Workday Data Privacy and Security Overview The privacy


- Slides: 5

Workday: Data Privacy and Security Overview • The privacy and security of HR data is the no. 1 priority of the Workday project Workday is the group-wide system for Human Resources (HR), it provides a platform for consistent HR processes and holds personal and job details for each employee in the company ü Significant due diligence has been conducted on data protection ü A legal workstream is underway to ensure compliance in each operating country ü Workday has implemented tight controls, an overview of their security approach can be found here: http: //www. workday. com/why_workday/reliable_and_secure. php 1

Workday security controls Compliance, privacy and security considerations are core to the overall design of Workday, which employs a unified approach to security at all computing layers. Access for end users to view or modify data is granted only via browser/mobile application. Access for systems to view or modify data granted only via web services. No access is provided at the database layer. Access utilizes single role‐based security logic to authenticate the user and to make sure they have been granted a role that allows the update. Workday provides a complete audit trail of changes made • • 2 Workday delivers applications via a software as a service (Saa. S) model, also known as the “Cloud”. In this service delivery model, Workday is responsible for providing the infrastructure (i. e. hardware and middleware that comprise the Workday infrastructure), data security, software development and operational processes Workday are fully ISO and Safe Harbour certified and our data will be hosted within the European Economic Area (in Dublin, Ireland) Detailed Workday security reports: – Workday’s Service Organization Controls 3 (SOC 3) report is available here: http: //www. workday. com/Documents/workday_soc 3_october_2014. pdf – If required, the very detailed SOC 1 and 2 reports are available here: https: //hyperiongrp. thruinc. net/Desktop/Distro/Open/006 P 1 FFIBSZ

Accessing Workday will be available via browser, Single Sign On within company network Ø Ø • 3 Workday will also be available via mobile device, such as tablet or smartphone Employees will see their own data Managers will see their team Executives will see dashboard analytics HR and Finance will see information required by their role Naturally, security guidelines apply at all times – everyone must always: – follow password guidelines – lock computer or mobile device when not in use – avoid exporting/emailing/printing personal data

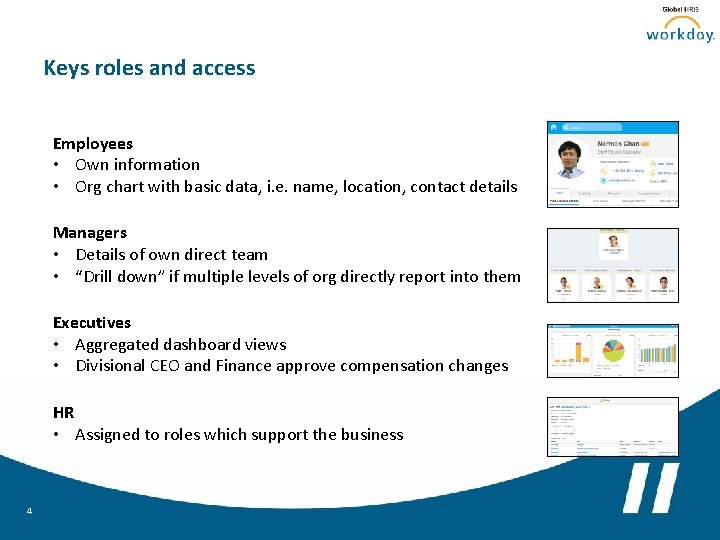
Keys roles and access Employees • Own information • Org chart with basic data, i. e. name, location, contact details Managers • Details of own direct team • “Drill down” if multiple levels of org directly report into them Executives • Aggregated dashboard views • Divisional CEO and Finance approve compensation changes HR • Assigned to roles which support the business 4

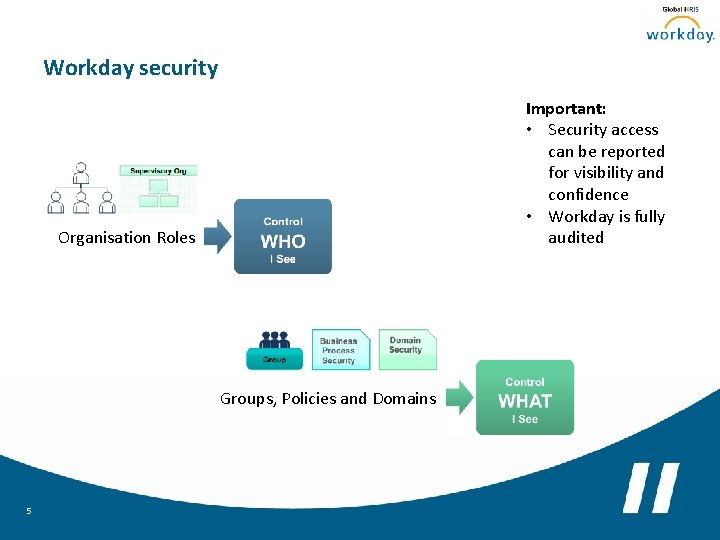
Workday security Important: • Security access can be reported for visibility and confidence • Workday is fully audited Organisation Roles Groups, Policies and Domains 5