Principles of Digital Watermarking Ingemar J Cox Matt





















































































































- Slides: 149

Principles of Digital Watermarking Ingemar J. Cox, Matt L. Miller, and Jeffrey A Bloom

Course outline UCL Adastral Park Postgraduate Campus q Part 1: Introduction and Applications q Part 2: Basic Algorithms and Concepts q Part 3: Advanced Watermarking Course outline

Part 1: Definitions and Applications

Definitions and Applications: Outline q Definitions of watermarking q Watermarking applications q Conclusions UCL Adastral Park Postgraduate Campus q Properties of watermarking systems Definitions and Applications

Definitions of watermarking Without common definitions, various approaches and technologies cannot be compared. Definitions and Applications

Watermarking is the practice of unobtrusively modifying a work of art (image, song, software program, geometric model, etc. ) to embed a message about that work. Multimedia watermarking is the practice of imperceptibly altering a work (image, song, etc. ) to embed a message about that work. UCL Adastral Park Postgraduate Campus Definitions of watermarking: Our definition Definitions and Applications

Original work Watermark embedder Message (regarding work) Watermarked work (looks like original) Detected message Watermark detector UCL Adastral Park Postgraduate Campus Definitions of watermarking: Basic design of a system Definitions and Applications

Definitions of watermarking: Other definitions q Sometimes more broadly defined as any data hiding (i. e. hidden data need not relate to work). q Sometimes more narrowly defined as owner identification (watermarks must indicate identity of owner). UCL Adastral Park Postgraduate Campus q Imperceptibility is not always considered essential (allows for visible watermarking). Definitions and Applications

Definitions of watermarking: Related terms q Steganography: keeping the existence of messages secret by hiding them within objects, media, or other messages. UCL Adastral Park Postgraduate Campus q Data hiding: any technology for preventing adversaries from perceiving or finding data. Definitions and Applications

Watermarking is the practice of unobtrusively modifying a work of art (image, song, software program, geometric model, etc. ) to embed a message about that work. Steganography is the practice of undetectably modifying a work to embed a message. UCL Adastral Park Postgraduate Campus Definitions of watermarking: Related terms

Original Undetectable UCL Adastral Park Postgraduate Campus Unobtrusive

Properties of systems Understanding, comparing, and selecting watermarking approaches or technologies takes place in the context of system properties. Definitions and Applications

List of properties to be discussed q Embedding effectiveness q Data payload q Blind vs. informed detection q False positive rate UCL Adastral Park Postgraduate Campus q Fidelity q Robustness q Security Definitions and Applications

q When we say “random work”, we mean a work drawn from an application-dependent distribution of works. Examples: x-rays, animation, natural image, classical music, speech, etc. q When we say “random watermark”, we mean a watermark message drawn from the set of possible messages. UCL Adastral Park Postgraduate Campus A note before we begin … Definitions and Applications

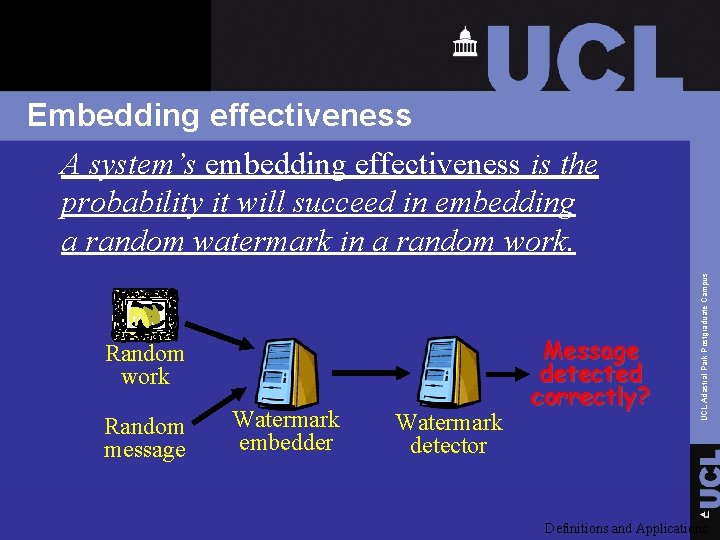
Random work Random message Watermark embedder Watermark detector Message detected correctly? UCL Adastral Park Postgraduate Campus Embedding effectiveness A system’s embedding effectiveness is the probability it will succeed in embedding a random watermark in a random work. Definitions and Applications

Embedding effectiveness Ø In some cases, it is not possible to embed required amount of information imperceptibly. Ø Actual implementations usually involve some round -off and truncation before watermarked work is stored, which sometimes make watermark undetectable. UCL Adastral Park Postgraduate Campus q Why might embedding effectiveness be less than 100 percent? Definitions and Applications

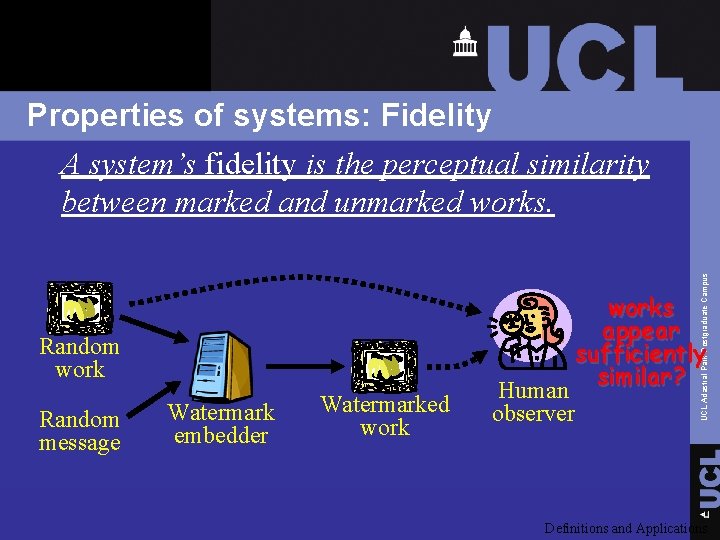
Random work Random message Watermark embedder Watermarked work Human observer UCL Adastral Park Postgraduate Campus Properties of systems: Fidelity A system’s fidelity is the perceptual similarity between marked and unmarked works appear sufficiently similar? Definitions and Applications

01101001… Random message Random work Watermark embedder Watermarked work UCL Adastral Park Postgraduate Campus Properties of systems: Data payload A system’s data payload is the amount of information that it can embed in a single work. Definitions and Applications

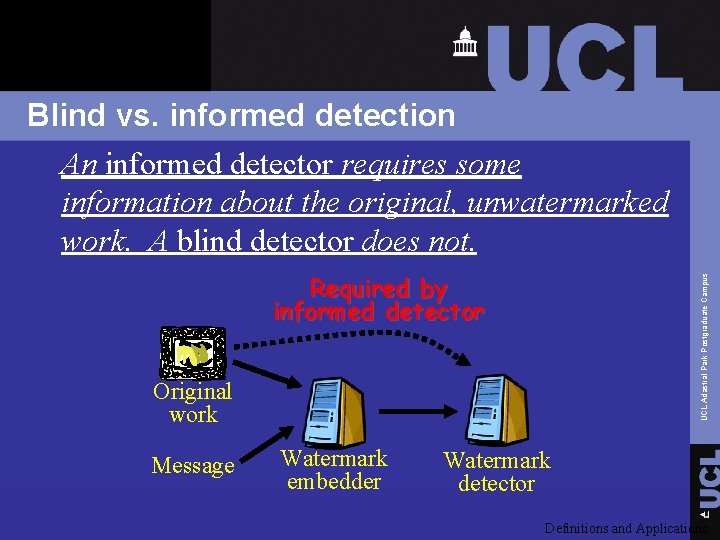
Blind vs. informed detection An informed detector requires some information about the original, unwatermarked work. A blind detector does not. UCL Adastral Park Postgraduate Campus Required by informed detector Original work Message Watermark embedder Watermark detector Definitions and Applications

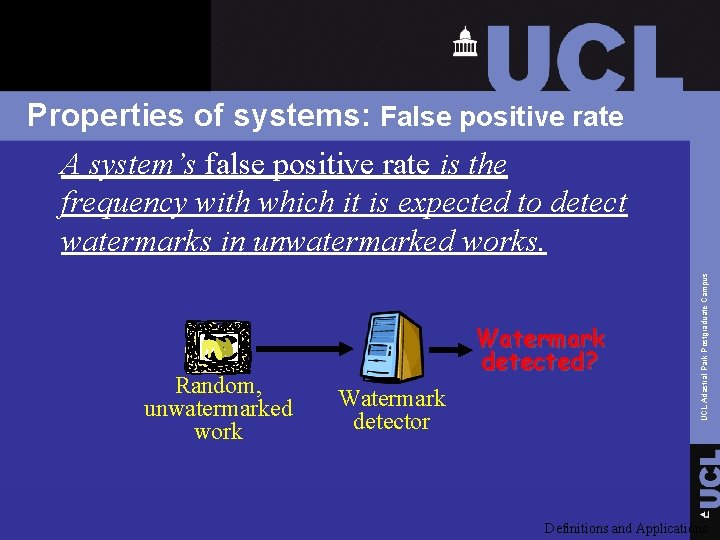
Random, unwatermarked work Watermark detected? Watermark detector UCL Adastral Park Postgraduate Campus Properties of systems: False positive rate A system’s false positive rate is the frequency with which it is expected to detect watermarks in unwatermarked works. Definitions and Applications

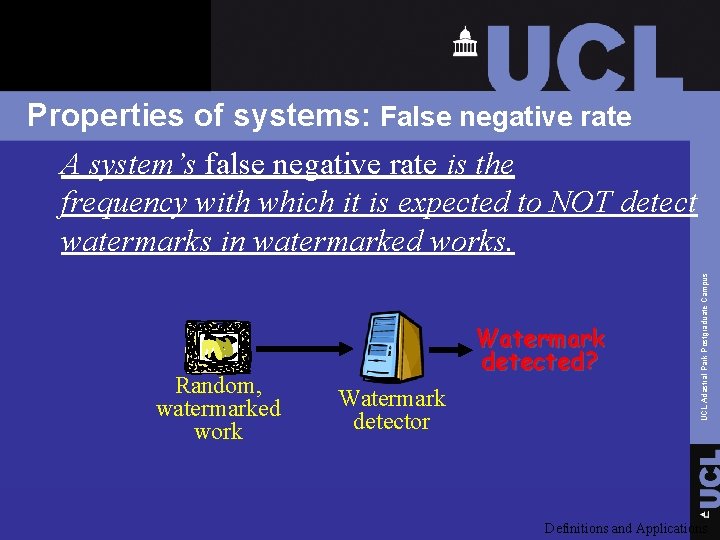
Random, watermarked work Watermark detected? Watermark detector UCL Adastral Park Postgraduate Campus Properties of systems: False negative rate A system’s false negative rate is the frequency with which it is expected to NOT detect watermarks in watermarked works. Definitions and Applications

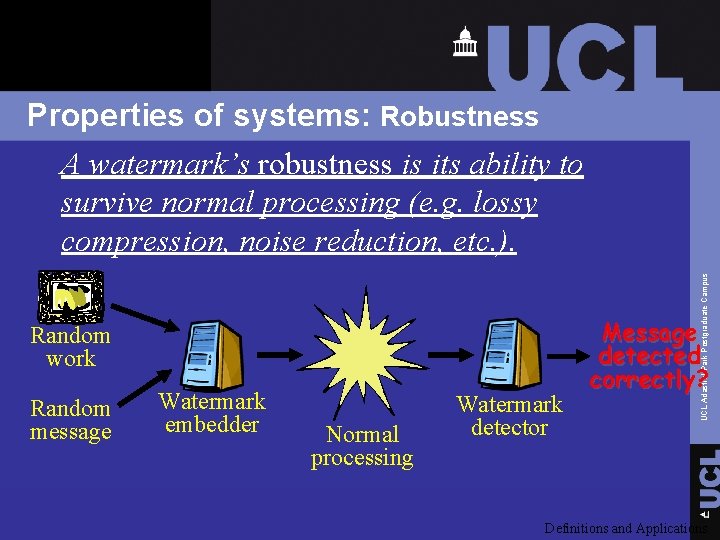
Random work Random message Watermark embedder Normal processing Watermark detector UCL Adastral Park Postgraduate Campus Properties of systems: Robustness A watermark’s robustness is its ability to survive normal processing (e. g. lossy compression, noise reduction, etc. ). Message detected correctly? Definitions and Applications

q Types of attacks Ø Unauthorized embedding (forgery) Ø Unauthorized detection Ø Unauthorized removal UCL Adastral Park Postgraduate Campus Properties of systems: Security A watermark’s security is its ability to resist hostile attacks, specifically designed to defeat the purpose of the watermark. Definitions and Applications

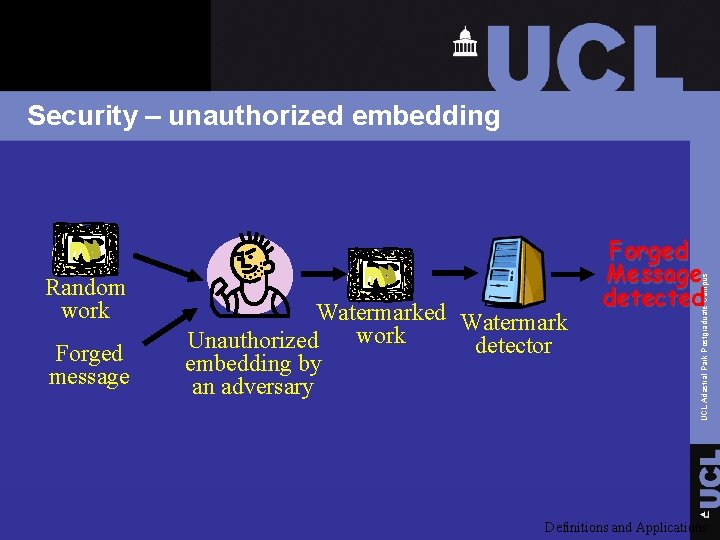
Security – unauthorized embedding Forged message Watermarked Watermark work Unauthorized detector embedding by an adversary UCL Adastral Park Postgraduate Campus Random work Forged Message detected Definitions and Applications

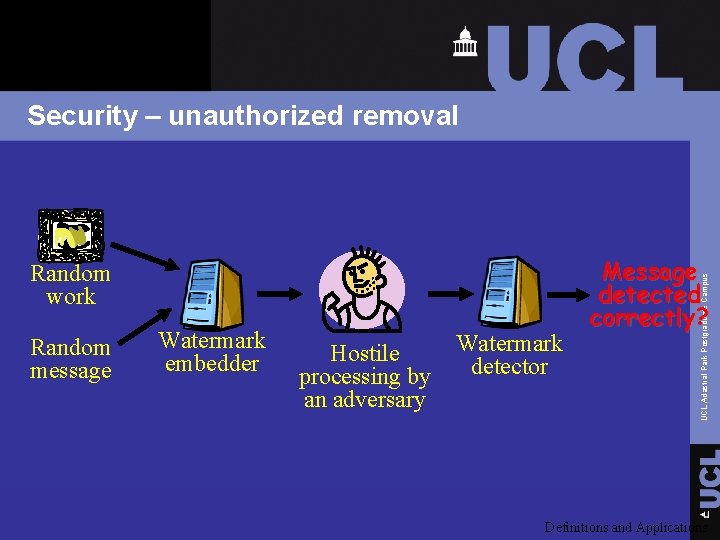
Security – unauthorized removal Random message Watermark embedder Hostile processing by an adversary Watermark detector Message detected correctly? UCL Adastral Park Postgraduate Campus Random work Definitions and Applications

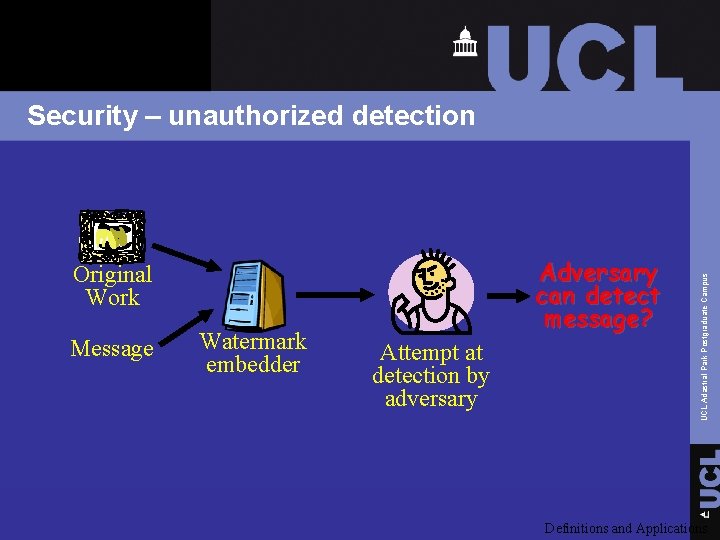
Adversary can detect message? Original Work Message Watermark embedder Attempt at detection by adversary UCL Adastral Park Postgraduate Campus Security – unauthorized detection Definitions and Applications

Watermarking applications Watermarking may be appropriate for applications in which data about a work must be imperceptibly embedded. Different applications place different requirements on system properties. Definitions and Applications

List of examples discussed q Broadcast Monitoring q Proof of Ownership q Transaction Tracking q Content Authentication UCL Adastral Park Postgraduate Campus q Owner Identification q Copy Control Definitions and Applications

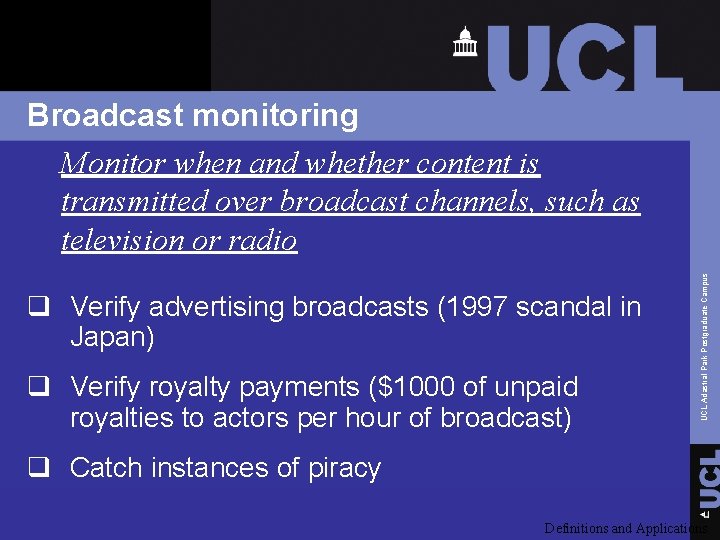
Original content Content was broadcast! Watermark embedder Broadcasting system Watermark detector UCL Adastral Park Postgraduate Campus Broadcast monitoring Definitions and Applications

q Verify advertising broadcasts (1997 scandal in Japan) q Verify royalty payments ($1000 of unpaid royalties to actors per hour of broadcast) UCL Adastral Park Postgraduate Campus Broadcast monitoring Monitor when and whether content is transmitted over broadcast channels, such as television or radio q Catch instances of piracy Definitions and Applications

Owner identification Original work Watermark embedder Distributed copy Alice is owner! Watermark detector UCL Adastral Park Postgraduate Campus Alice Definitions and Applications

Owner identification q Help honest people identify rightful owner q Notify people of copyright Ø In US, until 1988, such notice was required to retain copyright Ø Since 1988, presence of notice increases possible reward in lawsuits UCL Adastral Park Postgraduate Campus Watermark identifies owner of copyright, similar to a copyright notice Definitions and Applications

Owner identification UCL Adastral Park Postgraduate Campus The problem with text: this well-known image … Definitions and Applications

Owner identification UCL Adastral Park Postgraduate Campus … is a pirated part of a larger image. Definitions and Applications

Proof of ownership Original work Watermark embedder Distributed copy Alice is owner! Watermark detector UCL Adastral Park Postgraduate Campus Alice Bob Definitions and Applications

Proof of ownership q Differs from owner identification in two ways Ø Intended to carry burden of proof Ø Watermark need not be detectable by anyone other than owner (allows informed detection) UCL Adastral Park Postgraduate Campus Watermark is used to prove ownership in a court of law Definitions and Applications

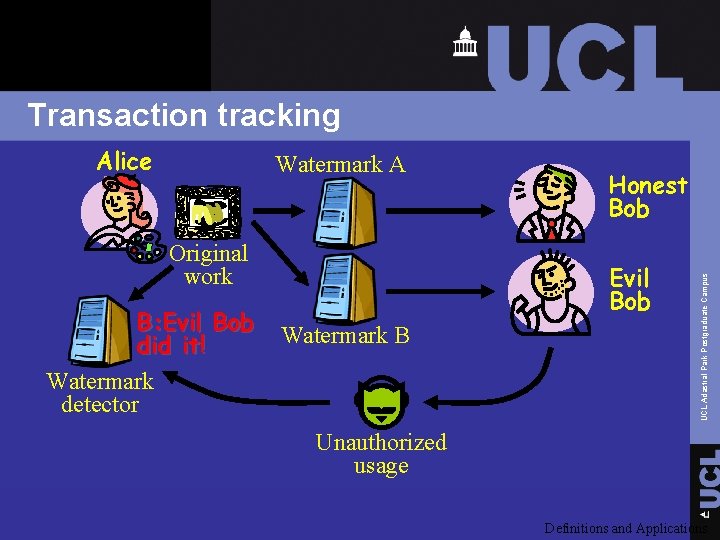
Transaction tracking Watermark A Original work B: Evil Bob did it! Watermark detector Honest Bob Evil Bob Watermark B UCL Adastral Park Postgraduate Campus Alice Unauthorized usage Definitions and Applications

Transaction tracking q Identifying pirates (Di. VX corporation) q Identifying information leaks (M. Thatcher, movie dailies) UCL Adastral Park Postgraduate Campus Watermarks record transaction histories of content, typically identifying first authorized recipient Definitions and Applications

Transaction tracking q One source of material is the annual distribution of Oscar screeners to the 5, 803 voting members of the Academy UCL Adastral Park Postgraduate Campus q The MPAA estimates that piracy costs the US film industry $3 B per year

Transaction tracking q Screeners appeared on the internet Ø The Last Samurai Ø Something's Gotta Give Ø Mystic River q Actor Carmine Caridi expelled from MPAA UCL Adastral Park Postgraduate Campus q Thomson system enabled the MPAA to distribute individually-watermarked VHS and DVD screeners to its 5, 803 eligible voting members

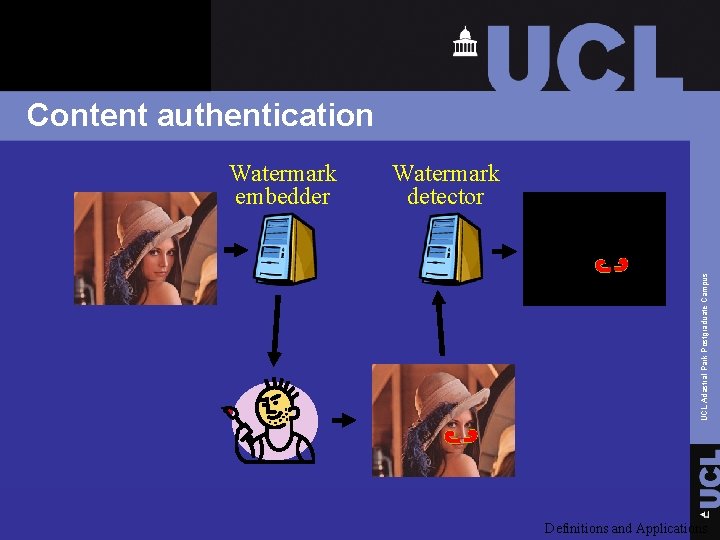
Content authentication Watermark detector UCL Adastral Park Postgraduate Campus Watermark embedder Definitions and Applications

Content authentication q Exact authentication: work is inauthentic if even one bit has changed q Selective authentication: work is inauthentic only if significantly changed q Tell-tale watermarks/localization: identify what changes have been made UCL Adastral Park Postgraduate Campus Watermark is used to detect modifications applied to cover work Definitions and Applications

Copy control q Record control: recording devices contain detectors and refuse to record copyrighted material q Playback control: players contain detectors and refuse to play pirated material UCL Adastral Park Postgraduate Campus Watermarks indicate whether content may be copied Definitions and Applications

Copy control Playback control Illegal copy Compliant recorder Record control UCL Adastral Park Postgraduate Campus Legal copy Compliant player Non-compliant recorder Definitions and Applications

Conclusions Definitions and Applications

Conclusions: Stuff not covered q Cipher and watermark keys q Modification and multiple watermarks q Cost UCL Adastral Park Postgraduate Campus q Erasability (whether watermark can be perfectly removed)

Conclusions: Take Away q Different applications place different requirements on system properties. UCL Adastral Park Postgraduate Campus q Watermarking may be appropriate for applications in which data about a work must be imperceptibly embedded.

Conclusions: Take Away Ø Ø Ø Ø Embedding effectiveness Fidelity Data payload Blind vs. informed detection False positive rate Robustness Security UCL Adastral Park Postgraduate Campus q Key properties include

Digression: The politics of DRM q Why does Hollywood care about piracy? Ø Loss in revenue Ø Evidence that peer-to-peer file sharing affects sales is mixed v But has been used to control the evolution of the digital market UCL Adastral Park Postgraduate Campus v But some level of piracy actually stimulates sales

Digression: The politics of DRM q Need content owners to provide content in new digital formats q Conflict of interests Ø Customers don’t want DRM Ø Legal and business contracts impose DRM UCL Adastral Park Postgraduate Campus q Why do computer and consumer electronics companies care about DRM?

Course outline UCL Adastral Park Postgraduate Campus q Part 1: Definitions and Applications q Part 2: Basic Algorithms and Concepts q Part 3: Informed Watermarking Course outline

Part 2: Basic Algorithms and Concepts

Basic Algorithms and Concepts: Outline q Algorithmic building blocks q Security issues q Conclusions UCL Adastral Park Postgraduate Campus q Robustness issues

Algorithmic building blocks Over the past 5 to 10 years of research, several ideas have emerged as basic building blocks of watermarking systems.

A simple watermark embedder Ø Watermark pattern, w Ø Cover image co Ø Embedding strength a q Compute watermarked image, cw, as UCL Adastral Park Postgraduate Campus q Given … Basic Algorithms and Concepts

UCL Adastral Park Postgraduate Campus A watermarked version of this … Basic Algorithms and Concepts

UCL Adastral Park Postgraduate Campus …looks like this Basic Algorithms and Concepts

Informed detection q Given q Subtract original to obtain watermark pattern (if present) UCL Adastral Park Postgraduate Campus Ø Possibly watermarked image c Ø Original cover image co Basic Algorithms and Concepts

Linear correlation test q Use linear correlation to determine whether UCL Adastral Park Postgraduate Campus q Linear correlation defined as q If c = co + n, then zlc(wn, w) @ 0 q If c = co + aw + n, then zlc(wn, w) @ azlc(w, w) Basic Algorithms and Concepts

Blind detection q No need to subtract out co before computing linear correlation. q White noise pattern tends to have lowmagnitude correlation with any image. UCL Adastral Park Postgraduate Campus q If w is chosen so that zlc(co, w) is likely to be close to 0, then zlc (c, w) @ zlc(wn, w). Basic Algorithms and Concepts

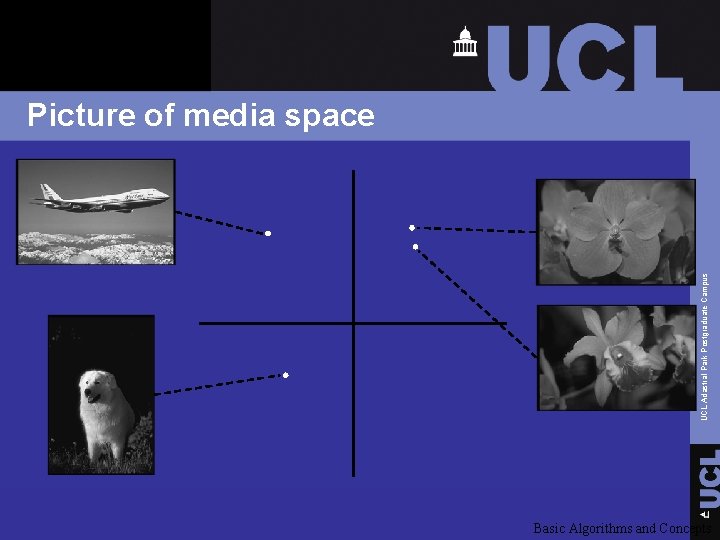
Interpreting system geometrically Ø 256 grayscale image -> 65, 536 dimensions (one for each pixel). Ø 5 second mono audio clip, sampled at 44, 100 Hz -> 220, 500 dimensions (one for each sample) UCL Adastral Park Postgraduate Campus q Media space – a high-dimensional space in which each point corresponds to a work. Basic Algorithms and Concepts

2 d pictures of media space Ø Abstraction of high-dimensional space (just pretend media space is really 2 d) Ø Projection of media space Ø Slice of media space UCL Adastral Park Postgraduate Campus q Several possible interpretations Basic Algorithms and Concepts

UCL Adastral Park Postgraduate Campus Picture of media space Basic Algorithms and Concepts

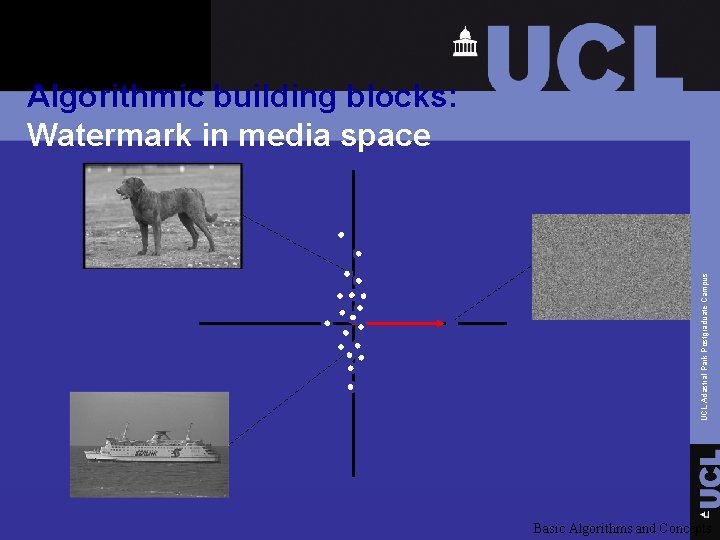
UCL Adastral Park Postgraduate Campus Algorithmic building blocks: Watermark in media space Basic Algorithms and Concepts

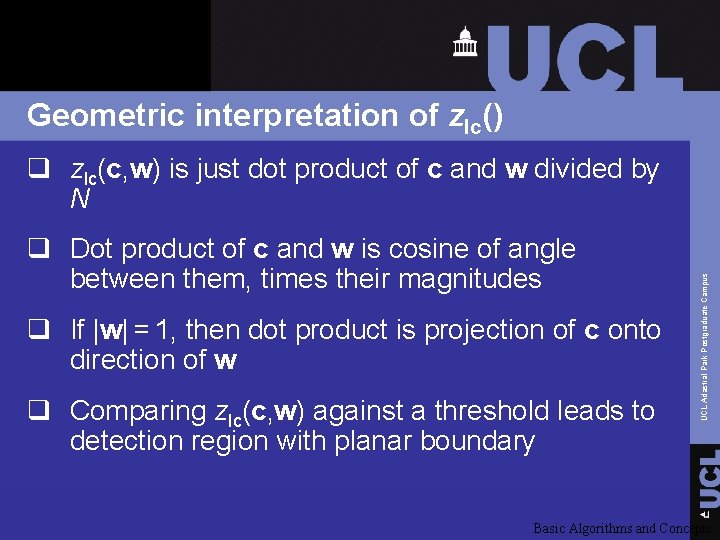
Geometric interpretation of zlc() q Dot product of c and w is cosine of angle between them, times their magnitudes q If |w| = 1, then dot product is projection of c onto direction of w q Comparing zlc(c, w) against a threshold leads to detection region with planar boundary UCL Adastral Park Postgraduate Campus q zlc(c, w) is just dot product of c and w divided by N Basic Algorithms and Concepts

UCL Adastral Park Postgraduate Campus Geometric interpretation of zlc() Basic Algorithms and Concepts

Now that we have a basic system … q cwn = ncw , where n is some scalar value q zlc(cwn, w) = n zlc(cw, w) q If n < 1, detection value might drop below threshold UCL Adastral Park Postgraduate Campus q … let’s consider a problem: What happens when we change the contrast of the image? Basic Algorithms and Concepts

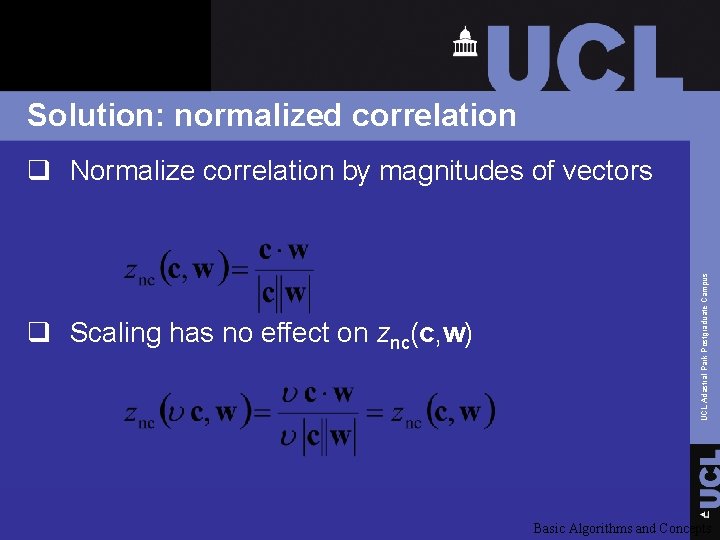
Solution: normalized correlation q Scaling has no effect on znc(c, w) UCL Adastral Park Postgraduate Campus q Normalize correlation by magnitudes of vectors Basic Algorithms and Concepts

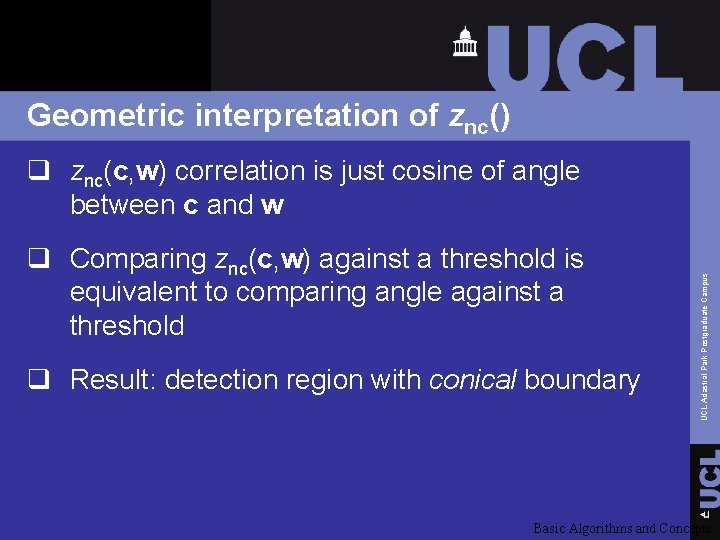
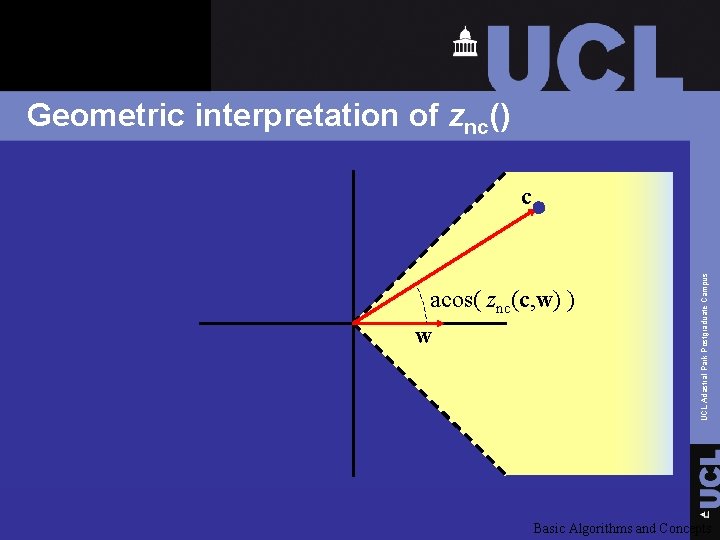
Geometric interpretation of znc() q Comparing znc(c, w) against a threshold is equivalent to comparing angle against a threshold q Result: detection region with conical boundary UCL Adastral Park Postgraduate Campus q znc(c, w) correlation is just cosine of angle between c and w Basic Algorithms and Concepts

Geometric interpretation of znc() acos( znc(c, w) ) w UCL Adastral Park Postgraduate Campus c Basic Algorithms and Concepts

Another problem q Detection value will depend on autocorrelation function of watermark pattern. q White noise pattern has close to zero autocorrelation. q Watermark is unlikely to be detected. UCL Adastral Park Postgraduate Campus q What happens if the image is spatially shifted a little? Basic Algorithms and Concepts

Possible solution q Fourier-magnitudes are invariant to translation UCL Adastral Park Postgraduate Campus q Watermark Fourier-magnitude instead of pixel values Basic Algorithms and Concepts

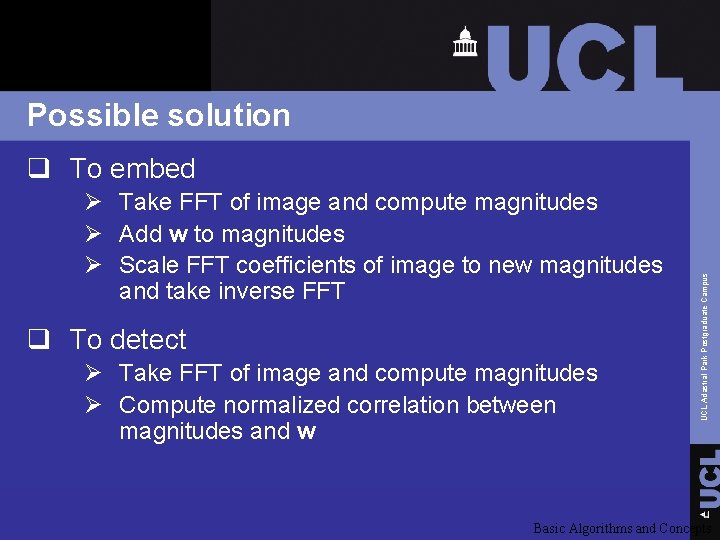
Possible solution Ø Take FFT of image and compute magnitudes Ø Add w to magnitudes Ø Scale FFT coefficients of image to new magnitudes and take inverse FFT q To detect Ø Take FFT of image and compute magnitudes Ø Compute normalized correlation between magnitudes and w UCL Adastral Park Postgraduate Campus q To embed Basic Algorithms and Concepts

Watermark extraction Ø A watermark extraction process that maps points in media space to points in some marking space (Fourier-magnitude space, in this case) Ø A simple watermarking system that operates in marking space UCL Adastral Park Postgraduate Campus q We can view the preceding system as comprising two basic parts Basic Algorithms and Concepts

Reasons for watermark extraction Ø Project into distortion invariant space Ø Invert distortions Ø Reduce noise q Reduce computational cost q Increase security Ø Key-based extraction UCL Adastral Park Postgraduate Campus q Increase robustness Basic Algorithms and Concepts

“Transform domain” watermarking Ø Ø “Spatial-domain watermarking” (no transform) “DCT-domain watermarking” “Wavelet-domain watermarking” Etc. q But … UCL Adastral Park Postgraduate Campus q Many authors categorize watermarking systems by transforms included in their extraction processes, e. g. … Basic Algorithms and Concepts

“Transform domain” watermarking Ø If T is a linear, energy-preserving transform, then zlc( T(c), w ) = zlc( c, T-1(w) ) Ø Thus a linear-correlation-based system in domain T is the same as a spatial-domain system with a different watermark pattern q It is the nonlinearities in the extraction process that distinguish a system’s behavior UCL Adastral Park Postgraduate Campus q … the transform alone says little about how the system works Basic Algorithms and Concepts

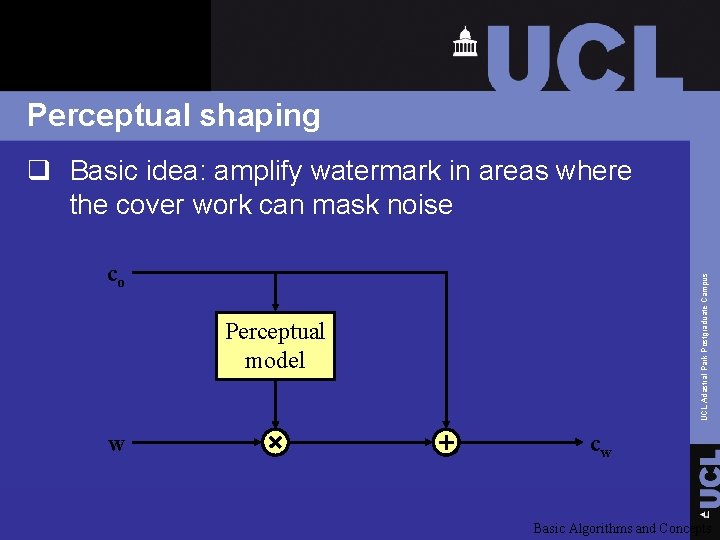
Perceptual shaping q Basic idea: amplify watermark in areas where the cover work can mask noise UCL Adastral Park Postgraduate Campus co Perceptual model w cw Basic Algorithms and Concepts

UCL Adastral Park Postgraduate Campus Image before embedding Basic Algorithms and Concepts

UCL Adastral Park Postgraduate Campus Without perceptual shaping Basic Algorithms and Concepts

UCL Adastral Park Postgraduate Campus With perceptual shaping Basic Algorithms and Concepts

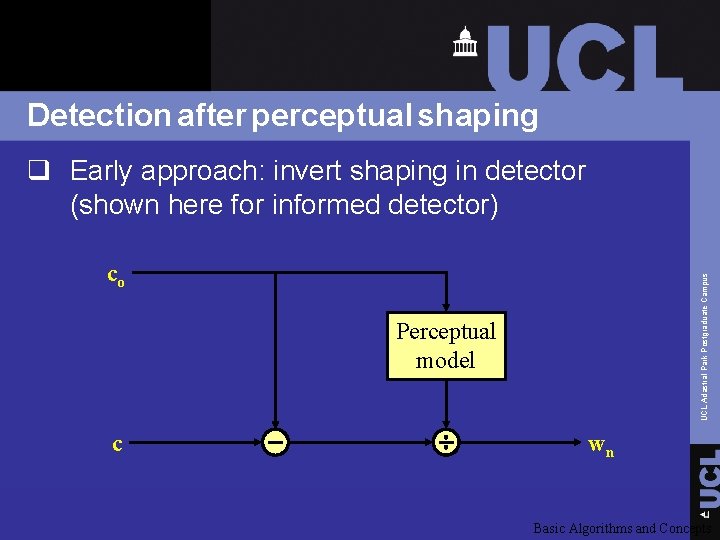
Detection after perceptual shaping q Early approach: invert shaping in detector (shown here for informed detector) UCL Adastral Park Postgraduate Campus co Perceptual model c wn Basic Algorithms and Concepts

Detection after perceptual shaping Ø Distortion of watermark pattern degrades detection value for given watermark scaling value, a, but … Ø … possible to use larger value of a because pattern is better hidden UCL Adastral Park Postgraduate Campus q Not necessary to invert perceptual shaping Basic Algorithms and Concepts

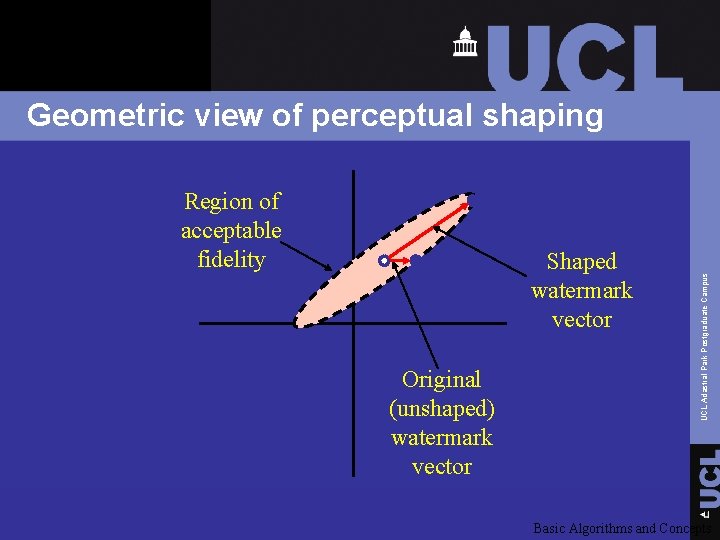
Region of acceptable fidelity Shaped watermark vector Original (unshaped) watermark vector UCL Adastral Park Postgraduate Campus Geometric view of perceptual shaping Basic Algorithms and Concepts

Robustness Issues The robustness of a watermark is its ability to survive normal processing.

Additive Noise Watermarked image is corrupted by additive noise q Linear Correlation (matched filtering) is optimal when noise is AWGN. UCL Adastral Park Postgraduate Campus q Basic Algorithms and Concepts

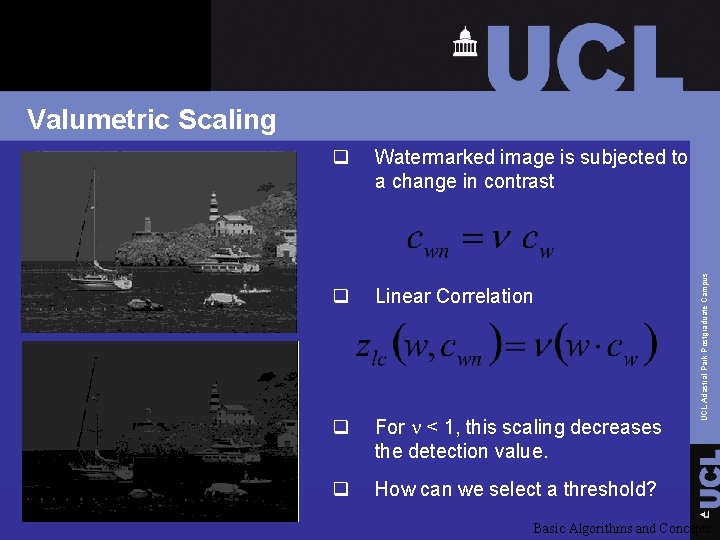
q Watermarked image is subjected to a change in contrast q Linear Correlation q For n < 1, this scaling decreases the detection value. q How can we select a threshold? UCL Adastral Park Postgraduate Campus Valumetric Scaling Basic Algorithms and Concepts

Valumetric Scaling Normalized Correlation Independent of vector magnitude q Describes the cosine of the angle between the vectors q -1 znc +1 1 -n q UCL Adastral Park Postgraduate Campus q Unit Sphere Basic Algorithms and Concepts

uncompressed work q Quantization noise cannot be modeled as additive white noise q There are current efforts to model quantization noise Transform Quantization Entropy Coding compressed work Canonical Transform Coder Ø Ø Eggers and Girod Appendix B. 5 UCL Adastral Park Postgraduate Campus Quantization Basic Algorithms and Concepts

Synchronization Geometric distortion in imagery Ø q translation, rotation, zoom, aspect ratio, skew, perspective distortion, warp Temporal distortion in audio Ø time delay, time scaling q Video can suffer from both geometric and temporal misalignments q Noise due to synchronization errors is not well modeled as additive white noise. UCL Adastral Park Postgraduate Campus q Basic Algorithms and Concepts

Synchronization Approaches Ø Detection applied at all possible temporal/geometric distortions Ø Negative impact on false positive probability Ø Usually requires too much computation UCL Adastral Park Postgraduate Campus q Exhaustive Search Basic Algorithms and Concepts

Synchronization Approaches Ø Synchronization pattern is embedded along with the payload-carrying pattern. Ø Registration to synchronization pattern prior to detection. Ø Negative impact on fidelity and security UCL Adastral Park Postgraduate Campus q Synchronization Basic Algorithms and Concepts

Synchronization Approaches Ø Watermark location in time or space is relative to extracted features Ø Example: audio reference pattern added between salient points UCL Adastral Park Postgraduate Campus q Implicit Synchronization Basic Algorithms and Concepts

Synchronization Approaches Ø Design patterns that are invariant to desynchronization Ø Example: Use of Fourier magnitude in watermark extraction process for shift invariance UCL Adastral Park Postgraduate Campus q Invariance Basic Algorithms and Concepts

Security Issues The security of a watermark is its ability to resist hostile attacks specifically designed to defeat the purpose of the watermark.

Robustness Ø Desynchronization Attacks Ø Noise Removal Attacks UCL Adastral Park Postgraduate Campus q Security against unauthorized removal requires robustness to any process that maintains fidelity Basic Algorithms and Concepts

Mosaic Attack q Each patch is too small for reliable detection q Patches are displayed in a table such that patch edges are adjacent UCL Adastral Park Postgraduate Campus q Image is broken into many small rectangular patches Basic Algorithms and Concepts

Collusion Attacks q Many different works, same watermark q Simple example: averaging Ø Average of many different works gives an estimate of the watermark Ø Average of many copies of the same work reduces the strength of each watermark UCL Adastral Park Postgraduate Campus q Many different watermarks, same work Basic Algorithms and Concepts

Copy Attack q Watermark is “copied” from one work to another q Example: apply a watermark removal attack to obtain an estimate of the watermark, add to fake. UCL Adastral Park Postgraduate Campus q Unauthorized Embedding Basic Algorithms and Concepts

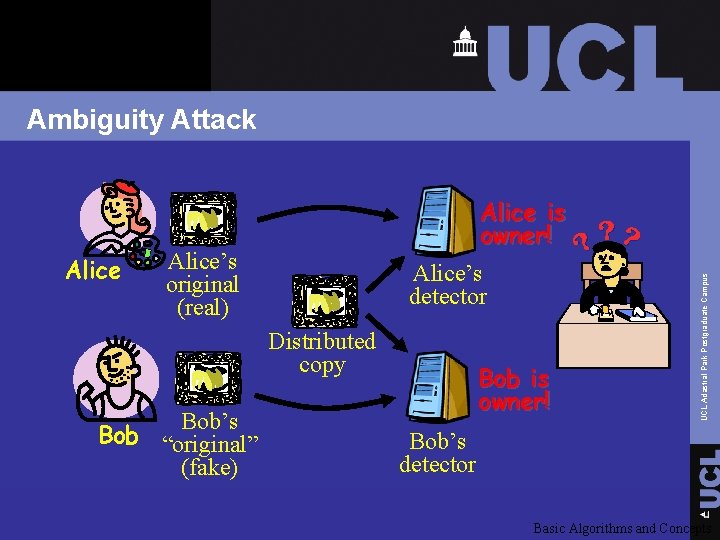
Ambiguity Attack q Example: define fake watermark pattern and subtract from the distributed image. This is the fake “original. ” Ø Difference between distributed and Bob’s original contains Bob’s watermark Ø Difference between distributed and Alice’s original contains Alice’s watermark UCL Adastral Park Postgraduate Campus q Create the appearance that a watermark has been added to someone else’s work Basic Algorithms and Concepts

Ambiguity Attack Alice’s original (real) Alice’s detector Distributed copy Bob’s Bob “original” (fake) Bob is owner! UCL Adastral Park Postgraduate Campus Alice is owner! Bob’s detector Basic Algorithms and Concepts

Ambiguity Attack Ø May be possible to implement by making watermark dependent on cryptographic hash of original work Ø Strictly-speaking, provides proof of ancestry, rather than proof of ownership UCL Adastral Park Postgraduate Campus q Solution to ambiguity attack: Alice uses system that cannot be hacked Basic Algorithms and Concepts

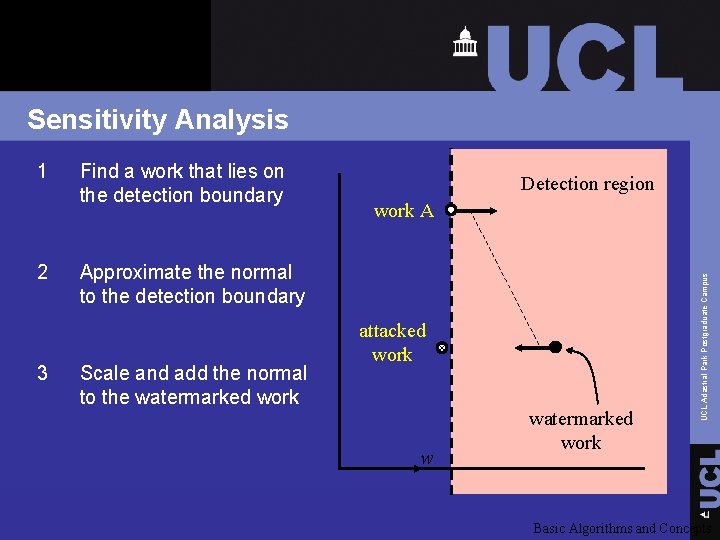
Sensitivity Analysis q Estimate the normal to the detection region surface boundary at some point q Assume that this normal indicates a short path out of the detection region UCL Adastral Park Postgraduate Campus q Technique for removing watermark when adversary has black box detector Basic Algorithms and Concepts

Sensitivity Analysis 2 3 Find a work that lies on the detection boundary Detection region work A Approximate the normal to the detection boundary Scale and add the normal to the watermarked work attacked work w watermarked work UCL Adastral Park Postgraduate Campus 1 Basic Algorithms and Concepts

Conclusions Basic Algorithms and Concepts

Conclusions: Major stuff not covered q Message-coding for multi-bit watermarks Ø “Constraint-based” watermarking (can usually be recast as correlation-based) Ø Quantization-based watermarking (will be covered in part 3) q Authentication methods UCL Adastral Park Postgraduate Campus q Non correlation-based watermarking q ROC Curves Basic Algorithms and Concepts

Conclusions: Take Away q Most processing is not well modeled as AWGN q Normalized correlation provides robustness to amplitude changes q Helpful to think of a work as a point in a high dimensional space UCL Adastral Park Postgraduate Campus q Linear correlation (matched filtering) is optimal for detecting a signal in AWGN Basic Algorithms and Concepts

Conclusions: Take Away q Perceptual modeling can improve fidelity and allow for stronger embedding q Robustness to desynchronization is an difficult problem q Collusion attacks and sensitivity analysis are significant security challenges UCL Adastral Park Postgraduate Campus q Watermark extraction: project a work to another space for embedding and/or detection Basic Algorithms and Concepts

Outline q Part 2: Basic Algorithms and Concepts q Part 3: Informed Watermarking UCL Adastral Park Postgraduate Campus q Part 1: Definitions and Applications

Part 3: Informed watermarking

Informed watermarking: Outline q Idea of informed watermarking q Informed shaping UCL Adastral Park Postgraduate Campus q Informed coding q Conclusions Informed watermarking

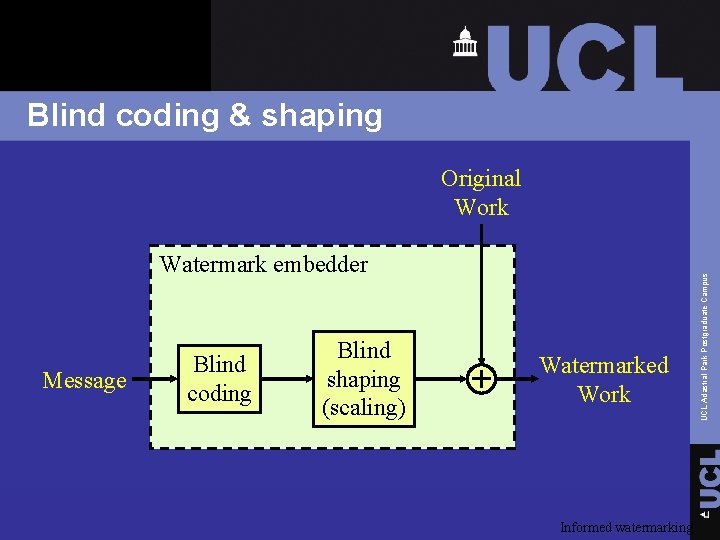
Idea of informed watermarking Informed watermarking is the practice of using information about the cover work during watermark coding and shaping. Informed watermarking

Blind coding & shaping Watermark embedder Message Blind coding Blind shaping (scaling) Watermarked Work Informed watermarking UCL Adastral Park Postgraduate Campus Original Work

Informed shaping Watermark embedder Message Blind coding Informed shaping Watermarked Work Informed watermarking UCL Adastral Park Postgraduate Campus Original Work

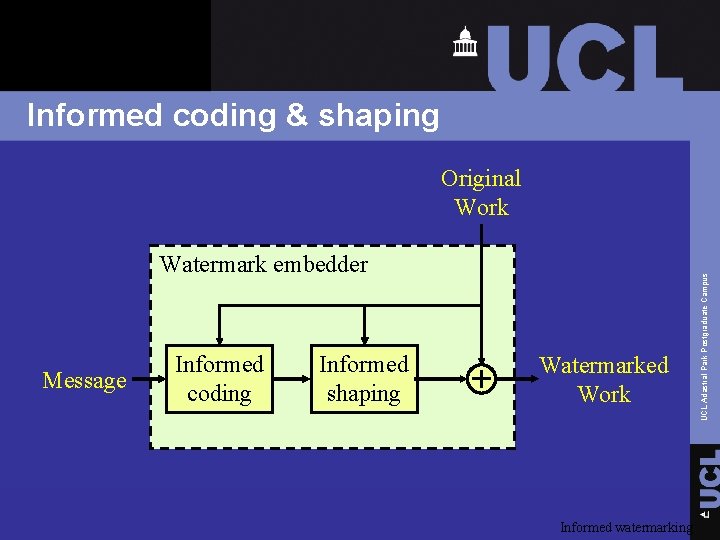
Informed coding & shaping Watermark embedder Message Informed coding Informed shaping Watermarked Work Informed watermarking UCL Adastral Park Postgraduate Campus Original Work

Central insight Ø Shannon’s model: transmitter has knowledge of channel’s noise characteristics Ø In watermarking, cover Work = (part of) noise Ø Theoretical results for this type of channel should apply to watermarking Informed watermarking UCL Adastral Park Postgraduate Campus q Watermarking with informed embedder and blind detector = communication with side information at the transmitter

Consequences q Informed shaping alone Ø Allows more precise control of fidelity/robustness tradeoff UCL Adastral Park Postgraduate Campus q Informed coding + informed shaping Ø Greatly increases payload for a given fidelity/robustness performance Ø Alternatively, improves fidelity/robustness performance for a given payload Informed watermarking

Informed shaping The cover work can be used to inform perceptual shaping. It can also be used to adjust watermark pattern for maximal robustness. Informed watermarking

Basic approach q Treat detection algorithm and parameters as given q Design best embedder we can Informed watermarking UCL Adastral Park Postgraduate Campus q Design detector (we’ll use the linear-correlation detector from Part 2)

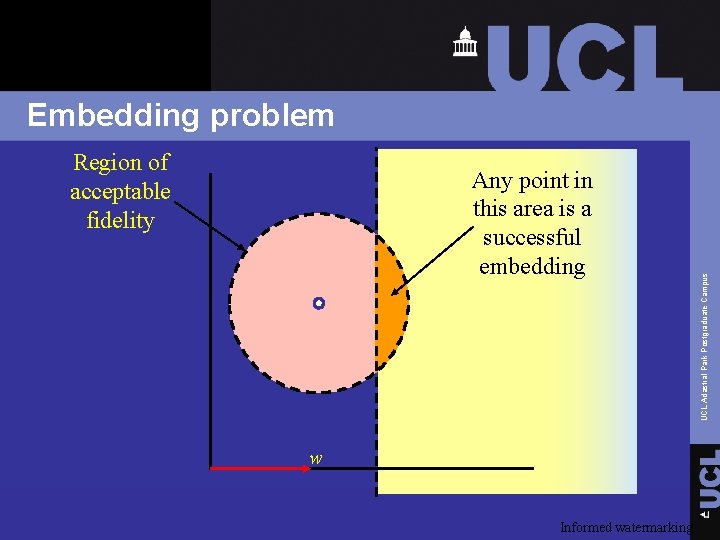
Embedding problem q Objective: produce an image within the intersection of a region of acceptable fidelity and the detection region Informed watermarking UCL Adastral Park Postgraduate Campus q The embedder is capable of producing any image

Region of acceptable fidelity Any point in this area is a successful embedding w Informed watermarking UCL Adastral Park Postgraduate Campus Embedding problem

Embedding problem q Several possible approaches UCL Adastral Park Postgraduate Campus Ø Maximize robustness for a given fidelity Ø Maximize fidelity for a given robustness q Either approach requires Ø Estimate of fidelity Ø Estimate of robustness Informed watermarking

Simple embedding method q Assume robustness is monotonic function of linear correlation q Under these assumptions, blind embedding achieves maximum “robustness” for given “fidelity” q Alternatively … Informed watermarking UCL Adastral Park Postgraduate Campus q Assume MSE indicates fidelity (better estimates lead to perceptual shaping)

Simple embedding method UCL Adastral Park Postgraduate Campus q … we can minimize fidelity impact while embedding for a constant “robustness” Informed watermarking

Estimating robustness Ø True for linear correlation Ø Not true for other detection measures q For normalized correlation, we have obtained good results by estimating amount of white noise that may be added before watermark is likely to be lost Informed watermarking UCL Adastral Park Postgraduate Campus q Simple assumption: robustness is monotonic function of detection value

Informed coding Significantly larger data payloads can be embedded if the mapping between messages and watermark patterns is dependent on the cover work. Informed watermarking

Informed coding: Outline q Writing on dirty paper (problem studied by M. Costa) UCL Adastral Park Postgraduate Campus q Dirty-paper codes q Application of dirty-paper codes to watermarking q Experimental results q Conclusions Informed watermarking

Informed coding: Writing on dirty paper Ø Obtain a piece of paper with normally-distributed dirt Ø Write a message using limited ink Ø Send message, acquiring more dirt along the way Ø Recipient cannot distinguish dirt from ink Ø How much information can we send? Informed watermarking UCL Adastral Park Postgraduate Campus q M. Costa studied a “dirty-paper channel”

First noise Second s noise n m Transmitter x y Receiver m’ x limited by power constraint: Informed watermarking UCL Adastral Park Postgraduate Campus Informed coding: The dirty-paper channel

First noise has no effect on channel capacity Informed watermarking UCL Adastral Park Postgraduate Campus Informed coding: Costa’s result

Informed coding: Dirty-paper codes Ø Dirty-paper code = code in which each message is represented by several alternative code vectors Ø From the set of vectors that represent the desired message, choose the one, u, that is closest to the first noise, s Ø Transmit a function of u and s, for example x = u-s Informed watermarking UCL Adastral Park Postgraduate Campus q Basic idea

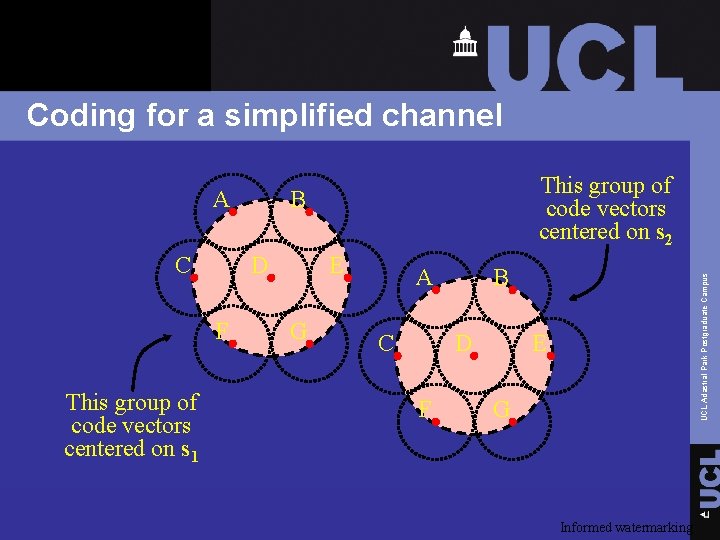
Coding for a simplified channel Ø First noise has only two possible values, s 1 and s 2 (i. e. there are only two possible patterns of dirt on the paper) Ø Remainder of channel is the same q If s 1 is sufficiently different from s 2, then Costa’s result is easy to obtain Informed watermarking UCL Adastral Park Postgraduate Campus q Consider a simplified version of the dirty-paper channel

Coding for a simplified channel C D F This group of code vectors centered on s 1 This group of code vectors centered on s 2 B E G A C B D F UCL Adastral Park Postgraduate Campus A E G Informed watermarking

Informed coding: Dirty-paper codes Try to design a dirty-paper code in which, within the power-constraint around every possible s, there is at least one code vector for each message. Informed watermarking UCL Adastral Park Postgraduate Campus For full dirty-paper channel:

Coding for full dirty-paper channel q Capacity cannot be achieved transmitting x = u – s. q Costa transmits x = u – as, where a is a carefully-chosen constant Informed watermarking UCL Adastral Park Postgraduate Campus q Code must ensure that, within the powerconstraint around every possible s, there is at least one code vector for each message.

Application to watermarking Ø In watermarking, noise is not Gaussian Ø Non-Gaussian noise necessitates non-spherical detection regions (e. g. cones) q Lessons from Costa Ø Use dirty-paper codes Ø Use non-trivial informed embedding Informed watermarking UCL Adastral Park Postgraduate Campus q Costa’s proof does not translate directly to watermarking

Practical dirty-paper codes Ø Requires exhaustive search during encoding and decoding Ø Practical for only very small data payloads q Lattice code is most-studied practical code Ø Chen & Wornell (“Dither Index Modulation”, “Quantization Index Modulation”) Ø Eggers, Su, & Girod (“Scalar Costa Scheme”) Informed watermarking UCL Adastral Park Postgraduate Campus q Costa’s code is generated randomly

Informed coding: Lattice codes q Bit encoded by choosing between two quantization points 0 1 0 1 0 Informed watermarking UCL Adastral Park Postgraduate Campus q Each dimension in marking space encodes one symbol, usually one bit

Properties of lattice codes q Not usually as robust as correlation-based systems Ø Correlation-based systems have better payload/robustness tradeoff when noise is high Ø Lattice codes susceptible to changes in image brightness or audio volume Informed watermarking UCL Adastral Park Postgraduate Campus q Typically much higher capacity than correlationbased systems (> 1000 bits)

Conclusions Informed watermarking

Conclusions: Stuff not covered q Informed-embedding for multi-bit watermarks q Application of informed-coding to correlationbased systems Informed watermarking UCL Adastral Park Postgraduate Campus q Syndrome coding

Conclusions: Take Away q Informed shaping q Informed coding Ø Define several patterns for each message, and embed the one that’s closest to the cover work Ø In theory, capacity of watermarking might be unaffected by distribution of cover works Informed watermarking UCL Adastral Park Postgraduate Campus Ø Embedder may choose any point in the detection region for the desired message Ø Best to base choice on an estimate of robustness

UCL Adastral Park Postgraduate Campus Future directions

Future directions q Research v Quantization index modulation v Syndrome coding v Trellis coding Ø Robustness v Non-random processes • Esp. geometric distortions UCL Adastral Park Postgraduate Campus Ø Informed coding

Future directions q Research v Collusion attacks v Others … UCL Adastral Park Postgraduate Campus Ø Security

Future directions q Commercial applications v Movie screeners v Digital cinema Ø Broadcast monitoring Ø Metadata v Lyrics in MP 3 files UCL Adastral Park Postgraduate Campus Ø Transaction tracking

Future directions q Commercial applications v Cameras v Surveillance video v Medical imagery Ø Enhancements to legacy systems v 3 D HDTV – Benoit Macq UCL Adastral Park Postgraduate Campus Ø Authentication

Future directions q Commercial applications? UCL Adastral Park Postgraduate Campus Ø Copy control Ø Proof of ownership

Future directions q Commercial applications v Not technology v Similar to commercial applications of cryptography UCL Adastral Park Postgraduate Campus Ø Must be based on a service or product
 Ingemar j. cox
Ingemar j. cox Watermarking and steganography
Watermarking and steganography Ingemar bohlin
Ingemar bohlin Ingemar bohlin
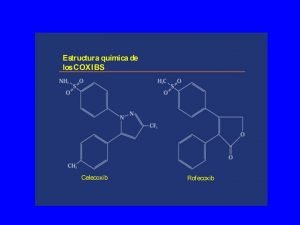
Ingemar bohlin Inhibidores selectivos de la cox-2
Inhibidores selectivos de la cox-2 Alccs
Alccs Cox regression
Cox regression Lysalgo
Lysalgo Coxweb
Coxweb Black cox model
Black cox model Alicia cox ph
Alicia cox ph Raymond cox qc
Raymond cox qc Jessica cox biografia
Jessica cox biografia What's wrong in the picture
What's wrong in the picture Kansas soil map
Kansas soil map Minitab box cox
Minitab box cox Biography of kobe bryant
Biography of kobe bryant Cox valga
Cox valga Efpractice
Efpractice Cox.net
Cox.net Cox 2 inhibitors
Cox 2 inhibitors Penny cox uf
Penny cox uf Cox=eox/tox
Cox=eox/tox Cox
Cox Haspsa
Haspsa Cox-merz rule
Cox-merz rule Cox emil
Cox emil Cox mill elementary school
Cox mill elementary school Tom cox intermediate
Tom cox intermediate Cox urban furniture
Cox urban furniture Minoxfen
Minoxfen Tom cox intermediate
Tom cox intermediate Nelson and cox
Nelson and cox Nele leosk
Nele leosk Nelson and cox
Nelson and cox Box-cox dönüşümü
Box-cox dönüşümü Wash sector cox's bazar
Wash sector cox's bazar Regressiokerroin
Regressiokerroin L
L Cox spam blocker
Cox spam blocker Cox investor relations
Cox investor relations Dr arzoo khalid
Dr arzoo khalid Carrie cox
Carrie cox Nele cox
Nele cox Pengertian warga digital adalah
Pengertian warga digital adalah Digital markets and digital goods
Digital markets and digital goods Digital data digital signals
Digital data digital signals Data encoding and transmission
Data encoding and transmission E-commerce: digital markets, digital goods
E-commerce: digital markets, digital goods Digital data to digital signal encoding
Digital data to digital signal encoding Luxinnovation logo
Luxinnovation logo E-commerce digital markets digital goods
E-commerce digital markets digital goods Acpo guidelines audit trail
Acpo guidelines audit trail Matt liotta
Matt liotta Jessica and matt have been together for 1 month
Jessica and matt have been together for 1 month Matt carver sai
Matt carver sai Matt rosenberg md
Matt rosenberg md Oded horovitz
Oded horovitz Matt poyton
Matt poyton Matt beckham
Matt beckham Matt nygren
Matt nygren Matt calvano
Matt calvano Matt toolan
Matt toolan Matthew 37-39
Matthew 37-39 Msg tired
Msg tired Weik fitness
Weik fitness Matt monro autumn leaves
Matt monro autumn leaves Matt bacak
Matt bacak Dr matt hewitt bons cork
Dr matt hewitt bons cork Matthew 14 22 33
Matthew 14 22 33 Dr matt chamberlain
Dr matt chamberlain Typografiskt mått med höjd
Typografiskt mått med höjd Typografiskt mått med höjd
Typografiskt mått med höjd Matt 16:24
Matt 16:24 100 000 reasons matt redman
100 000 reasons matt redman Dr matt dwyer
Dr matt dwyer Nick walker matt jansen split
Nick walker matt jansen split Matt doughty
Matt doughty Matt looney
Matt looney Matt carver sai
Matt carver sai Kari jess
Kari jess Matthew 6 31
Matthew 6 31 28 - 18
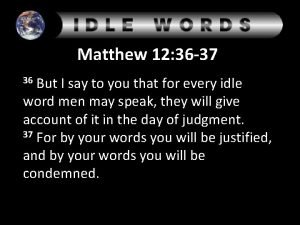
28 - 18 Matthew 12:36 commentary
Matthew 12:36 commentary Lt meeting
Lt meeting Matt bickley
Matt bickley Solving quadratic equations dr frost
Solving quadratic equations dr frost Matt mayo
Matt mayo Matt moshiri
Matt moshiri Matt hispano
Matt hispano Dr matt hewitt wife
Dr matt hewitt wife Matt dzurik
Matt dzurik Matt rosemier
Matt rosemier Conjoint analysis
Conjoint analysis Matt liotta
Matt liotta Why did john the baptist hesitate to baptize jesus
Why did john the baptist hesitate to baptize jesus Matthew 12 nlt
Matthew 12 nlt The stars
The stars Jess and matt
Jess and matt Kärlfog
Kärlfog Matt boggus
Matt boggus Matt bogoshian
Matt bogoshian Matt 6:5-7
Matt 6:5-7 Matt ryan southampton
Matt ryan southampton Matt wagaman
Matt wagaman Matt sakaguchi
Matt sakaguchi Matt 10:12
Matt 10:12 Matt bellamy age
Matt bellamy age Matthew 4 1-11 kjv
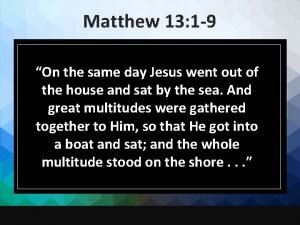
Matthew 4 1-11 kjv Matt 13:1-9
Matt 13:1-9 Matthew moisan
Matthew moisan Shayok chakraborty
Shayok chakraborty Matthew 5 amp
Matthew 5 amp Matt 17 20
Matt 17 20 Matt kittay
Matt kittay Matt joyce
Matt joyce Matt baldock
Matt baldock Matt robie
Matt robie Matt rosenberg md
Matt rosenberg md Matt huddleston
Matt huddleston Matt thiessen
Matt thiessen Cse 3541
Cse 3541 Matt prusak
Matt prusak Dr matthew tinney
Dr matthew tinney Matt pharr tamu
Matt pharr tamu The talented mr ripley chapter summary
The talented mr ripley chapter summary Matt 20:25-28
Matt 20:25-28 Matt tietjen
Matt tietjen Matt brim
Matt brim Matt staufer
Matt staufer Matt weyant
Matt weyant Matt yurgelun
Matt yurgelun Matt boggus
Matt boggus Matt casella
Matt casella What is mi
What is mi Matthew 22 34 40
Matthew 22 34 40 Matt zler
Matt zler Matt mettler
Matt mettler Eight parables
Eight parables Taylor stein uf
Taylor stein uf Matt colletti
Matt colletti Matt h evans
Matt h evans Dr frost interior and exterior angles
Dr frost interior and exterior angles Matt palmero
Matt palmero Matt talbot hostel
Matt talbot hostel Centreville high school
Centreville high school Matt dollinger
Matt dollinger Matt hourihan
Matt hourihan Matt strassler
Matt strassler Edr features
Edr features