Security Strategies in Windows Platforms and Applications Lesson













- Slides: 31

Security Strategies in Windows Platforms and Applications Lesson 11 Hardening the Microsoft Windows Operating System © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved.

Learning Objective and Key Concepts Learning Objective § Identify and implement the most effective security controls to make computers and networks as secure as possible. Key Concepts § Hardening techniques § Hardening servers and clients § Hardening networks Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 2

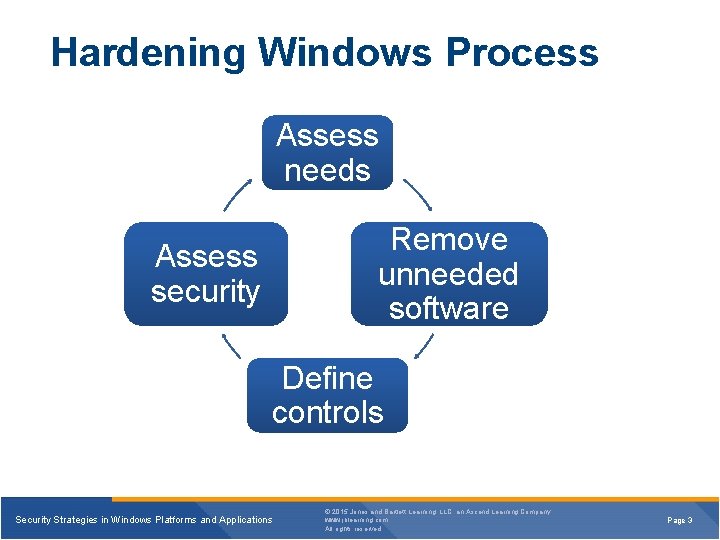
Hardening Windows Process Assess needs Remove unneeded software Assess security Define controls Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 3

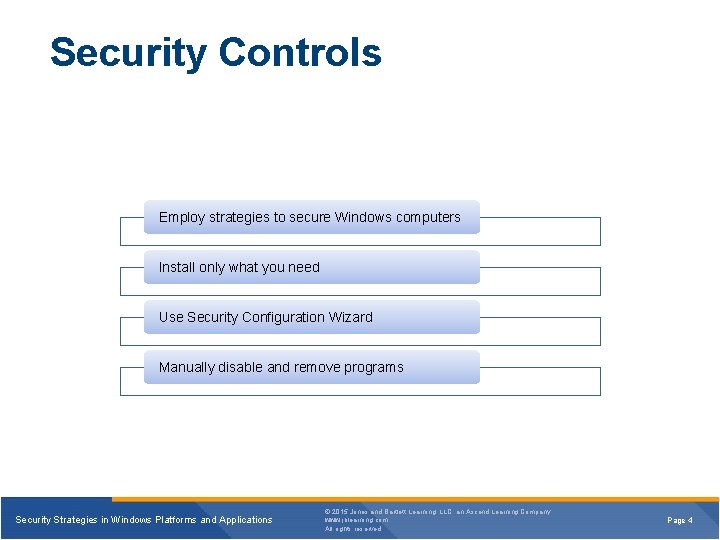
Security Controls Employ strategies to secure Windows computers Install only what you need Use Security Configuration Wizard Manually disable and remove programs Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 4

Windows Security Configuration Wizard—Configuration Action Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 5

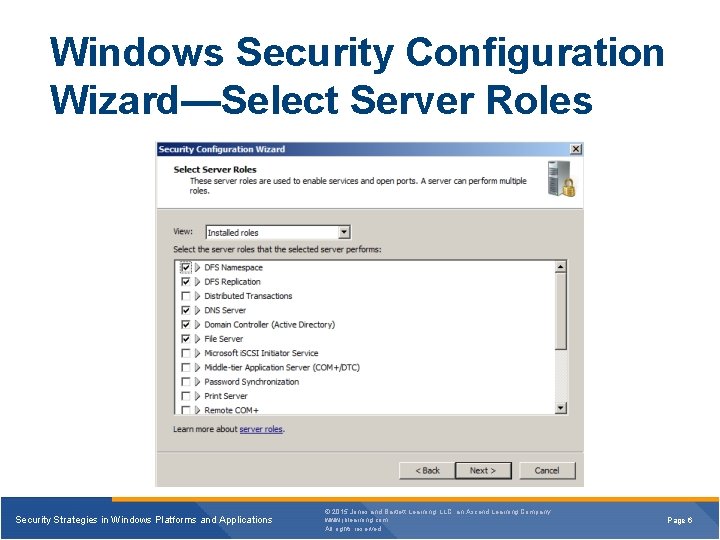
Windows Security Configuration Wizard—Select Server Roles Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 6

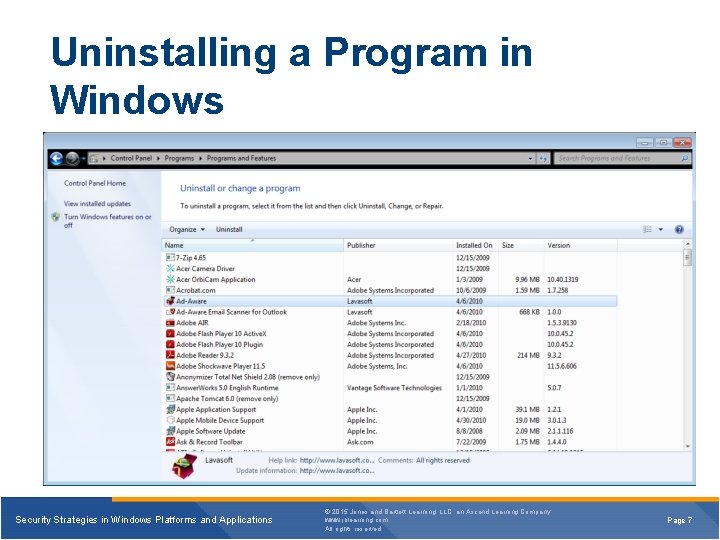
Uninstalling a Program in Windows Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 7

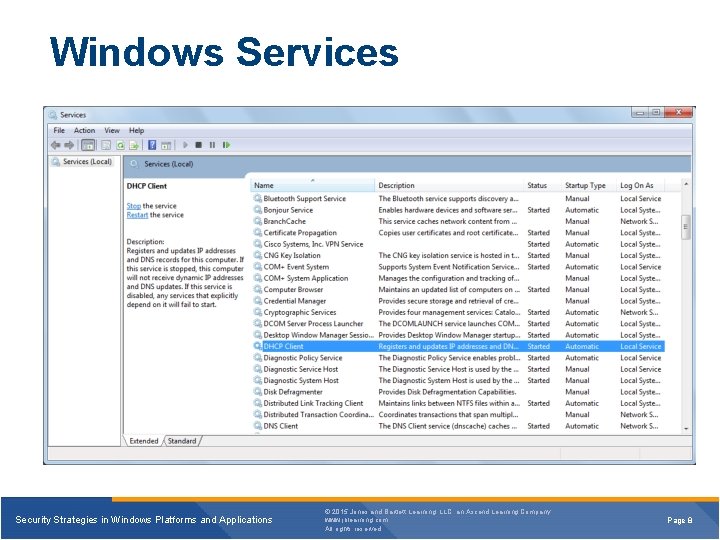
Windows Services Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 8

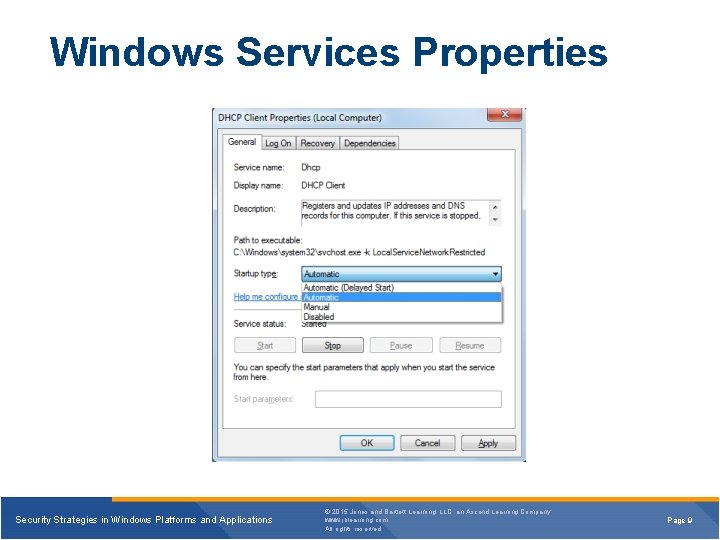
Windows Services Properties Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 9

Addressing Authentication Weaknesses § Run SCW on each server § Disallow older authentication methods § Remove or disable any unused or inactive user accounts § Protect Administrator user rights § Establish and enforce strong account policies • Password policy • Account policy • Kerberos policy Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 10

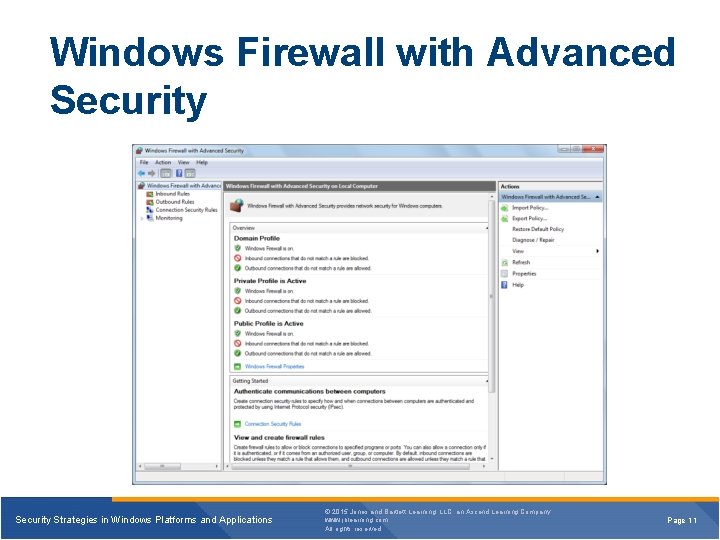
Windows Firewall with Advanced Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 11

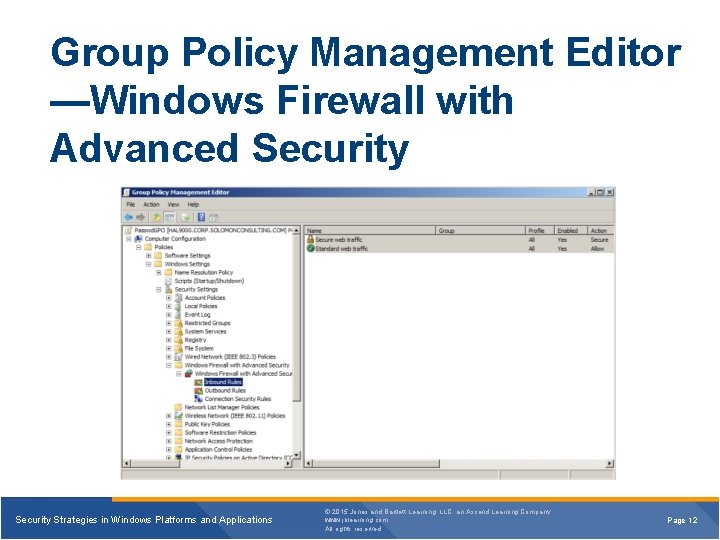
Group Policy Management Editor —Windows Firewall with Advanced Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 12

Securing Information and Operations § Active Directory (AD) • Limit the number of administrators with access to AD • Ensure that administrators use separate Administrator user accounts • Administrators should have one account for AD administration and at least one other account for other administration tasks • Create an AD security group • Require that AD administrators do their AD work only from dedicated terminal servers instead of workstations Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 13

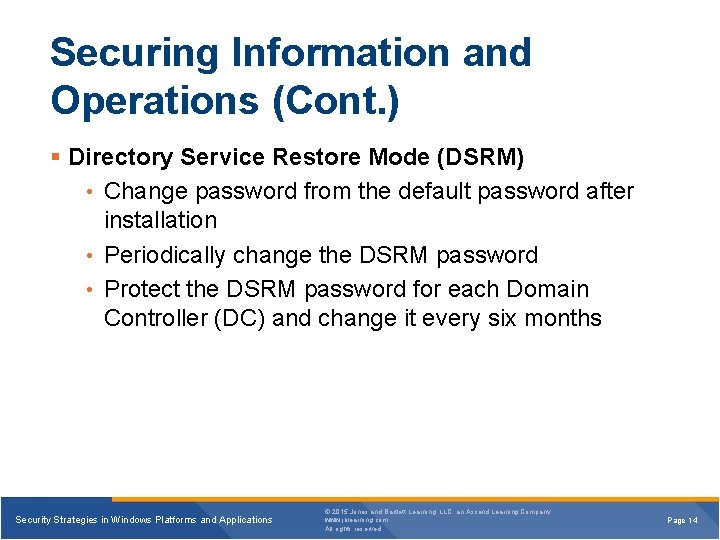
Securing Information and Operations (Cont. ) § Directory Service Restore Mode (DSRM) • Change password from the default password after installation • Periodically change the DSRM password • Protect the DSRM password for each Domain Controller (DC) and change it every six months Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 14

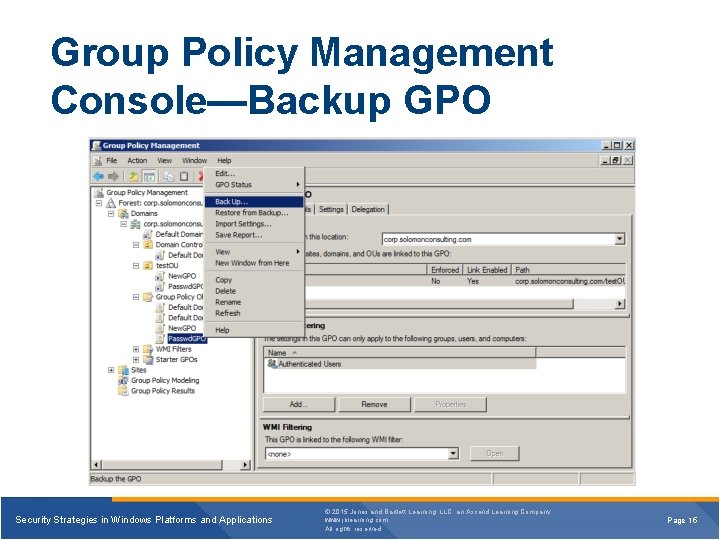
Group Policy Management Console—Backup GPO Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 15

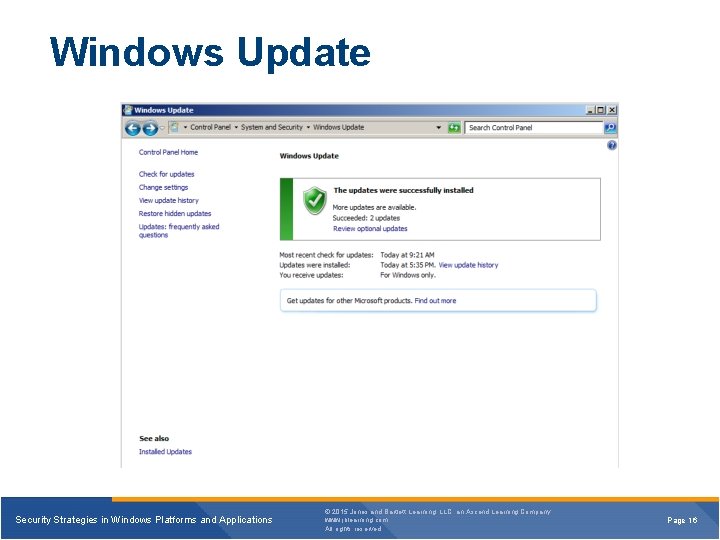
Windows Update Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 16

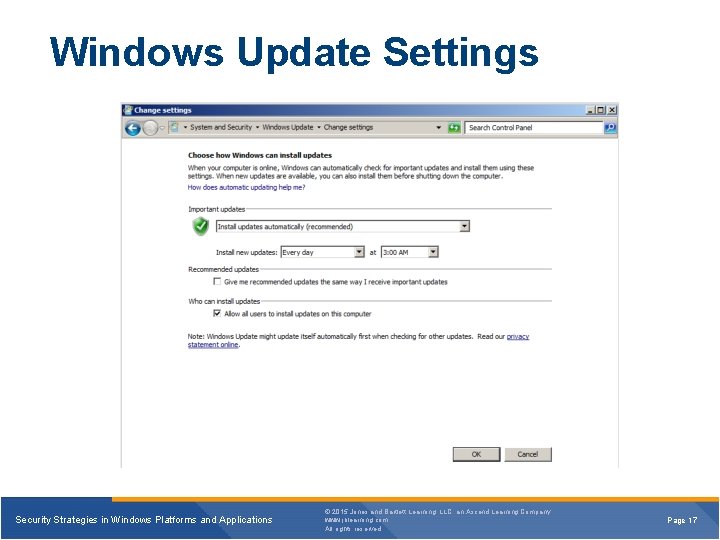
Windows Update Settings Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 17

Hardening Servers § Ensure server computers don’t do anything they’re not supposed to do § Harden the services they are supposed to provide § Run SCW utility § Use nmap utility § Enable IPSec for server-to-server communications Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 18

Hardening Workstations § Use malware protection § Mitigate vulnerabilities § Disable programs and services not used § Review firewall settings Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 19

Hardening Servers and Workstations Network Access Control (NAC) Authentication Servers Remote Authentication Dial In User Service (RADIUS) Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 20

Hardening Servers and Workstations Terminal Access Controller Access Control System Plus (TACACS+) Virtual Private Networks (VPNs) Encryption Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 21

Hardening PKI § Public key infrastructure (PKI): The hardware, software, policies, and procedures to manage all aspects of digital certificates § Makes environments more secure § Ensure all computers that participate are hardened § Harden Certificate Authority (CA) servers Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 22

Hardening PKI (Cont. ) § Ensure your CAs are physically secure and only accessible by authorized administrators § Backup CA keys and store them in a safe location § Use GPOs to distribute root CA certificates Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 23

Creating Security Awareness Methods to Remind Users of the Importance of Security Posters and banners E-mail newsletters and security policy updates Periodic Web site reminders Social media messages Daily or weekly tip programs Contests with security themes Security events on specific dates Lunch-and-learn meetings Visible modeling of good security behaviors by organization’s leaders Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 24

Best Practices § Install only the Server Core option when you don’t need extra functionality. § Select the minimum number of roles. § Run SCW immediately after installation of Windows Server. § Install updates; configure for automatic Windows updates. § Install and run Microsoft Baseline Security Analyzer (MBSA). § Create one or more user accounts with Administrator rights. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 25

Best Practices (Cont. ) § Disable the Administrator and Guest user accounts. § Disable all unneeded services. § Close all ports not required by services or applications. § Create GPOs for all security settings, including firewall rules. § Use AD to distribute all configuration changes using GPOs. § Create a backup of each GPO. § Scan all computers for open ports. § Limit physical access to all critical servers. § Create an initial baseline backup. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 26

Best Practices (Cont. ) § Change the AD DSRM password periodically, at least every six months. § Install anti-malware software on each computer. § Ensure all anti-malware software and data is current. § Use NAC software or devices to control remote computer connections. § Use remote authentication methods to authorize remote computers and users. § Require secure VPNs to access internal network resources. § Use IPSec with digital certificates to authenticate computer-to-computer connections in the datacenter. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 27

Best Practices (Cont. ) § Require security awareness training prior to issuing access credentials. § Require periodic recurrent security awareness training to retain access credentials. § Provide continuing security awareness. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 28

Summary § Methods of hardening Microsoft Windows § Process of hardening Microsoft Windows § Key roles involved in hardening environments § Recent security breaches Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 29

Securing Windows Methods Network Security Controls Securing Network Services Hardening Windows Authentication Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 30

Virtual Lab § Securing Servers with the Security Configuration Wizard and the Windows Firewall Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 31