Message Authentication Codes and Hash Functions Dr Ayad

















- Slides: 34

Message Authentication Codes and Hash Functions Dr. Ayad Ibrahim

Message Authentication n Message authentication is concerned with n n n Protecting the integrity of a message Validating identity of originator Three Methods to provide message authentication n Encryption Message authentication code (MAC) Hash function 2

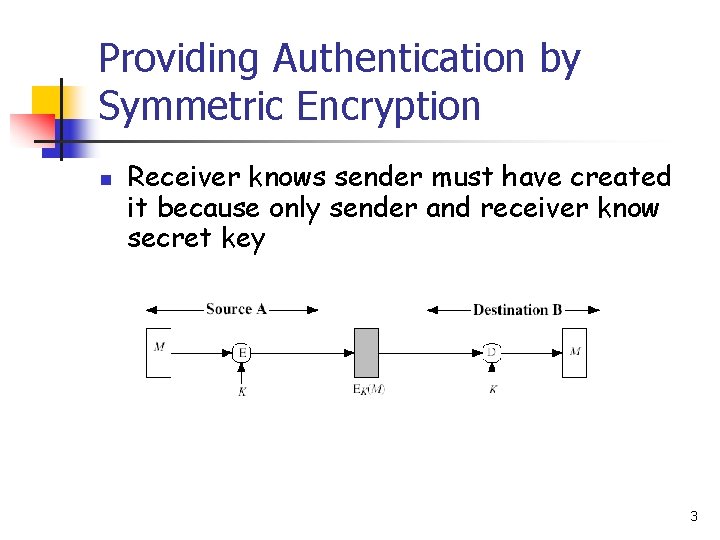
Providing Authentication by Symmetric Encryption n Receiver knows sender must have created it because only sender and receiver know secret key 3

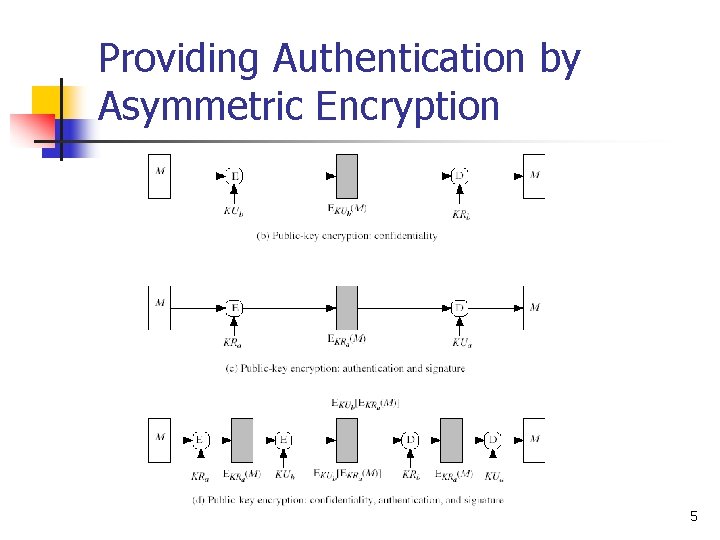
Providing Authentication by Asymmetric Encryption n n Encryption provides no confidence of sender because anyone potentially knows public key However if sender signs message using its private key and then encrypts with receiver’s public key, we have both confidentiality and authentication 4

Providing Authentication by Asymmetric Encryption 5

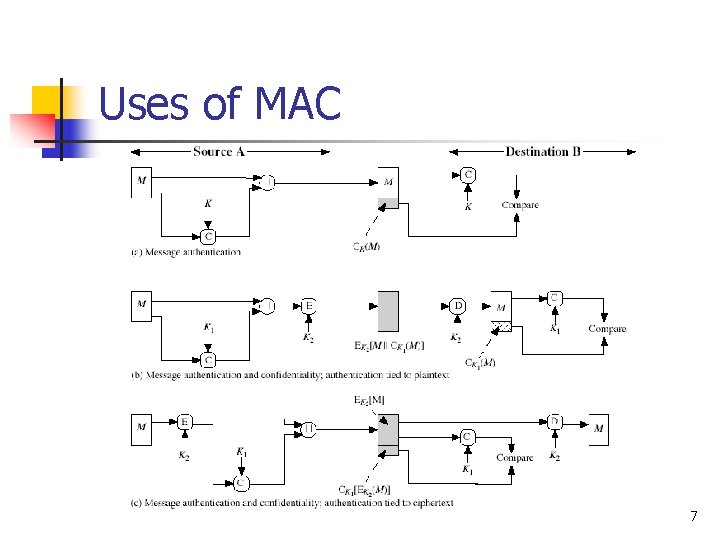
Message Authentication Code (MAC) n Generated by an algorithm that creates a small fixed-sized block n n n depending on both message and some key Appended to message as a signature Receiver performs same computation on message and checks it matches the MAC 6

Uses of MAC 7

MAC Properties n Cryptographic checksum n n MAC = CK(M) condenses a variable-length message M using a secret key K to a fixed-sized authenticator Many-to-one function n n potentially many messages have same MAC make sure finding collisions is very difficult 8

Requirements for MACs n Need the MAC to satisfy the following: “knowing a message and MAC, it is infeasible to find another message with same MAC”. 9

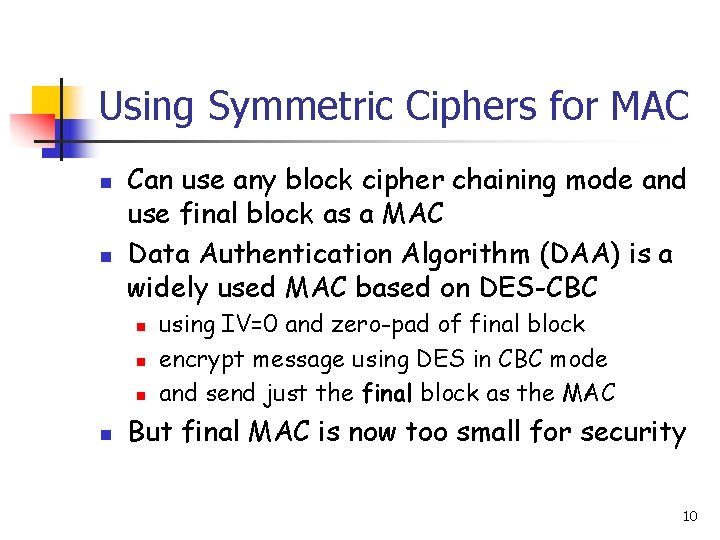
Using Symmetric Ciphers for MAC n n Can use any block cipher chaining mode and use final block as a MAC Data Authentication Algorithm (DAA) is a widely used MAC based on DES-CBC n n using IV=0 and zero-pad of final block encrypt message using DES in CBC mode and send just the final block as the MAC But final MAC is now too small for security 10

Hash Functions n n Condense arbitrary message to fixed size Usually assume that the hash function is public and not keyed Hash value used to detect changes to message Used often to create a digital signature 11

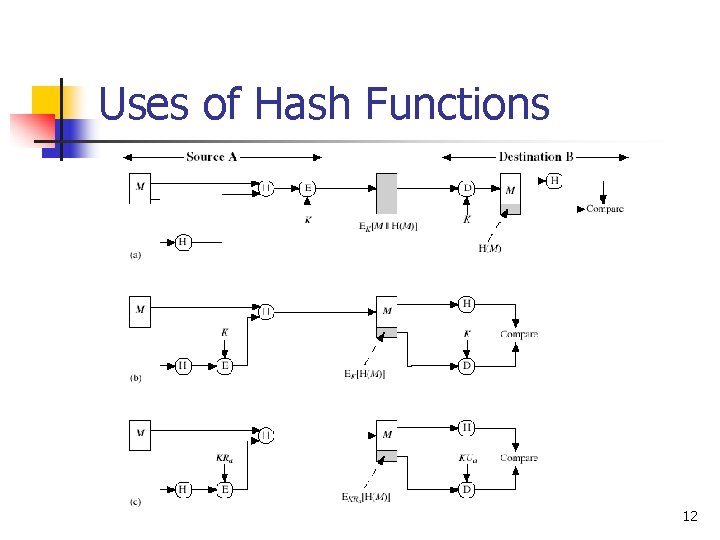
Uses of Hash Functions 12

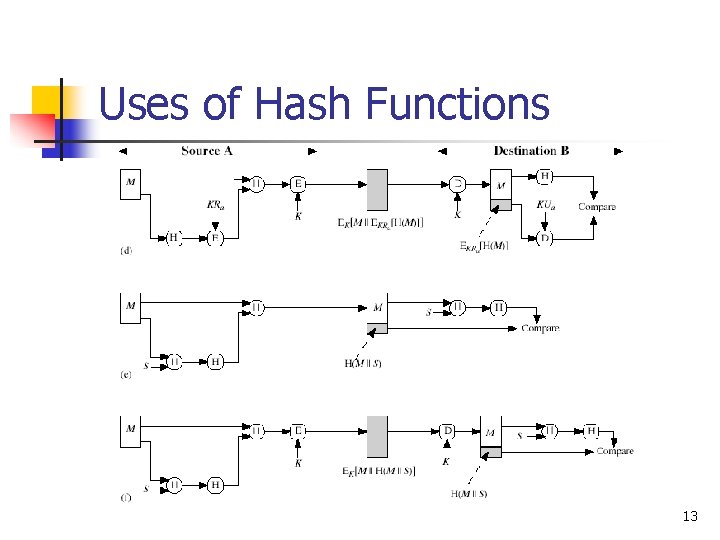
Uses of Hash Functions 13

Hash Function Properties n Hash function produces a fingerprint of some file/message/data h = H(M) 14

Requirements for Hash Functions 1. 2. 3. 4. 5. 6. can be applied to any sized message M produce fixed-length output h easy to compute h=H(M) for any message M one-way property: given h is infeasible to find x s. t. H(x)=h weak collision resistance: given x is infeasible to find y s. t. H(y)=H(x) strong collision resistance: infeasible to find any x, y s. t. H(y)=H(x) 15

Simple Hash Functions n n n We can use XOR of message blocks Not secure since can manipulate any message and either not change hash or change hash also Need a stronger cryptographic function 16

Block Ciphers as Hash Functions n Can use block ciphers as hash functions n n n use H 0=0 and zero-pad of final block compute Hi = EMi [Hi-1] use final block as the hash value similar to CBC but without a key Resulting hash is too small (64 -bit) n both due to direct birthday attack 17

Birthday Attacks n n n If there are 23 people in a room, the probability that at least two people have the same birthday is slightly more than 50%. If there are 30, the probability is around 70%. Finding collisions of a hash function using Birthday Paradox. 1. randomly chooses k messages, x 1, x 2, …, xk 2. search if there is a pair of messages, say x i and xj such that h(xi) = h(xj). If so, one collision is found. This birthday attack imposes a lower bound on the size of message digests. If n = 64, the probability of finding one collision will be higher than half after slightly more than 232 random hashes being tried. 18

Birthday Attacks n n n The probability that all 23 people have different birthdays is Therefore, the probability of at least two having the same birthday is 1 - 0. 493=0. 507 More generally, suppose we have N objects, where N is large. There are r people, and each chooses an object. Then 19

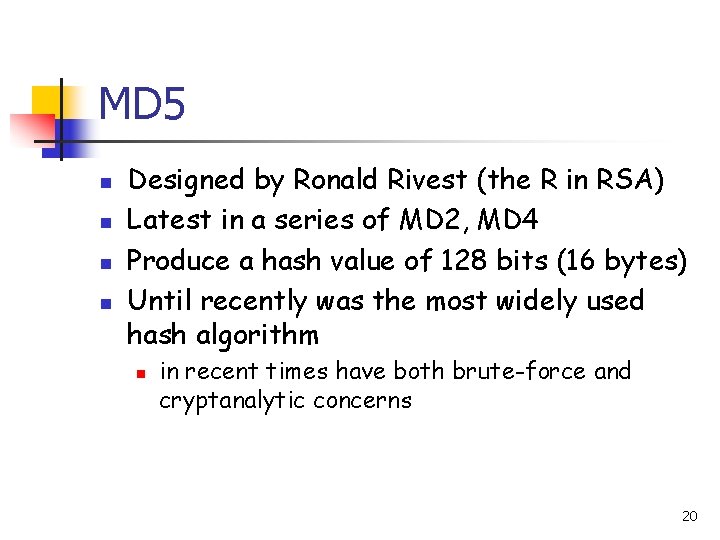
MD 5 n n Designed by Ronald Rivest (the R in RSA) Latest in a series of MD 2, MD 4 Produce a hash value of 128 bits (16 bytes) Until recently was the most widely used hash algorithm n in recent times have both brute-force and cryptanalytic concerns 20

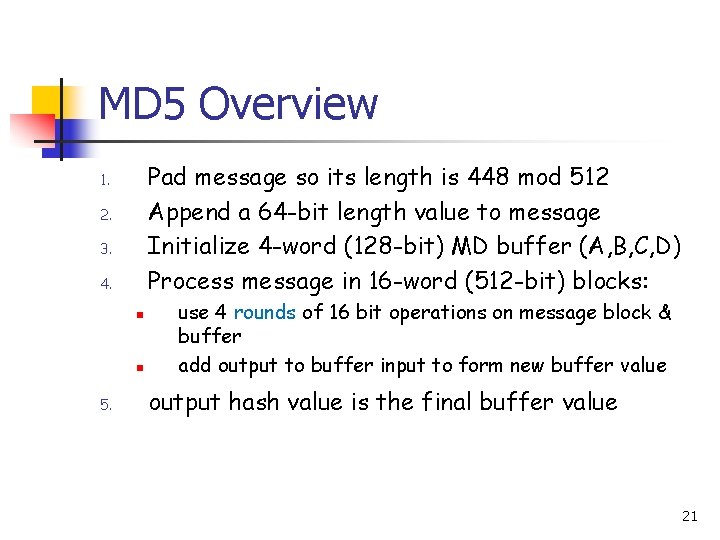
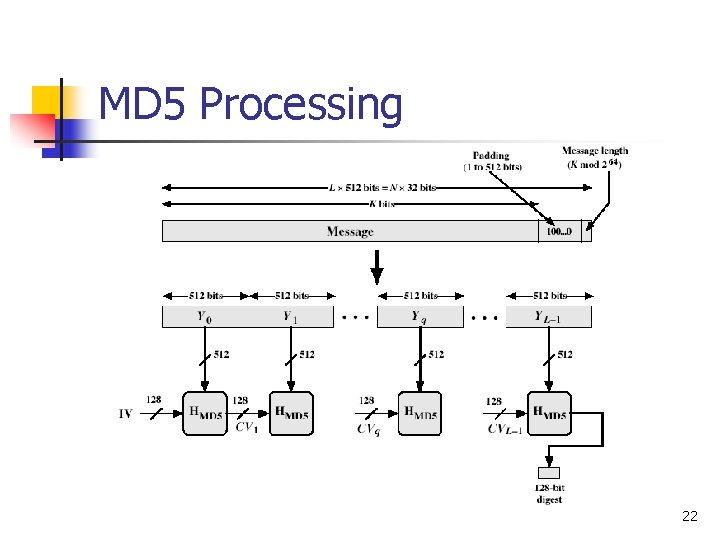
MD 5 Overview Pad message so its length is 448 mod 512 Append a 64 -bit length value to message Initialize 4 -word (128 -bit) MD buffer (A, B, C, D) Process message in 16 -word (512 -bit) blocks: 1. 2. 3. 4. n n 5. use 4 rounds of 16 bit operations on message block & buffer add output to buffer input to form new buffer value output hash value is the final buffer value 21

MD 5 Processing 22

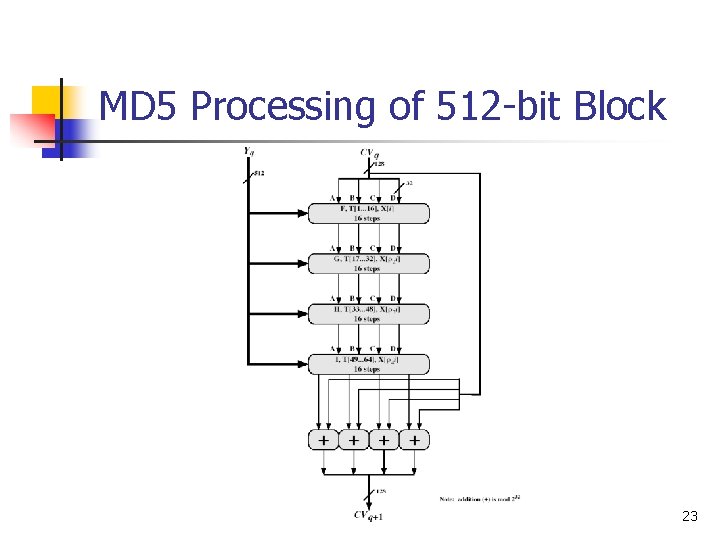
MD 5 Processing of 512 -bit Block 23

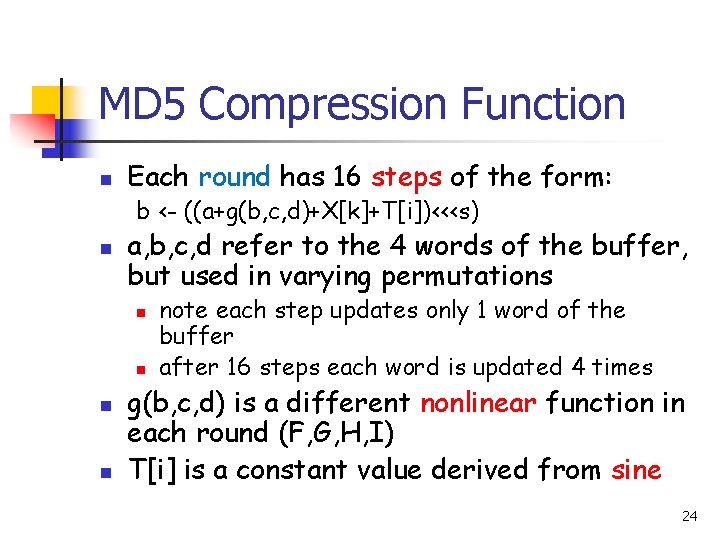
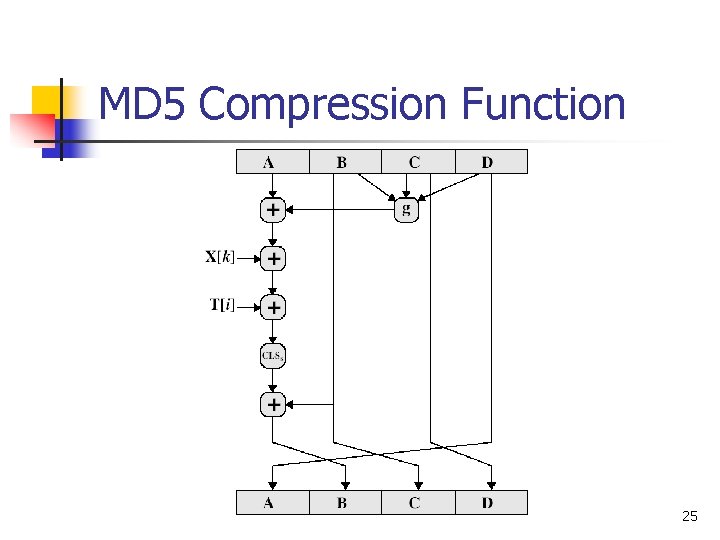
MD 5 Compression Function n Each round has 16 steps of the form: b <- ((a+g(b, c, d)+X[k]+T[i])<<<s) n a, b, c, d refer to the 4 words of the buffer, but used in varying permutations n n note each step updates only 1 word of the buffer after 16 steps each word is updated 4 times g(b, c, d) is a different nonlinear function in each round (F, G, H, I) T[i] is a constant value derived from sine 24

MD 5 Compression Function 25

Secure Hash Algorithm (SHA-1) n n Designed by NIST & NSA in 1993, revised 1995 as SHA-1 US standard for use with DSA signature scheme Produce hash values of 160 bits (20 bytes) Now the generally preferred hash algorithm 26

SHA-1 Overview pad message so its length is 448 mod 512 append a 64 -bit length value to message initialize 5 -word (160 -bit) buffer (A, B, C, D, E) to 1. 2. 3. (67452301, efcdab 89, 98 badcfe, 10325476, c 3 d 2 e 1 f 0) process message in 16 -word (512 -bit) chunks: 4. n n n 5. expand 16 words into 80 words by mixing & shifting use 4 rounds of 20 bit operations on message block & buffer add output to input to form new buffer value output hash value is the final buffer value 27

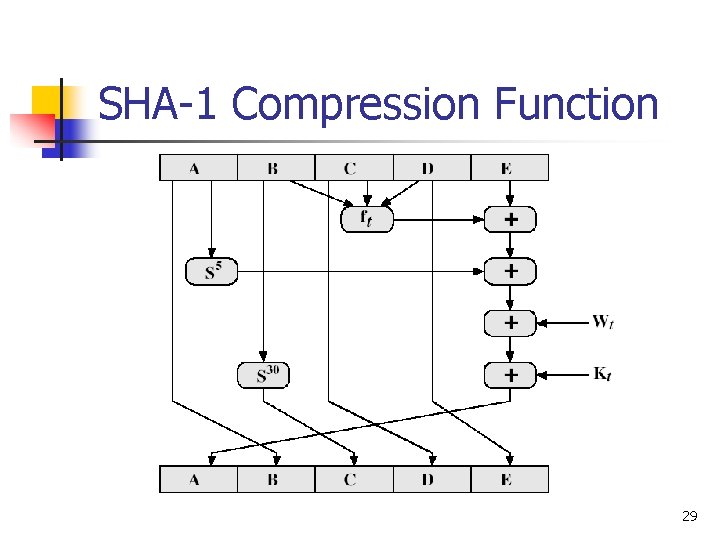
SHA-1 Compression Function n Each round has 20 steps which replaces the 5 buffer words thus: (A, B, C, D, E) <-(E+f(t, B, C, D)+(A<<5)+Wt+Kt), A, (B<<30), C, D) n n n a, b, c, d refer to the 4 words of the buffer t is the step number f(t, B, C, D) is nonlinear function for round Wt is derived from the message block Kt is a constant value derived from sine 28

SHA-1 Compression Function 29

SHA-1 vs MD 5 n n Brute force attack is harder (160 vs 128 bits for MD 5) Not vulnerable to any known attacks (compared to MD 4 and MD 5) A little slower than MD 5 (80 vs 64 steps) Both designed as simple and compact 30

Keyed Hash Functions as MACs n Desirable to create a MAC using a hash function rather than a block cipher n n n hash functions are generally faster Hash includes a key along with the message Original proposal: Keyed. Hash = Hash(Key|Message) n some weaknesses were found with this proposal n Eventually led to development of HMAC 31

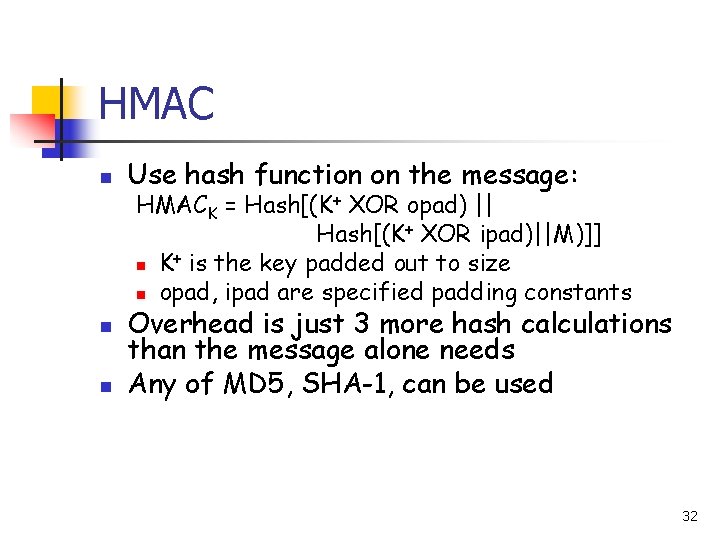
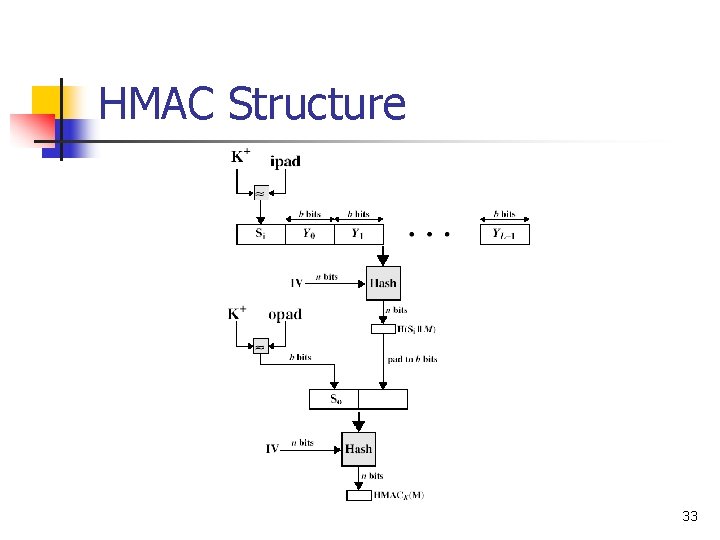
HMAC n n n Use hash function on the message: HMACK = Hash[(K+ XOR opad) || Hash[(K+ XOR ipad)||M)]] + n K is the key padded out to size n opad, ipad are specified padding constants Overhead is just 3 more hash calculations than the message alone needs Any of MD 5, SHA-1, can be used 32

HMAC Structure 33

Security of HMAC n n Security of HMAC relates to that of the underlying hash algorithm Attacking HMAC requires either: n n brute force attack on key used birthday attack (but since keyed would need to observe a very large number of messages) 34