Cryptography and Security Services Mechanisms and Applications Chapter

















- Slides: 34

Cryptography and Security Services: Mechanisms and Applications Chapter 6 Integrity and Authentication Manuel Mogollon m_mogollon@verizon. net M. Mogollon - 0

Session 4 – Contents • Integrity — Message Authentication Code (MAC) — Hash Functions • Authentication — Digital Signature Standard (FIPS 186 -2) — DSA (ANSI X 9. 30 — RSA (ANSI X 9. 31) — El. Gamal — ECDSA (ANSI X 9. 62) Integrity 1 Authentication M. Mogollon - 1

Integrity Assurance that a message was not accidentally or deliberately modified in transit by replacement, insertion, or deletion. Integrity Hash Functions SHA MD 5 Digital Signature MAC Encryption HMAC SHA-1 SHA-384 DES CBC HMAC-SHA-1 -96 SHA-256 SHA-512 AES-XCBCMAC-96 HMAC-MD 5 -96 Integrity 2 Authentication M. Mogollon - 2

What is Integrity? integrity / n. (1) The property of ensuring that data is transmitted from source to destination without undetected alteration. (2) The process of preventing undetected alteration of data. Integrity 3 Authentication M. Mogollon - 3

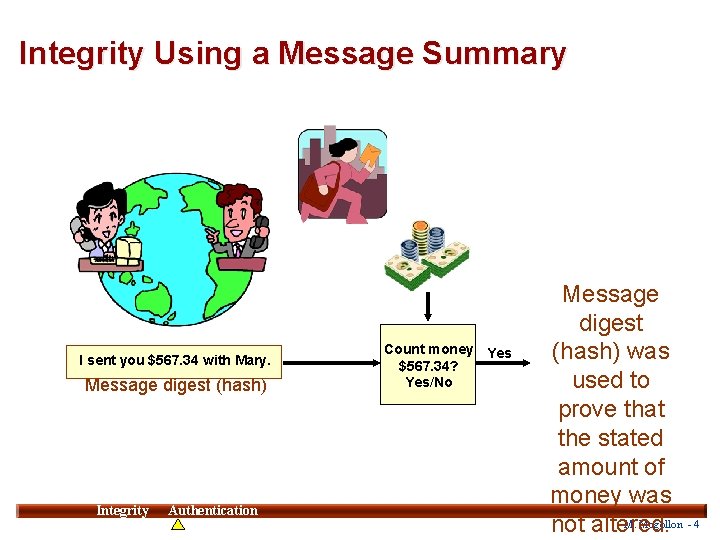
Integrity Using a Message Summary I sent you $567. 34 with Mary. Message digest (hash) Integrity Authentication Count money Yes $567. 34? Yes/No Message digest (hash) was used to prove that the stated amount of money was 4 M. Mogollon - 4 not altered.

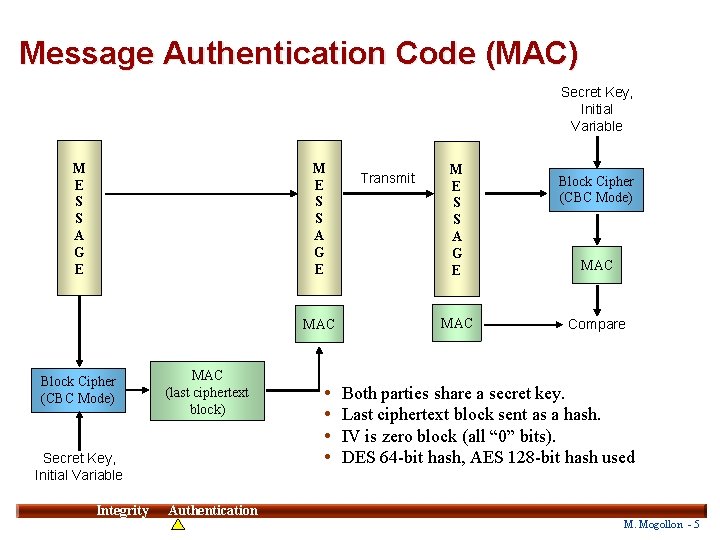
Message Authentication Code (MAC) Secret Key, Initial Variable M E S S A G E MAC Block Cipher (CBC Mode) MAC (last ciphertext block) Secret Key, Initial Variable Integrity • • Transmit M E S S A G E MAC Block Cipher (CBC Mode) MAC Compare Both parties share a secret key. Last ciphertext block sent as a hash. IV is zero block (all “ 0” bits). DES 64 -bit hash, AES 128 -bit hash used 5 Authentication M. Mogollon - 5

Using CBC Mode as a Hash Function IV Cleartext Block + + Block Cipher Crypto Variable • Sends last ciphertext block as a hash. • Uses a fixed known IV. • DES hash: 64 bits. • AES hash: 128 bits Ciphertext Block Last ciphertext block Integrity 6 Authentication M. Mogollon - 6

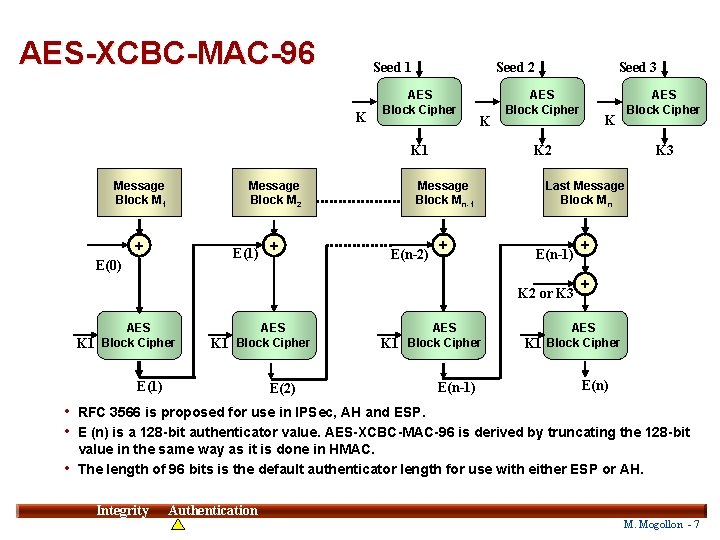
AES-XCBC-MAC-96 Seed 1 K Seed 2 AES Block Cipher K K 1 Message Block M 2 + E(1) + E(0) AES Block Cipher K 1 E(1) E(2) K + K 3 Last Message Block Mn E(n-1) K 2 or K 3 AES Block Cipher K 1 AES Block Cipher K 2 Message Block Mn-1 E(n-2) Seed 3 AES Block Cipher K 1 E(n-1) + + AES K 1 Block Cipher E(n) • RFC 3566 is proposed for use in IPSec, AH and ESP. • E (n) is a 128 -bit authenticator value. AES-XCBC-MAC-96 is derived by truncating the 128 -bit value in the same way as it is done in HMAC. • The length of 96 bits is the default authenticator length for use with either ESP or AH. Integrity 7 Authentication M. Mogollon - 7

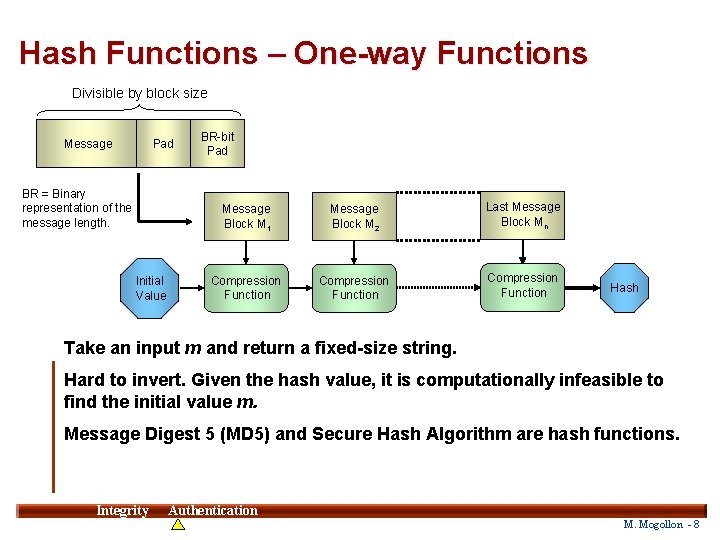
Hash Functions – One-way Functions Divisible by block size Message Pad BR = Binary representation of the message length. Initial Value BR-bit Pad Message Block M 1 Message Block M 2 Last Message Block Mn Compression Function Hash Take an input m and return a fixed-size string. Hard to invert. Given the hash value, it is computationally infeasible to find the initial value m. Message Digest 5 (MD 5) and Secure Hash Algorithm are hash functions. Integrity 8 Authentication M. Mogollon - 8

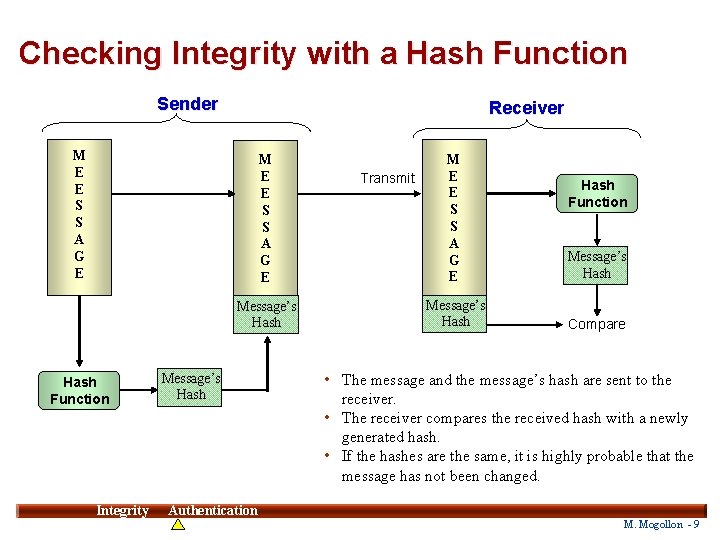
Checking Integrity with a Hash Function Sender Receiver M E E S S A G E Message’s Hash Function Integrity Message’s Hash Transmit M E E S S A G E Message’s Hash Compare Hash Function • The message and the message’s hash are sent to the receiver. • The receiver compares the received hash with a newly generated hash. • If the hashes are the same, it is highly probable that the message has not been changed. 9 Authentication M. Mogollon - 9

Secure Hash Standard • On April 17, 1995, the National Institute of Standards and Technology, NIST, approved the Secure Hash Standard, FIPS PUB 180 -1, which included one secure hash algorithm, the SHA-1. • On February 1, 2003, a new Secure Hash Signature Standard (SHS) (FIPS PUB 180 -2) was approved; it added three hash algorithms, SHA-1, SHA-256, SHA-384, and SHA-512. • The SHA-1 algorithm specified in the FIPS PUB 180 -2 is the same algorithm that was specified previously in FIPS 180 -1, although some of the notation was modified to be consistent with the notation used in the SHA-256, SHA 384, and SHA-512 algorithms. Integrity 10 Authentication M. Mogollon - 10

SHA Basic Properties Algorithm Message Size (bits) Block Size (bits) Word Size (bits) Message Digest Size (bits) Security (bits) SHA-1 < 264 512 32 160 80 SHA-256 < 264 512 32 256 128 SHA-384 < 2128 1024 64 384 192 SHA-512 < 2128 1024 64 512 256 Integrity 11 Authentication M. Mogollon - 11

Secure Hash Algorithm SHA-1 • SHA-1 is used to generate a condensed representation of a message called a message digest. • The SHA-1 is required for use with the Digital Signature Algorithm (DSA), as specified in the Digital Signature Standard (DSS), and whenever a secure hash algorithm is required for federal applications. • The SHA-1 sequentially processes blocks of 512 bits when computing the message digest; padding is required, even if the message is a multiple of 512. Padding is done as follows: — Append a “ 1” bit followed by a “ 0” bits until the length is 64 bits less than a multiple of 512 (length = 448 mod 512). — Append a 64 -bit representation of the pre-padded message length. • The padded message length is 512 × n. Integrity Authentication Hash functions are used to prove that the transmitted data was not altered. M. Mogollon - 12 12

Computing SHA-1 Message Digest 512 bits Message Block M 1 8 bits . . 8 bits Word [0] 8 bits H 0(0) H 1(0) H 2(0) H 3(0) H 4(0) Integrity 8 bits New H Values H 0(1) = a + H 0(0) H 1(1) = b + H 1(0) H 2(1) = c + H 2(0) H 3(1) = d + H 3(0) H 4(1) = e + H 4(0) 8 bits . . 8 bits Word [0] Message Block M(2) Compression Function a = H 0(0) b = H 1(0) c = H 2(0) d = H 3(0) e = H 4(0) 8 bits Word [15] Message Block M(1) Initial H Values 512 bits Message Block M(N) Compression Function a = H 0(1) b = H 1(1) c = H 2(1) d = H 3(1) e = H 4(1) 8 bits Word [15] Message Block M(N) New H Values H 0(2) = a + H 0(1) H 1(2) = b + H 1(1) H 2(2) = c + H 2(1) H 3(2) = d + H 3(1) H 4(2) = e + H 4(1) . . . Compression Function New H Values a = H 0(N - 1) b = H 1(N - 1) c = H 2(N - 1) d = H 3(N - 1) e = H 4(N - 1) H 0(N) = a + H 0(N - 1) H 1(N) = b + H 1(N - 1) H 2(N) = c + H 2(N - 1) H 3(N) = d + H 3(N - 1) H 4(N) = e + H 4(N - 1) 13 Authentication M. Mogollon - 13

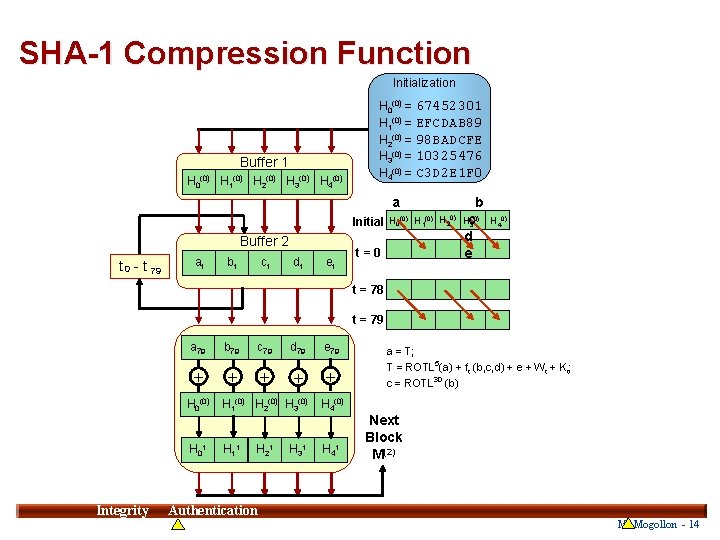
SHA-1 Compression Function Initialization Buffer 1 H 0(0) H 1(0) H 2(0) H 3(0) H 4(0) H 0(0) = 67452301 H 1(0) = EFCDAB 89 H 2(0) = 98 BADCFE H 3(0) = 10325476 H 4(0) = C 3 D 2 E 1 F 0 a Initial H 0(0) H 1(0) H 20) Buffer 2 t 0 - t 79 at bt ct dt et t=0 b 0) Hc 3 d e H 40) t = 78 t = 79 a 79 b 79 c 79 d 79 e 79 + + + H 0(0) H 01 Integrity H 1(0) H 2(0) H 3(0) H 11 H 21 H 31 a = T; T = ROTL 5(a) + ft (b, c, d) + e + Wt + Kt; c = ROTL 30 (b) H 4(0) H 41 Next Block M(2) 14 Authentication M. Mogollon - 14

SHA-1 Operations • Bitwise logical word operations — — x ^ y = bitwise logical "and" of x and y. x ν y = bitwise logical "inclusive-or" of x and y. x XOR y = bitwise logical "exclusive-or" of x and y. ¬ x = bitwise logical "complement" of x. • X + Y is defined as follows: words x and y represent integers x and y, where 0 ≤ x ≤ 232 and 0 ≤ y ≤ 232. For positive integers U and V, let U mod V be the remainder upon dividing U by V. Compute Z = (X + Y) mod 232. Then 0 ≤ Z ≤ 232. Convert Z to a word, z, and define z = x + y. • ROTLn(x) = (x << n) v (x >> 32 -n). (Circular left shift operation) — x << n is obtained as follows: discard the left-most n bits of X and then pad the result with n zeroes on the right (the result will still be 32 bits). — x >> 32 - n is obtained by discarding the right-most 32 - n bits of X and then padding the result with n zeroes on the left. Integrity 15 Authentication M. Mogollon - 15

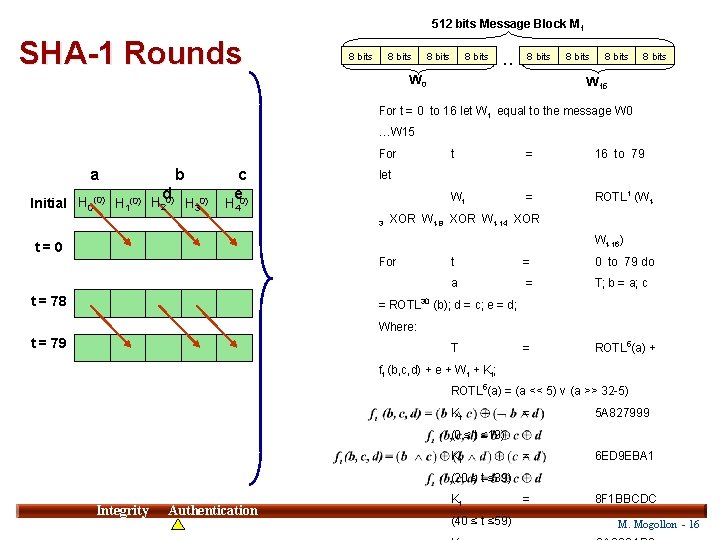
512 bits Message Block M 1 SHA-1 Rounds 8 bits . . 8 bits W 0 8 bits W 15 For t = 0 to 16 let W t equal to the message W 0 …W 15 For a b d Initial H 0(0) H 1(0) H 20) H 30) c e 0) t = 16 to 79 Wt = ROTL 1 (Wt- let H 4 3 XOR Wt-8 XOR Wt-14 XOR Wt-16) t=0 For t = 78 t = 0 to 79 do a = T; b = a; c = ROTL 5(a) + = ROTL 30 (b); d = c; e = d; Where: t = 79 T ft (b, c, d) + e + Wt + Kt; ROTL 5(a) = (a << 5) v (a >> 32 -5) Kt = 5 A 827999 = 6 ED 9 EBA 1 = 8 F 1 BBCDC (0 ≤ t ≤ 19) Kt (20 ≤ t ≤ 39) Integrity Authentication Kt (40 ≤ t ≤ 59) M. Mogollon - 16 16

MD 5 • MD 2, MD 4, and MD 5 are message-digest algorithms developed by Ronald Rivest in 1989, 1990, and 1991. • All three algorithms produce a 128 -bit message digest of the message input that may have any length, but, in reality it is expected that the message will have less than 264 bits. • The MD 5 sequentially processes blocks of 512 bits when computing the message digest, and padding is required even if the message is a multiple of 512. Padding is done as follows: — Append a “ 1” bit followed by a “ 0” bits until the length is 64 bits less than a multiple of 512 (length = 448 mod 512). — Append a 64 -bit representation of the pre-padded message length • The padded message length is 512 × n. Integrity 17 Authentication M. Mogollon - 17

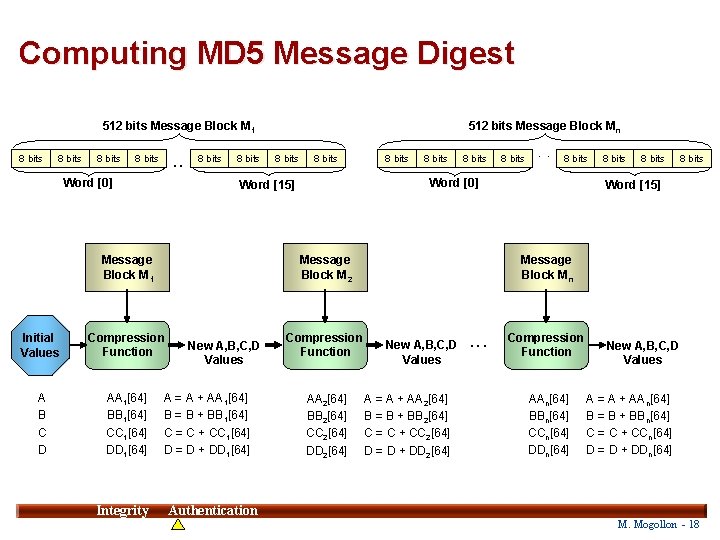
Computing MD 5 Message Digest 512 bits Message Block M 1 8 bits . . 8 bits Word [0] 8 bits 8 bits Message Block M 2 Initial Values Compression Function A B C D AA 1[64] BB 1[64] CC 1[64] DD 1[64] New A, B, C, D Values A = A + AA 1[64] B = B + BB 1[64] C = C + CC 1[64] D = D + DD 1[64] 8 bits . . 8 bits Word [0] Word [15] Message Block M 1 Integrity 512 bits Message Block Mn Compression Function AA 2[64] BB 2[64] CC 2[64] DD 2[64] 8 bits Word [15] Message Block Mn New A, B, C, D Values A = A + AA 2[64] B = B + BB 2[64] C = C + CC 2[64] D = D + DD 2[64] . . . Compression Function AAn[64] BBn[64] CCn[64] DDn[64] New A, B, C, D Values A = A + AAn[64] B = B + BBn[64] C = C + CCn[64] D = D + DDn[64] 18 Authentication M. Mogollon - 18

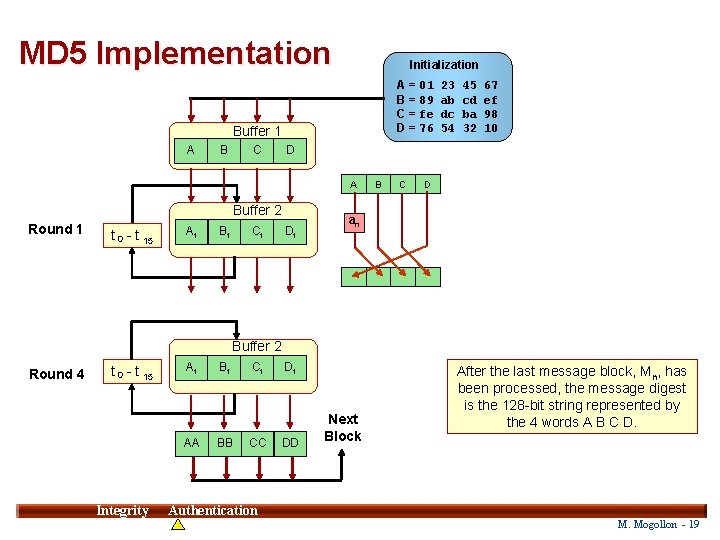
MD 5 Implementation Initialization A = 01 B = 89 C = fe D = 76 Buffer 1 A B C Buffer 2 t 0 - t 15 At Bt Ct 45 cd ba 32 67 ef 98 10 D A Round 1 23 ab dc 54 Dt B C D an Buffer 2 Round 4 t 0 - t 15 At AA Integrity Bt BB Ct CC Dt DD Next Block After the last message block, Mn, has been processed, the message digest is the 128 -bit string represented by the 4 words A B C D. 19 Authentication M. Mogollon - 19

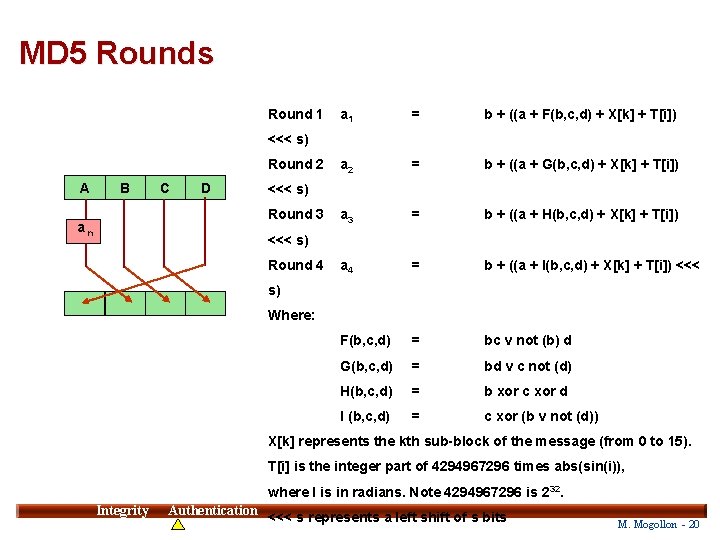
MD 5 Rounds Round 1 a 1 = b + ((a + F(b, c, d) + X[k] + T[i]) a 2 = b + ((a + G(b, c, d) + X[k] + T[i]) a 3 = b + ((a + H(b, c, d) + X[k] + T[i]) a 4 = b + ((a + I(b, c, d) + X[k] + T[i]) <<< F(b, c, d) = bc v not (b) d G(b, c, d) = bd v c not (d) H(b, c, d) = b xor c xor d I (b, c, d) = c xor (b v not (d)) <<< s) Round 2 A B C D <<< s) Round 3 an <<< s) Round 4 s) Where: X[k] represents the kth sub-block of the message (from 0 to 15). T[i] is the integer part of 4294967296 times abs(sin(i)), where I is in radians. Note 4294967296 is 232. Integrity Authentication <<< s represents a left shift of s bits 20 M. Mogollon - 20

Hash Functions Secure Hash Algorithm (SHA-1) • Developed by NSA and is required for use with the Digital Signature Algorithm (DSA) • Works on messages up to 264 in length. • Produces a 160 -bit message digest. • Processes block messages of 512 bits. • Has four rounds of twenty operations in main loop of algorithm. • Performs a non-linear operation on three of the five variables a, b, c, d, e in each operation Integrity Message Digest 5 (MD 5) • Developed by Ronald Rivest in 1991 (MD 2 in 89, MD 4 in 90). • Works on messages up to 264 in length. • Produces a 128 -bit message digest. • Processes block messages of 512 bits. • Has four rounds of sixteen operations in main loop of algorithm. • Performs a non-linear operation on three of the four variables A, B, C, D in each operation 21 Authentication M. Mogollon - 21

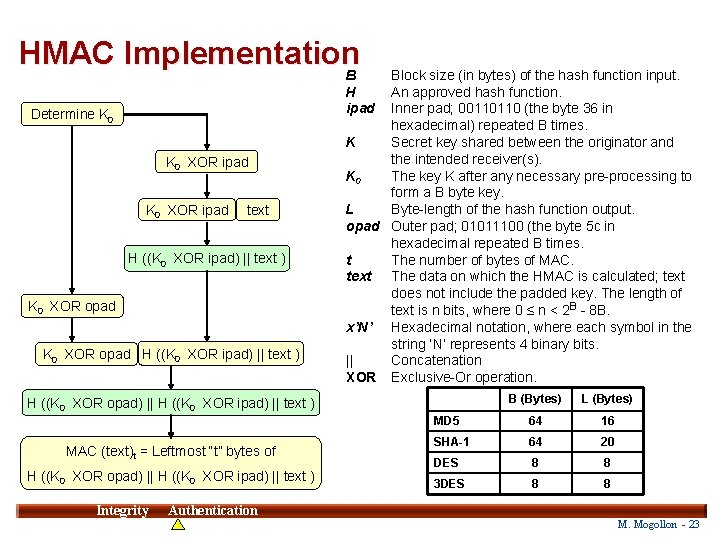
Keyed-Hash Message Authentication Code (HMAC) IP Header AH Message Shared Key 128 bit PAD Hash Function SHA-1 or MD 5 160 or 128 bits • HMAC is cryptographically strong way to use a specific hash function for MAC calculation. • The hash function is applied twice in succession. — In the first round, the input to the hash function is the shared secret key and the message. — The 160 -bit or 128 -bit output hash value and the key are input again to the hash function in the second round. • HMAC output could be truncated (i. e. , the length of the MAC used is less than the length of the output of the MAC function). If HMAC is truncated to 96 bits, it is then called HMAC-MD 5 -96 or HMAC-SHA-1 -96 Integrity 22 Authentication M. Mogollon - 22

HMAC Implementation B Determine K 0 XOR ipad text H ((K 0 XOR ipad) || text ) K 0 XOR opad H ((K 0 XOR ipad) || text ) Block size (in bytes) of the hash function input. H An approved hash function. ipad Inner pad; 00110110 (the byte 36 in hexadecimal) repeated B times. K Secret key shared between the originator and the intended receiver(s). K 0 The key K after any necessary pre-processing to form a B byte key. L Byte-length of the hash function output. opad Outer pad; 01011100 (the byte 5 c in hexadecimal repeated B times. t The number of bytes of MAC. text The data on which the HMAC is calculated; text does not include the padded key. The length of text is n bits, where 0 ≤ n < 2 B - 8 B. x’N’ Hexadecimal notation, where each symbol in the string ‘N’ represents 4 binary bits. || Concatenation XOR Exclusive-Or operation. B (Bytes) L (Bytes) MD 5 64 16 SHA-1 64 20 DES 8 8 3 DES 8 8 H ((K 0 XOR opad) || H ((K 0 XOR ipad) || text ) MAC (text)t = Leftmost “t” bytes of H ((K 0 XOR opad) || H ((K 0 XOR ipad) || text ) Integrity 23 Authentication M. Mogollon - 23

What is Authentication? authentication / n. (1) The act of identifying or verifying the entity that originated the message or the corroboration (proof) of the sender's identity, i. e. , that he is who he claims to be. Written messages are authenticated with a handwritten signature so the receiver of the message is able to validate the message. (2) access. The act of identifying or verifying the eligibility of a station, originator, or individual to access specific categories of information. digital signature / n. electronic equivalent of a signature on a message. It combines a one-way hash function with public key cryptography. A digital signature must be a function of the documents it signs. A Digital Signature is created by taking the hash function of a message and encrypting it with the sender’s private key. Integrity 24 Authentication M. Mogollon - 24

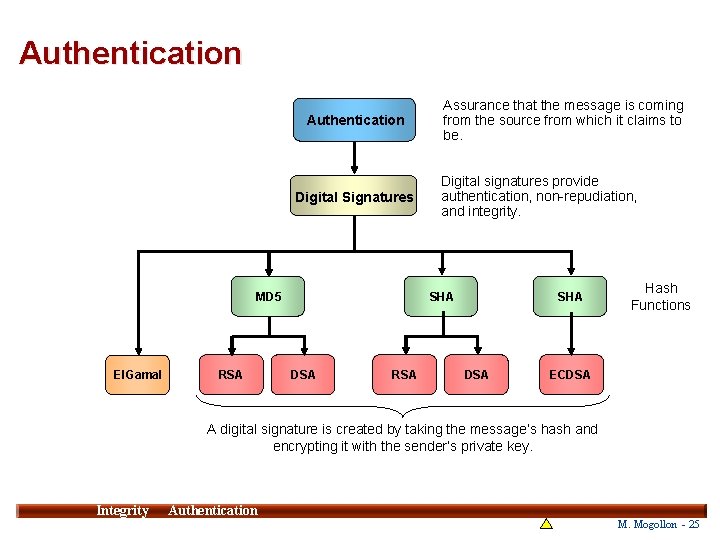
Authentication Digital Signatures MD 5 El. Gamal RSA Assurance that the message is coming from the source from which it claims to be. Digital signatures provide authentication, non-repudiation, and integrity. SHA DSA RSA SHA DSA Hash Functions ECDSA A digital signature is created by taking the message’s hash and encrypting it with the sender’s private key. Integrity 25 Authentication M. Mogollon - 25

Digital Signatures • A digital signature is the electronic analogue of a handwritten signature. Digital signatures provide the following: — Authentication -It should be possible for the recipient of a message to ascertain its origin; — Non-repudiation -A sender should not be able to later deny having sent and signed the message; — Integrity -It should be possible for the recipient of the message to verify that it has not been modified in transit. • A digital signature must provide the following assurances: — The signature is not forgeable. — The signature can be validated. — Once a message is signed, the sender must not be able to repudiate it. Integrity 26 Authentication M. Mogollon - 26

Digital Signatures Alice’s Private Key Hash Encipher Alice’s Public Key Digital Signature Hash Decipher Hash Function Verification Cleartext Message Alice (Sender) Cleartext Message Hash Function Hash Bob (Recipient) If both values are equal, the message is from Alice and it has not been tampered with. A Digital Signature is created by taking the hash function of a message and encrypting it with the sender’s private key. Integrity 27 Authentication M. Mogollon - 27

Digital Signatures • The Digital Signature Standard (DSS), FIPS Pub 186 -2, prescribes three algorithms suitable for digital signatures: — Digital Signature Algorithm (DSA) – Standard for digital authentication. – Initial 512 -bit key size increased to 1024 for better security. — RSA algorithm – Uses MD 5 as a hash and RSA public Key for signing. — ECDSA algorithm. – Described in Appendix 6 of the FIPS Pub 186 -2 are the recommended Elliptic Curves for Federal Government use. • El. Gamal — Signs the message, not the message digest of the message. Integrity 28 Authentication M. Mogollon - 28

Digital Signature Algorithm (DSA) Alice Bob p, q, g, y p, q, g x y = gx mod p r = (g k mod p) mod q s = (k -1(H(m) + x r)) mod q Send Message m and Alice’s signature, r and s H (m) = Secure Hash Algorithm of message m Bob verifies signature by computing w = (s′)-1 mod q u 1 = ((H(m′) w) mod q u 2 = ((r′) w) mod q v = ((g u 1 y u 2) mod p) mod q p, q, and g can be public. x is an integer with 0 < x < q. Alice’s private and public keys are x and y. x and k must be secret. k must be changed for each signature. Integrity If v = r, then the signature is verified. m′, r′, and s′ are the received versions of m, r, and s, 29 Authentication M. Mogollon - 29

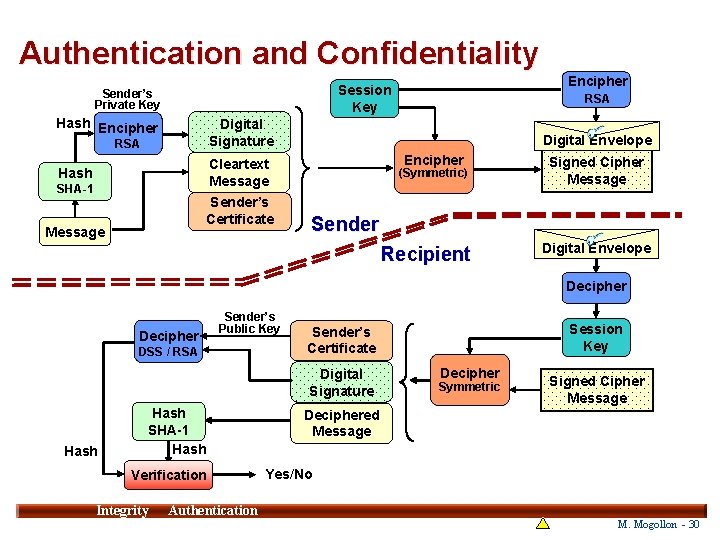
Authentication and Confidentiality Encipher Session Key Sender’s Private Key Hash Encipher RSA Digital Signature RSA Cleartext Message Sender’s Certificate Hash SHA-1 Message Digital Envelope Encipher (Symmetric) Signed Cipher Message Sender Recipient Digital Envelope Decipher Sender’s Public Key DSS / RSA Digital Signature Hash SHA-1 Hash Verification Integrity Session Key Sender’s Certificate Decipher Symmetric Signed Cipher Message Deciphered Message Yes/No 30 Authentication M. Mogollon - 30

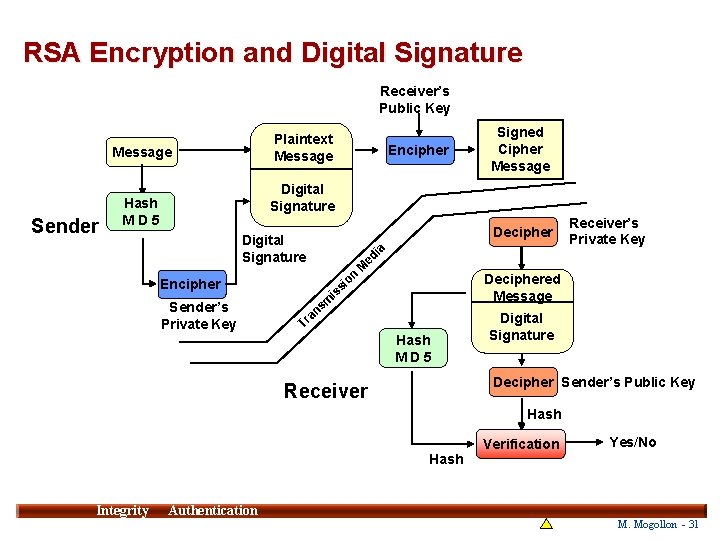
RSA Encryption and Digital Signature Receiver’s Public Key Plaintext Message Sender Encipher Signed Cipher Message Digital Signature Hash MD 5 Decipher Digital Signature ia ed on M Deciphered Message si is Encipher Sender’s Private Key Receiver’s Private Key m s an r T Hash MD 5 Digital Signature Decipher Sender’s Public Key Receiver Hash Verification Yes/No Hash Integrity 31 Authentication M. Mogollon - 31

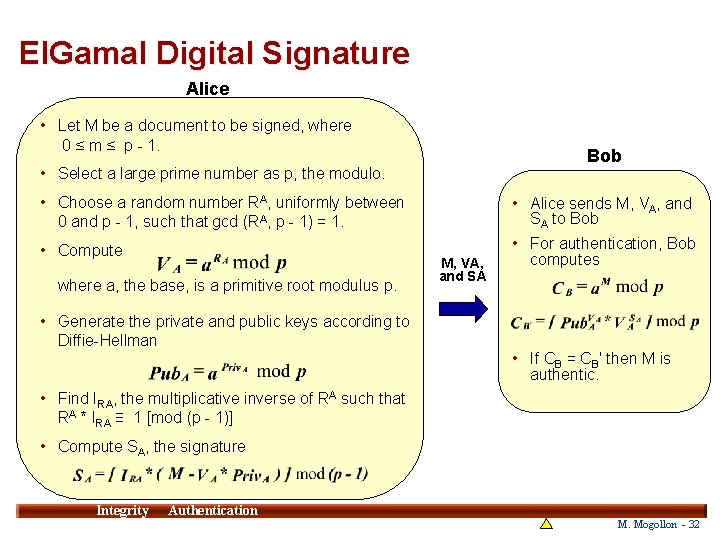
El. Gamal Digital Signature Alice • Let M be a document to be signed, where 0 ≤ m ≤ p - 1. Bob • Select a large prime number as p, the modulo. • Choose a random number RA, uniformly between 0 and p - 1, such that gcd (RA, • Alice sends M, VA, and SA to Bob p - 1) = 1. • For authentication, Bob • Compute where a, the base, is a primitive root modulus p. M, VA, and SA computes • Generate the private and public keys according to Diffie-Hellman • If CB = CB′ then M is authentic. • Find IRA, the multiplicative inverse of RA such that RA * IRA ≡ 1 [mod (p - 1)] • Compute SA, the signature Integrity 32 Authentication M. Mogollon - 32

To Probe Further • • MD 5 Message Digest Algorithm, RFC 1321 • Kohnfelder, L. M. (February 1978). On the Signature Reblocking Problem in Public-Key Cryptosystems (p. 179). Communications of the ACM, Vol. 21, No. 2. • National Institute of Standards and Technology (1995). Secure Hash Standard. FIPS PUB 180 -1. • National Institute of Standards and Technology (1995). The Keyed-Hash Message Authentication Code. FIPS PUB 198 • National Institute of Standards and Technology (2000). Digital Signature Standard. FIPS PUB 186 -2 • Newman, D. B. , Omura, J K. , Pickholtz, R. L. (April 1987). Public Key Management for Network Security (pp. 12 -13). IEEE Network Magazine, Vol. 1, No. 2. El. Gamal, T. A. (July 1985). Public Key Cryptosystem and a Signature Scheme Based on Discrete Logarithms (pp. 469 -472). IEEE Transactions on Information Theory, Vol. IT-31. Integrity 33 Authentication M. Mogollon - 33