Chapter 3 MAC Media Address Control Layer Chapter







![CSMA/CA with RTS/CTS Ø Solve Ø hidden terminal problem High overhead NAV(RTS) [LOCK] Sender CSMA/CA with RTS/CTS Ø Solve Ø hidden terminal problem High overhead NAV(RTS) [LOCK] Sender](https://slidetodoc.com/presentation_image_h/b07f33eaf8dcca78c658eed553088f9e/image-32.jpg)


![References [1] Andrew S. Tanenbaum , “Computer Network 4/e” , PHPTR [2] 曾煜棋, 潘孟鉉, References [1] Andrew S. Tanenbaum , “Computer Network 4/e” , PHPTR [2] 曾煜棋, 潘孟鉉,](https://slidetodoc.com/presentation_image_h/b07f33eaf8dcca78c658eed553088f9e/image-37.jpg)






- Slides: 109

Chapter 3 MAC (Media Address Control) Layer

Chapter 3 Outline Ø 3. 1. Ø 3. 2. Ø 3. 3. Ø 3. 4. Ø 3. 5. 2 802. 11 碰撞議題相關研究 802. 11 MAC機制 802. 11 節能、省電議題相關研究 802. 15. 4 MAC protocols for WSN Jang Ping Sheu 2020/11/2

Chapter 3 Outline Ø 3. 1. Ø 3. 2. Ø 3. 3. Ø 3. 4. Ø 3. 5. 3 802. 11 碰撞議題相關研究 802. 11 MAC機制 802. 11 節能、省電議題相關研究 802. 15. 4 MAC protocols for WSN Jang Ping Sheu 2020/11/2

Collision Avoidance Reservation based 4 TDMA、FDMA、 CDMA Contention based (Slotted)ALOHA、 CSMA、MACA Hybrid DAMA Jang Ping Sheu 2020/11/2


Reservation Based Ø FDMA → 一個點可以一直傳送,但頻寬較少。 F(頻帶) Guard Band T(時間) 6 Jang Ping Sheu 2020/11/2

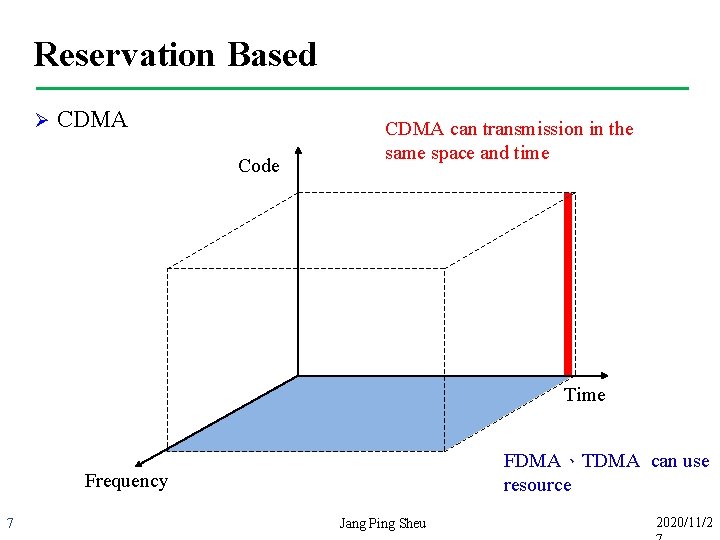
Reservation Based Ø CDMA Code CDMA can transmission in the same space and time Time FDMA、TDMA can use resource Frequency 7 Jang Ping Sheu 2020/11/2

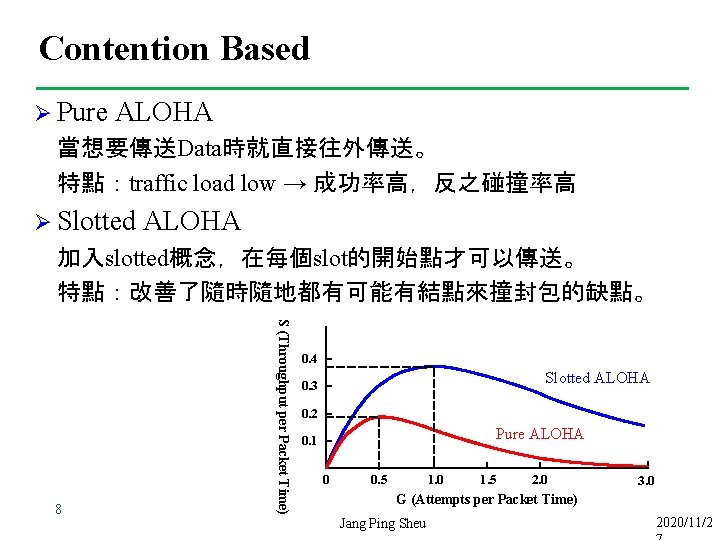
Contention Based Ø Pure ALOHA 當想要傳送Data時就直接往外傳送。 特點:traffic load low → 成功率高,反之碰撞率高 Ø Slotted ALOHA 加入slotted概念,在每個slot的開始點才可以傳送。 特點:改善了隨時隨地都有可能有結點來撞封包的缺點。 S (Throughput per Packet Time) 8 0. 4 Slotted ALOHA 0. 3 0. 2 Pure ALOHA 0. 1 0 0. 5 1. 0 1. 5 2. 0 3. 0 G (Attempts per Packet Time) Jang Ping Sheu 2020/11/2

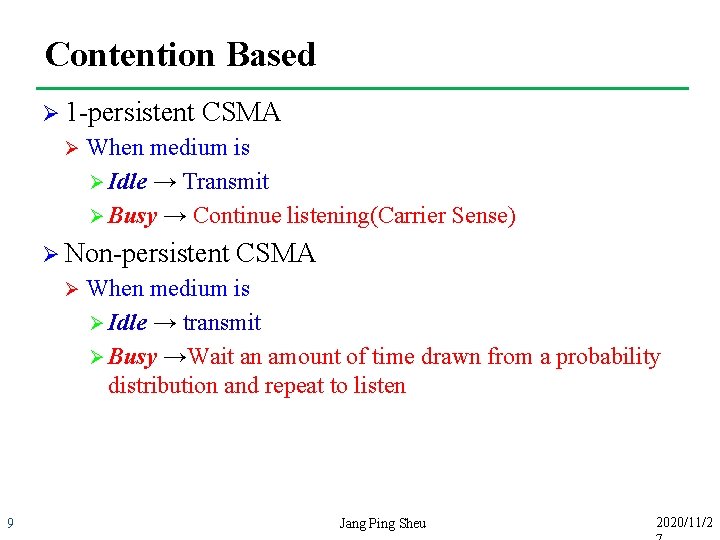
Contention Based Ø 1 -persistent Ø CSMA When medium is Ø Idle → Transmit Ø Busy → Continue listening(Carrier Sense) Ø Non-persistent Ø 9 CSMA When medium is Ø Idle → transmit Ø Busy →Wait an amount of time drawn from a probability distribution and repeat to listen Jang Ping Sheu 2020/11/2

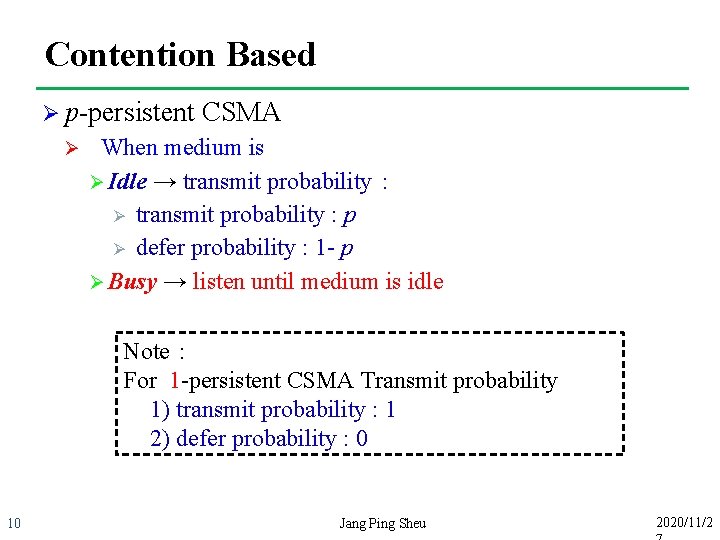
Contention Based Ø p-persistent Ø CSMA When medium is Ø Idle → transmit probability: Ø transmit probability : p Ø defer probability : 1 - p Ø Busy → listen until medium is idle Note: For 1 -persistent CSMA Transmit probability 1) transmit probability : 1 2) defer probability : 0 10 Jang Ping Sheu 2020/11/2

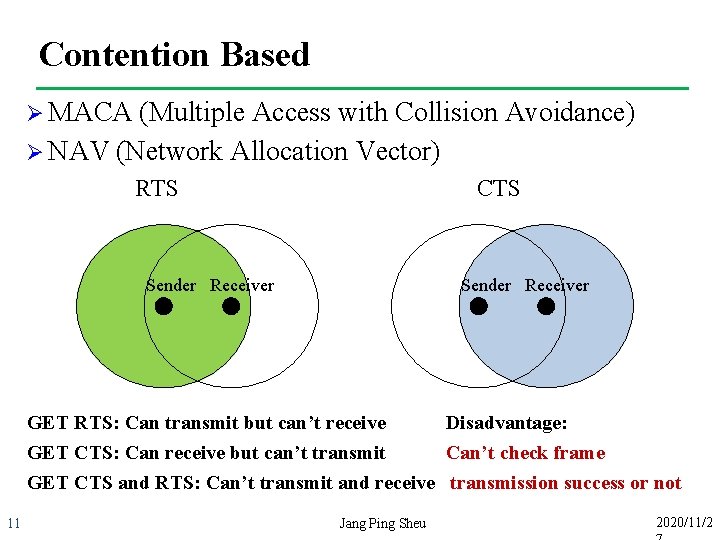
Contention Based Ø MACA (Multiple Access with Collision Avoidance) Ø NAV (Network Allocation Vector) RTS CTS Sender Receiver GET RTS: Can transmit but can’t receive Disadvantage: GET CTS: Can receive but can’t transmit Can’t check frame GET CTS and RTS: Can’t transmit and receive transmission success or not 11 Jang Ping Sheu 2020/11/2

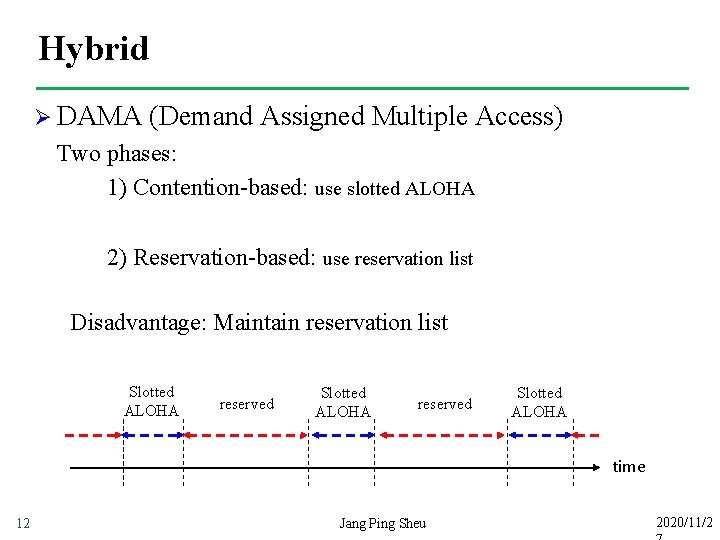
Hybrid Ø DAMA (Demand Assigned Multiple Access) Two phases: 1) Contention-based: use slotted ALOHA 2) Reservation-based: use reservation list Disadvantage: Maintain reservation list Slotted ALOHA reserved Slotted ALOHA time 12 Jang Ping Sheu 2020/11/2

Chapter 3 Outline Ø 3. 1. Ø 3. 2. Ø 3. 3. Ø 3. 4. Ø 3. 5. 13 802. 11 碰撞議題相關研究 802. 11 MAC機制 802. 11 節能、省電議題相關研究 802. 15. 4 MAC protocols for WSN Jang Ping Sheu 2020/11/2

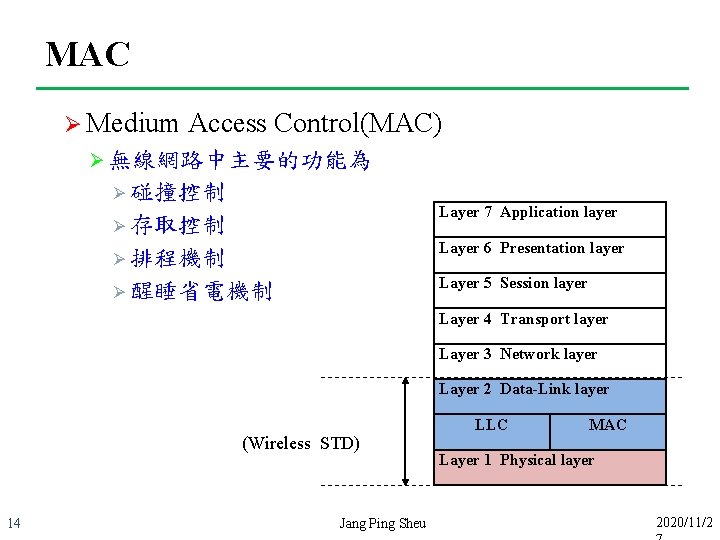
MAC Ø Medium Access Control(MAC) Ø 無線網路中主要的功能為 Ø 碰撞控制 Layer 7 Application layer Ø 存取控制 Ø 排程機制 Layer 6 Presentation layer Ø 醒睡省電機制 Layer 5 Session layer Layer 4 Transport layer Layer 3 Network layer Layer 2 Data-Link layer (Wireless STD) 14 Jang Ping Sheu LLC MAC Layer 1 Physical layer 2020/11/2

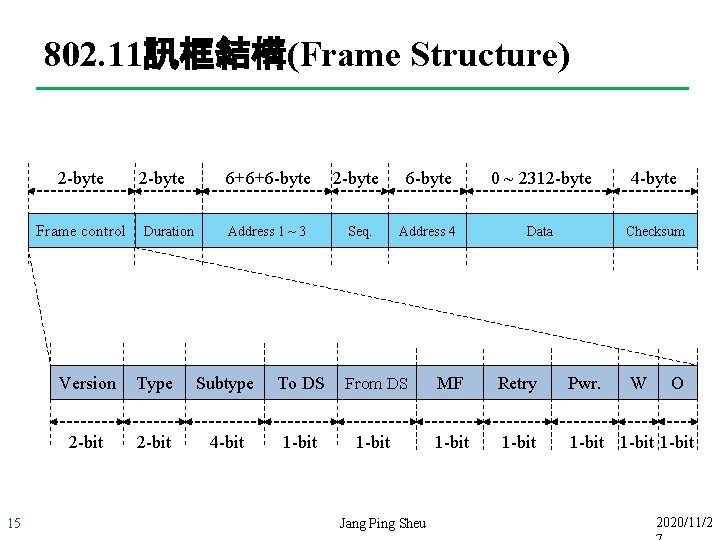
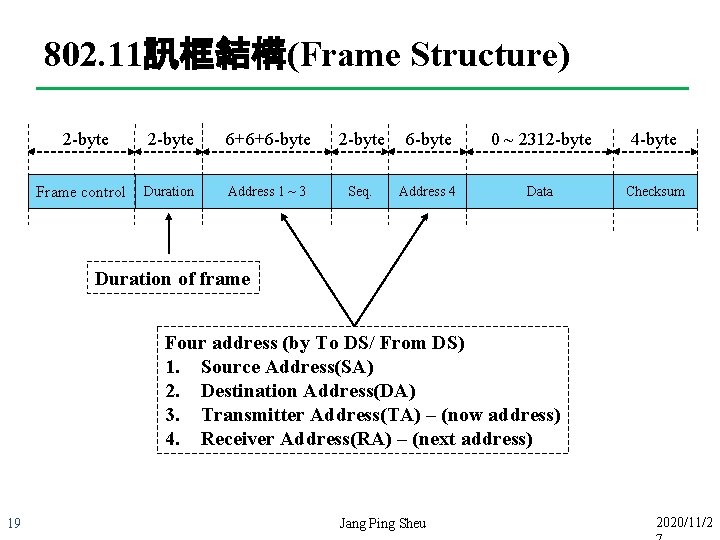
802. 11訊框結構(Frame Structure) 2 -byte Frame control 15 2 -byte Duration 6+6+6 -byte 2 -byte 6 -byte 0 ~ 2312 -byte 4 -byte Address 1 ~ 3 Seq. Address 4 Data Checksum Version Type Subtype To DS From DS MF Retry Pwr. 2 -bit 4 -bit 1 -bit 1 -bit Jang Ping Sheu W O 2020/11/2

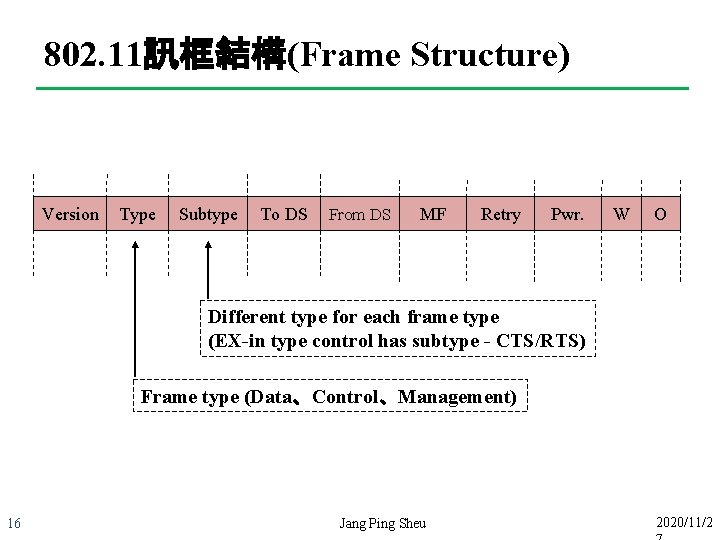
802. 11訊框結構(Frame Structure) Version Type Subtype To DS From DS MF Retry Pwr. W O Different type for each frame type (EX-in type control has subtype - CTS/RTS) Frame type (Data、Control、Management) 16 Jang Ping Sheu 2020/11/2

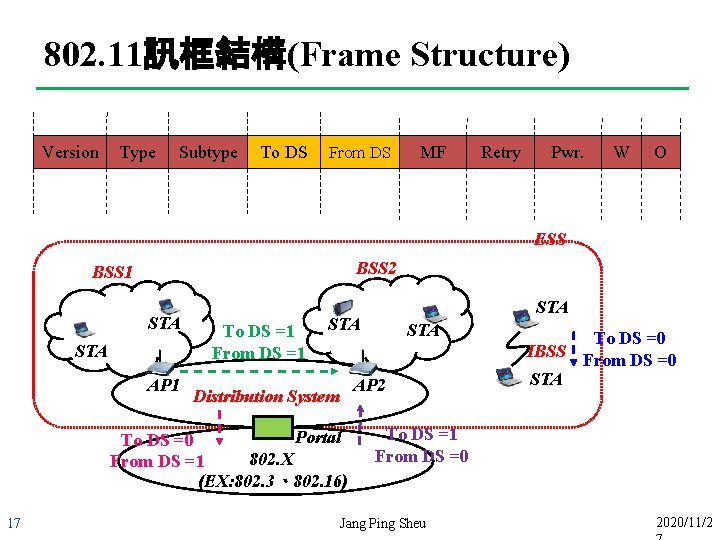
802. 11訊框結構(Frame Structure) Version Type Subtype To DS From DS MF Retry Pwr. W O ESS BSS 2 BSS 1 STA AP 1 To DS =1 From DS =1 STA AP 2 Distribution System Portal To DS =0 802. X From DS =1 (EX: 802. 3、802. 16) 17 STA To DS =0 IBSS From DS =0 STA To DS =1 From DS =0 Jang Ping Sheu 2020/11/2

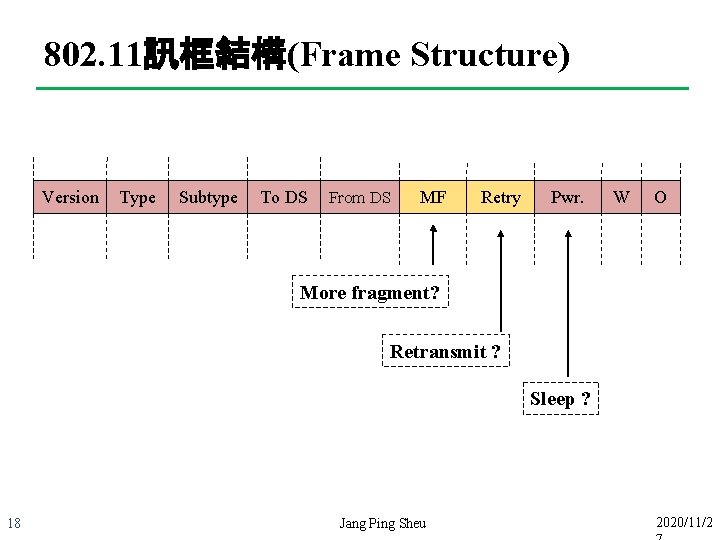
802. 11訊框結構(Frame Structure) Version Type Subtype To DS From DS MF Retry Pwr. W O More fragment? Retransmit ? Sleep ? 18 Jang Ping Sheu 2020/11/2

802. 11訊框結構(Frame Structure) 2 -byte Frame control 2 -byte 6+6+6 -byte 2 -byte 6 -byte 0 ~ 2312 -byte 4 -byte Duration Address 1 ~ 3 Seq. Address 4 Data Checksum Duration of frame Four address (by To DS/ From DS) 1. Source Address(SA) 2. Destination Address(DA) 3. Transmitter Address(TA) – (now address) 4. Receiver Address(RA) – (next address) 19 Jang Ping Sheu 2020/11/2

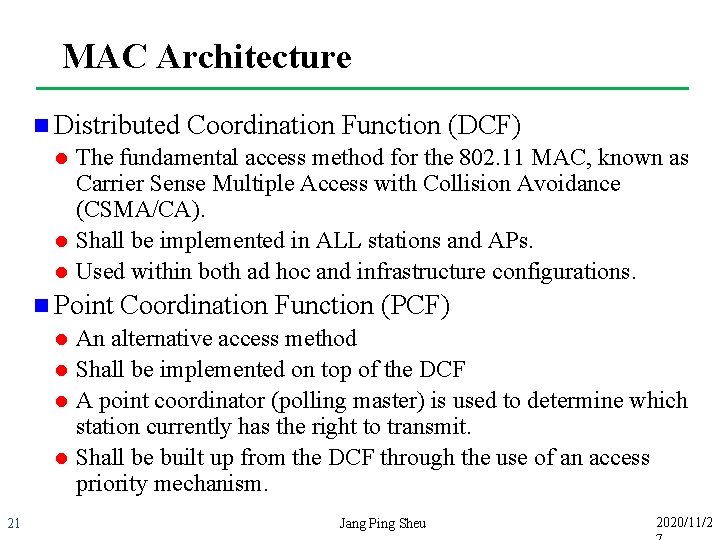
MAC Architecture Contention-Free Services (Real-time) Contention. Service (Asynchronous) Point Coordination Function (PCF) MAC Extent Distributed Coordination Function (DCF) 20 Jang Ping Sheu 2020/11/2

MAC Architecture n Distributed l l l The fundamental access method for the 802. 11 MAC, known as Carrier Sense Multiple Access with Collision Avoidance (CSMA/CA). Shall be implemented in ALL stations and APs. Used within both ad hoc and infrastructure configurations. n Point l l 21 Coordination Function (DCF) Coordination Function (PCF) An alternative access method Shall be implemented on top of the DCF A point coordinator (polling master) is used to determine which station currently has the right to transmit. Shall be built up from the DCF through the use of an access priority mechanism. Jang Ping Sheu 2020/11/2

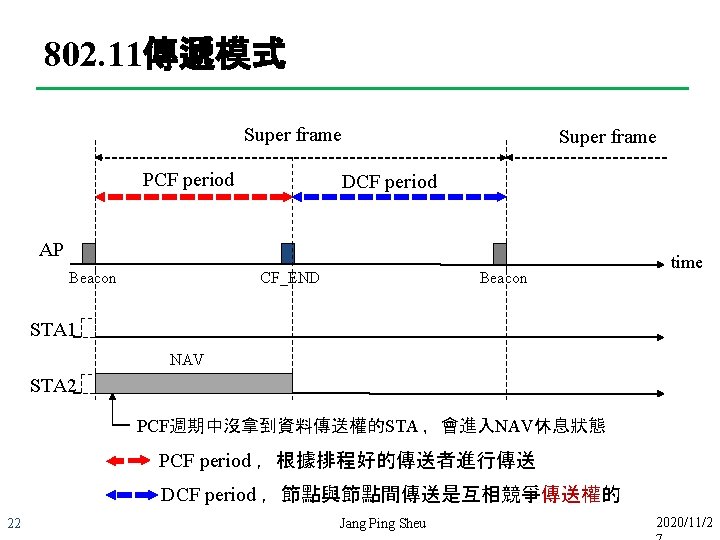
802. 11傳遞模式 Super frame PCF period Super frame DCF period AP Beacon CF_END Beacon time STA 1 NAV STA 2 PCF週期中沒拿到資料傳送權的STA ,會進入NAV休息狀態 PCF period ,根據排程好的傳送者進行傳送 DCF period ,節點與節點間傳送是互相競爭傳送權的 22 Jang Ping Sheu 2020/11/2

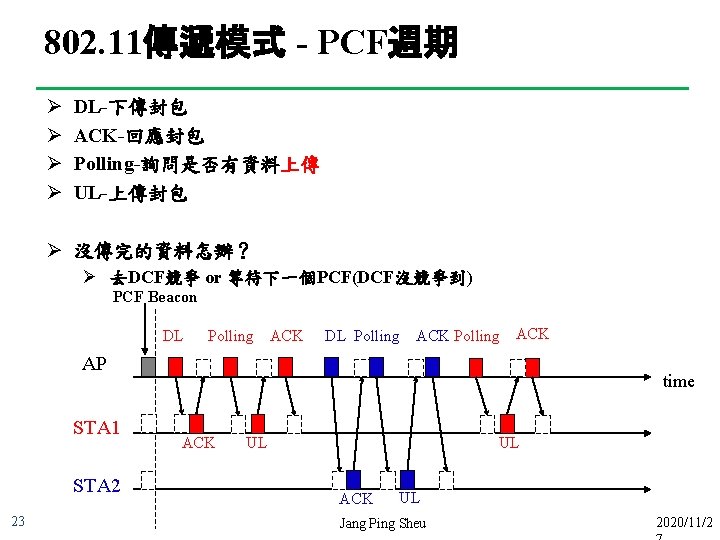
802. 11傳遞模式 - PCF週期 Ø Ø DL-下傳封包 ACK-回應封包 Polling-詢問是否有資料上傳 UL-上傳封包 Ø 沒傳完的資料怎辦? Ø 去DCF競爭 or 等待下一個PCF(DCF沒競爭到) PCF Beacon DL Polling ACK AP STA 1 STA 2 23 time ACK UL UL ACK UL Jang Ping Sheu 2020/11/2

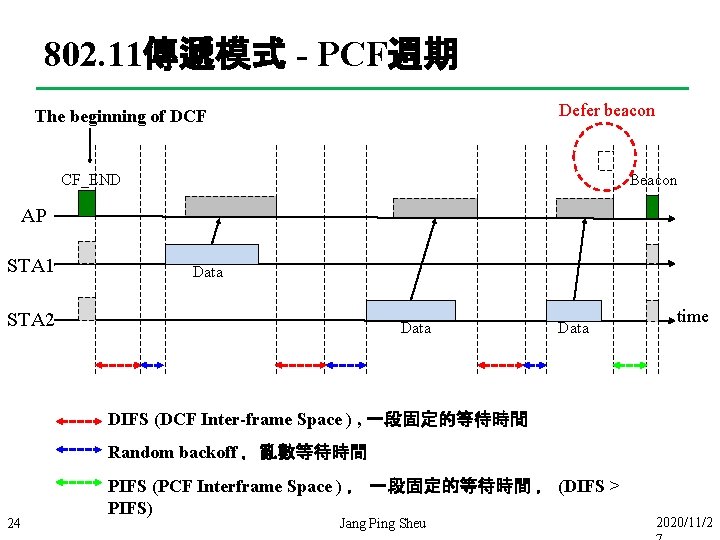
802. 11傳遞模式 - PCF週期 Defer beacon The beginning of DCF CF_END Beacon AP STA 1 Data STA 2 Data time DIFS (DCF Inter-frame Space ) , 一段固定的等待時間 Random backoff ,亂數等待時間 24 PIFS (PCF Interframe Space ) , 一段固定的等待時間 , (DIFS > PIFS) Jang Ping Sheu 2020/11/2

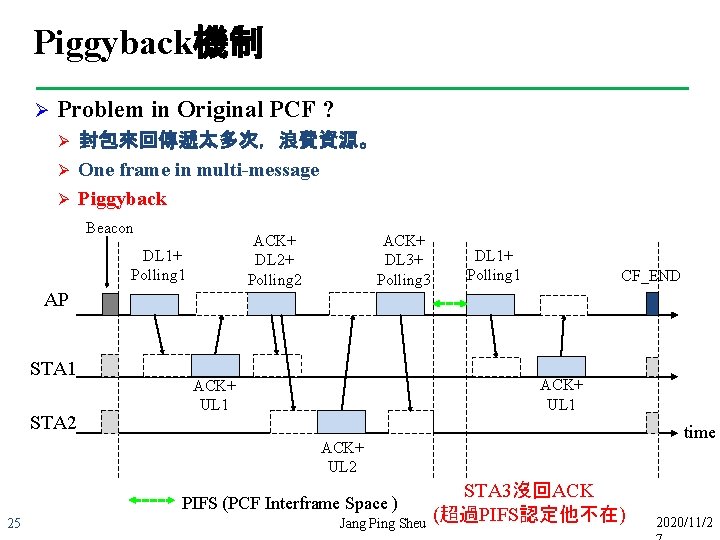
Piggyback機制 Ø Problem in Original PCF ? Ø Ø Ø 封包來回傳遞太多次,浪費資源。 One frame in multi-message Piggyback Beacon ACK+ DL 2+ Polling 2 DL 1+ Polling 1 ACK+ DL 3+ Polling 3 DL 1+ Polling 1 CF_END AP STA 1 STA 2 ACK+ UL 1 time ACK+ UL 2 PIFS (PCF Interframe Space ) 25 Jang Ping Sheu STA 3沒回ACK (超過PIFS認定他不在) 2020/11/2

DCF Operation n MAC l n If l 26 begins frame transmission If both PHY and virtual carrier sense mechanisms indicate the medium is idle for an interval of DIFS (or EIFS if previously received frame contained errors). medium is busy during the DIFS interval, Backoff interval is selected and increment retry counter For each slot time, if medium is detected to be idle, decrement backoff interval; MAC begins to transmit if backoff interval is expired. If the transmission is not successful (i. e. collision), CW is doubled and new backoff interval is selected and countdown is begun, again. When to stop? Jang Ping Sheu 2020/11/2

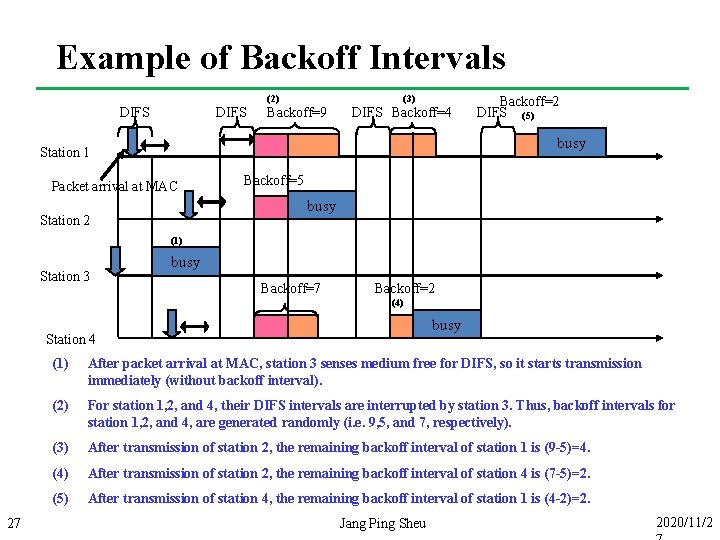
Example of Backoff Intervals (2) DIFS (3) Backoff=9 DIFS Backoff=4 Backoff=2 DIFS (5) busy Station 1 Packet arrival at MAC Backoff=5 busy Station 2 (1) Station 3 busy Backoff=7 Backoff=2 (4) busy Station 4 27 (1) After packet arrival at MAC, station 3 senses medium free for DIFS, so it starts transmission immediately (without backoff interval). (2) For station 1, 2, and 4, their DIFS intervals are interrupted by station 3. Thus, backoff intervals for station 1, 2, and 4, are generated randomly (i. e. 9, 5, and 7, respectively). (3) After transmission of station 2, the remaining backoff interval of station 1 is (9 -5)=4. (4) After transmission of station 2, the remaining backoff interval of station 4 is (7 -5)=2. (5) After transmission of station 4, the remaining backoff interval of station 1 is (4 -2)=2. Jang Ping Sheu 2020/11/2

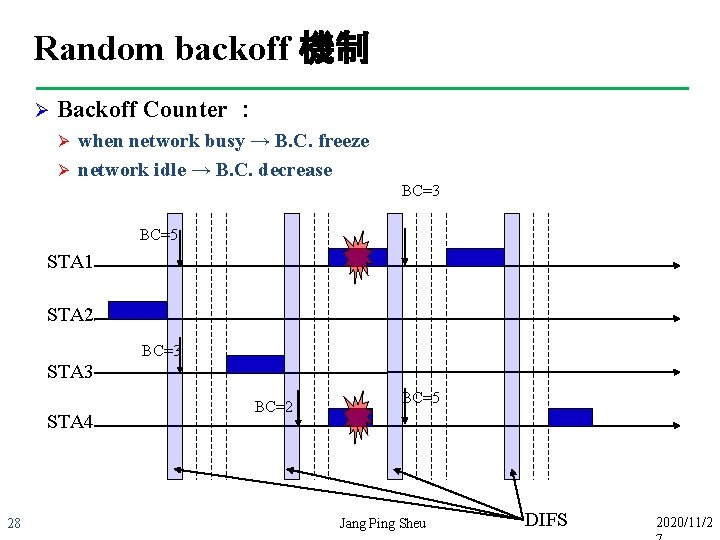
Random backoff 機制 Ø Backoff Counter : Ø Ø when network busy → B. C. freeze network idle → B. C. decrease BC=3 BC=5 STA 1 STA 2 BC=3 STA 4 28 BC=2 BC=5 Jang Ping Sheu DIFS 2020/11/2

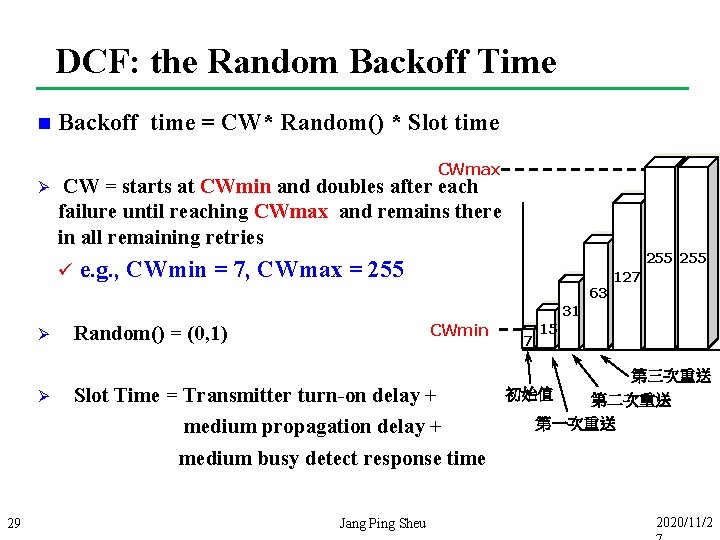
DCF: the Random Backoff Time n Backoff time = CW* Random() * Slot time CWmax Ø CW = starts at CWmin and doubles after each failure until reaching CWmax and remains there in all remaining retries ü 8 e. g. , CWmin = 7, CWmax = 255 63 255 127 31 Ø Ø 29 CWmin Random() = (0, 1) Slot Time = Transmitter turn-on delay + medium propagation delay + medium busy detect response time Jang Ping Sheu 7 15 第三次重送 初始值 第二次重送 第一次重送 2020/11/2

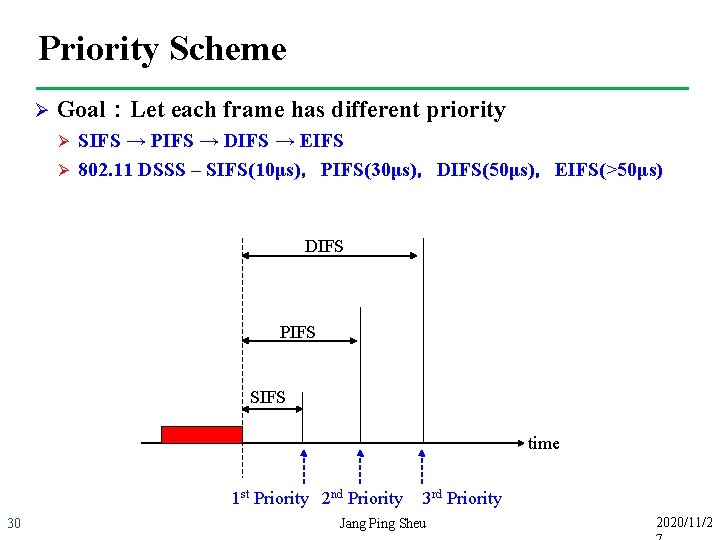
Priority Scheme Ø Goal:Let each frame has different priority Ø Ø SIFS → PIFS → DIFS → EIFS 802. 11 DSSS – SIFS(10μs),PIFS(30μs),DIFS(50μs),EIFS(>50μs) DIFS PIFS SIFS time 1 st Priority 2 nd Priority 30 3 rd Priority Jang Ping Sheu 2020/11/2

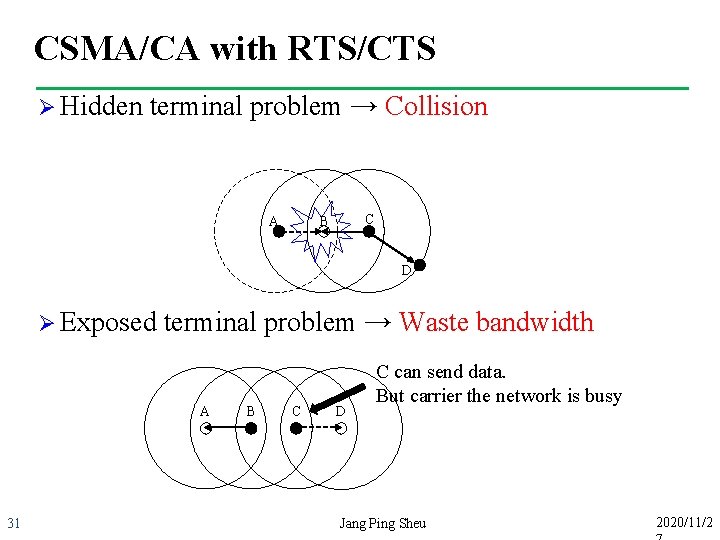
CSMA/CA with RTS/CTS Ø Hidden terminal problem → Collision A C B D Ø Exposed terminal problem → Waste bandwidth A 31 B C D C can send data. But carrier the network is busy Jang Ping Sheu 2020/11/2
![CSMACA with RTSCTS Ø Solve Ø hidden terminal problem High overhead NAVRTS LOCK Sender CSMA/CA with RTS/CTS Ø Solve Ø hidden terminal problem High overhead NAV(RTS) [LOCK] Sender](https://slidetodoc.com/presentation_image_h/b07f33eaf8dcca78c658eed553088f9e/image-32.jpg)
CSMA/CA with RTS/CTS Ø Solve Ø hidden terminal problem High overhead NAV(RTS) [LOCK] Sender Neighbor Data RTS Sender Receiver ACK CTS Receiver Neighbor 32 Receiver NAV(CTS) [LOCK] time Jang Ping Sheu 2020/11/2

Chapter 3 Outline Ø 3. 1. Ø 3. 2. Ø 3. 3. Ø 3. 4. Ø 3. 5. 33 802. 11 MAC機制 802. 11 碰撞議題相關研究 802. 11 節能、省電議題相關研究 802. 15. 4 MAC protocols for WSN Jang Ping Sheu 2020/11/2

802. 11內建省電模式 Ø In 34 802. 11 Power Saving mode Ø 802. 11 Infrastructure mode的省電模式 Ø Have AP Ø Ad-hoc mode的802. 11省電模式 Ø Only node Jang Ping Sheu 2020/11/2

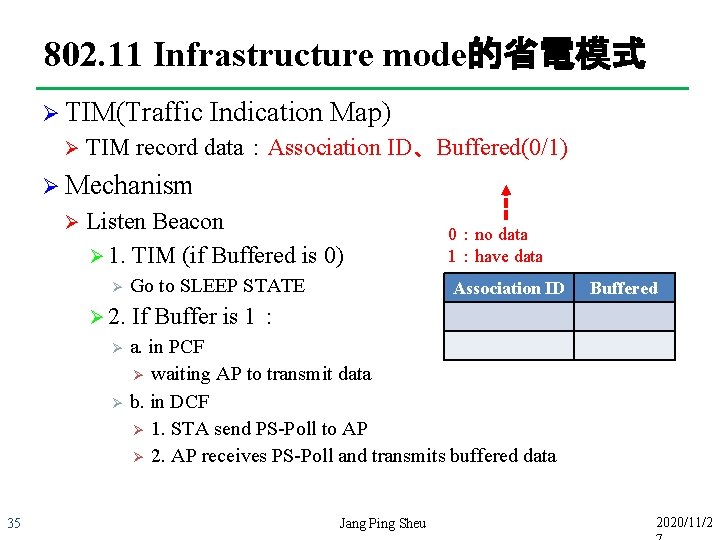
802. 11 Infrastructure mode的省電模式 Ø TIM(Traffic Ø Indication Map) TIM record data:Association ID、Buffered(0/1) Ø Mechanism Ø Listen Beacon Ø 1. TIM (if Buffered is 0) Ø Ø 2. Ø Ø 35 Go to SLEEP STATE 0:no data 1:have data Association ID Buffered If Buffer is 1: a. in PCF Ø waiting AP to transmit data b. in DCF Ø 1. STA send PS-Poll to AP Ø 2. AP receives PS-Poll and transmits buffered data Jang Ping Sheu 2020/11/2

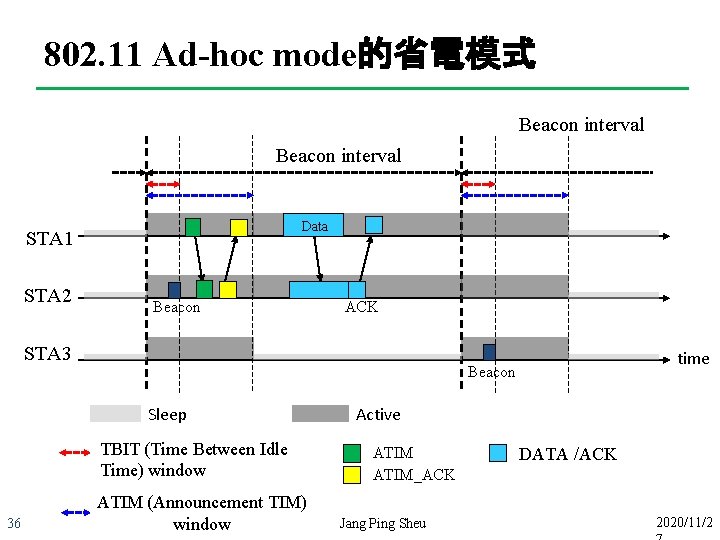
802. 11 Ad-hoc mode的省電模式 Beacon interval Data STA 1 STA 2 Beacon ACK STA 3 Beacon Sleep TBIT (Time Between Idle Time) window 36 time ATIM (Announcement TIM) window Active ATIM_ACK Jang Ping Sheu DATA /ACK 2020/11/2
![References 1 Andrew S Tanenbaum Computer Network 4e PHPTR 2 曾煜棋 潘孟鉉 References [1] Andrew S. Tanenbaum , “Computer Network 4/e” , PHPTR [2] 曾煜棋, 潘孟鉉,](https://slidetodoc.com/presentation_image_h/b07f33eaf8dcca78c658eed553088f9e/image-37.jpg)
References [1] Andrew S. Tanenbaum , “Computer Network 4/e” , PHPTR [2] 曾煜棋, 潘孟鉉, 林致宇 , “無線網域及個人網路-隨意及感測網路之技 術與應用” , 知城 [3] N. Abramson, “The ALOHA system – another alternative for computer communications” , in proc. Fall Joint Computer Conference. [4] Jung-Hyon Jun, Young-June Choi, and Saewoong Bahk , “Affinity-Based Power Saving MAC Protocol in Ad Hoc Network” , in proc. IEEE Per. Com 2005 [5] V. Bharghavan, A. Demers, S. Shenker, and L. Zhang, “ MACAW: A media access protocol for wireless LAN's. ” in proc. ACM SIGCOMM '94 [6] IEEE Std 802. 11 -1997 [7] IEEE Std 802. 11 a-1999 [8] IEEE Std 802. 11 b-1999 37 Jang Ping Sheu 2020/11/2

Chapter 3 Outline Ø 3. 1. Ø 3. 2. Ø 3. 3. Ø 3. 4. Ø 3. 5. 38 802. 11 MAC機制 802. 11 碰撞議題相關研究 802. 11 節能、省電議題相關研究 802. 15. 4 MAC protocols for WSN Jang Ping Sheu 2020/11/2

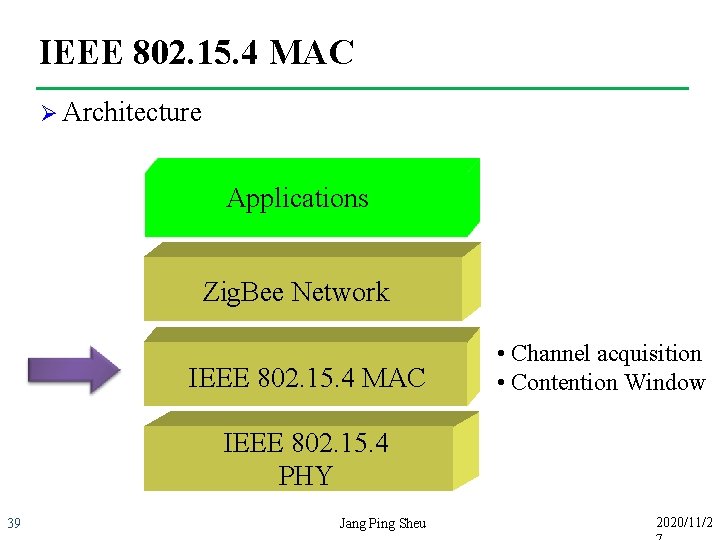
IEEE 802. 15. 4 MAC Ø Architecture Applications Zig. Bee Network IEEE 802. 15. 4 MAC • Channel acquisition • Contention Window IEEE 802. 15. 4 PHY 39 Jang Ping Sheu 2020/11/2

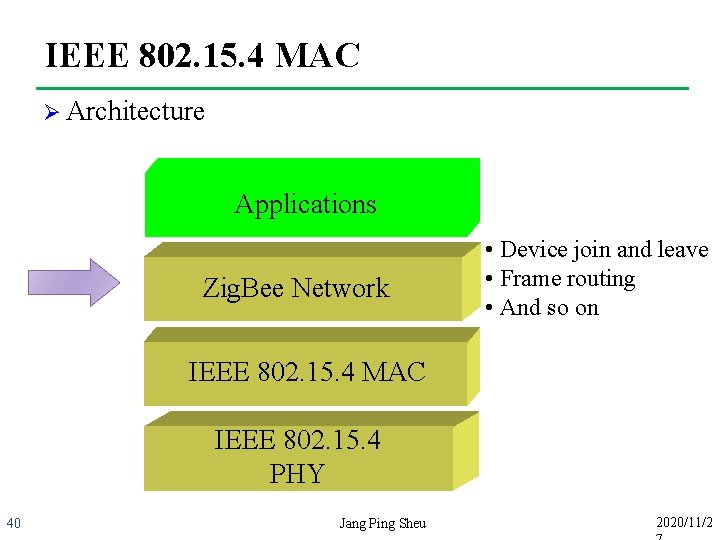
IEEE 802. 15. 4 MAC Ø Architecture Applications Zig. Bee Network • Device join and leave • Frame routing • And so on IEEE 802. 15. 4 MAC IEEE 802. 15. 4 PHY 40 Jang Ping Sheu 2020/11/2

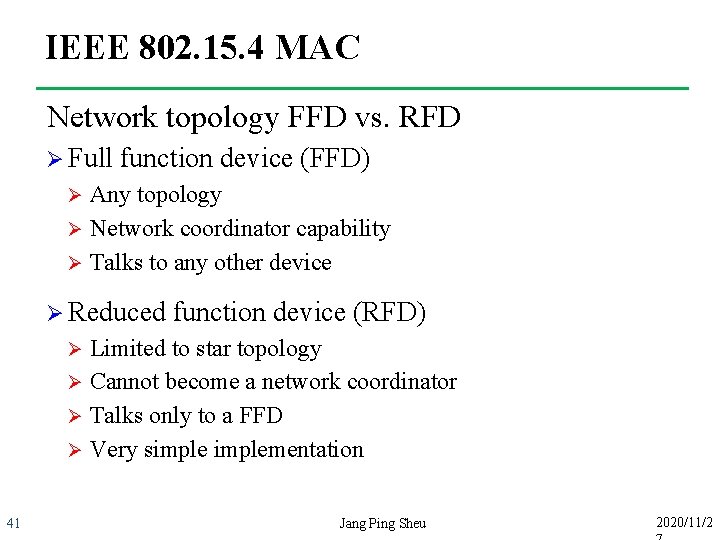
IEEE 802. 15. 4 MAC Network topology FFD vs. RFD Ø Full function device (FFD) Any topology Ø Network coordinator capability Ø Talks to any other device Ø Ø Reduced function device (RFD) Limited to star topology Ø Cannot become a network coordinator Ø Talks only to a FFD Ø Very simplementation Ø 41 Jang Ping Sheu 2020/11/2

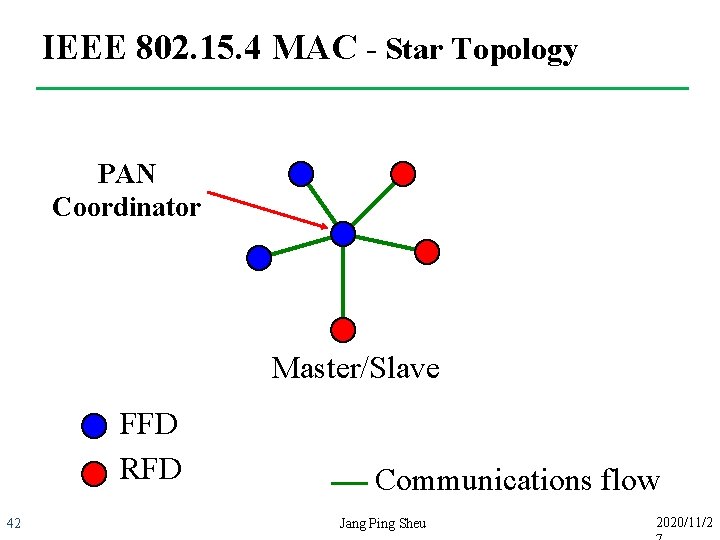
IEEE 802. 15. 4 MAC - Star Topology PAN Coordinator Master/Slave FFD RFD 42 Communications flow Jang Ping Sheu 2020/11/2

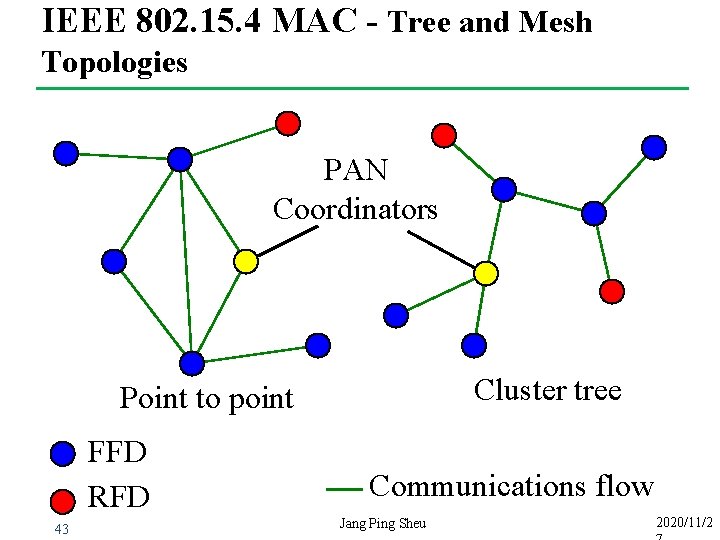
IEEE 802. 15. 4 MAC - Tree and Mesh Topologies PAN Coordinators Cluster tree Point to point FFD RFD 43 Communications flow Jang Ping Sheu 2020/11/2

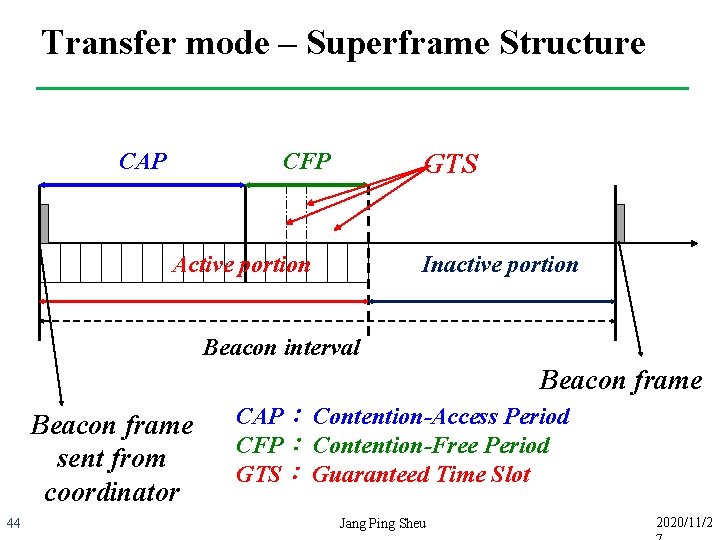
Transfer mode – Superframe Structure CAP CFP GTS Active portion Inactive portion Beacon interval Beacon frame sent from coordinator 44 CAP︰ Contention-Access Period CFP︰ Contention-Free Period GTS︰ Guaranteed Time Slot Jang Ping Sheu 2020/11/2

Transfer mode – GTS Concepts Ø Beacon interval = a. Base. Superframe. Duration × 2 SO symbols Ø a. Base. Superframe. Duration為IEEE 802. 15. 4預設參數。 Ø Active portion的長度為: a. Base. Superframe. Duration × 2 BO symbols (BO≦SO≦ 14) 45 Ø 當SO =15時,代表不使用superframe的架構。 Ø A Guaranteed Time Slot (GTS) allows a device to operate on the channel within a portion of the superframe Ø A GTS shall only be allocated by the PAN coordinator Ø The PAN coordinator can allocated up to seven GTSs at the same time Jang Ping Sheu 2020/11/2

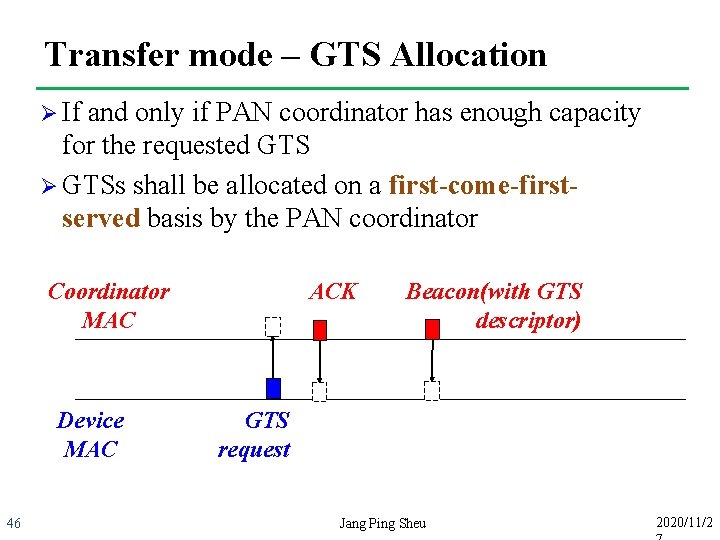
Transfer mode – GTS Allocation Ø If and only if PAN coordinator has enough capacity for the requested GTS Ø GTSs shall be allocated on a first-come-firstserved basis by the PAN coordinator Coordinator MAC Device MAC 46 ACK Beacon(with GTS descriptor) GTS request Jang Ping Sheu 2020/11/2

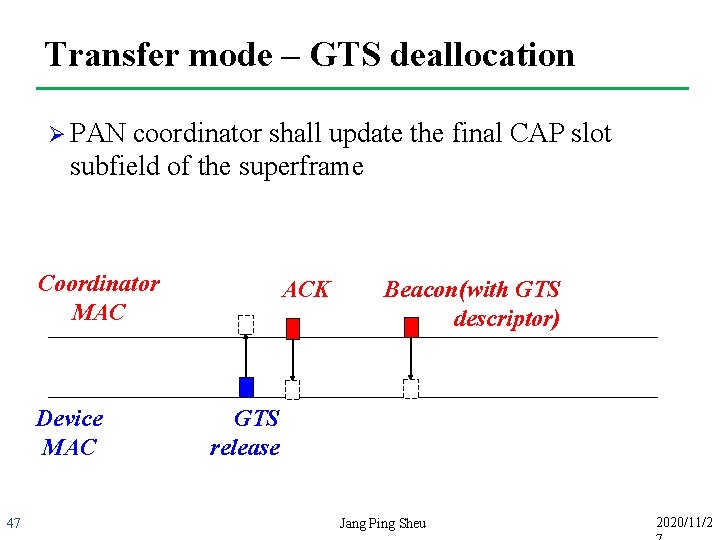
Transfer mode – GTS deallocation Ø PAN coordinator shall update the final CAP slot subfield of the superframe Coordinator MAC Device MAC 47 ACK Beacon(with GTS descriptor) GTS release Jang Ping Sheu 2020/11/2

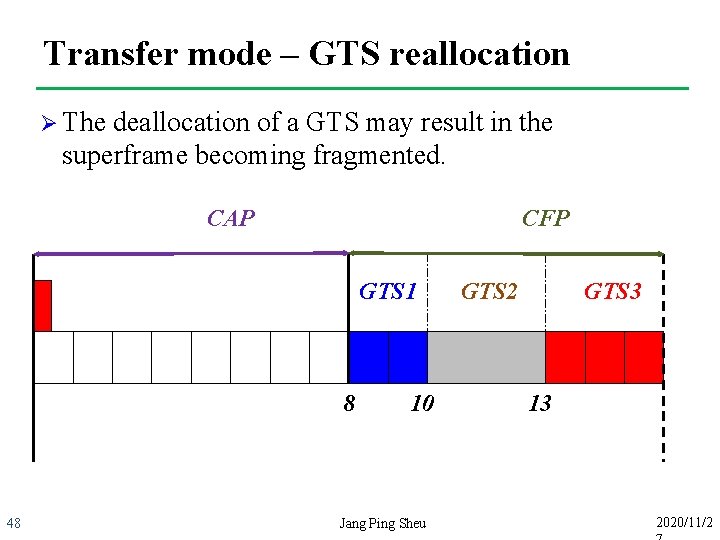
Transfer mode – GTS reallocation Ø The deallocation of a GTS may result in the superframe becoming fragmented. CAP CFP GTS 1 8 48 10 Jang Ping Sheu GTS 2 GTS 3 13 2020/11/2

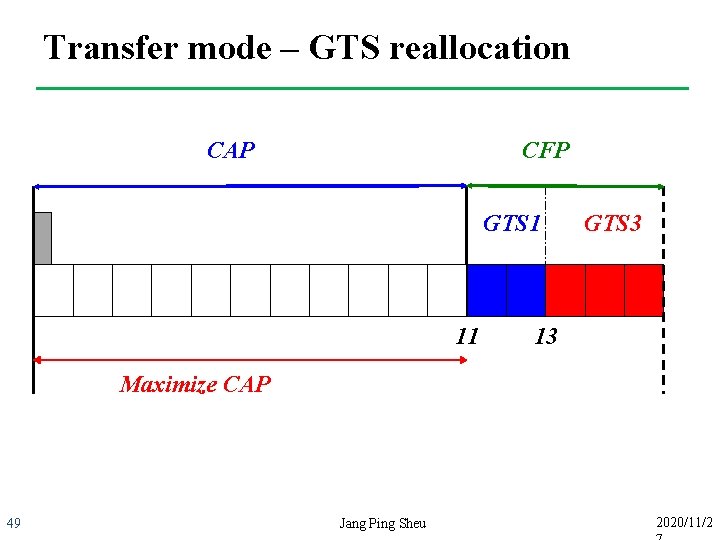
Transfer mode – GTS reallocation CAP CFP GTS 1 11 GTS 3 13 Maximize CAP 49 Jang Ping Sheu 2020/11/2

Data Transfer Model - Channel Access Ø Beacon-enable networks Ø Ø Ø Non Beacon-enable networks Ø Ø 50 With beacon frame Slotted CSMA/CA channel access mechanism No beacon frame Unslotted CSMA/CA channel access mechanism Jang Ping Sheu 2020/11/2

Beacon-enable Networks Ø Slotted ü CSMA/CA Algorithm Every device in the PAN shall be aligned with the superframe slot 51 Jang Ping Sheu 2020/11/2

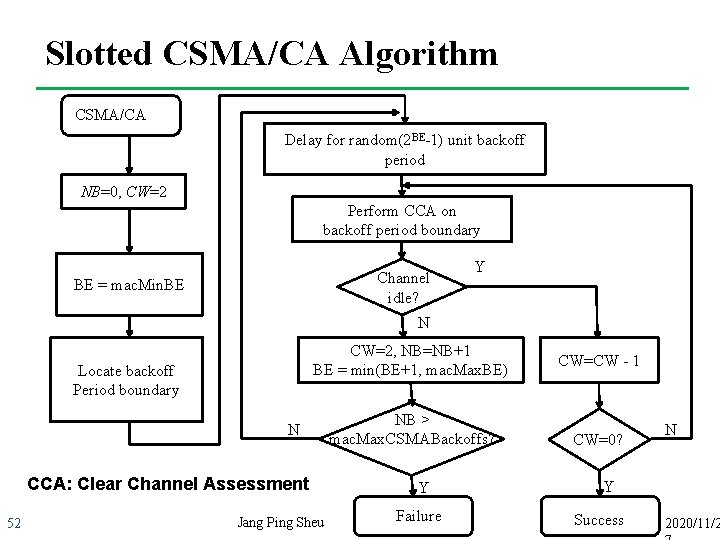
Slotted CSMA/CA Algorithm CSMA/CA Delay for random(2 BE-1) unit backoff period NB=0, CW=2 Perform CCA on backoff period boundary Channel idle? BE = mac. Min. BE Y N CW=2, NB=NB+1 BE = min(BE+1, mac. Max. BE) Locate backoff Period boundary N CCA: Clear Channel Assessment 52 Jang Ping Sheu NB > mac. Max. CSMABackoffs? Y Failure CW=CW - 1 CW=0? N Y Success 2020/11/2

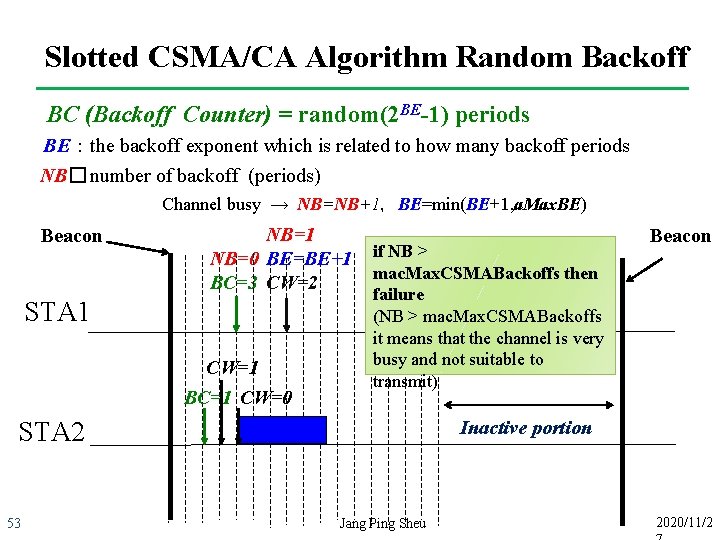
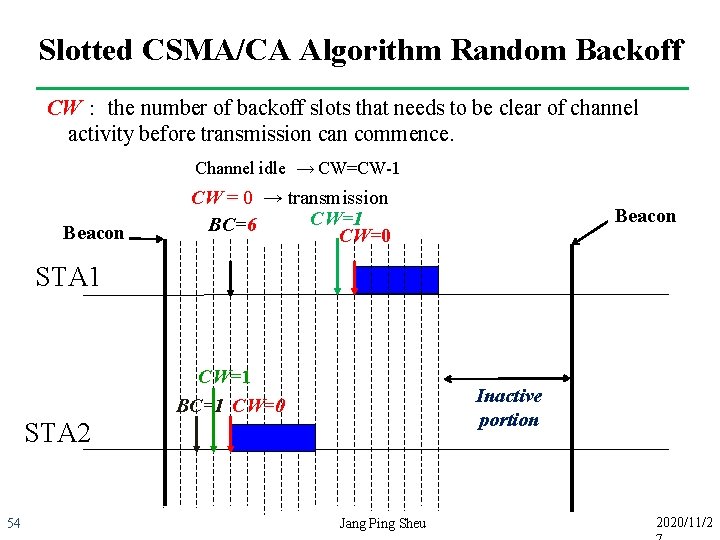
Slotted CSMA/CA Algorithm Random Backoff BC (Backoff Counter) = random(2 BE-1) periods BE:the backoff exponent which is related to how many backoff periods NB� number of backoff (periods) Channel busy → NB=NB+1,BE=min(BE+1, a. Max. BE) Beacon NB=1 NB=0 BE=BE+1 BC=3 CW=2 STA 1 CW=1 BC=1 CW=0 if NB > mac. Max. CSMABackoffs then failure (NB > mac. Max. CSMABackoffs it means that the channel is very busy and not suitable to transmit) Inactive portion STA 2 53 Beacon Jang Ping Sheu 2020/11/2

Slotted CSMA/CA Algorithm Random Backoff CW: the number of backoff slots that needs to be clear of channel activity before transmission can commence. Channel idle → CW=CW-1 Beacon CW = 0 → transmission CW=1 BC=6 CW=0 Beacon STA 1 CW=1 BC=1 CW=0 Inactive portion STA 2 54 Jang Ping Sheu 2020/11/2

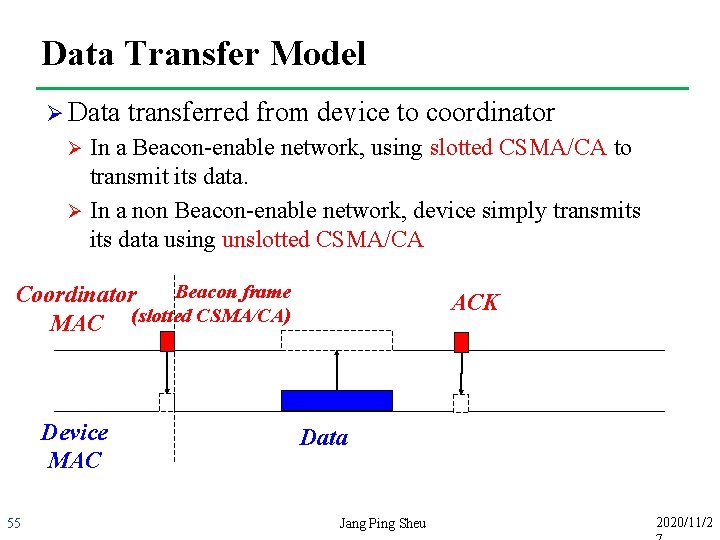
Data Transfer Model Ø Data transferred from device to coordinator In a Beacon-enable network, using slotted CSMA/CA to transmit its data. Ø In a non Beacon-enable network, device simply transmits data using unslotted CSMA/CA Ø Beacon frame Coordinator MAC (slotted CSMA/CA) Device MAC 55 ACK Data Jang Ping Sheu 2020/11/2

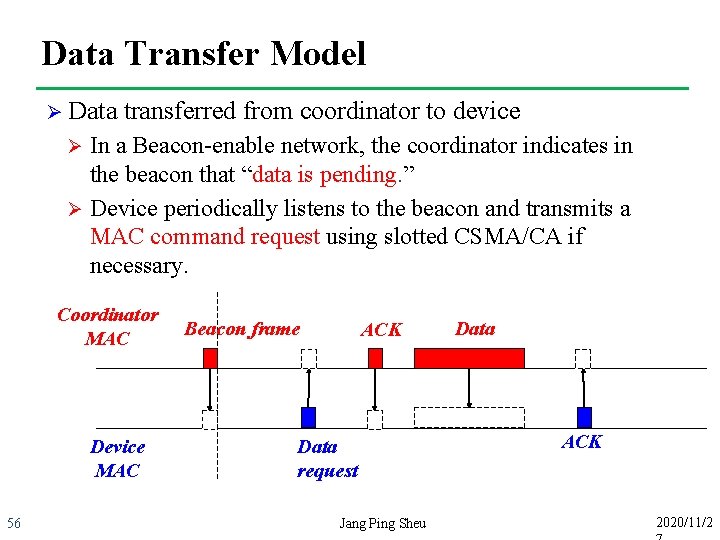
Data Transfer Model Ø Data transferred from coordinator to device In a Beacon-enable network, the coordinator indicates in the beacon that “data is pending. ” Ø Device periodically listens to the beacon and transmits a MAC command request using slotted CSMA/CA if necessary. Ø Coordinator MAC Device MAC 56 Beacon frame ACK Data request Jang Ping Sheu Data ACK 2020/11/2

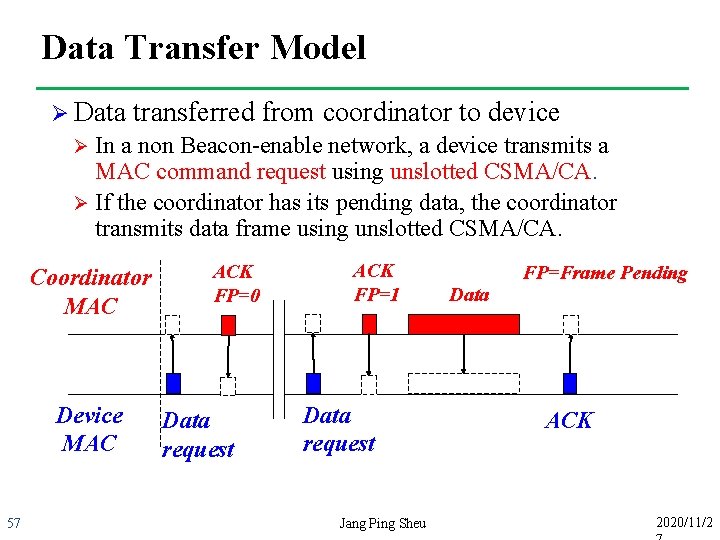
Data Transfer Model Ø Data transferred from coordinator to device In a non Beacon-enable network, a device transmits a MAC command request using unslotted CSMA/CA. Ø If the coordinator has its pending data, the coordinator transmits data frame using unslotted CSMA/CA. Ø Coordinator MAC Device MAC 57 ACK FP=0 Data request ACK FP=1 Data request Jang Ping Sheu Data FP=Frame Pending ACK 2020/11/2

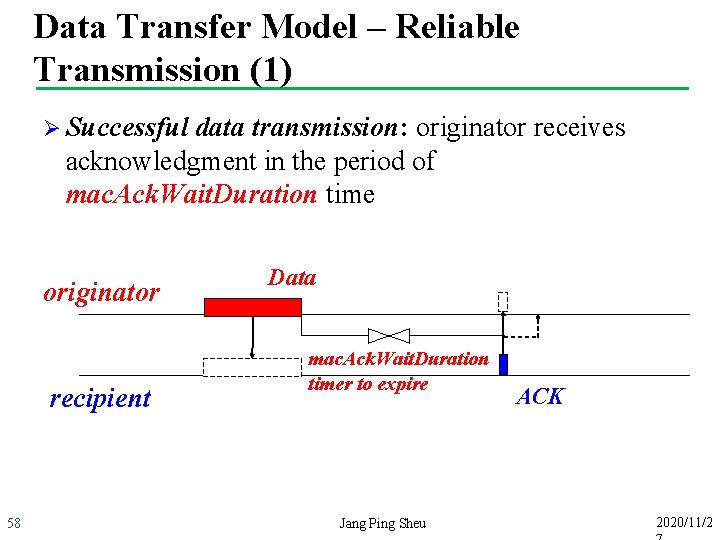
Data Transfer Model – Reliable Transmission (1) Ø Successful data transmission: originator receives acknowledgment in the period of mac. Ack. Wait. Duration time originator recipient 58 Data mac. Ack. Wait. Duration timer to expire Jang Ping Sheu ACK 2020/11/2

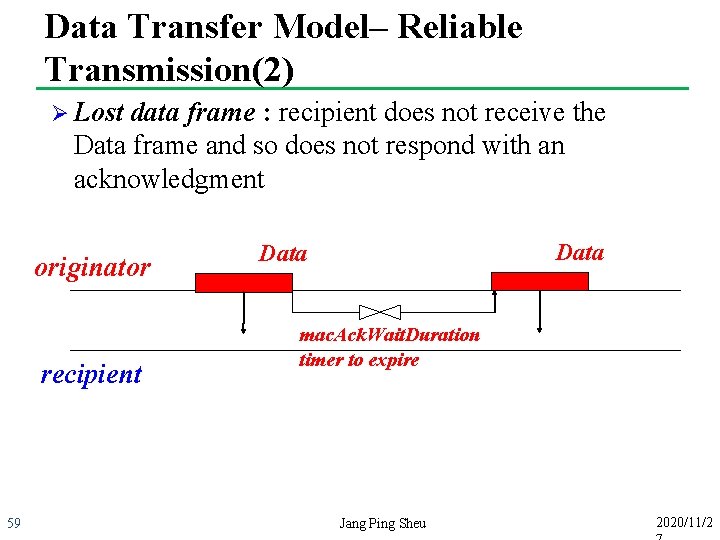
Data Transfer Model– Reliable Transmission(2) Ø Lost data frame : recipient does not receive the Data frame and so does not respond with an acknowledgment originator recipient 59 Data mac. Ack. Wait. Duration timer to expire Jang Ping Sheu 2020/11/2

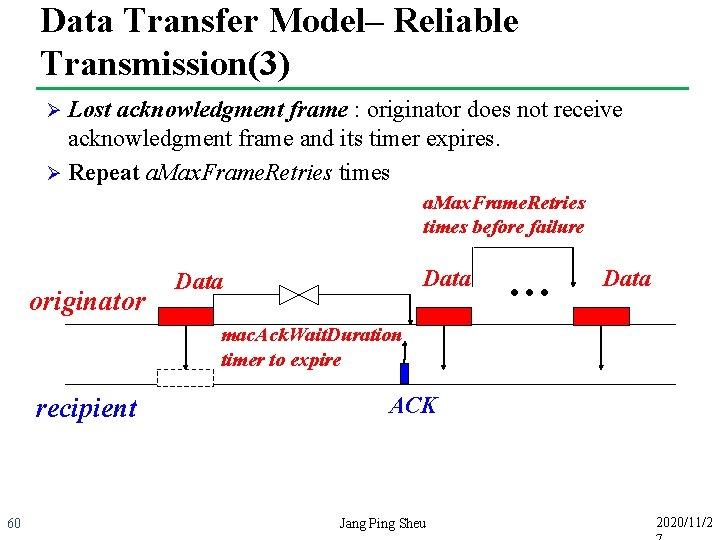
Data Transfer Model– Reliable Transmission(3) Lost acknowledgment frame : originator does not receive acknowledgment frame and its timer expires. Ø Repeat a. Max. Frame. Retries times Ø a. Max. Frame. Retries times before failure originator Data … Data mac. Ack. Wait. Duration timer to expire recipient 60 ACK Jang Ping Sheu 2020/11/2

Chapter 3 Outline Ø 3. 1. Ø 3. 2. Ø 3. 3. Ø 3. 4. Ø 3. 5. 61 802. 11 MAC機制 802. 11 碰撞議題相關研究 802. 11 節能、省電議題相關研究 802. 15. 4 MAC protocols for WSNs Jang Ping Sheu 2020/11/2

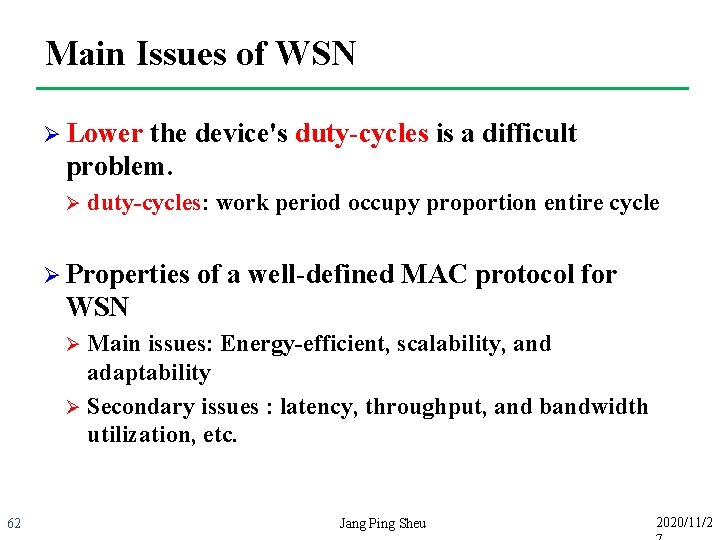
Main Issues of WSN Ø Lower the device's duty-cycles is a difficult problem. Ø duty-cycles: work period occupy proportion entire cycle Ø Properties of a well-defined MAC protocol for WSN Main issues: Energy-efficient, scalability, and adaptability Ø Secondary issues : latency, throughput, and bandwidth utilization, etc. Ø 62 Jang Ping Sheu 2020/11/2

Energy Problems on the MAC Layer Ø Collision Ø Overhearing Ø Control-packet overhead Ø The major problem is “idle listening” 63 Jang Ping Sheu 2020/11/2

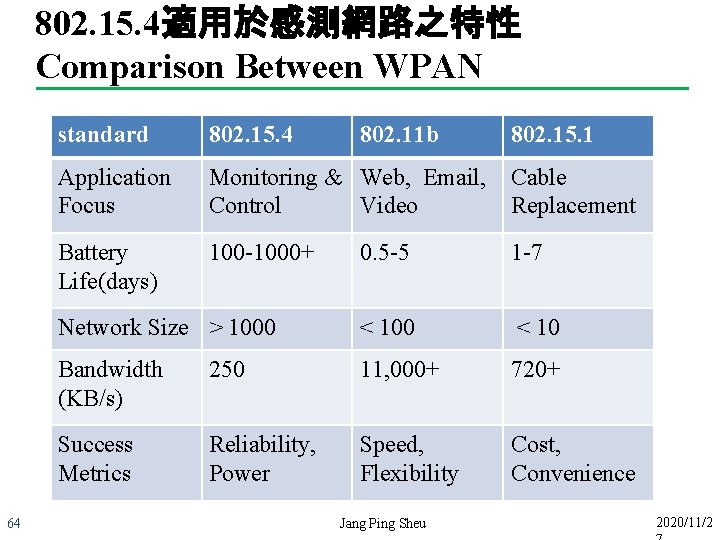
802. 15. 4適用於感測網路之特性 Comparison Between WPAN 64 standard 802. 15. 4 802. 11 b Application Focus Monitoring & Web, Email, Control Video Cable Replacement Battery Life(days) 100 -1000+ 0. 5 -5 1 -7 Network Size > 1000 < 10 Bandwidth (KB/s) 250 11, 000+ 720+ Success Metrics Reliability, Power Speed, Flexibility Cost, Convenience Jang Ping Sheu 802. 15. 1 2020/11/2

MAC Protocols for WSNs Ø Asynchronous MAC protocols No synchronization or coordinate schedule between neighbor nodes Ø S-MAC, T-MAC, B-MAC, Wise MAC, etc. Ø Ø Synchronous MAC protocols Time synchronization is achieved externally or synchronization is managed by specific node Ø TRAMA, DMAC, LEACH, etc. Ø 65 Jang Ping Sheu 2020/11/2

S-MAC Ø S-MAC assume sensor networks to be composed of many small nodes deployed in an ad hoc fashion. 66 Ø The large number of nodes can also take advantage of short-range, multi-hop communication to conserve energy. Ø Most communication will be between nodes as peers, rather than to a single base-station. Jang Ping Sheu 2020/11/2

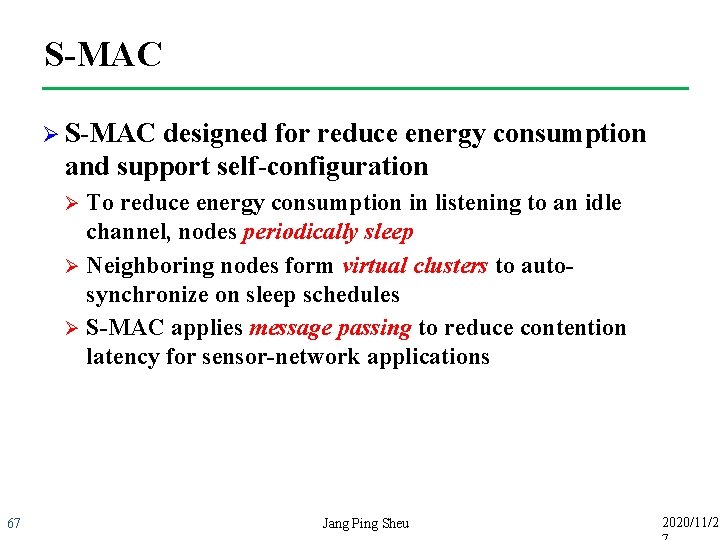
S-MAC Ø S-MAC designed for reduce energy consumption and support self-configuration To reduce energy consumption in listening to an idle channel, nodes periodically sleep Ø Neighboring nodes form virtual clusters to autosynchronize on sleep schedules Ø S-MAC applies message passing to reduce contention latency for sensor-network applications Ø 67 Jang Ping Sheu 2020/11/2

S-MAC Ø Locally managed synchronizations periodic sleep– listen schedules sleep Listen sleep Sleep Ø Virtual Listen sleep Active cluster C A Cluster 1 68 time Jang Ping Sheu B D Cluster 2 2020/11/2

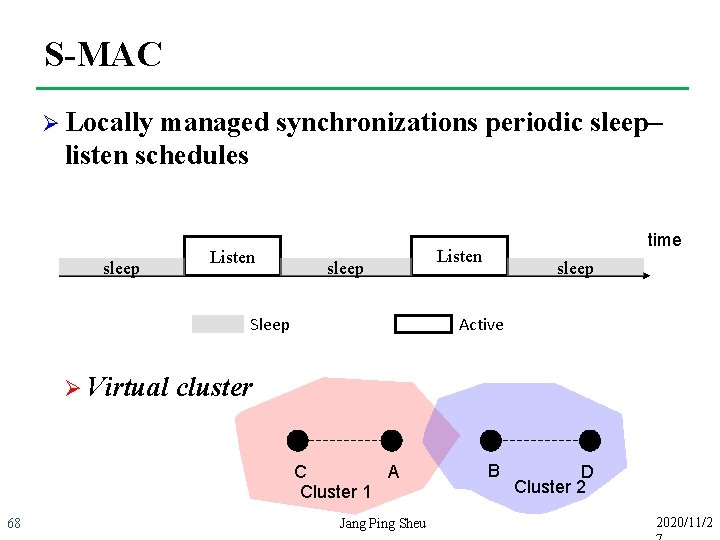
S-MAC Ø Every node should wakeup in Listen period Synchronization period Control period (RTS/CTS) ※ Node use CSMA before sending any packet Sending data / sleep period Listen period Sender Receiver 69 CS TX sync CS TX RTS RX CTS RX RTS CS TX CTS Jang Ping Sheu TX data RX data 2020/11/2

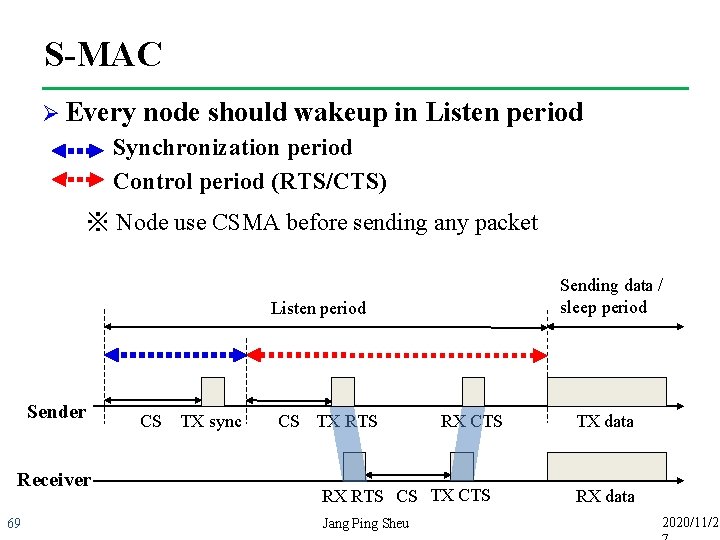
S-MAC n Re-transmit l l n message problem Long message => re-transmission will take a long time Short message => large control overhead (RTS/CTS) message passing 1 Sender 2 3 4 5 3 Receiver Re-transmit 3 ok Neighbor of receiver sleep 70 RTS CTS sleep Transmit data ACK 2020/11/2

S-MAC n Adaptive-Listening l 71 Node who overhears its neighbor’s transmissions (ideally only RTS or CTS) wake up for a short period of time at the end of the data transmission. If the node is the next-hop node => remain active after data transmission, prepare to forwarding its neighbor’s message. If the node does not receive anything during the adaptive listening => go back to sleep. Jang Ping Sheu 2020/11/2

S-MAC-Summary Ø Locally time synchronization between neighbors Ø Power saving method: Ø Fixed wakeup/sleep interval Ø Transmit Ø 72 Characteristic: Contention transmission through CSMA Jang Ping Sheu 2020/11/2

S-MAC-Summary Ø Advantage Idle listening is reduced by sleep schedules Ø Time synchronization overhead may be prevented by sleep schedule announcements Ø Ø Disadvantage Adaptive listening incurs overhearing or idle listening Ø Sleep and listen periods are predefined and constant Ø 73 Jang Ping Sheu 2020/11/2

Timeout T-MAC Ø To improve the idle listening problem of the fixed duty cycle solution, such like S-MAC Ø T-MAC protocol is to reduce idle listening by transmitting all messages in bursts of variable length, and sleeping between bursts Ø An adaptive duty cycle in a novel way: by dynamically ending the active part of it 74 Jang Ping Sheu 2020/11/2

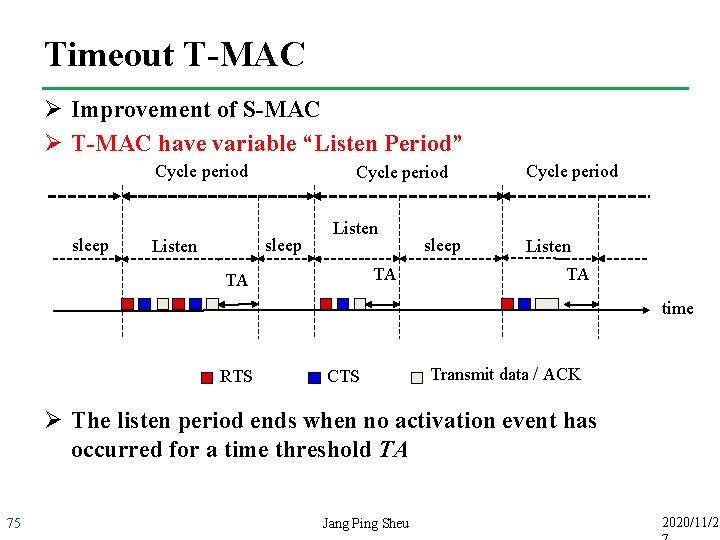
Timeout T-MAC Ø Improvement of S-MAC Ø T-MAC have variable “Listen Period” Cycle period sleep Listen TA TA sleep Cycle period Listen TA time RTS CTS Transmit data / ACK Ø The listen period ends when no activation event has occurred for a time threshold TA 75 Jang Ping Sheu 2020/11/2

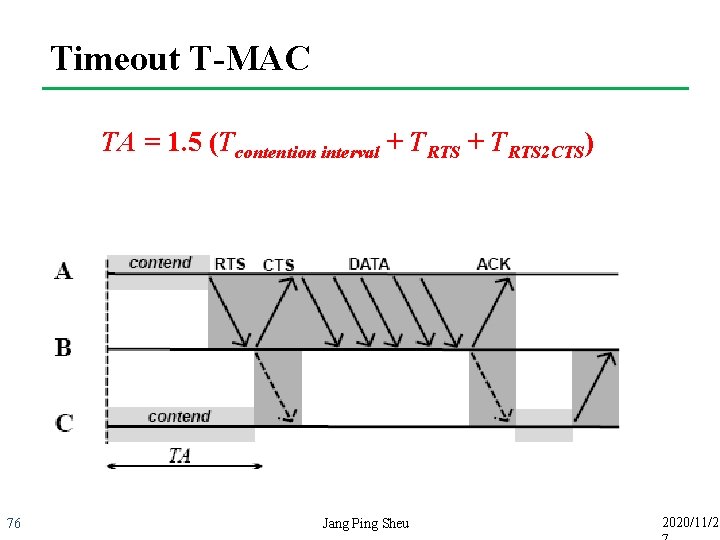
Timeout T-MAC TA = 1. 5 (Tcontention interval + TRTS 2 CTS) 76 Jang Ping Sheu 2020/11/2

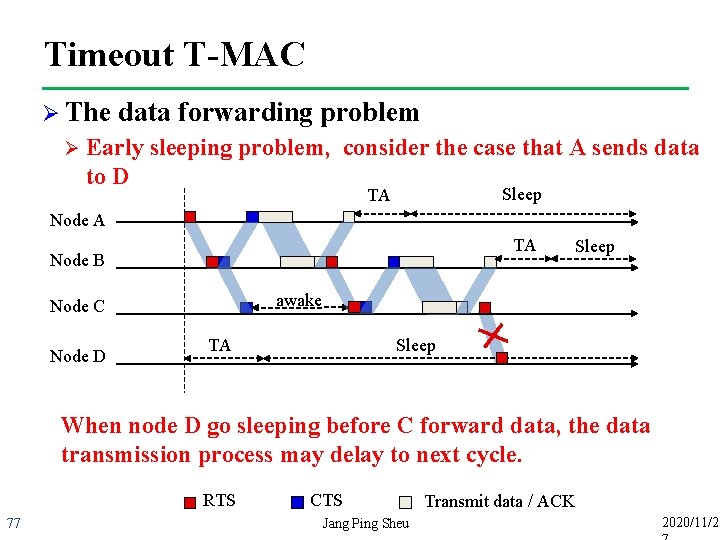
Timeout T-MAC Ø The Ø data forwarding problem Early sleeping problem, consider the case that A sends data to D Sleep TA Node A TA Node B awake Node C Node D Sleep TA Sleep When node D go sleeping before C forward data, the data transmission process may delay to next cycle. RTS 77 CTS Jang Ping Sheu Transmit data / ACK 2020/11/2

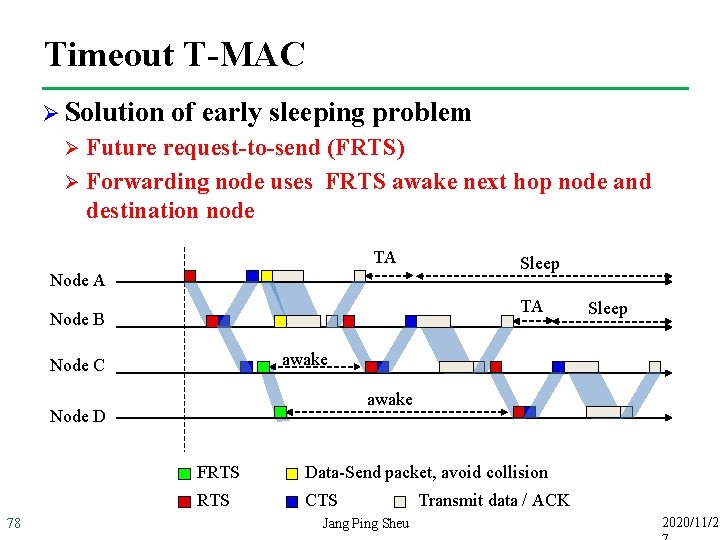
Timeout T-MAC Ø Solution of early sleeping problem Future request-to-send (FRTS) Ø Forwarding node uses FRTS awake next hop node and destination node Ø TA Node A TA Node B Sleep awake Node C awake Node D 78 Sleep FRTS Data-Send packet, avoid collision RTS CTS Jang Ping Sheu Transmit data / ACK 2020/11/2

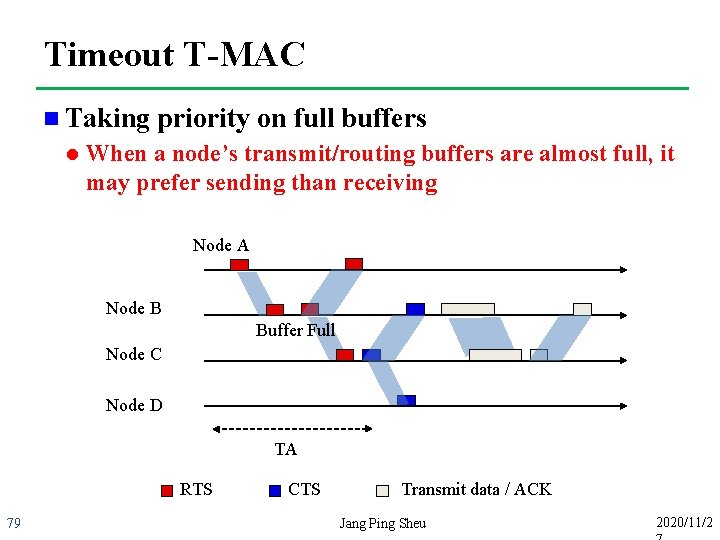
Timeout T-MAC n Taking l priority on full buffers When a node’s transmit/routing buffers are almost full, it may prefer sending than receiving Node A Node B Buffer Full Node C Node D TA RTS 79 CTS Transmit data / ACK Jang Ping Sheu 2020/11/2

Timeout T-MAC-Summary Ø Locally Ø Power Ø time synchronization between neighbors saving method: Dynamic wakeup/sleep interval Ø Transmit Ø 80 Characteristic: Contention transmission through CSMA Jang Ping Sheu 2020/11/2

Timeout T-MAC Ø Advantage Ø Enhance the poor results of the S-MAC protocol under variable traffic loads Ø Disadvantage Early sleeping problem Ø Higher latency than S-MAC Ø 81 81 Jang Ping Sheu 2020/11/2

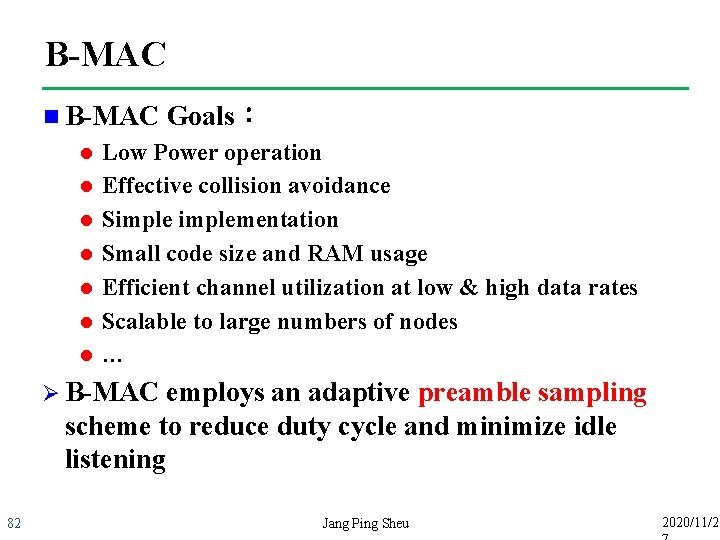
B-MAC n B-MAC l l l l Goals: Low Power operation Effective collision avoidance Simplementation Small code size and RAM usage Efficient channel utilization at low & high data rates Scalable to large numbers of nodes … Ø B-MAC employs an adaptive preamble sampling scheme to reduce duty cycle and minimize idle listening 82 Jang Ping Sheu 2020/11/2

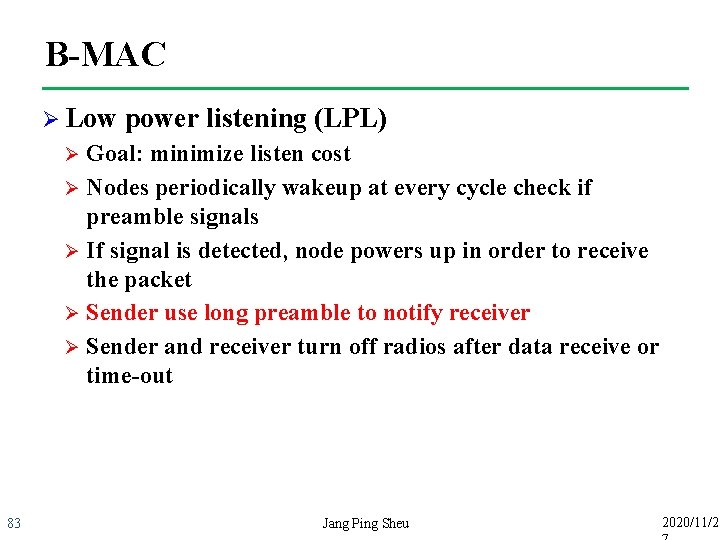
B-MAC Ø Low power listening (LPL) Goal: minimize listen cost Ø Nodes periodically wakeup at every cycle check if preamble signals Ø If signal is detected, node powers up in order to receive the packet Ø Sender use long preamble to notify receiver Ø Sender and receiver turn off radios after data receive or time-out Ø 83 Jang Ping Sheu 2020/11/2

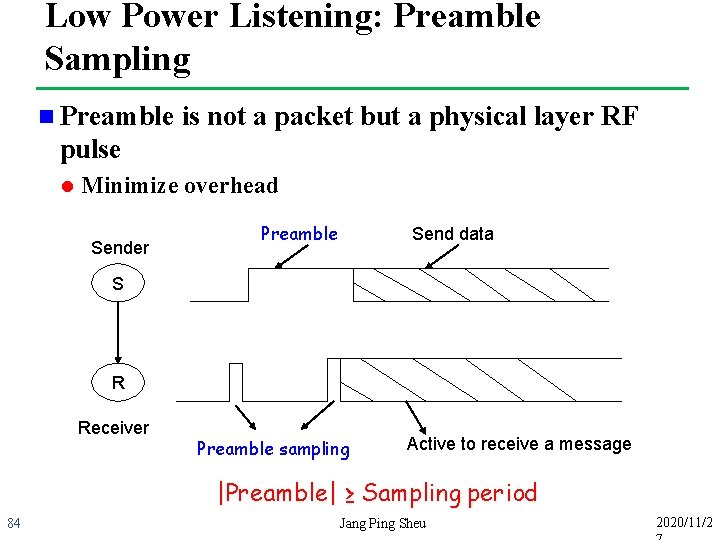
Low Power Listening: Preamble Sampling n Preamble is not a packet but a physical layer RF pulse l Minimize overhead Sender Preamble Send data S R Receiver Preamble sampling Active to receive a message |Preamble| ≥ Sampling period 84 Jang Ping Sheu 2020/11/2

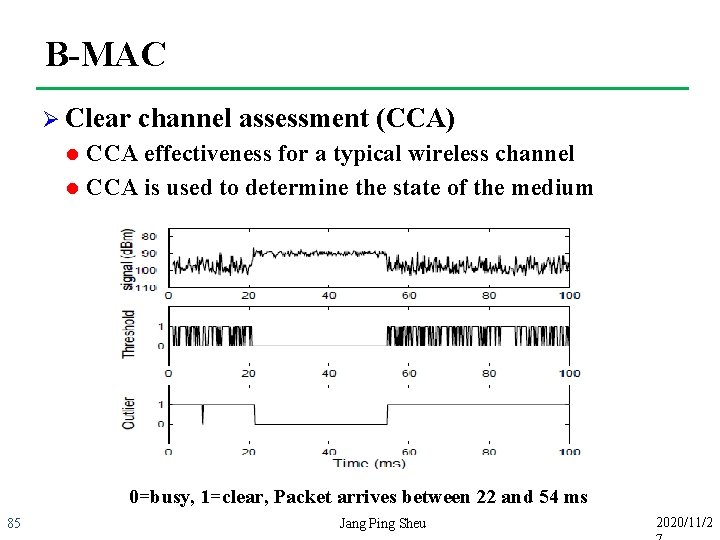
B-MAC Ø Clear l l channel assessment (CCA) CCA effectiveness for a typical wireless channel CCA is used to determine the state of the medium 0=busy, 1=clear, Packet arrives between 22 and 54 ms 85 Jang Ping Sheu 2020/11/2

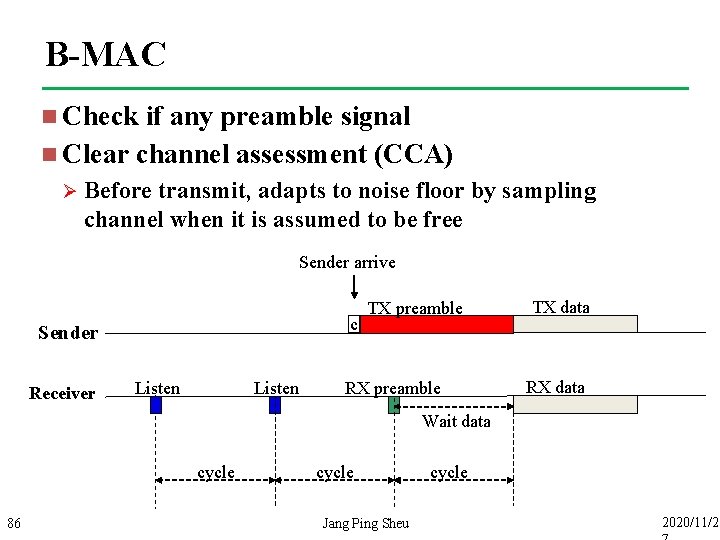
B-MAC n Check if any preamble signal n Clear channel assessment (CCA) Ø Before transmit, adapts to noise floor by sampling channel when it is assumed to be free Sender arrive c Sender Receiver Listen TX preamble RX preamble TX data RX data Wait data cycle 86 cycle Jang Ping Sheu cycle 2020/11/2

B-MAC- Summary n B-MAC is a non-time-synchronization method, it uses a long enough preamble to notify the receiver. n Power saving method: Self-defined wakeup/sleep interval Ø Long preamble notification Ø n Transmit Ø 87 Characteristic: Contention method through Clear Channel Assessment algorithm Jang Ping Sheu 2020/11/2

B-MAC- Summary n Advantage Doesn’t need any synchronization Ø RTS/CTS (optional) Ø Clean and simple interface Ø n Disadvantage Transmission delay will be long Ø Bad performance when heavy traffic load Ø 88 Jang Ping Sheu 2020/11/2

MAC protocols for WSN n Asynchronous MAC protocols No synchronization or coordinate schedule between neighbor nodes Ø S-MAC, T-MAC, B-MAC, … Ø n Synchronous MAC protocols Time synchronization is achieved externally or synchronization is managed by specific node Ø TRAMA, DMAC, … Ø 89 Jang Ping Sheu 2020/11/2

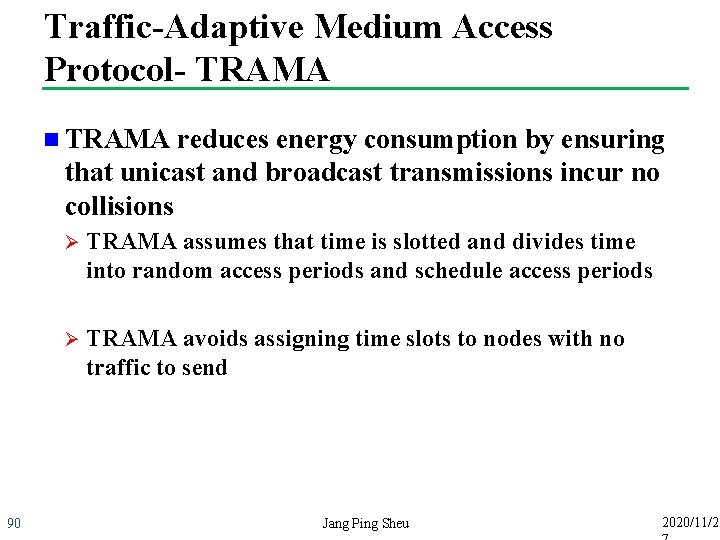
Traffic-Adaptive Medium Access Protocol- TRAMA n TRAMA reduces energy consumption by ensuring that unicast and broadcast transmissions incur no collisions 90 Ø TRAMA assumes that time is slotted and divides time into random access periods and schedule access periods Ø TRAMA avoids assigning time slots to nodes with no traffic to send Jang Ping Sheu 2020/11/2

TRAMA n Nodes need globally synchronized n Time divided into: Random access periods Ø Scheduled access periods Ø n Three main protocols: Neighbor Protocol (NP) Ø Adaptive Election Algorithm (AEA) Ø Schedule Exchange Protocol (SEP) Ø 91 Jang Ping Sheu 2020/11/2

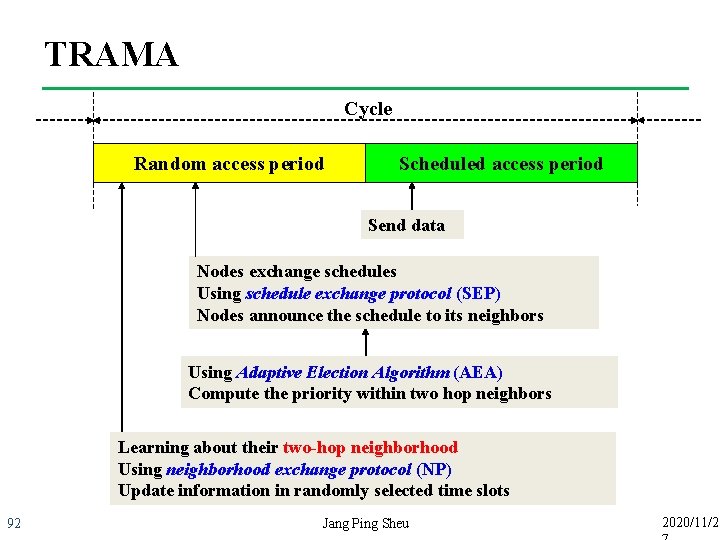
TRAMA Cycle Random access period Scheduled access period Send data Nodes exchange schedules Using schedule exchange protocol (SEP) Nodes announce the schedule to its neighbors Using Adaptive Election Algorithm (AEA) Compute the priority within two hop neighbors Learning about their two-hop neighborhood Using neighborhood exchange protocol (NP) Update information in randomly selected time slots 92 Jang Ping Sheu 2020/11/2

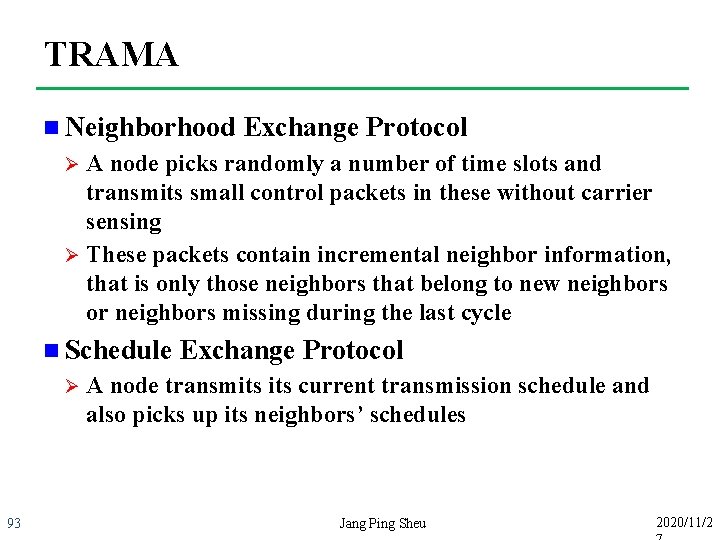
TRAMA n Neighborhood Exchange Protocol A node picks randomly a number of time slots and transmits small control packets in these without carrier sensing Ø These packets contain incremental neighbor information, that is only those neighbors that belong to new neighbors or neighbors missing during the last cycle Ø n Schedule Ø 93 Exchange Protocol A node transmits current transmission schedule and also picks up its neighbors’ schedules Jang Ping Sheu 2020/11/2

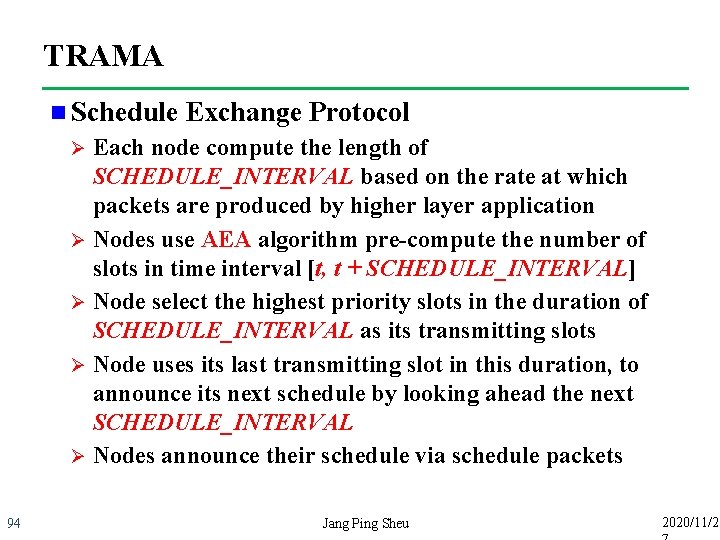
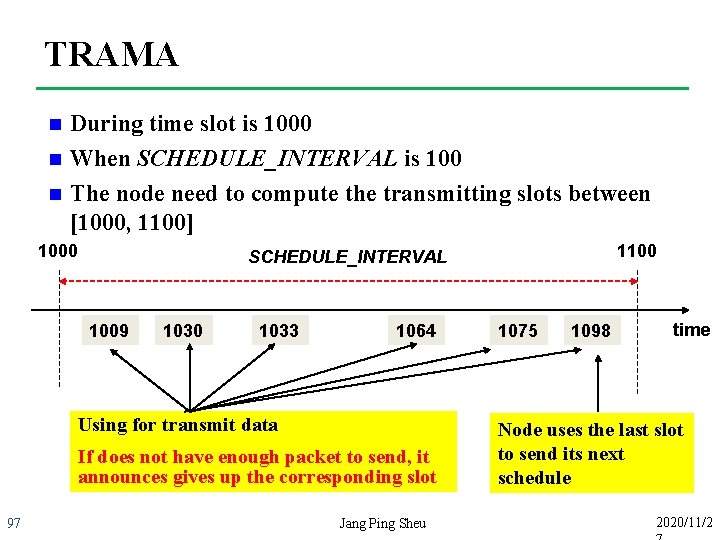
TRAMA n Schedule Exchange Protocol Each node compute the length of SCHEDULE_INTERVAL based on the rate at which packets are produced by higher layer application Ø Nodes use AEA algorithm pre-compute the number of slots in time interval [t, t + SCHEDULE_INTERVAL] Ø Node select the highest priority slots in the duration of SCHEDULE_INTERVAL as its transmitting slots Ø Node uses its last transmitting slot in this duration, to announce its next schedule by looking ahead the next SCHEDULE_INTERVAL Ø Nodes announce their schedule via schedule packets Ø 94 Jang Ping Sheu 2020/11/2

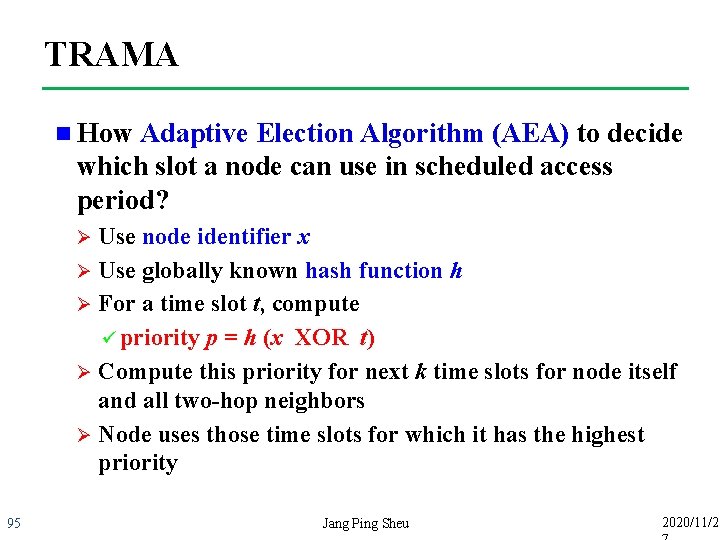
TRAMA n How Adaptive Election Algorithm (AEA) to decide which slot a node can use in scheduled access period? Use node identifier x Ø Use globally known hash function h Ø For a time slot t, compute ü priority p = h (x XOR t) Ø Compute this priority for next k time slots for node itself and all two-hop neighbors Ø Node uses those time slots for which it has the highest priority Ø 95 Jang Ping Sheu 2020/11/2

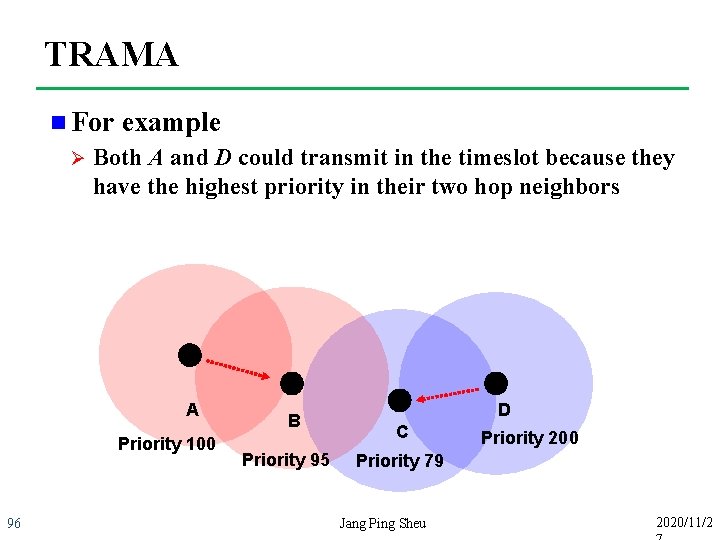
TRAMA n For Ø example Both A and D could transmit in the timeslot because they have the highest priority in their two hop neighbors A Priority 100 96 B Priority 95 D C Priority 200 Priority 79 Jang Ping Sheu 2020/11/2

TRAMA n n n During time slot is 1000 When SCHEDULE_INTERVAL is 100 The node need to compute the transmitting slots between [1000, 1100] 1000 1009 1030 1033 1064 Using for transmit data If does not have enough packet to send, it announces gives up the corresponding slot 97 1100 SCHEDULE_INTERVAL Jang Ping Sheu 1075 1098 time Node uses the last slot to send its next schedule 2020/11/2

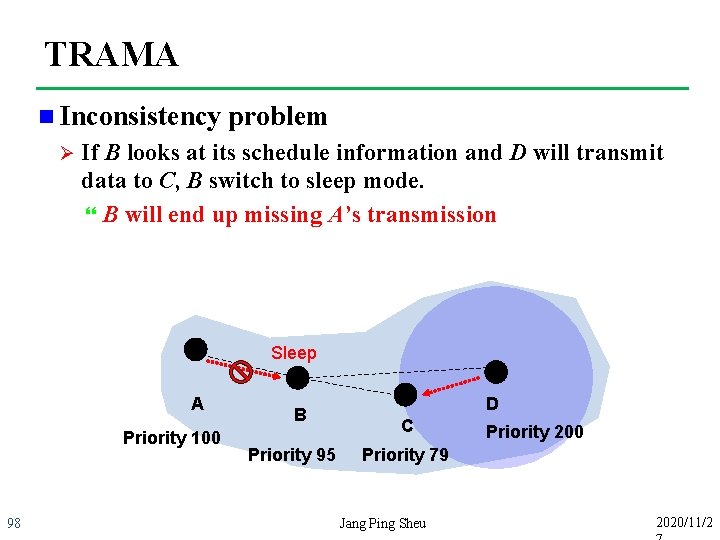
TRAMA n Inconsistency Ø problem If B looks at its schedule information and D will transmit data to C, B switch to sleep mode. B will end up missing A’s transmission Sleep A Priority 100 98 B Priority 95 D C Priority 200 Priority 79 Jang Ping Sheu 2020/11/2

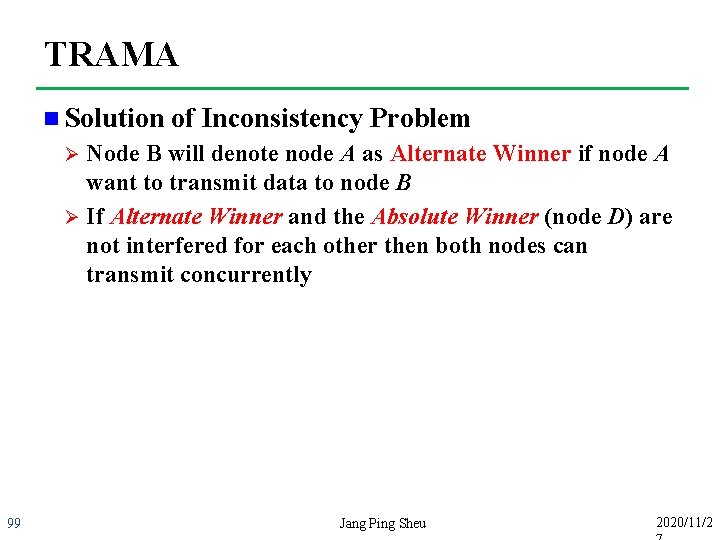
TRAMA n Solution of Inconsistency Problem Node B will denote node A as Alternate Winner if node A want to transmit data to node B Ø If Alternate Winner and the Absolute Winner (node D) are not interfered for each other then both nodes can transmit concurrently Ø 99 Jang Ping Sheu 2020/11/2

TRAMA- Summary n Global synchronized time slot n Power saving method: Ø Higher percentage of sleep time and less collision probability is achieved compared to CSMA based protocols Ø Transmit Ø Ø 100 Characteristic: Contention-Free TDMA Adaptive Election Algorithm decide transmission Jang Ping Sheu 2020/11/2

TRAMA- Summary n Advantages Only use two hop neighbor information can decide transmission priority Ø Higher percentage of sleep time, less collision probability and higher maximum throughput than contention-based S-MAC Ø n Disadvantages Higher delay problem Ø Substantial memory/CPU requirements for schedule computation Ø 101 Jang Ping Sheu 2020/11/2

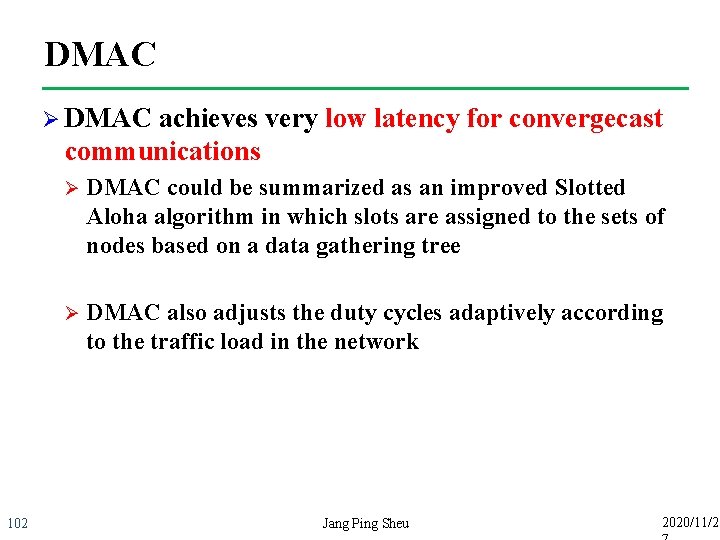
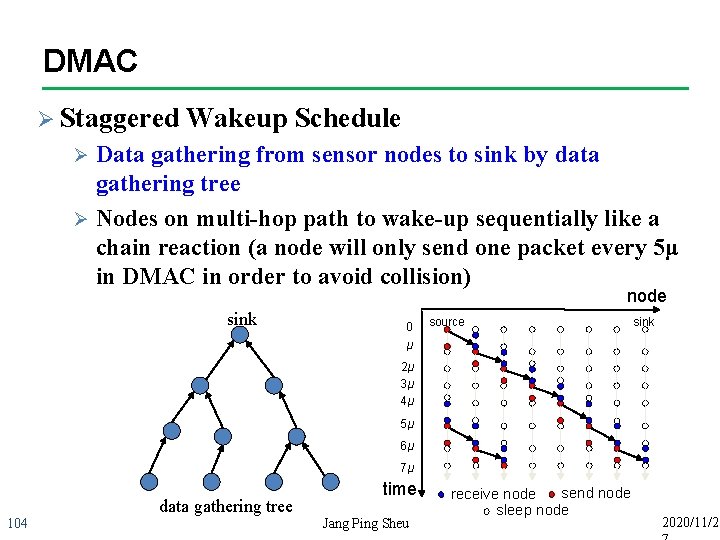
DMAC Ø DMAC achieves very low latency for convergecast communications 102 Ø DMAC could be summarized as an improved Slotted Aloha algorithm in which slots are assigned to the sets of nodes based on a data gathering tree Ø DMAC also adjusts the duty cycles adaptively according to the traffic load in the network Jang Ping Sheu 2020/11/2

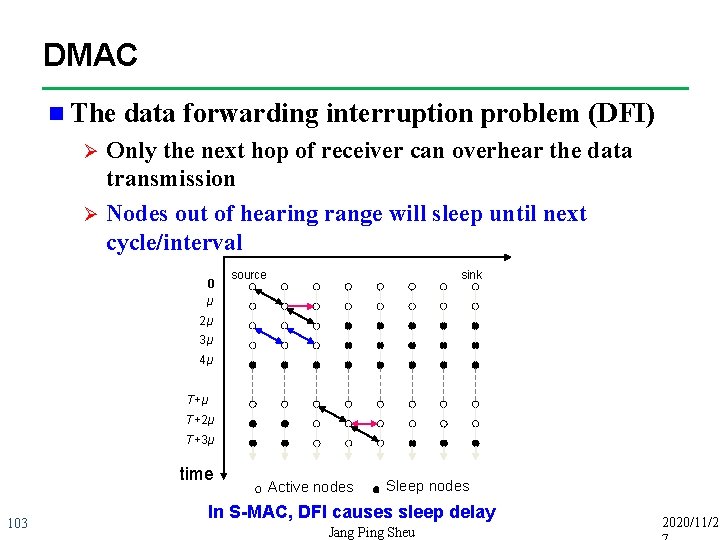
DMAC n The data forwarding interruption problem (DFI) Only the next hop of receiver can overhear the data transmission Ø Nodes out of hearing range will sleep until next cycle/interval Ø 0 μ source sink 2μ 3μ 4μ T+2μ T+3μ time 103 Active nodes Sleep nodes In S-MAC, DFI causes sleep delay Jang Ping Sheu 2020/11/2

DMAC Ø Staggered Wakeup Schedule Data gathering from sensor nodes to sink by data gathering tree Ø Nodes on multi-hop path to wake-up sequentially like a chain reaction (a node will only send one packet every 5μ in DMAC in order to avoid collision) Ø node sink 0 source sink μ 2μ 3μ 4μ 5μ 6μ 7μ data gathering tree 104 time Jang Ping Sheu send node receive node sleep node 2020/11/2

DMAC Ø When nodes has multiple packets to send Ø DMAC use slot-by-slot mechanism Ø Piggyback a more data flag in MAC header Ø Node not active at next slot, but schedule a 3μ sleep then goes to receiving state. sleep RX TX sink More data flag sleep RX TX sleep More data flag RX TX sleep time More data flag RX TX 105 sleep RX TX sleep Jang Ping Sheu 2020/11/2

DMAC-Summary n Need external time synchronized in prescribe area n Power saving method: Ø Sleep schedule of a node an offset that depends upon its depth on the tree n Transmit Characteristic: Improved Slotted Aloha algorithm Ø Contention-Free slots are assigned based on a data gathering tree Ø 106 Jang Ping Sheu 2020/11/2

DMAC-Summary n Advantage: Ø DMAC achieves very good latency compared to other sleep/listen period assignment methods n Disadvantage Ø 107 Collision avoidance methods are not utilized, if number of nodes that have the same schedule try to send to the same node, collisions will occur Jang Ping Sheu 2020/11/2

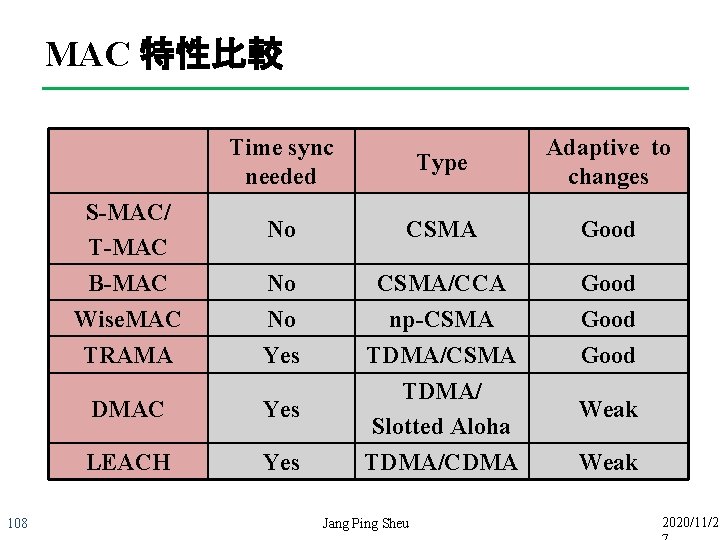
MAC 特性比較 108 Time sync needed Type Adaptive to changes S-MAC/ T-MAC No CSMA Good B-MAC No CSMA/CCA Good Wise. MAC No np-CSMA Good TRAMA Yes TDMA/CSMA Good DMAC Yes TDMA/ Slotted Aloha Weak LEACH Yes TDMA/CDMA Weak Jang Ping Sheu 2020/11/2

References 109 1. Ilker Demirkol, Cem Ersoy, Fatih Alagöz , “MAC Protocols for Wireless Sensor Networks: A Survey, ” Communications Magazine, IEEE , April 2006 2. Deborah Estrin, John Heidemann, and Wei Ye, “An Energy-Efficient MAC Protocol for Wireless Sensor Networks, ”IEEE INFOCOM 2002. 3. W. Ye, J. Heidemann, and D. Estrin, “Medium Access Control with Coordinated Adaptive Sleeping for Wireless Sensor Networks, ” IEEE/ACM Trans. Net. 2004 , 4. Koen Langendoen and Tijs van Dam, “An Adaptive Energy-Efficient MAC Protocol for Wireless Sensor Networks, ” The First ACM Conference on Embedded Networked Sensor Systems (Sensys&03), pp. 171 --180, 2003 5. David. Culler, Jason. Hill, and Joseph. Polastre, “Versatile Low Power Media Access for Wireless Sensor Networks, ” the 2 nd ACM Conference on Embedded Networked Sensor Systems (Sen. Sys), November 3 -5, 2004 6. A. El-Hoiydi, “Spatial TDMA and CSMA with Preamble Sampling for Low Power Ad Hoc Wireless Sensor Networks, ” Proc. ISCC 2002 7. C. C. Enz et al. , “Wise. NET: An Ultralow-Power Wireless Sensor Network Solution, ” IEEE Comp. , vol. 37, no. 8, Aug. 2004. 8. V. Rajendran, K. Obraczka, and J. J. Garcia-Luna-Aceves, “Energy-Efficient, Collision-Free Medium Access Control for Wireless Sensor Networks, ” Proc. ACM Sen. Sys ‘ 03, Los Angeles, CA, Nov. 2003, pp. 181– 92. 9. W. Rabiner Heinzelman, A. Chandrakasan, and H. Balakrishnan, “Energy-Efficient Communication Protocols for Wireless Microsensor Networks, ” Hawaii International Conference on System Sciences (HICSS '00), January 2000. 10. G. Lu, B. Krishnamachari, and C. S. Raghavendra, “An Adaptive Energy-Efficient and Low-Latency MAC for Data Gathering in Wireless Sensor Networks, ” Proc. 18 th Int’l. Parallel and Distrib. Processing Symp. , Apr. 2004, p. 224. 11. Holger Karl, Andreas Willig , “Protocols and architectures for wireless sensor networks, ” Jang Ping Sheu 2020/11/2