Security Strategies in Windows Platforms and Applications Lesson












- Slides: 26

Security Strategies in Windows Platforms and Applications Lesson 6 Group Policy Control in Microsoft Windows © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved.

Learning Objective and Key Concepts Learning Objective § Define and apply Group Policy controls in Microsoft Windows. Key Concepts § Group Policy Object § Auditing Group Policy § Group Policy best practices Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 2

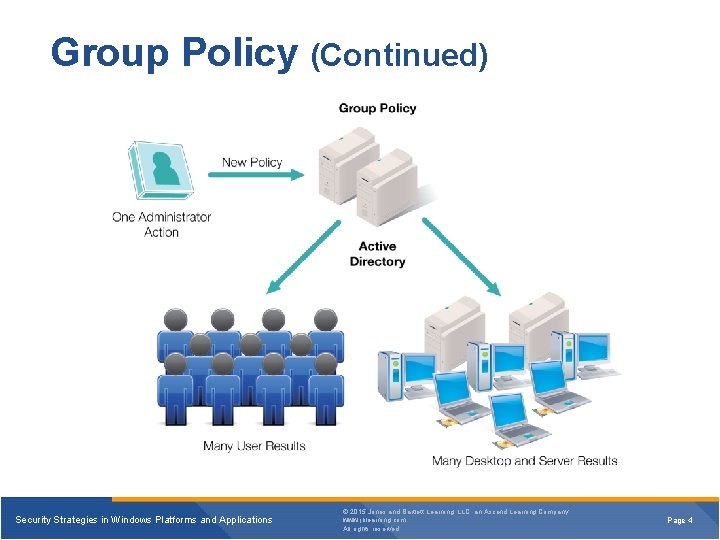
Group Policy and Group Policy Objects § Some Group Policy features include: • Centralized location for settings • Useful to deploy security settings • Automatic settings distribution • Options to apply standard settings § Collections of Group Policy settings can be stored in named objects called Group Policy Objects (GPOs) Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 3

Group Policy (Continued) Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 4

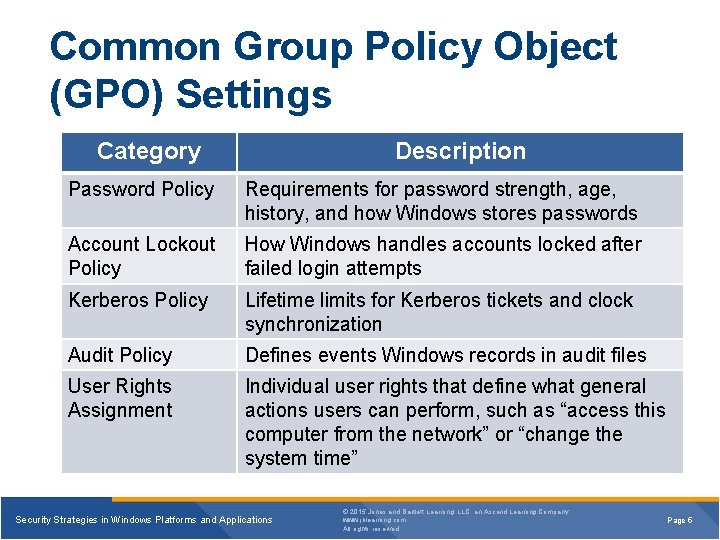
Common Group Policy Object (GPO) Settings Category Description Password Policy Requirements for password strength, age, history, and how Windows stores passwords Account Lockout Policy How Windows handles accounts locked after failed login attempts Kerberos Policy Lifetime limits for Kerberos tickets and clock synchronization Audit Policy Defines events Windows records in audit files User Rights Assignment Individual user rights that define what general actions users can perform, such as “access this computer from the network” or “change the system time” Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 5

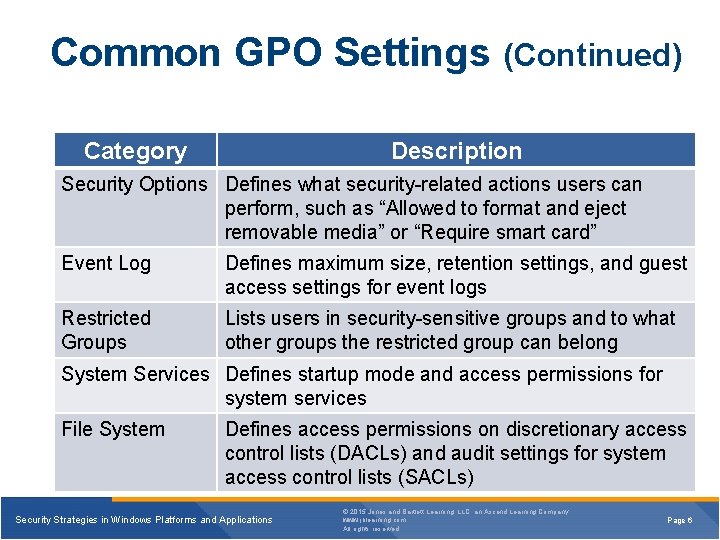
Common GPO Settings (Continued) Category Description Security Options Defines what security-related actions users can perform, such as “Allowed to format and eject removable media” or “Require smart card” Event Log Defines maximum size, retention settings, and guest access settings for event logs Restricted Groups Lists users in security-sensitive groups and to what other groups the restricted group can belong System Services Defines startup mode and access permissions for system services File System Defines access permissions on discretionary access control lists (DACLs) and audit settings for system access control lists (SACLs) Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 6

Group Policy Strategies § Create GPOs for closely-related settings. § Avoid making GPOs too specific. § Create organizational units (OUs) for logical groups of computers. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 7

Group Policy Strategies (Continued) § Use Microsoft resources for effective GPOs: • Group Policy best practices analyzer • Security compliance management toolkit • GPO accelerator Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 8

Making Group Policy Conform to Security Policy § GPOs you define and use should conform to your security policy § Reasons: • To allow management to meet security responsibilities • To ensure that there are no gaps in your security policy and your policy doesn’t contain additional controls Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 9

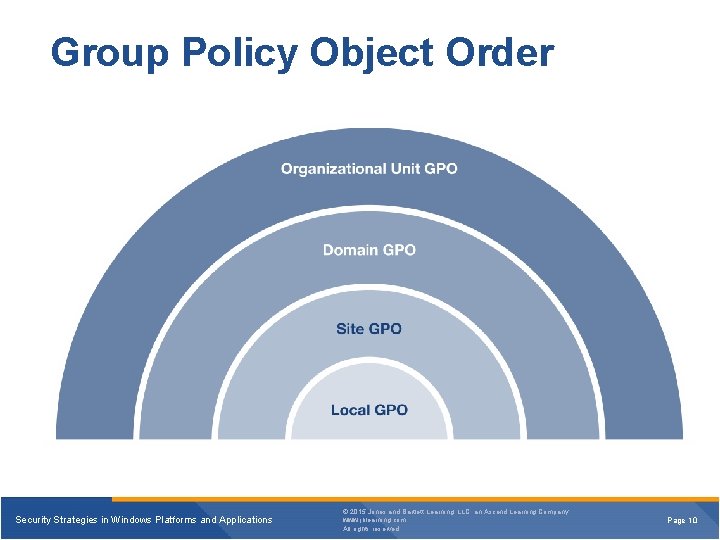
Group Policy Object Order Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 10

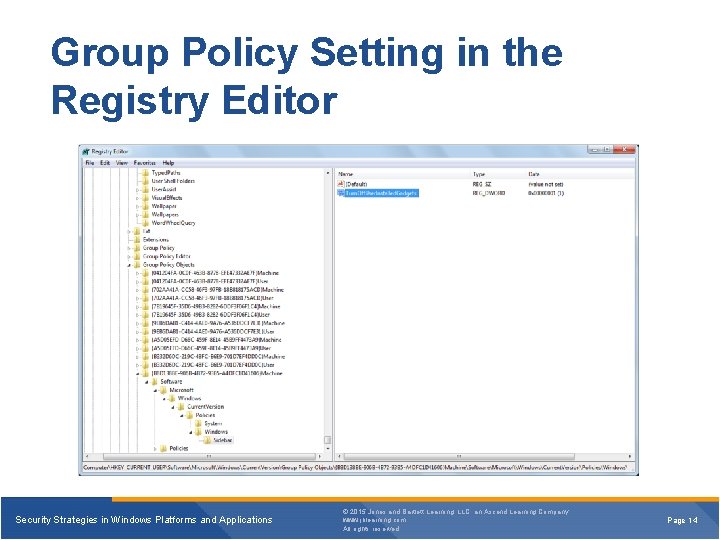
Types of GPOs in the Registry § The Registry: • Is a database in Windows that stores configuration settings for the computer and users • Stores Group Policy settings in HKEY_CURRENT_USER (HKCU) or HKEY_LOCAL_MACHINE (HKLM) Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 11

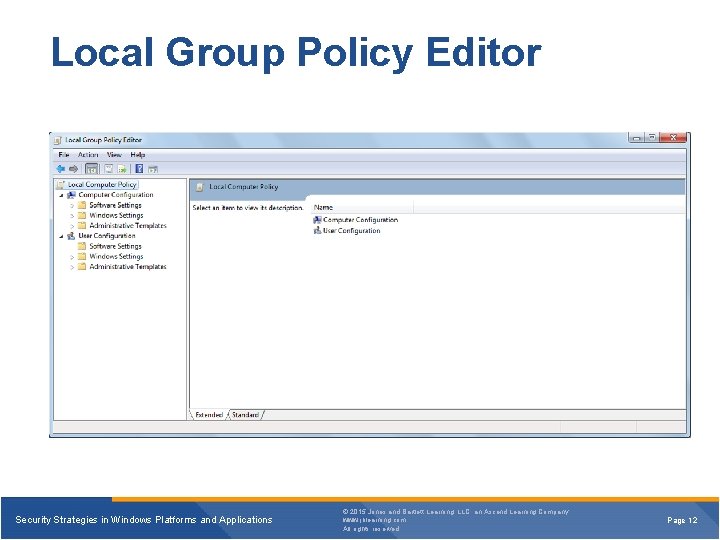
Local Group Policy Editor Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 12

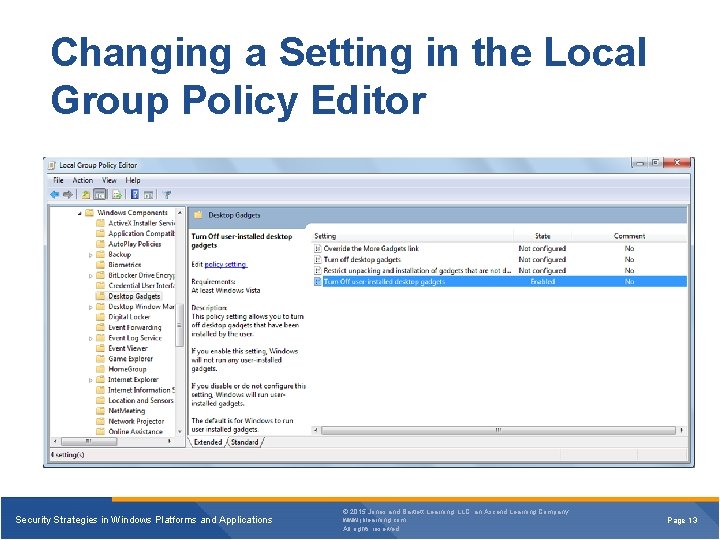
Changing a Setting in the Local Group Policy Editor Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 13

Group Policy Setting in the Registry Editor Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 14

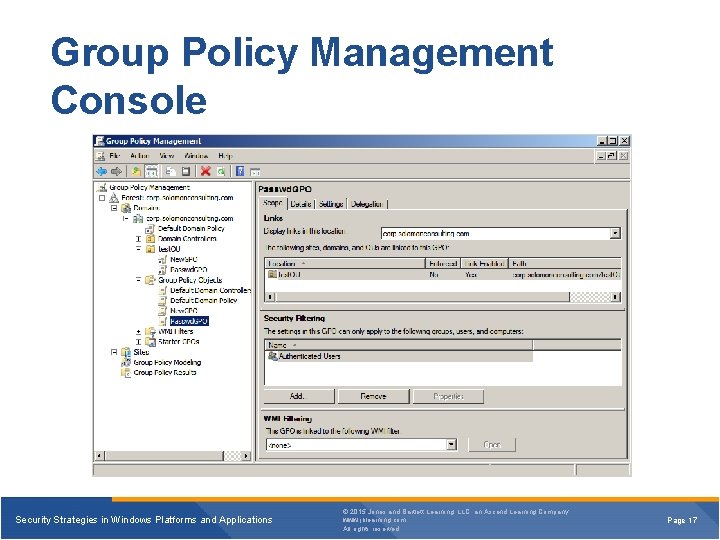
Types of GPOs in Active Directory § Defining GPOs in AD lets you centralize security rules and control how Windows applies each rule § Create AD GPOs on a domain controller using the Group Policy Management Console (GPMC) Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 15

Actions You Can Perform in the GPMC § Create and edit GPOs § Import and export GPOs § Copy and paste GPOs § Back up and restore GPOs § Search for GPOs § Create reports on GPOs Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 16

Group Policy Management Console Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 17

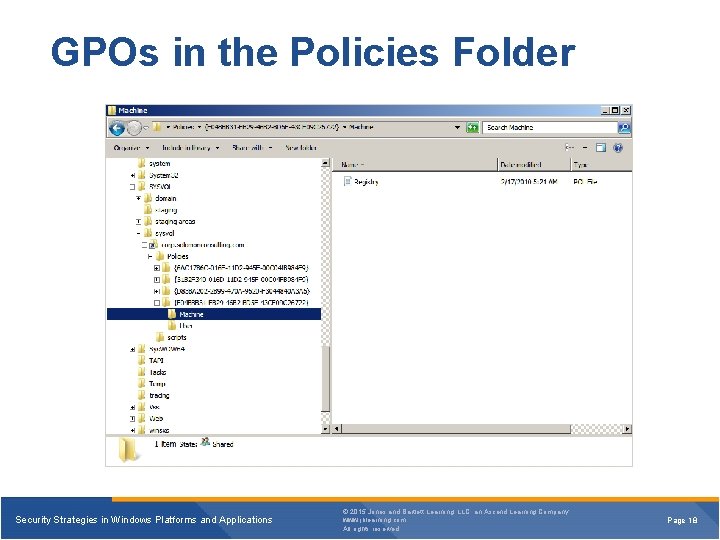
GPOs in the Policies Folder Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 18

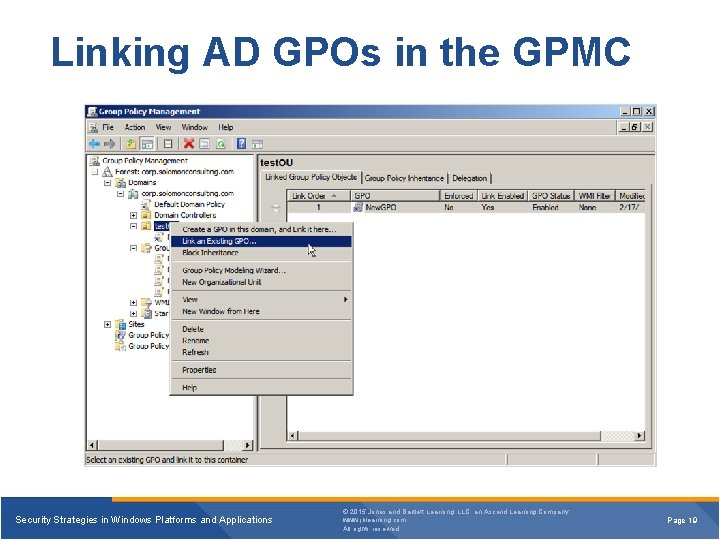
Linking AD GPOs in the GPMC Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 19

Designing, Deploying, and Tracking Group Policy Controls GPO application order Security filters GPT Windows Management Instrumentation (WMI) filters Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 20

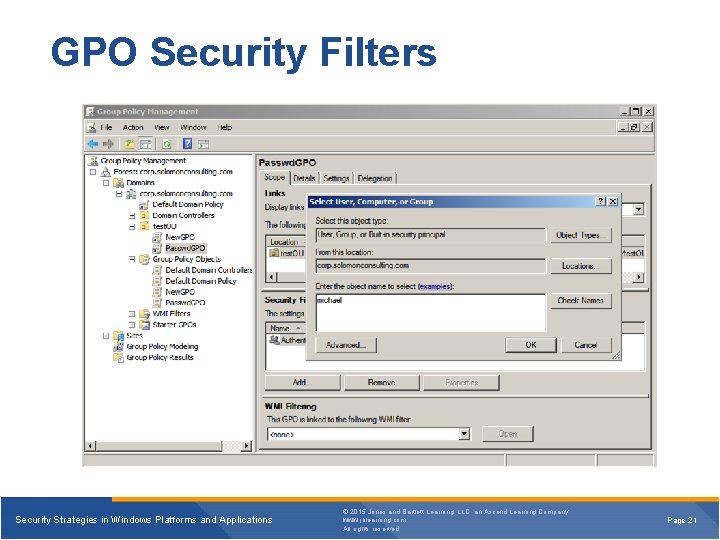
GPO Security Filters Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 21

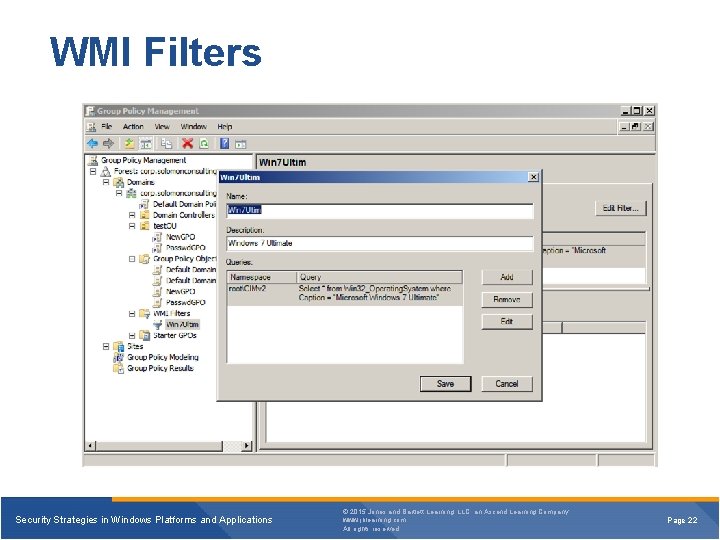
WMI Filters Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 22

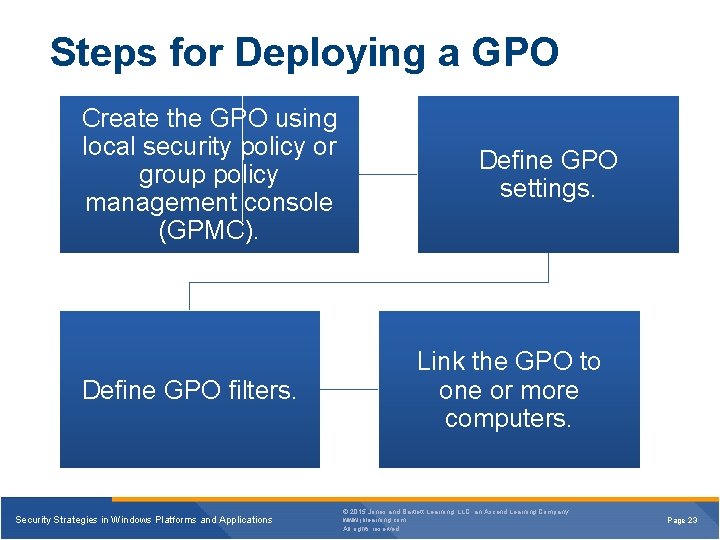
Steps for Deploying a GPO Create the GPO using local security policy or group policy management console (GPMC). Define GPO filters. Security Strategies in Windows Platforms and Applications Define GPO settings. Link the GPO to one or more computers. © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 23

Auditing Group Policy § Group Policy Inventory • You must download from Microsoft • Provides an inventory list of GPO and other settings § Resultant Set of Policy (RSOP) • Included in Windows • Shows what settings apply to a specific user on a specific computer Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 24

Best Practices Group Policy Guidelines § Define OUs that reflect your organization’s functional structure. § Create OU GPOs for controls required in your security policy. § Use meaningful names for GPOs to make maintenance and administration easier. § Deploy GPOs in a test environment before deploying to your live environment. § Use security filtering and WMI filters to restrict settings when necessary. § Back up your GPOs regularly. § Do not modify the default policies—instead, create new GPOs. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 25

Summary § Group Policy strategies § Auditing Group Policy § Group Policy best practices Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 26