Security Strategies in Windows Platforms and Applications Lesson



- Slides: 15

Security Strategies in Windows Platforms and Applications Lesson 1 Microsoft Windows and the Threat Landscape © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved.

Learning Objective and Key Concepts Learning Objective § Explain information security and how it applies to the Microsoft Windows operating systems. Key Concepts § Information security § Microsoft Windows and the typical IT infrastructure § Anatomy of Microsoft Windows systems and their application vulnerabilities Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 2

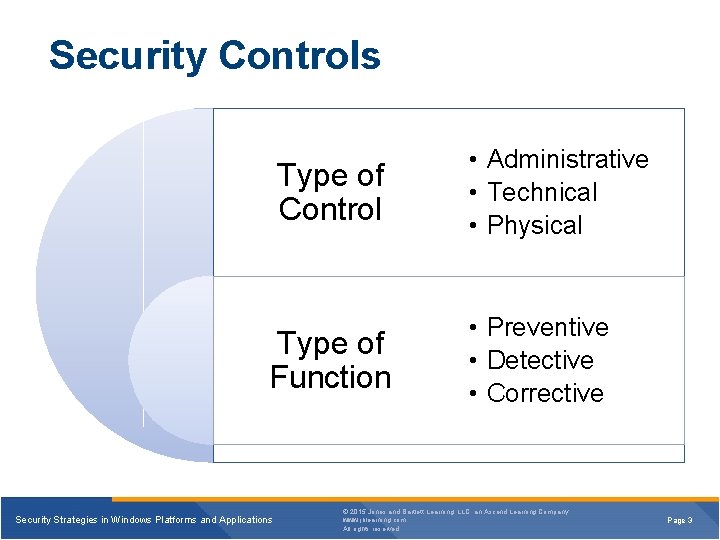
Security Controls Type of Control Type of Function Security Strategies in Windows Platforms and Applications • Administrative • Technical • Physical • Preventive • Detective • Corrective © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 3

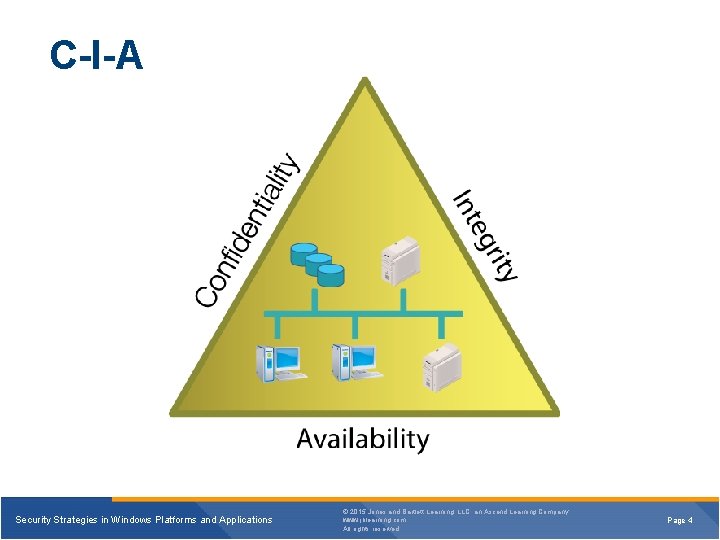
C-I-A Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 4

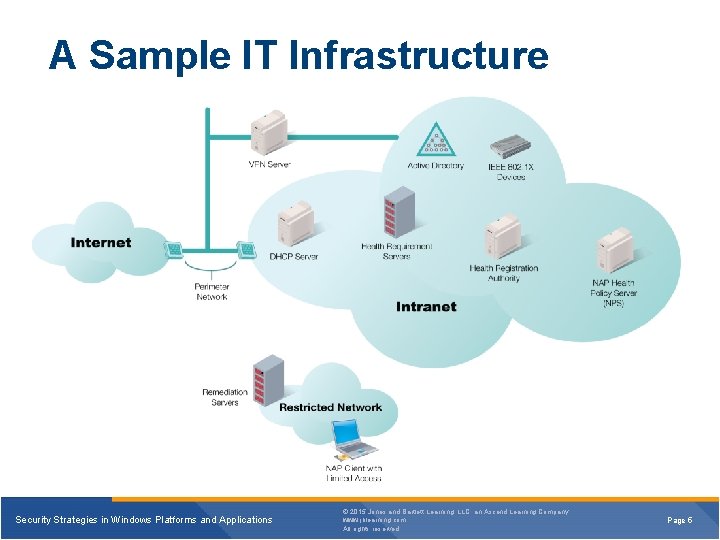
A Sample IT Infrastructure Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 5

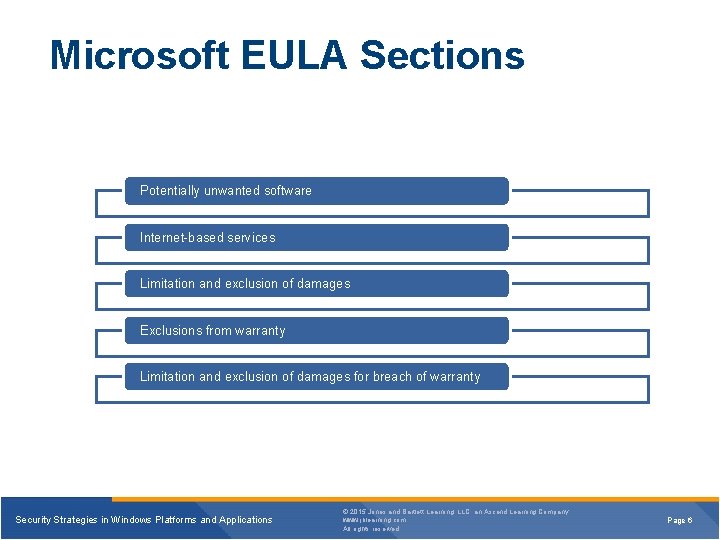
Microsoft EULA Sections Potentially unwanted software Internet-based services Limitation and exclusion of damages Exclusions from warranty Limitation and exclusion of damages for breach of warranty Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 6

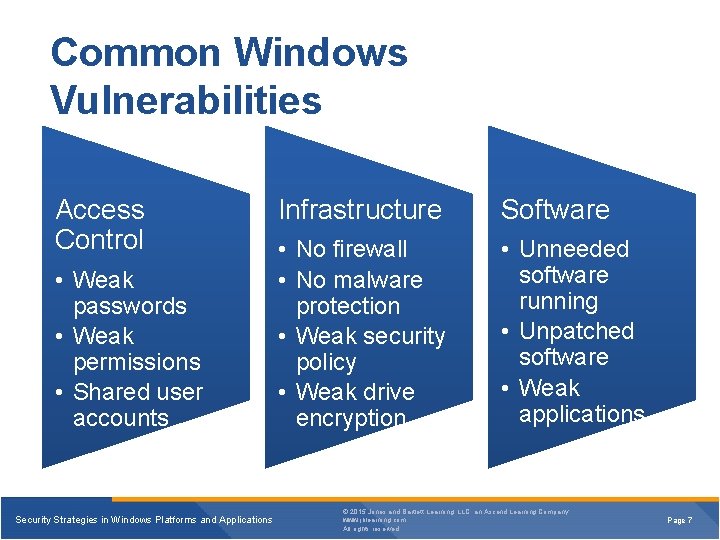
Common Windows Vulnerabilities Access Control • Weak passwords • Weak permissions • Shared user accounts Security Strategies in Windows Platforms and Applications Infrastructure Software • No firewall • No malware protection • Weak security policy • Weak drive encryption • Unneeded software running • Unpatched software • Weak applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 7

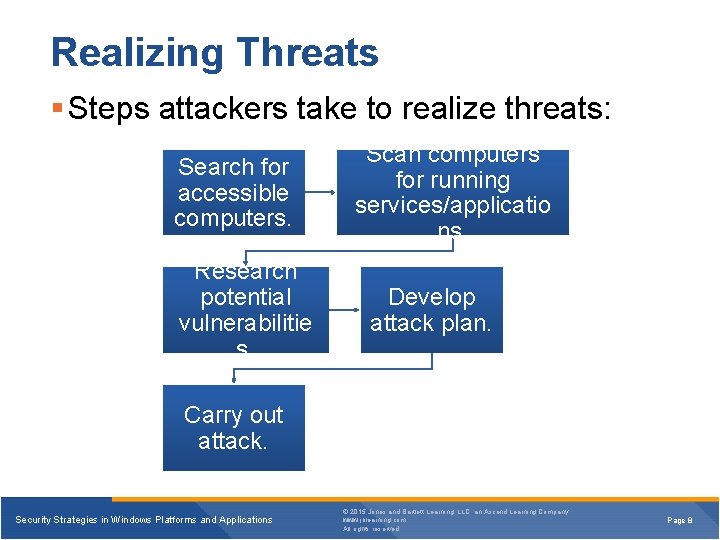
Realizing Threats § Steps attackers take to realize threats: Search for accessible computers. Research potential vulnerabilitie s. Scan computers for running services/applicatio ns. Develop attack plan. Carry out attack. Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 8

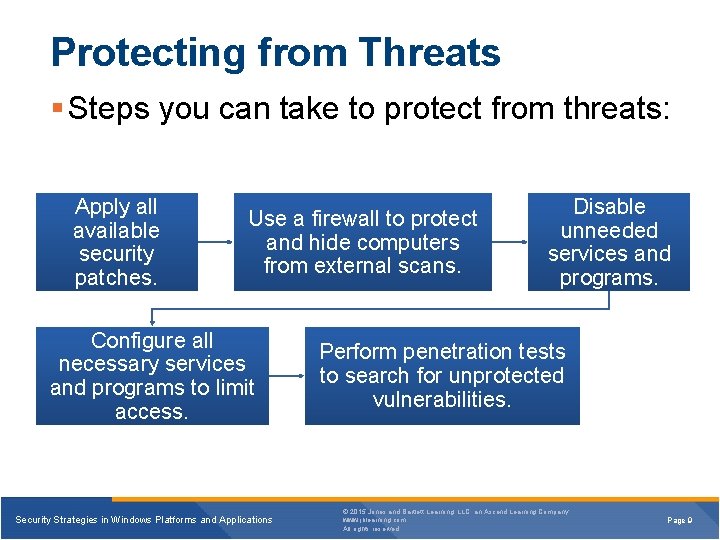
Protecting from Threats § Steps you can take to protect from threats: Apply all available security patches. Use a firewall to protect and hide computers from external scans. Configure all necessary services and programs to limit access. Security Strategies in Windows Platforms and Applications Disable unneeded services and programs. Perform penetration tests to search for unprotected vulnerabilities. © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 9

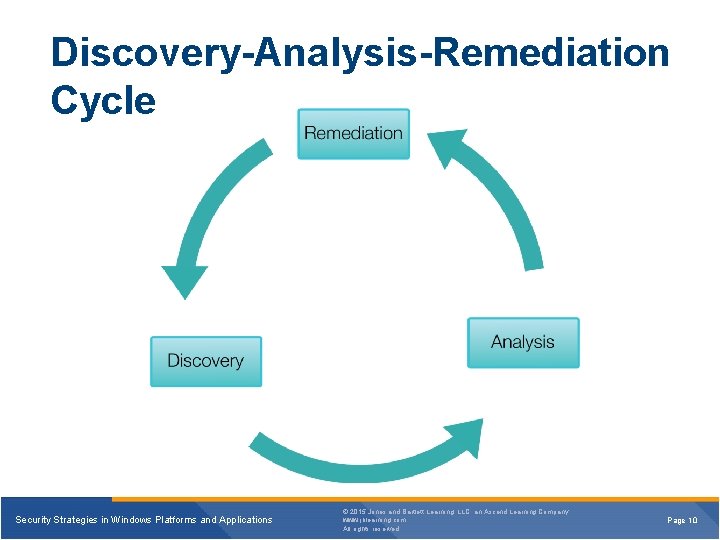
Discovery-Analysis-Remediation Cycle Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 10

Common Forms of Attack Threat Description Trojan horse A malicious program that tricks users into running it—often through social engineering Backdoor Programs that allow unauthorized access Denial of service Any action that dramatically slows down or blocks access to one or more resources Robot/intermediary process A process that runs on one target computer that launches attacks on other computers Unprotected Windows Share A situation that allows attackers to install tools, including malicious software Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 11

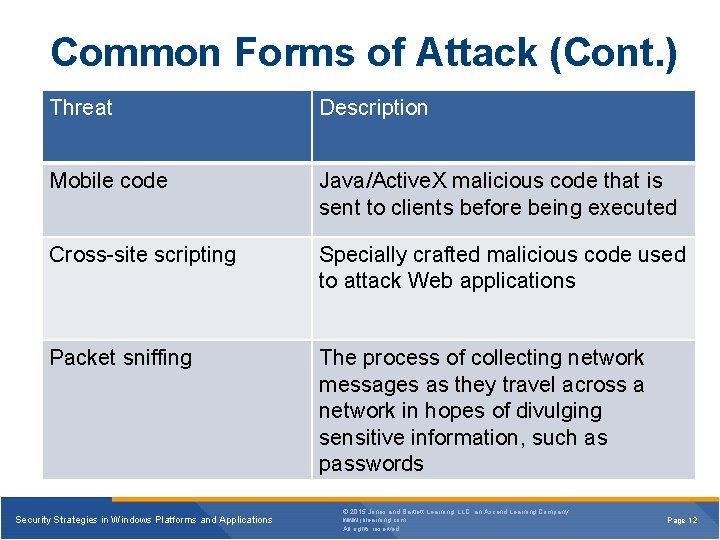
Common Forms of Attack (Cont. ) Threat Description Mobile code Java/Active. X malicious code that is sent to clients before being executed Cross-site scripting Specially crafted malicious code used to attack Web applications Packet sniffing The process of collecting network messages as they travel across a network in hopes of divulging sensitive information, such as passwords Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 12

Summary § Features of a Windows system § Common Windows vulnerabilities § Windows users and groups § Use of Microsoft Windows Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 13

OPTIONAL SLIDES Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 14

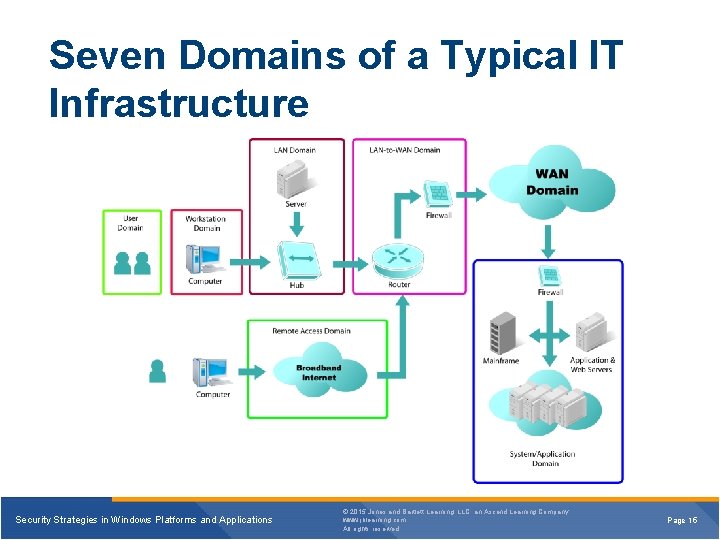
Seven Domains of a Typical IT Infrastructure Security Strategies in Windows Platforms and Applications © 2015 Jones and Bartlett Learning, LLC, an Ascend Learning Company www. jblearning. com All rights reserved. Page 15