Chapter 30 Security Credit most slides from Forouzan


















- Slides: 62

Chapter 30 Security Credit: most slides from Forouzan, TCP/IP protocol suit TCP/IP Protocol Suite 1

Criminal Expoits and Attacks n n Phishing: Masquerading as a well-known site to obtain a user’ personal info. Denial of Service: Intentionally blocking a site to prevent business activities. Loss of control: an intruder gains control of a system. Loss of data: Steal or delete. TCP/IP Protocol Suite 2

Techniques used n n n n n Wiretapping Replay – sending packets captured from previous session such as username and password. Buffer overflow: sending more data than receiver expects, thereby storing values in memory buffer. Address spoofing. Faking IP source address Name spoofing. Misspelling of a well-known name or poisoning name server. SYN flood – sending stream of TCP SYN Key breaking – guessing password Port Scanning – to find vulnerability Packet Interception – man in the middle attack. TCP/IP Protocol Suite 3

Security Techniques n n n Encryption Digital Signatures Firewall Intrusion detection systems Packet inspection and content scanning VPN TCP/IP Protocol Suite 4

28. 1 CRYPTOGRAPHY The word cryptography in Greek means “secret writing. ” The term today refers to the science and art of transforming messages to make them secure and immune to attacks. The topics discussed in this section include: Symmetric-Key Cryptography Asymmetric-Key Cryptography Comparison TCP/IP Protocol Suite 5

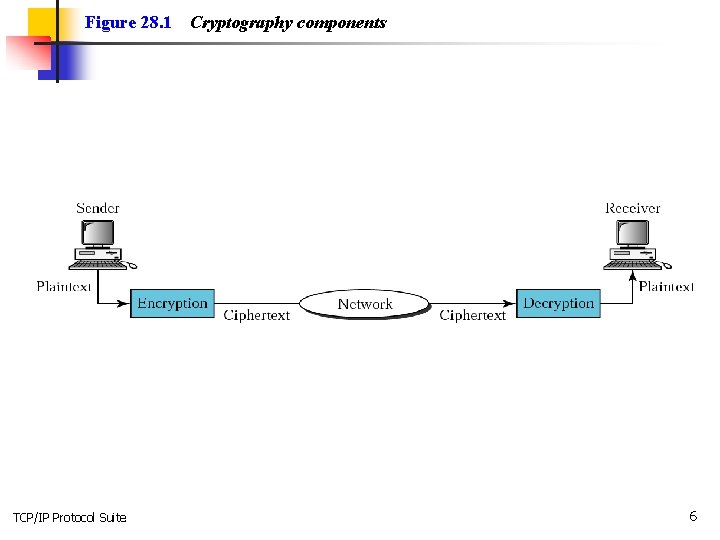
Figure 28. 1 TCP/IP Protocol Suite Cryptography components 6

Note: In cryptography, the encryption/decryption algorithms are public; the keys are secret. TCP/IP Protocol Suite 7

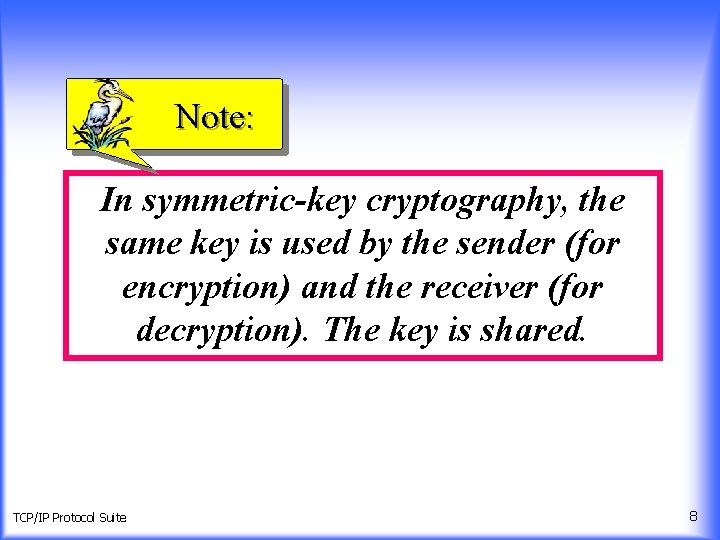
Note: In symmetric-key cryptography, the same key is used by the sender (for encryption) and the receiver (for decryption). The key is shared. TCP/IP Protocol Suite 8

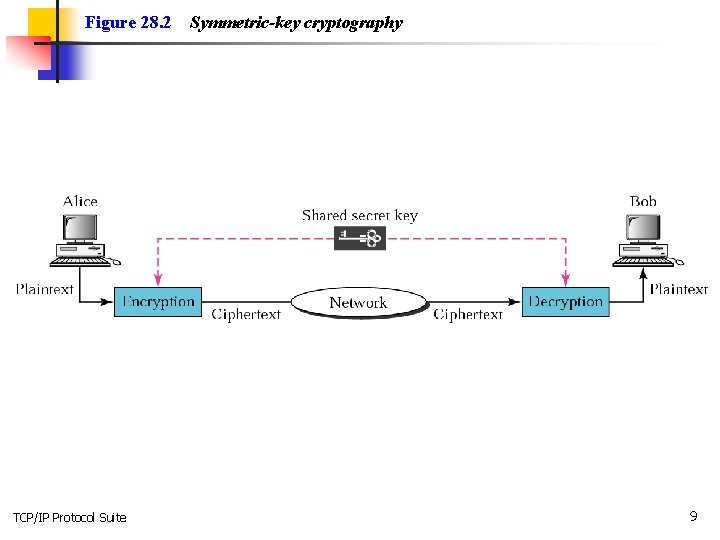
Figure 28. 2 TCP/IP Protocol Suite Symmetric-key cryptography 9

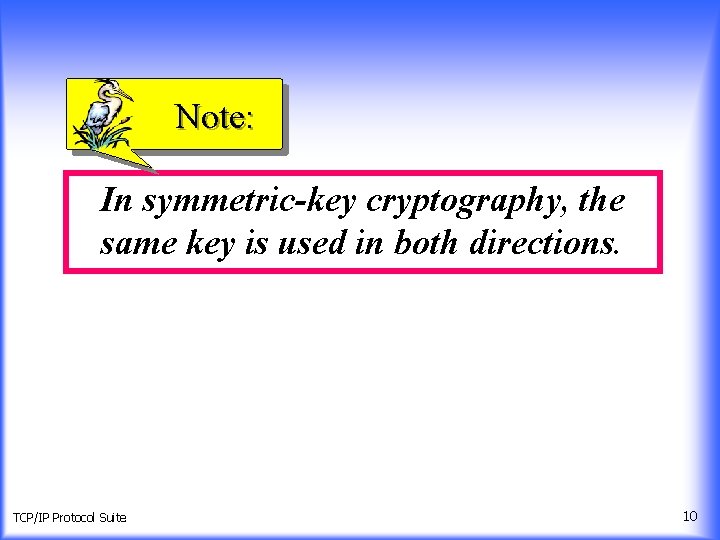
Note: In symmetric-key cryptography, the same key is used in both directions. TCP/IP Protocol Suite 10

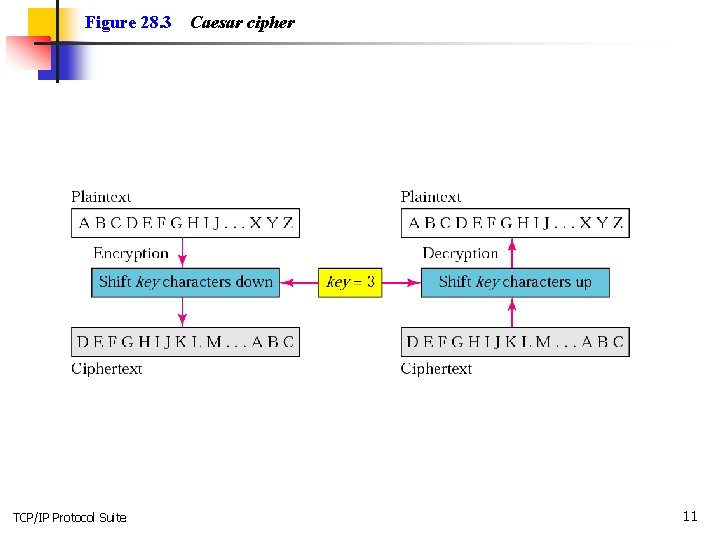
Figure 28. 3 TCP/IP Protocol Suite Caesar cipher 11

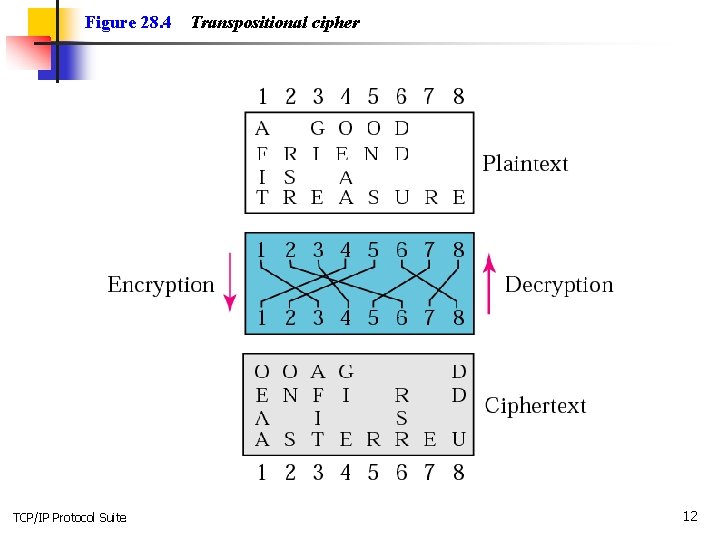
Figure 28. 4 TCP/IP Protocol Suite Transpositional cipher 12

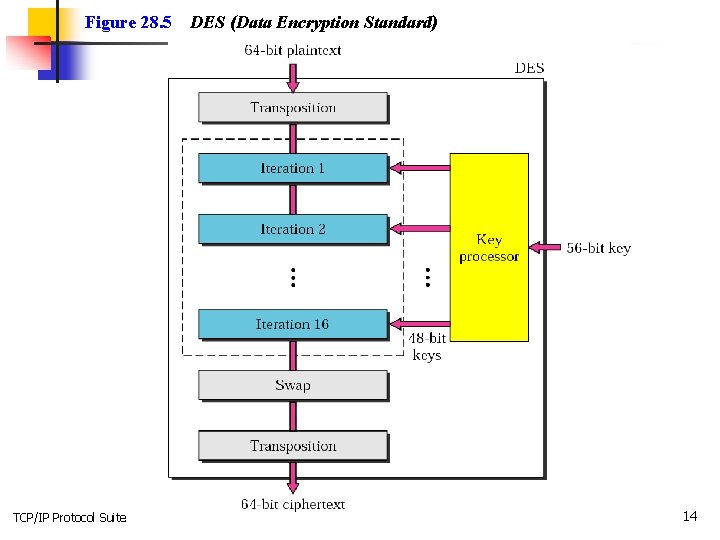
Data encryption Standard (DES) n n n Is a block cipher Takes 64 -bit plaintext and creates a 64 -bit ciphertext. The cipher key is a 56 -bit key. It uses 16 rounds, each round mixes and swapps (left half with right half) TCP/IP Protocol Suite 13

Figure 28. 5 TCP/IP Protocol Suite DES (Data Encryption Standard) 14

Note: The DES cipher uses the same concept as the Caesar cipher, but the encryption/ decryption algorithm is much more complex. TCP/IP Protocol Suite 15

Asymmetric-key ciphers n n The secret key is personal and unshared. Symmetric key scheme would require n(n-1)/2 keys, for a million people it would require half a billion shared secret keys. Whereas, in asymmetric scheme we would only require a million secret keys. Asymmetric ciphers use two keys, private and public. Asymmetric is much slower. Both symmetric and asymmetric can be used if need to be. Think: if you want to send a secret symmetric key, you can use asymmetric. TCP/IP Protocol Suite 16

Protocols n n IPSec (internet Security Protocol) operates in the network layer. Used in VPN. n IP sec supports Authentication Header (AH) protocol and Encapsulation Security Payload (ESP) protocol The SSL (Secure Socket Layer) protocol serves as a security for transferring encrypted data. WEP (Wired Equivalent Privacy) standard. Data stream is encrypted with RC 4 algorithm. RC 4 is simple, it is not very secure. WPA (Wi-Fi Protected Access) specification and AES (Advanced Encryption standard) more secure for encrypting wireless data. TCP/IP Protocol Suite 17

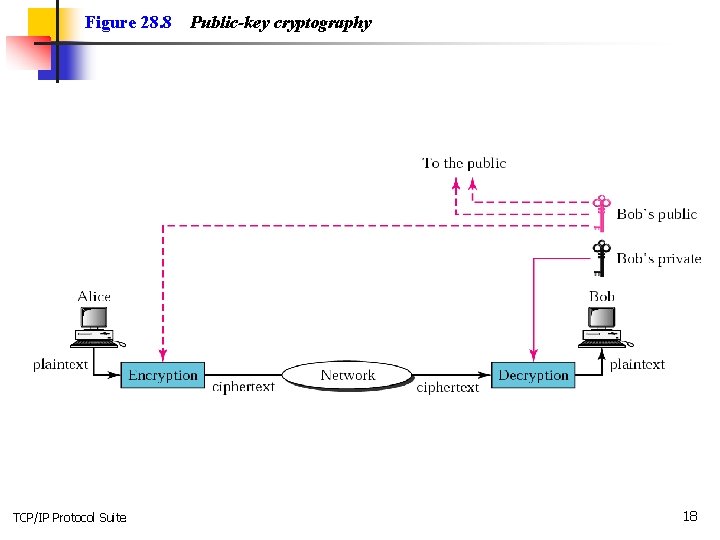
Figure 28. 8 TCP/IP Protocol Suite Public-key cryptography 18

Note: Symmetric-key cryptography is often used for long messages. TCP/IP Protocol Suite 19

Note: Asymmetric-key algorithms are more efficient for short messages. TCP/IP Protocol Suite 20

Note: Digital signature can provide authentication, integrity, and nonrepudiation for a message. TCP/IP Protocol Suite 21

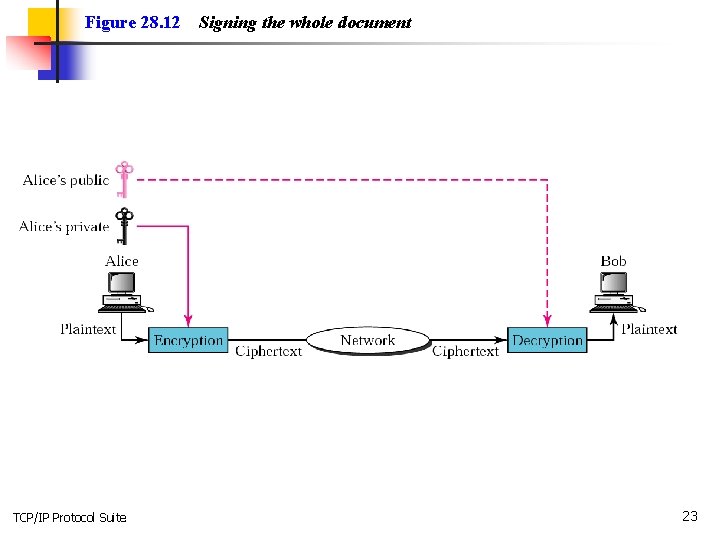
28. 3 DIGITAL SIGNATURE Digital signature can provide nonrepudiation for a message. authentication, integrity, and The topics discussed in this section include: Signing the Whole Document Signing the Digest TCP/IP Protocol Suite 22

Figure 28. 12 TCP/IP Protocol Suite Signing the whole document 23

Note: Digital signature does not provide privacy. If there is a need for privacy, another layer of encryption/decryption must be applied. TCP/IP Protocol Suite 24

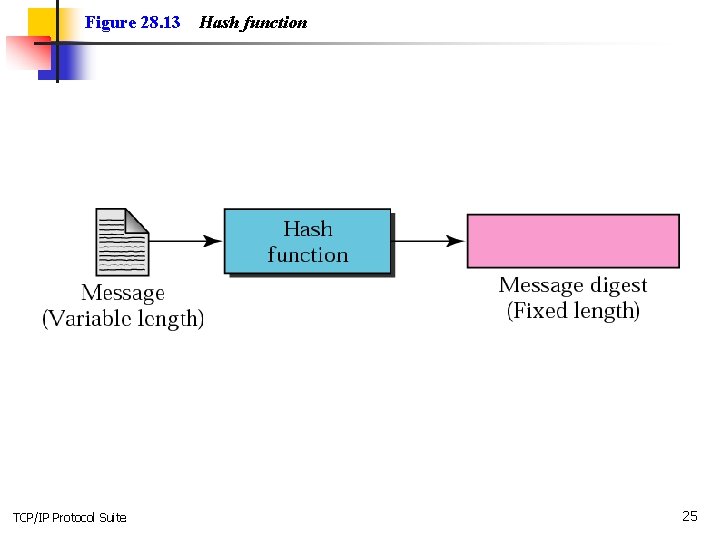
Figure 28. 13 TCP/IP Protocol Suite Hash function 25

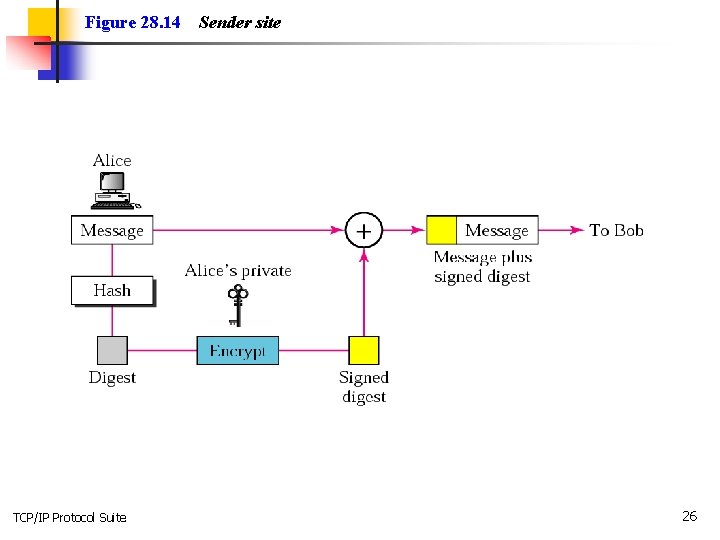
Figure 28. 14 TCP/IP Protocol Suite Sender site 26

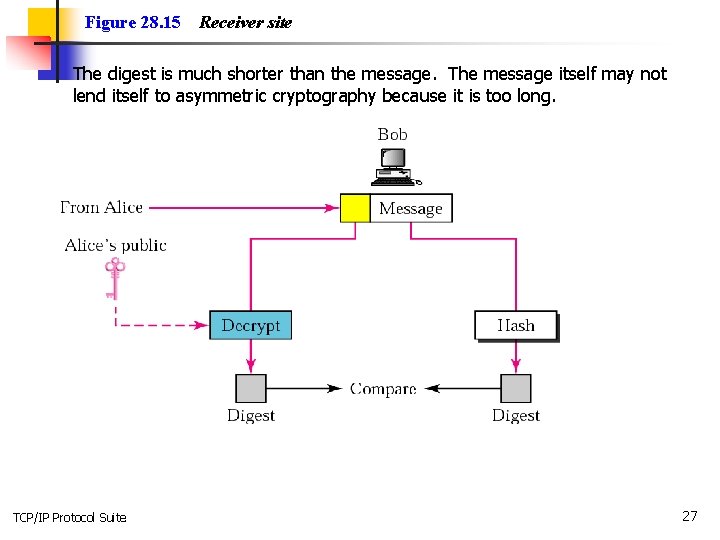
Figure 28. 15 n Receiver site The digest is much shorter than the message. The message itself may not lend itself to asymmetric cryptography because it is too long. TCP/IP Protocol Suite 27

Hash functions n n n Message of arbitrary length is made into a fixed length message. MD 2, MD 4, MD 5 SHA (Secure Hash Algorithm) developed by NIST. TCP/IP Protocol Suite 28

Non-repudiation n n If alice signs a message then denies it, the message can be verified. That means we have to keep the messages. A trusted center can be created. Alice send the digitally signed message to the trusted center who verifies it, saves a copy of the message, recreates the message with its own signature and send to bob. Bob can verify the trusted center’s public key. TCP/IP Protocol Suite 29

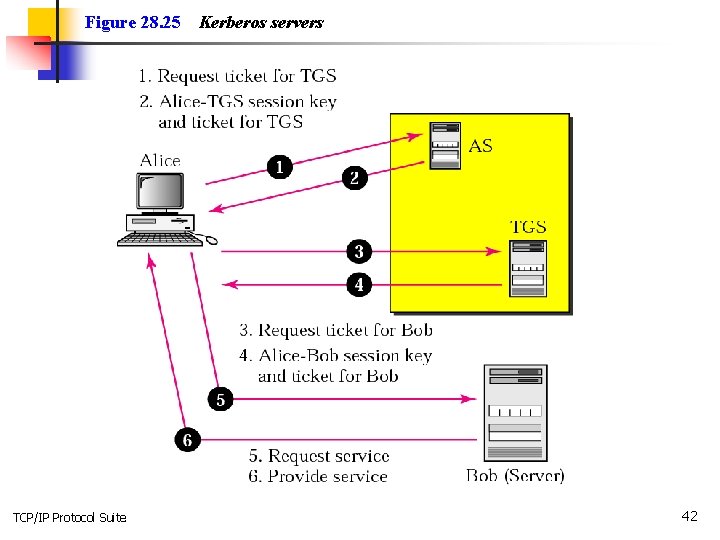
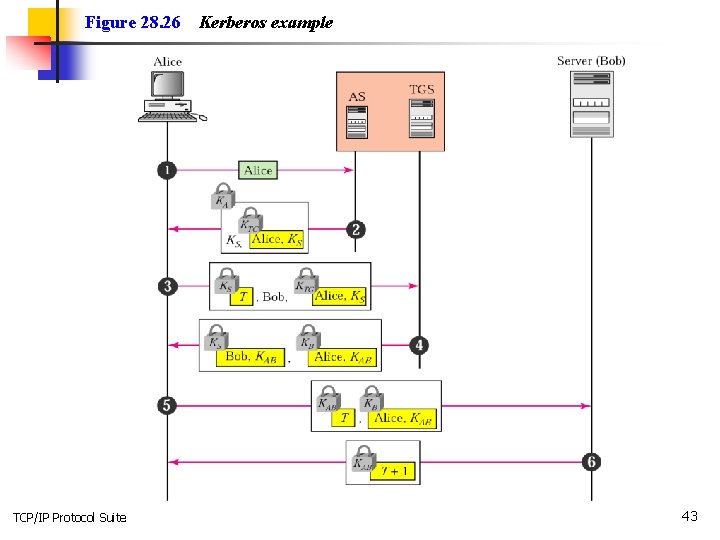
28. 5 KEY MANAGEMENT In this section we explain how symmetric keys are distributed and how public keys are certified. The topics discussed in this section include: Symmetric-Key Distribution Public-Key Certification Kerberos TCP/IP Protocol Suite 30

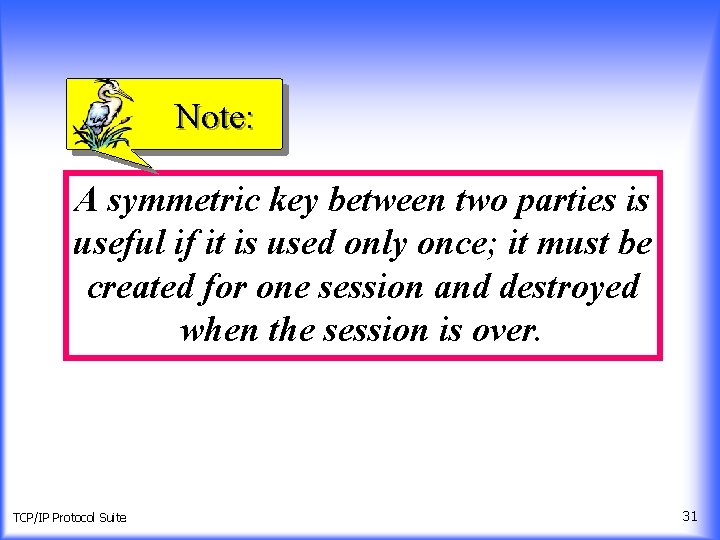
Note: A symmetric key between two parties is useful if it is used only once; it must be created for one session and destroyed when the session is over. TCP/IP Protocol Suite 31

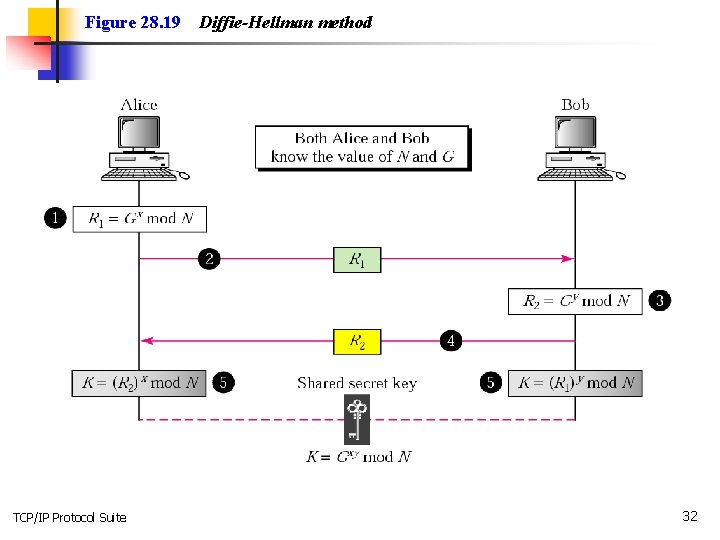
Figure 28. 19 TCP/IP Protocol Suite Diffie-Hellman method 32

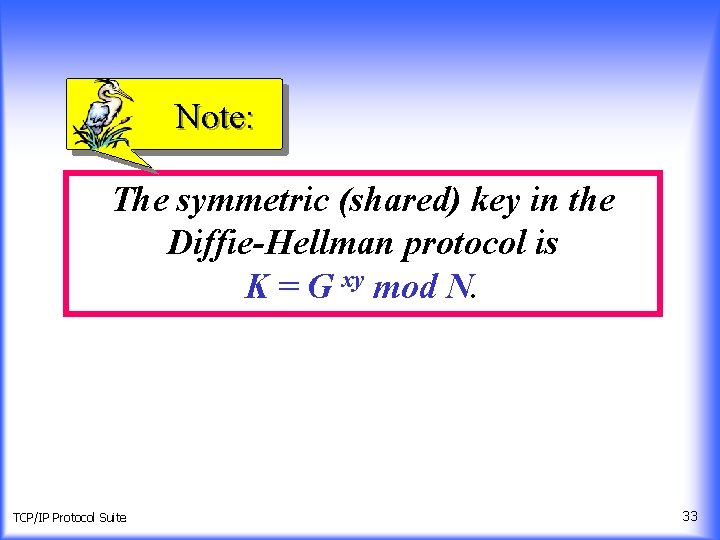
Note: The symmetric (shared) key in the Diffie-Hellman protocol is K = G xy mod N. TCP/IP Protocol Suite 33

Example 1 Let us give an example to make the procedure clear. Our example uses small numbers, but note that in a real situation, the numbers are very large. Assume G = 7 and N = 23. The steps are as follows: 1. Alice chooses x = 3 and calculates R 1 = 73 mod 23 = 21. 2. Alice sends the number 21 to Bob. 3. Bob chooses y = 6 and calculates R 2 = 76 mod 23 = 4. 4. Bob sends the number 4 to Alice. 5. Alice calculates the symmetric key K = 43 mod 23 = 18. 6. Bob calculates the symmetric key K = 216 mod 23 = 18. The value of K is the same for both Alice and Bob; G = 18. TCP/IP Protocol Suite xy mod N = 718 mod 23 34

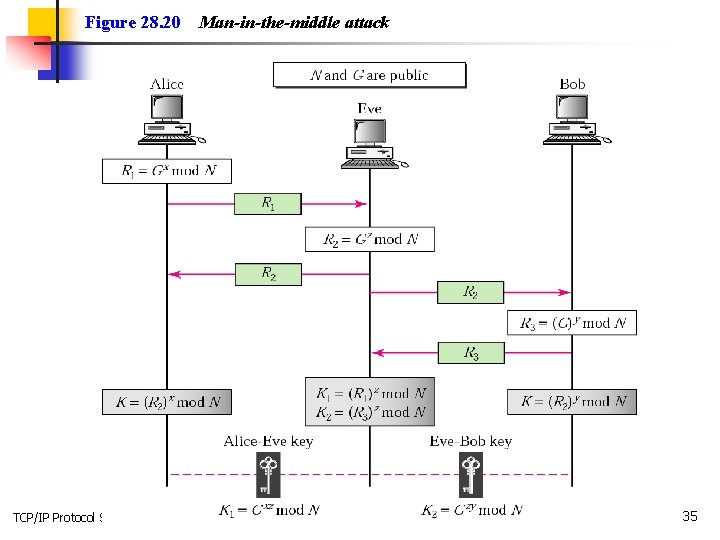
Figure 28. 20 TCP/IP Protocol Suite Man-in-the-middle attack 35

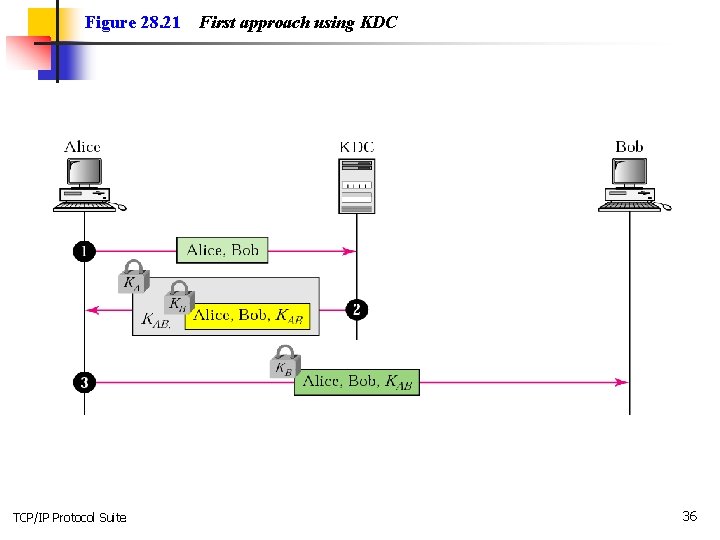
Figure 28. 21 TCP/IP Protocol Suite First approach using KDC 36

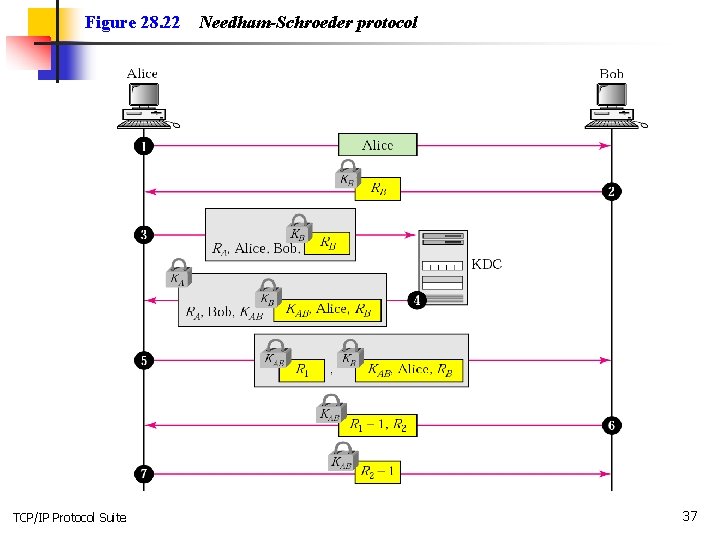
Figure 28. 22 TCP/IP Protocol Suite Needham-Schroeder protocol 37

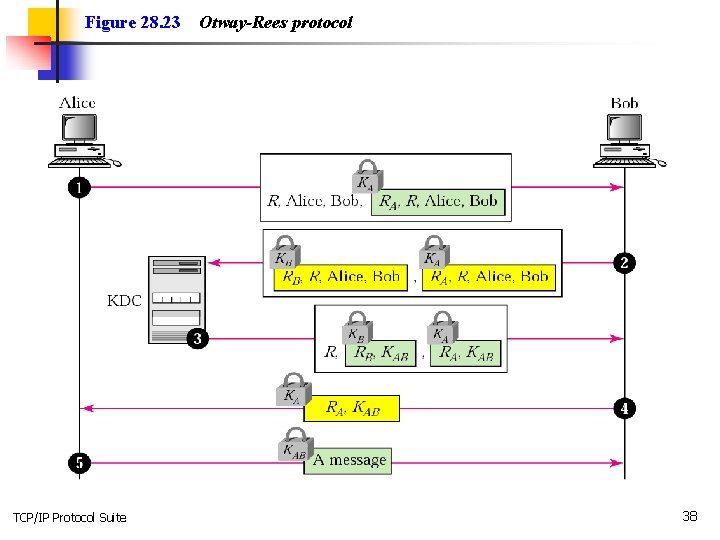
Figure 28. 23 TCP/IP Protocol Suite Otway-Rees protocol 38

Note: In public-key cryptography, everyone has access to everyone’s public key. TCP/IP Protocol Suite 39

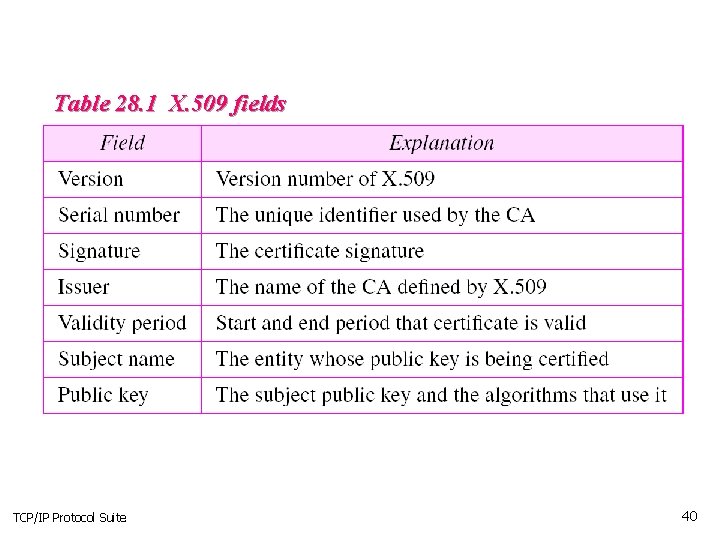
Table 28. 1 X. 509 fields TCP/IP Protocol Suite 40

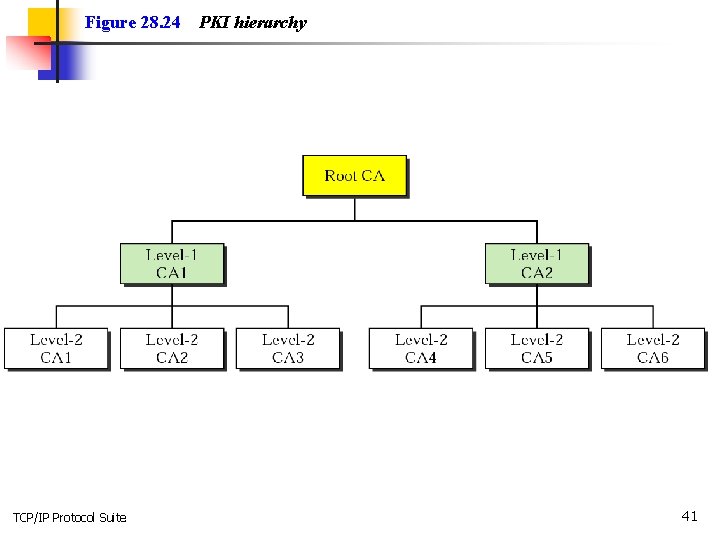
Figure 28. 24 TCP/IP Protocol Suite PKI hierarchy 41

Figure 28. 25 TCP/IP Protocol Suite Kerberos servers 42

Figure 28. 26 TCP/IP Protocol Suite Kerberos example 43

28. 6 SECURITY IN THE INTERNET In this section we discuss a security method for each of the top 3 layers of the Internet model. At the IP level we discuss a protocol called IPSec; at the transport layer we discuss a protocol that “glues” a new layer to the transport layer; at the application layer we discuss a security method called PGP. The topics discussed in this section include: IP Level Security: IPSec Transport Layer Security Application Layer Security: PGP TCP/IP Protocol Suite 44

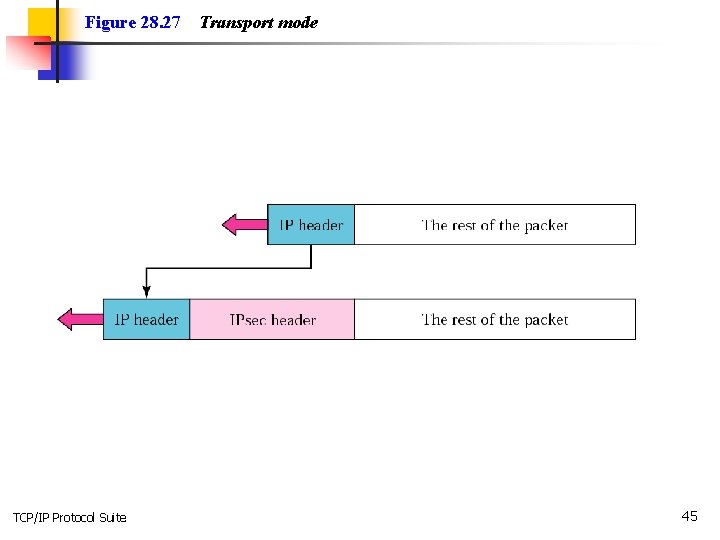
Figure 28. 27 TCP/IP Protocol Suite Transport mode 45

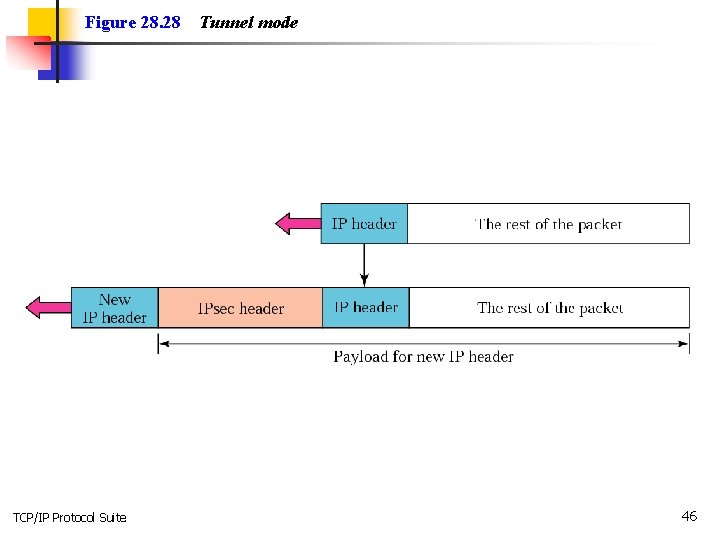
Figure 28. 28 TCP/IP Protocol Suite Tunnel mode 46

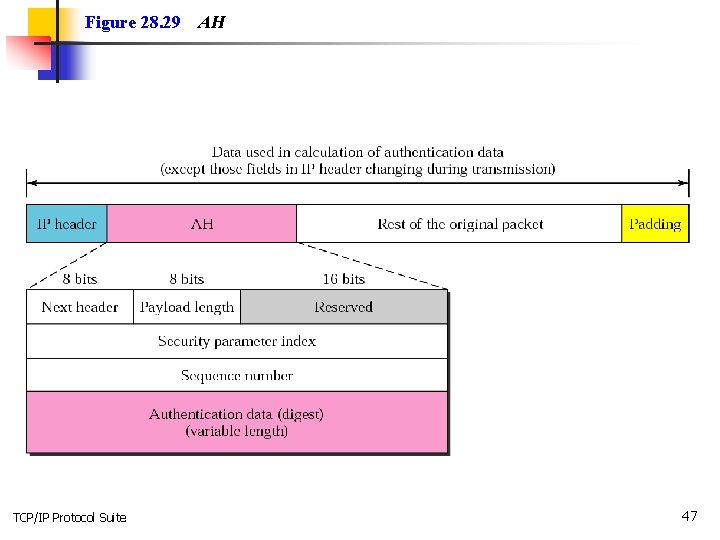
Figure 28. 29 TCP/IP Protocol Suite AH 47

Note: The AH protocol provides message authentication and integrity, but not privacy. TCP/IP Protocol Suite 48

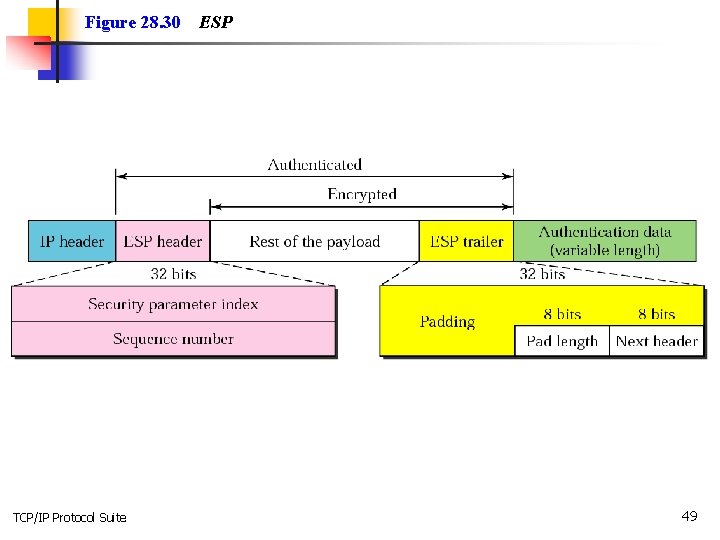
Figure 28. 30 TCP/IP Protocol Suite ESP 49

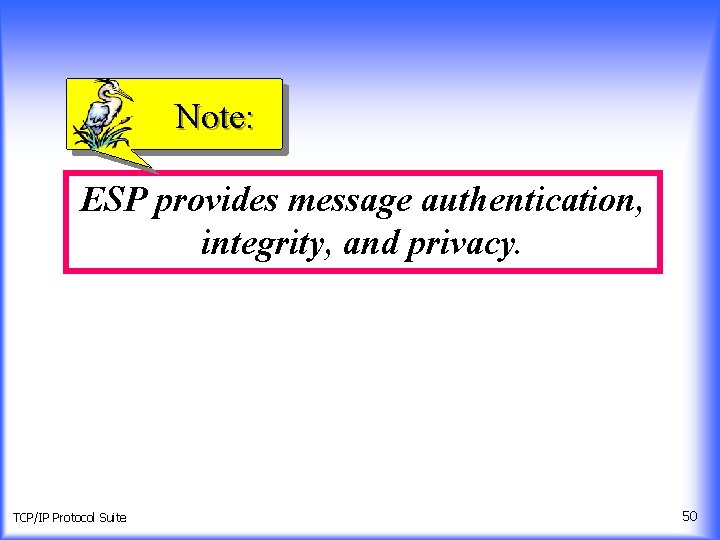
Note: ESP provides message authentication, integrity, and privacy. TCP/IP Protocol Suite 50

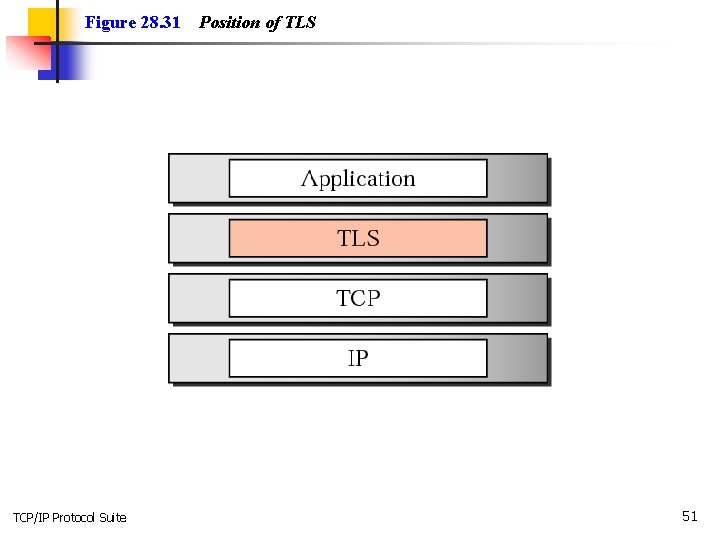
Figure 28. 31 TCP/IP Protocol Suite Position of TLS 51

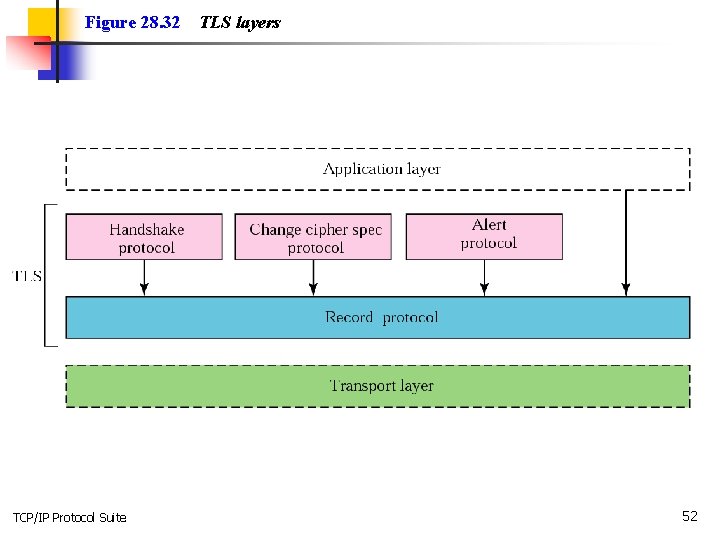
Figure 28. 32 TCP/IP Protocol Suite TLS layers 52

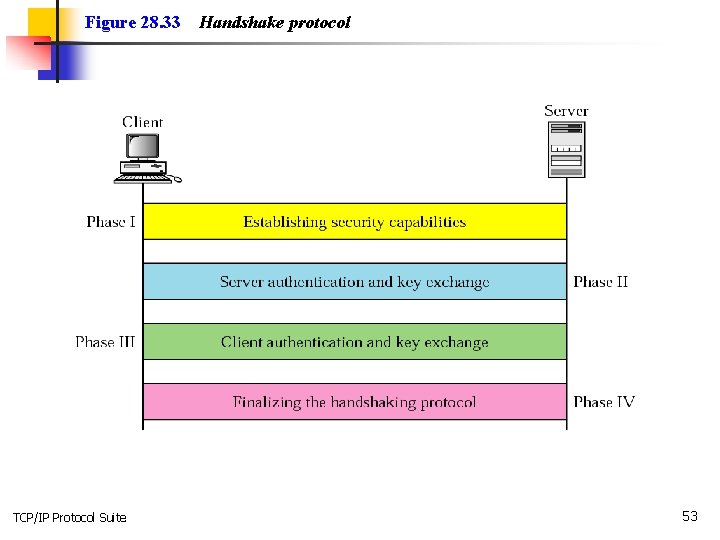
Figure 28. 33 TCP/IP Protocol Suite Handshake protocol 53

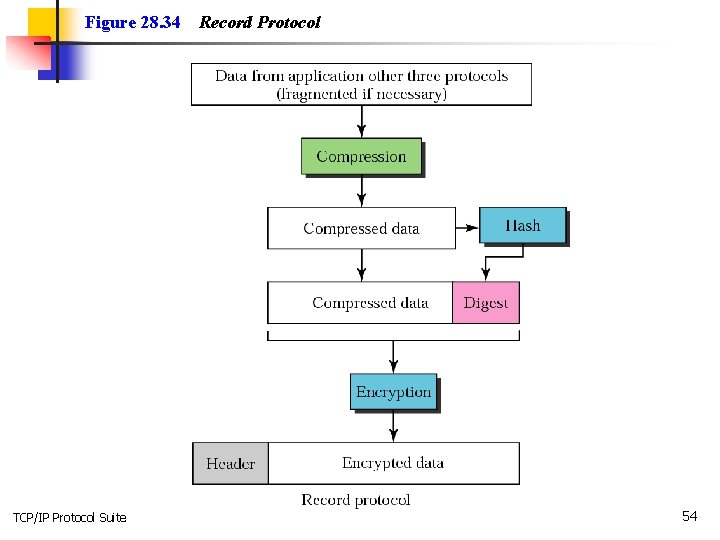
Figure 28. 34 TCP/IP Protocol Suite Record Protocol 54

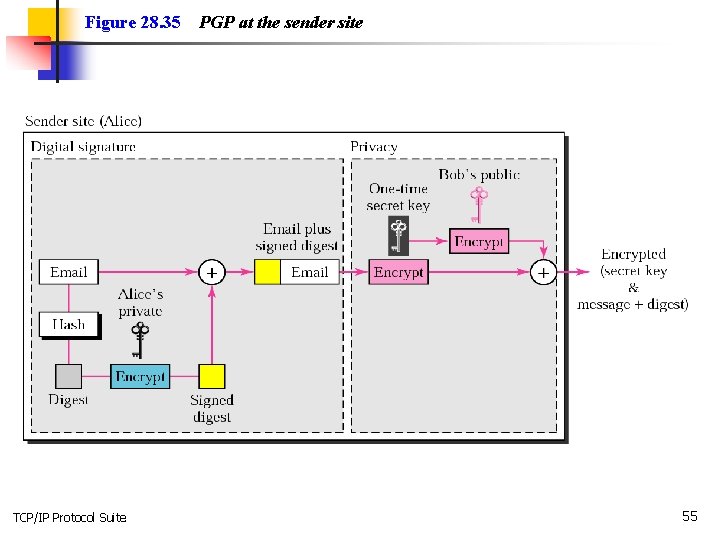
Figure 28. 35 TCP/IP Protocol Suite PGP at the sender site 55

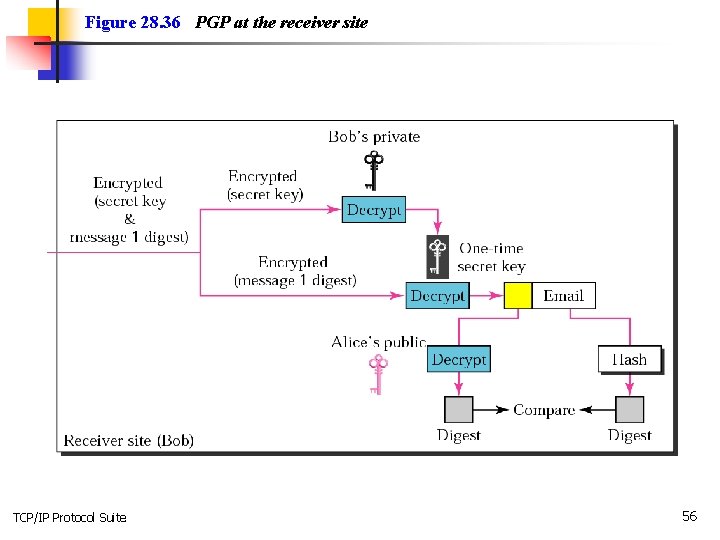
Figure 28. 36 PGP at the receiver site TCP/IP Protocol Suite 56

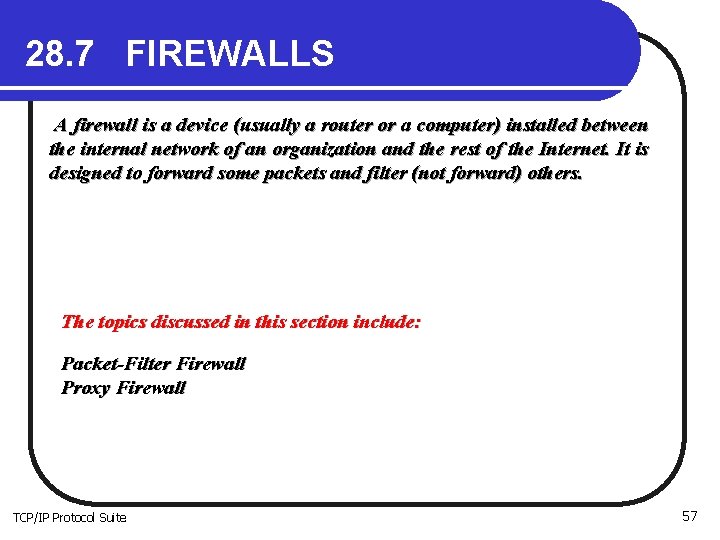
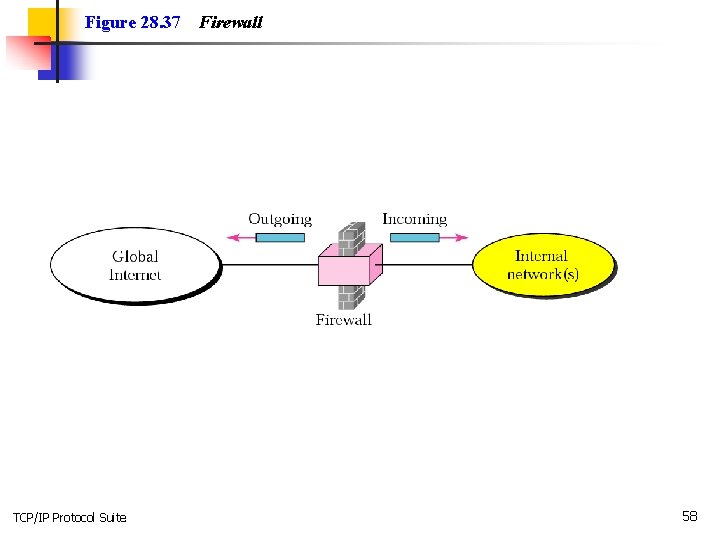
28. 7 FIREWALLS A firewall is a device (usually a router or a computer) installed between the internal network of an organization and the rest of the Internet. It is designed to forward some packets and filter (not forward) others. The topics discussed in this section include: Packet-Filter Firewall Proxy Firewall TCP/IP Protocol Suite 57

Figure 28. 37 TCP/IP Protocol Suite Firewall 58

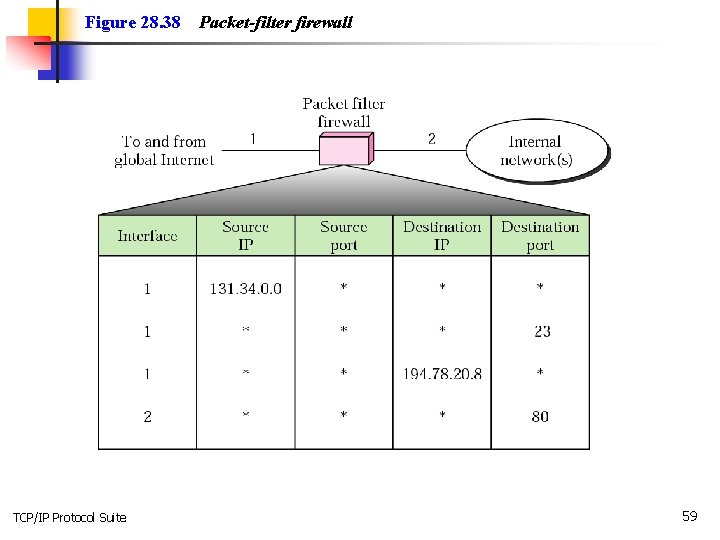
Figure 28. 38 TCP/IP Protocol Suite Packet-filter firewall 59

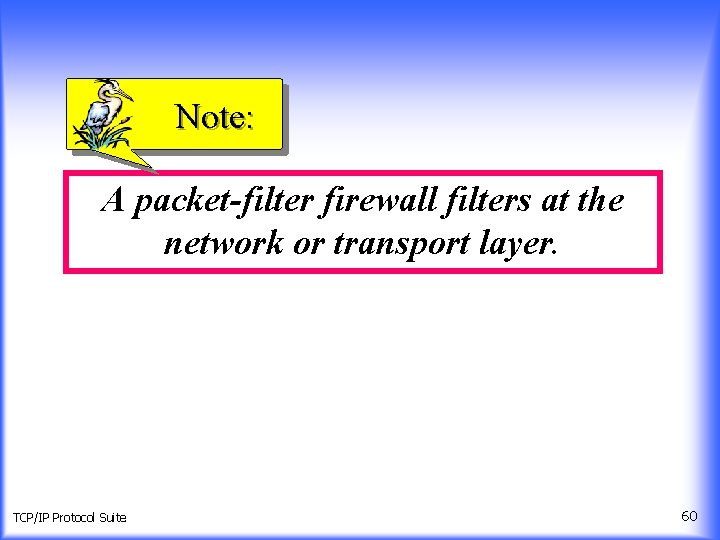
Note: A packet-filter firewall filters at the network or transport layer. TCP/IP Protocol Suite 60

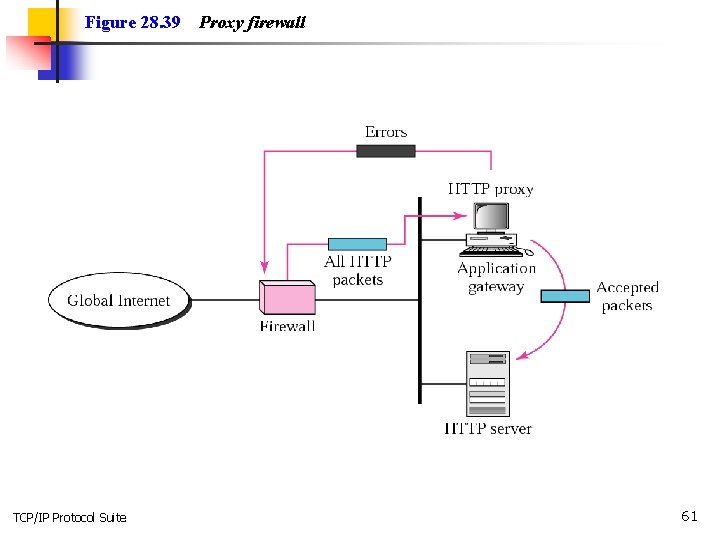
Figure 28. 39 TCP/IP Protocol Suite Proxy firewall 61

Note: A proxy firewall filters at the application layer. TCP/IP Protocol Suite 62