Cryptanalysis of Mutual Authentication and Key Exchange for








![References • [1] Azrz, A. , AND DIFFIE, W. “A secure communcations protocol to References • [1] Azrz, A. , AND DIFFIE, W. “A secure communcations protocol to](https://slidetodoc.com/presentation_image/8dbc3f1015d7c245968ef079699cb397/image-29.jpg)
- Slides: 30

Cryptanalysis of Mutual Authentication and Key Exchange for Low Power Wireless Communications Source:IEEE communications letters. Vol. 7 No. 5 May 2003 Author:Kyungah Shim Speaker:郭翰鍾 Team 9 members:Yung-Kun Lin(林詠焜) Yao-Ju Lee (李耀儒) Han-Chung Kuo (郭翰鍾) Date: 2003/11/24

Outline • Introduction • Public Key Based MAKEP (Azrz, A. , AND DIFFIE, W. ) • Wong and Chan’s MAKEPs (Wong and Chan’s ) • Server-specify MAKEP / Linear MAKEP • The Unknown key-Share Attacks (Kyungah Shim) • Server-specify MAKEP / Linear MAKEP • Improvement of the Wong-Chan’s MAKEPs • Server-specify MAKEP / Linear MAKEP • Comments on MAKEP for low power wireless communications (Siaw-Lynn Ng and Chris Mitchell ) • Server-specify MAKEP / Linear MAKEP • Summaries • References 2020/9/29 2

Introduction • MAKEP:Mutually authenticated key exchange protocol • Provide tow communicating parties with some assurance • Know each other’s true identity • Sharing a common session key known only to them 2020/9/29 3

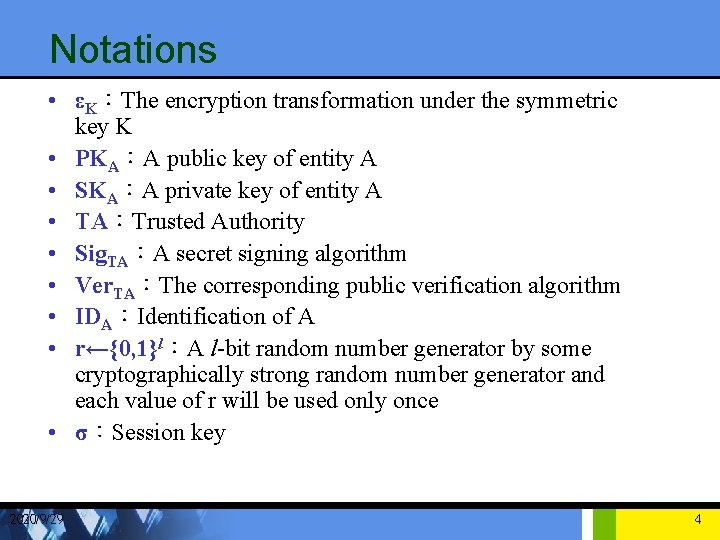
Notations • εK:The encryption transformation under the symmetric key K • PKA:A public key of entity A • SKA:A private key of entity A • TA:Trusted Authority • Sig. TA:A secret signing algorithm • Ver. TA:The corresponding public verification algorithm • IDA:Identification of A • r←{0, 1}l:A l-bit random number generator by some cryptographically strong random number generator and each value of r will be used only once • σ:Session key 2020/9/29 4

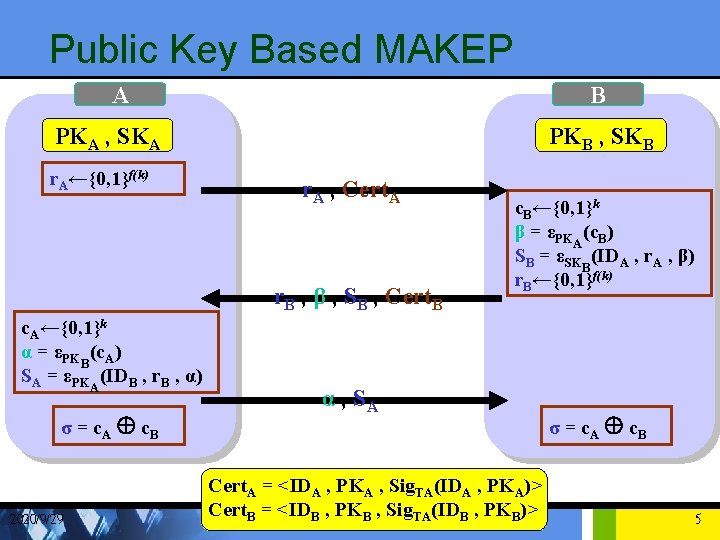
Public Key Based MAKEP A B PKA , SKA r. A←{0, 1}f(k) PKB , SKB r. A , Cert. A r. B , β , SB , Cert. B c. A←{0, 1}k α = εPKB(c. A) SA = εPKA(IDB , r. B , α) σ = c. A Å c. B 2020/9/29 c. B←{0, 1}k β = εPKA(c. B) SB = εSKB(IDA , r. A , β) r. B←{0, 1}f(k) α , SA Cert. A = <IDA , PKA , Sig. TA(IDA , PKA)> Cert. B = <IDB , PKB , Sig. TA(IDB , PKB)> σ = c. A Å c. B 5

Primitive element • (r. A , SB) and (r. B , SA) • Two challenge-response pairs to provide the mutual authentication • (α or β) • The ‘binding’ of each party’s encrypted session key to the corresponding challenge number (r. B or r. A) • (SA and SB):used to ensure the freshness of the session key • Detect both replay attack and man-in-the-middle attack 2020/9/29 6

Wong and Chan’s MAKEPs (2001) • Server-specific & Linear MAKEPs A Low-power wireless device (client) 2020/9/29 B Powerful base station (server) 7

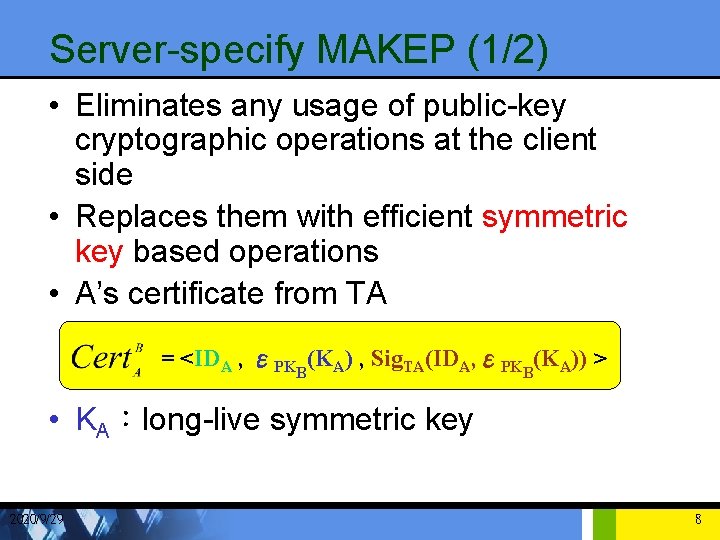
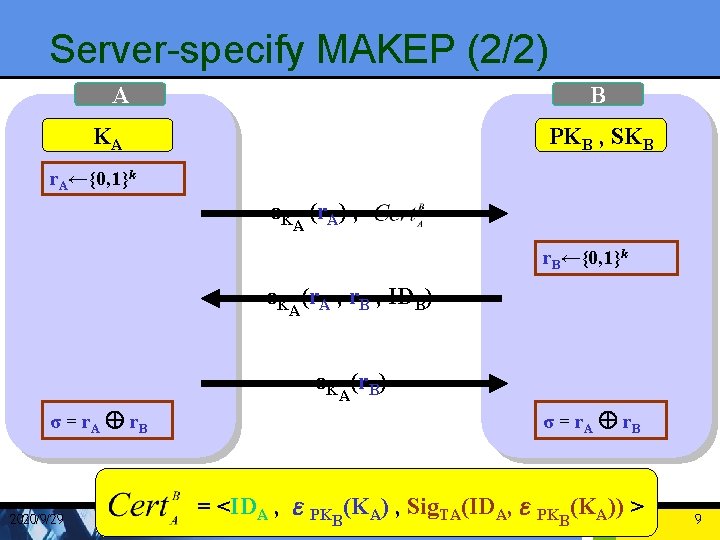
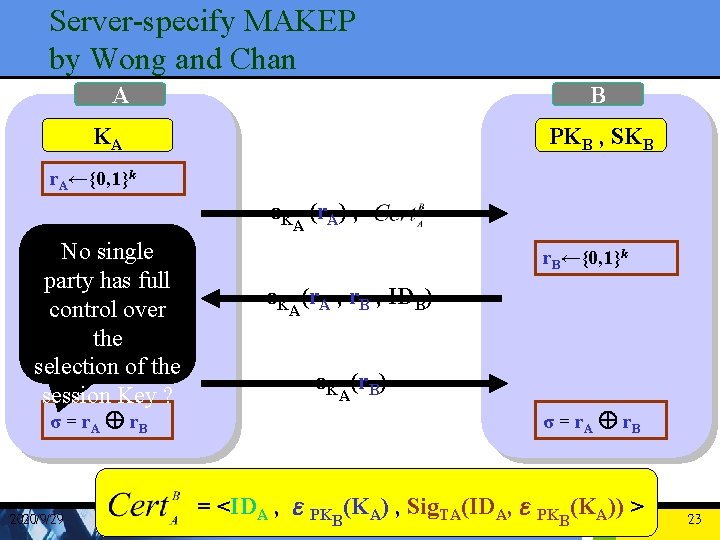
Server-specify MAKEP (1/2) • Eliminates any usage of public-key cryptographic operations at the client side • Replaces them with efficient symmetric key based operations • A’s certificate from TA = <IDA , εPKB(KA) , Sig. TA(IDA, εPKB(KA)) > • KA:long-live symmetric key 2020/9/29 8

Server-specify MAKEP (2/2) A B KA PKB , SKB r. A←{0, 1}k εK (r. A) , A r. B←{0, 1}k εK (r. A , r. B , IDB) A εK (r. B) σ = r. A Å r. B 2020/9/29 A σ = r. A Å r. B = <IDA , εPKB(KA) , Sig. TA(IDA, εPKB(KA)) > 9

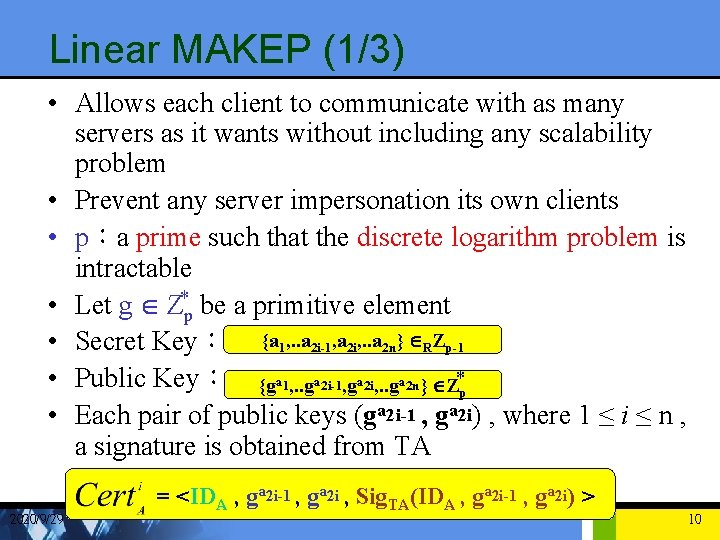
Linear MAKEP (1/3) • Allows each client to communicate with as many servers as it wants without including any scalability problem • Prevent any server impersonation its own clients • p:a prime such that the discrete logarithm problem is intractable • Let g Î Z*p be a primitive element • Secret Key: {a 1, . . a 2 i-1, a 2 i, . . a 2 n} ÎRZp-1 • Public Key: {ga 1, . . ga 2 i-1, ga 2 i, . . ga 2 n} ÎZ*p • Each pair of public keys (ga 2 i-1 , ga 2 i) , where 1 ≤ i ≤ n , a signature is obtained from TA 2020/9/29 = <IDA , ga 2 i-1 , ga 2 i , Sig. TA(IDA , ga 2 i-1 , ga 2 i) > 10

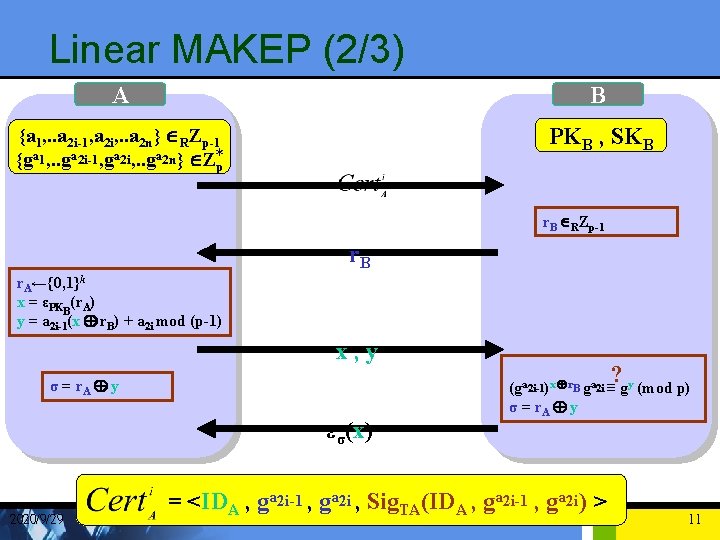
Linear MAKEP (2/3) A B {a 1, . . a 2 i-1, a 2 i, . . a 2 n} ÎRZp-1 {ga 1, . . ga 2 i-1, ga 2 i, . . ga 2 n} ÎZ*p PKB , SKB r. B ÎRZp-1 r. B r. A←{0, 1}k x = εPKB(r. A) y = a 2 i-1(x Å r. B) + a 2 i mod (p-1) x, y σ = r. A Å y εσ(x) 2020/9/29 ? (ga 2 i-1)x Å r. B ga 2 i ≡ gy (mod p) σ = r. A Å y = <IDA , ga 2 i-1 , ga 2 i , Sig. TA(IDA , ga 2 i-1 , ga 2 i) > 11

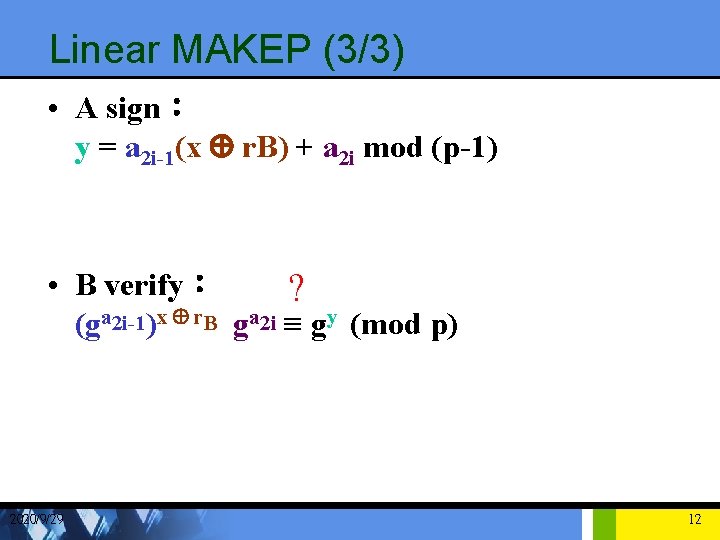
Linear MAKEP (3/3) • A sign: y = a 2 i-1(x Å r. B) + a 2 i mod (p-1) • B verify: ? (ga 2 i-1)x Å r. B ga 2 i ≡ gy (mod p) 2020/9/29 12

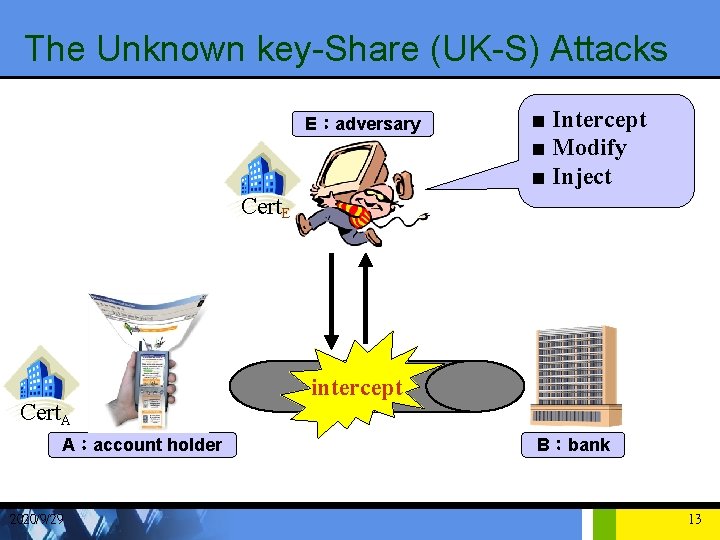
The Unknown key-Share (UK-S) Attacks E:adversary ■ Intercept ■ Modify ■ Inject Cert. E Cert. A A:account holder 2020/9/29 intercept B:bank 13

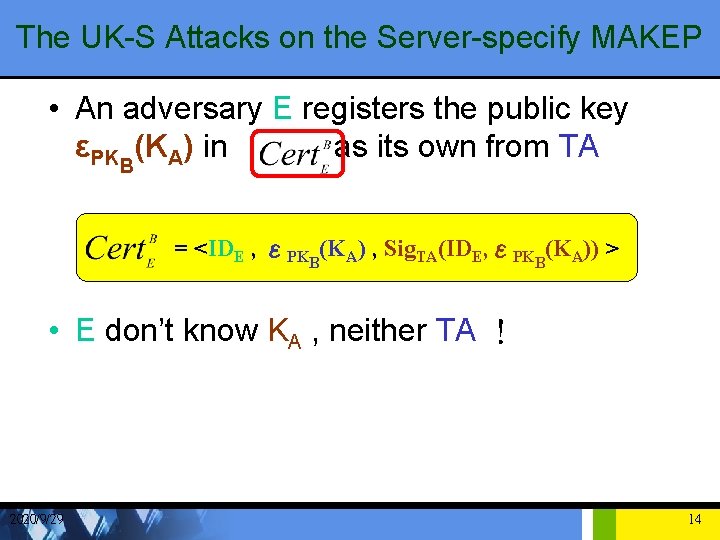
The UK-S Attacks on the Server-specify MAKEP • An adversary E registers the public key εPKB(KA) in as its own from TA = <IDE , εPKB(KA) , Sig. TA(IDE, εPKB(KA)) > • E don’t know KA , neither TA ! 2020/9/29 14

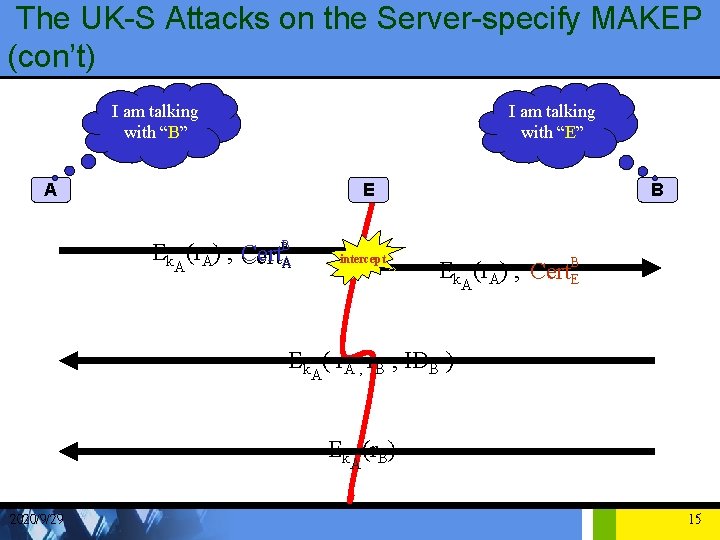
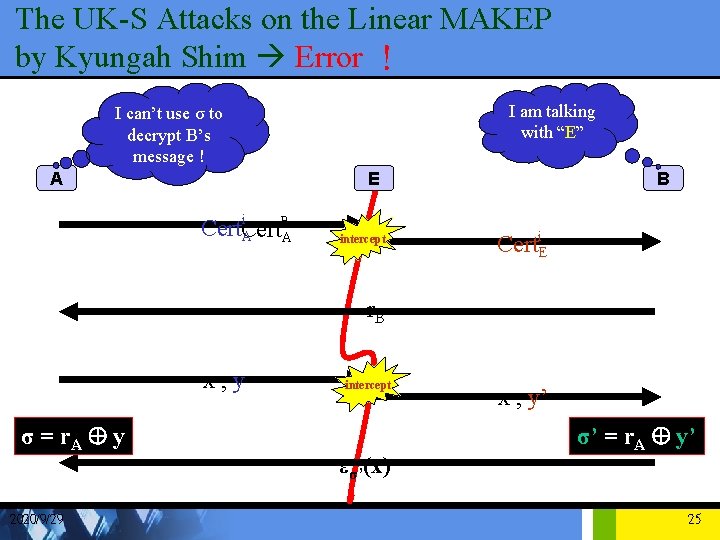
The UK-S Attacks on the Server-specify MAKEP (con’t) I am talking with “B” I am talking with “E” A E Ek (r. A) , Cert. BA A intercept B Ek (r. A) , Cert. BE A Ek ( r. A , r. B , IDB ) A Ek (r. B) A 2020/9/29 15

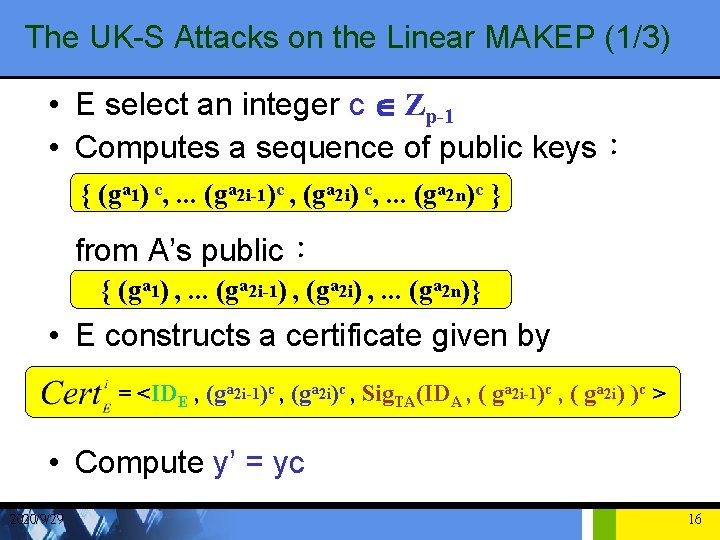
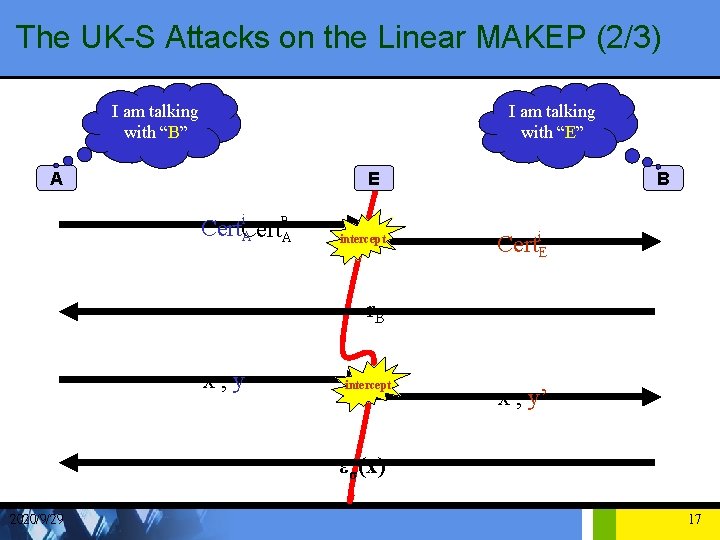
The UK-S Attacks on the Linear MAKEP (1/3) • E select an integer c Î Zp-1 • Computes a sequence of public keys: { (ga 1) c, . . . (ga 2 i-1)c , (ga 2 i) c, . . . (ga 2 n)c } from A’s public: { (ga 1) , . . . (ga 2 i-1) , (ga 2 i) , . . . (ga 2 n)} • E constructs a certificate given by = <IDE , (ga 2 i-1)c , (ga 2 i)c , Sig. TA(IDA , ( ga 2 i-1)c , ( ga 2 i) )c > • Compute y’ = yc 2020/9/29 16

The UK-S Attacks on the Linear MAKEP (2/3) I am talking with “B” I am talking with “E” A E i B Cert A A intercept B Certi. E r. B x, y intercept x , y’ εσ(x) 2020/9/29 17

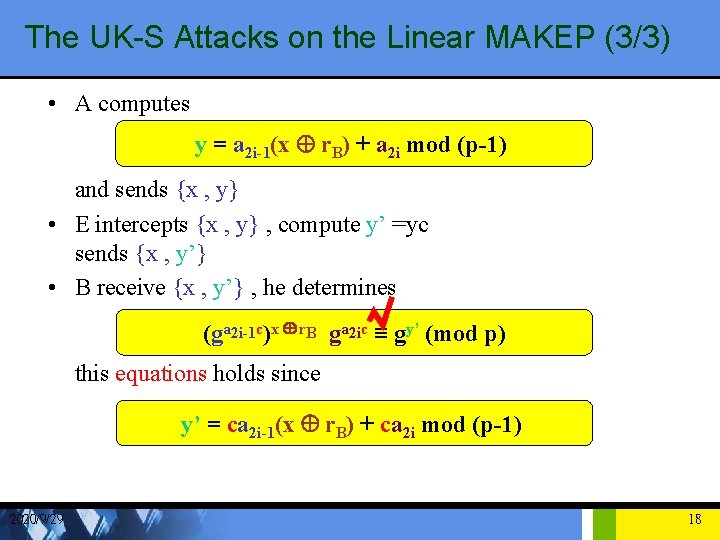
The UK-S Attacks on the Linear MAKEP (3/3) • A computes y = a 2 i-1(x Å r. B) + a 2 i mod (p-1) and sends {x , y} • E intercepts {x , y} , compute y’ =yc sends {x , y’} • B receive {x , y’} , he determines (ga 2 i-1 c)x Å r. B ga 2 ic ≡ gy’ (mod p) this equations holds since y’ = ca 2 i-1(x Å r. B) + ca 2 i mod (p-1) 2020/9/29 18

Improvement of the Wong-Chan’s MAKEPs • The UK-S attacks can be prevented by including the identities of the sender and intended recipient in the message being encrypted 2020/9/29 19

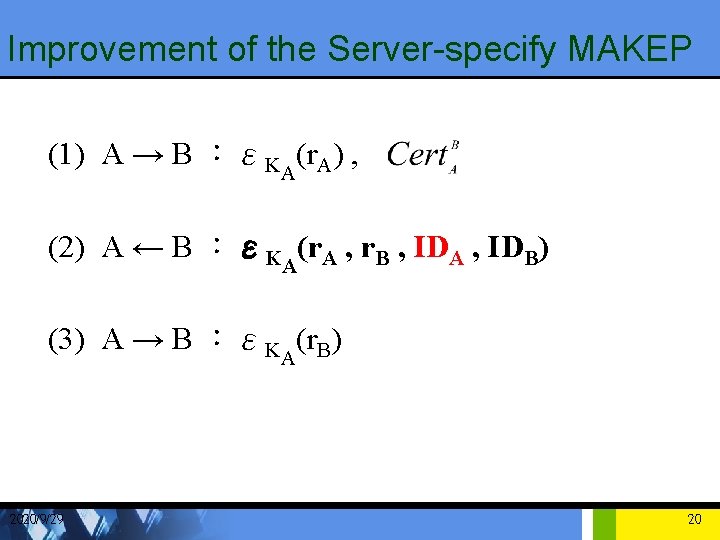
Improvement of the Server-specify MAKEP (1) A → B :εKA(r. A) , (2) A ← B :εKA(r. A , r. B , IDA , IDB) (3) A → B :εKA(r. B) 2020/9/29 20

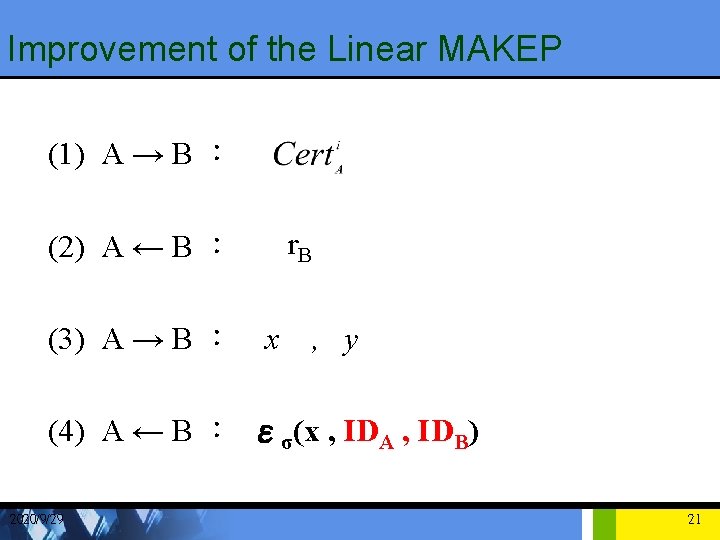
Improvement of the Linear MAKEP (1) A → B : r. B (2) A ← B : (3) A → B : x , y (4) A ← B : εσ(x , IDA , IDB) 2020/9/29 21

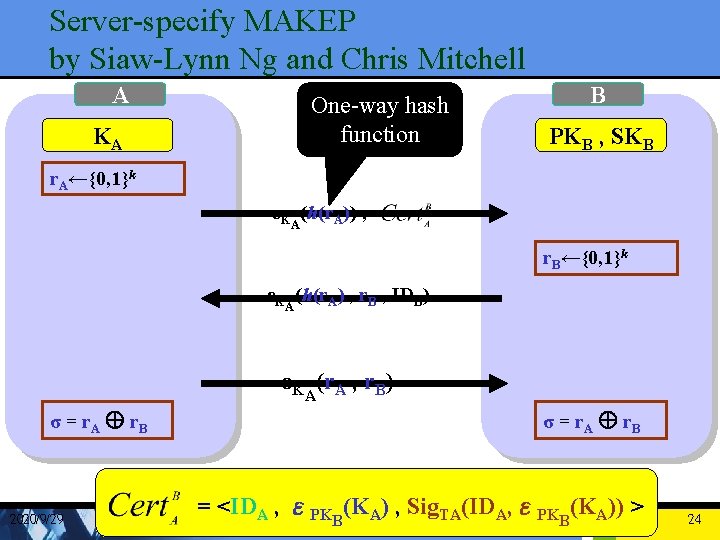
Comments on MAKEP for low power wireless communications • Siaw-Lynn Ng and Chris Mitchell point out an error in one of the attacks • UK-S Attacks on the Linear MAKEP is not true ! • They also demonstrate further undesirable properties in the protocol of Wong and Chan 2020/9/29 22

Server-specify MAKEP by Wong and Chan A B KA PKB , SKB r. A←{0, 1}k εK (r. A) , A No single party has full control over the selection of the session Key ? σ = r. A Å r. B 2020/9/29 r. B←{0, 1}k εK (r. A , r. B , IDB) A εK (r. B) A σ = r. A Å r. B = <IDA , εPKB(KA) , Sig. TA(IDA, εPKB(KA)) > 23

Server-specify MAKEP by Siaw-Lynn Ng and Chris Mitchell A KA One-way hash function B PKB , SKB r. A←{0, 1}k εKA(h(r. A)) , r. B←{0, 1}k εKA(h(r. A) , r. B , IDB) εK (r. A , r. B) σ = r. A Å r. B 2020/9/29 A σ = r. A Å r. B = <IDA , εPKB(KA) , Sig. TA(IDA, εPKB(KA)) > 24

The UK-S Attacks on the Linear MAKEP by Kyungah Shim Error ! I am talking with “E” I can’t use σ to decrypt B’s message ! A E i B Cert A A intercept B Certi. E r. B x, y σ = r. A Å y 2020/9/29 intercept εσ’(x) x , y’ σ’ = r. A Å y’ 25

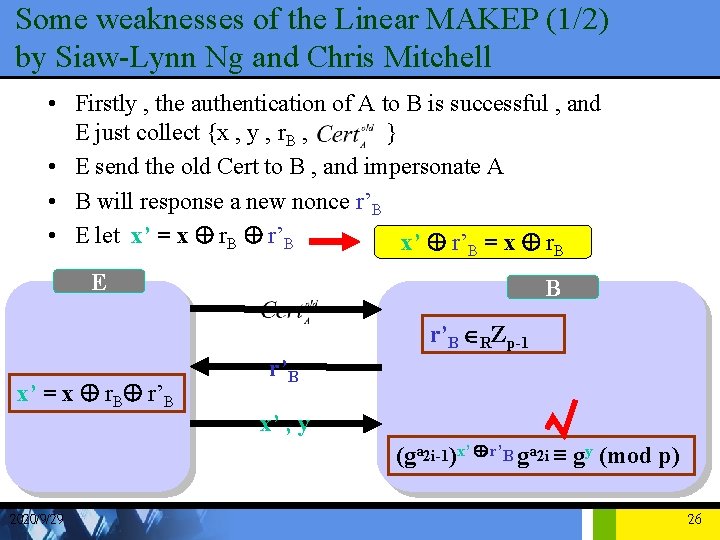
Some weaknesses of the Linear MAKEP (1/2) by Siaw-Lynn Ng and Chris Mitchell • Firstly , the authentication of A to B is successful , and E just collect {x , y , r. B , } • E send the old Cert to B , and impersonate A • B will response a new nonce r’B • E let x’ = x Å r. B Å r’B x’ Å r’ = x Å r B E B B r’B ÎRZp-1 x’ = x Å r. BÅ r’B x’ , y (ga 2 i-1)x’ Å r’B ga 2 i ≡ gy (mod p) 2020/9/29 26

Some weaknesses of the Linear MAKEP (2/2) by Siaw-Lynn Ng and Chris Mitchell • If the secret key {a 2 i-1 , a 2 i} and public key {ga 2 i-1 , ga 2 i} , use more than once • 1 st :E can get (r. B , x , y) • 2 nd :E can get (r. B’ , x’ , y’) • E find the public key of 1 st and 2 nd are same , then he can compute y = a 2 i-1(x Å r. B) + a 2 i mod (p-1) y’ = a 2 i-1(x’ Å r. B’) + a 2 i mod (p-1) E can get a 2 i & a 2 i-1 ! 2020/9/29 27

Summaries • The protocols from Wong and Chan are suitable for wireless network. • The Un-know key attack can be solve by adding information of receiver • The UK-S Attacks on Server-specify MAKEP is true , but maybe no UK-S Attacks Linear MAKEP • A secure implementation of Linear MAKEP, while efficient in terms of computation, would incur a significant overhead in communication load, thereby potentially making it impractical 2020/9/29 28
![References 1 Azrz A AND DIFFIE W A secure communcations protocol to References • [1] Azrz, A. , AND DIFFIE, W. “A secure communcations protocol to](https://slidetodoc.com/presentation_image/8dbc3f1015d7c245968ef079699cb397/image-29.jpg)
References • [1] Azrz, A. , AND DIFFIE, W. “A secure communcations protocol to prevent unauthorized access - privacy and authentication for wireless local area networks”. IEEE Persona. I Commzlnications (First Quarter 1994). • [2] D. S. Wong and A. H. Chan, “Mutually authentication and key exchange for low power wireless communications, ” Proc. IEEE MILCOM 2001 Conf. , vol. 1, pp. 39– 43, Oct. 2001. • [3] Kyungah Shim. “Cryptanalysis of mutual authentication and key exchange for low power wireless communications”. IEEE Communications Letters , Vol 7 , No 5 , 2003 , pp 248– 250. • [4] Siaw-Lynn Ng and Chris Mitchell “Comments on mutual authentication and key exchange protocols for low power wireless communications” , IEEE Communications Letters. 2020/9/29 29

Thank You ! Question ? 2020/9/29 30