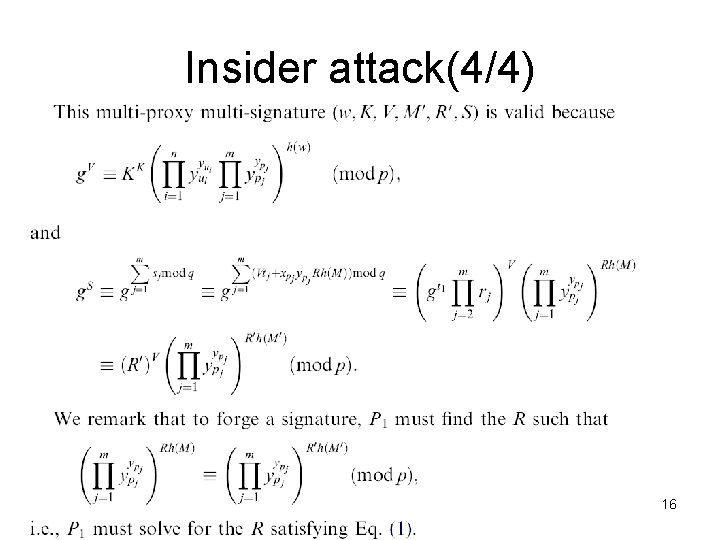
Insider attack(4/4) 16

Modifications to foil the attack • The basic differences are the choice of moduli and the replacement of R with R^2 in the calculations. 17

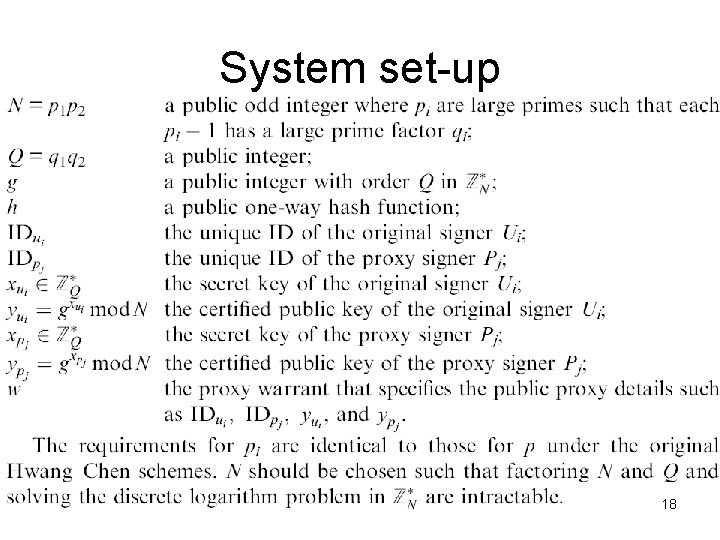
System set-up 18

g with order Q(1/4) 19

g with order Q(2/4) 20

g with order Q(3/4) 21

g with order Q(4/4) 22

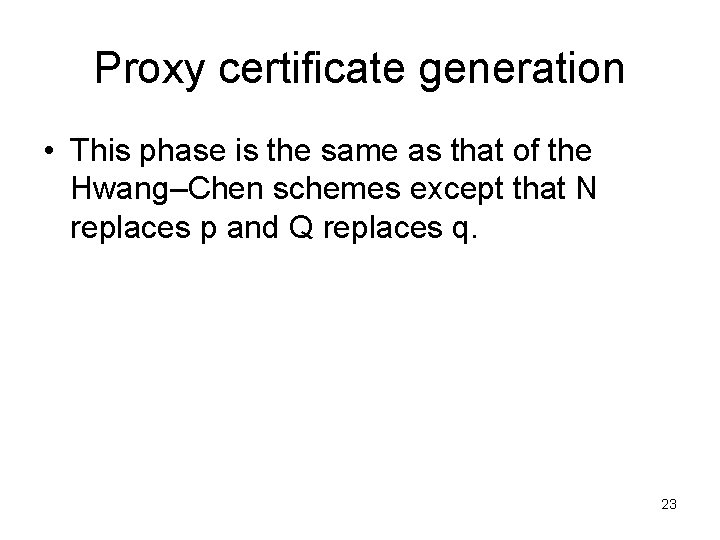
Proxy certificate generation • This phase is the same as that of the Hwang–Chen schemes except that N replaces p and Q replaces q. 23

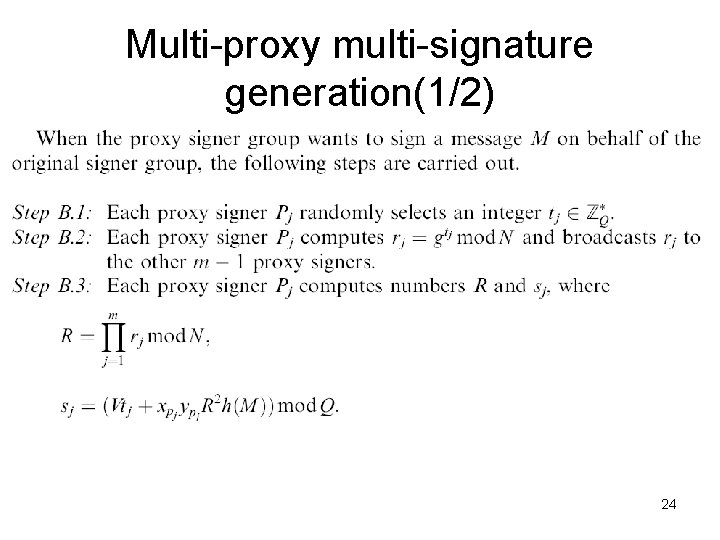
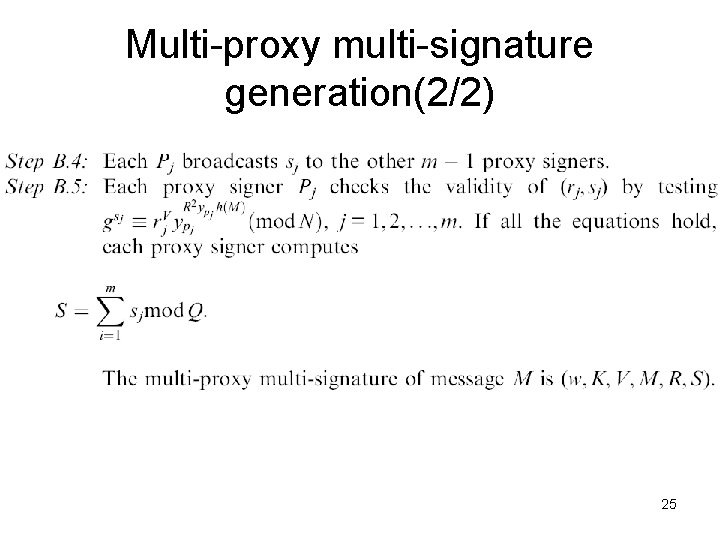
Multi-proxy multi-signature generation(1/2) 24

Multi-proxy multi-signature generation(2/2) 25

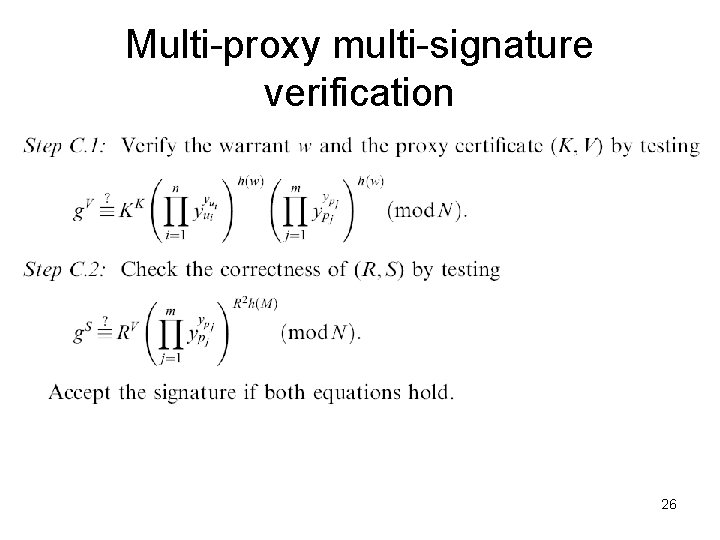
Multi-proxy multi-signature verification 26

Discussions(1/2) • The security of the modified scheme is based on the following intractability assumptions: 27

Discussions(2/2) 28