INFORMATION SECURITY MANAGEMENT PROTECTION MECHANISMS CRYPTOGRAPHY Cryptography Encryption












- Slides: 24

INFORMATION SECURITY MANAGEMENT PROTECTION MECHANISMS - CRYPTOGRAPHY

Cryptography • Encryption – The process of converting an original message into a form that cannot be understood by unauthorized individuals • Cryptology – The science of encryption – Composed of two disciplines: – – cryptography cryptanalysis

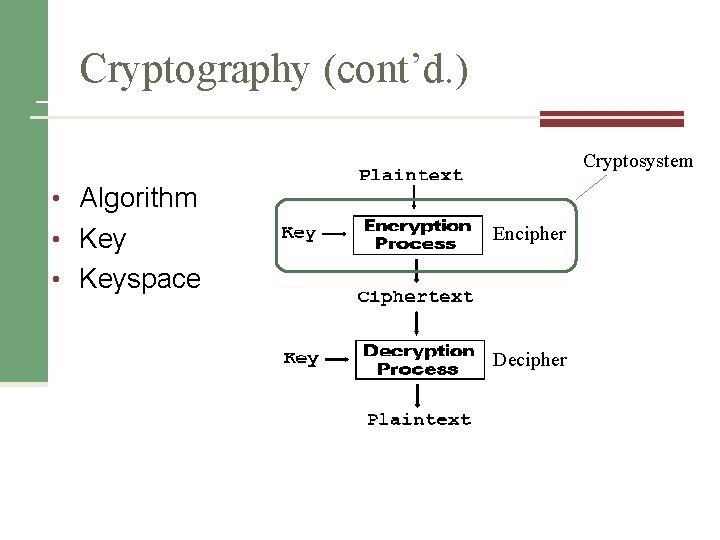
Cryptography (cont’d. ) Cryptosystem • Algorithm • Key Encipher • Keyspace Decipher

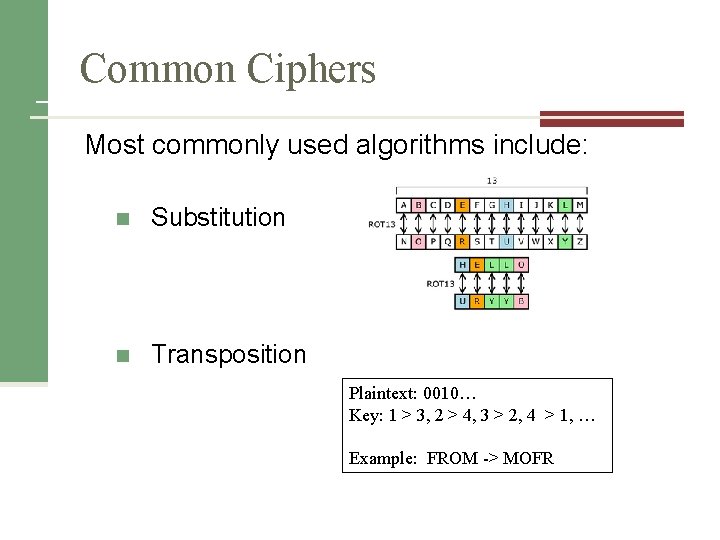
Common Ciphers Most commonly used algorithms include: n Substitution n Transposition Plaintext: 0010… Key: 1 > 3, 2 > 4, 3 > 2, 4 > 1, … Example: FROM -> MOFR

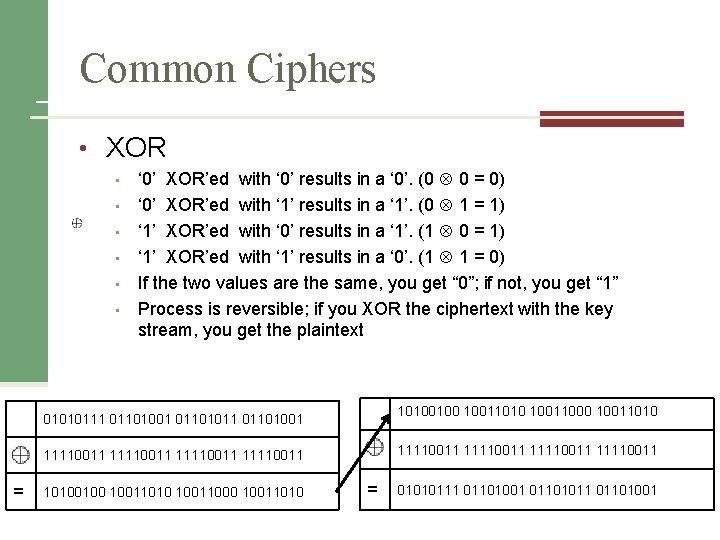
Common Ciphers • XOR • • • ‘ 0’ XOR’ed with ‘ 0’ results in a ‘ 0’. (0 0 = 0) ‘ 0’ XOR’ed with ‘ 1’ results in a ‘ 1’. (0 1 = 1) ‘ 1’ XOR’ed with ‘ 0’ results in a ‘ 1’. (1 0 = 1) ‘ 1’ XOR’ed with ‘ 1’ results in a ‘ 0’. (1 1 = 0) If the two values are the same, you get “ 0”; if not, you get “ 1” Process is reversible; if you XOR the ciphertext with the key stream, you get the plaintext 10100100 10011010 10011000 10011010 01010111 01101001 01101011 01101001 11110011 11110011 = 10100100 10011010 10011000 10011010 = 01010111 01101001 01101011 01101001

Common Ciphers • Book or running key cipher – Uses text in a book as the algorithm to decrypt a message – The key relies on two components: n n Knowing which book to use A list of codes representing the page number, line number, and word number of the plaintext word

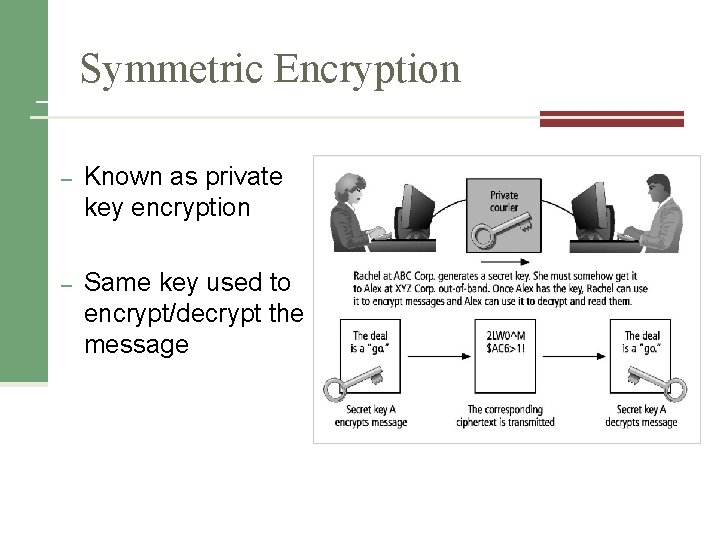
Symmetric Encryption – Known as private key encryption – Same key used to encrypt/decrypt the message

Symmetric Encryption Cryptosystem • Data Encryption Standard (DES) – Based on the Data Encryption Algorithm which uses a 64 -bit block size and a 56 -bit key – Cracked in 1997 – Triple DES (3 DES) improved version • Advanced Encryption Standard (AES) – Based on the Rinjndael Block Cipher n Variable block length and a key length of either 128, 192, or 256 bits

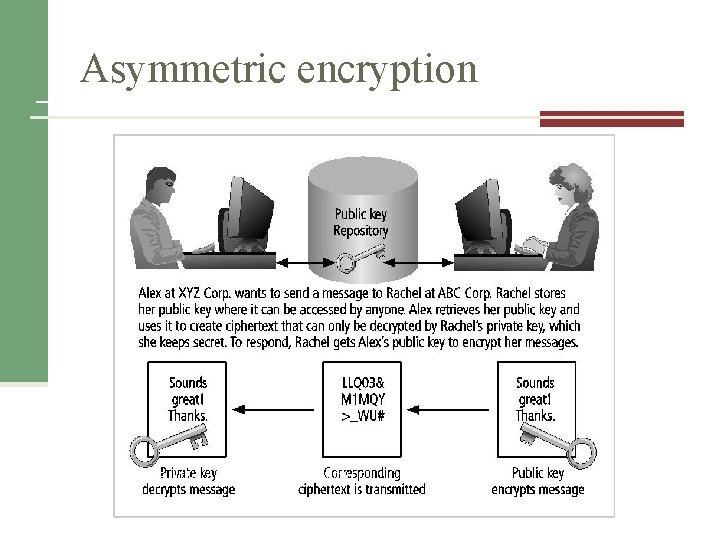
Asymmetric encryption Uses two different, but related keys Either key used to encrypt/decrypt message n However, if Key A is used to encrypt the message, then only Key B can decrypt it; conversely, if Key B is used to encrypt a message, then only Key A can decrypt it n Most valuable when one of the keys is private and the other is public

Asymmetric encryption Figure 10 -12 Public key encryption Source: Course Technology/Cengage Learning

Digital Signatures – Asymmetric process is reversed n n The fact that the message was sent by the organization that owns the private key cannot be refuted This nonrepudiation is the foundation of digital signatures • Based on: • Digital certificate • A certificate authority (CA)

Public key infrastructure (PKI) • The entire set of hardware, software, and cryptosystems necessary to implement public key encryption • PKI systems are based on public key cryptosystems and include digital certificates and certificate authorities

Encryption Operations (cont’d. ) • PKI provides the following services – Authentication – Integrity – Confidentiality – Authorization – Nonrepudiation

Using Cryptographic Controls • Modern cryptosystems can generate unbreakable ciphertext • Cryptographic controls used for: – – – e-mail and its attachments e-commerce transactions remote access through VPN connections

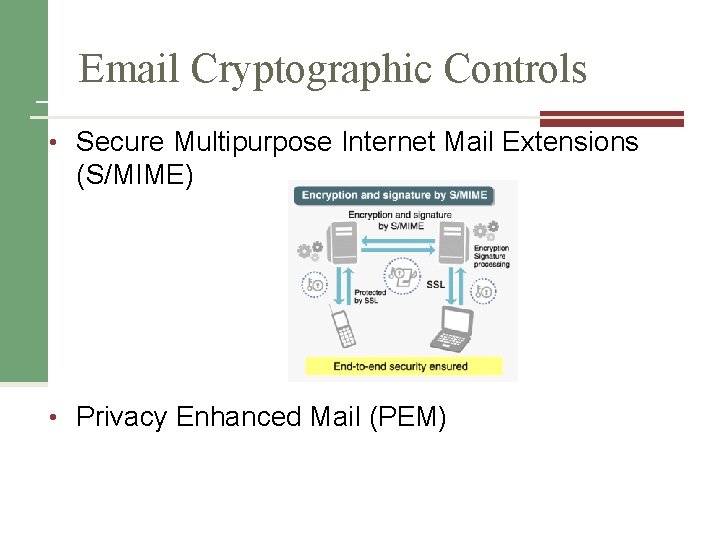
Email Cryptographic Controls • Secure Multipurpose Internet Mail Extensions (S/MIME) • Privacy Enhanced Mail (PEM)

Email Cryptographic Controls • Pretty Good Privacy (PGP) – Uses the IDEA Cipher n – A 128 -bit symmetric key block encryption algorithm with 64 -bit blocks for message encoding Like PEM, it uses RSA for symmetric key exchange and to support digital signatures

Securing the Web • IP Security (IPSec) – The primary and dominant cryptographic authentication and encryption product of the IETF’s IP Protocol Security Working Group – Combines several different cryptosystems: n n Diffie-Hellman key exchange Public key cryptography Bulk encryption algorithms Digital certificates

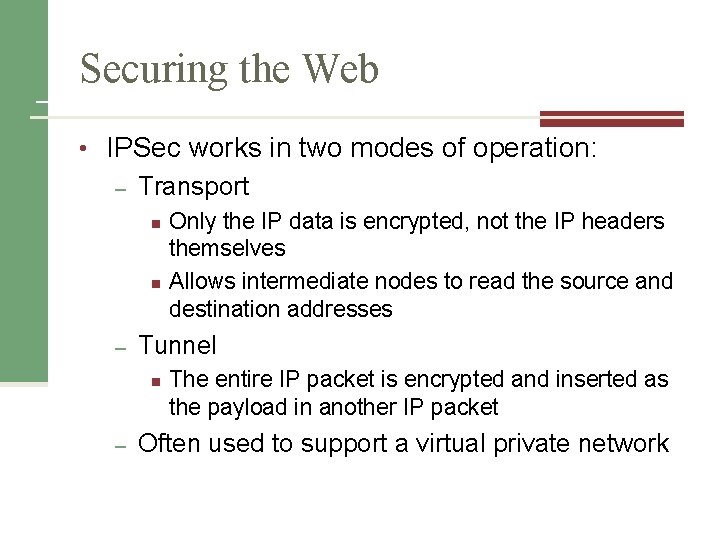
Securing the Web • IPSec works in two modes of operation: – Transport n n – Tunnel n – Only the IP data is encrypted, not the IP headers themselves Allows intermediate nodes to read the source and destination addresses The entire IP packet is encrypted and inserted as the payload in another IP packet Often used to support a virtual private network

Securing the Web • Secure Electronic Transactions (SET) – Encrypts credit card transfers with DES for encryption and RSA for key exchange • Secure Sockets Layer (SSL) – Uses RSA for key transfer n n On IDEA, DES, or 3 DES for encrypted symmetric key-based data transfer HTTPS

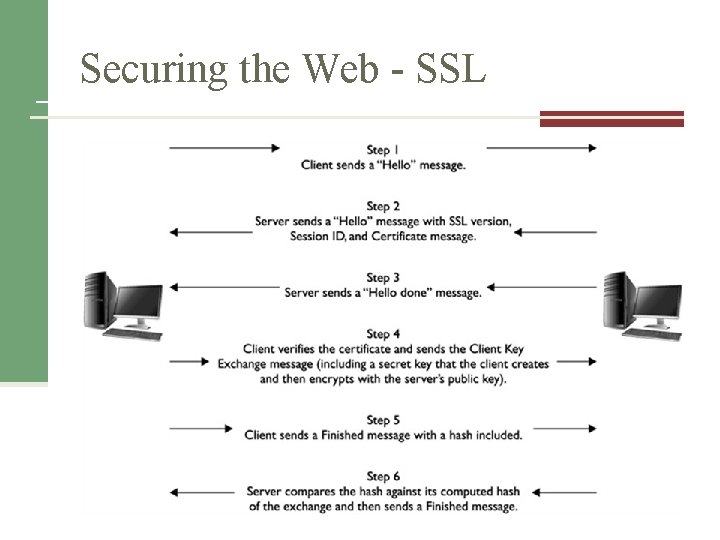
Securing the Web - SSL

Securing the Web • Secure Shell (SSH) – – Provides security for remote access connections over public networks by using tunneling, authentication services between a client and a server Used to secure replacement tools for terminal emulation, remote management, and file transfer applications

Hacking Cryptography n Known plaintext attack n Ciphertext-only attack n Replay attack

Managing Cryptographic Controls • Don’t lose your keys • Know who you are communicating with • It may be illegal to use a specific encryption technique when communicating to some nations • Every cryptosystem has weaknesses • Give access only to those with a business need • When placing trust into a certificate authority, ask “Who watches the watchers? ”

Managing Cryptographic Controls (cont’d. ) • There is no security in obscurity • Security protocols and the cryptosystems they use are installed and configured by humans – They are only as good as their installers • Make sure that your organization’s use of cryptography is based on well-constructed policy and supported with sound management procedures