Security Credit most slides from Forouzan TCPIP protocol
































- Slides: 80

Security Credit: most slides from Forouzan, TCP/IP protocol suit TCP/IP Protocol Suite 1

Criminal Expoits and Attacks n n Phishing: Masquerading as a well-known site to obtain a user’ personal info. Denial of Service: Intentionally blocking a site to prevent business activities. Loss of control: an intruder gains control of a system. Loss of data: Steal or delete. TCP/IP Protocol Suite 2

Attacks n Software Based Attackes n n Hardware Based Attacks n n Malware – Malicious software – damaging or annoying software. Viruses or worms. Bios, USB devices, NAS, Cell phones Attacks on Virtualized Systems

Software based attacks: Viruses Attaches to a legitimate software (carrier, a program or document) and then replicates through other programs, devices, emails, instant messaging, etc. Computer crashes, destruction of HD, fill up HD, Reduce security settings allowing others to come in, reformat HD, etc. File infecting virus attaches to executables (such as cascade virus), resident virus loaded into RAM (such as Randex, Meve, Mr. Klunky), Boot virus infects MBR (Polyboot. B , Anti. EXE), companion virus adds program to OS replacing legitimate OS programs (Stator, Asimove. 1539), Macro virus written in any macro scripting (Melissa. A, Bablas. Pc). Polymorphic virus changes itself to avoid detection

Worms n n n Stand alone programs Takes advantage of the OS/application vulnerabilities. Worms uses networks to send copies of itself slowing down networks. While virus requires user action to start an infected program, worms do not (can start executing itself). Worms as they travel through internet can leave a payload behind on each system which can delete files or allow remote controlling of the system.

Concealing malware n Trojan horses, rootkits, logic bombs and privilege escalation.

Trojan Horse n Installed with the knowledge of the user. A program advertised as a utility but actually does something else (screen saver, calendar, player, etc. ). These programs may do a legitimate activity, but also might capture credit card info, etc and send it.

Rootkits n Programs installed on computers that takes control of certain aspects of the computer by replacing OS utilities. Sony installed a program on their CDs (2005) preventing copying of the CD by operating system routines. Others used this idea and created their own, or added features to Sony’s program. Rootkits do not spread themselves. Very difficult to remove from HD. Boot from another device and see if problems disappear.

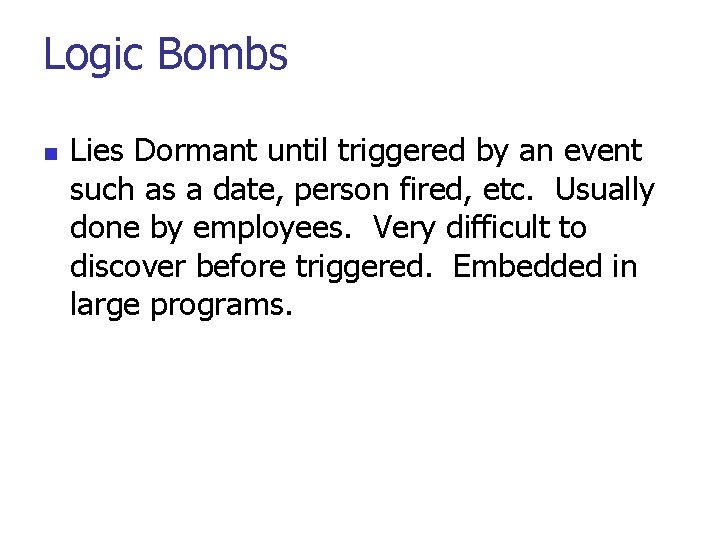
Logic Bombs n Lies Dormant until triggered by an event such as a date, person fired, etc. Usually done by employees. Very difficult to discover before triggered. Embedded in large programs.

Privilege Escalation n Either change own privilege to higher level, or use another employees higher privilege. Done by exploiting vulnerabilities of OS.

Malware for profit n n Spam, spyware and botnets Spam n Waste of time, checking and deleting. Email lists are sold by many ISPs, and other sites.

Spyware n n n Tracking software installed without the knowledge of the user. Advertises and Collects and distributes personal information. Harder to detect and remove than viruses. Causes the computer to slow down, freezes up, new browser toolbars or menus installed, hijacked homepage and increased popups. Adware – a software that delivers advertising for gambling sites or pornography. Keeps track of browsing behavior and reports to give specific pop-ups for merchandize. Keyloggers. A small hardware attached to the keyboard interface or a resident software that monitors and logs each keystroke.

Botnets n n n Programs that render your computer to be controlled remotely. The computer is called a zombie. Thousands of zombie computers under the control of a single attacker is called a botnet. Attackers use internet relay chat (IRC) to remotely control the zombies. Zombies are used for spamming, spreading malware, denying services, etc.

Hardware based attacks n BIOS n n BIOS can be flashed with viruses or rootkits. Flashing the bios can render the computer useless until it is replaced. You can write protect BIOS to prevent this from happening. USB devices NAS and SANs can get all malware discussed. Cell phones – infected messages, launch attacks, make calls, etc.

Attacks on Virtualized systems n n n Operating system virtualization with virtual machine Storage virtualization Multiple os on the same machine. However, existing anti virus/spam software do not work. Additional concern – one existing virtual machine may infect another. Protection approaches: n n Hypervisor-runs on the physical machine and manages the virtual machines. Run security software such as a firewall on the physical machine

Techniques used n n n n n Wiretapping Replay – sending packets captured from previous session such as username and password. Buffer overflow: sending more data than receiver expects, thereby storing values in memory buffer. Address spoofing. Faking IP source address Name spoofing. Misspelling of a well-known name or poisoning name server. SYN flood – sending stream of TCP SYN Key breaking – guessing password Port Scanning – to find vulnerability Packet Interception – man in the middle attack. TCP/IP Protocol Suite 16

Goals of a security n n n Confidentiality – protect our confidential information in storage and transmission. Integrity – Information is not changed unintentionally. Only changed by authorized people. Availability – Information should be available to authorized users. TCP/IP Protocol Suite 17

Security Techniques n n n Encryption Digital Signatures Firewall Intrusion detection systems Packet inspection and content scanning VPN TCP/IP Protocol Suite 18

28. 1 CRYPTOGRAPHY The word cryptography in Greek means “secret writing. ” The term today refers to the science and art of transforming messages to make them secure and immune to attacks. The topics discussed in this section include: Symmetric-Key Cryptography Asymmetric-Key Cryptography Comparison TCP/IP Protocol Suite 19

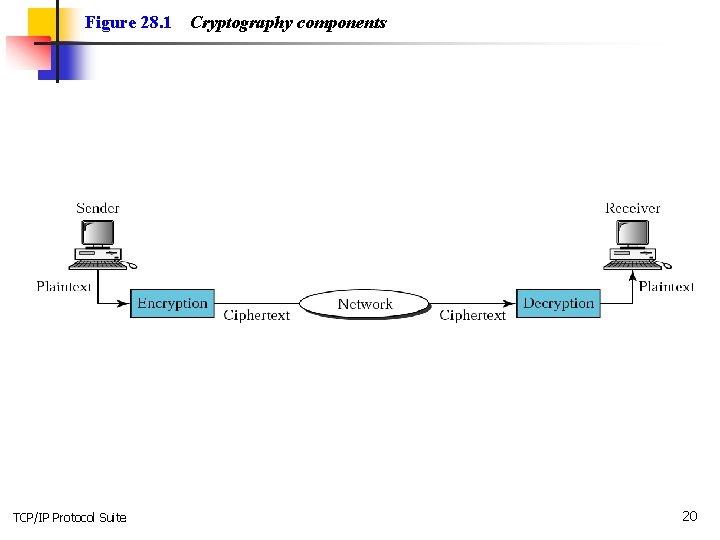
Figure 28. 1 TCP/IP Protocol Suite Cryptography components 20

Note: In cryptography, the encryption/decryption algorithms are public; the keys are secret. TCP/IP Protocol Suite 21

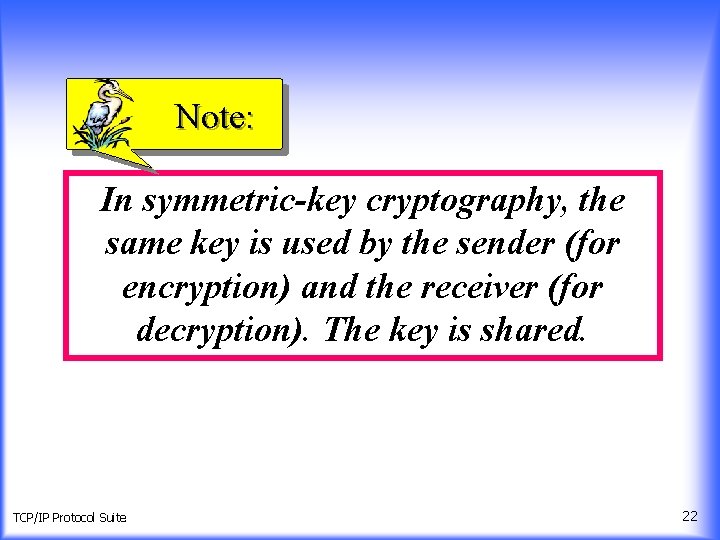
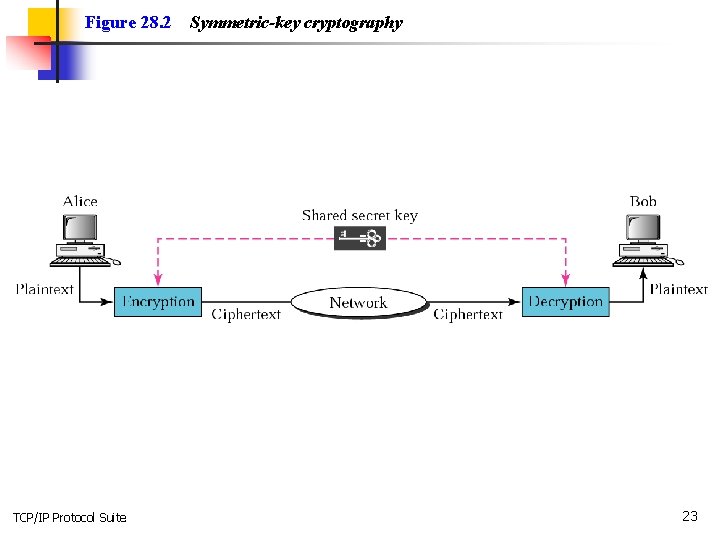
Note: In symmetric-key cryptography, the same key is used by the sender (for encryption) and the receiver (for decryption). The key is shared. TCP/IP Protocol Suite 22

Figure 28. 2 TCP/IP Protocol Suite Symmetric-key cryptography 23

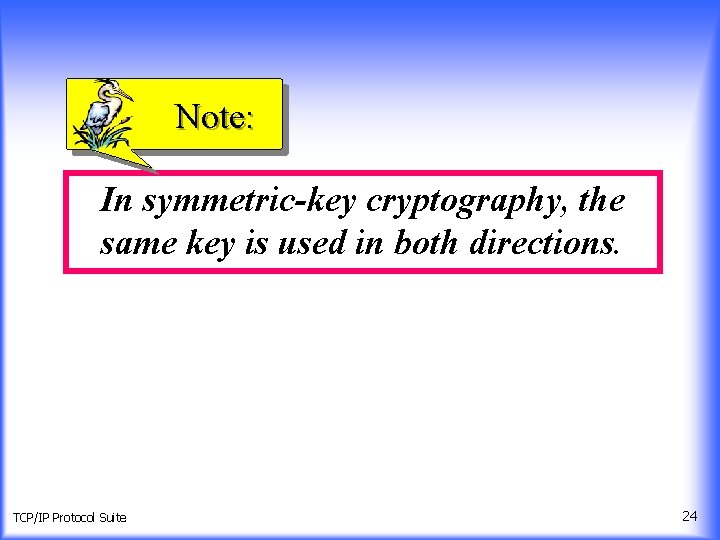
Note: In symmetric-key cryptography, the same key is used in both directions. TCP/IP Protocol Suite 24

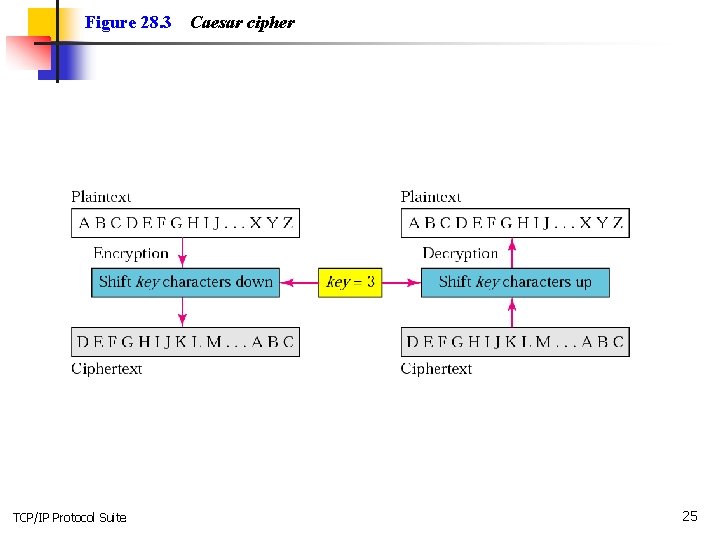
Figure 28. 3 TCP/IP Protocol Suite Caesar cipher 25

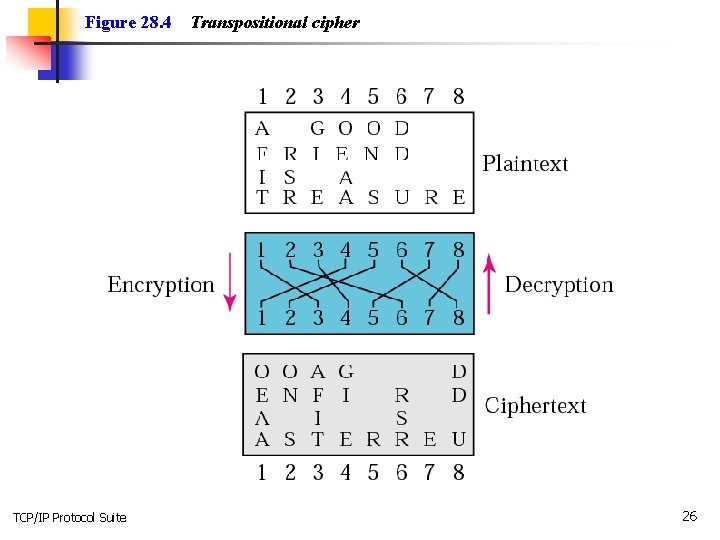
Figure 28. 4 TCP/IP Protocol Suite Transpositional cipher 26

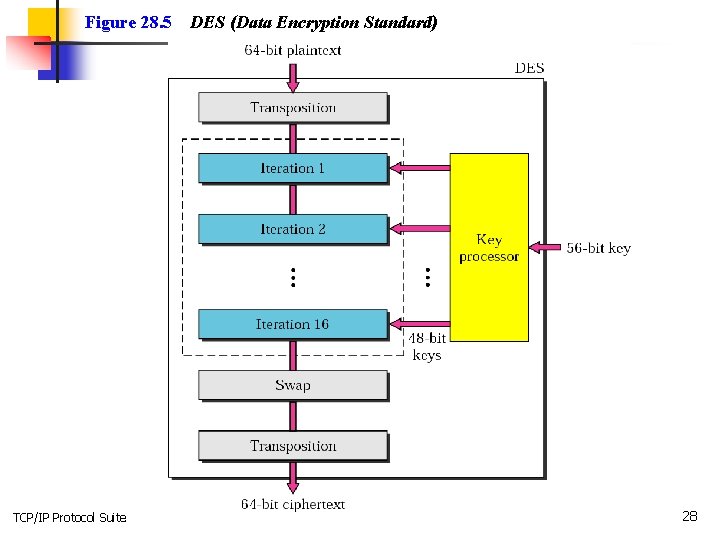
Data encryption Standard (DES) n n n Is a block cipher Takes 64 -bit plaintext and creates a 64 -bit ciphertext. The cipher key is a 56 -bit key. It uses 16 rounds, each round mixes and swapps (left half with right half) TCP/IP Protocol Suite 27

Figure 28. 5 TCP/IP Protocol Suite DES (Data Encryption Standard) 28

Note: The DES cipher uses the same concept as the Caesar cipher, but the encryption/ decryption algorithm is much more complex. TCP/IP Protocol Suite 29

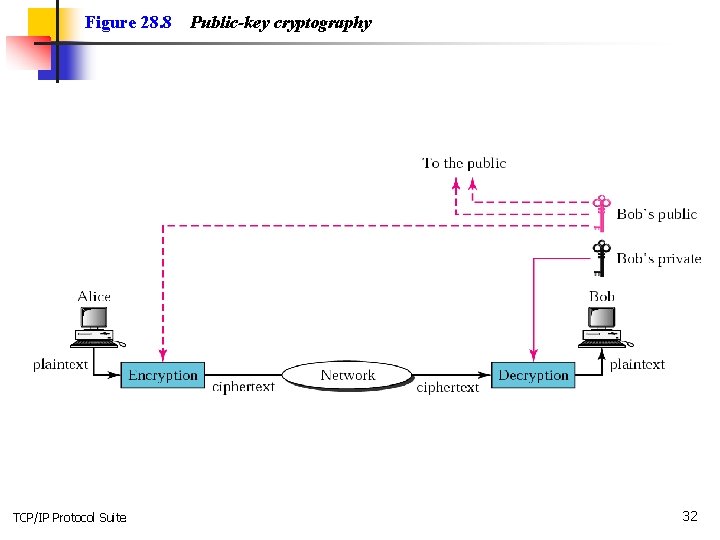
Asymmetric-key ciphers n n The secret key is personal and unshared. Symmetric key scheme would require n(n-1)/2 keys, for a million people it would require half a billion shared secret keys. Whereas, in asymmetric scheme we would only require a million secret keys. Asymmetric ciphers use two keys, private and public. Asymmetric is much slower. Both symmetric and asymmetric can be used if need to be. Think: if you want to send a secret symmetric key, you can use asymmetric. TCP/IP Protocol Suite 30

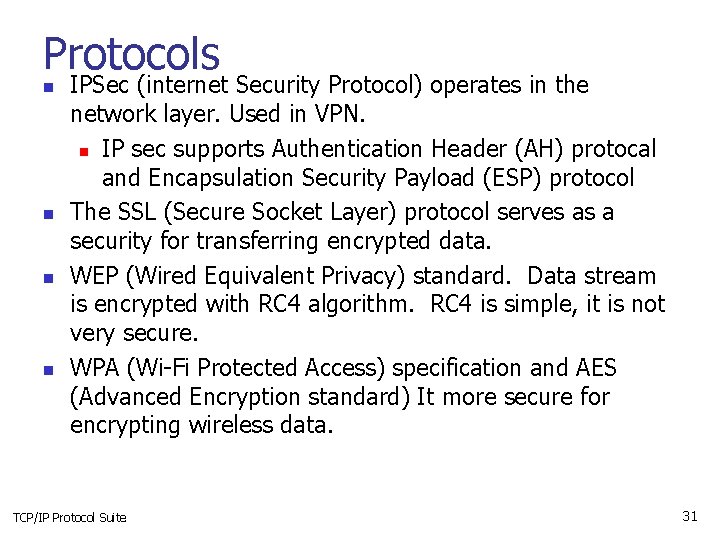
Protocols n n IPSec (internet Security Protocol) operates in the network layer. Used in VPN. n IP sec supports Authentication Header (AH) protocal and Encapsulation Security Payload (ESP) protocol The SSL (Secure Socket Layer) protocol serves as a security for transferring encrypted data. WEP (Wired Equivalent Privacy) standard. Data stream is encrypted with RC 4 algorithm. RC 4 is simple, it is not very secure. WPA (Wi-Fi Protected Access) specification and AES (Advanced Encryption standard) It more secure for encrypting wireless data. TCP/IP Protocol Suite 31

Figure 28. 8 TCP/IP Protocol Suite Public-key cryptography 32

Note: Symmetric-key cryptography is often used for long messages. TCP/IP Protocol Suite 33

Note: Asymmetric-key algorithms are more efficient for short messages. TCP/IP Protocol Suite 34

Note: Digital signature can provide authentication, integrity, and nonrepudiation for a message. TCP/IP Protocol Suite 35

28. 3 DIGITAL SIGNATURE Digital signature can provide nonrepudiation for a message. authentication, integrity, and The topics discussed in this section include: Signing the Whole Document Signing the Digest TCP/IP Protocol Suite 36

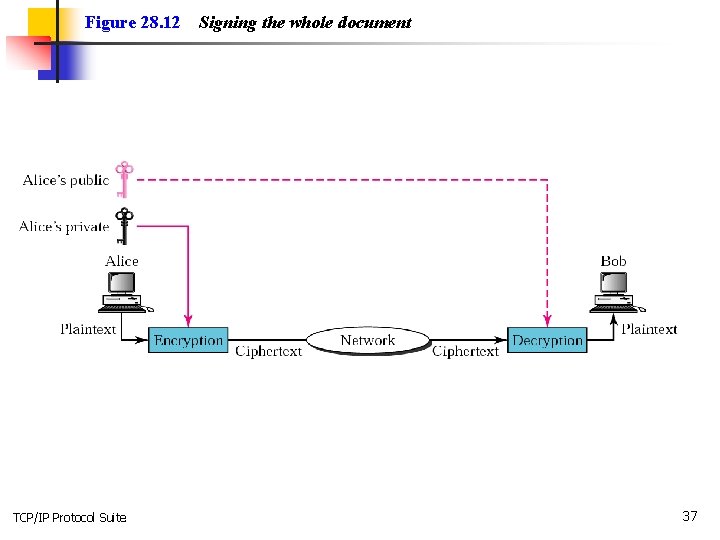
Figure 28. 12 TCP/IP Protocol Suite Signing the whole document 37

Note: Digital signature does not provide privacy. If there is a need for privacy, another layer of encryption/decryption must be applied. TCP/IP Protocol Suite 38

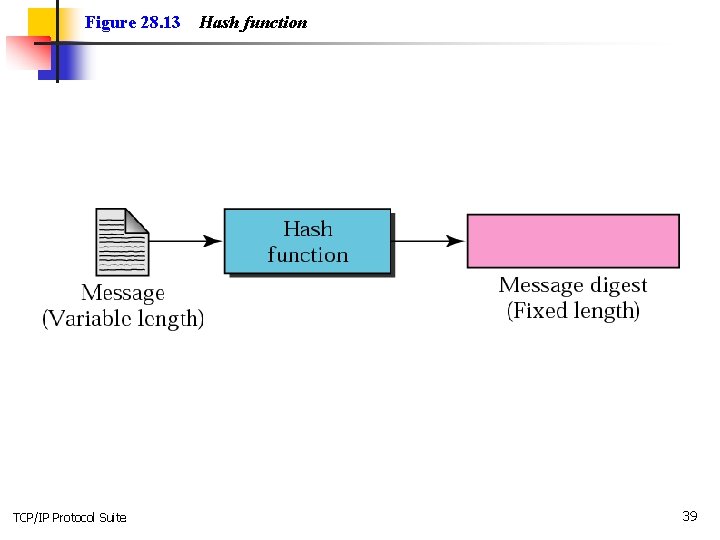
Figure 28. 13 TCP/IP Protocol Suite Hash function 39

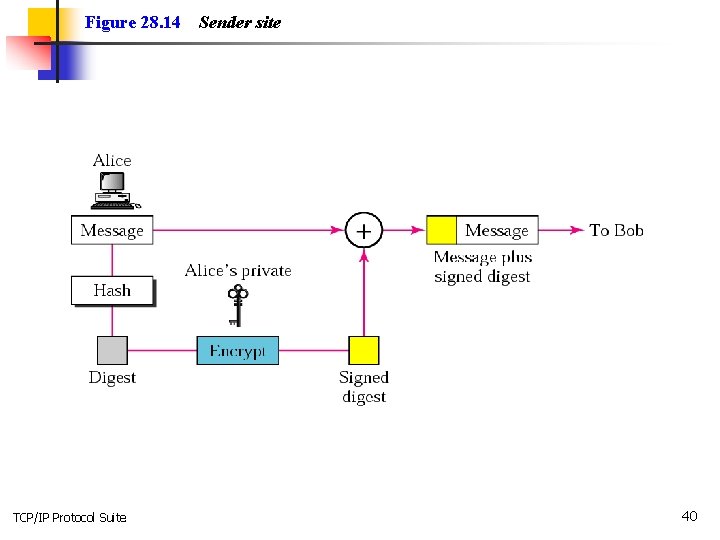
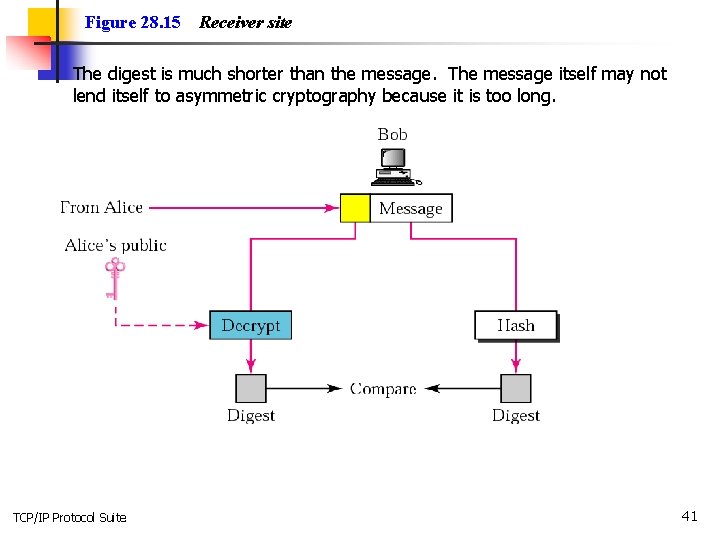
Figure 28. 14 TCP/IP Protocol Suite Sender site 40

Figure 28. 15 n Receiver site The digest is much shorter than the message. The message itself may not lend itself to asymmetric cryptography because it is too long. TCP/IP Protocol Suite 41

Hash functions n n n Message of arbitrary length is made into a fixed length message. MD 2, MD 4, MD 5 SHA (Secure Hash Algorithm) developed by NIST. TCP/IP Protocol Suite 42

Non-repudiation n n If alice signs a message then denies it, the message can be verified. That means we have to keep the messages. A trusted center can be created. Alice send the digitally signed message to the trusted center who verifies it, saves a copy of the message, recreates the message with its own signature and send to bob. Bob can verify the trusted center’s public key. TCP/IP Protocol Suite 43

28. 5 KEY MANAGEMENT In this section we explain how symmetric keys are distributed and how public keys are certified. The topics discussed in this section include: Symmetric-Key Distribution Public-Key Certification Kerberos TCP/IP Protocol Suite 44

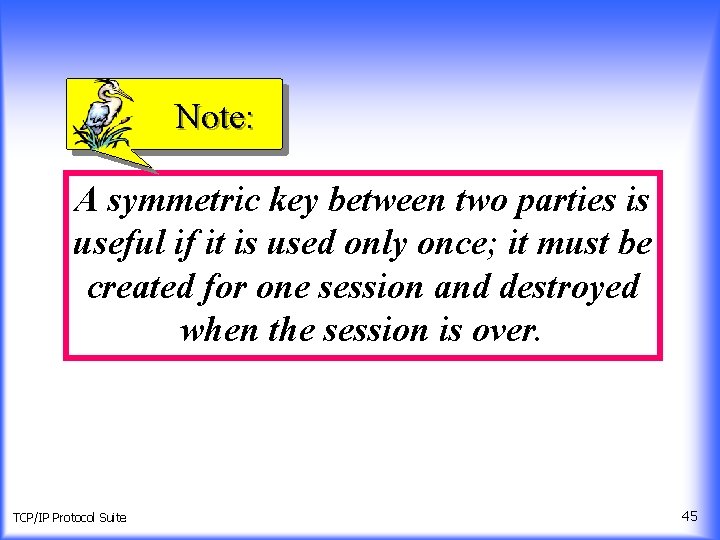
Note: A symmetric key between two parties is useful if it is used only once; it must be created for one session and destroyed when the session is over. TCP/IP Protocol Suite 45

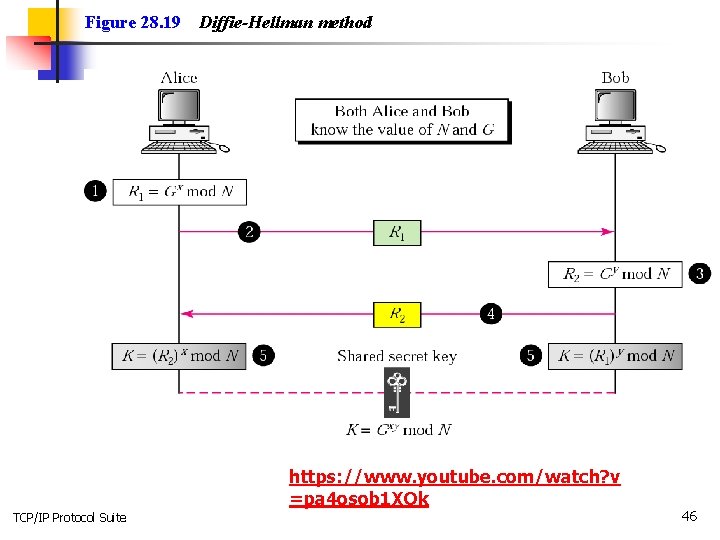
Figure 28. 19 Diffie-Hellman method https: //www. youtube. com/watch? v =pa 4 osob 1 XOk TCP/IP Protocol Suite 46

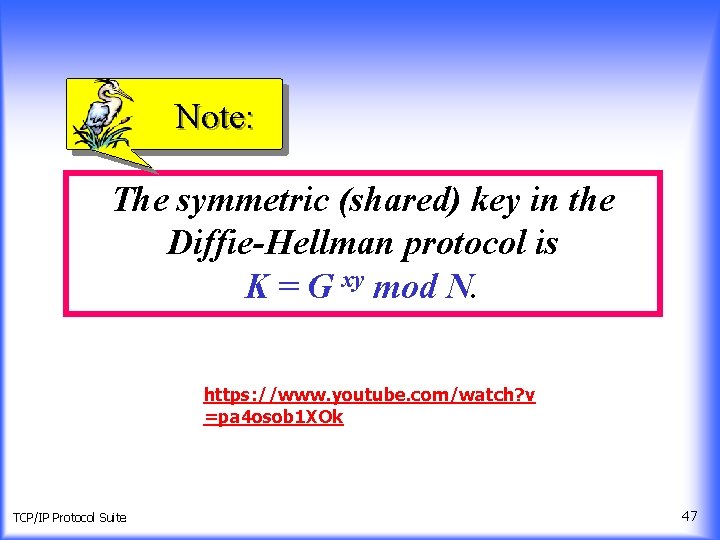
Note: The symmetric (shared) key in the Diffie-Hellman protocol is K = G xy mod N. https: //www. youtube. com/watch? v =pa 4 osob 1 XOk TCP/IP Protocol Suite 47

Example 1 Let us give an example to make the procedure clear. Our example uses small numbers, but note that in a real situation, the numbers are very large. Assume G = 7 and N = 23. The steps are as follows: 1. Alice chooses x = 3 and calculates R 1 = 73 mod 23 = 21. 2. Alice sends the number 21 to Bob. 3. Bob chooses y = 6 and calculates R 2 = 76 mod 23 = 4. 4. Bob sends the number 4 to Alice. 5. Alice calculates the symmetric key K = 43 mod 23 = 18. 6. Bob calculates the symmetric key K = 216 mod 23 = 18. The value of K is the same for both Alice and Bob; G = 18. TCP/IP Protocol Suite xy mod N = 718 mod 23 48

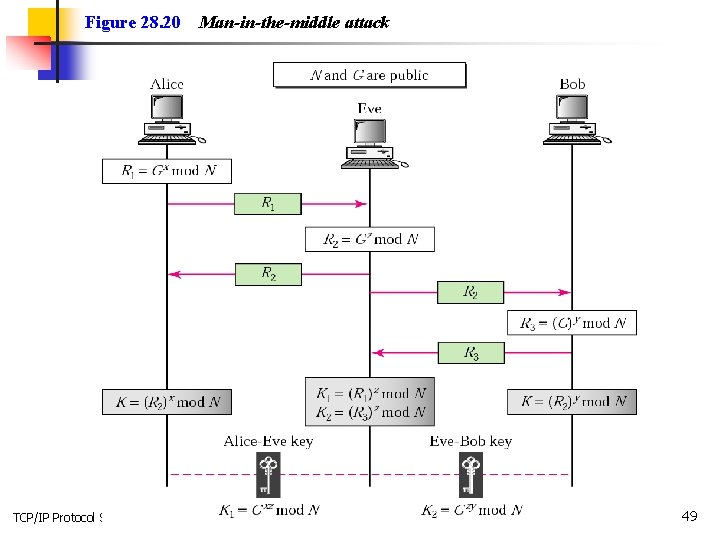
Figure 28. 20 TCP/IP Protocol Suite Man-in-the-middle attack 49

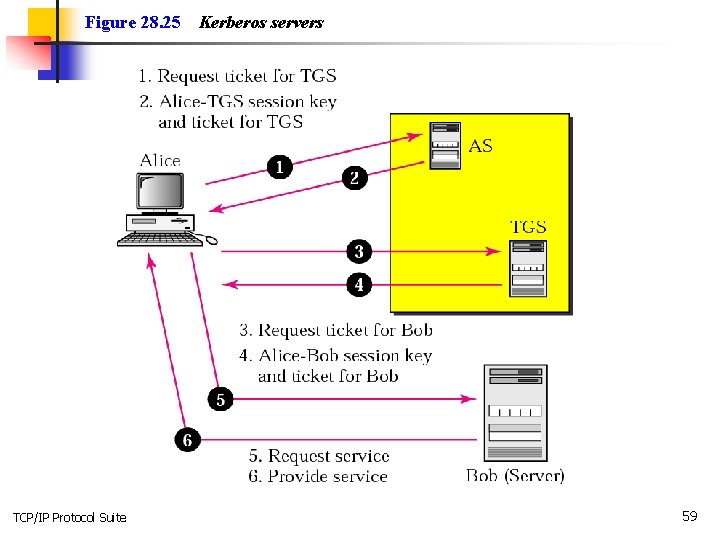
Key distribution center A typical operation with a KDC involves a request from a user to use some service. The KDC will use cryptographic techniques to authenticate requesting users as themselves. It will also check whether an individual user has the right to access the service requested. If the authenticated user meets all prescribed conditions, the KDC can issue a ticket permitting access. KDCs mostly operate with symmetric encryption. In most (but not all) cases the KDC shares a key with each of all the other parties. The KDC produces a ticket based on a server key. The client receives the ticket and submits it to the appropriate server. The server can verify the submitted ticket and grant access to the user submitting it. Security systems using KDCs include Kerberos. (Actually, Kerberos partitions KDC functionality between two different agents: the AS (Authentication Server) and the TGS (Ticket Granting Service). ) https: //www. youtube. com/watch? v =u 7 MQo. SN 19 O 4 TCP/IP Protocol Suite 50

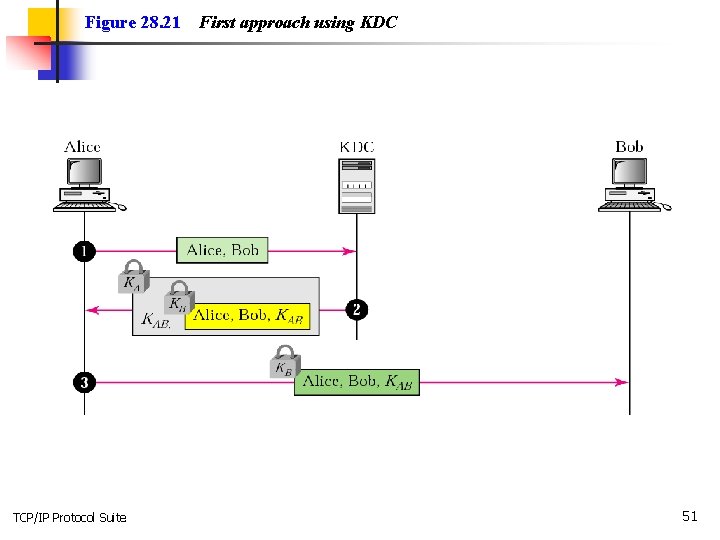
Figure 28. 21 TCP/IP Protocol Suite First approach using KDC 51

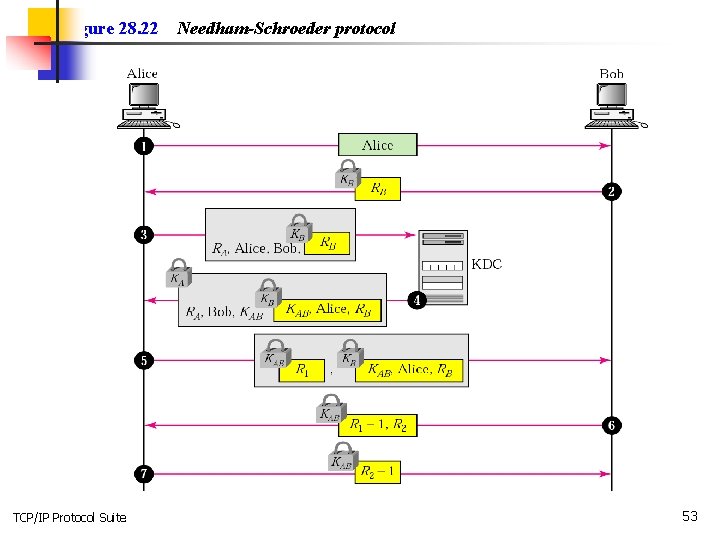
Needham–Schroeder protocol The term Needham–Schroeder protocol can refer to one of the two communication protocols intended for use over an insecure network, both proposed by Roger Needham and Michael Schroeder. [1] These are: The Needham–Schroeder Symmetric Key Protocol is based on a symmetric encryption algorithm. It forms the basis for the Kerberos protocol. This protocol aims to establish a session key between two parties on a network, typically to protect further communication. The Needham–Schroeder Public-Key Protocol, based on public-key cryptography. This protocol is intended to provide mutual authentication between two parties communicating on a network, but in its proposed form is insecure. https: //www. youtube. com/watch? v =QLHd 44 L 8 A_E&t=37 s TCP/IP Protocol Suite 52

Figure 28. 22 TCP/IP Protocol Suite Needham-Schroeder protocol 53

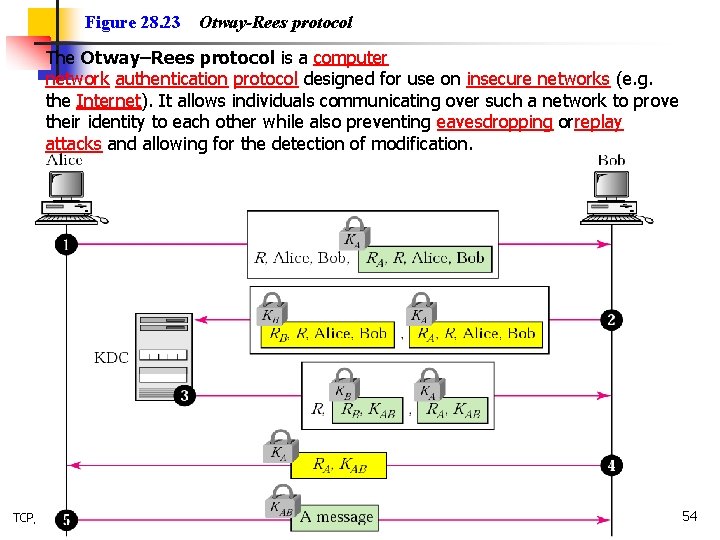
Figure 28. 23 Otway-Rees protocol The Otway–Rees protocol is a computer network authentication protocol designed for use on insecure networks (e. g. the Internet). It allows individuals communicating over such a network to prove their identity to each other while also preventing eavesdropping orreplay attacks and allowing for the detection of modification. TCP/IP Protocol Suite 54

Note: In public-key cryptography, everyone has access to everyone’s public key. TCP/IP Protocol Suite 55

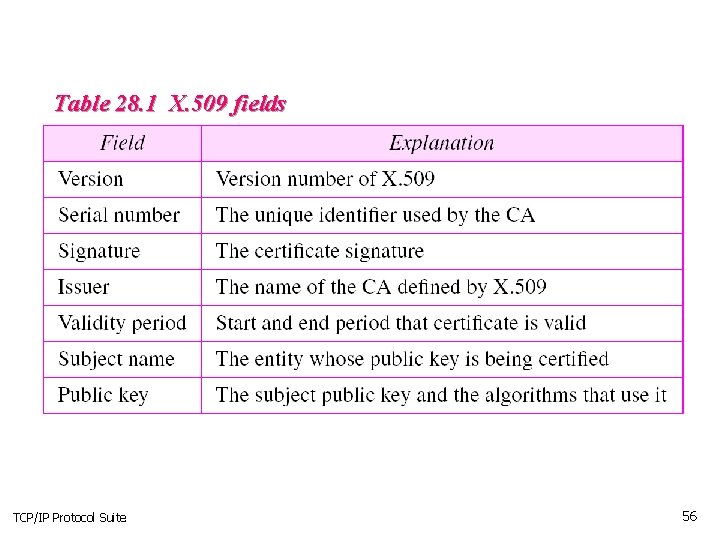
Table 28. 1 X. 509 fields TCP/IP Protocol Suite 56

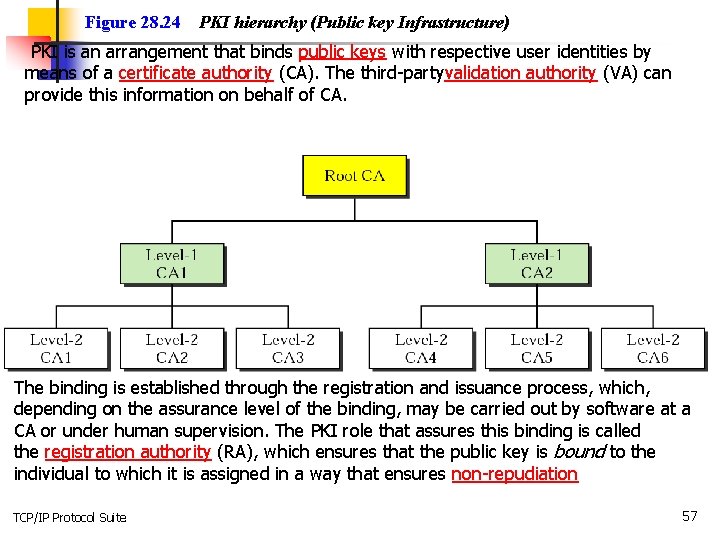
Figure 28. 24 PKI hierarchy (Public key Infrastructure) PKI is an arrangement that binds public keys with respective user identities by means of a certificate authority (CA). The third-partyvalidation authority (VA) can provide this information on behalf of CA. The binding is established through the registration and issuance process, which, depending on the assurance level of the binding, may be carried out by software at a CA or under human supervision. The PKI role that assures this binding is called the registration authority (RA), which ensures that the public key is bound to the individual to which it is assigned in a way that ensures non-repudiation TCP/IP Protocol Suite 57

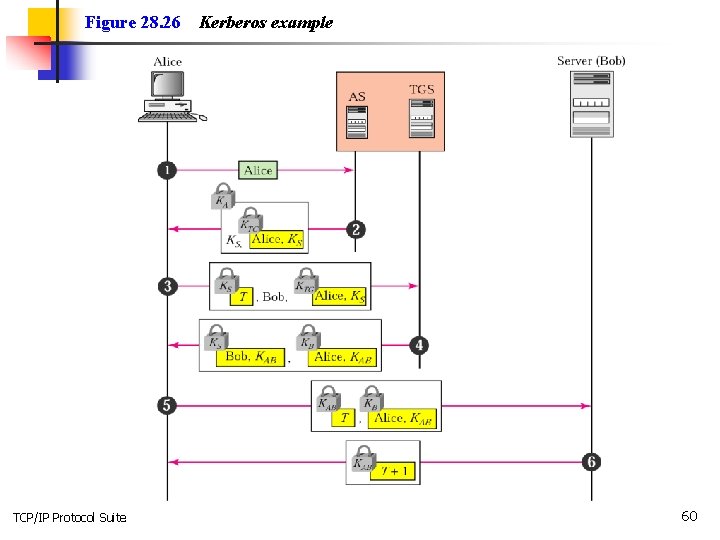
Kerberos a computer network authentication protocol which works on the basis of 'tickets' to allow nodes communicating over a non-secure network to prove their identity to one another in a secure manner. Its designers aimed it primarily at a client–server model and it provides mutual authentication—both the user and the server verify each other's identity. Kerberos protocol messages are protected against eavesdroppingand replay attacks. Kerberos builds on symmetric key cryptography and requires a trusted third party, and optionally may use public-key cryptography during certain phases of authentication. https: //www. youtube. com/watch? v =u 7 MQo. SN 19 O 4 TCP/IP Protocol Suite 58

Figure 28. 25 TCP/IP Protocol Suite Kerberos servers 59

Figure 28. 26 TCP/IP Protocol Suite Kerberos example 60

28. 6 SECURITY IN THE INTERNET In this section we discuss a security method for each of the top 3 layers of the Internet model. At the IP level we discuss a protocol called IPSec; at the transport layer we discuss a protocol that “glues” a new layer to the transport layer; at the application layer we discuss a security method called PGP. The topics discussed in this section include: IP Level Security: IPSec Transport Layer Security Application Layer Security: PGP TCP/IP Protocol Suite 61

Internet Protocol Security (IPsec) is a protocol suite for securing Internet Protocol (IP) communications by authenticating and encrypting each IP packet of a communication session. IPsec includes protocols for establishing mutual authentication between agents at the beginning of the session and negotiation of cryptographic keys to be used during the session. IPsec can be used in protecting data flows between a pair of hosts (host-tohost), between a pair of security gateways (network-to-network), or between a security gateway and a host (network-to-host). [1] Internet Protocol security (IPsec) uses cryptographic security services to protect communications over Internet Protocol (IP) networks. IPsec supports network-level peer authentication, data origin authentication, data integrity, data confidentiality (encryption), and replay protection. IPsec is an end-to-end security scheme operating in the Internet Layer of the Internet Protocol Suite, while some other Internet security systems in widespread use, such as Transport Layer Security (TLS) and Secure Shell(SSH), operate in the upper layers of the TCP/IP model. Hence, IPsec protects any application traffic across an IP network. Applications do not need to be specifically designed to use IPsec. Without IPsec, the use of TLS/SSL must be designed into an application to protect the application protocols. TCP/IP Protocol Suite 62

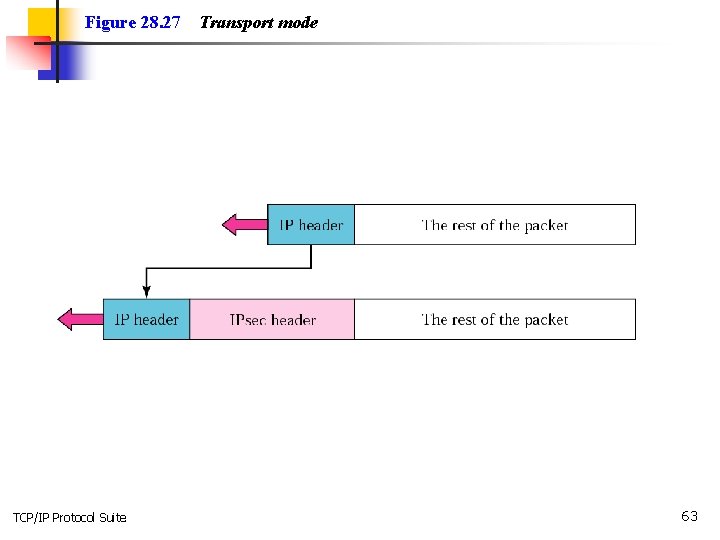
Figure 28. 27 TCP/IP Protocol Suite Transport mode 63

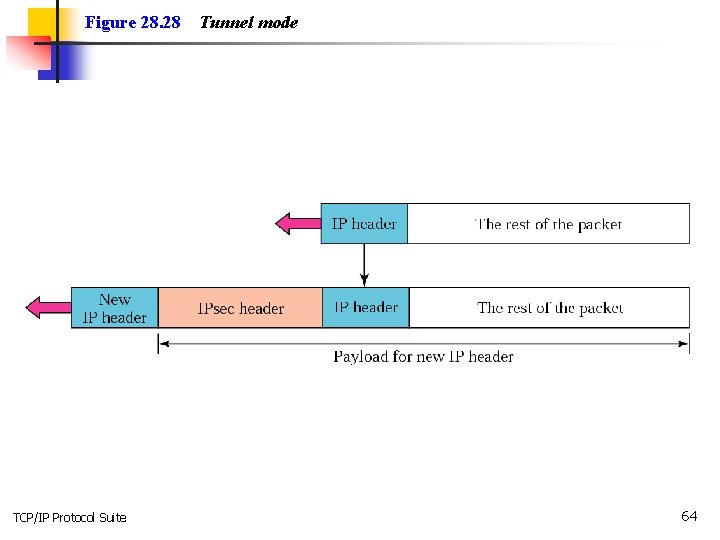
Figure 28. 28 TCP/IP Protocol Suite Tunnel mode 64

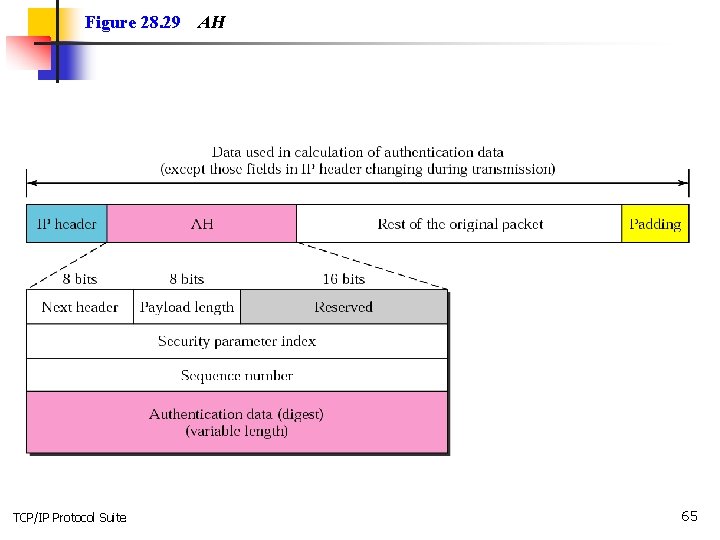
Figure 28. 29 TCP/IP Protocol Suite AH 65

Note: The AH protocol provides message authentication and integrity, but not privacy. TCP/IP Protocol Suite 66

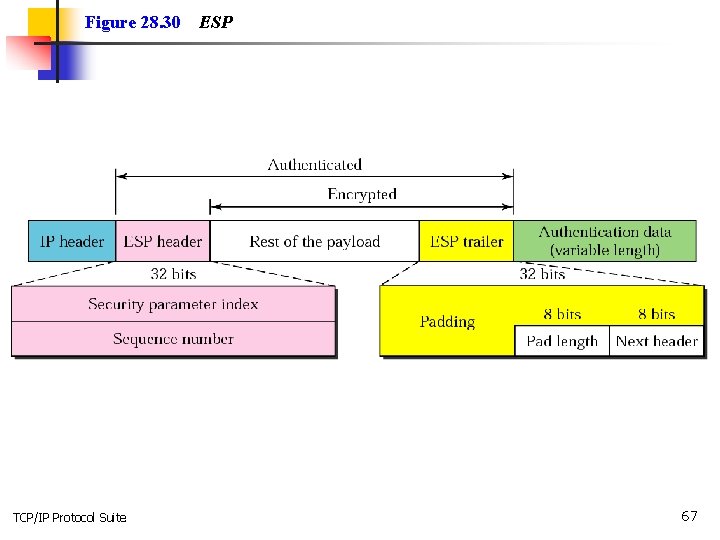
Figure 28. 30 TCP/IP Protocol Suite ESP 67

Note: ESP provides message authentication, integrity, and privacy. TCP/IP Protocol Suite 68

Figure 28. 31 TCP/IP Protocol Suite Position of TLS 69

Figure 28. 32 TCP/IP Protocol Suite TLS layers 70

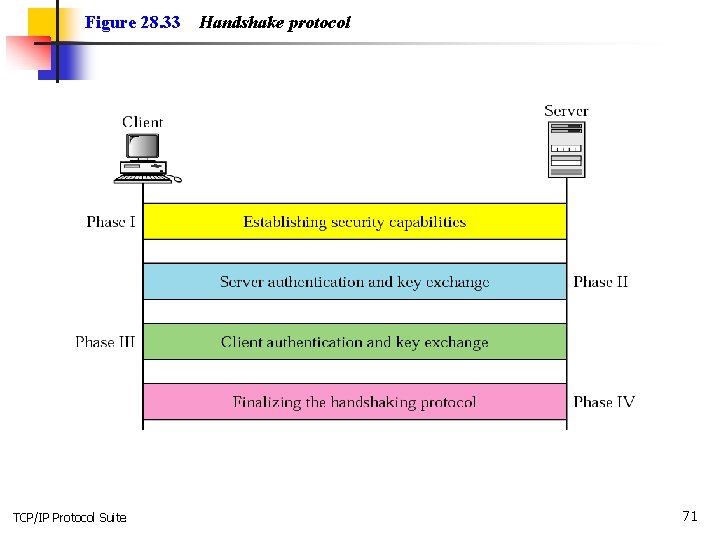
Figure 28. 33 TCP/IP Protocol Suite Handshake protocol 71

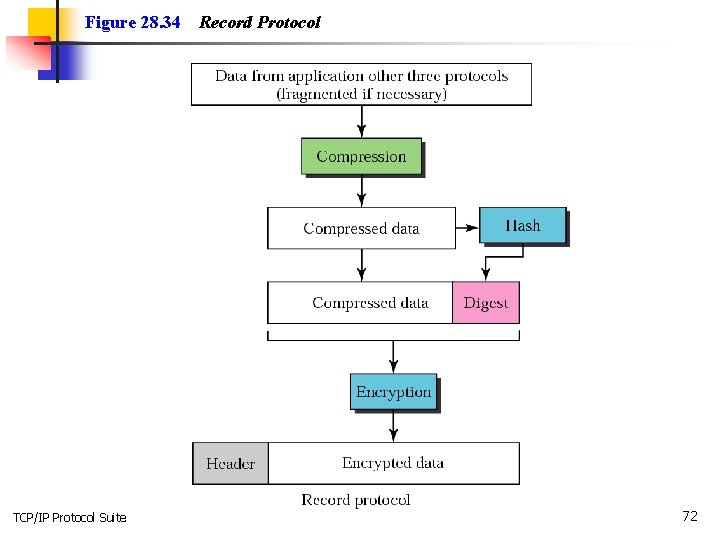
Figure 28. 34 TCP/IP Protocol Suite Record Protocol 72

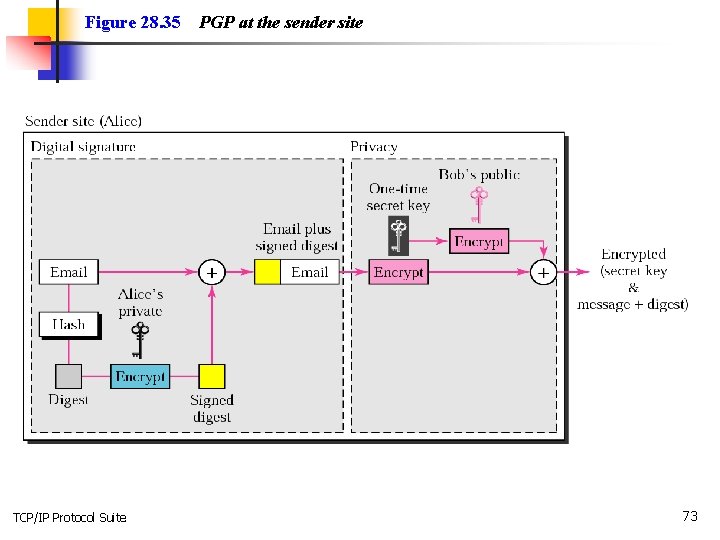
Figure 28. 35 TCP/IP Protocol Suite PGP at the sender site 73

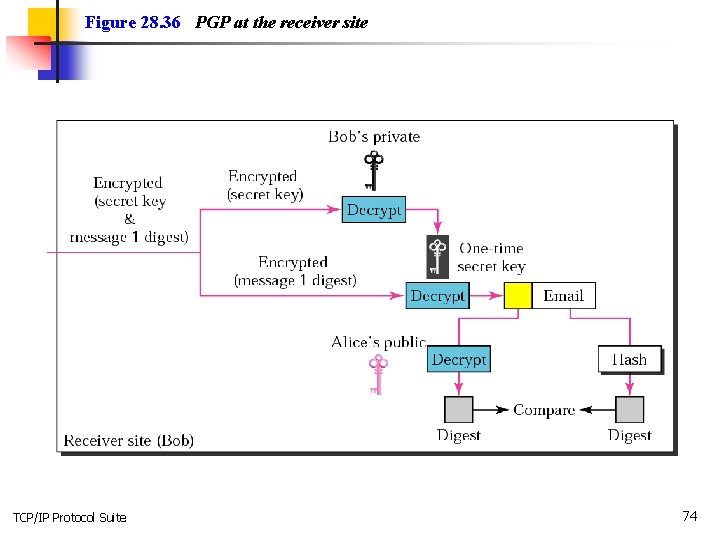
Figure 28. 36 PGP at the receiver site TCP/IP Protocol Suite 74

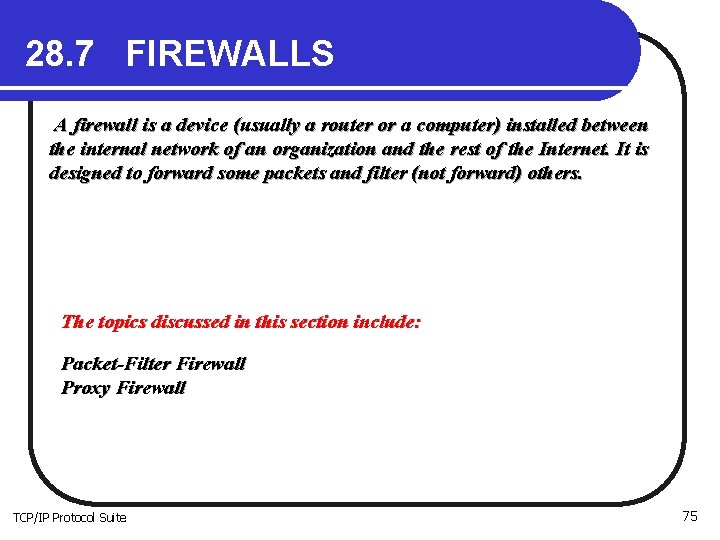
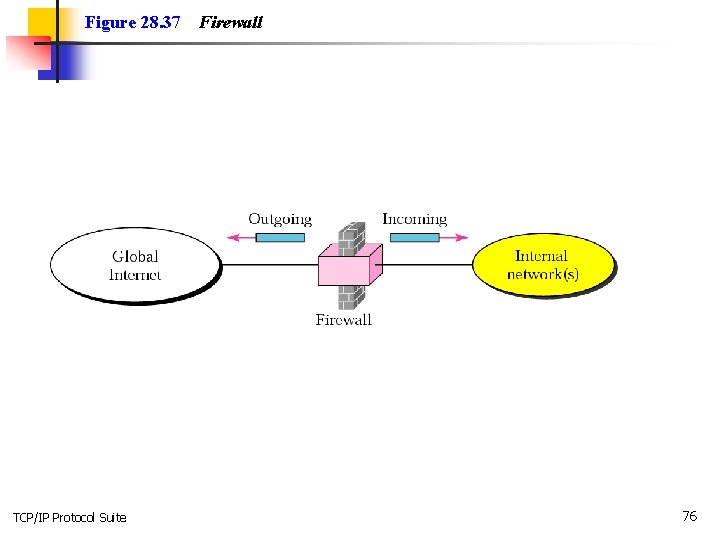
28. 7 FIREWALLS A firewall is a device (usually a router or a computer) installed between the internal network of an organization and the rest of the Internet. It is designed to forward some packets and filter (not forward) others. The topics discussed in this section include: Packet-Filter Firewall Proxy Firewall TCP/IP Protocol Suite 75

Figure 28. 37 TCP/IP Protocol Suite Firewall 76

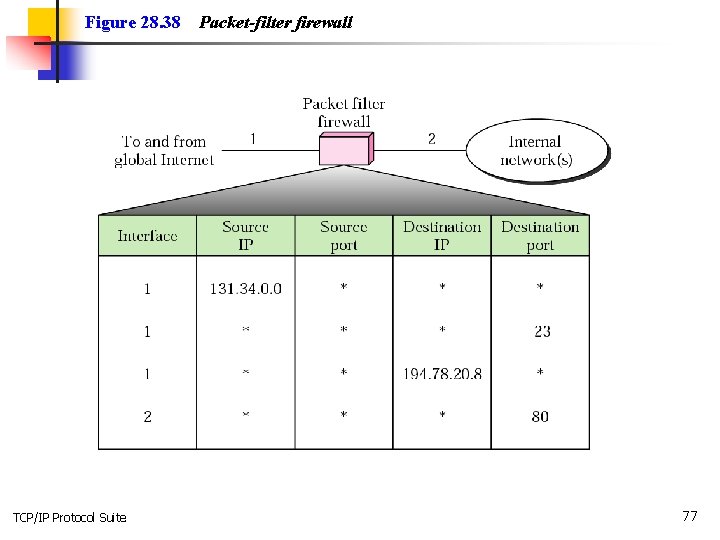
Figure 28. 38 TCP/IP Protocol Suite Packet-filter firewall 77

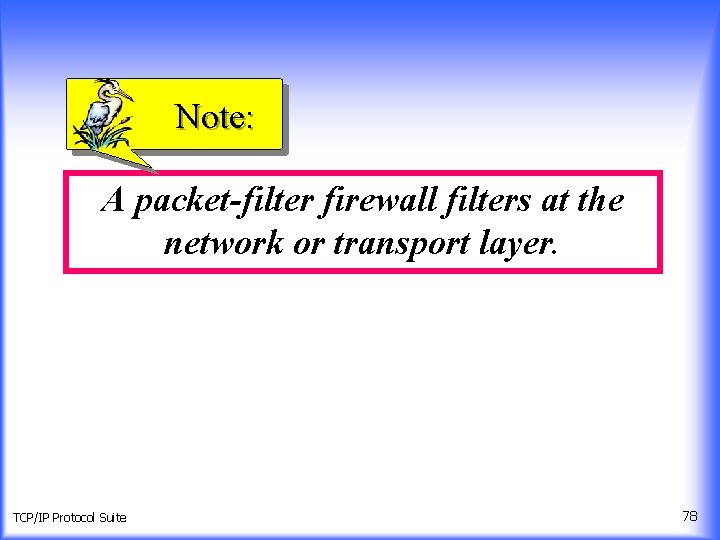
Note: A packet-filter firewall filters at the network or transport layer. TCP/IP Protocol Suite 78

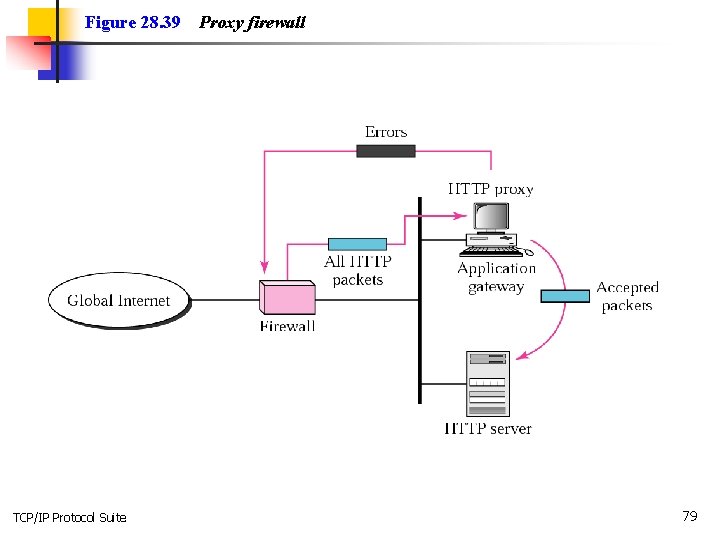
Figure 28. 39 TCP/IP Protocol Suite Proxy firewall 79

Note: A proxy firewall filters at the application layer. TCP/IP Protocol Suite 80