Privacy in Software Development Secure software made easier


























- Slides: 84

Privacy in Software Development Secure software made easier

Agenda • • Privacy Basics Privacy Guidelines for Developing Software and Services – Section I: Definitions and Concepts – Section II: Development Scenarios and Guidelines • • Driving Privacy Compliance Additional Resources

Purpose & Scope Purpose: • Provide an introduction to privacy guidelines for developing software and services. Scope: • • • Product Services Website privacy guidelines

Learning Objectives Upon completion of this course, you should be able to: • • Describe principles and impacts of privacy compliance. Define best practices for collecting, storing and using personal data.

Privacy Basics

What is Privacy? We use privacy to mean: • • Telling users what data is collected and how it will be used. Giving users a choice when their data will be used for purposes other than originally disclosed. Ensuring data is protected and can only be used for the purposes disclosed. Ensuring data practices comply with Federal, State and International laws.

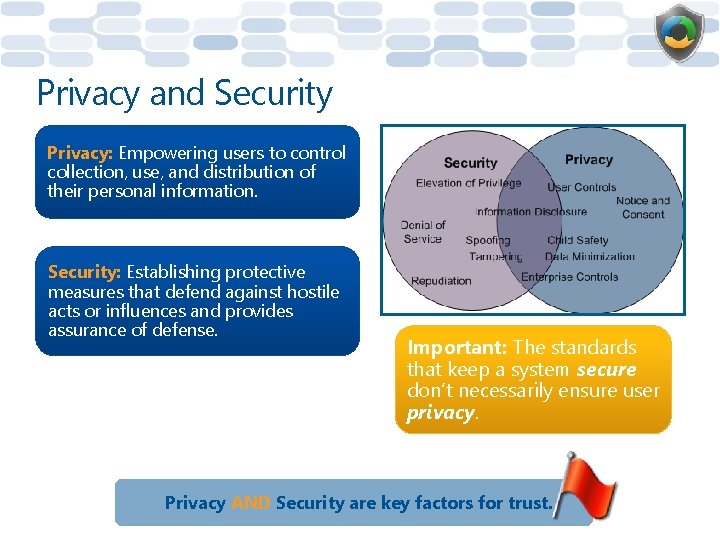
Privacy and Security Privacy: Empowering users to control collection, use, and distribution of their personal information. Security: Establishing protective measures that defend against hostile acts or influences and provides assurance of defense. Important: The standards that keep a system secure don’t necessarily ensure user privacy. Privacy AND Security are key factors for trust.

Investing in Privacy Minimizes potential for legal/PR issues • • High stakes, lowers overall risk COPPA, GLBA, HIPAA, CFAA, EU, FTC Unblocks Product Deployments • Enterprise, Government Increases User Satisfaction and Trust • • • Competitive differentiator Loyalty goes up with choice and control Powerful emotional factor, “Right Thing” to do

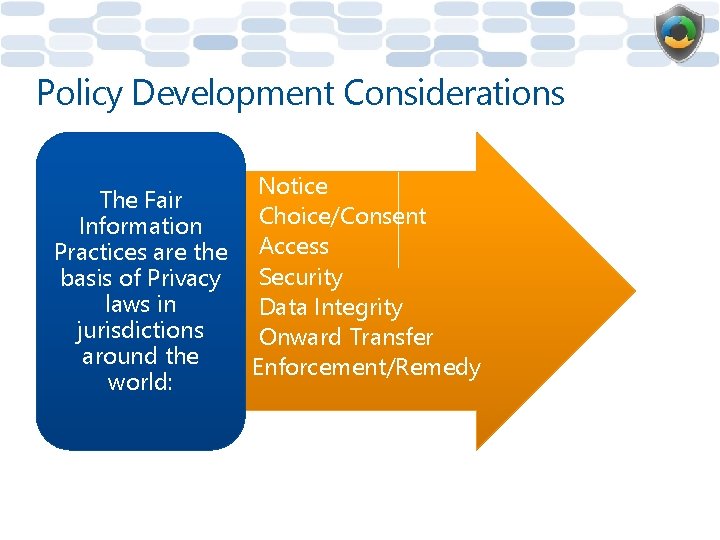
Policy Development Considerations • Notice The Fair Information • Practices are the • basis of Privacy • laws in • jurisdictions • around the • world: Choice/Consent Access Security Data Integrity Onward Transfer Enforcement/Remedy

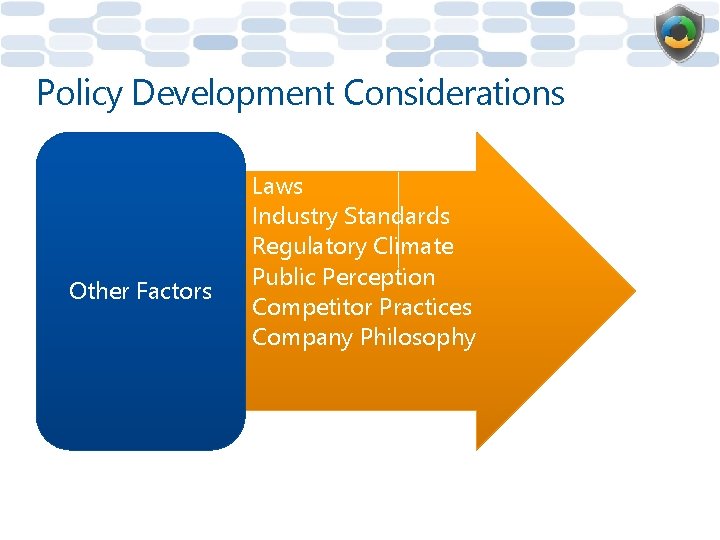
Policy Development Considerations • • Other Factors • • Laws Industry Standards Regulatory Climate Public Perception Competitor Practices Company Philosophy

Privacy Guidelines for Development

Guidelines for Development Section One Section Two • Definitions and Concepts • Development Scenarios and Rules

Definitions and Concepts

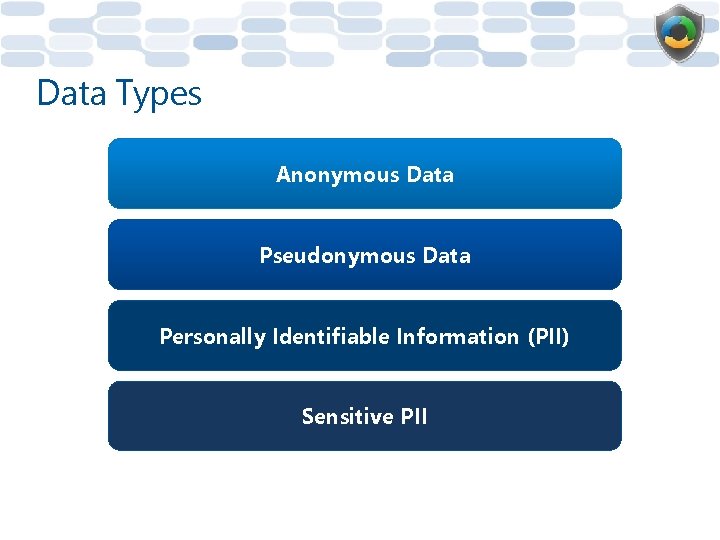
Data Types Anonymous Data Pseudonymous Data Personally Identifiable Information (PII) Sensitive PII

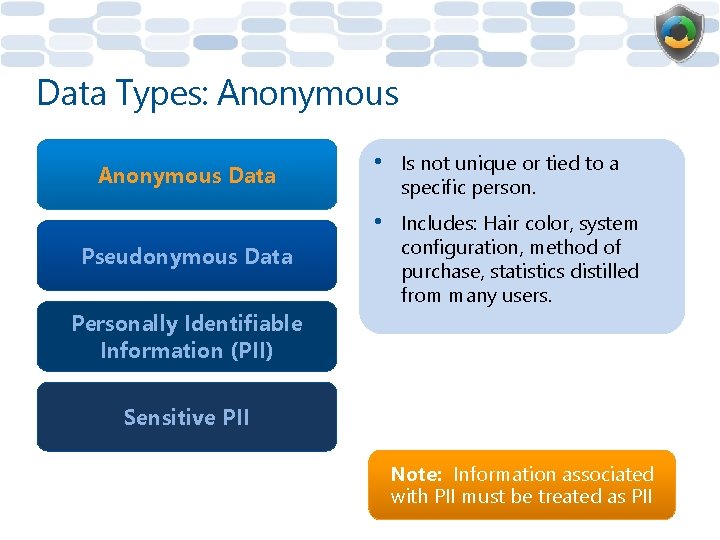
Data Types: Anonymous Data Pseudonymous Data • Is not unique or tied to a specific person. • Includes: Hair color, system configuration, method of purchase, statistics distilled from many users. Personally Identifiable Information (PII) Sensitive PII Note: Information associated with PII must be treated as PII

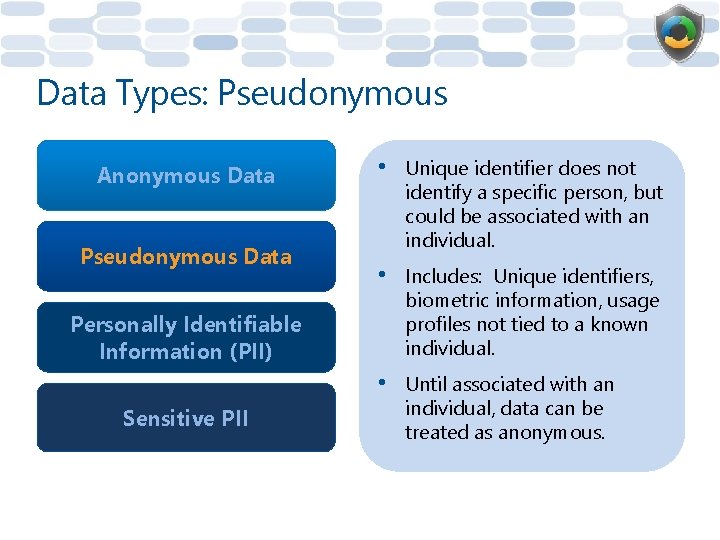
Data Types: Pseudonymous Anonymous Data Pseudonymous Data • Unique identifier does not identify a specific person, but could be associated with an individual. • Includes: Unique identifiers, biometric information, usage profiles not tied to a known individual. • Until associated with an individual, data can be treated as anonymous. Personally Identifiable Information (PII) Sensitive PII

Data Types: PII Anonymous Data Pseudonymous Data Personally Identifiable Information (PII) Sensitive PII • Data that identifies (or can be used to contact or locate) a specific individual. • Includes: Name, address, phone number, fax number, email address, or any information associated with PII.

Data Types: Sensitive PII Anonymous Data Pseudonymous Data • A subset of PII that has special requirements due to higher risk associated with the data. • Includes: Medical and/or financial data, national ID numbers (e. g. , SSN), and credit card information. • Also includes data that could be used to discriminate (i. e. race/ethnicity; political, religious or philosophical beliefs; union membership). Personally Identifiable Information (PII) Sensitive PII

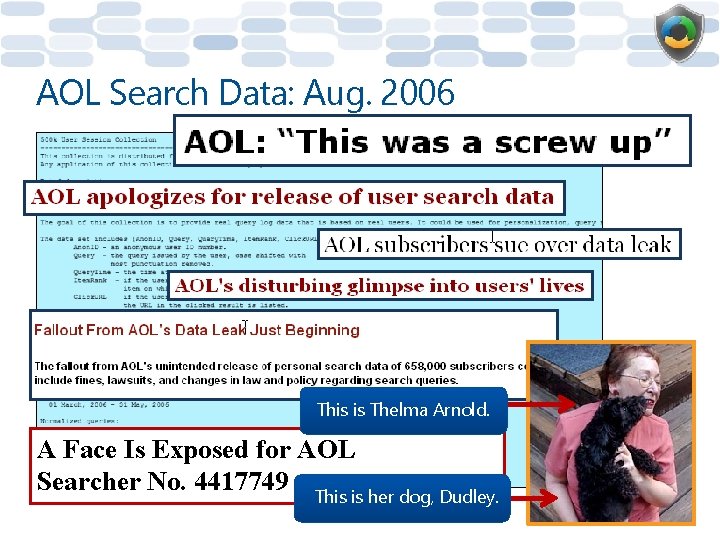
PII Knowledge Test What type of data did AOL release online?

AOL Search Data: Aug. 2006 This is Thelma Arnold. A Face Is Exposed for AOL Searcher No. 4417749 This is her dog, Dudley.

Notice and Consent Fundamentals Types of notice • • Prominent Discoverable Types of consent • • • Opt-in explicit consent Opt-out explicit consent Implicit consent þ Please send me the latest information on special offers of Xbox® games.

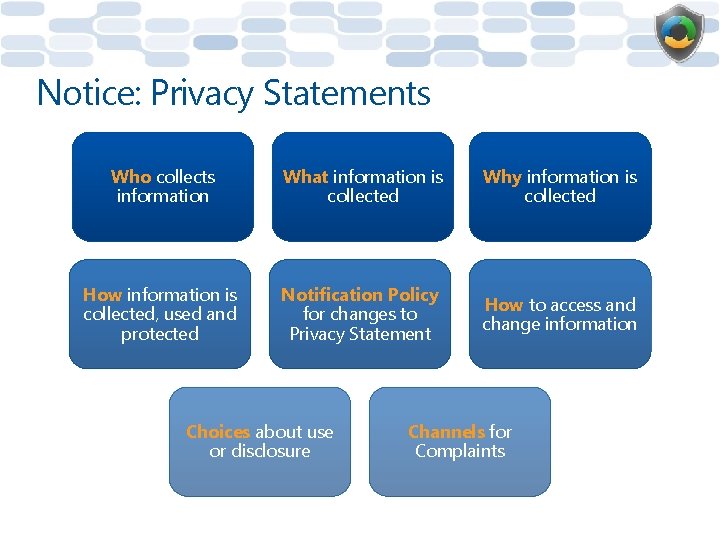
Notice: Privacy Statements Who collects information What information is collected Why information is collected How information is collected, used and protected Notification Policy for changes to Privacy Statement How to access and change information Choices about use or disclosure Channels for Complaints

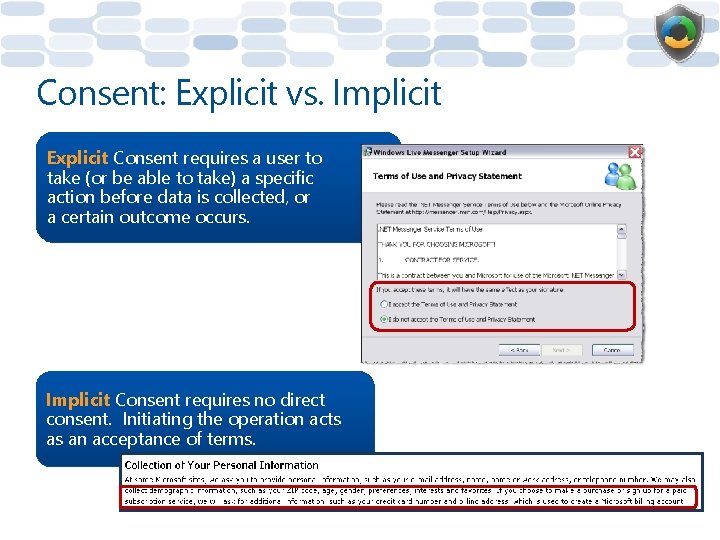
Consent: Explicit vs. Implicit Explicit Consent requires a user to take (or be able to take) a specific action before data is collected, or a certain outcome occurs. Implicit Consent requires no direct consent. Initiating the operation acts as an acceptance of terms.

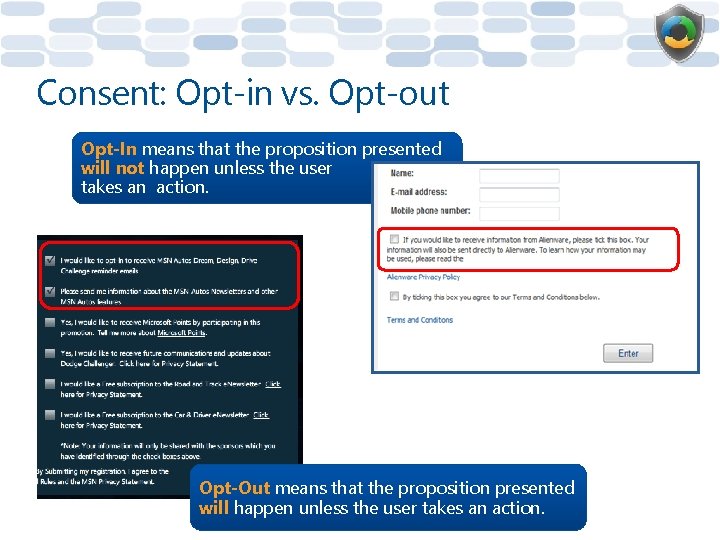
Consent: Opt-in vs. Opt-out Opt-In means that the proposition presented will not happen unless the user takes an action. Opt-Out means that the proposition presented will happen unless the user takes an action. 25

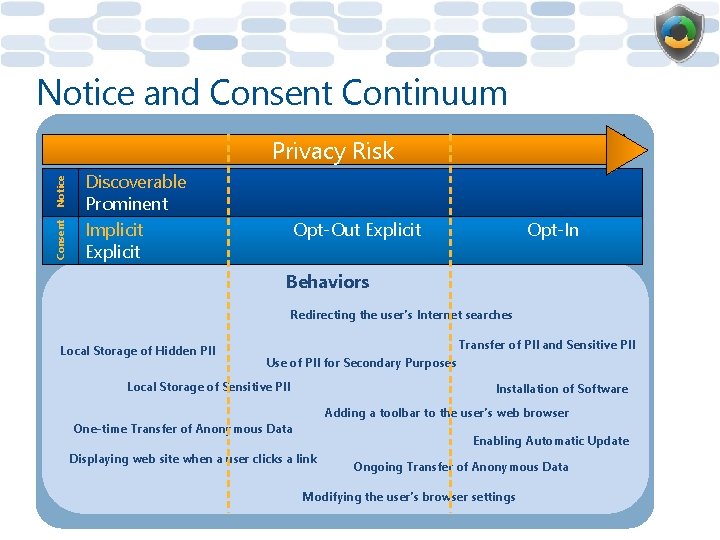
Notice and Consent Continuum Consent Notice Privacy Risk Discoverable Prominent Implicit Explicit Opt-Out Explicit Opt-In Behaviors Redirecting the user’s Internet searches Local Storage of Hidden PII Transfer of PII and Sensitive PII Use of PII for Secondary Purposes Local Storage of Sensitive PII Installation of Software Adding a toolbar to the user’s web browser One-time Transfer of Anonymous Data Enabling Automatic Update Displaying web site when a user clicks a link Ongoing Transfer of Anonymous Data Modifying the user’s browser settings

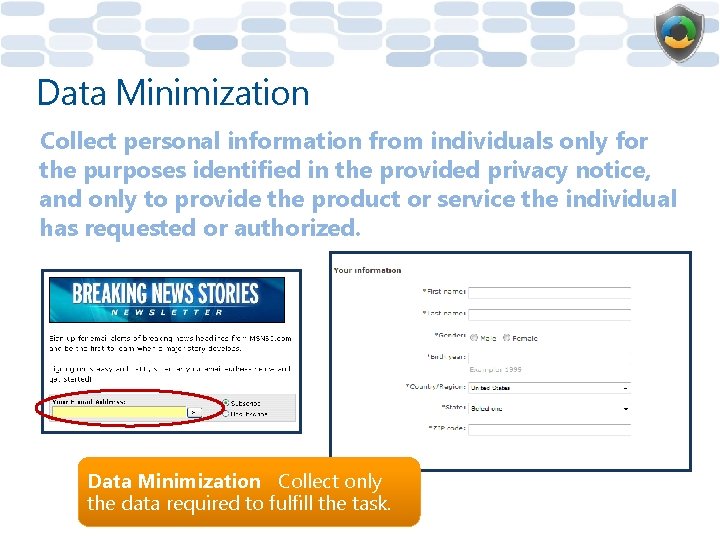
Data Minimization Collect personal information from individuals only for the purposes identified in the provided privacy notice, and only to provide the product or service the individual has requested or authorized. Data Minimization Collect only the data required to fulfill the task.

Other Concepts • • Privacy controls Shared computers Children’s privacy Software installation practices Server products Pre-release products Essential transfers and updates

Scenarios 1 Transferring PII to and from the user’s system 2 Storing PII on the user’s system 3 Transferring anonymous/pseudonymous data from user systems 4 Installing software on a user’s system 5 Deploying a web site 6 5. Storing and processing user data at the company 7 6. Transferring user data outside the company 8 7. Interacting with children 9 8. Server Deployment

Scenario 1 Transferring PII To and From the User’s System

1 Examples • • • Sending product registration to the company. Transferring a file containing hidden PII. Submitting data entered by the user in a Web form. Transferring financial information to a web service. Displaying profile information stored at the company to the user.

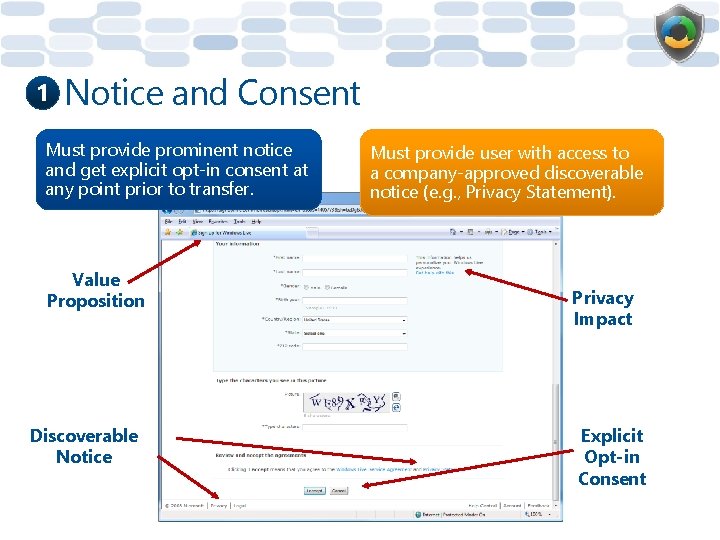
1 Notice and Consent Must provide prominent notice and get explicit opt-in consent at any point prior to transfer. Value Proposition Discoverable Notice Must provide user with access to a company-approved discoverable notice (e. g. , Privacy Statement). Privacy Impact Explicit Opt-in Consent

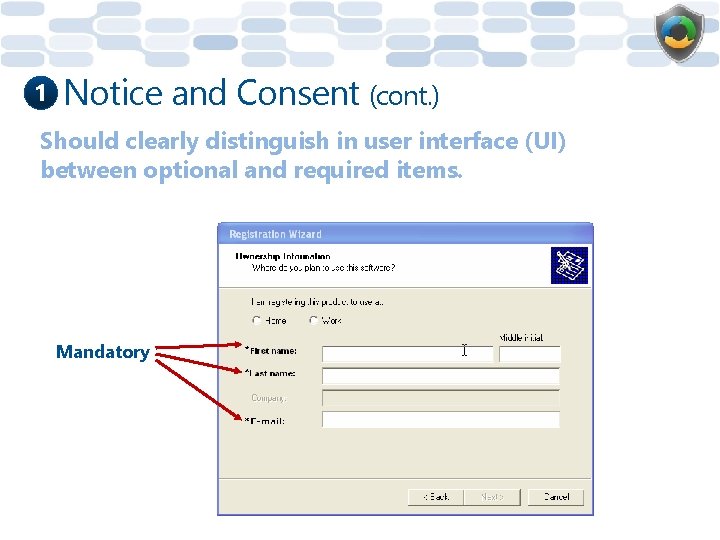
1 Notice and Consent (cont. ) Should clearly distinguish in user interface (UI) between optional and required items. Mandatory

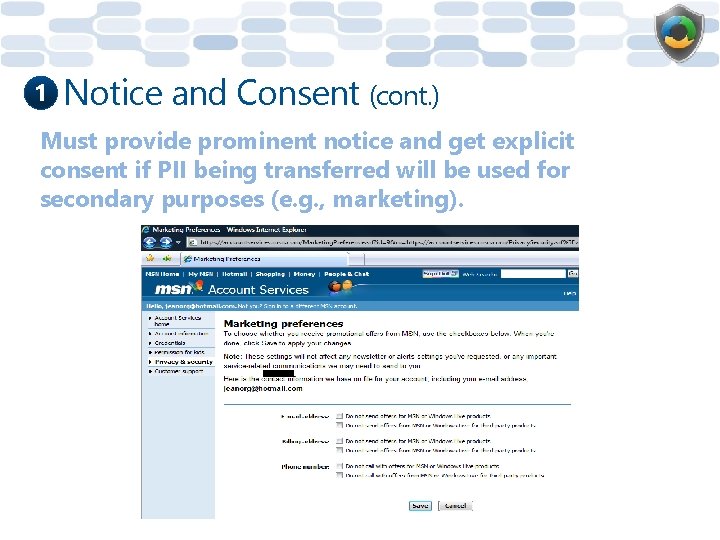
1 Notice and Consent (cont. ) Must provide prominent notice and get explicit consent if PII being transferred will be used for secondary purposes (e. g. , marketing).

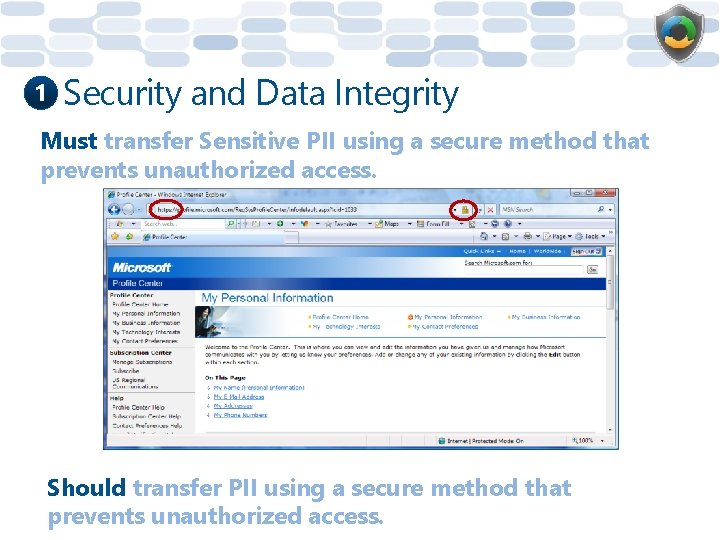
1 Security and Data Integrity Must transfer Sensitive PII using a secure method that prevents unauthorized access. Should transfer PII using a secure method that prevents unauthorized access.

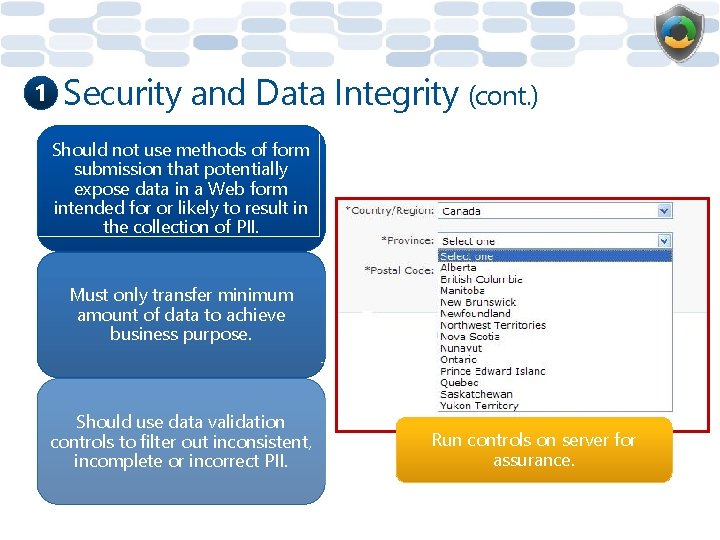
1 Security and Data Integrity (cont. ) Should not use methods of form submission that potentially expose data in a Web form intended for or likely to result in the collection of PII. Must only transfer minimum amount of data to achieve business purpose. Should use data validation controls to filter out inconsistent, incomplete or incorrect PII. Run controls on server for assurance.

1 Customer controls The user must be able to control automatic collection and transfer of PII.

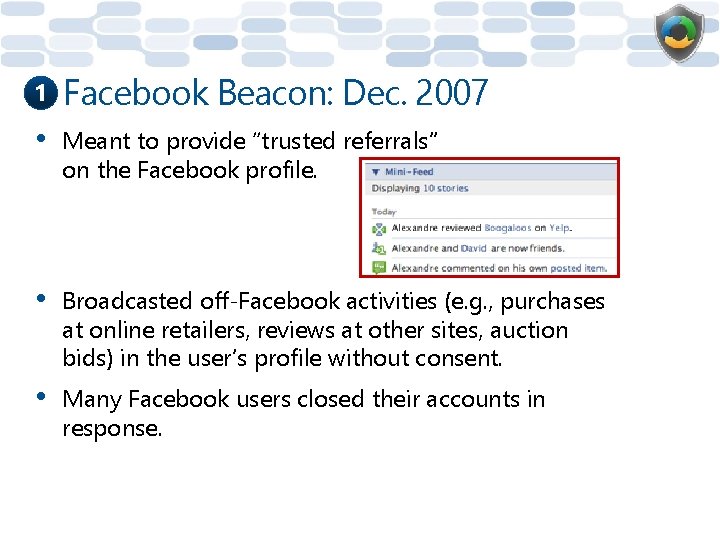
1 Facebook Beacon: Dec. 2007 • Meant to provide “trusted referrals” on the Facebook profile. • Broadcasted off-Facebook activities (e. g. , purchases at online retailers, reviews at other sites, auction bids) in the user’s profile without consent. • Many Facebook users closed their accounts in response.

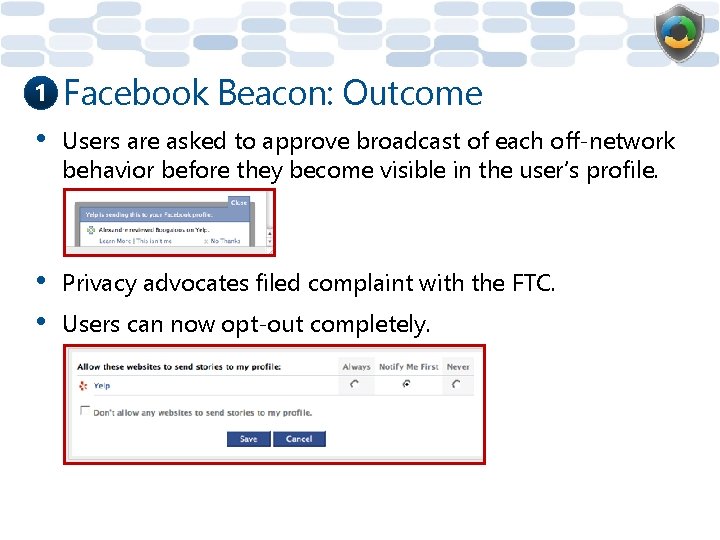
1 Facebook Beacon: Outcome • Users are asked to approve broadcast of each off-network behavior before they become visible in the user’s profile. • • Privacy advocates filed complaint with the FTC. Users can now opt-out completely.

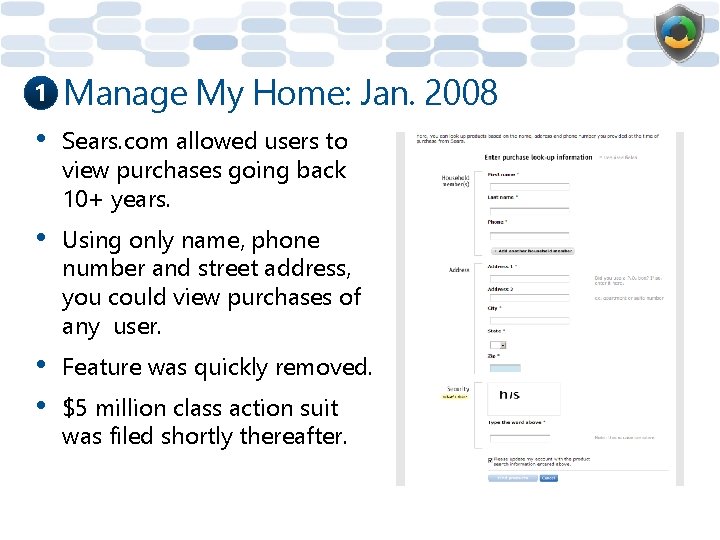
1 Manage My Home: Jan. 2008 • Sears. com allowed users to view purchases going back 10+ years. • Using only name, phone number and street address, you could view purchases of any user. • • Feature was quickly removed. $5 million class action suit was filed shortly thereafter.

Scenario 2 Storing PII On the User’s System

2 Examples • • • Storing the user’s contacts. Caching Web pages that contain PII. Storing PII in cookie.

2 Notice and Consent • Must provide user with notice and get consent prior to storage of Sensitive PII, or when storing PII in a persistent cookie. • Should provide Discoverable Notice describing what data is stored and how to control prior to storing Hidden PII (e. g. , metadata).

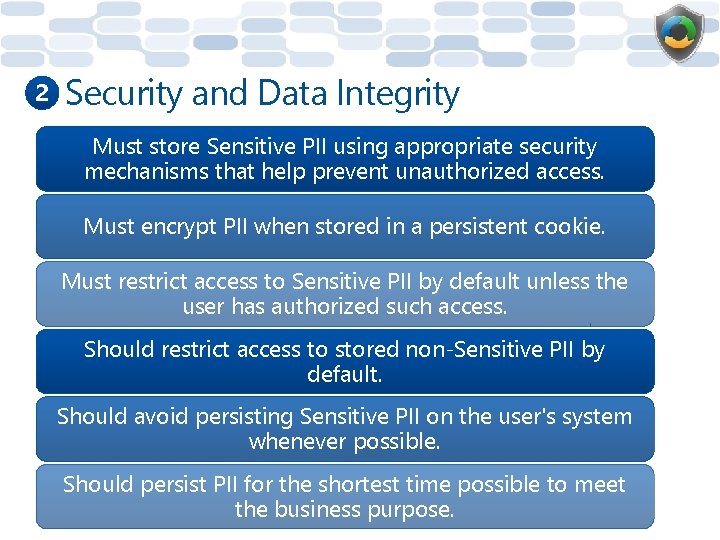
2 Security and Data Integrity Must store Sensitive PII using appropriate security mechanisms that help prevent unauthorized access. Must encrypt PII when stored in a persistent cookie. Must restrict access to Sensitive PII by default unless the user has authorized such access. Should restrict access to stored non-Sensitive PII by default. Should avoid persisting Sensitive PII on the user's system whenever possible. Should persist PII for the shortest time possible to meet the business purpose.

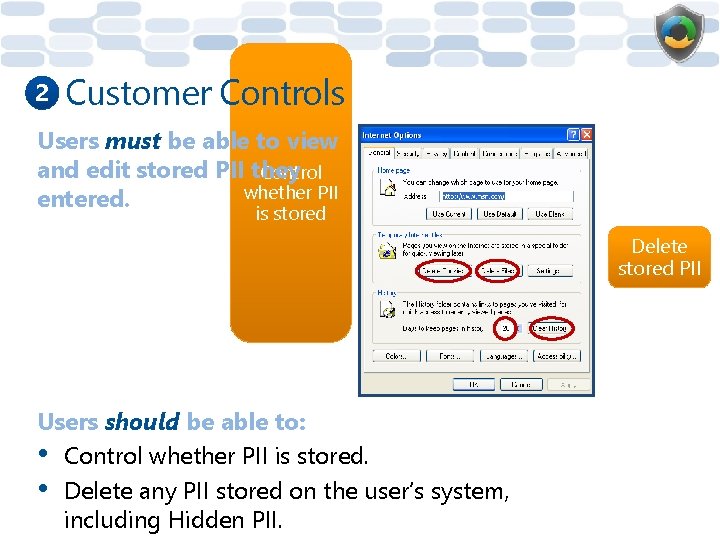
2 Customer Controls Users must be able to view and edit stored PII they Control whether PII entered. is stored Delete stored PII Users should be able to: • Control whether PII is stored. • Delete any PII stored on the user’s system, including Hidden PII.

Scenario 3 Transferring Anonymous/ Pseudonymous Data From User Systems

3 Examples • Anonymous monitoring by an ISP to assess the quality of an Internet connection. • Sending anonymous error reports to the company.

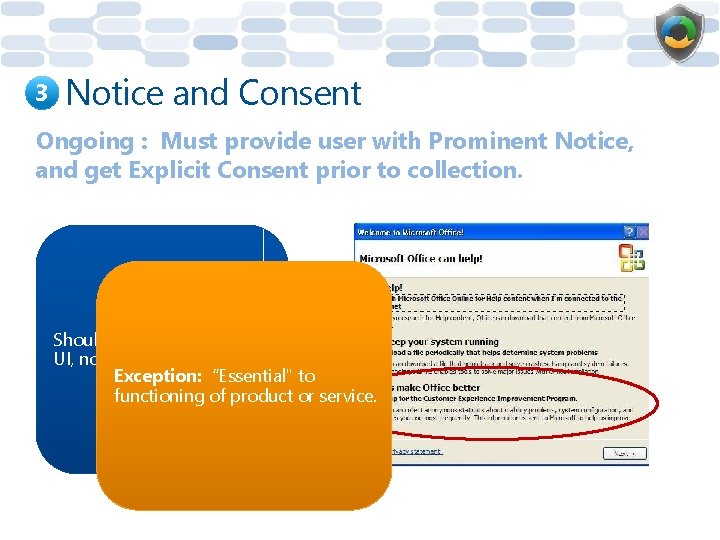
3 Notice and Consent Ongoing : Must provide user with Prominent Notice, and get Explicit Consent prior to collection. Should be provided in the UI, not license agreement. Exception: “Essential" to functioning of product or service.

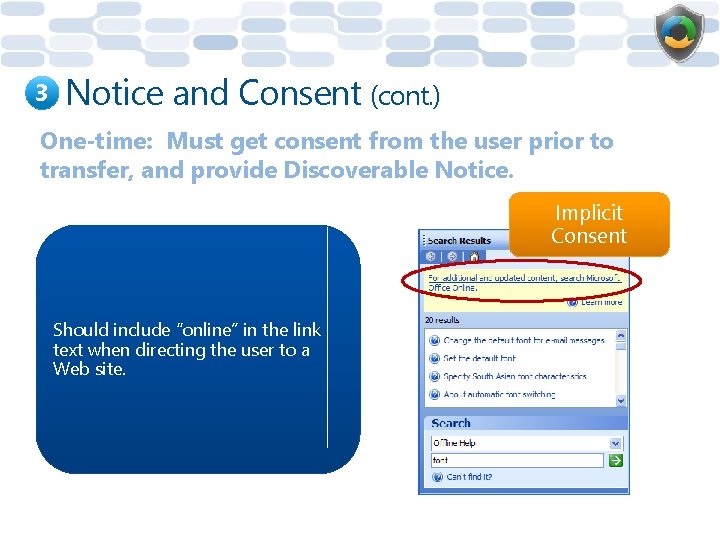
3 Notice and Consent (cont. ) One-time: Must get consent from the user prior to transfer, and provide Discoverable Notice. Implicit Consent Should include “online” in the link text when directing the user to a Web site.

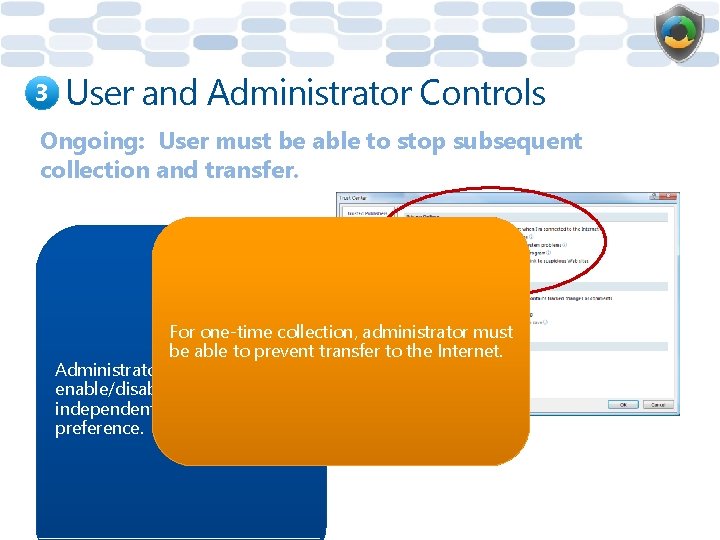
3 User and Administrator Controls Ongoing: User must be able to stop subsequent collection and transfer. For one-time collection, administrator must be able to prevent transfer to the Internet. Administrator must be able to enable/disable transfer independent of user's preference.

Scenario 4 Installing Software On a User’s System

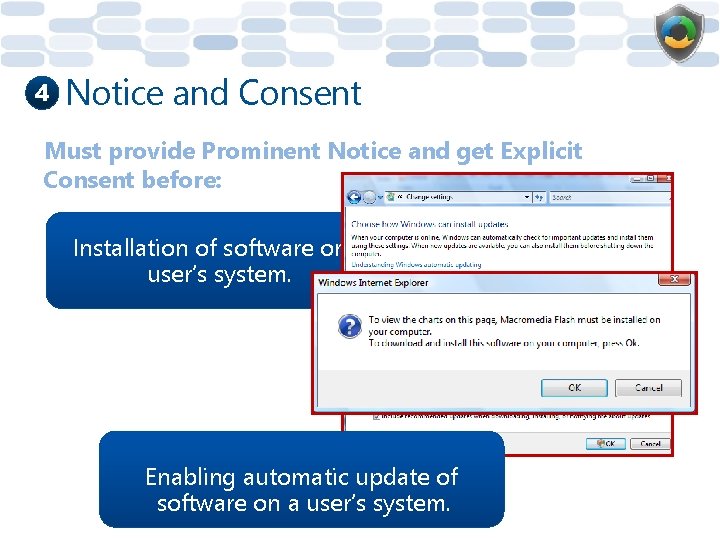
4 Examples • • Installing a boxed product. Installing a download. Installing automatic updates. Installing Active X controls.

4 Notice and Consent Must provide Prominent Notice and get Explicit Consent before: Installation of software on a user’s system. Enabling automatic update of software on a user’s system.

4 Notice and Consent (cont. ) • Should provide Prominent Notice in the UI when privacy settings are migrated. • Should not migrate a privacy setting on an upgrade if the meaning of the privacy setting has changed. • Should not migrate any privacy settings from a pre-release version to a final release version.

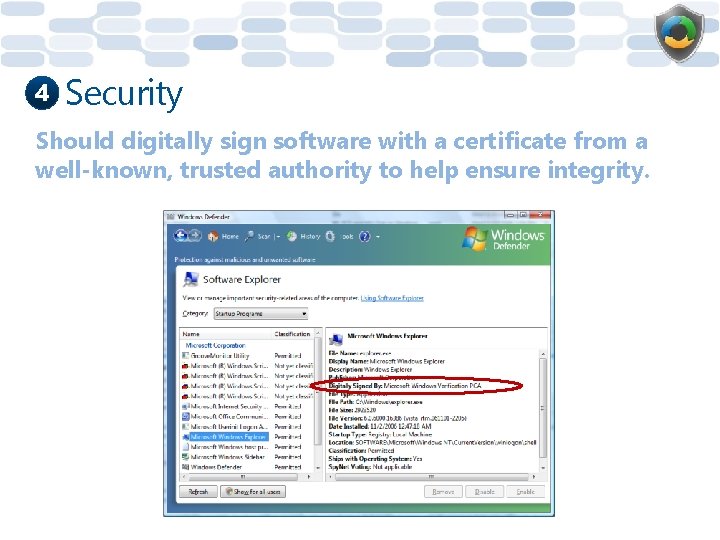
4 Security Should digitally sign software with a certificate from a well-known, trusted authority to help ensure integrity.

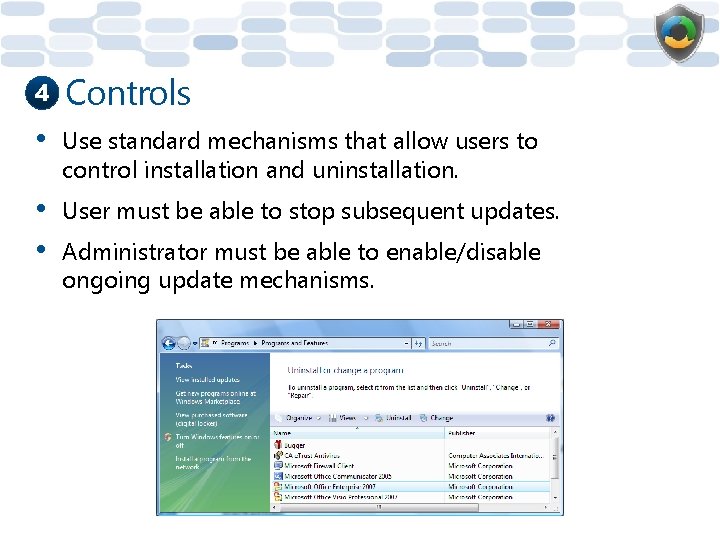
4 Controls • Use standard mechanisms that allow users to control installation and uninstallation. • • User must be able to stop subsequent updates. Administrator must be able to enable/disable ongoing update mechanisms.

4 Zango: Nov. 2006 • One of world’s largest distributors of adware FTC Act Violations Deceptive failure to (usually bundled with “lureware”). • adequately disclose adware, unfair installation of adware to Zango, and unfair uninstall practices. Adware sends Internet usage data and displays pop-up ads based on usage.

Scenario 5 Deploying a Website

5 Example • Creating a web portal directed at consumers.

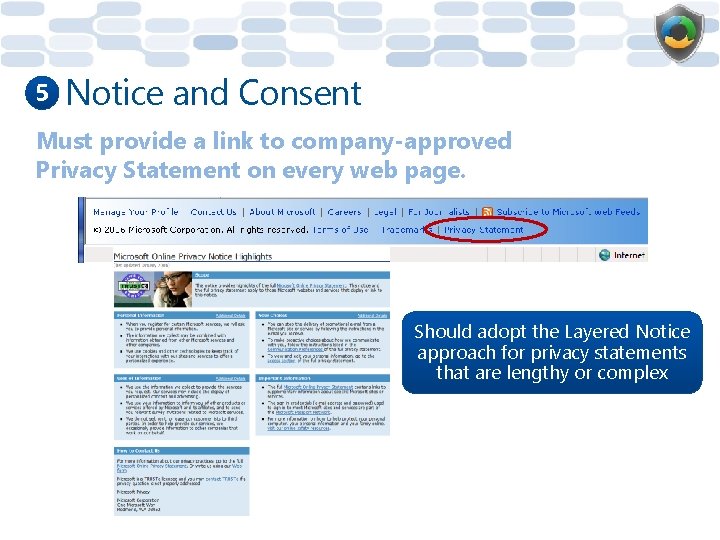
5 Notice and Consent Must provide a link to company-approved Privacy Statement on every web page. Should adopt the Layered Notice approach for privacy statements that are lengthy or complex

5 Use of Cookies • Must not use persistent cookies where a session cookie would satisfy the purpose. • Should not store PII in a persistent cookie unless absolutely necessary. • Must get Explicit Opt-In Consent from user for persistent cookies that store PII.

Scenario 6 Storing and Processing User Data at the Company

6 Examples • • • Storing user data in database or web log. Generating statistics from collected user data. Transferring data from one internal group to another internal group.

6 Security and Data Integrity Must: • Store PII using appropriate security mechanisms to help prevent unauthorized access. • Restrict PII access to those with a need to know, and revoke access when no longer needed. • Store minimum amount of data, for the shortest amount of time necessary to achieve business purpose. • Maintain data integrity.

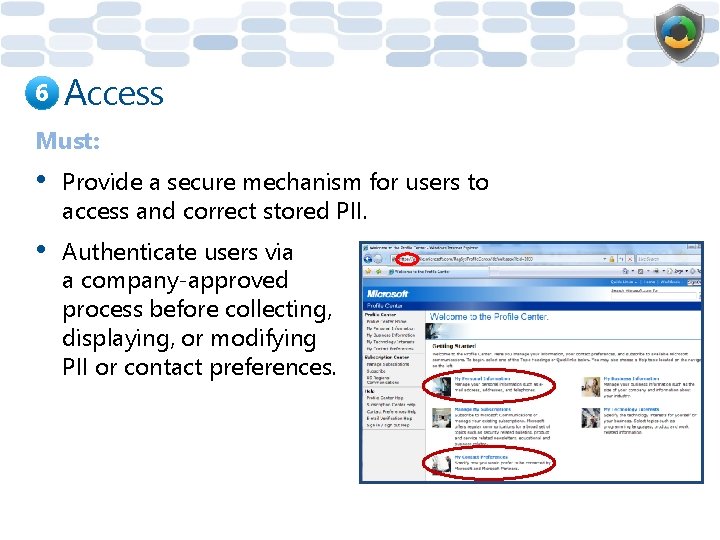
6 Access Must: • Provide a secure mechanism for users to access and correct stored PII. • Authenticate users via a company-approved process before collecting, displaying, or modifying PII or contact preferences.

6 BJ’s Warehouse • Complaint: Alleged that BJ’s did not employ reasonable and appropriate measures to secure PII collected at its stores (no reference to representations in privacy statement). • Settlement: (1) maintain comprehensive ISP, (2) biannual independent audits of security program for 20 years. Obligations • Do what you say. • Keep personal information secure, regardless of wording used in Privacy Statement. Misrepresenting privacy practices is an unfair trade practice. The FTC regulates privacy and security practices through consumer protection law.

Scenario 7 Transferring Data Outside of the Company

7 Examples • • Sending PII from the company to an agent. Sending PII from the company to an independent third party that will use PII for its own purposes.

7 Notice and Consent To share PII to with an independent third party: • • Provide separate Explicit Opt-In Consent mechanism. Provide link to third party Privacy Statement. To share PII with an agent: • • Discoverable Notice is required. Limit use to what was disclosed at point of collection. Additional uses require notice and consent to cover expanded use.

7 Other Security • Must transfer PII using a secure method that prevents unauthorized access. • Must only transfer minimum data necessary. Access • Must provide means for users to update contact preferences for future transfers of PII to independent third parties. Additional Requirements • Company-approved contract containing adequate data protection provisions with third party. • Meet all legal requirements if data will cross borders.

Scenario 8 Interacting With Children

8 Examples Note: These rules apply only to the U. S. , South Korea and Spain, where they are legal requirements. • • Hosting a website intended to help elementary school children with their homework. Collecting a user’s age or birth date on a website that is not inherently attractive to children. Under 13 The United States Must obtain company approval before collecting PII from children. Under 14 Spain South Korea

8 Notice and Consent IF: • Site or service is attractive to or directed at children; • Site collects, uses or discloses user PII; • The user is underage; REMEMBER: • Age should be collected in a manner that doesn’t encourage children to lie. • Session cookies should be used to prevent children from back-clicking to THEN: change their age. • Collect age of all users. • Block PII collection and disclosure; OR • Notify parent, and obtain consent prior to collection, use or disclosure.

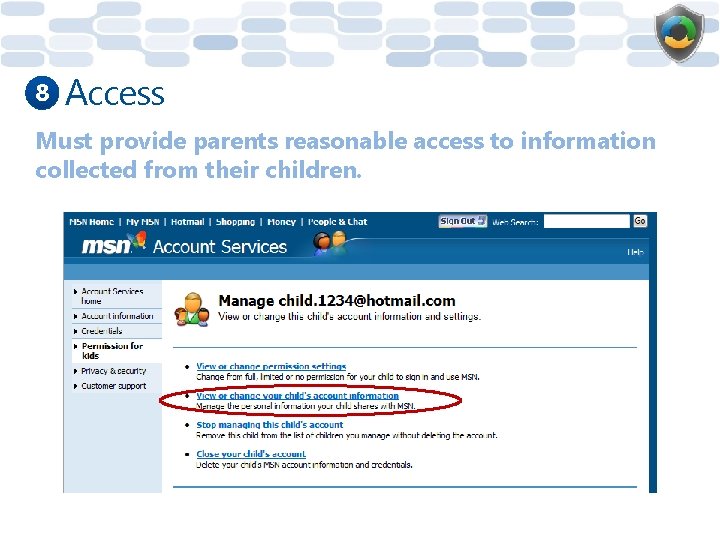
8 Access Must provide parents reasonable access to information collected from their children.

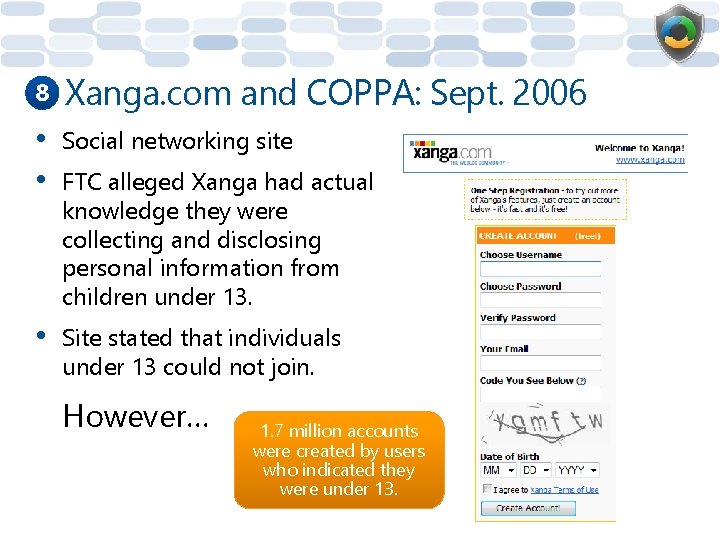
8 Xanga. com and COPPA: Sept. 2006 • • Social networking site • Site stated that individuals under 13 could not join. FTC alleged Xanga had actual knowledge they were collecting and disclosing personal information from children under 13. However… 1. 7 million accounts were created by users who indicated they were under 13.

Scenario 9 Server Deployment

9 Examples • • • Software installation in an enterprise. Storage of user data in an enterprise. Transfer of user data outside enterprise firewall.

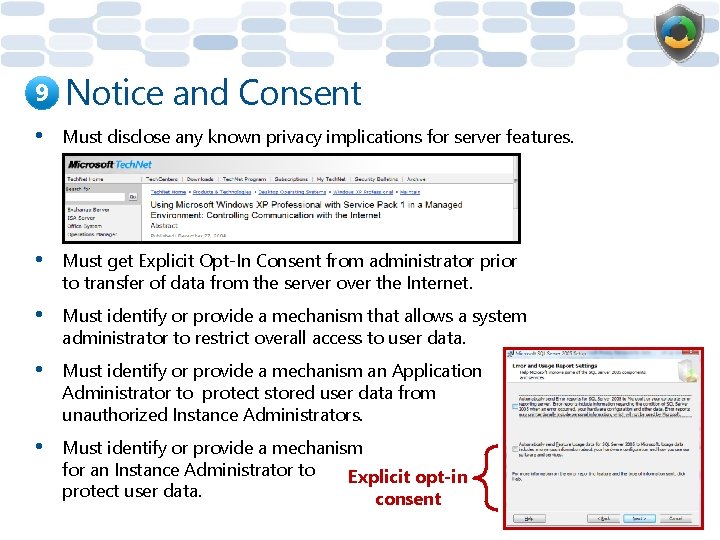
9 Notice and Consent • Must disclose any known privacy implications for server features. • Must get Explicit Opt-In Consent from administrator prior to transfer of data from the server over the Internet. • Must identify or provide a mechanism that allows a system administrator to restrict overall access to user data. • Must identify or provide a mechanism an Application Administrator to protect stored user data from unauthorized Instance Administrators. • Must identify or provide a mechanism for an Instance Administrator to Explicit opt-in protect user data. consent 79

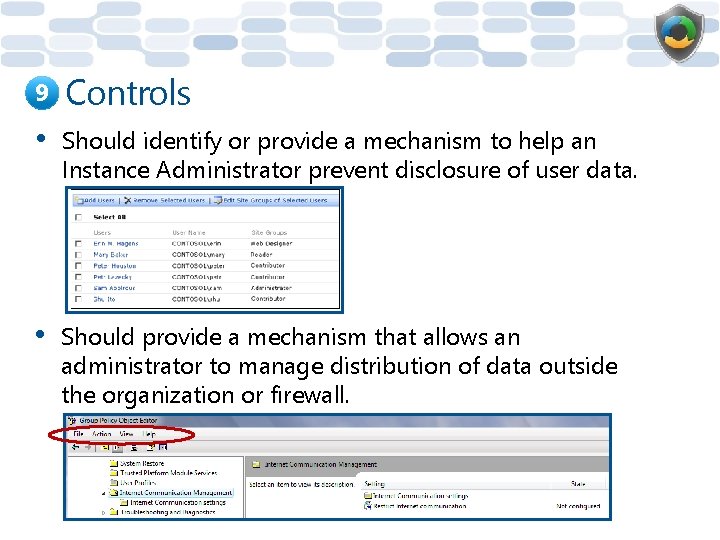
9 Controls • Should identify or provide a mechanism to help an Instance Administrator prevent disclosure of user data. • Should provide a mechanism that allows an administrator to manage distribution of data outside the organization or firewall.

Summary

Summary You should now understand: • • • Privacy principles. Impacts of Privacy noncompliance. Guidelines for collecting, storing and using personal data.

Resources For more information see: “Privacy Guidelines for Developing Software Products and Services” http: //www. microsoft. com/downloads/ details. aspx? Family. ID=c 48 cf 80 f-6 e 87 -48 f 5 - 83 ec-a 18 d 1 ad 2 fc 1 f&displaylang=en

Resources SDL Portal http: //www. microsoft. com/sdl SDL Blog http: //blogs. msdn. com/sdl/ SDL Process on MSDN (Web) http: //msdn. microsoft. com/enus/library/cc 307748. aspx SDL Process on MSDN (MS Word) http: //www. microsoft. com/downloa ds/details. aspx? Family. ID=d 045 a 05 a-c 1 fc-48 c 3 -b 4 d 5 b 20353 f 97122&displaylang=en

Questions?

© 2008 Microsoft Corporation. All rights reserved. Microsoft, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.