Message authentication MAC hashes Message authentication Goal here








- Slides: 11

Message authentication: MAC, hashes

Message authentication • Goal here: having received a message one would like to make sure that the message has not been altered on the way – �� Produce a short sequence of bits that depends on the message and on a secret key – �� To authenticate the message, the partner will compute the same bit pattern, assuming he shares the same secret key • �� This does not necessarily includes encrypting or signing the message – �� The message can be sent in plain, with the authenticator appended – �� This is not a digital signature: the receiver can produce the same MAC – �� One may encrypt the authenticator with his private key to produce a digital signature – �� One may encrypt both the message and the authenticator • �� Possible attacks on message authentication: – �� Content modification – �� Sequence modification–modifications to a sequence of messages, including insertion, deletion, reordering – �� Timing modification–delay or replay message

Authentication functions • Three types of authentication exist • �� Message encryption–the ciphertext serves as authenticator • �� Message authentication code (MAC)–a public function of the message and a secret key producing a fixedlength value to serve as authenticator • �� This does not provide a digital signature because A and B share the same key • �� Hash function–a public function mapping an arbitrary length message into a fixed-length hash value to serve as authenticator – �� This does not provide a digital signature because there is no key

I. Message encryption as authentication • Main idea here: the message must have come from A because the ciphertext can be decrypted using his (secret or public) key • �� Also, none of the bits in the message have been altered because an opponent does not know how to manipulate the bits of the ciphertext to induce meaningful changes to the plaintext • �� Conclusion: encryption (either symmetric or public-key) provides authentication as well as confidentiality

More to authentication than simple encryption? • �� Often one needs alternative authentication schemes than just encrypting the message – �� Sometimes one needs to avoid encryption of full messages due to legal requirements – �� Encryption and authentication may be separated in the system architecture – �� If a message is broadcast to several destinations in a network (such as a military control center), then it is cheaper and more reliable to have just one node responsible to evaluate the authenticity –message will be sent in plain with an attached authenticator – �� If one side has a heavy load, it cannot afford to decrypt all messages – it will just check the authenticity of some randomly selected messages – �� If the message is sent encrypted, it is of course protected over the network. However, once the receiver decrypts the message, it is no longer secure. Using a different type of authentication protects the message also on the local computer

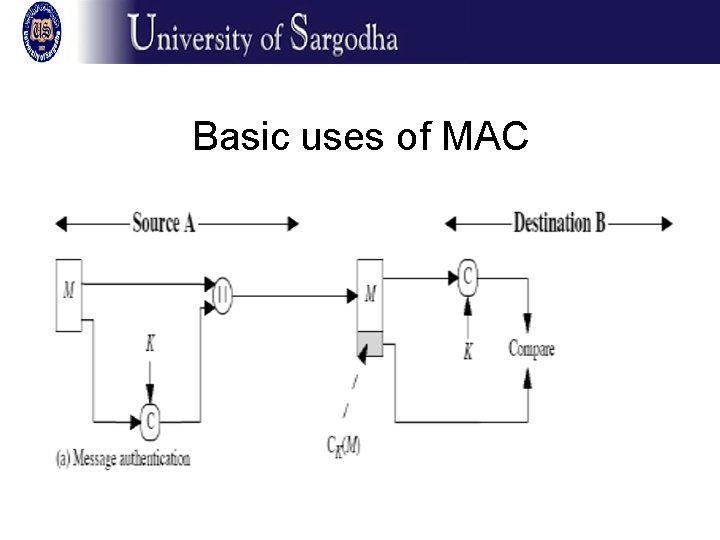
Message authentication code (MAC) • To generate the MAC of a message M, Alice gives M and the secret key K to a MAC function C: MAC=CK(M) – �� Alice will send M plus the MAC to Bob – �� Bob has the same secret key K and generates the MAC himself to check the match • �� Typical attacks on MACs – �� Produce an illegitimate message with the same signature as a given (or chosen) legitimate one – �� Produce a valid MAC for an illegitimate message • �� Requirements for MACs – �� The MAC function is in general many-to-one –messages are arbitrarily long and the MAC has fixed length, thus there will be more than one message with the same MAC – �� Computationally easy to compute the MAC – �� Knowing M and CK(M) it is computationally infeasible to construct another message M’ with CK(M’)= CK(M) – �� CK(M) is uniformly distributed –if the attacker chooses a random bit pattern of length n, the chances of it being the correct signature is 2 -n – �� If M’ is obtained from M by certain transformations (even switching one bit), then the probability that the two have the same MAC is 2 -n

Basic uses of MAC

cryptographic hash • A "hash" (also called a "digest", and informally a "checksum") is a kind of "signature" for a stream of data that represents the contents • We'll note here that though hashes and digests are often informally called "checksums", they really aren't. True checksums, such as a Cyclic Redundancy Check are designed to catch data-transmission errors and not deliberate attempts at tampering with data • Many Unix and Linux systems provide the md 5 sum program, which reads a stream of data and produces a fixed, 128 -bit number that summarizes that stream using the popular "MD 5" method. • This shows that all input streams yield hashes of the same length, and to experiment, try changing just one character of a small test file. You'll find that even very small changes to the input yields sweeping changes in the value of the hash, and this is known as the avalanche effect.

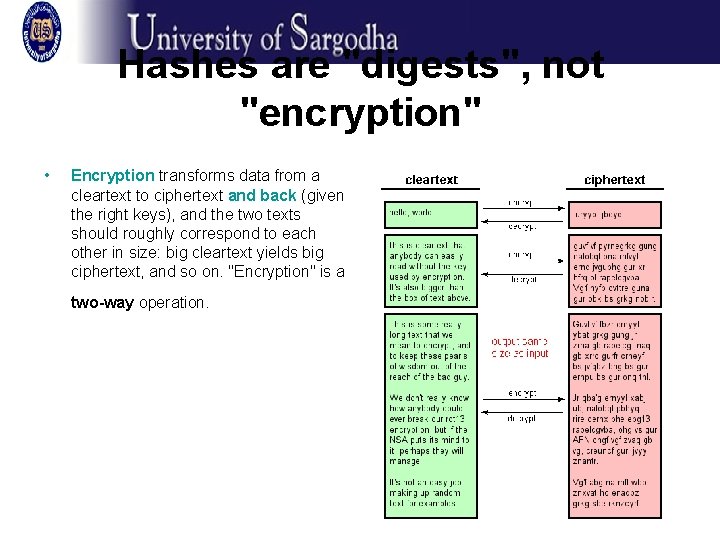
Hashes are "digests", not "encryption" • Encryption transforms data from a cleartext to ciphertext and back (given the right keys), and the two texts should roughly correspond to each other in size: big cleartext yields big ciphertext, and so on. "Encryption" is a two-way operation.

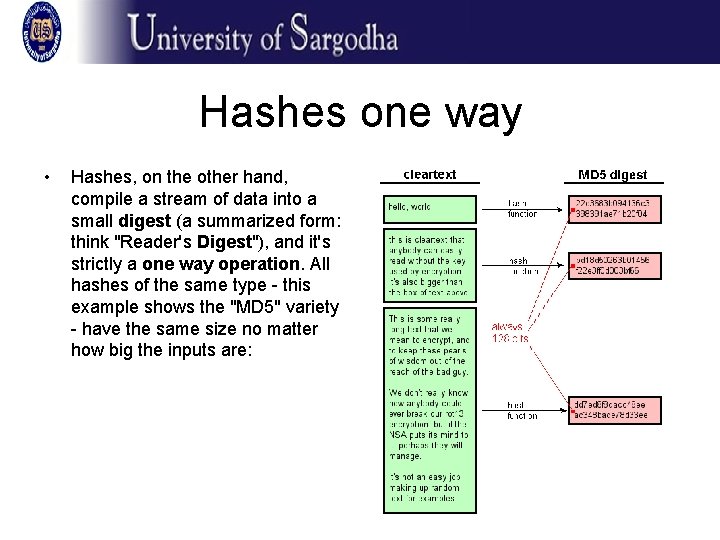
Hashes one way • Hashes, on the other hand, compile a stream of data into a small digest (a summarized form: think "Reader's Digest"), and it's strictly a one way operation. All hashes of the same type - this example shows the "MD 5" variety - have the same size no matter how big the inputs are:

• Authentication based on hash functions A fixed-length hash value h is generated by a function H that takes as input a message of arbitrary length: h=H(M) – �� A sends M and H(M) – �� B authenticates the message by computing H(M) and checking the match • �� Requirements for a hash function – – – • • �� H can be applied to a message of any size �� H produces fixed-length output �� Computationally easy to compute H(M) �� Computationally infeasible to find M such that H(M)=h, for a given h �� Computationally infeasible to find M’ such that H(M’)=H(M), for a given M �� Computationally infeasible to find M, M’ with H(M)=H(M’) (to resist to birthday attacks) �� Note: the hash function is not considered secret –some other means are required to protect it �� Note 2: Hash function plus secrecy (key) gives a MAC –these are called HMACs